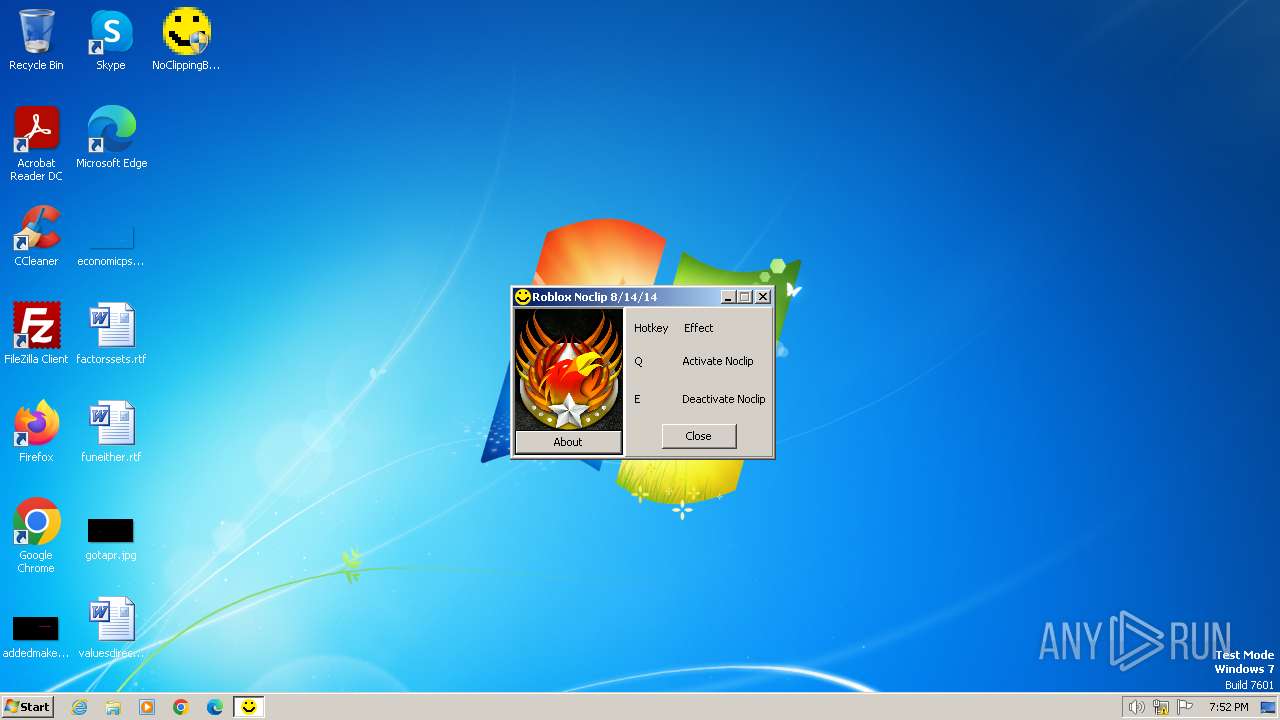
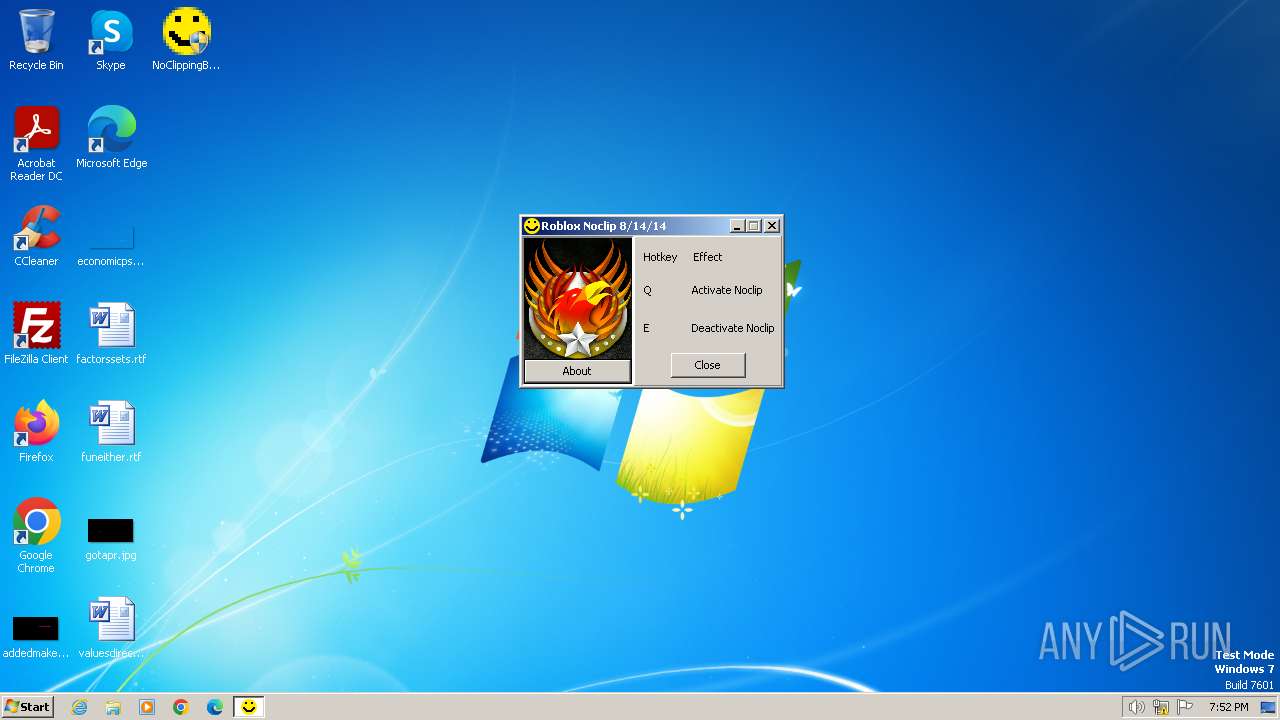
| File name: | NoClippingBro_[unknowncheats.me]_.exe |
| Full analysis: | https://app.any.run/tasks/a60fde04-1473-4797-a0e8-d3247bf7a657 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2024, 18:52:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1BF97464516EBA32632E4978EF2F7E4F |
| SHA1: | ECBADE5BED7C0E5077A780AE40F9989C35F2C0DF |
| SHA256: | 3E636D37906E3D578472E3FC0E32FC627D5D459C65F8436EAAECDDB5440B29FF |
| SSDEEP: | 98304:PirUeUkFkHKzsCEx41M9fg1rlFsb4KAUoVF+f6eY/b/WlmPBUFihKRkEeSD2mTRO:dXkeG8b/s7QV |
MALICIOUS
Changes the autorun value in the registry
- sidebar.exe (PID: 2920)
SUSPICIOUS
Executable content was dropped or overwritten
- NoClippingBro_[unknowncheats.me]_.exe (PID: 748)
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3592)
Reads the Internet Settings
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
- sidebar.exe (PID: 2920)
Reads security settings of Internet Explorer
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
- sidebar.exe (PID: 2920)
There is functionality for communication over UDP network (YARA)
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
Process drops legitimate windows executable
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3592)
Reads Microsoft Outlook installation path
- sidebar.exe (PID: 2920)
Reads Internet Explorer settings
- sidebar.exe (PID: 2920)
Reads settings of System Certificates
- filezilla.exe (PID: 1476)
Connects to unusual port
- fzsftp.exe (PID: 1916)
INFO
Create files in a temporary directory
- NoClippingBro_[unknowncheats.me]_.exe (PID: 748)
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3592)
Reads the computer name
- NoClippingBro_[unknowncheats.me]_.exe (PID: 748)
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
- xmplayer.exe (PID: 2296)
- sidebar.exe (PID: 2920)
- fzsftp.exe (PID: 1916)
- wmpnscfg.exe (PID: 524)
- filezilla.exe (PID: 1476)
Checks supported languages
- NoClippingBro_[unknowncheats.me]_.exe (PID: 748)
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3592)
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
- xmplayer.exe (PID: 2296)
- sidebar.exe (PID: 2920)
- filezilla.exe (PID: 1476)
- wmpnscfg.exe (PID: 524)
- fzsftp.exe (PID: 1916)
Sends debugging messages
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
The process uses the downloaded file
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
- sidebar.exe (PID: 2920)
Manual execution by a user
- sidebar.exe (PID: 2920)
- filezilla.exe (PID: 1476)
- wmpnscfg.exe (PID: 524)
The process uses Lua
- NoClippingBro_[unknowncheats.me]_.exe (PID: 3060)
Creates files or folders in the user directory
- sidebar.exe (PID: 2920)
- filezilla.exe (PID: 1476)
- fzsftp.exe (PID: 1916)
Reads the machine GUID from the registry
- sidebar.exe (PID: 2920)
- filezilla.exe (PID: 1476)
- fzsftp.exe (PID: 1916)
Reads Environment values
- sidebar.exe (PID: 2920)
Checks proxy server information
- sidebar.exe (PID: 2920)
Creates files in the program directory
- sidebar.exe (PID: 2920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (47.3) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:06:28 14:45:44+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 36352 |
| InitializedDataSize: | 5585920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15eb |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
47
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | "C:\Users\admin\Desktop\NoClippingBro_[unknowncheats.me]_.exe" | C:\Users\admin\Desktop\NoClippingBro_[unknowncheats.me]_.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1476 | "C:\Program Files\FileZilla FTP Client\filezilla.exe" | C:\Program Files\FileZilla FTP Client\filezilla.exe | — | explorer.exe | |||||||||||
User: admin Company: FileZilla Project Integrity Level: MEDIUM Description: FileZilla FTP Client Version: 3, 65, 0, 0 Modules
| |||||||||||||||
| 1916 | "C:\Program Files\FileZilla FTP Client\fzsftp.exe" -v | C:\Program Files\FileZilla FTP Client\fzsftp.exe | filezilla.exe | ||||||||||||
User: admin Company: FileZilla Project Integrity Level: MEDIUM Description: SFTP module for FileZilla based on PuTTY's psftp component Version: Unidentified build Modules
| |||||||||||||||
| 2296 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\xmplayer.exe" CEAFCA1A660_30A4_40BE_AF24D4FF39135AAE | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\xmplayer.exe | — | NoClippingBro_[unknowncheats.me]_.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2920 | "C:\Program Files\Windows Sidebar\sidebar.exe" /showGadgets | C:\Program Files\Windows Sidebar\sidebar.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Desktop Gadgets Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3060 | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\NoClippingBro_[unknowncheats.me]_.exe "C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\CET_TRAINER.CETRAINER" "-ORIGIN:C:\Users\admin\Desktop\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\NoClippingBro_[unknowncheats.me]_.exe | NoClippingBro_[unknowncheats.me]_.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Version: 6.4.0.4106 Modules
| |||||||||||||||
| 3256 | "C:\Users\admin\Desktop\NoClippingBro_[unknowncheats.me]_.exe" | C:\Users\admin\Desktop\NoClippingBro_[unknowncheats.me]_.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3592 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\NoClippingBro_[unknowncheats.me]_.exe" -ORIGIN:"C:\Users\admin\Desktop\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\NoClippingBro_[unknowncheats.me]_.exe | NoClippingBro_[unknowncheats.me]_.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
4 172
Read events
4 140
Write events
28
Delete events
4
Modification events
| (PID) Process: | (3060) NoClippingBro_[unknowncheats.me]_.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3060) NoClippingBro_[unknowncheats.me]_.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3060) NoClippingBro_[unknowncheats.me]_.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3060) NoClippingBro_[unknowncheats.me]_.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3060) NoClippingBro_[unknowncheats.me]_.exe | Key: | HKEY_CURRENT_USER\Software\Cheat Engine\Window Positions |
| Operation: | write | Name: | AdvancedOptions Position |
Value: 7E010000FF0100007402000029010000 | |||
| (PID) Process: | (3060) NoClippingBro_[unknowncheats.me]_.exe | Key: | HKEY_CURRENT_USER\Software\Cheat Engine\Window Positions |
| Operation: | write | Name: | frmAutoInject Position |
Value: 8701000000050000AF0100004B010000 | |||
| (PID) Process: | (2920) sidebar.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Sidebar\Settings |
| Operation: | write | Name: | ShowGadgets |
Value: 1 | |||
| (PID) Process: | (2920) sidebar.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Sidebar |
Value: C:\Program Files\Windows Sidebar\sidebar.exe /autoRun | |||
| (PID) Process: | (2920) sidebar.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2920) sidebar.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
5
Suspicious files
4
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 748 | NoClippingBro_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\CET_Archive.dat | — | |
MD5:— | SHA256:— | |||
| 3592 | NoClippingBro_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\NoClippingBro_[unknowncheats.me]_.exe | executable | |
MD5:052F561D15254E91BC505D5066F4F16C | SHA256:98269F89557E11C629155A2E29235FCE7D1B25BAA78A2A475AD1A27E626E75A6 | |||
| 3592 | NoClippingBro_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\xmplayer.exe | executable | |
MD5:B1761FCB265515ADB02D3675C6E0D135 | SHA256:D66240856AD4A49CDCBAD9DCDD03422E46F269F245B5A74CB750875535A6DC5A | |||
| 3592 | NoClippingBro_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\win32\dbghelp.dll | executable | |
MD5:9139604740814E53298A5E8428BA29D7 | SHA256:150782FCA5E188762A41603E2D5C7AAD6B6419926BCADF350EBF84328E50948F | |||
| 748 | NoClippingBro_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\NoClippingBro_[unknowncheats.me]_.exe | executable | |
MD5:808DE473370EF6B5D98AB752F245A3CA | SHA256:65CBED2E8DB313B8966638E40EB27F94156C294EB060B28A02C130D146518C39 | |||
| 1476 | filezilla.exe | C:\Users\admin\AppData\Local\FileZilla\default_refresh20x20.png | image | |
MD5:4200F34DDE6326197C308F620DE40E17 | SHA256:81FAD4C1D3BB7678FCD32B29DCF113B4AB869653C4A31EDEF61EC560CFD1D5B5 | |||
| 1476 | filezilla.exe | C:\Users\admin\AppData\Roaming\FileZilla\layout.xml | xml | |
MD5:2C67357412FE5428D2EB67E2178925FA | SHA256:6E8BEE236C7BB6E2CD249AF7449B0F08AFCEBEBE4140CF818750E4489D570B69 | |||
| 3592 | NoClippingBro_[unknowncheats.me]_.exe | C:\Users\admin\AppData\Local\Temp\cetrainers\CETCC05.tmp\extracted\defines.lua | text | |
MD5:D8F9B4A10A48EBD8936255F6215C8A43 | SHA256:D4347332B232622283E7DD3781F64966BD1097D06CCA7052B467CF99E62898F2 | |||
| 2920 | sidebar.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Sidebar\Settings.ini | text | |
MD5:30D295030F52A72ECDA3994602164E4C | SHA256:E441993B15AF83500BE37304EADBE48CBC127CAB7D8FB531F770753FA56C4902 | |||
| 1476 | filezilla.exe | C:\Users\admin\AppData\Local\FileZilla\default_sitemanager20x20.png | image | |
MD5:0DA3E808ABE002C20B4451F5D0F2990F | SHA256:6B2CE84C384134C13BCDBF03F3163EBD9B59E6E40D5A881DF02A2B671F8F12A1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
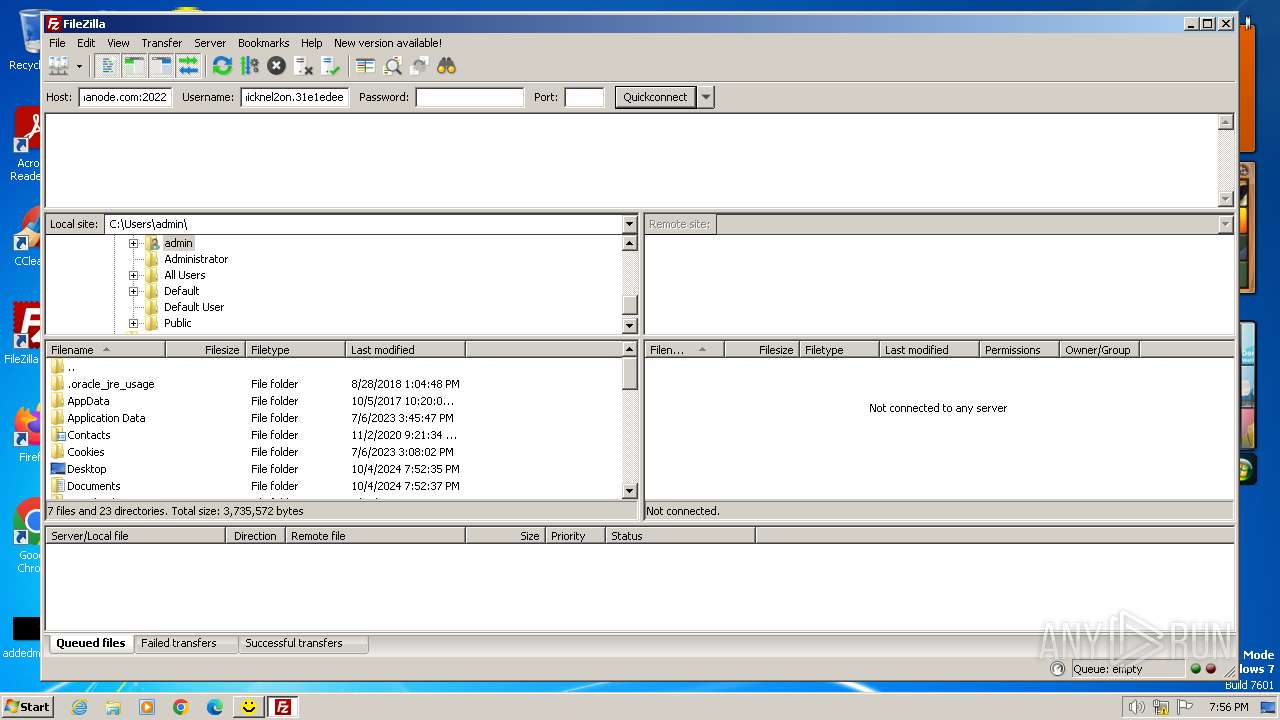
1916 | fzsftp.exe | 144.76.58.217:2022 | gold.magmanode.com | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
gold.magmanode.com |
| unknown |
Threats
Process | Message |
|---|---|
NoClippingBro_[unknowncheats.me]_.exe | Offset of LBR_Count=760 |
NoClippingBro_[unknowncheats.me]_.exe | sizeof fxstate = 512 |
NoClippingBro_[unknowncheats.me]_.exe | symbolloader thread finished |
NoClippingBro_[unknowncheats.me]_.exe | Symbolhandler: sync: Calling finishedloadingsymbols |
NoClippingBro_[unknowncheats.me]_.exe | finishedLoadingSymbols called |
NoClippingBro_[unknowncheats.me]_.exe | exit finishedLoadingSymbols() |
NoClippingBro_[unknowncheats.me]_.exe | after finishedloadingsymbols |
NoClippingBro_[unknowncheats.me]_.exe | Symbol loader thread has finished without errors |