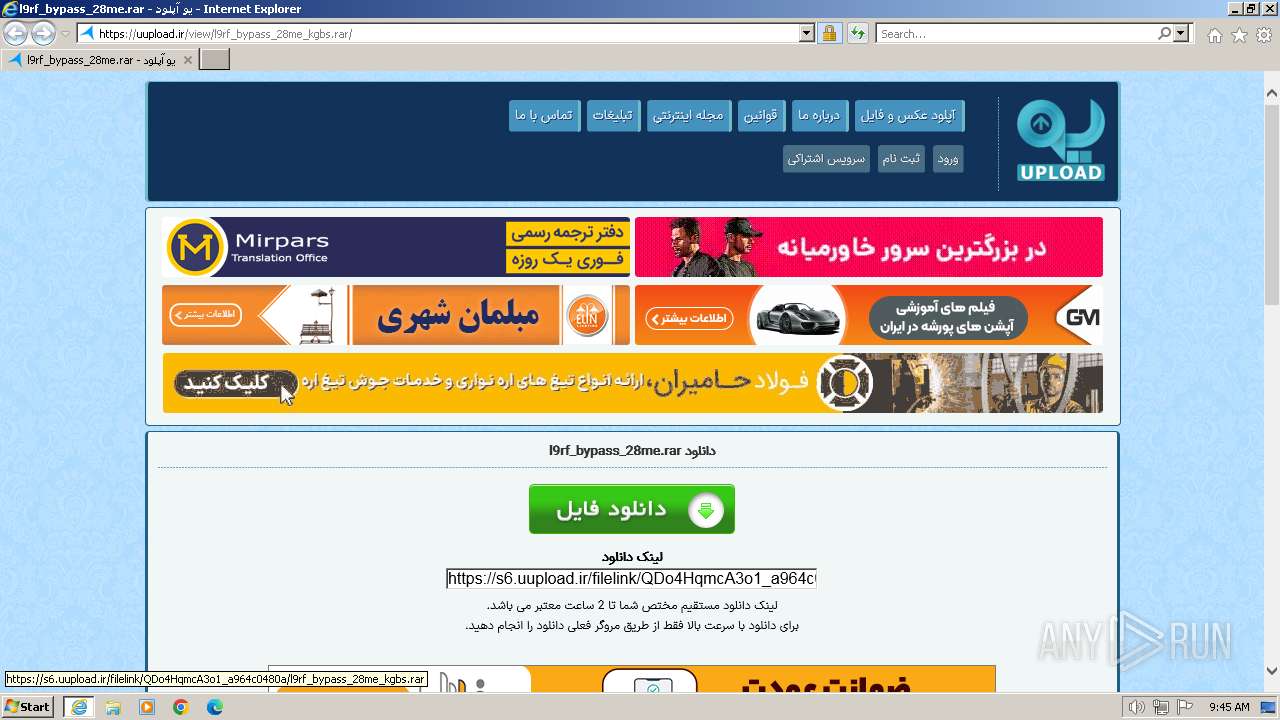
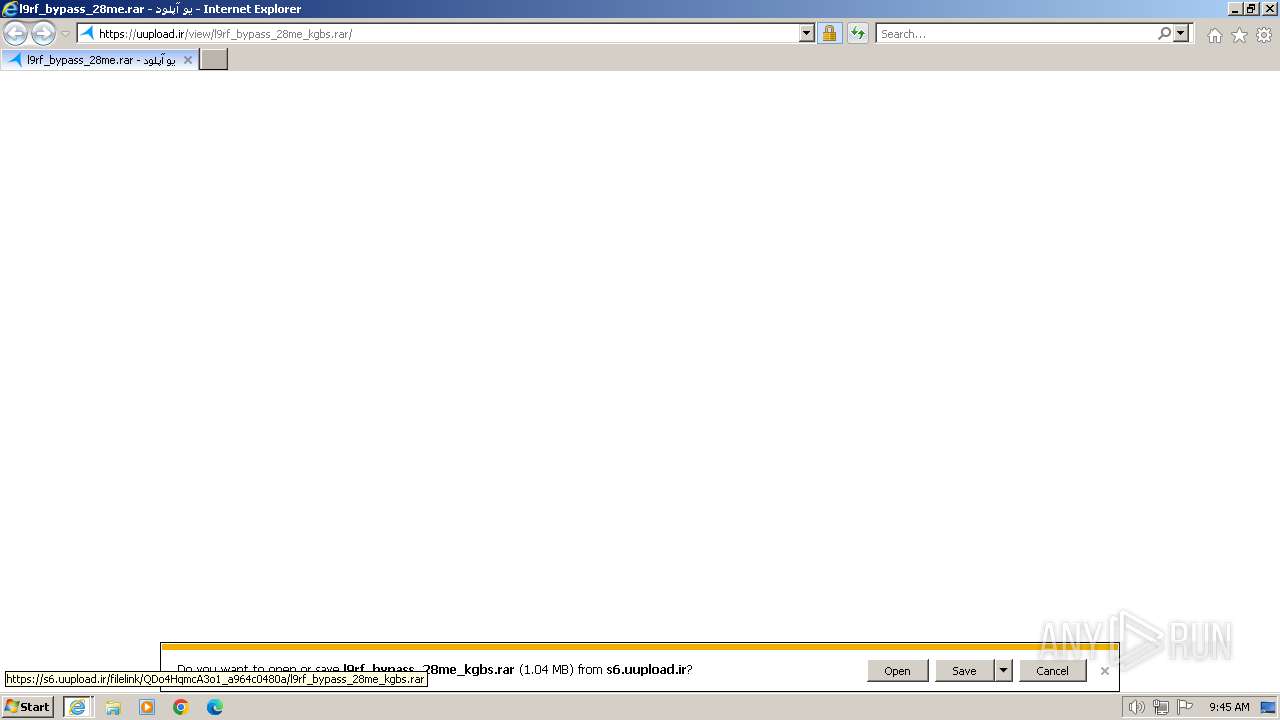
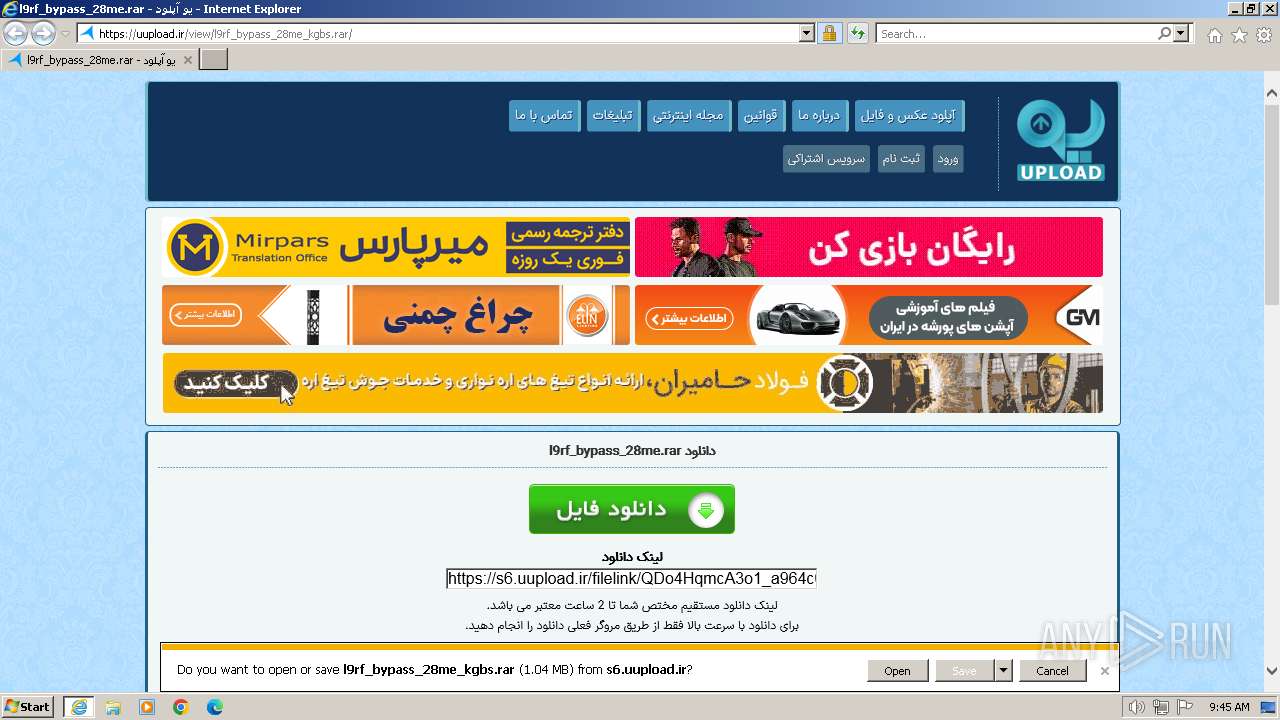
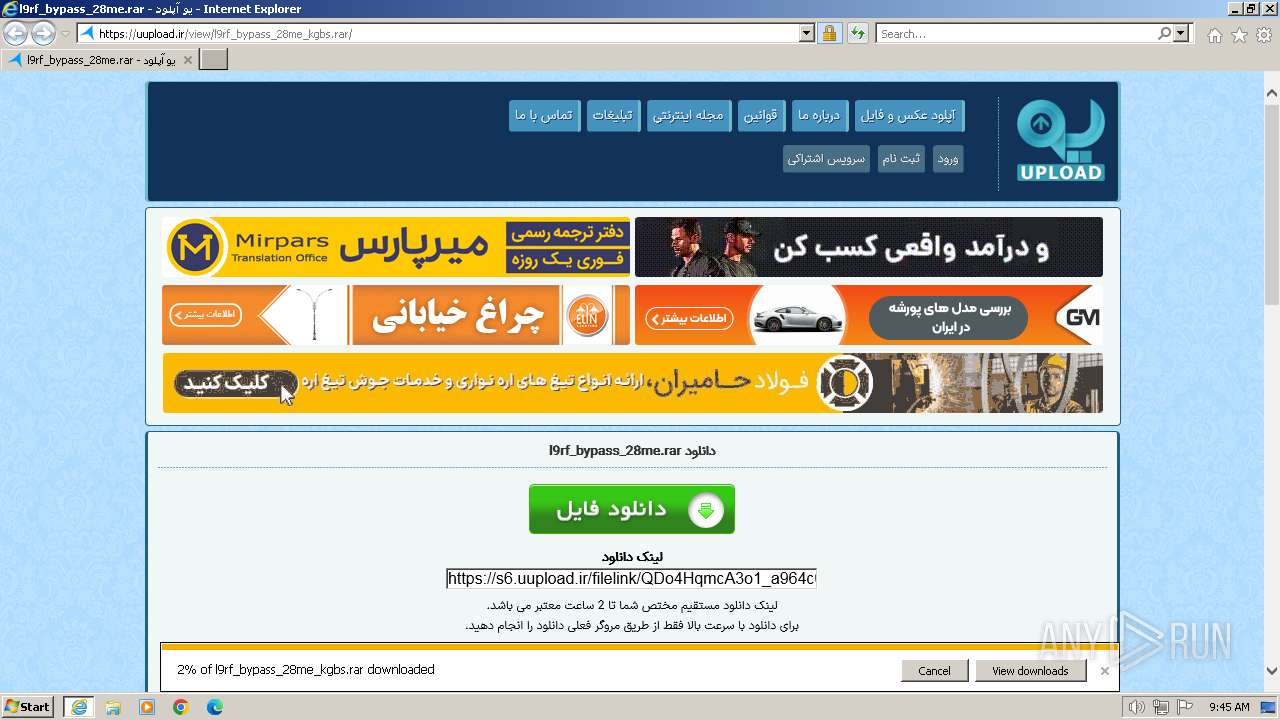
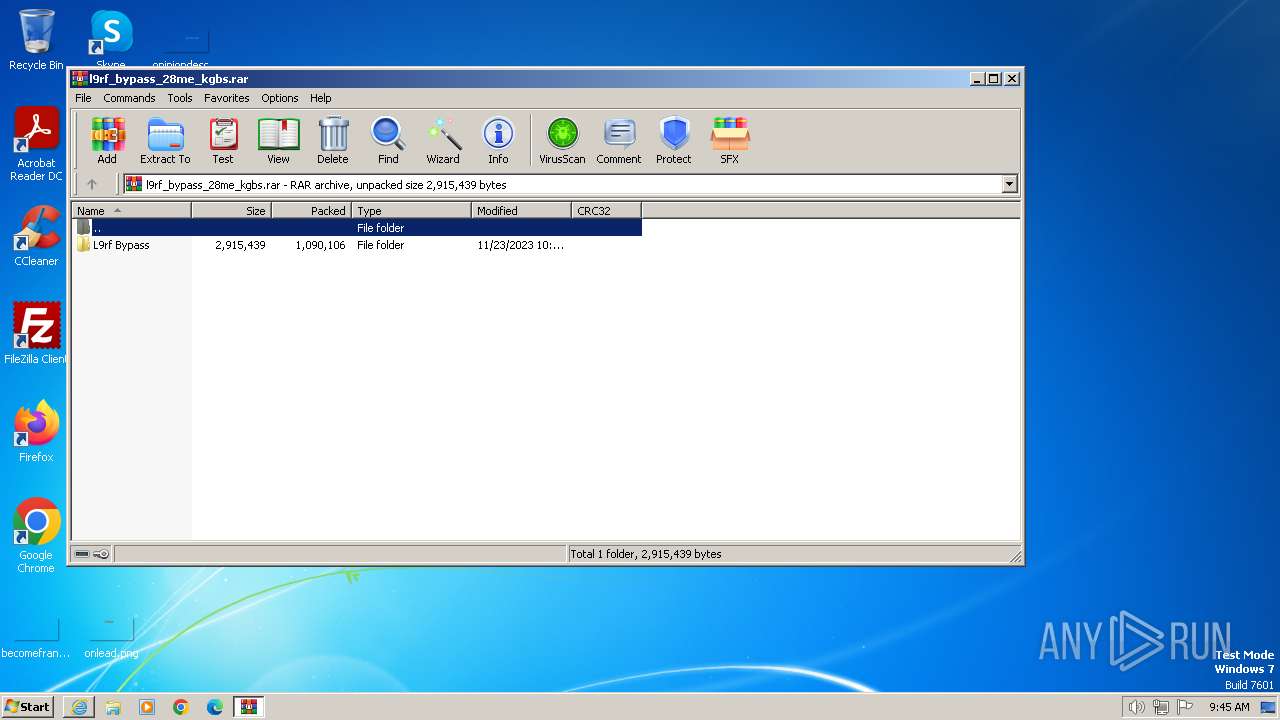
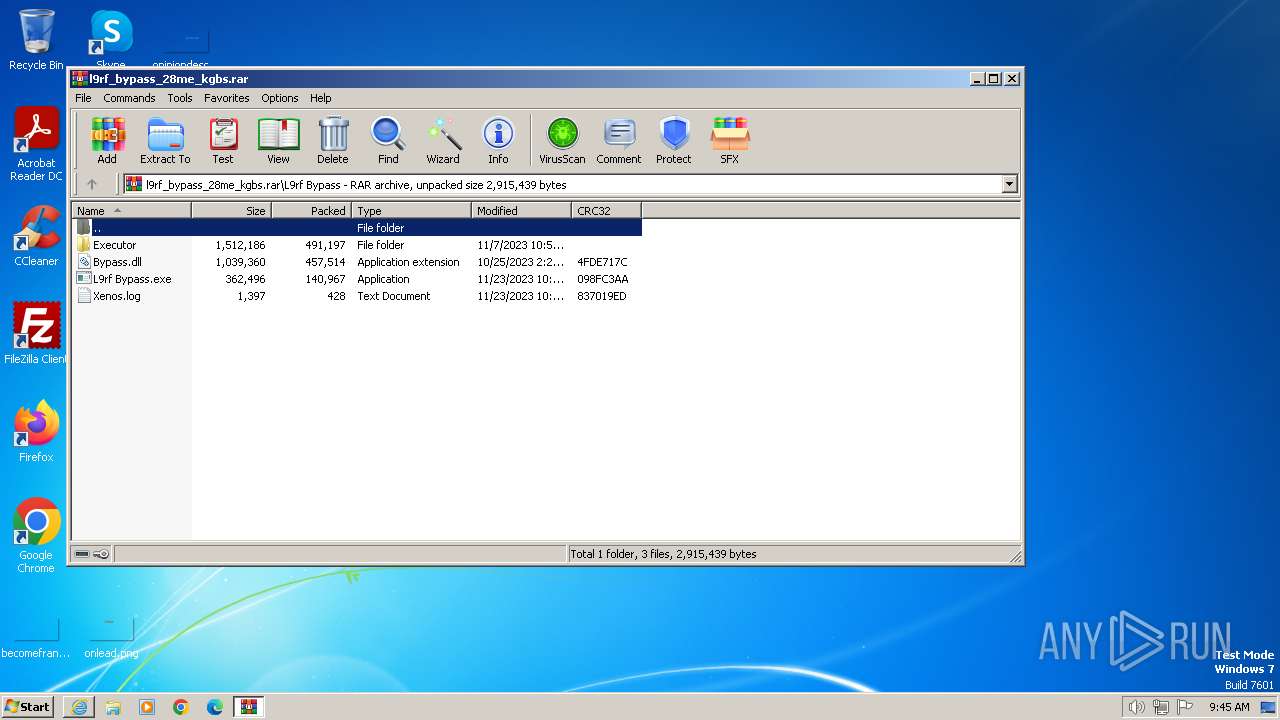
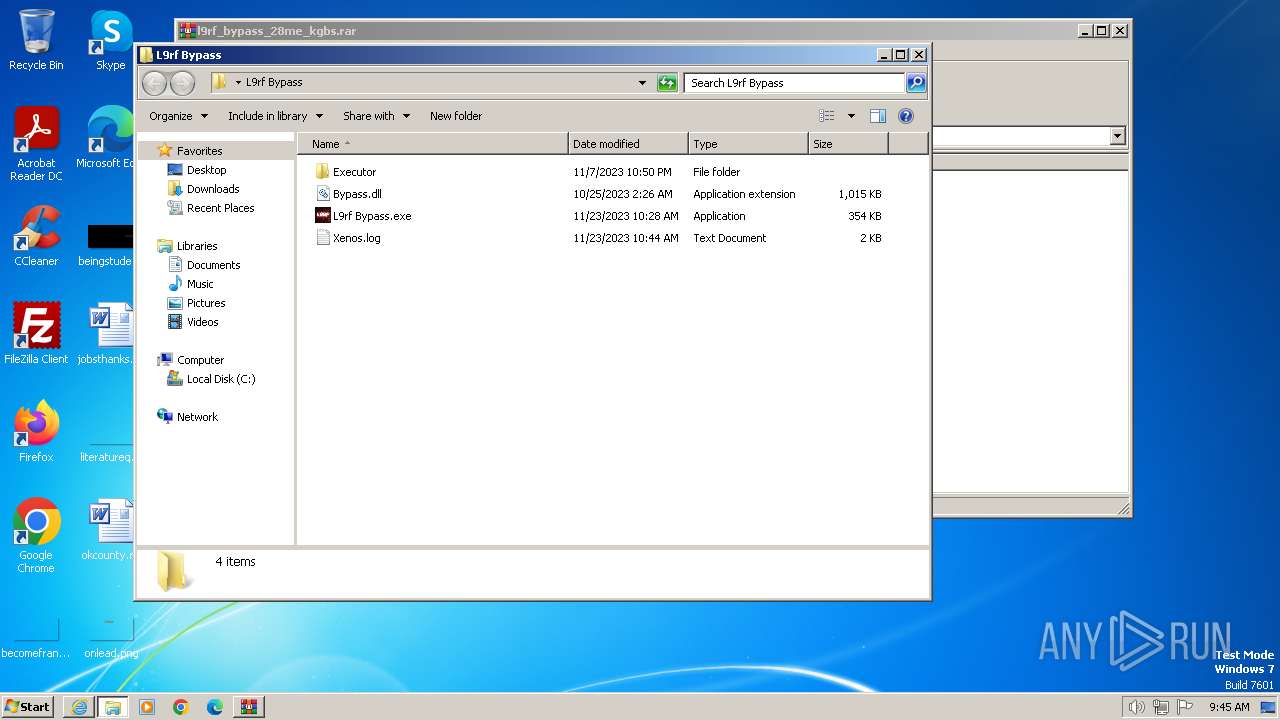
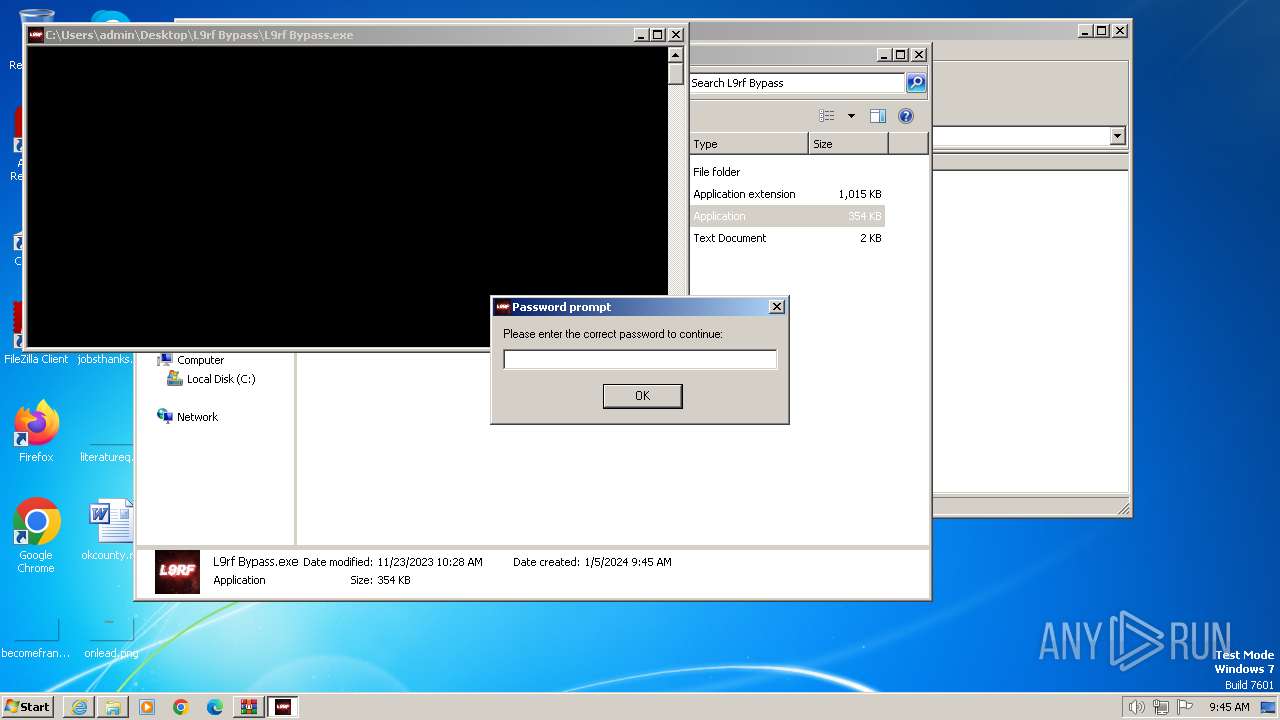
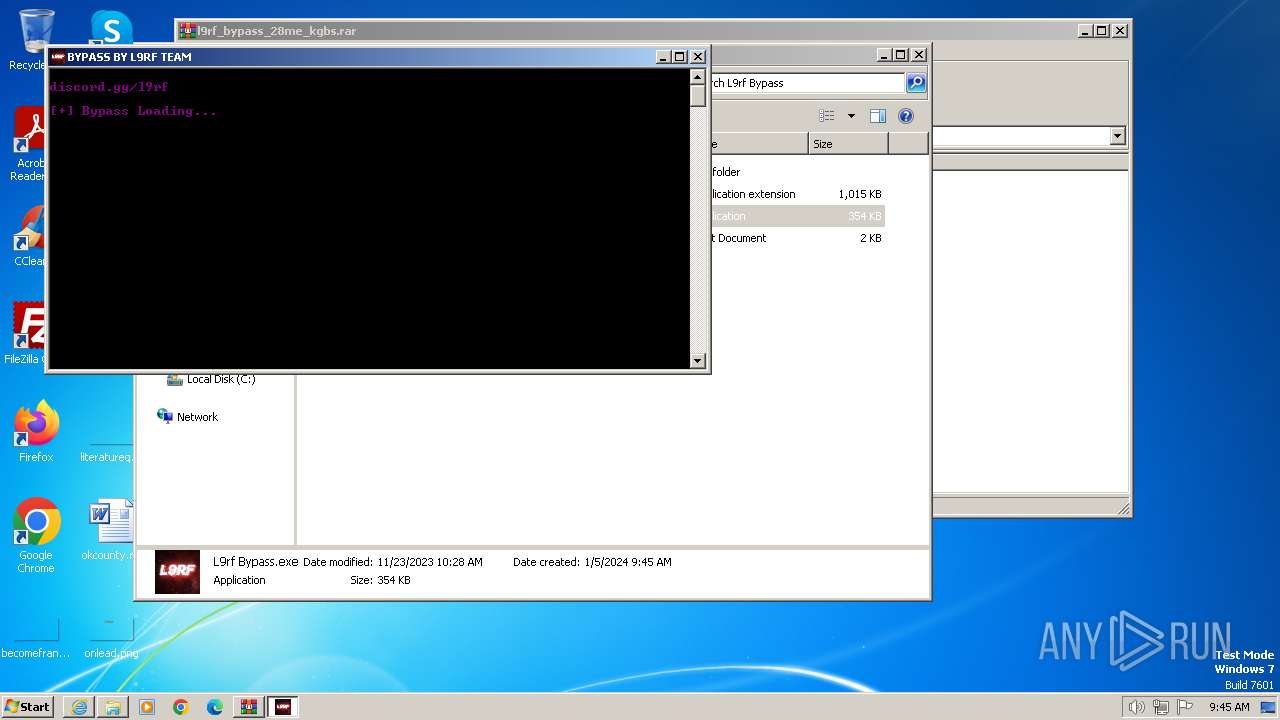
| URL: | https://uupload.ir/view/l9rf_bypass_28me_kgbs.rar/ |
| Full analysis: | https://app.any.run/tasks/1bfa910d-4bf2-47cc-b549-049d2813efc8 |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2024, 09:44:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 7A59218E640BB492C648D0D0C90A342A |
| SHA1: | 31D23BF1936753AAF131B8BE489FEED12AB37379 |
| SHA256: | 3E7B96234B8E796375BED9860853453B3798CDF59E84557E66E66F24A7B73F66 |
| SSDEEP: | 3:N8bfByKkmHcuWusl:2LUmHN5sl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executing commands from a ".bat" file
- L9rf Bypass.exe (PID: 1268)
Starts CMD.EXE for commands execution
- L9rf Bypass.exe (PID: 1268)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2320)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2668)
- iexplore.exe (PID: 2124)
Application launched itself
- iexplore.exe (PID: 2124)
Checks supported languages
- L9rf Bypass.exe (PID: 2808)
- L9rf Bypass.exe (PID: 1268)
Manual execution by a user
- L9rf Bypass.exe (PID: 1268)
- L9rf Bypass.exe (PID: 2808)
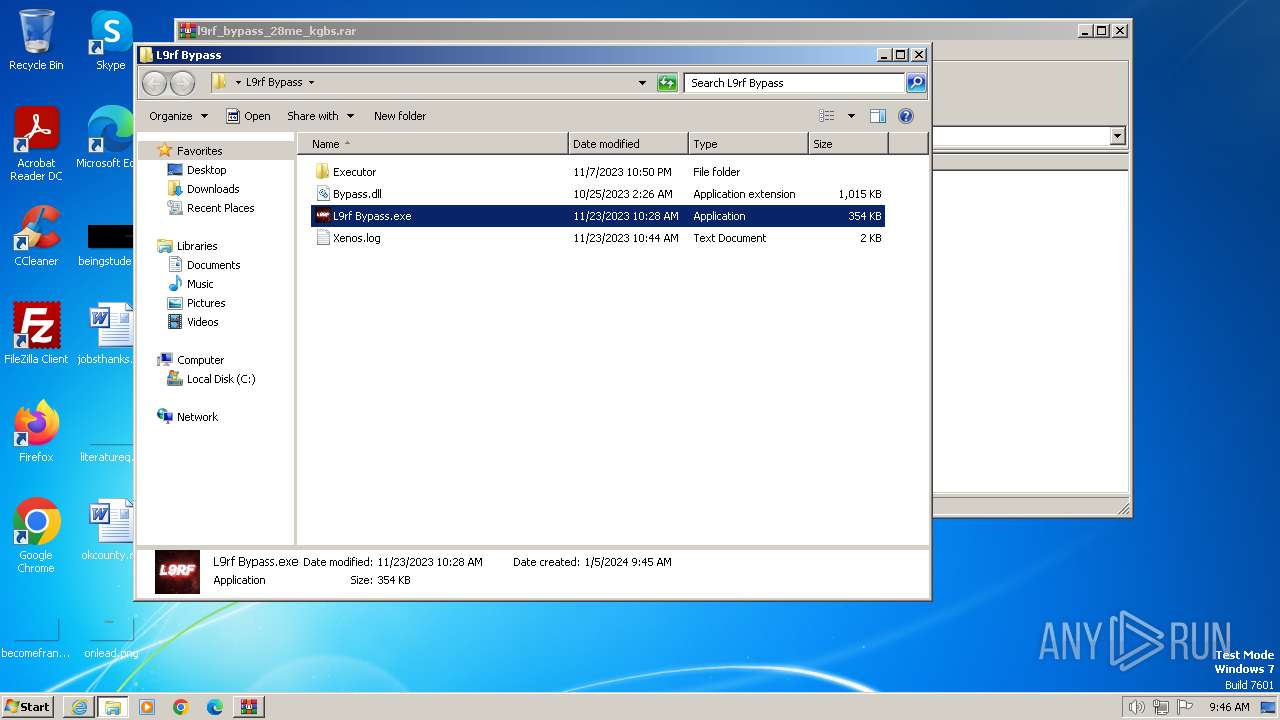
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2668)
Create files in a temporary directory
- L9rf Bypass.exe (PID: 1268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
11
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1268 | "C:\Users\admin\Desktop\L9rf Bypass\L9rf Bypass.exe" | C:\Users\admin\Desktop\L9rf Bypass\L9rf Bypass.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 216 Modules
| |||||||||||||||
| 1308 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2124 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://uupload.ir/view/l9rf_bypass_28me_kgbs.rar/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2292 | timeout /t 5 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2124 CREDAT:2954514 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2320 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\164E.tmp\165E.tmp\165F.bat "C:\Users\admin\Desktop\L9rf Bypass\L9rf Bypass.exe"" | C:\Windows\System32\cmd.exe | — | L9rf Bypass.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 216 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2668 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\l9rf_bypass_28me_kgbs.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2756 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
20 907
Read events
20 806
Write events
95
Delete events
6
Modification events
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
3
Suspicious files
48
Text files
59
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07DB822C3548410165E7DFA39F71BDE_69F97A00F12C73CFA11337B06F06B3DE | binary | |
MD5:BBC53F1958D997239C63917861847F8D | SHA256:DB6D62BAF0E887D435D682B366170E214017ABBD4810AA768D05E012F4CDFB8B | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | binary | |
MD5:2D3F0E6ACDDB3FA8D9B192AA6DF0C960 | SHA256:4B8B19F4B8E038A086A3434917C7325ABEBD0B60BB186A2EAD26D80F36B7EC1E | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\l9rf_bypass_28me_kgbs[1].htm | html | |
MD5:6AA026E3B1BDE550271EA7539D02116B | SHA256:1F54516B3F974341A4F34B2B8E84682FF06C27795D5124205A5A16DD3E1C1F31 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B46656D2CCFDF48ED2FCEC3CEF4398C8 | SHA256:0596D66479B0E8AE4B6CD0E3D726760543B1EAC5A96C8C0E99640D5492DA87F5 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | binary | |
MD5:C67AC1C7A85987DE517F3939A879F548 | SHA256:02ABBF33FBA55579BF2480466F23467756A8548B3ABAB8614A2F28846440369E | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\video-js[1].css | text | |
MD5:AFFF6493B6E8B1CCCFC2C134C77C1009 | SHA256:A343FDD5967BBF5CF420AA577DD577304FBFAB878A94F74237881FFB226DE566 | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\jquery-3.1.1.min[1].js | text | |
MD5:E071ABDA8FE61194711CFC2AB99FE104 | SHA256:85556761A8800D14CED8FCD41A6B8B26BF012D44A318866C0D81A62092EFD9BF | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\genjscript[1].js | text | |
MD5:C3ED50C957F583CB087248E8D6AF2E74 | SHA256:60F858CF323CEAF0F25D95BE56C419851E42CE1D925924E11E134B91DDDDF3EF | |||
| 1308 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\logo3[1].png | image | |
MD5:E35B5DA6EF367009D0A412C833C359E8 | SHA256:E910834FEADB5E6A7FEC6E38B66F9EA8087EE71EF95057339EE3A99457DA9381 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
47
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1308 | iexplore.exe | GET | 200 | 95.101.54.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 95.101.54.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6243fee378382ed7 | unknown | compressed | 4.66 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 23.36.162.85:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | unknown | binary | 1.50 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 23.36.162.85:80 | http://subca.ocsp-certum.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCECbd0itGycRNWmlNOYB%2Bcq0%3D | unknown | binary | 1.54 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 23.36.162.85:80 | http://dvcasha2.ocsp-certum.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNcCPjJ499lHmfPUvPsRjzr1YchwQU5TGtvzoRlvSDvFA81LeQm5Du3iUCEGXkhZuD2wYDOrEe0u4O7Y0%3D | unknown | binary | 1.56 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1308 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCZXmpIP%2Bo%2BHhJmodADfw%2Fc | unknown | binary | 472 b | unknown |
1308 | iexplore.exe | GET | 200 | 23.36.162.85:80 | http://dvcasha2.ocsp-certum.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNcCPjJ499lHmfPUvPsRjzr1YchwQU5TGtvzoRlvSDvFA81LeQm5Du3iUCEHeCZPkkKaNAJw3cL1YuoGQ%3D | unknown | binary | 1.56 Kb | unknown |
1308 | iexplore.exe | GET | 200 | 95.101.54.235:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?45a9dd4385f2d15b | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1308 | iexplore.exe | 212.33.193.83:443 | uupload.ir | Asiatech Data Transmission company | IR | unknown |
1308 | iexplore.exe | 95.101.54.235:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1308 | iexplore.exe | 23.36.162.85:80 | subca.ocsp-certum.com | Akamai International B.V. | DE | unknown |
1308 | iexplore.exe | 185.147.178.24:443 | plus.sabavision.com | Fannavaran-e Idea Pardaz-e Saba PJSC | IR | unknown |
1308 | iexplore.exe | 142.250.185.200:443 | www.googletagmanager.com | GOOGLE | US | unknown |
1308 | iexplore.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1308 | iexplore.exe | 185.166.104.4:443 | cdn.yektanet.com | Avaye Hamrahe Houshmande Hezardastan PJSC | IR | unknown |
1308 | iexplore.exe | 185.143.233.120:443 | van.najva.com | Noyan Abr Arvan Co. ( Private Joint Stock) | IR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
uupload.ir |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
subca.ocsp-certum.com |
| whitelisted |
dvcasha2.ocsp-certum.com |
| whitelisted |
plus.sabavision.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
cdn.yektanet.com |
| malicious |
van.najva.com |
| unknown |
x1.c.lencr.org |
| whitelisted |