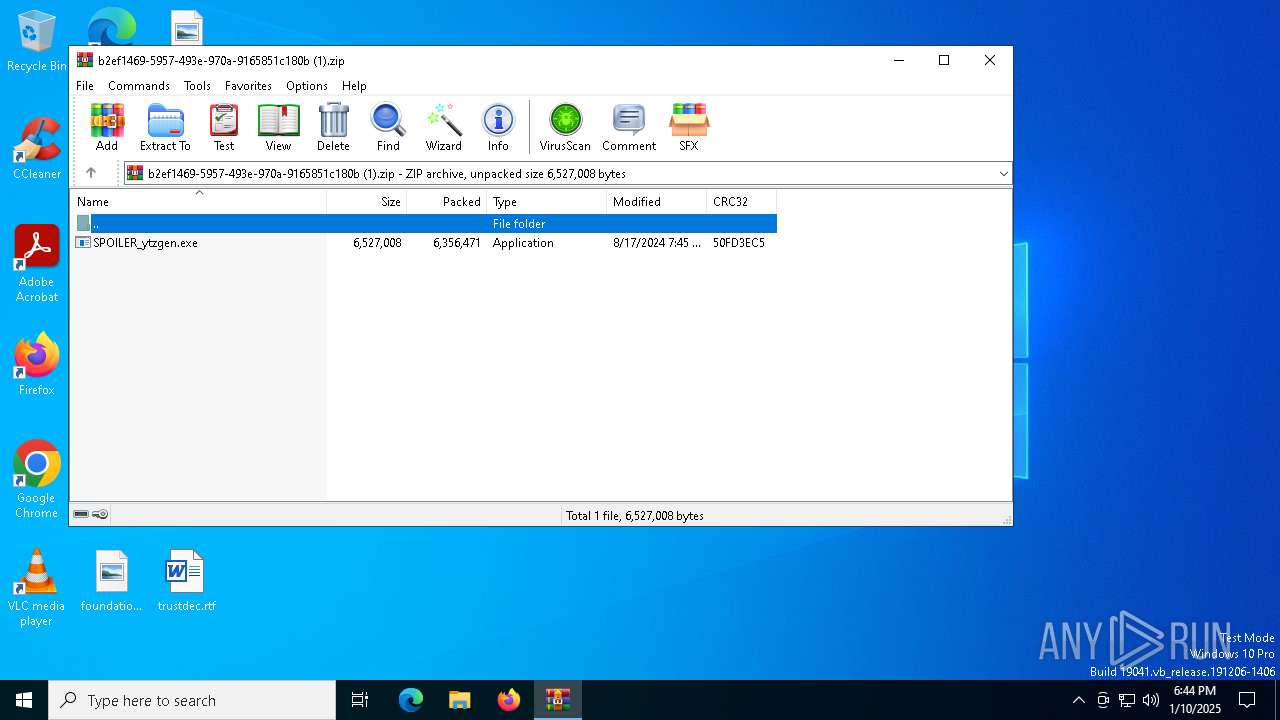
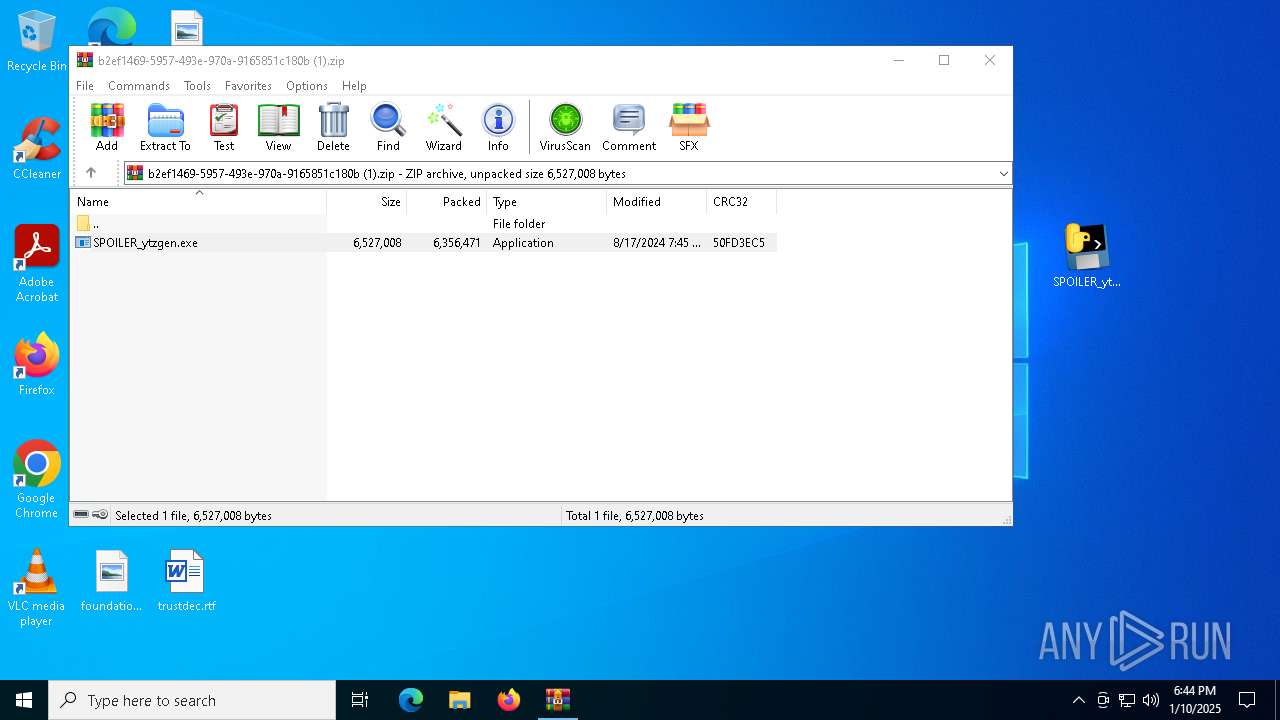
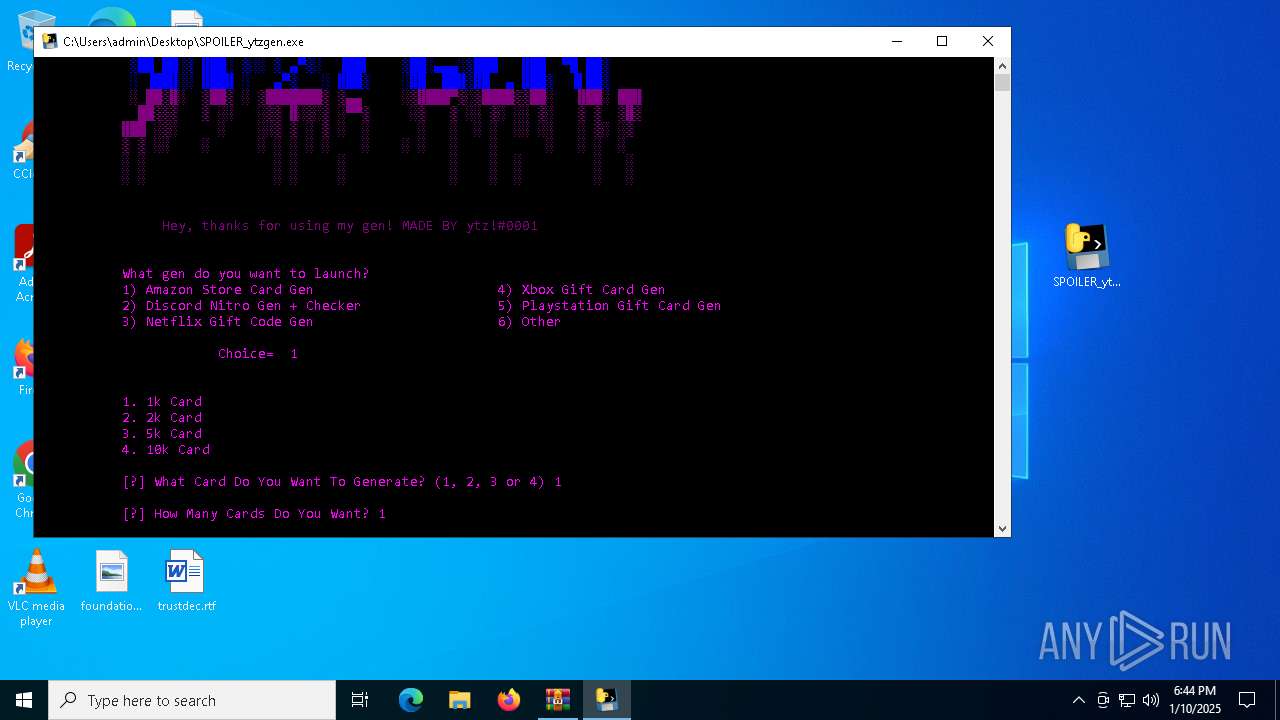
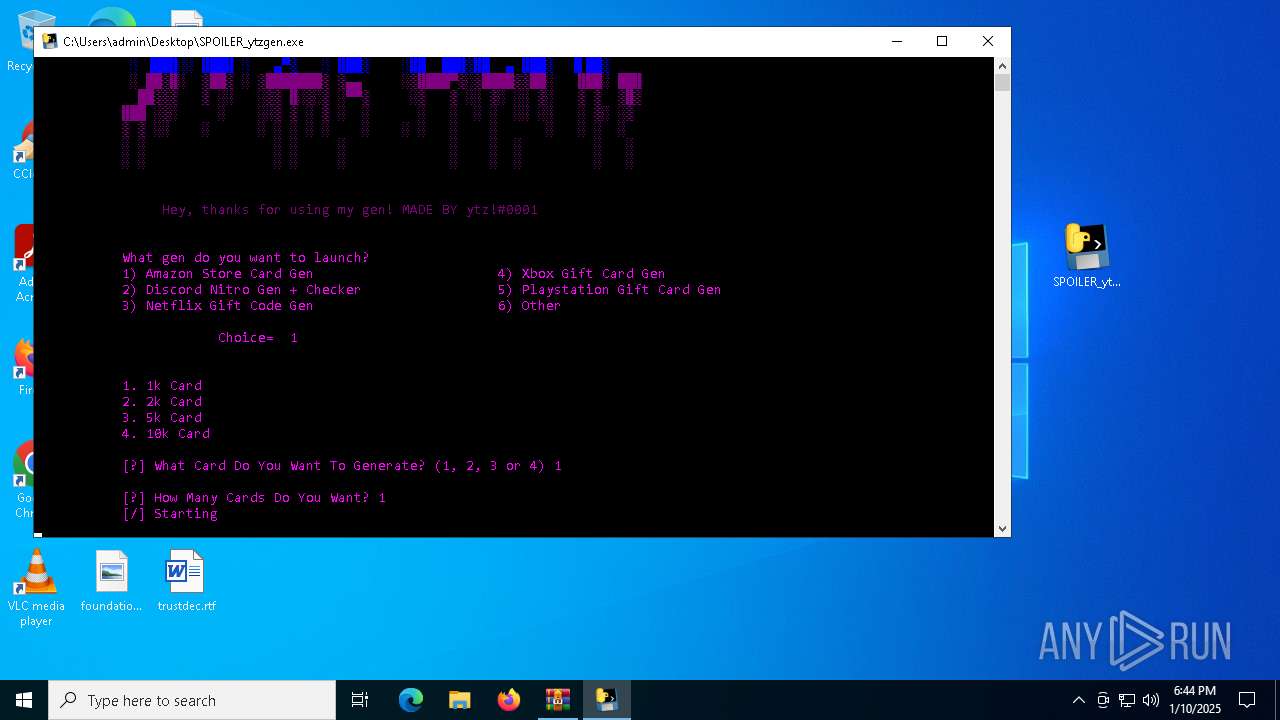
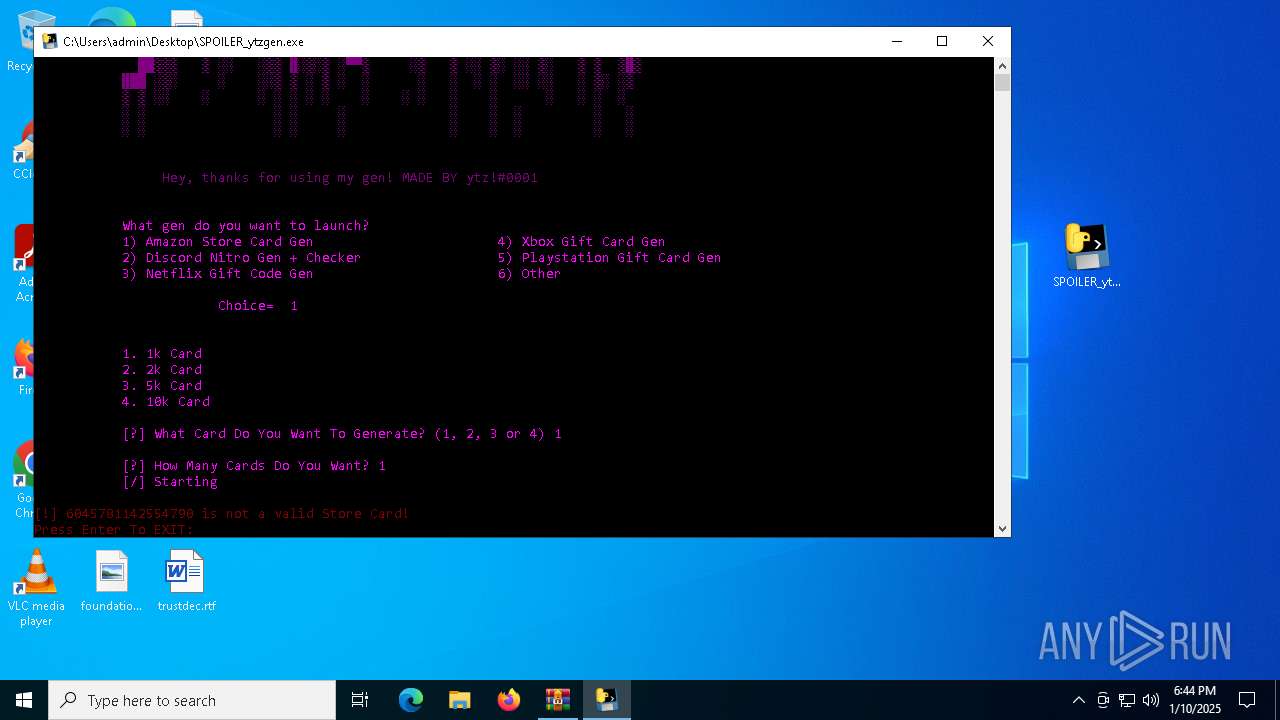
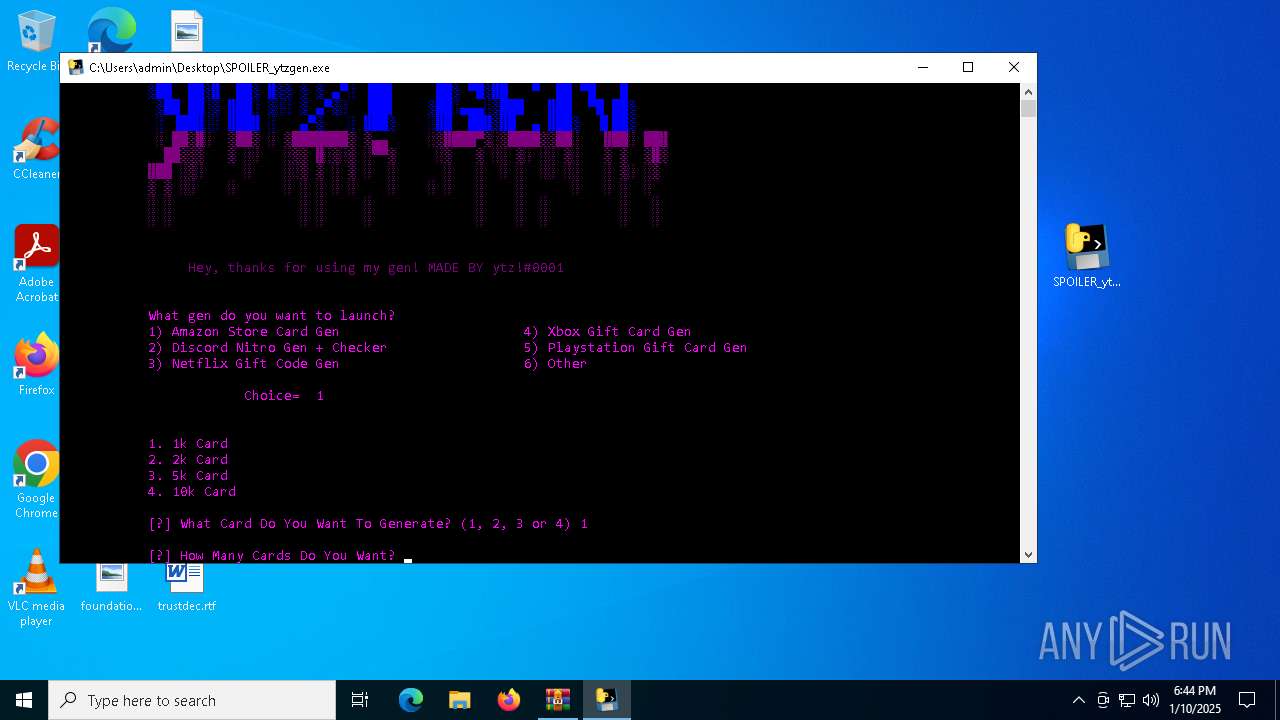
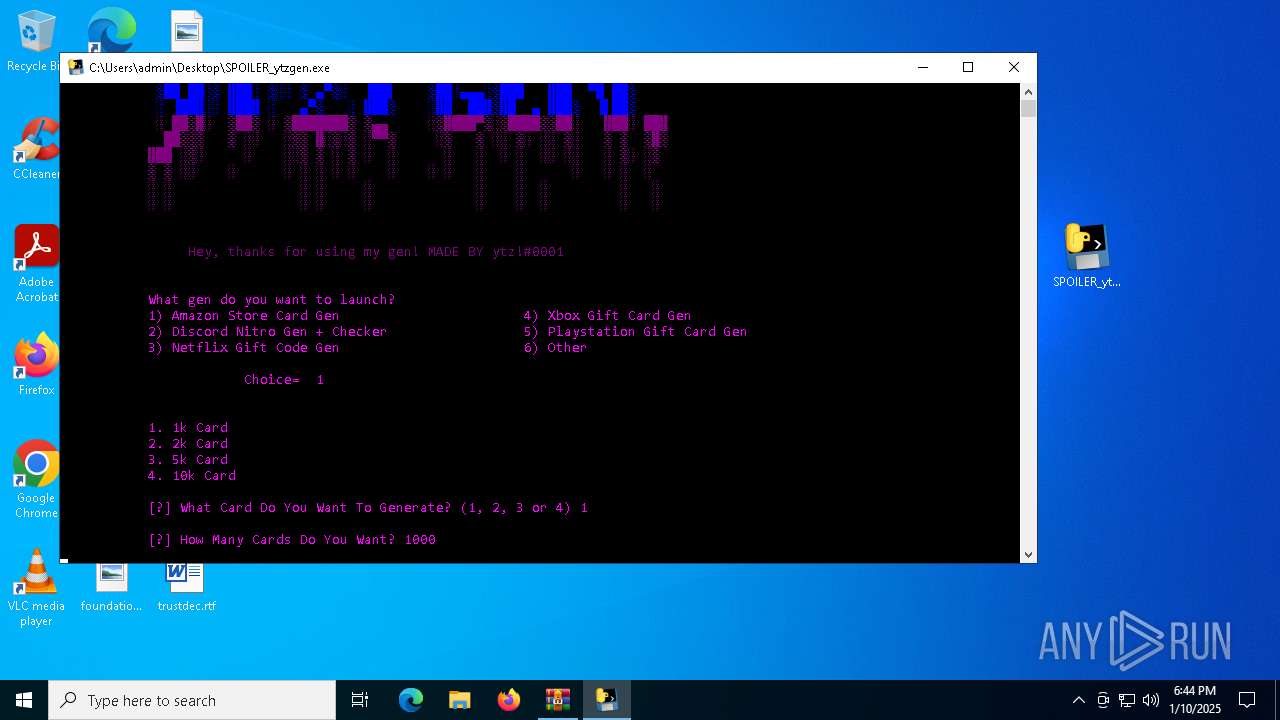
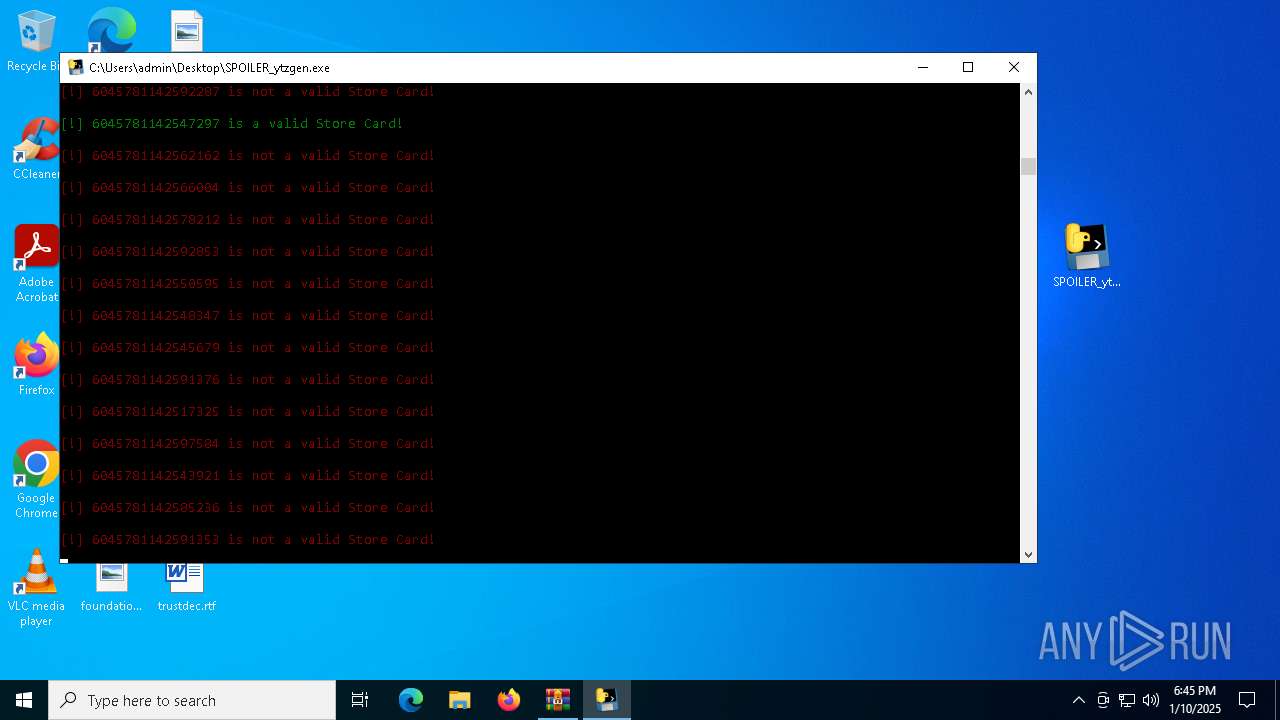
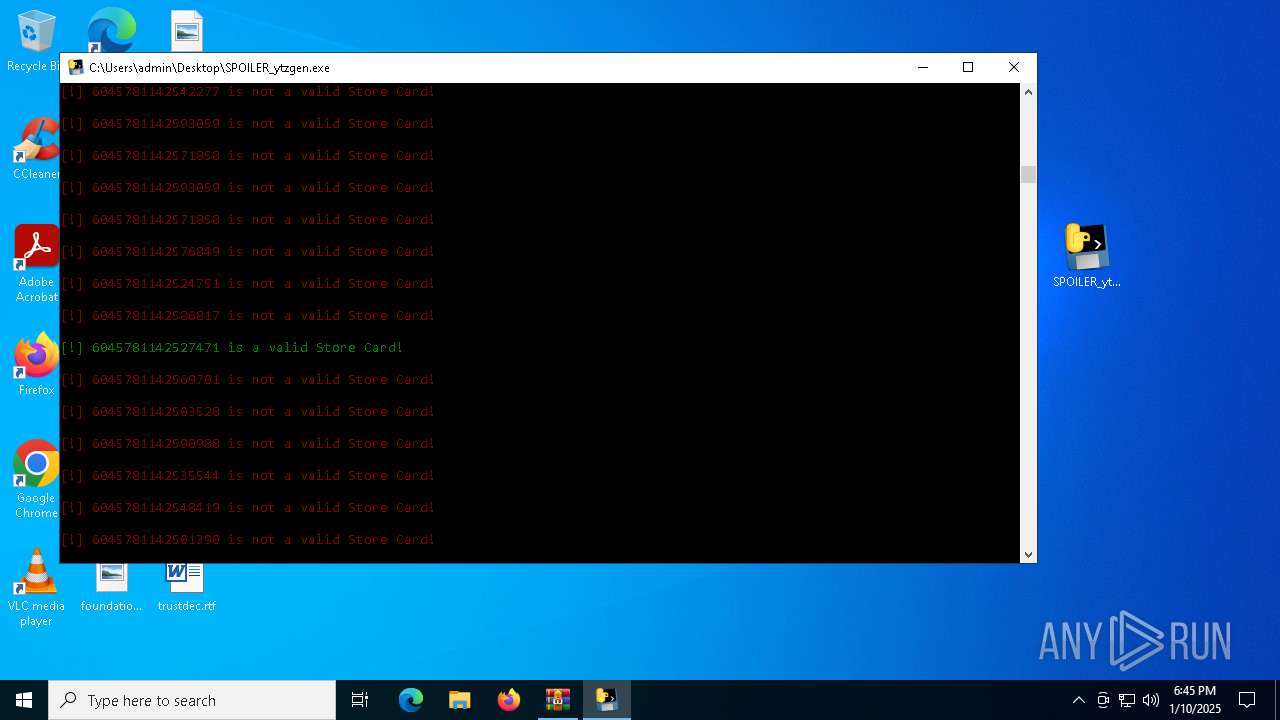
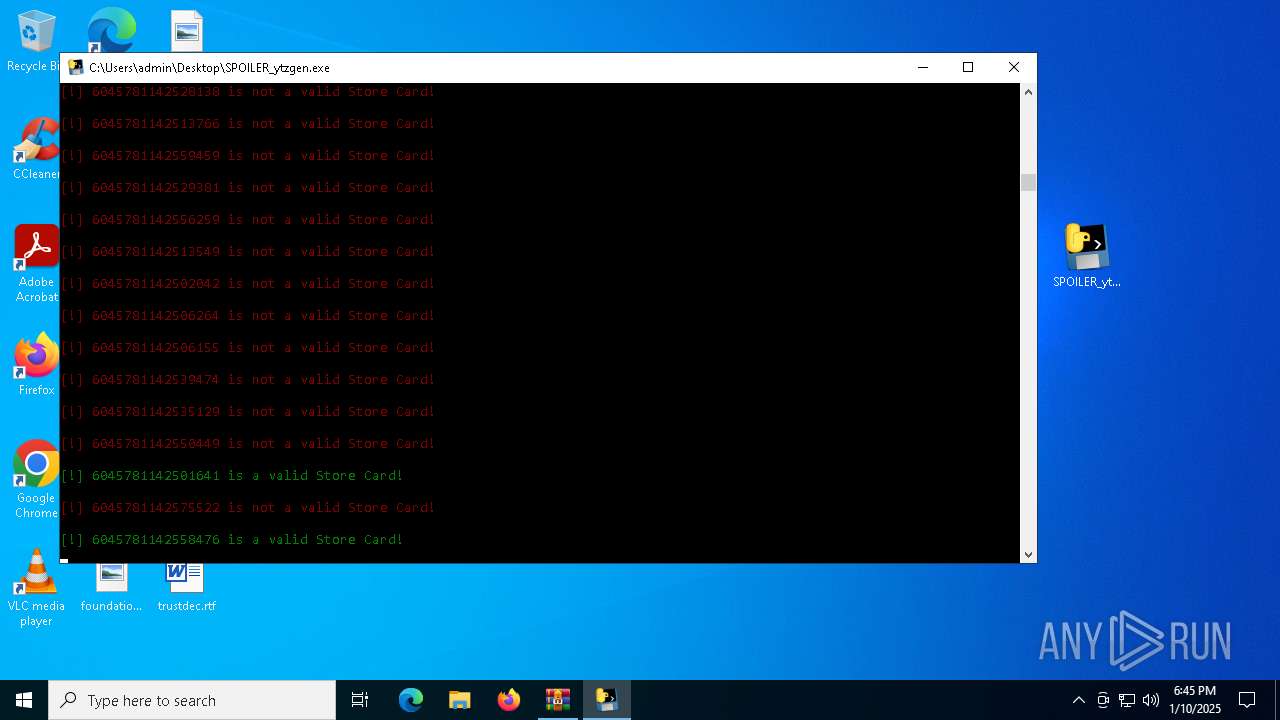
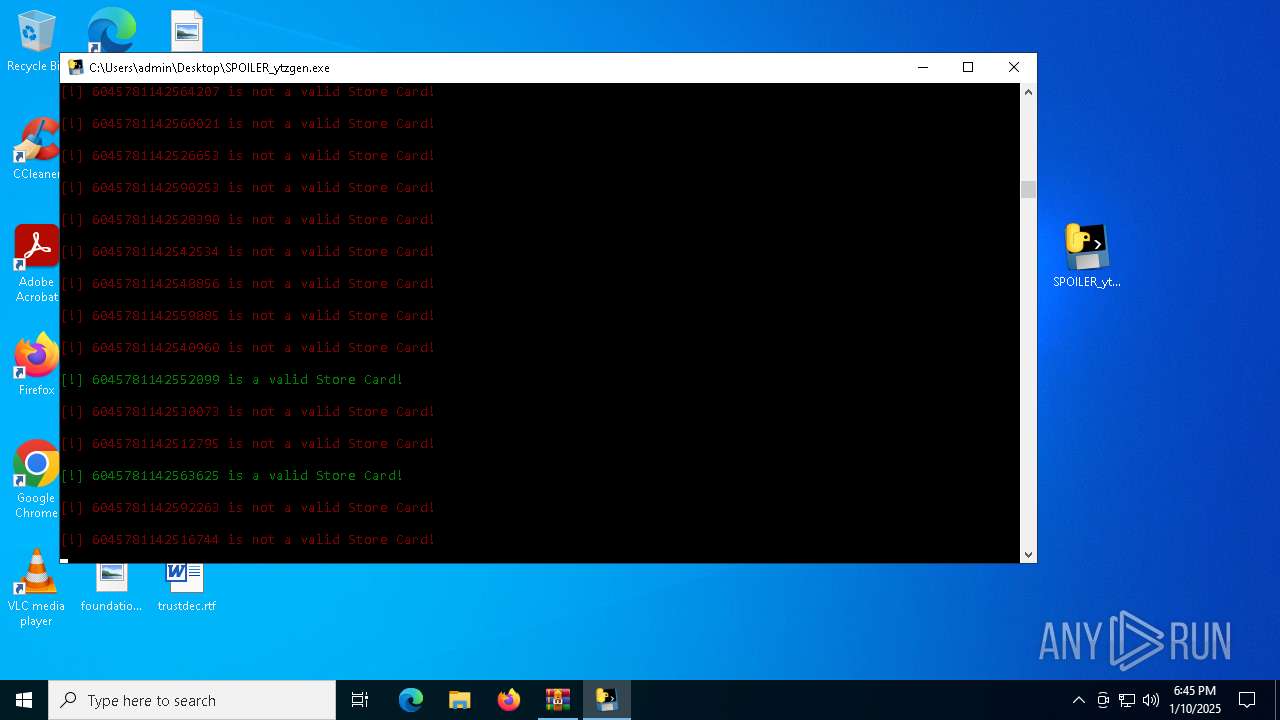
| File name: | b2ef1469-5957-493e-970a-9165851c180b (1).zip |
| Full analysis: | https://app.any.run/tasks/444c4f6c-1917-4fdd-8cdd-707e5cf5196d |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2025, 18:44:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3817E2A273413E59E033F408AA5B0F0F |
| SHA1: | A4A08F36ACF4E778899692EB3EFDAC5230D3F303 |
| SHA256: | 3E7CEFC43E542908A112C5528114677FEE4E456F62EDFF488B676505F1F43B0D |
| SSDEEP: | 98304:M+fBJZu8nZleFMVnb2MdYemTX0U38mRlJplE9WGexpeAtIOGtJJxs61YpZtKn7bF:tJnUe5FII4cb8nvUS6 |
MALICIOUS
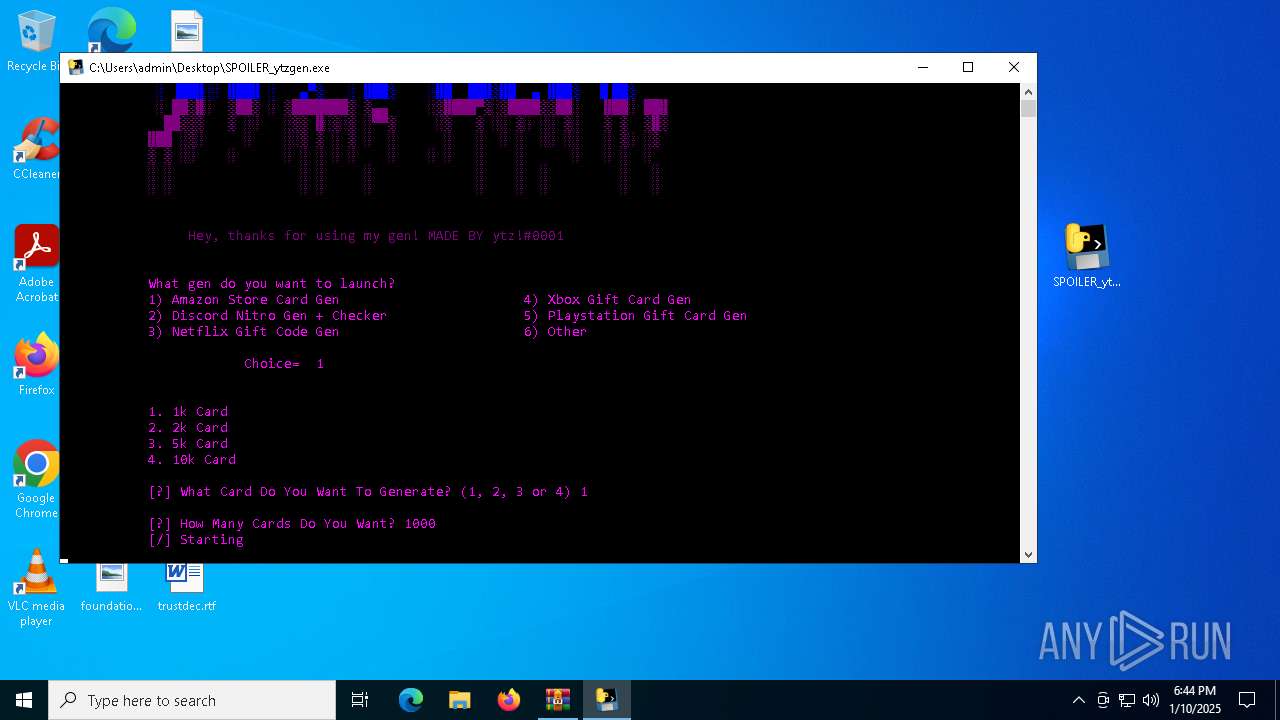
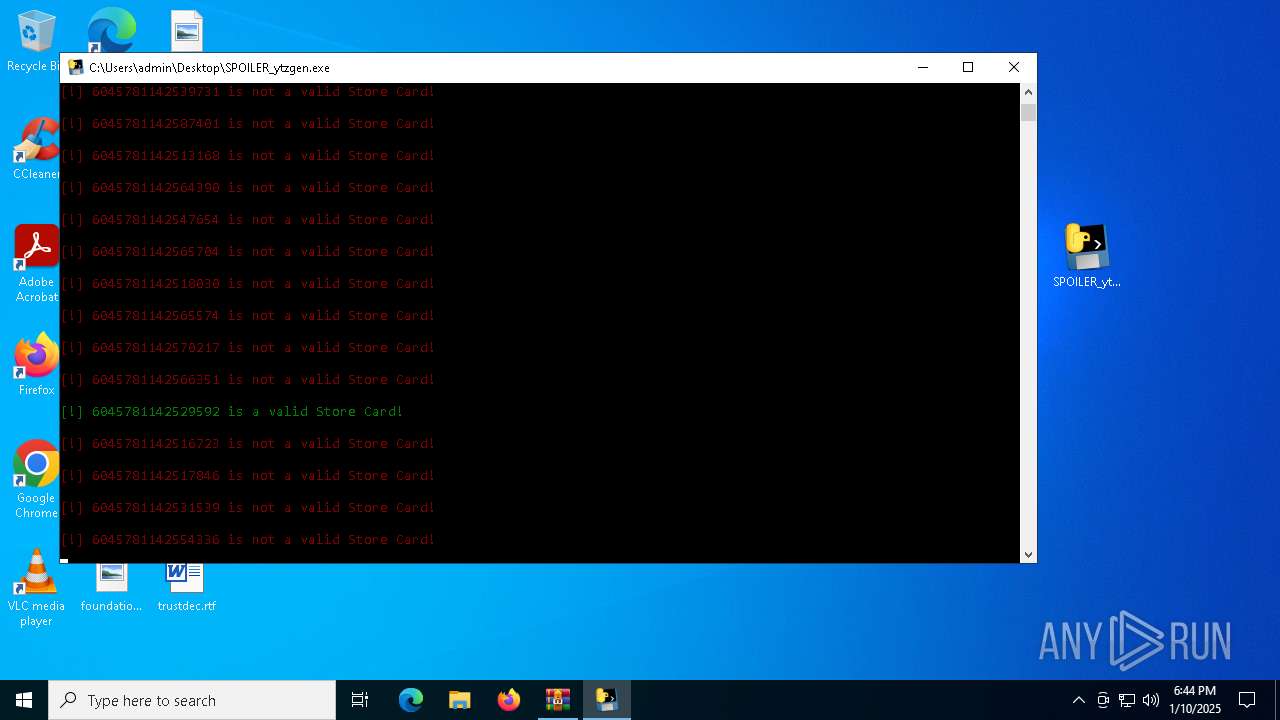
Generic archive extractor
- WinRAR.exe (PID: 6480)
SUSPICIOUS
Executable content was dropped or overwritten
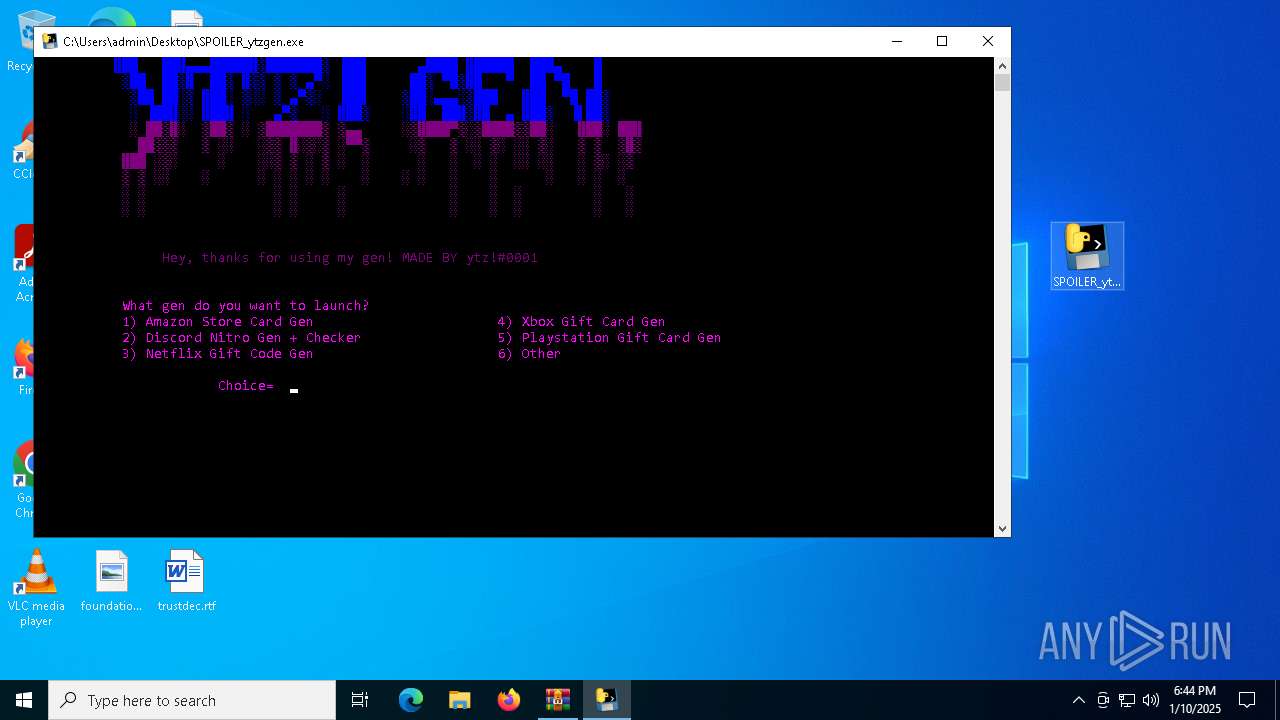
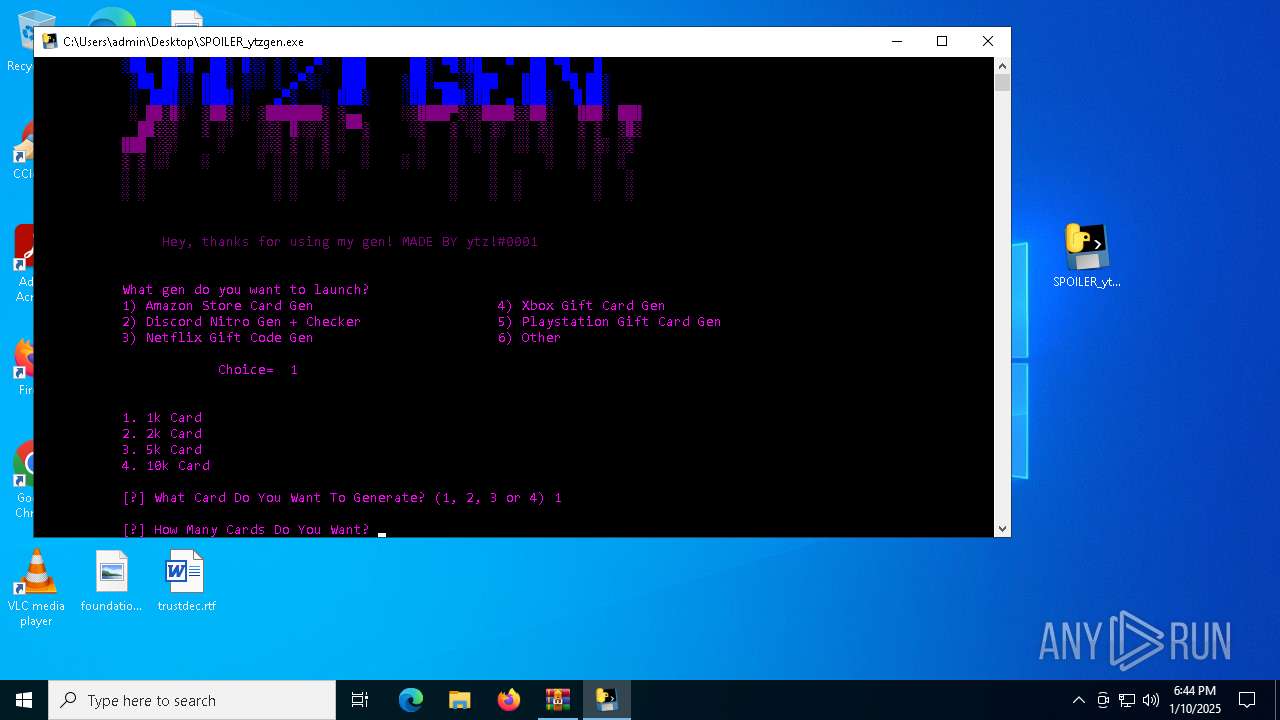
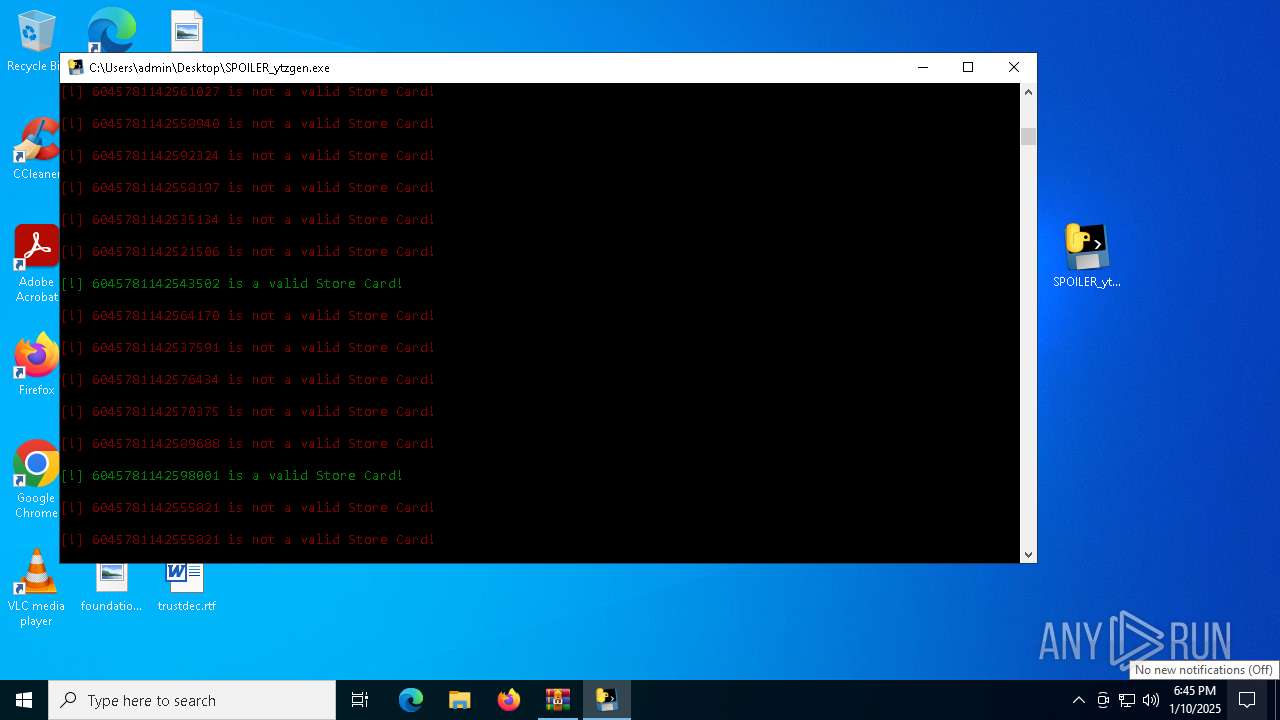
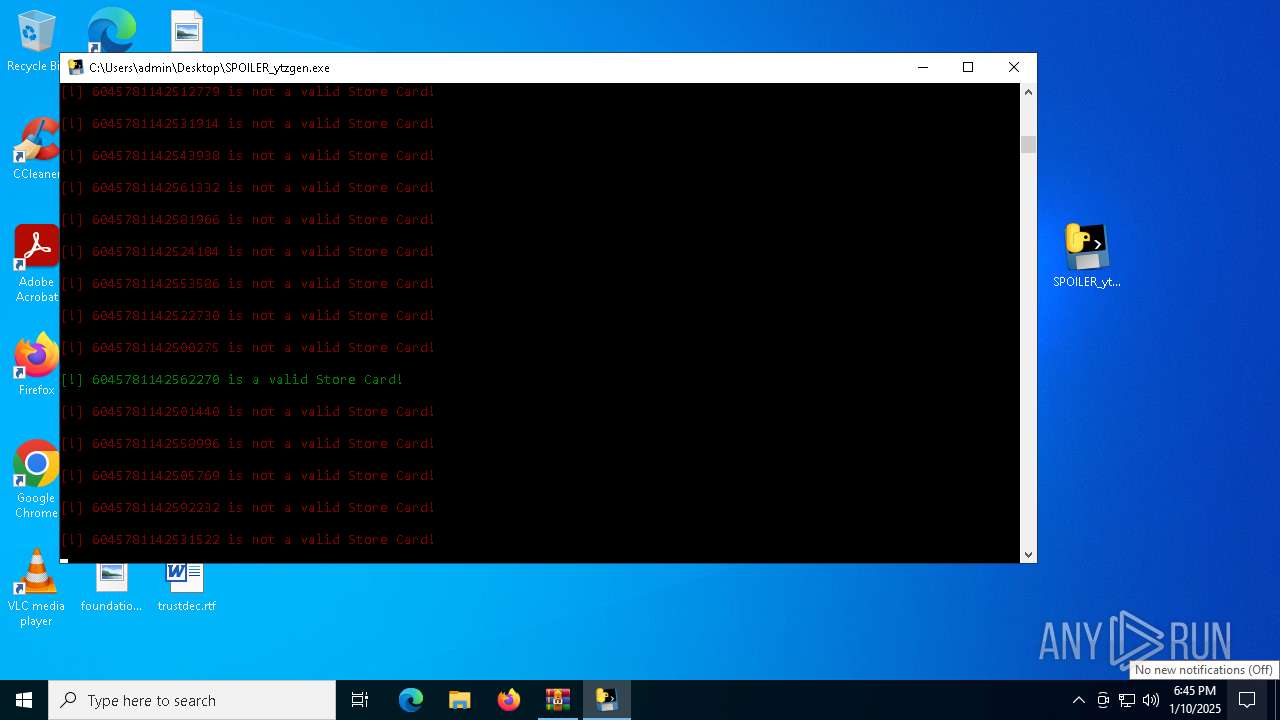
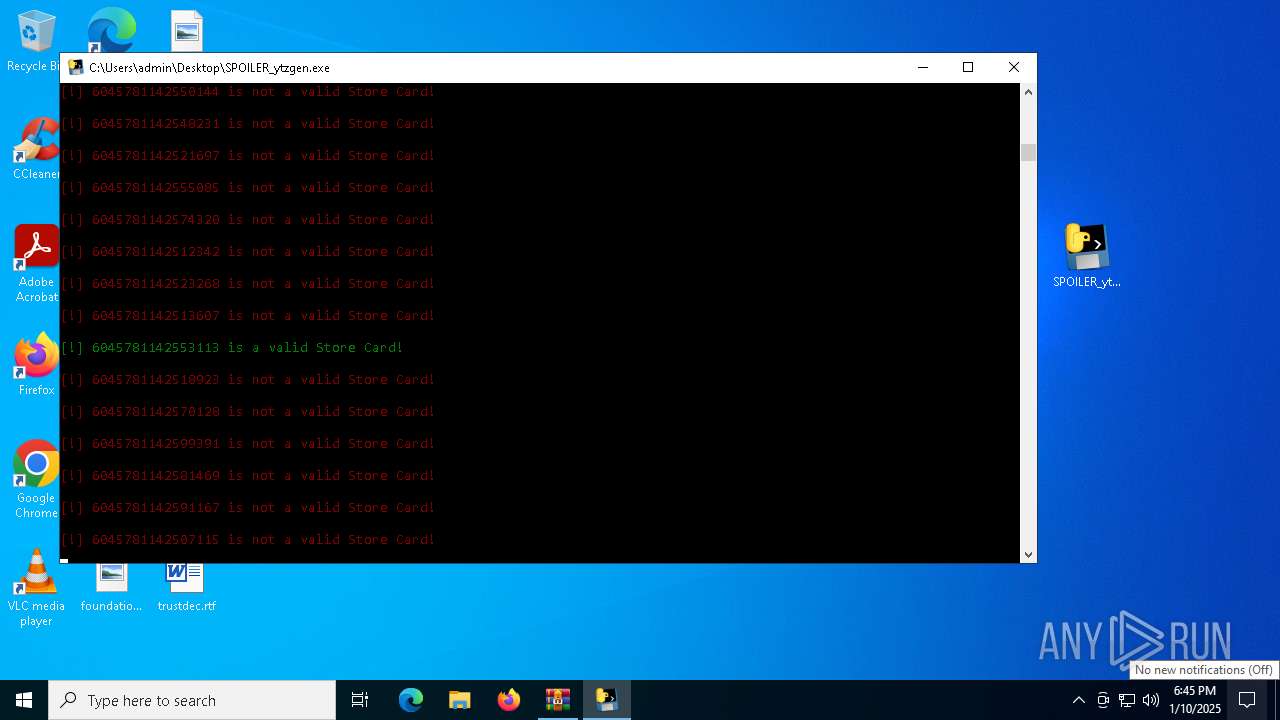
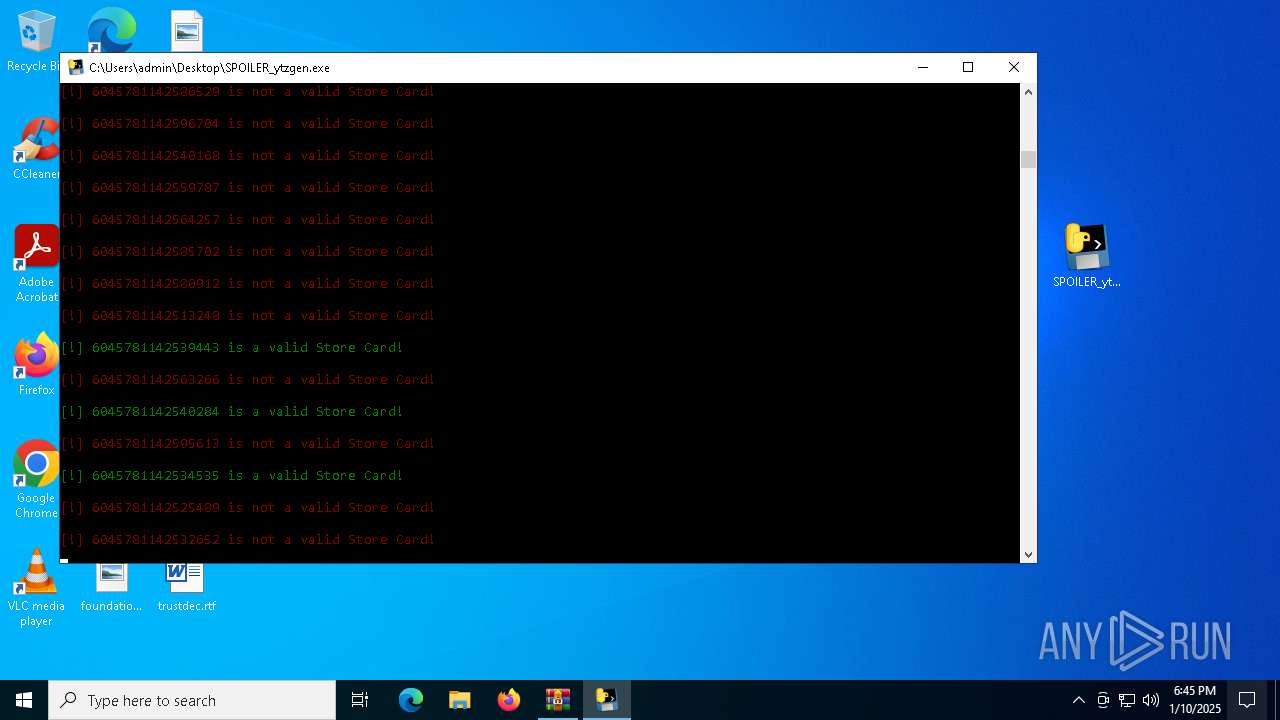
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
The process drops C-runtime libraries
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
Process drops legitimate windows executable
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
Process drops python dynamic module
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
Application launched itself
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
Starts CMD.EXE for commands execution
- SPOILER_ytzgen.exe (PID: 5920)
- SPOILER_ytzgen.exe (PID: 5460)
Loads Python modules
- SPOILER_ytzgen.exe (PID: 5920)
- SPOILER_ytzgen.exe (PID: 5460)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6480)
Manual execution by a user
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
The sample compiled with english language support
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
Create files in a temporary directory
- SPOILER_ytzgen.exe (PID: 6152)
- SPOILER_ytzgen.exe (PID: 4672)
PyInstaller has been detected (YARA)
- SPOILER_ytzgen.exe (PID: 6152)
Checks supported languages
- SPOILER_ytzgen.exe (PID: 5460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:17 16:45:02 |
| ZipCRC: | 0x50fd3ec5 |
| ZipCompressedSize: | 6356471 |
| ZipUncompressedSize: | 6527008 |
| ZipFileName: | SPOILER_ytzgen.exe |
Total processes
133
Monitored processes
9
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2828 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SPOILER_ytzgen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SPOILER_ytzgen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | C:\WINDOWS\system32\cmd.exe /c | C:\Windows\System32\cmd.exe | — | SPOILER_ytzgen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4672 | "C:\Users\admin\Desktop\SPOILER_ytzgen.exe" | C:\Users\admin\Desktop\SPOILER_ytzgen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5460 | "C:\Users\admin\Desktop\SPOILER_ytzgen.exe" | C:\Users\admin\Desktop\SPOILER_ytzgen.exe | — | SPOILER_ytzgen.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5920 | "C:\Users\admin\Desktop\SPOILER_ytzgen.exe" | C:\Users\admin\Desktop\SPOILER_ytzgen.exe | — | SPOILER_ytzgen.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6152 | "C:\Users\admin\Desktop\SPOILER_ytzgen.exe" | C:\Users\admin\Desktop\SPOILER_ytzgen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6220 | C:\WINDOWS\system32\cmd.exe /c | C:\Windows\System32\cmd.exe | — | SPOILER_ytzgen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6480 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\b2ef1469-5957-493e-970a-9165851c180b (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 814
Read events
1 806
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\b2ef1469-5957-493e-970a-9165851c180b (1).zip | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6480) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
31
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\_queue.pyd | executable | |
MD5:C8A1F1DC297B6DD10C5F7BC64F907D38 | SHA256:827A07B27121200ED9FB2E9EFD13CCBF57CA7D32D9D9D1619F1C303FB4D607B7 | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\_lzma.pyd | executable | |
MD5:AFFF5DB126034438405DEBADB4B38F08 | SHA256:75D450E973CD1CCBD0F9A35BA0D7E6D644125EB311CC432BB424A299D9A52EE0 | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\_hashlib.pyd | executable | |
MD5:0D75220CF4691AF4F97EBCBD9A481C62 | SHA256:9DA79ABFED52C7432A25A513F14134F3782C73EC7142E2D90223610EAEF54303 | |||
| 6480 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6480.46844\SPOILER_ytzgen.exe | executable | |
MD5:CE6019D976A036B4D10664FCA449CF7F | SHA256:B43D0038293BE4D4EFD337AB9F925D0B6ED3FAE09DEA1A7AFE57D5FC4F5881D3 | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\VCRUNTIME140.dll | executable | |
MD5:F34EB034AA4A9735218686590CBA2E8B | SHA256:9D2B40F0395CC5D1B4D5EA17B84970C29971D448C37104676DB577586D4AD1B1 | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\_ctypes.pyd | executable | |
MD5:3FC444A146F7D667169DCB4F48760F49 | SHA256:B545DB2339AE74C523363B38835E8324799720F744C64E7142DDD48E4B619B68 | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\_decimal.pyd | executable | |
MD5:8A2530A8D7E3B443D2A9409923EB1CBA | SHA256:4F1ECC777C30DF39CD70600CD0C9DC411ADB622AF86287B612F78BE2A23B352C | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\_socket.pyd | executable | |
MD5:F59DDB8B1EEAC111D6A003F60E45B389 | SHA256:9558DDA6A3F6AD0C3091D643E2D3BF5BF20535904F691D2BDB2CE78EDF46C2DA | |||
| 4672 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI46722\VCRUNTIME140.dll | executable | |
MD5:F34EB034AA4A9735218686590CBA2E8B | SHA256:9D2B40F0395CC5D1B4D5EA17B84970C29971D448C37104676DB577586D4AD1B1 | |||
| 6152 | SPOILER_ytzgen.exe | C:\Users\admin\AppData\Local\Temp\_MEI61522\certifi\cacert.pem | text | |
MD5:B18E918767D99291F8771414B76A8E65 | SHA256:A59FDE883A0EF9D74AB9DAD009689E00173D28595B57416C98B2EE83280C6E4C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6352 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6244 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6068 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |