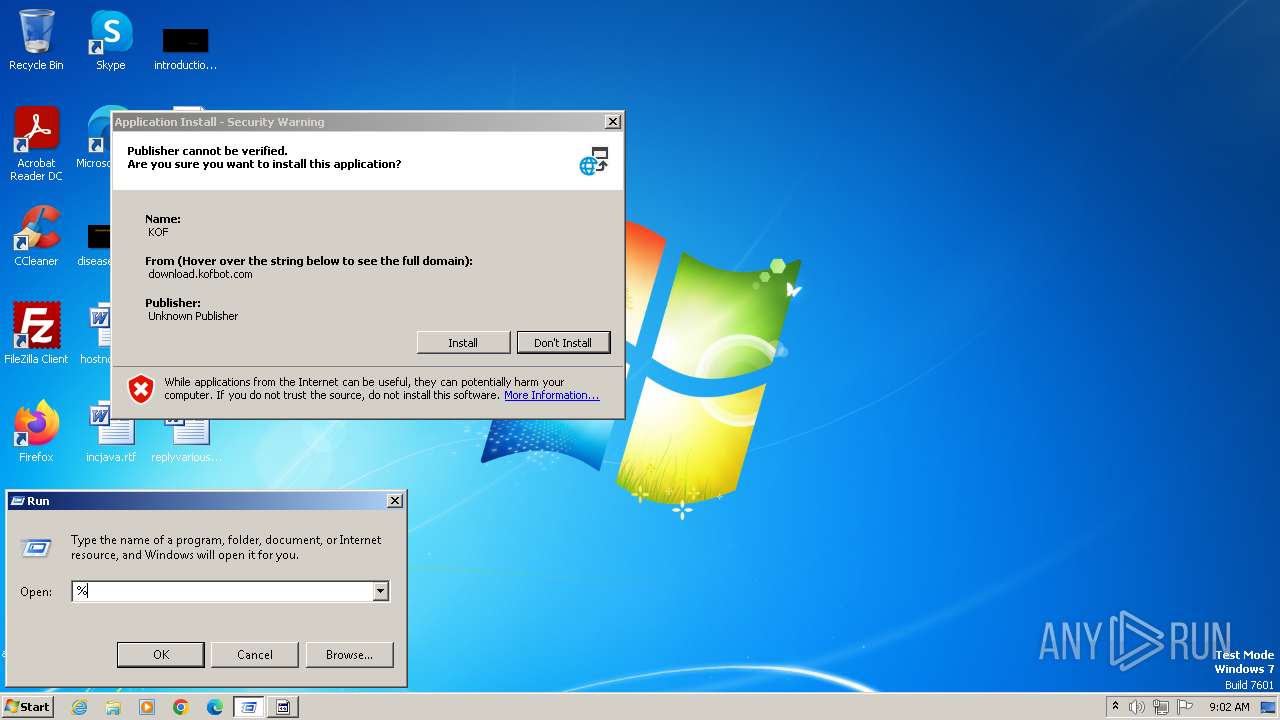
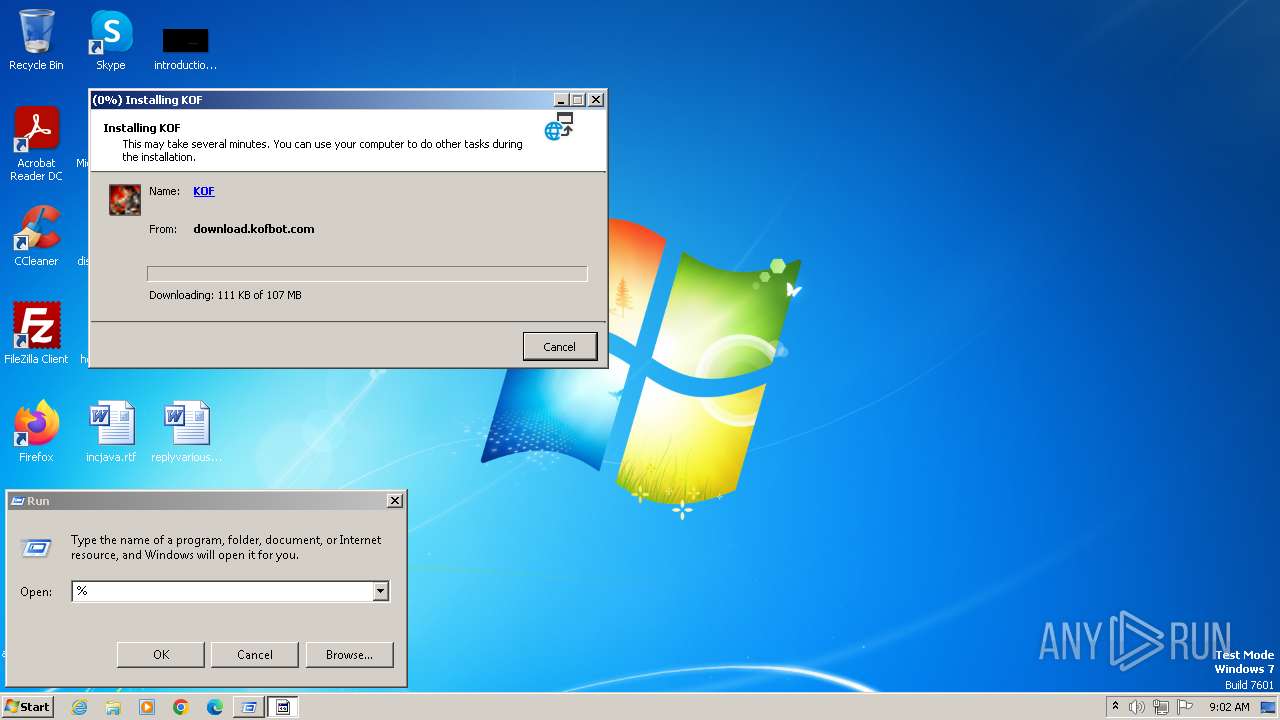
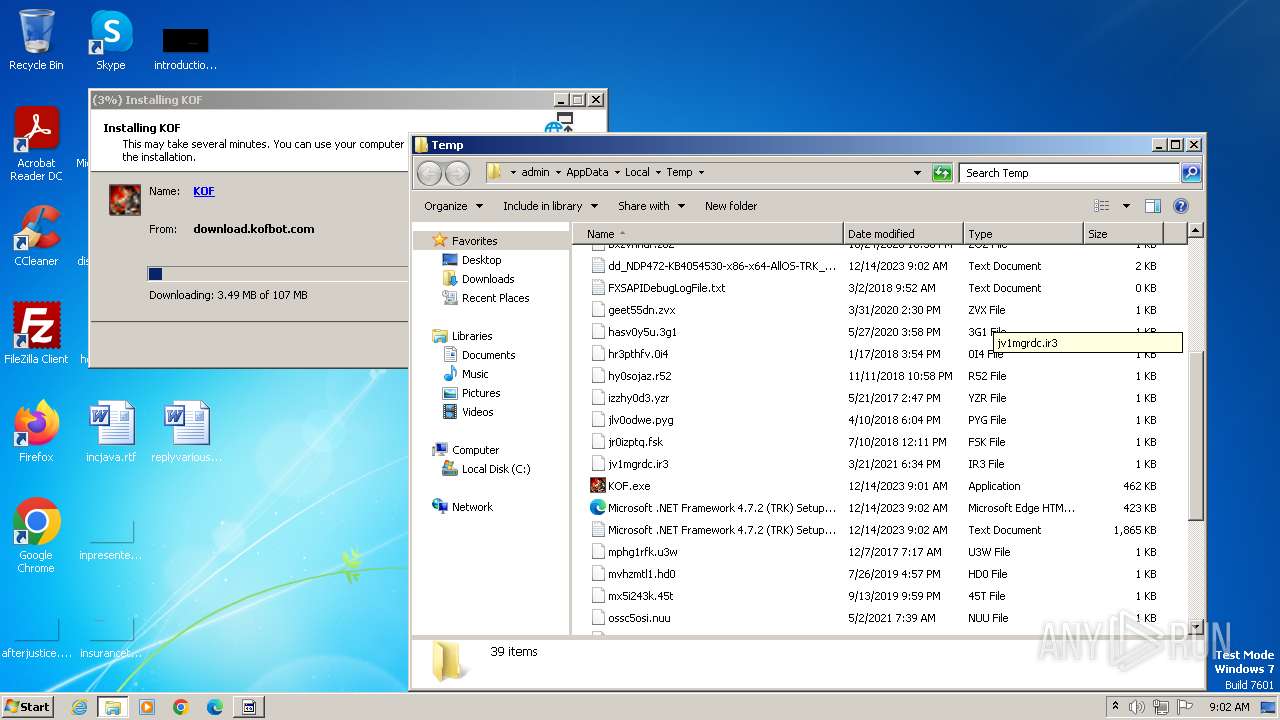
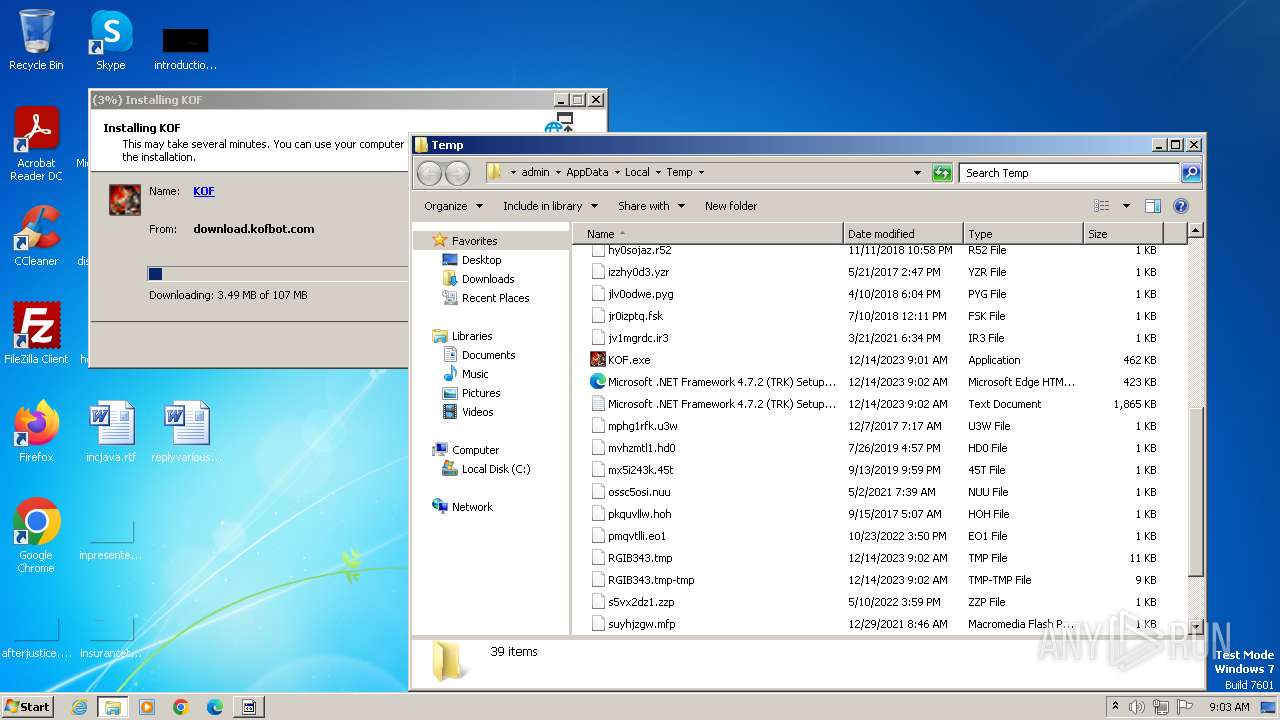
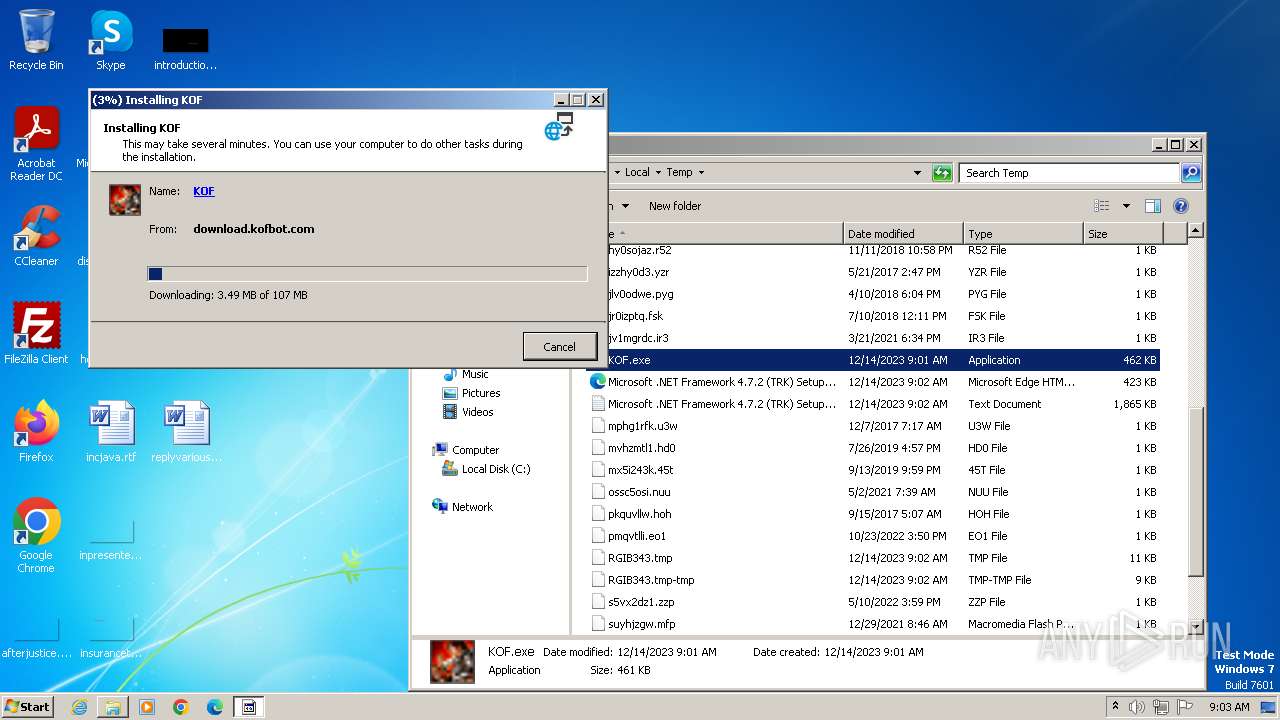
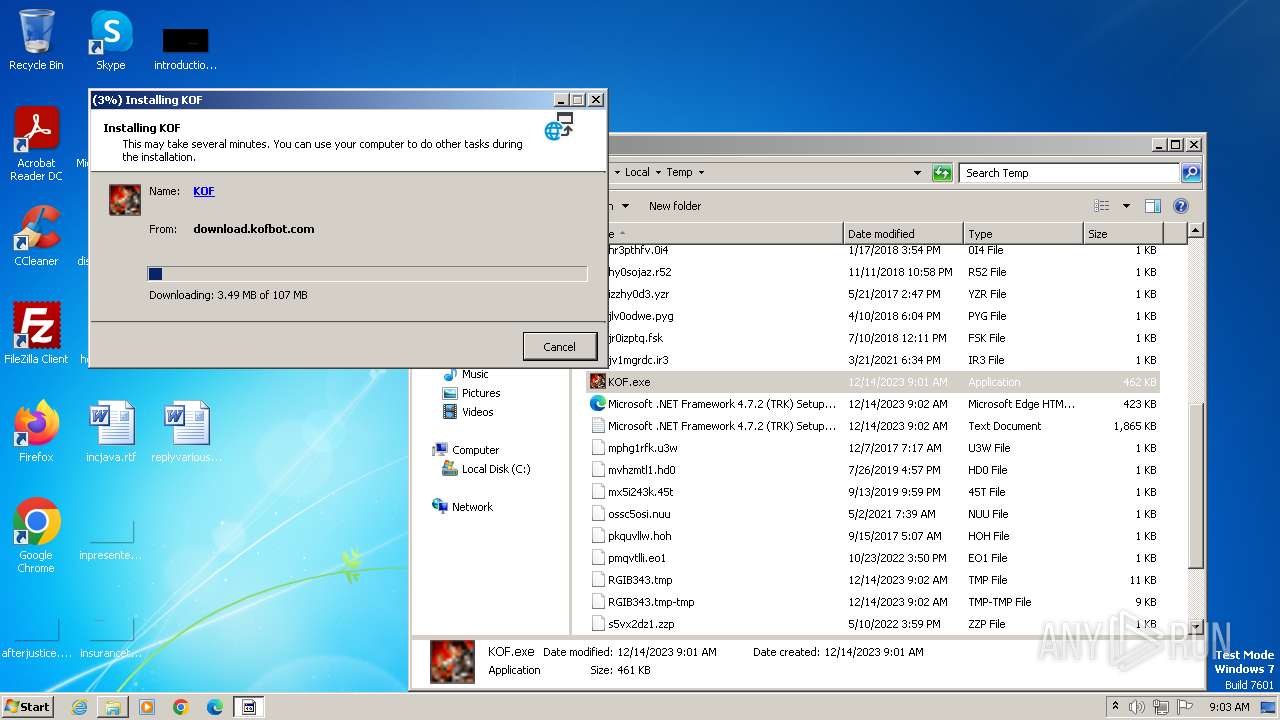
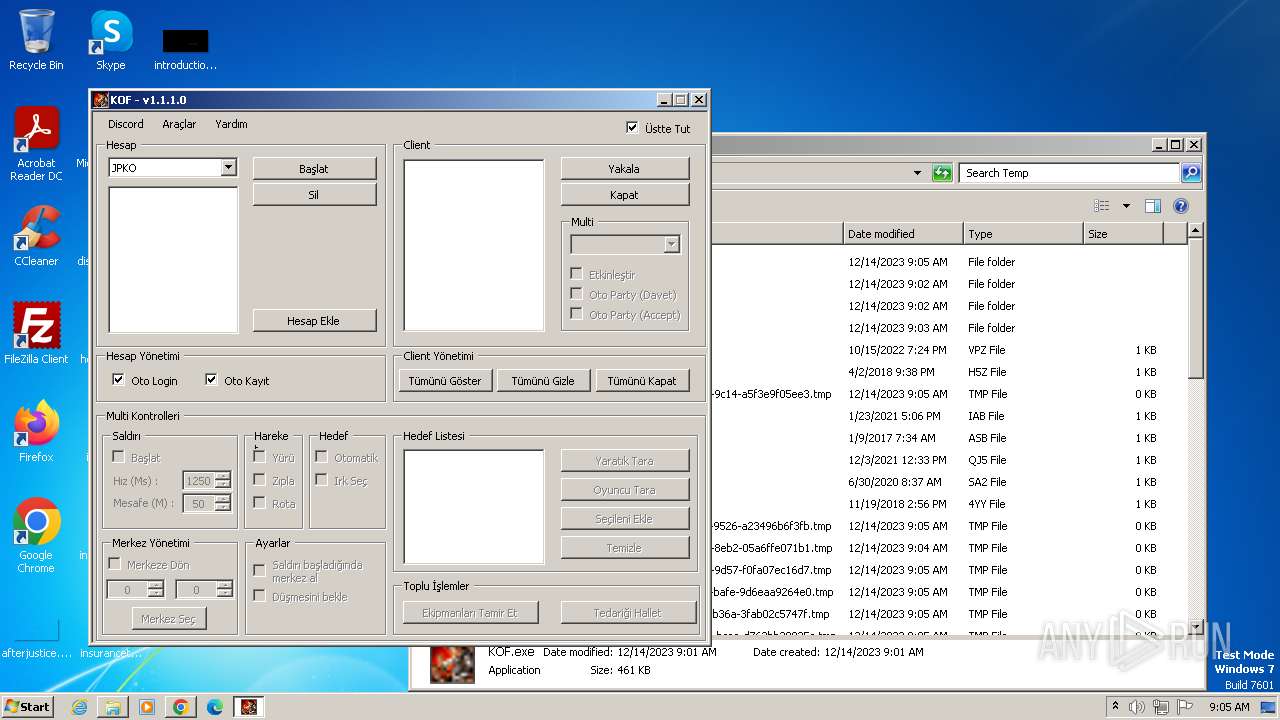
| File name: | KOF.exe |
| Full analysis: | https://app.any.run/tasks/63878f65-afdc-411c-bdd2-5c574f680cad |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2023, 09:01:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A9FAFC7B50F784F20DDCBAF70577BFD5 |
| SHA1: | 010D5747CA9E472C2EEFA28B690FC382383C39DD |
| SHA256: | 3E9A0CFFDF5B724528BFA9D9E12F5393869D706BB6670AC01D6C56D5EF1B9E08 |
| SSDEEP: | 12288:BSUQLpdw6GRg1NHNizch6cIcfbNXOxA6N:BSUsdw6GRQSzo3X4Am |
MALICIOUS
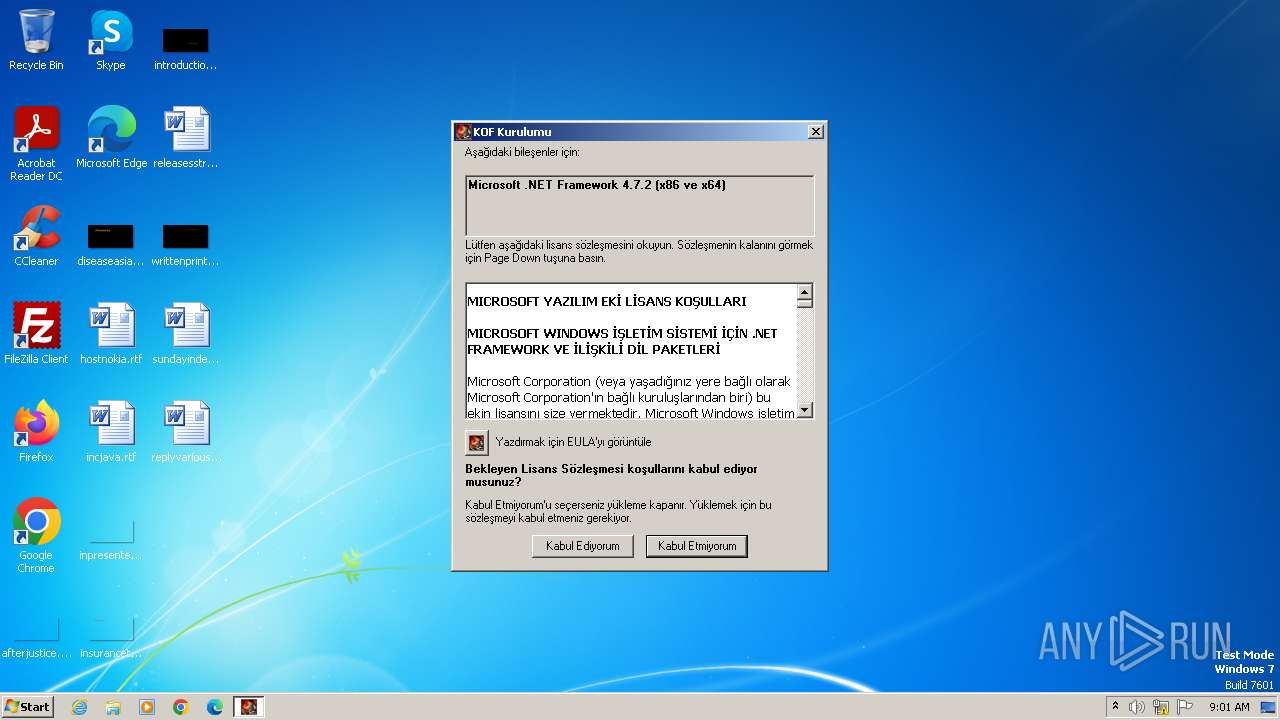
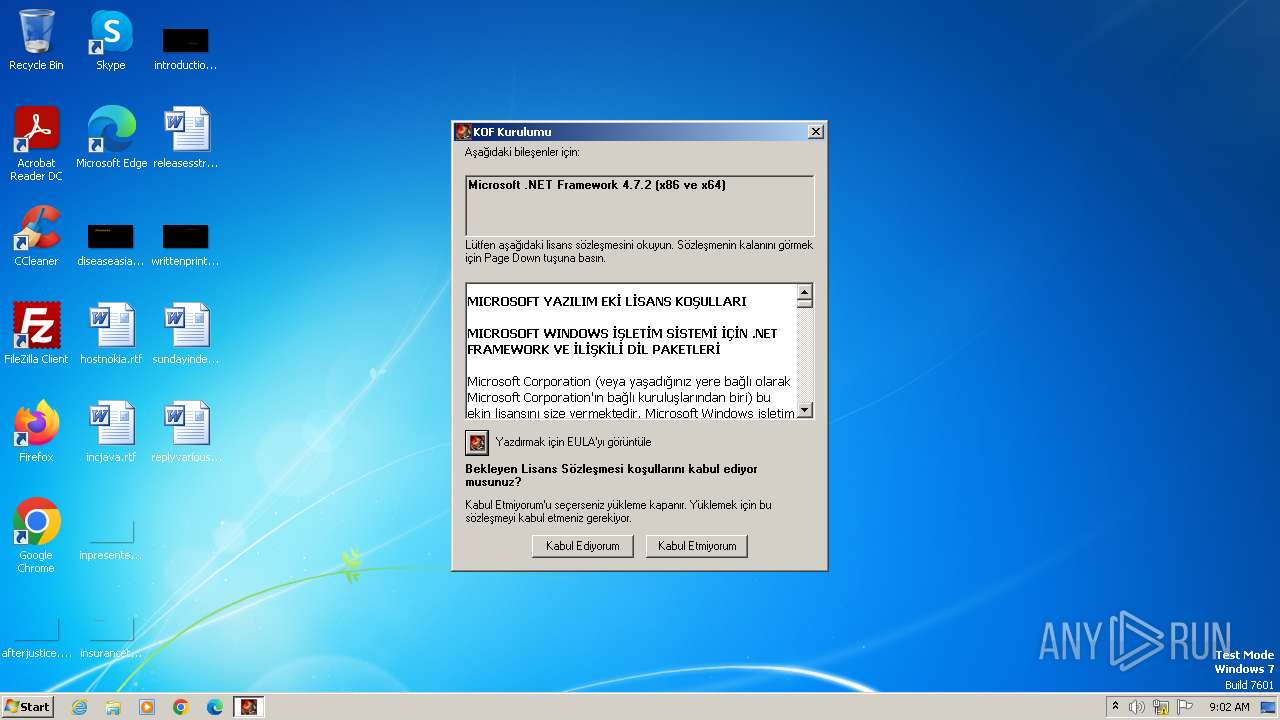
Drops the executable file immediately after the start
- KOF.exe (PID: 3048)
- NDP472-KB4054530-x86-x64-AllOS-TRK.exe (PID: 4088)
- dfsvc.exe (PID: 3260)
- msiexec.exe (PID: 3252)
Creates a writable file in the system directory
- msiexec.exe (PID: 3252)
- aspnet_regiis.exe (PID: 3736)
SUSPICIOUS
Reads the Internet Settings
- KOF.exe (PID: 3048)
- Setup.exe (PID: 3564)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 3020)
- KOF.exe (PID: 2804)
- KOF.exe (PID: 1808)
Reads security settings of Internet Explorer
- KOF.exe (PID: 3048)
- Setup.exe (PID: 3564)
- KOF.exe (PID: 3020)
Process drops legitimate windows executable
- KOF.exe (PID: 3048)
- NDP472-KB4054530-x86-x64-AllOS-TRK.exe (PID: 4088)
- msiexec.exe (PID: 3252)
- dfsvc.exe (PID: 3260)
- chrome.exe (PID: 544)
Reads settings of System Certificates
- KOF.exe (PID: 3048)
- Setup.exe (PID: 3564)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 3020)
Checks Windows Trust Settings
- KOF.exe (PID: 3048)
- Setup.exe (PID: 3564)
- msiexec.exe (PID: 3252)
- KOF.exe (PID: 3020)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3252)
Reads Internet Explorer settings
- dfsvc.exe (PID: 3260)
Application launched itself
- KOF.exe (PID: 2804)
- KOF.exe (PID: 1808)
INFO
Checks supported languages
- KOF.exe (PID: 3048)
- wmpnscfg.exe (PID: 1556)
- wmpnscfg.exe (PID: 3108)
- NDP472-KB4054530-x86-x64-AllOS-TRK.exe (PID: 4088)
- msiexec.exe (PID: 3252)
- Setup.exe (PID: 3564)
- msiexec.exe (PID: 3508)
- msiexec.exe (PID: 2912)
- aspnet_regiis.exe (PID: 3736)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 3020)
- KOF.exe (PID: 2804)
- KOF.exe (PID: 3232)
- KOF.exe (PID: 1808)
- KOF.exe (PID: 3008)
Manual execution by a user
- wmpnscfg.exe (PID: 1556)
- wmpnscfg.exe (PID: 3108)
- KOF.exe (PID: 3020)
- chrome.exe (PID: 544)
- rundll32.exe (PID: 3292)
Create files in a temporary directory
- KOF.exe (PID: 3048)
- Setup.exe (PID: 3564)
- NDP472-KB4054530-x86-x64-AllOS-TRK.exe (PID: 4088)
- msiexec.exe (PID: 3252)
- mofcomp.exe (PID: 3884)
- aspnet_regiis.exe (PID: 3736)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 3020)
Reads the computer name
- KOF.exe (PID: 3048)
- wmpnscfg.exe (PID: 1556)
- wmpnscfg.exe (PID: 3108)
- NDP472-KB4054530-x86-x64-AllOS-TRK.exe (PID: 4088)
- Setup.exe (PID: 3564)
- msiexec.exe (PID: 3252)
- msiexec.exe (PID: 3508)
- msiexec.exe (PID: 2912)
- aspnet_regiis.exe (PID: 3736)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 3020)
- KOF.exe (PID: 2804)
- KOF.exe (PID: 3232)
- KOF.exe (PID: 1808)
- KOF.exe (PID: 3008)
Reads Microsoft Office registry keys
- KOF.exe (PID: 3048)
Reads the machine GUID from the registry
- KOF.exe (PID: 3048)
- NDP472-KB4054530-x86-x64-AllOS-TRK.exe (PID: 4088)
- Setup.exe (PID: 3564)
- msiexec.exe (PID: 3252)
- msiexec.exe (PID: 3508)
- msiexec.exe (PID: 2912)
- aspnet_regiis.exe (PID: 3736)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 2804)
- KOF.exe (PID: 3232)
- KOF.exe (PID: 1808)
- KOF.exe (PID: 3008)
- KOF.exe (PID: 3020)
Checks proxy server information
- KOF.exe (PID: 3048)
- dfsvc.exe (PID: 3260)
- KOF.exe (PID: 3020)
Creates files or folders in the user directory
- KOF.exe (PID: 3048)
- Setup.exe (PID: 3564)
- dfsvc.exe (PID: 3260)
Reads Environment values
- Setup.exe (PID: 3564)
- dfsvc.exe (PID: 3260)
Reads CPU info
- Setup.exe (PID: 3564)
Application launched itself
- msiexec.exe (PID: 3252)
- chrome.exe (PID: 544)
Process checks are UAC notifies on
- dfsvc.exe (PID: 3260)
Creates files in the program directory
- KOF.exe (PID: 3232)
Drops the executable file immediately after the start
- chrome.exe (PID: 544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:04:06 22:31:00+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 383488 |
| InitializedDataSize: | 88064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x37d3e |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 16.0.31206.173 |
| ProductVersionNumber: | 16.0.31206.173 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | Setup |
| FileVersion: | 16.0.31206.173 built by: D16.10 |
| InternalName: | setup.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | setup.exe |
| ProductName: | - |
| ProductVersion: | 16.0.31206.173 |
Total processes
114
Monitored processes
53
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=3312 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2112 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3728 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1376 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=3344 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2248 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4708 --field-trial-handle=1160,i,5745007391235583629,10993894489268881963,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\kof...tion_0000000000000000_0001.0001_9f30f701036d4b1a\KOF.exe" | C:\Users\admin\AppData\Local\Apps\2.0\OQVLXTZK.4P5\AK6KX289.K1P\kof...tion_0000000000000000_0001.0001_9f30f701036d4b1a\KOF.exe | — | dfsvc.exe | |||||||||||
User: admin Company: Shorty Integrity Level: MEDIUM Description: KOF Exit code: 0 Version: 1.1.1.0 Modules
| |||||||||||||||
Total events
32 742
Read events
31 989
Write events
516
Delete events
237
Modification events
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (2132) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
355
Suspicious files
279
Text files
352
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3046.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{392E8C52-0BC7-444D-9345-01A1CDB17E4C}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2132 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:B080A782713A035F52B117872D5D4E12 | SHA256:C5ADC68409565B0E56A0BD47DB567DC6793768088CE93D3DB427019D750576D6 | |||
| 2132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VSD4A3.tmp\~$eula.rtf | binary | |
MD5:6DFB52C9085422C114E51A39F6E31E7E | SHA256:3B2C09FBE90F5C51CDC477E901E083DB4B462D7DE0AE86C6730C242DA96F2C3B | |||
| 3048 | KOF.exe | C:\Users\admin\AppData\Local\Temp\VSD4A3.tmp\eula.rtf | text | |
MD5:46EC7CF1550757570AF451B845CAEAE3 | SHA256:4956B28C1553ABC49A76B4FA338029393DCA940922236EA52D612D8DB176B3E2 | |||
| 2132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{B16F9750-086F-4D7D-8EDA-929A2E585840}.tmp | binary | |
MD5:CE2054C5546B7C8BF6AB1C3C11046CE5 | SHA256:C2ACABB9A2C0BE784155DCB2C2ACBE0FE58E6AF3561DD36FF0501BE529F40FFD | |||
| 3048 | KOF.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CD9E5EC53462D991D833DF870DD7F0D1 | SHA256:CFE2E85838DE4EEA895C039AE862074F388B714F45AB0651A7B9A019BA54A41A | |||
| 3048 | KOF.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3048 | KOF.exe | C:\Users\admin\AppData\Local\Temp\VSD4A3.tmp\KOF.exe | executable | |
MD5:A9FAFC7B50F784F20DDCBAF70577BFD5 | SHA256:3E9A0CFFDF5B724528BFA9D9E12F5393869D706BB6670AC01D6C56D5EF1B9E08 | |||
| 2132 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{E91A4D8C-717C-4DB6-8D25-864D1441F5F1}.tmp | binary | |
MD5:CB5A93B080BC2E580EA7C48296498095 | SHA256:88D8340F5688A48B6DE7EECE9ACCB7CD4FF41313379E344DF2CF674A4F17CA86 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
134
DNS requests
231
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3048 | KOF.exe | GET | 200 | 2.18.97.123:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | binary | 1.05 Kb | unknown |
3048 | KOF.exe | GET | 302 | 23.32.186.57:80 | http://go.microsoft.com/fwlink/?LinkId=863258&clcid=0x41f | unknown | — | — | unknown |
3564 | Setup.exe | GET | 200 | 88.221.110.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | binary | 824 b | unknown |
3048 | KOF.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3564 | Setup.exe | GET | 200 | 88.221.110.122:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | binary | 767 b | unknown |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
3564 | Setup.exe | GET | 200 | 88.221.110.122:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | binary | 555 b | unknown |
3564 | Setup.exe | GET | 200 | 88.221.110.122:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | binary | 519 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d3b771b78e4ef5fc | unknown | compressed | 65.2 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 5.54 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3048 | KOF.exe | 23.32.186.57:80 | go.microsoft.com | AKAMAI-AS | BR | unknown |
3048 | KOF.exe | 68.232.34.200:443 | download.visualstudio.microsoft.com | EDGECAST | US | whitelisted |
3048 | KOF.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3048 | KOF.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3048 | KOF.exe | 2.18.97.123:80 | www.microsoft.com | Akamai International B.V. | FR | unknown |
3048 | KOF.exe | 88.221.110.122:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
download.visualstudio.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
download.kofbot.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|