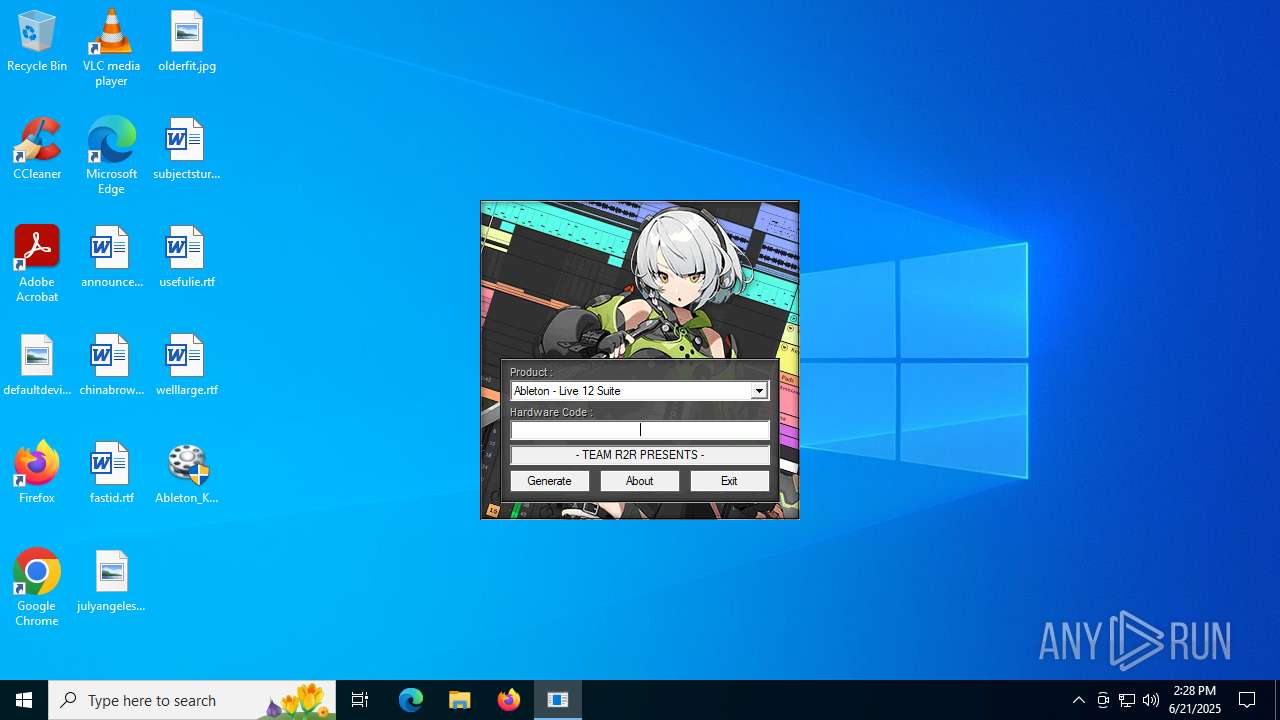
| File name: | Ableton_KeyGen.exe |
| Full analysis: | https://app.any.run/tasks/6c73a795-0a07-4fa5-97d8-e2e06009ad56 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 14:28:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 7E1329F086BE6599D92CC72DE9BB7092 |
| SHA1: | 8857FDC7E2DC64D6BB6E8FC057E3DE11F1A1BA51 |
| SHA256: | 3E5A4418610A7B376714A235A49082645524B4162DDA27AE04529C21C26530B5 |
| SSDEEP: | 24576:9P3sUkCvMbgCfj6XHKO4bRxWYXG8Csdo1dM2Qgkd8QGYsPPykWwuUhO6Vzdzo9jZ:9P3sUkC0bg0j6XHKO4bRxWt8CQoLM2Q7 |
MALICIOUS
GENERIC has been found (auto)
- Ableton_KeyGen.exe (PID: 4192)
SUSPICIOUS
Executable content was dropped or overwritten
- Ableton_KeyGen.exe (PID: 4192)
There is functionality for taking screenshot (YARA)
- Ableton_KeyGen.exe (PID: 4192)
- keygen.exe (PID: 2320)
INFO
Checks supported languages
- Ableton_KeyGen.exe (PID: 4192)
- keygen.exe (PID: 2320)
Create files in a temporary directory
- Ableton_KeyGen.exe (PID: 4192)
- keygen.exe (PID: 2320)
Reads the computer name
- keygen.exe (PID: 2320)
Reads the software policy settings
- slui.exe (PID: 2620)
Checks proxy server information
- slui.exe (PID: 2620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:08 23:05:20+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3557 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
139
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | Ableton_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2620 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3752 | "C:\Users\admin\Desktop\Ableton_KeyGen.exe" | C:\Users\admin\Desktop\Ableton_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 4192 | "C:\Users\admin\Desktop\Ableton_KeyGen.exe" | C:\Users\admin\Desktop\Ableton_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
3 753
Read events
3 753
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4192 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 4192 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | binary | |
MD5:EAC249A6CBD92E5A744F1921261B4134 | SHA256:9AE311E672F224A27350DD37CCE871187377531741DF048082B9CB680CD12882 | |||
| 4192 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:06BCC4D8A84B71A8EBA29F61427E5539 | SHA256:24B991E26B12F2ED3CFEF48E35F0AC00CCA857FDF0FEAB994A7D481A11514D26 | |||
| 4192 | Ableton_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RLIVE2.dll | executable | |
MD5:EE949648A4E084BA17C54B09F4FA446E | SHA256:DCA2A82C8AE80F16CFCADFA5A5AE40970185E35EB0AA91A1E282E826C735A131 | |||
| 2320 | keygen.exe | C:\Users\admin\AppData\Local\Temp\~DFB8618AFDD6B72A80.TMP | binary | |
MD5:B59EDFABDFB34A1C40DBD4F3F1DBE6D7 | SHA256:6FE223E923D7DF44E365247D7BE87D0BECC18C4D12B3C5F2203B9F0B94C8A45A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
54
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.24.77.10:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.2:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.132:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
3504 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3504 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3504 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 4.245.163.56:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | POST | 400 | 20.190.160.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4156 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.10:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6024 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |