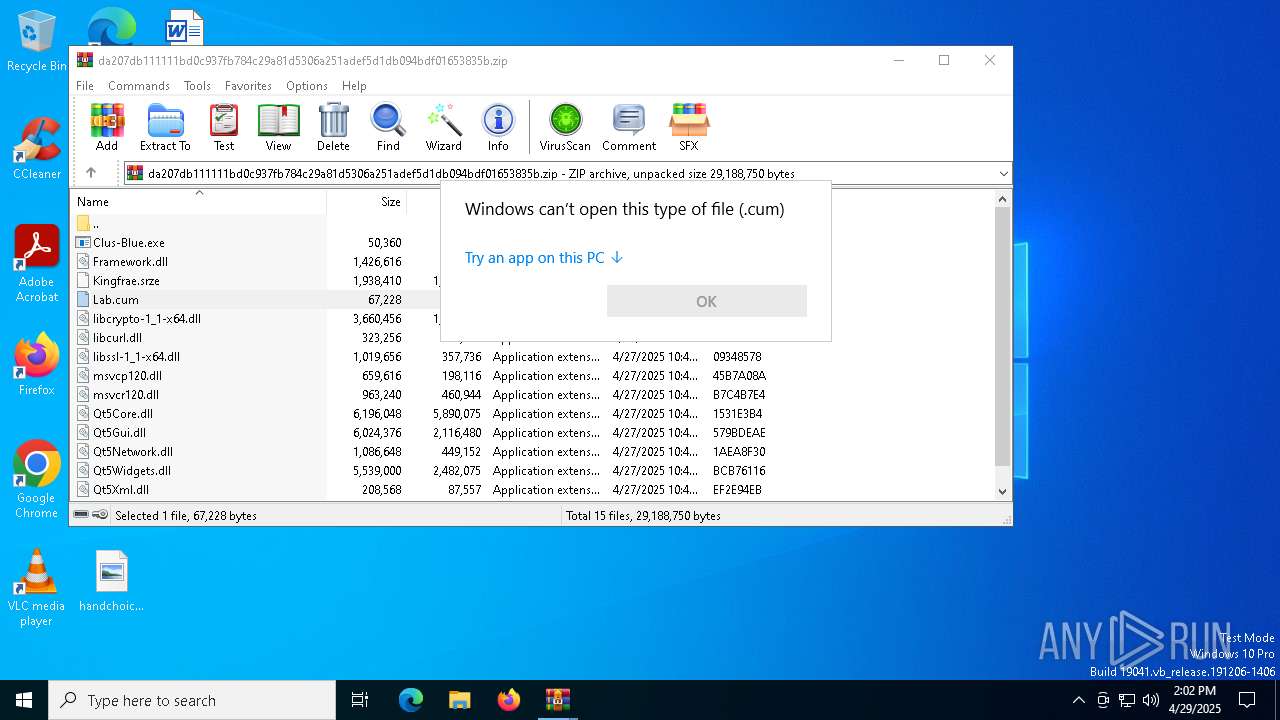
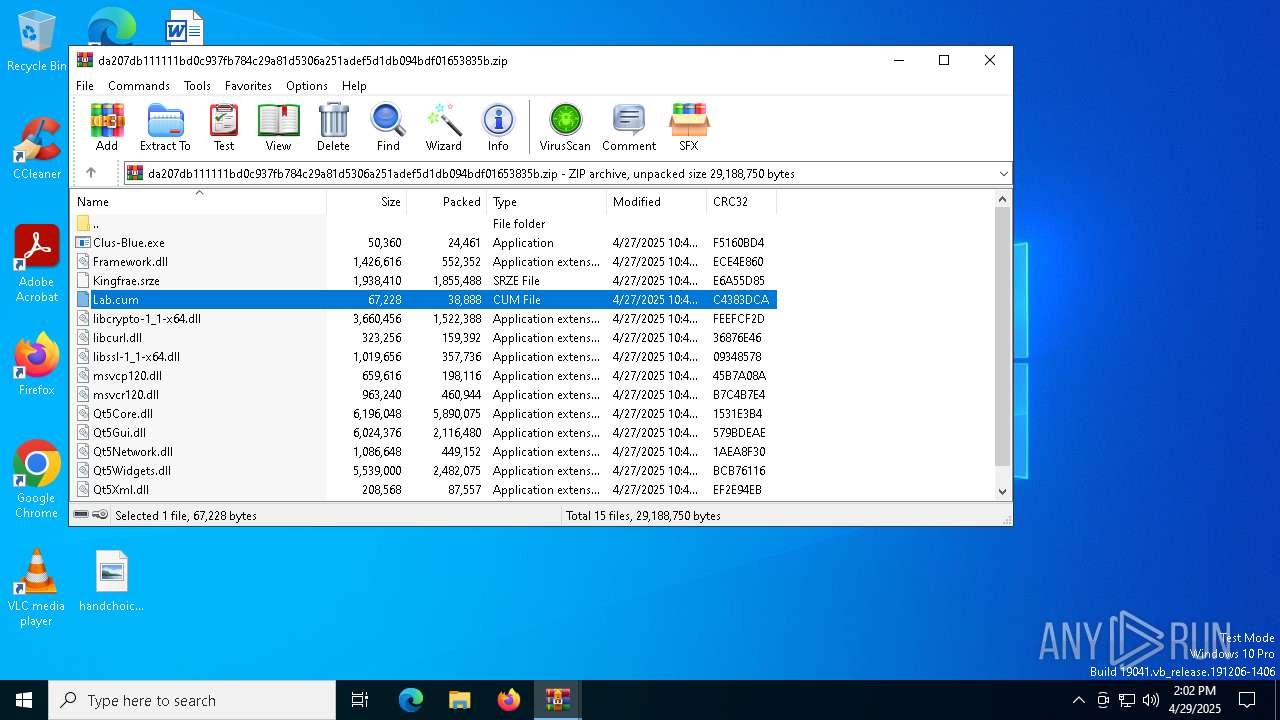
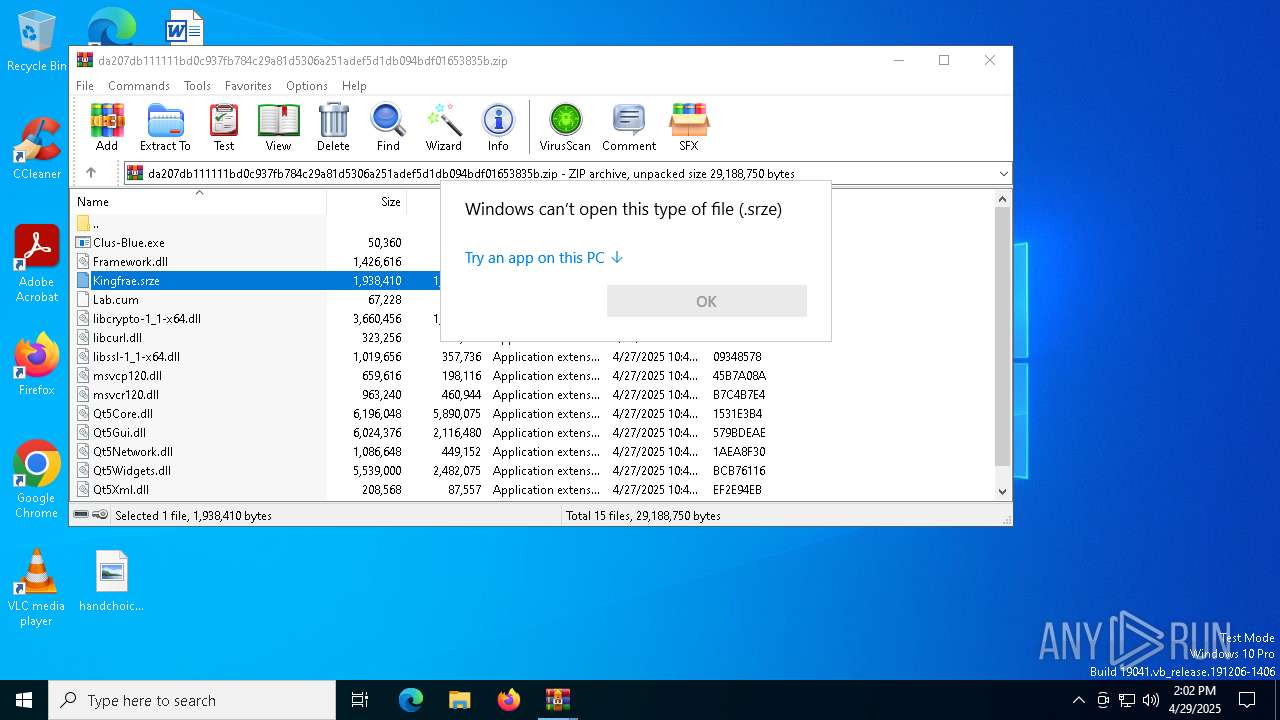
| File name: | da207db111111bd0c937fb784c29a81d5306a251adef5d1db094bdf01653835b.zip |
| Full analysis: | https://app.any.run/tasks/b585f3a3-e4a2-4db3-91ea-d78eef951faa |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 14:01:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 0603223EB183E2A4050BA6D95808CCCC |
| SHA1: | 0F27B60D9AFAAF60313C829101CA45297D91E9B6 |
| SHA256: | 3E66F59E37B70A839A20D0DF5BBF84A3942D4D281EA6A4FA1EB2F04572A76DD9 |
| SSDEEP: | 98304:foXnoL/m2qz6XeuqqEVODR7OnZSzxIPbWHu7DtqBUE/Gc4xpfbWL1DilWMXeBQ+H:mEjDlXcvmIbKWJfUEjnS5QbDEdmyWm |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 7420)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7408)
- WinRAR.exe (PID: 7692)
- Clus-Blue.exe (PID: 5384)
Application launched itself
- WinRAR.exe (PID: 7408)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7408)
- WinRAR.exe (PID: 7692)
Executable content was dropped or overwritten
- Clus-Blue.exe (PID: 5384)
- Clus-Blue.exe (PID: 2772)
- Clus-Blue.exe (PID: 7572)
The process drops C-runtime libraries
- Clus-Blue.exe (PID: 5384)
Starts itself from another location
- Clus-Blue.exe (PID: 5384)
Starts application with an unusual extension
- Clus-Blue.exe (PID: 7572)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7408)
- WinRAR.exe (PID: 7692)
- Clus-Blue.exe (PID: 5384)
Checks supported languages
- Clus-Blue.exe (PID: 5384)
- 360Tray.exe (PID: 5756)
- Clus-Blue.exe (PID: 7572)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7692)
Reads the computer name
- Clus-Blue.exe (PID: 5384)
- Clus-Blue.exe (PID: 2772)
- 360Tray.exe (PID: 5756)
- Clus-Blue.exe (PID: 7572)
- ping.com (PID: 2236)
Creates files in the program directory
- Clus-Blue.exe (PID: 5384)
- Clus-Blue.exe (PID: 2772)
The sample compiled with chinese language support
- Clus-Blue.exe (PID: 2772)
Reads the machine GUID from the registry
- 360Tray.exe (PID: 5756)
Create files in a temporary directory
- Clus-Blue.exe (PID: 7572)
- Clus-Blue.exe (PID: 2772)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 2096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:29 14:01:22 |
| ZipCRC: | 0x7dbacfc1 |
| ZipCompressedSize: | 16175429 |
| ZipUncompressedSize: | 16212933 |
| ZipFileName: | da207db111111bd0c937fb784c29a81d5306a251adef5d1db094bdf01653835b.zip |
Total processes
143
Monitored processes
11
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2096 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | C:\Users\admin\AppData\Local\Temp\47165984\ping.com | C:\Users\admin\AppData\Local\Temp\47165984\ping.com | — | Clus-Blue.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2772 | C:\ProgramData\Fidl\Clus-Blue.exe | C:\ProgramData\Fidl\Clus-Blue.exe | Clus-Blue.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5384 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Clus-Blue.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Clus-Blue.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5756 | "C:\ProgramData\Fidl\360Tray.exe" "C:\ProgramData\Fidl\360Tray.exe" /onui | C:\ProgramData\Fidl\360Tray.exe | — | Clus-Blue.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: MEDIUM Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 12, 0, 0, 1761 Modules
| |||||||||||||||
| 6272 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7208 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7408 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\da207db111111bd0c937fb784c29a81d5306a251adef5d1db094bdf01653835b.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7420 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7572 | "C:\ProgramData\Fidl\Clus-Blue.exe" | C:\ProgramData\Fidl\Clus-Blue.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
5 852
Read events
5 834
Write events
18
Delete events
0
Modification events
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\da207db111111bd0c937fb784c29a81d5306a251adef5d1db094bdf01653835b.zip | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7408) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
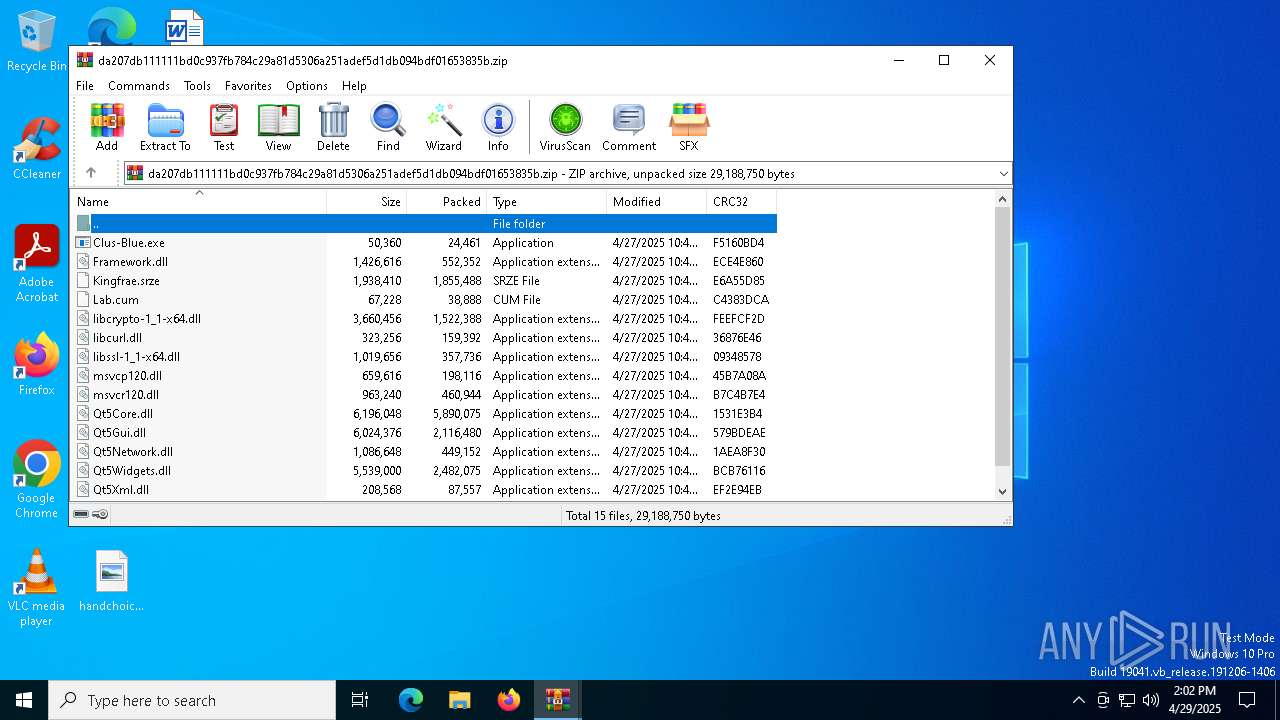
Executable files
28
Suspicious files
11
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Qt5Core.dll | executable | |
MD5:5AF1A8D3E720C2ECD7C835510429DA9F | SHA256:45A830C44F93ABA5658E5E9697DE42B3F3EB383BBBF174ADE65A78F9A6C7D8B2 | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Qt5Xml.dll | executable | |
MD5:EFEE87118A310EDB82A7A6AEEBAEC1C1 | SHA256:0A6D4E2FB47E8DB1D35EA70D66D40097469CBF61979FD10AA2BEB44A6CA06324 | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Qt5Gui.dll | executable | |
MD5:72AC63E9E9F015D6471DDE58297A4FC6 | SHA256:6B8A49B6B37D69213762C8F2C8A9970014364F4055F08A850D27C0343FBE00DE | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Clus-Blue.exe | executable | |
MD5:20BC61AA222AA74059F4D42872A76EB5 | SHA256:B1465F5CE1D0F83EF9B6086C81D8788B50C09BD329374BD3D04DC61807551435 | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Qt5Network.dll | executable | |
MD5:D73AA4F8749269D1590541E567387489 | SHA256:7BFDFED166846921DAB87D51CA9B338C1FDD7F96C117E3BA0EDC07ED06DD9CB1 | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Framework.dll | executable | |
MD5:2207332818329E3CE4E5E020BA1B1F04 | SHA256:C554A0BD610BA0B10D8D92BB588FC86893B59985E4ED9316D340781C482FCAA2 | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Utility.dll | executable | |
MD5:48B0445F21B92190B1E199AD31F89CBC | SHA256:3094FB377E55EF2DEAE50B6C350EA2B6D37FD098D75CD3F874E5AF705A5BB3E8 | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\msvcr120.dll | executable | |
MD5:AEB29CCC27E16C4FD223A00189B44524 | SHA256:D28C7AB34842B6149609BD4E6B566DDAB8B891F0D5062480A253EF20A6A2CAAA | |||
| 7692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7692.15658\Qt5Widgets.dll | executable | |
MD5:2BD07ACEF2FFD5AD8388B714D4F81995 | SHA256:250C3717663E4AB3CE50E4A53BC532BF0C0850D2917773DD7E482E733081A1A1 | |||
| 5384 | Clus-Blue.exe | C:\ProgramData\Fidl\libcrypto-1_1-x64.dll | executable | |
MD5:CF1DF078FA02C3F20A613FF9FACEEE46 | SHA256:0897F6EF6C7875F64ED82AD83473FD8EA119CFEAA959B0AB2B2F981C1DA7C679 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.34:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 172.211.123.250:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6404 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5304 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |