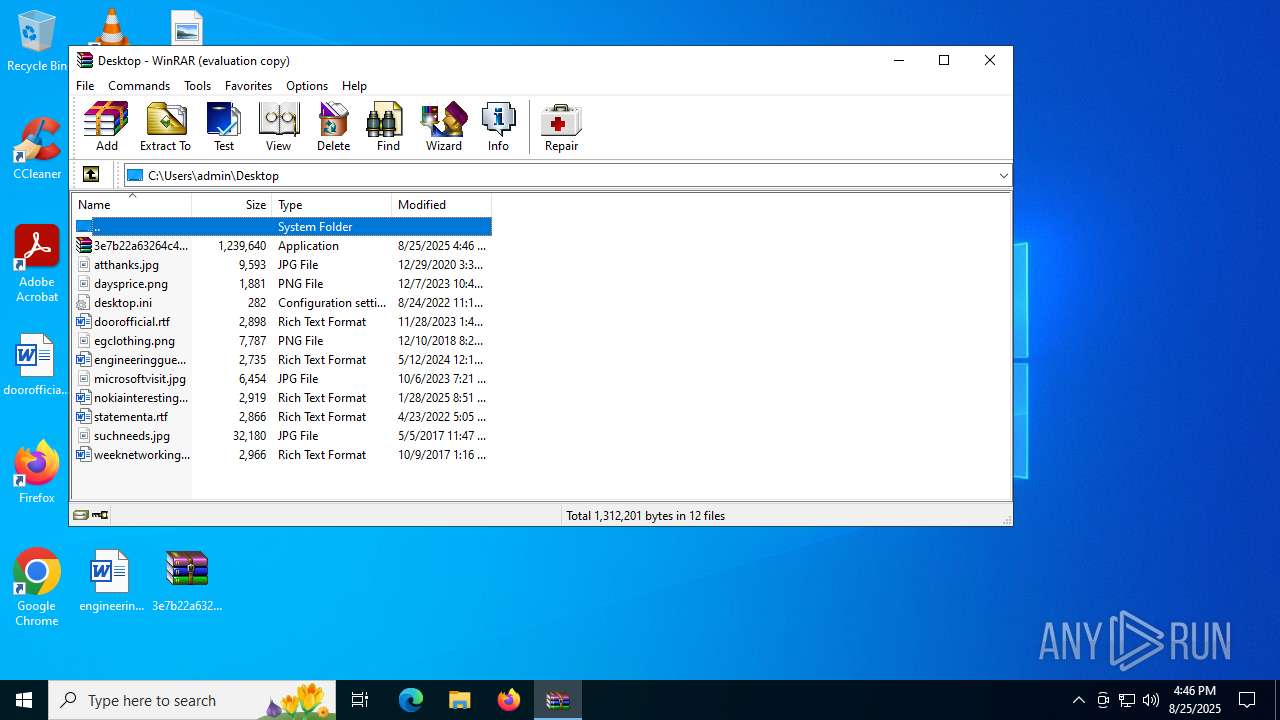
| File name: | 3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe |
| Full analysis: | https://app.any.run/tasks/cfbcf09e-e858-45a4-9fd7-f887cebc3838 |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2025, 16:46:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | A11F85A1E9786F87B60A818DCE47C166 |
| SHA1: | 559A28BB80CAABA23C738773362BB44BDD4C88C9 |
| SHA256: | 3E7B22A63264C415CA350F96755E0A76164834156DF828FF53E317F469638CA5 |
| SSDEEP: | 98304:mvINs4dxB0Y/srGGGGGGSnNfYU7zhiKC5U8kk/kdHPflEtLMH46qmHBHiBb+n5/F:X3Z |
MALICIOUS
Changes the autorun value in the registry
- mscaps.exe (PID: 2728)
SUSPICIOUS
Executable content was dropped or overwritten
- explorer.exe (PID: 984)
- mscaps.exe (PID: 2728)
Detected use of alternative data streams (AltDS)
- mscaps.exe (PID: 2728)
INFO
Checks supported languages
- 3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe (PID: 3028)
- mscaps.exe (PID: 2728)
- launch.exe (PID: 2604)
Reads security settings of Internet Explorer
- explorer.exe (PID: 984)
Manual execution by a user
- launch.exe (PID: 2604)
- mscaps.exe (PID: 2728)
Launching a file from a Registry key
- mscaps.exe (PID: 2728)
The sample compiled with english language support
- explorer.exe (PID: 984)
- 3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe (PID: 3028)
Creates files or folders in the user directory
- mscaps.exe (PID: 2728)
Reads the software policy settings
- slui.exe (PID: 2972)
Checks proxy server information
- slui.exe (PID: 2972)
Create files in a temporary directory
- explorer.exe (PID: 984)
- mscaps.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:03:05 08:37:55+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2560 |
| InitializedDataSize: | 215552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x167f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.0.0 |
| ProductVersionNumber: | 5.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| ProductName: | WinRAR |
| CompanyName: | Alexander Roshal |
| FileDescription: | WinRAR archiver |
| FileVersion: | 5.1.0 |
| ProductVersion: | 5.1.0 |
| InternalName: | WinRAR |
| LegalCopyright: | Copyright © Alexander Roshal 1993-2013 |
| OriginalFileName: | WinRAR.exe |
Total processes
149
Monitored processes
6
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | explorer.exe | C:\Windows\SysWOW64\explorer.exe | 3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2604 | "C:\Users\admin\AppData\Roaming\Microsoft\Defender\launch.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Defender\launch.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Nt Module Starter Exit code: 1 Version: 6.1.7600.16385 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\AppData\Roaming\Microsoft\Protect\SETUP\mscaps.exe" /s /n /i:U shell32.dll | C:\Users\admin\AppData\Roaming\Microsoft\Protect\SETUP\mscaps.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2972 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\Desktop\3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe" | C:\Users\admin\Desktop\3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.1.0 Modules
| |||||||||||||||
| 3460 | "C:\Users\admin\Desktop\3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe" | C:\Users\admin\Desktop\3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.1.0 | |||||||||||||||
Total events
3 889
Read events
3 888
Write events
1
Delete events
0
Modification events
| (PID) Process: | (2728) mscaps.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | JREUpdate |
Value: "C:\Users\admin\AppData\Roaming\Microsoft\Protect\SETUP\mscaps.exe" /s /n /i:U shell32.dll | |||
Executable files
3
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 984 | explorer.exe | C:\Users\admin\AppData\Local\Temp\@AED898.tmp.exe | executable | |
MD5:1046E2A4C9E500426ACF52115FC1F386 | SHA256:F28D383D51CCC70071FA79D5257981BFA6BCE3A409DCF7593CF8141A11F23014 | |||
| 2728 | mscaps.exe | C:\Users\admin\AppData\Local\Temp\D1.tmp | text | |
MD5:37512BCC96B2C0C0CF0AD1ED8CFAE5CD | SHA256:27E678BF5DC82219D6EDD744F0B82567A26E40F8A9DCD6487205E13058E3ED1F | |||
| 984 | explorer.exe | C:\Users\admin\Desktop\3e7b22a63264c415ca350f96755e0a76164834156df828ff53e317f469638ca5.exe | executable | |
MD5:746BD4CE1110823063E68BB61A24EA28 | SHA256:E77143C5F17500EFFE2EFE215777142D006BBED3313BF0A33BD3C1672E66B180 | |||
| 2728 | mscaps.exe | C:\Users\admin\AppData\Roaming\Microsoft\Protect\SETUP\wtime32.dll | executable | |
MD5:978888892A1ED13E94D2FCB832A2A6B5 | SHA256:C7DC3AC34CFCADBA2AEDF1727CE95C7E54A8E4B3ADA1373916ADB25DCF05E369 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
42
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.64:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | POST | 400 | 20.190.159.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | POST | 400 | 20.190.159.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | POST | 400 | 20.190.159.71:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | POST | 400 | 20.190.159.68:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
2692 | SIHClient.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.31.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
— | — | POST | 400 | 20.190.159.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7032 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7032 | RUXIMICS.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7032 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
windowsupdate.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |