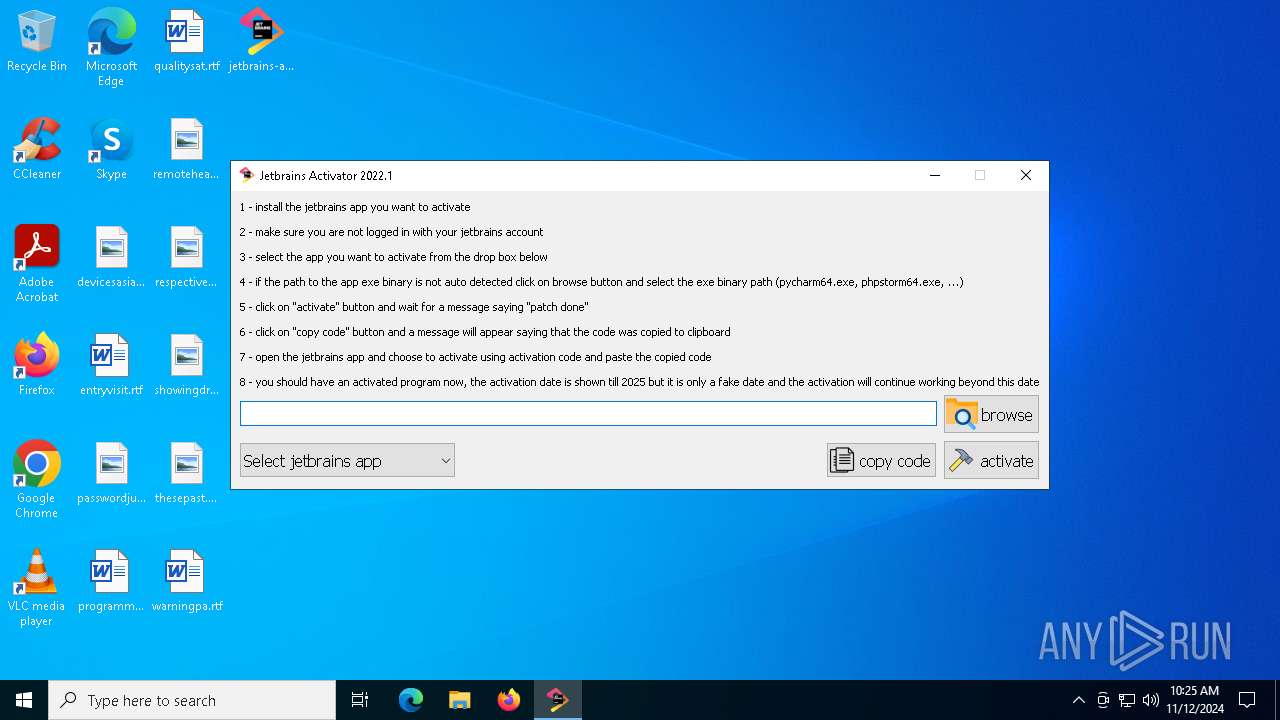
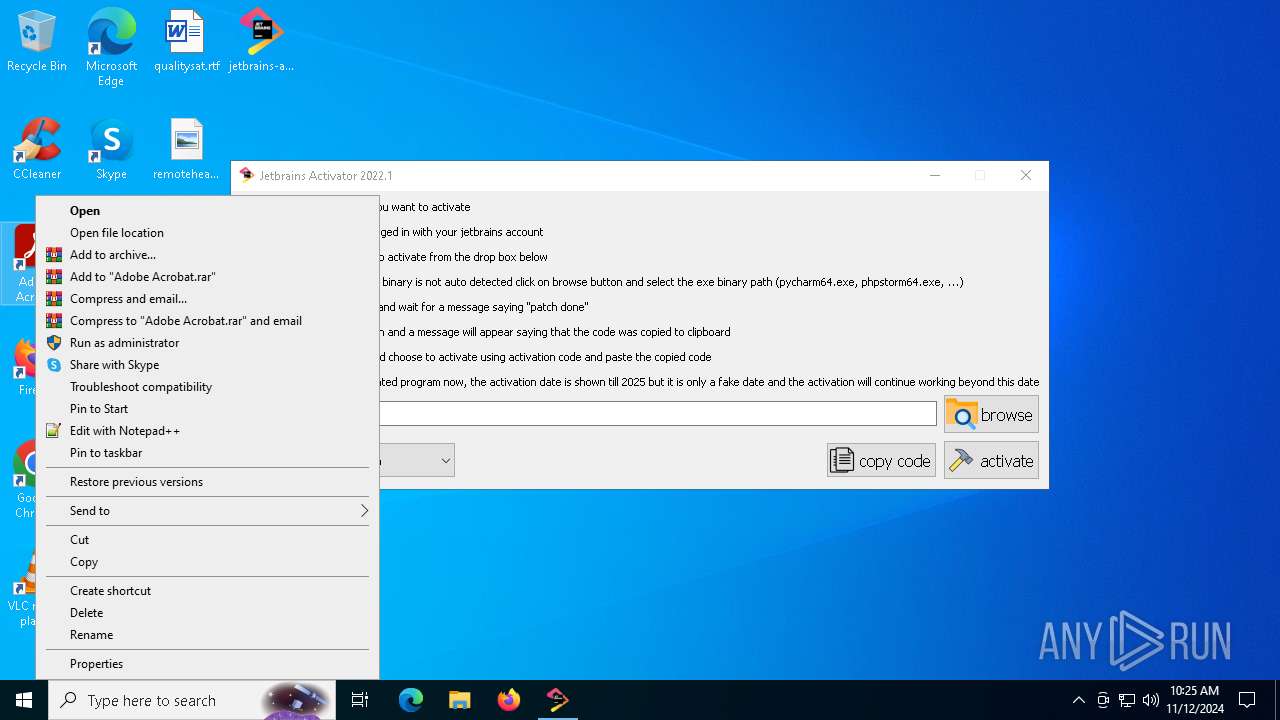
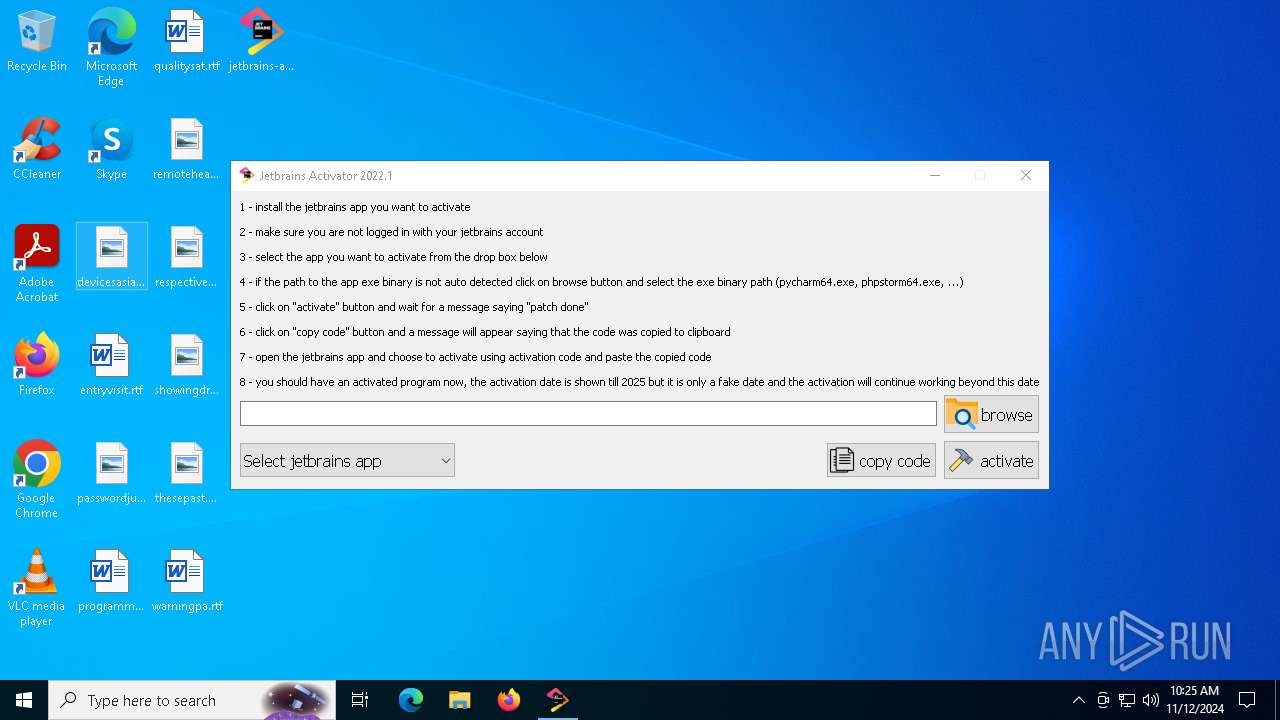
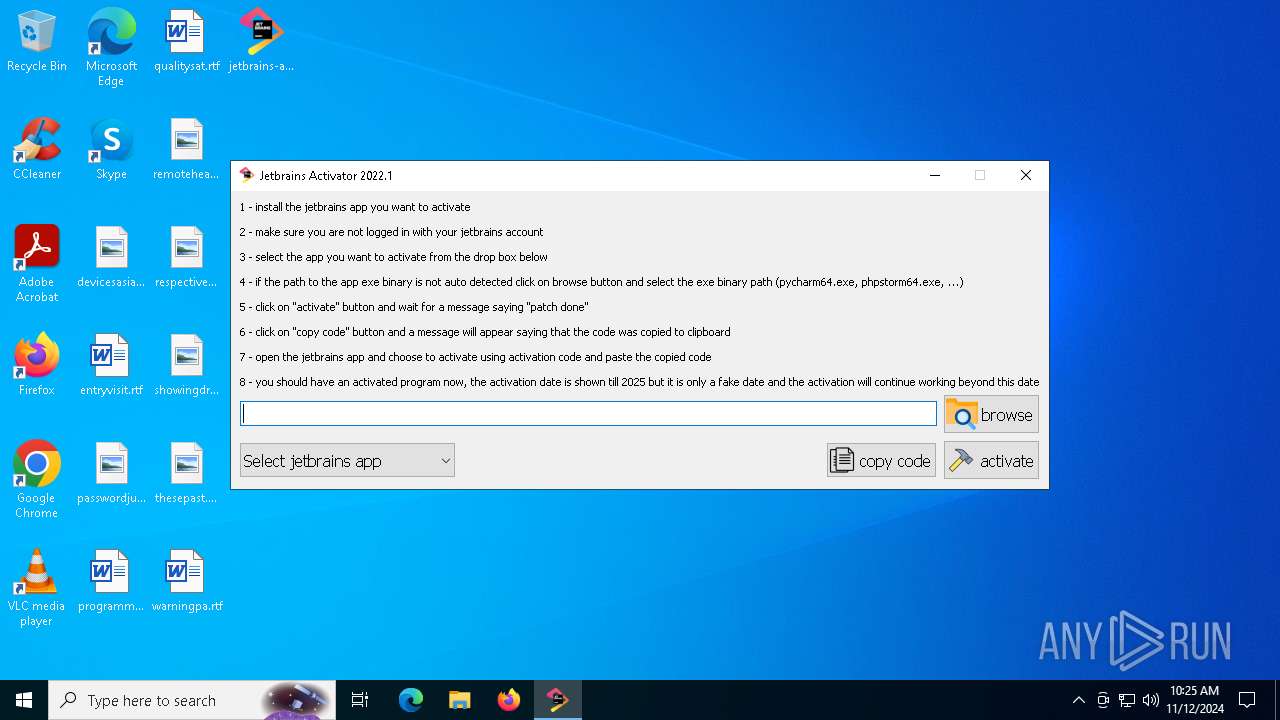
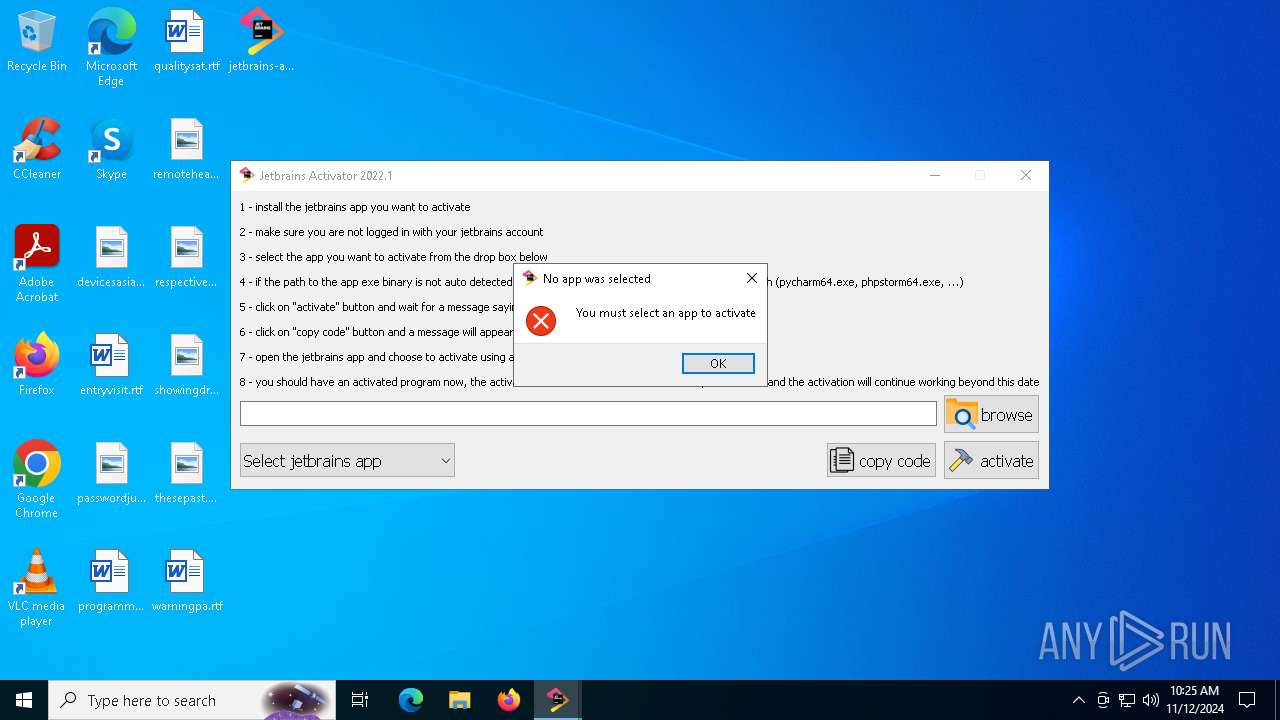
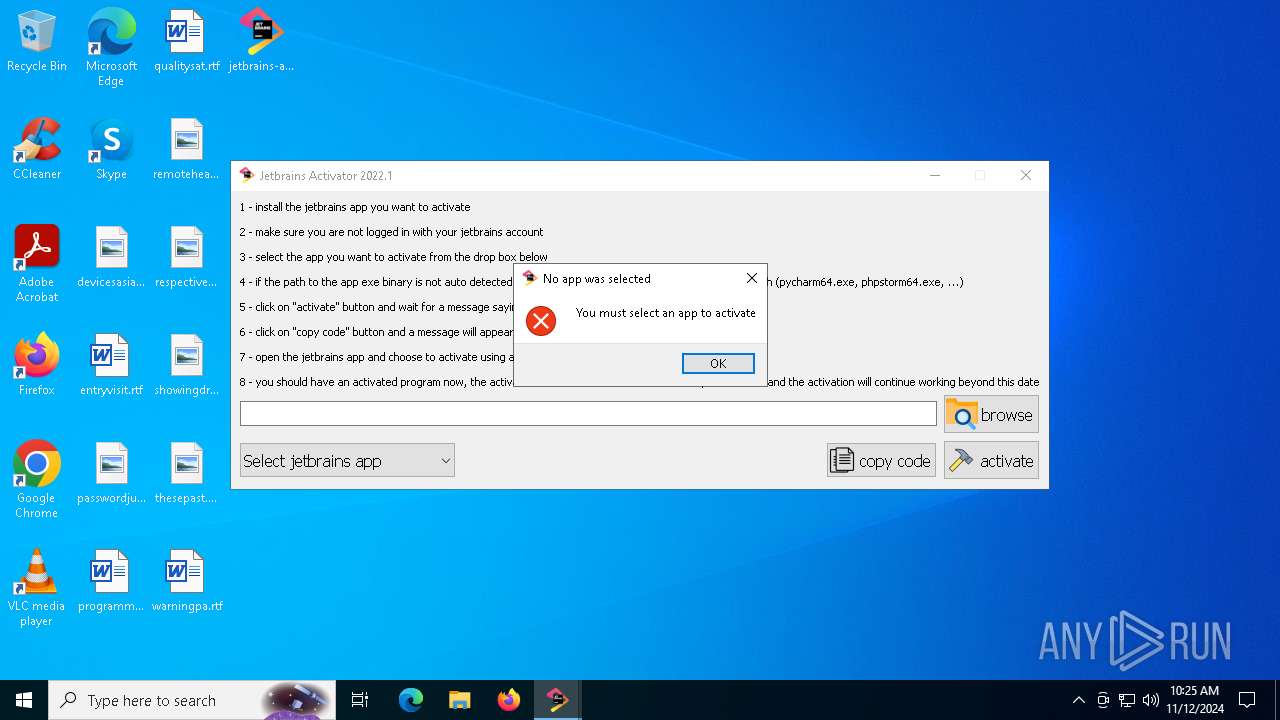
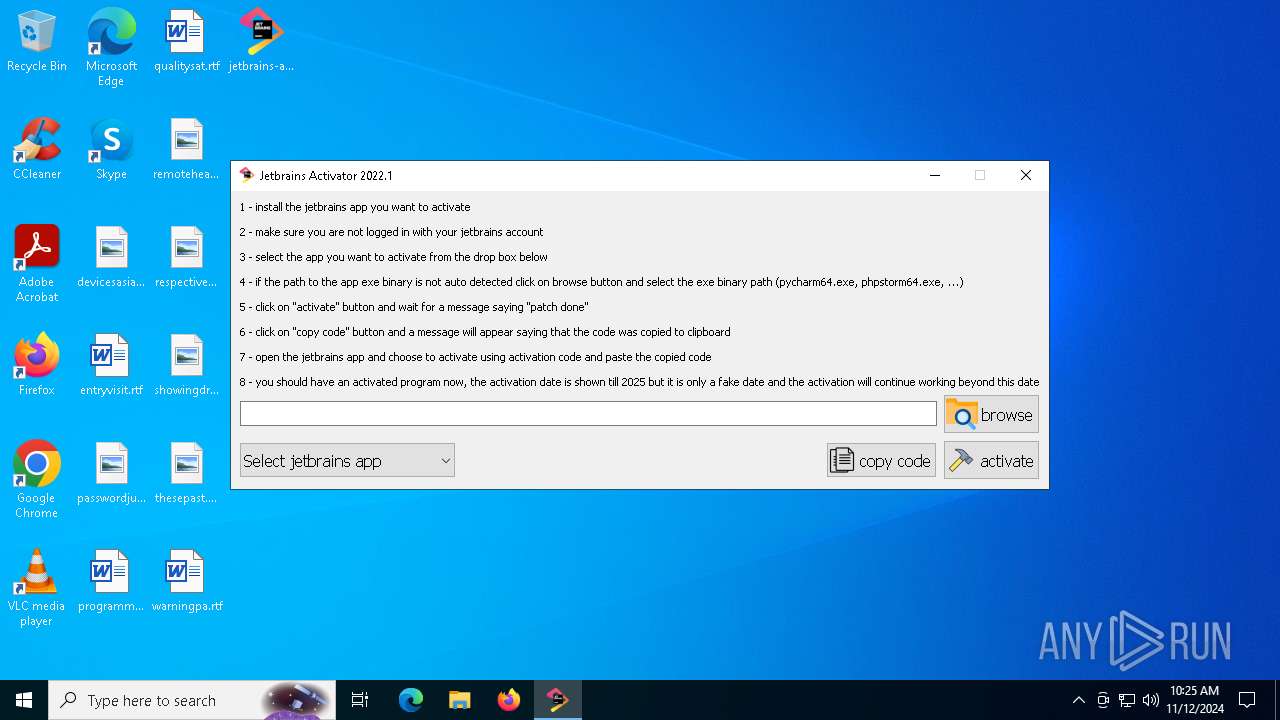
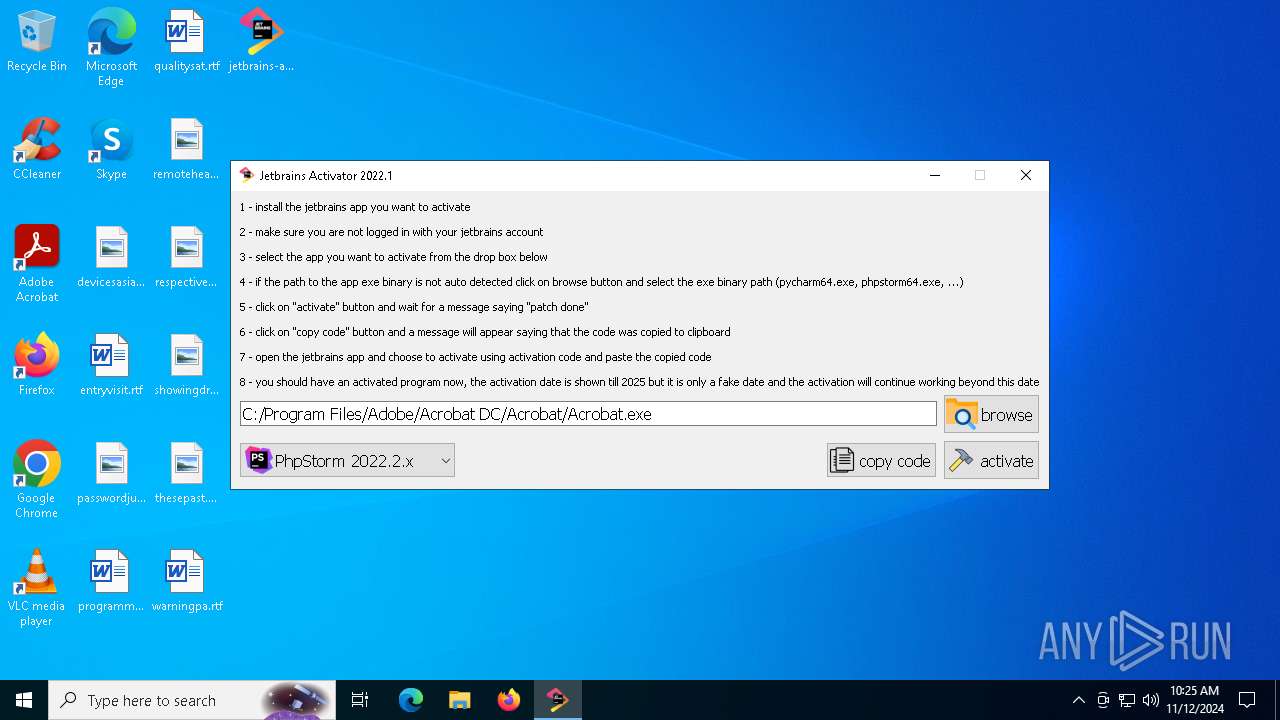
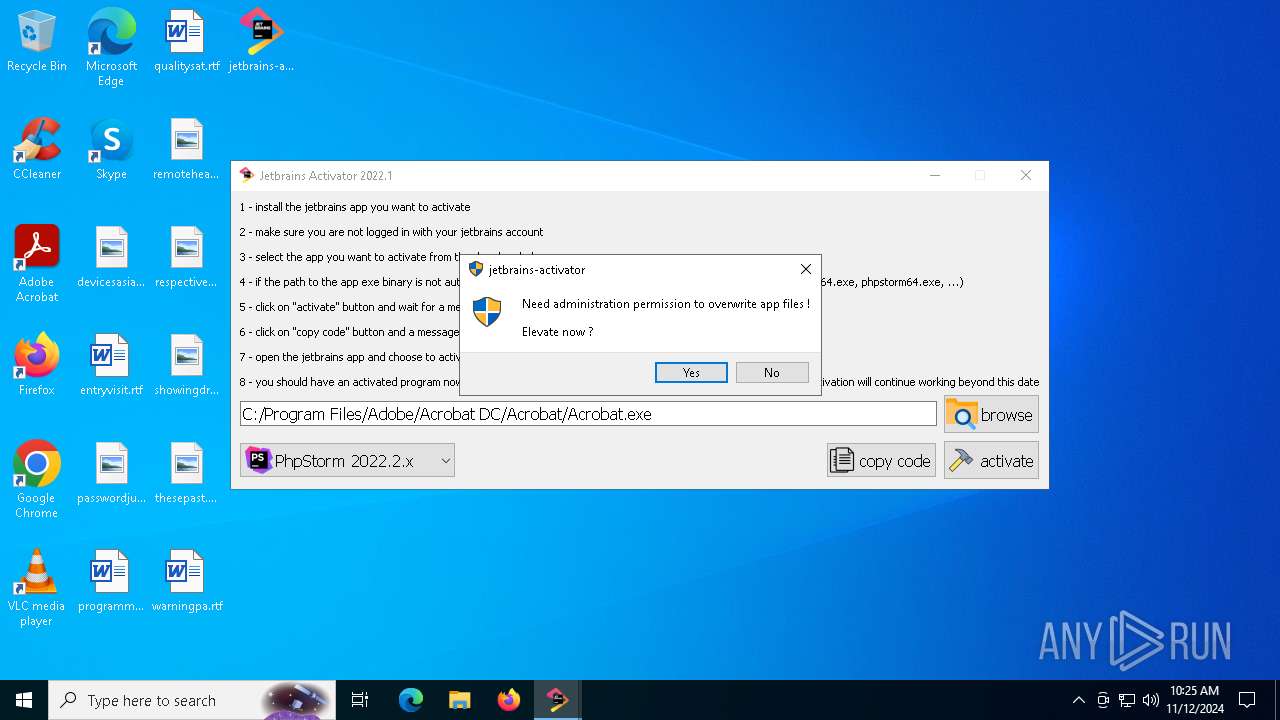
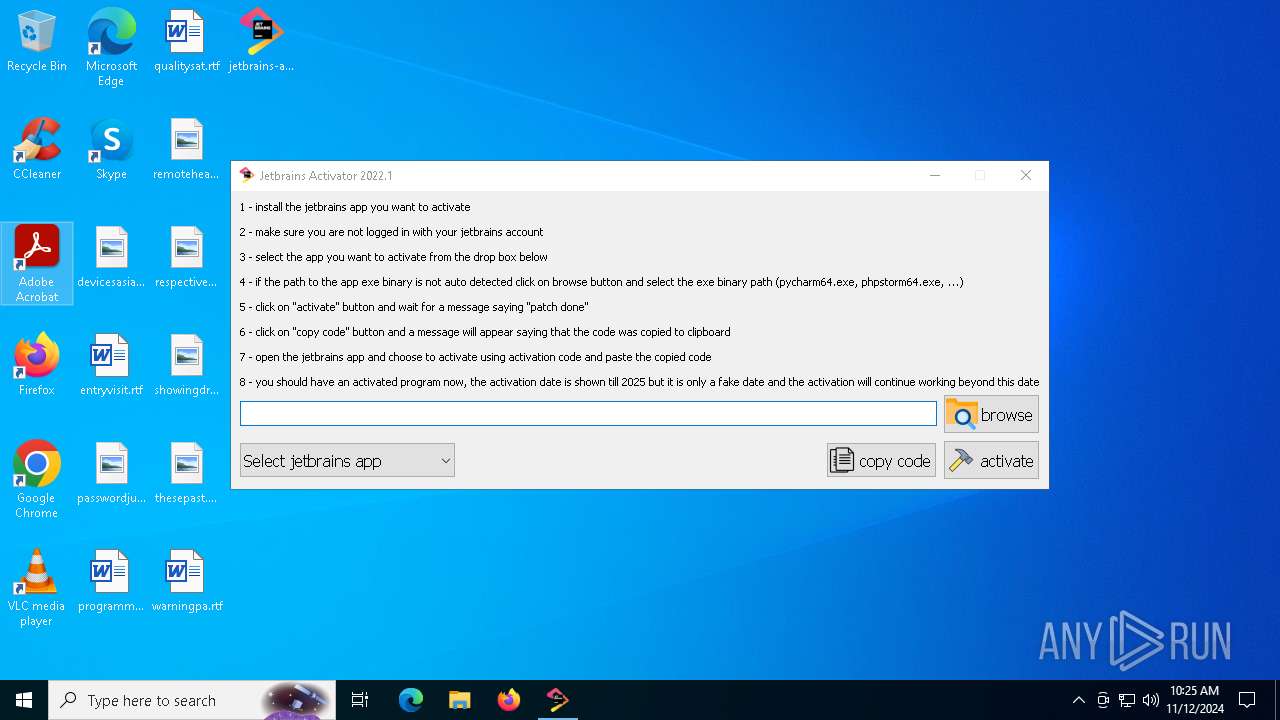
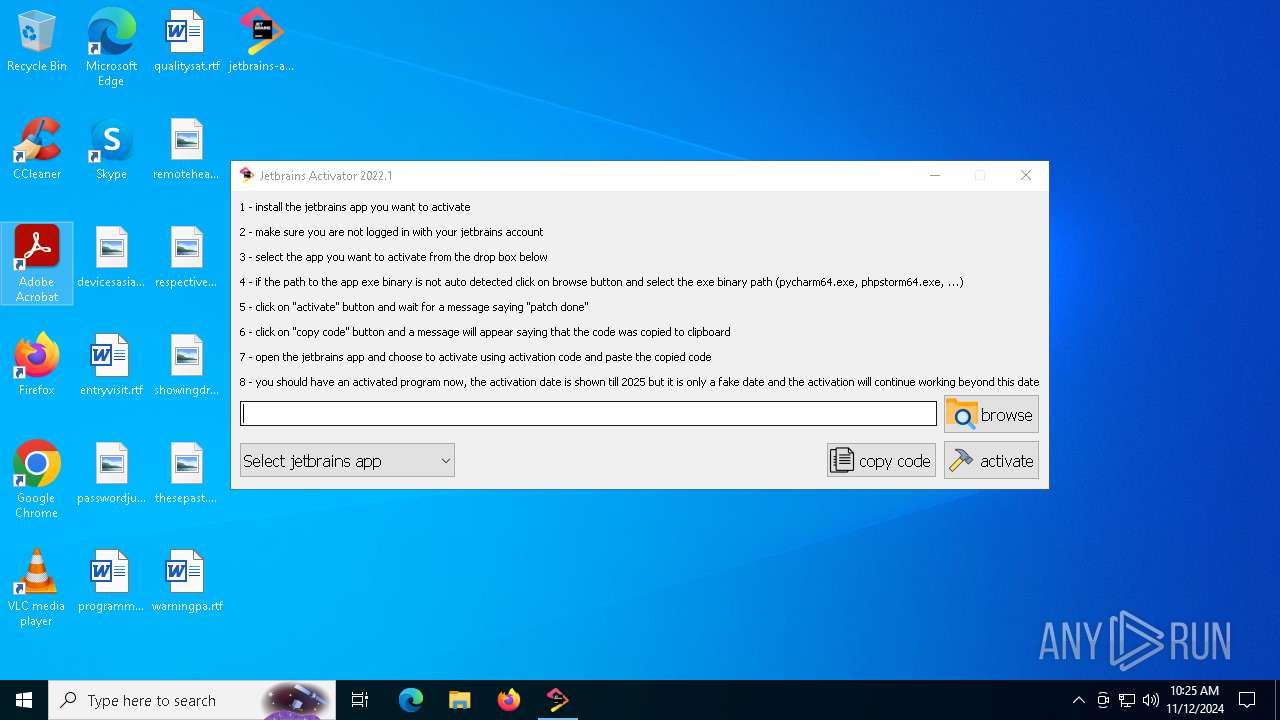
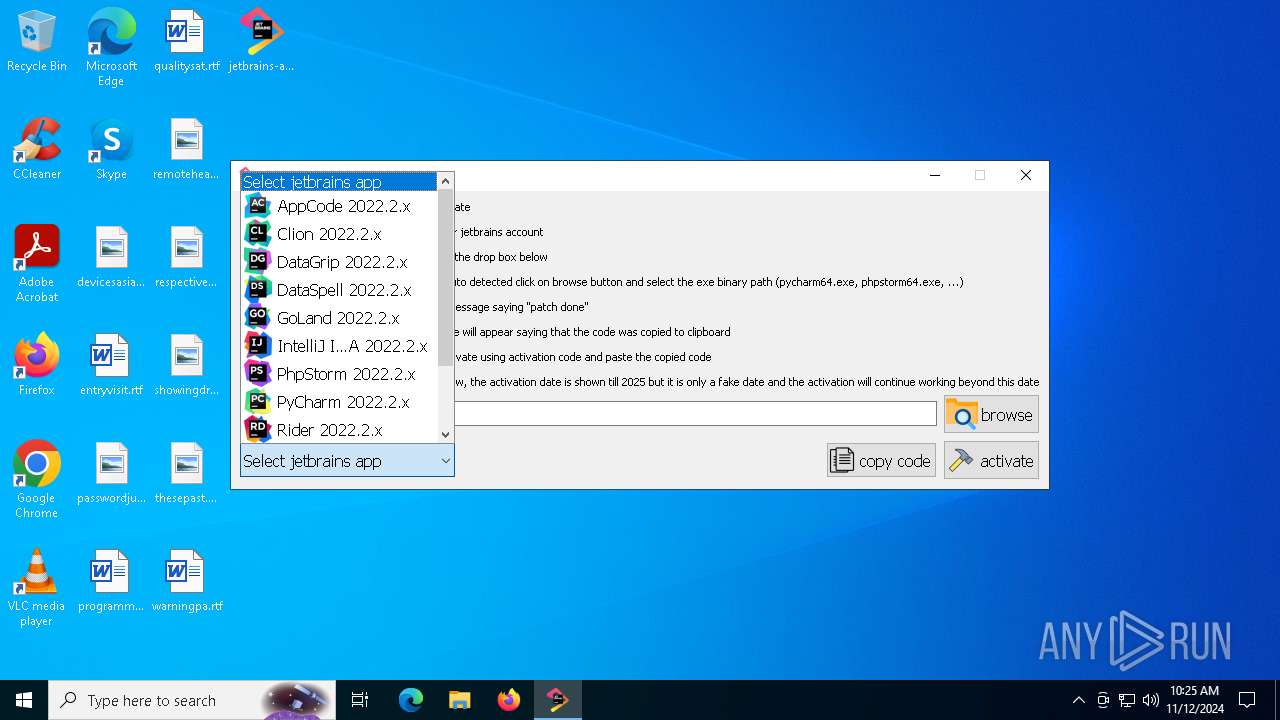
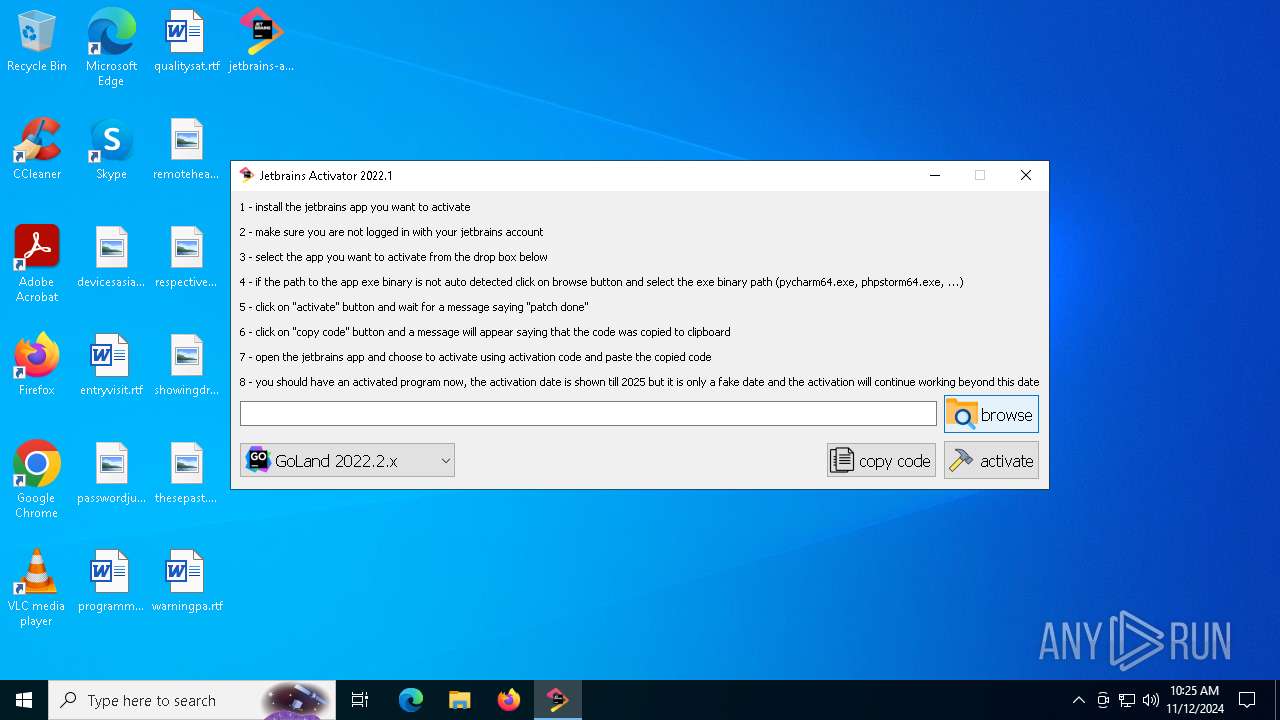
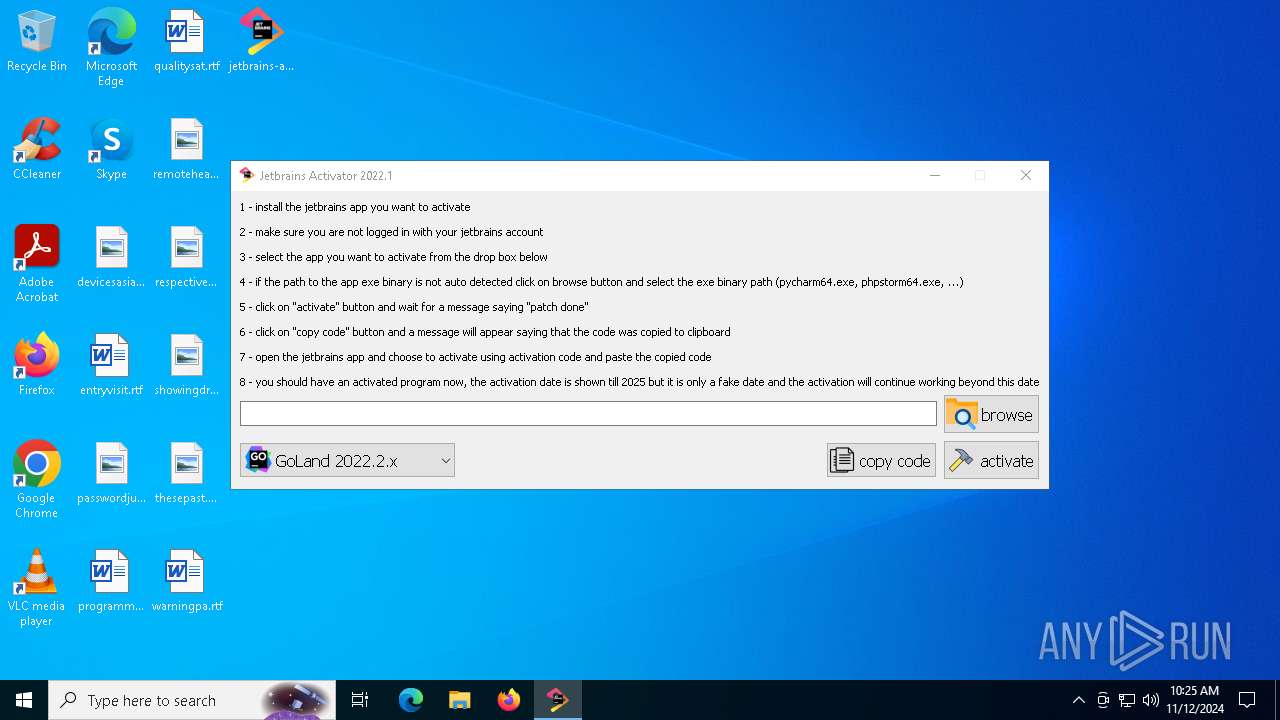
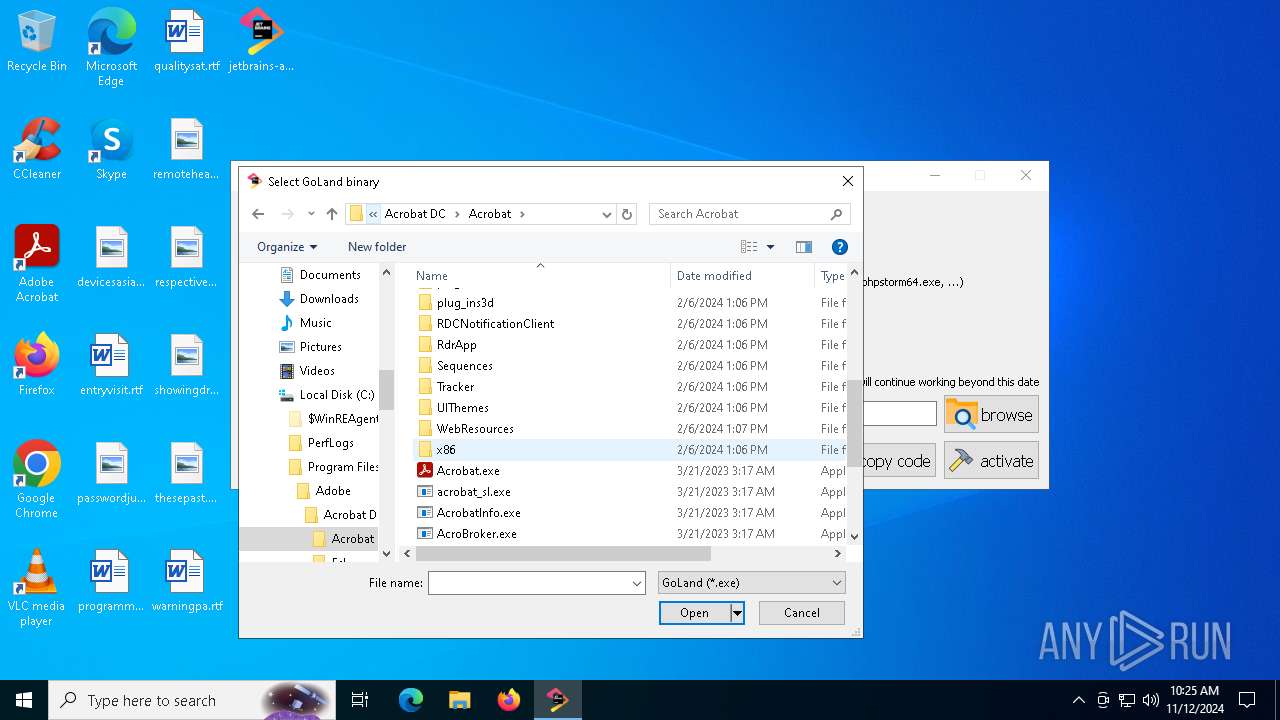
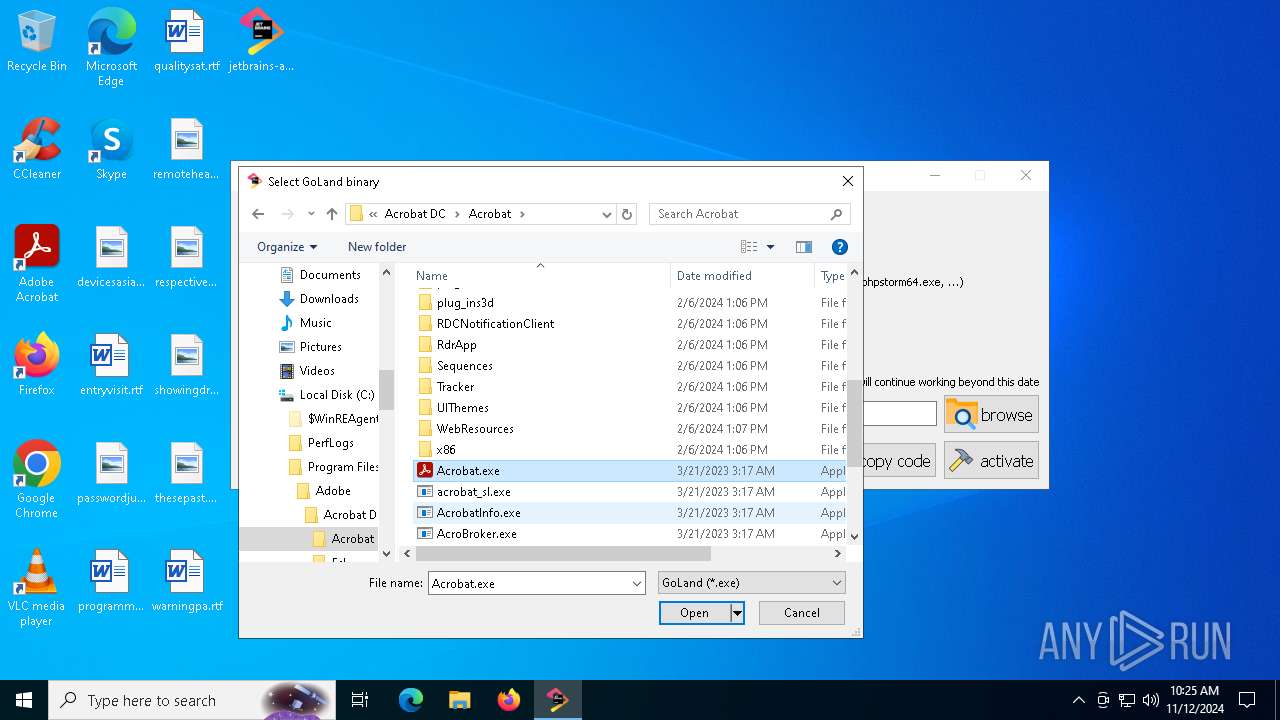
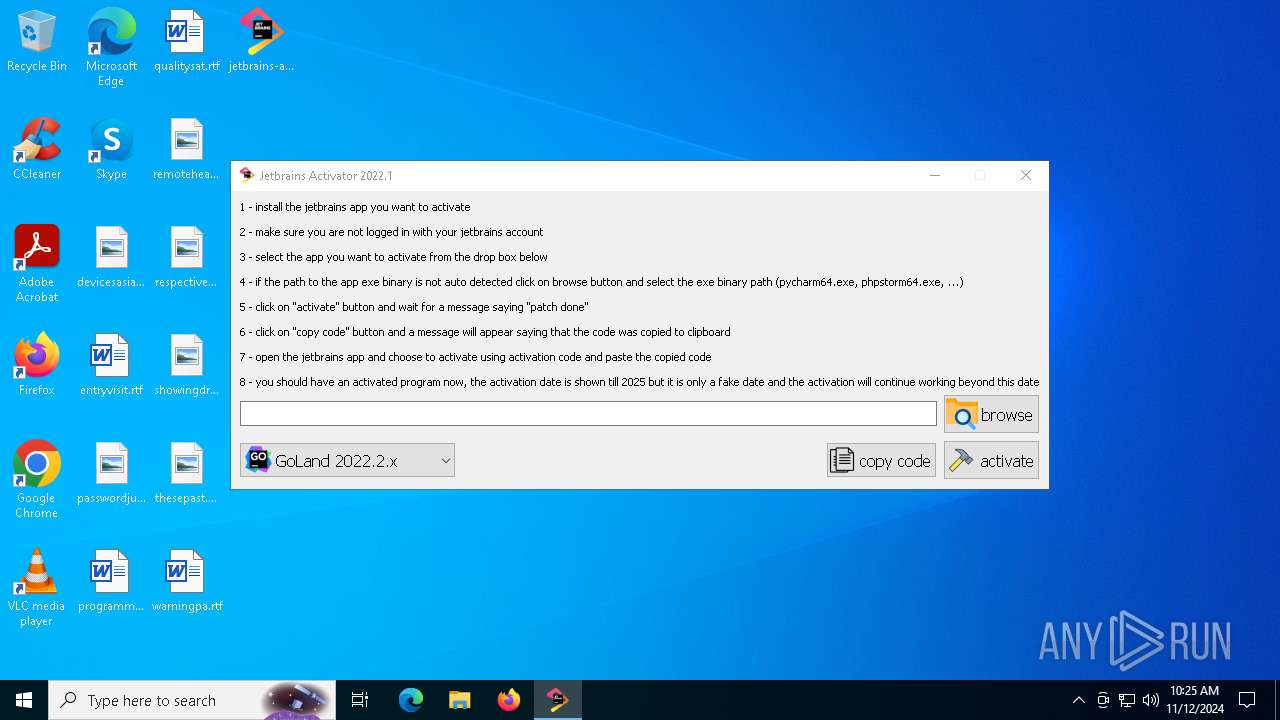
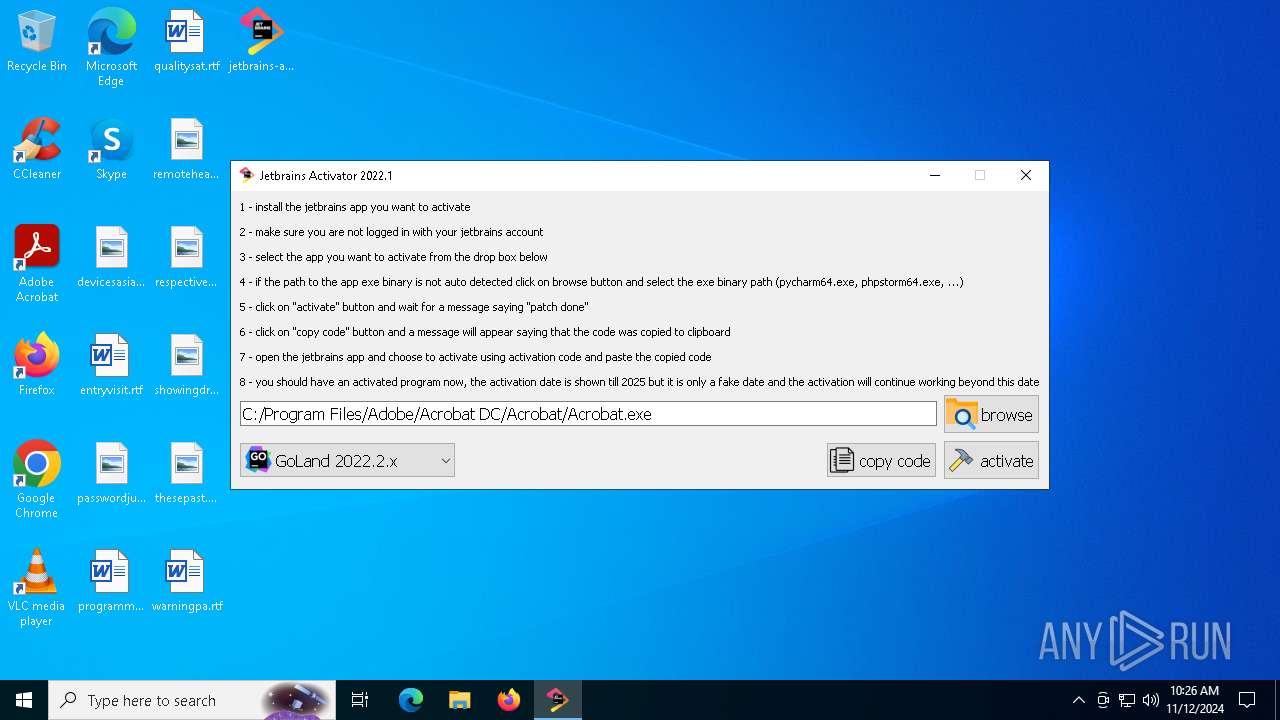
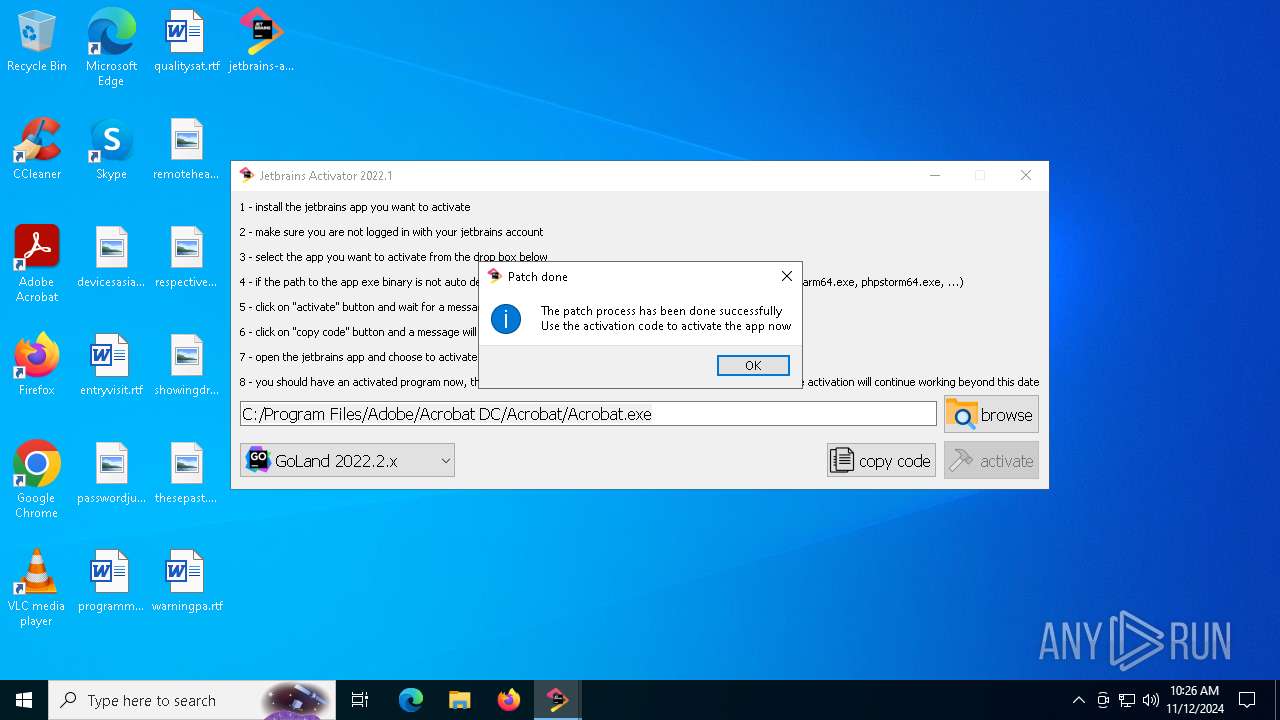
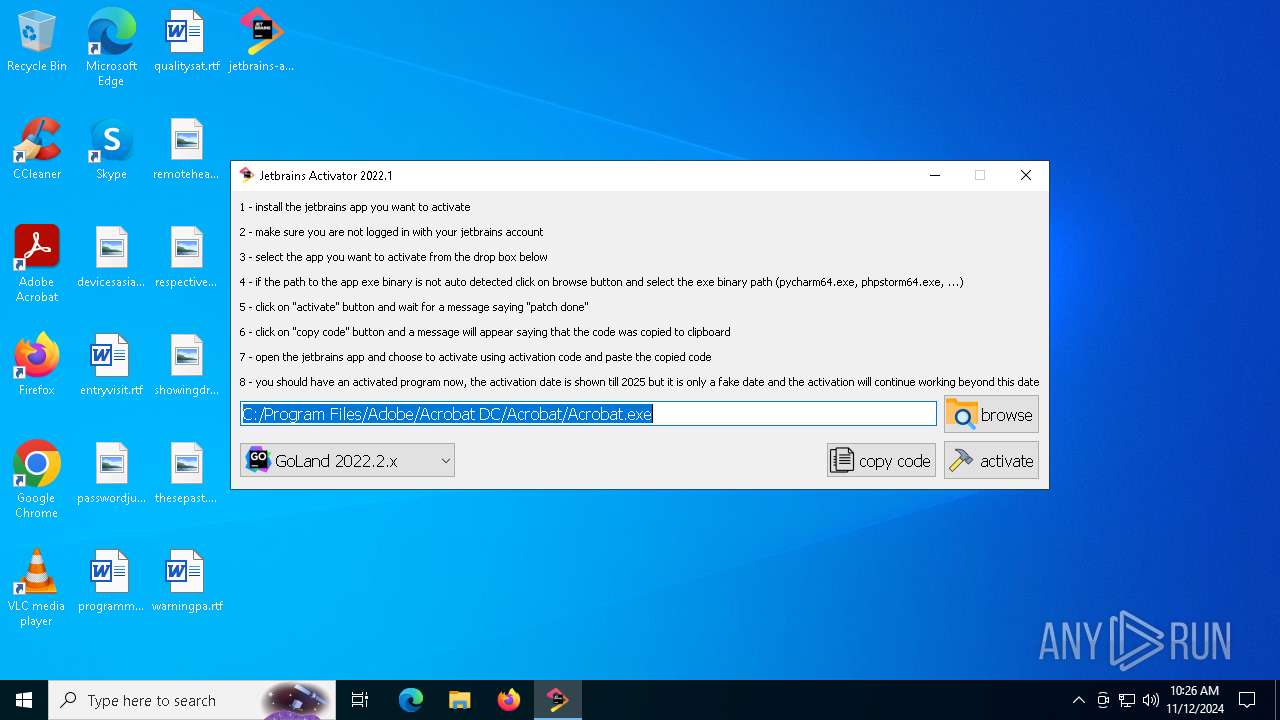
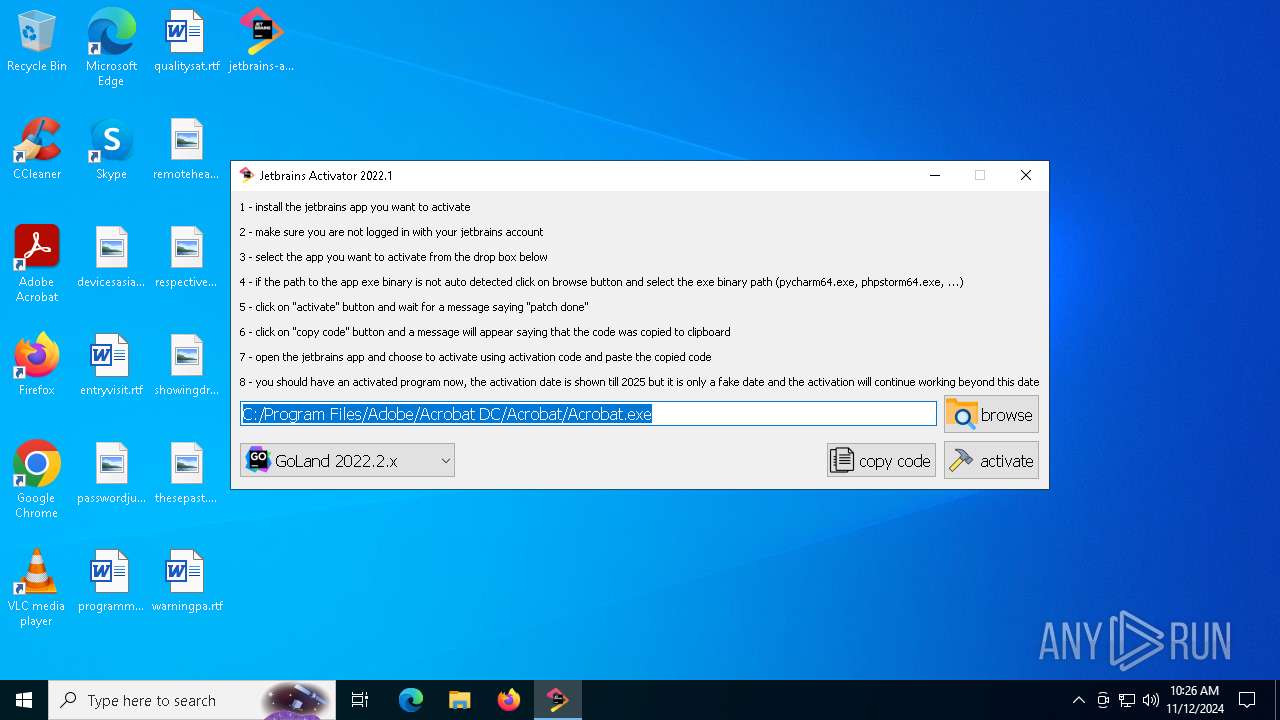
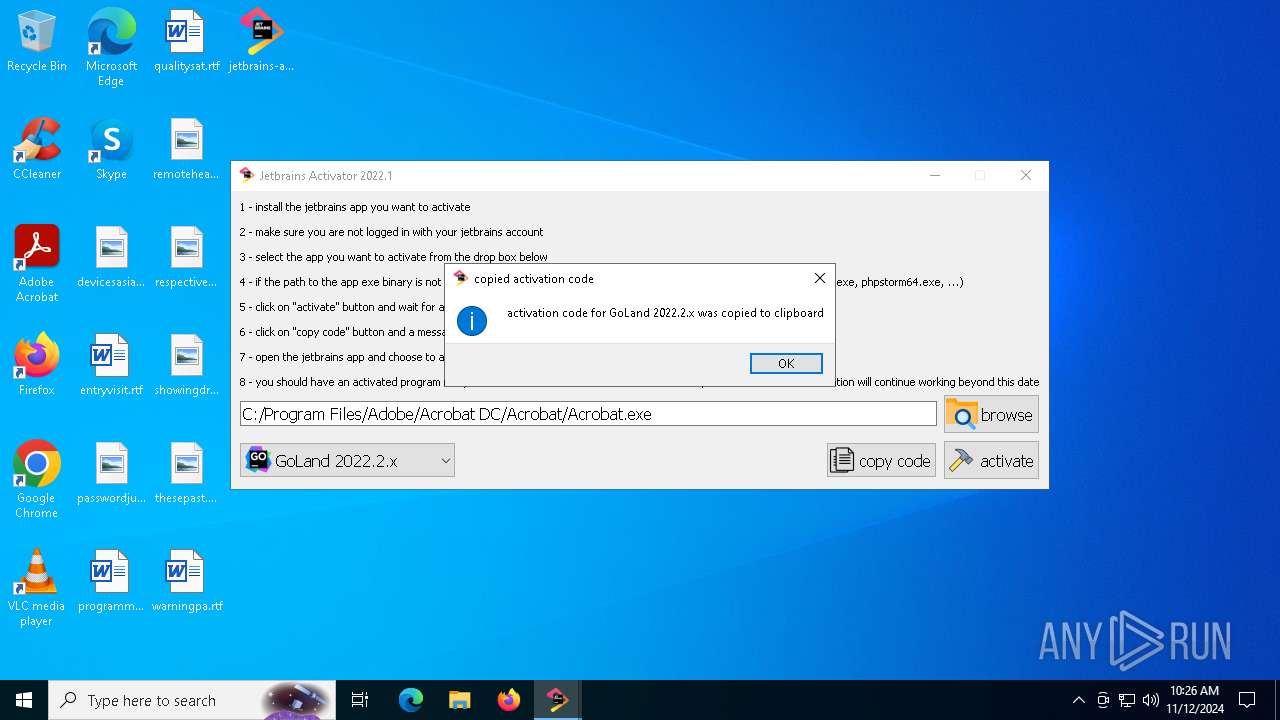
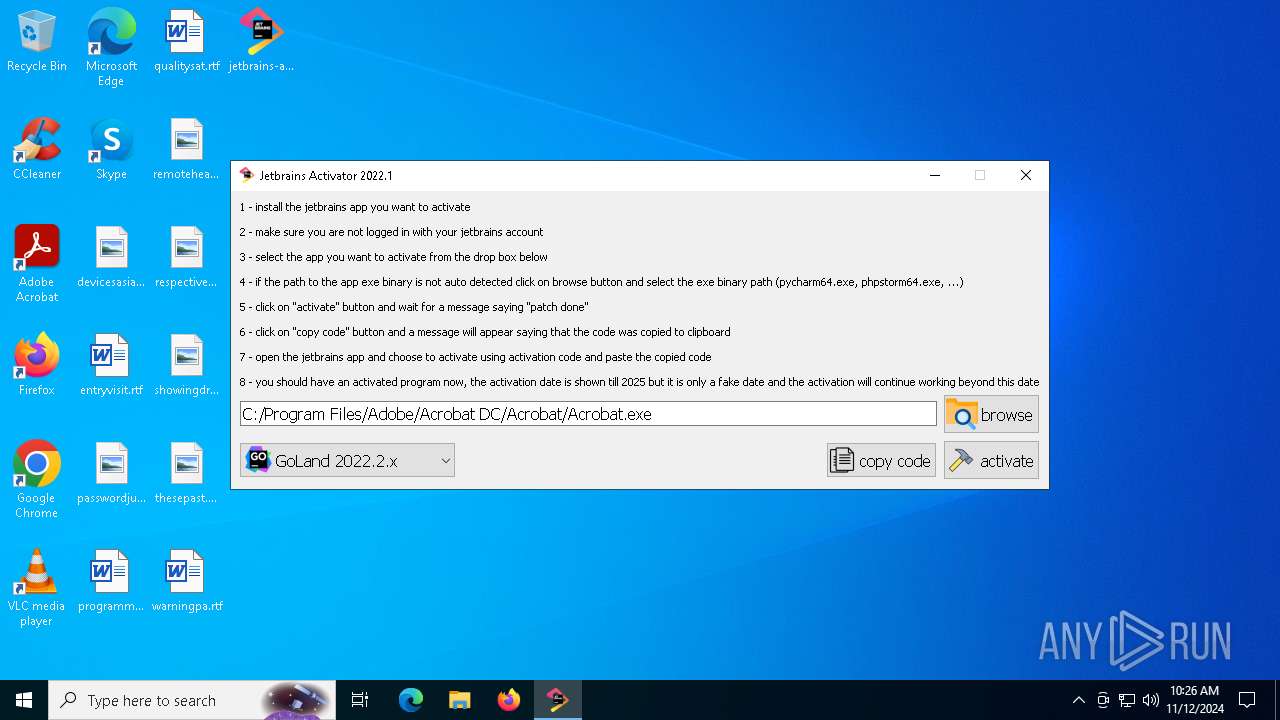
| File name: | jetbrains-activator.exe |
| Full analysis: | https://app.any.run/tasks/f32ddc14-66ab-414f-8bf0-ea1d9def2bb3 |
| Verdict: | Malicious activity |
| Analysis date: | November 12, 2024, 10:24:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | 9DFF2CDB371334619B15372AA3F6085C |
| SHA1: | EA651AF34BFE2052668E37BCD3F60696EBAFFA1C |
| SHA256: | 3E52C0B97F67287C212E5BC779B0E7DD843FB0DF2EF11B74E1891898D492782C |
| SSDEEP: | 98304:ScTE9EF5E3hzztBDbkGp2RIUR9gdK615JLeHmi+l4m08qqo0VBjLt3fFV4Ar2IIi:C+693MbDJIxny/h9CM/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- jetbrains-activator.exe (PID: 540)
Creates file in the systems drive root
- jetbrains-activator.exe (PID: 2576)
Executes as Windows Service
- AGSService.exe (PID: 1160)
Application launched itself
- jetbrains-activator.exe (PID: 2576)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 2956)
INFO
Manual execution by a user
- svchost.exe (PID: 2892)
- svchost.exe (PID: 2540)
- svchost.exe (PID: 2960)
- OfficeClickToRun.exe (PID: 2912)
- AGSService.exe (PID: 2932)
- svchost.exe (PID: 2560)
- svchost.exe (PID: 2840)
- svchost.exe (PID: 2920)
- svchost.exe (PID: 3044)
- svchost.exe (PID: 2968)
- spoolsv.exe (PID: 2584)
- svchost.exe (PID: 2444)
- svchost.exe (PID: 2568)
- svchost.exe (PID: 2708)
- svchost.exe (PID: 2348)
- svchost.exe (PID: 2644)
- svchost.exe (PID: 2792)
- svchost.exe (PID: 3320)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 3840)
- sppsvc.exe (PID: 4028)
- svchost.exe (PID: 3096)
- svchost.exe (PID: 3808)
- svchost.exe (PID: 5904)
- svchost.exe (PID: 5632)
- Acrobat.exe (PID: 4640)
- svchost.exe (PID: 3820)
- svchost.exe (PID: 4924)
- svchost.exe (PID: 4104)
- svchost.exe (PID: 4164)
- svchost.exe (PID: 4952)
- svchost.exe (PID: 3952)
- TrustedInstaller.exe (PID: 5092)
- svchost.exe (PID: 4844)
- svchost.exe (PID: 4732)
- svchost.exe (PID: 5760)
- svchost.exe (PID: 4672)
- svchost.exe (PID: 4312)
- svchost.exe (PID: 772)
- svchost.exe (PID: 5184)
- svchost.exe (PID: 6904)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 1980)
- svchost.exe (PID: 1180)
- svchost.exe (PID: 2404)
- svchost.exe (PID: 1772)
- uhssvc.exe (PID: 2592)
- svchost.exe (PID: 3032)
- Taskmgr.exe (PID: 4596)
- svchost.exe (PID: 6076)
- svchost.exe (PID: 3120)
- Taskmgr.exe (PID: 1584)
- svchost.exe (PID: 4492)
- svchost.exe (PID: 5764)
- svchost.exe (PID: 6864)
Reads the computer name
- jetbrains-activator.exe (PID: 2576)
Checks supported languages
- jetbrains-activator.exe (PID: 2576)
Sends debugging messages
- Acrobat.exe (PID: 7084)
Application launched itself
- Acrobat.exe (PID: 4640)
- AcroCEF.exe (PID: 6852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:02:01 22:17:42+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 9542656 |
| InitializedDataSize: | 9126400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8d77e8 |
| OSVersion: | 6 |
| ImageVersion: | 11 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.0.49893 |
| ProductVersionNumber: | 11.0.0.49893 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 11.0.0.49893 |
| LegalCopyright: | - |
| OriginalFileName: | jetbrains-activator.exe |
| ProductName: | jetbrains-activator |
| ProductVersion: | 11.0.0.49893 |
Total processes
308
Monitored processes
77
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Users\admin\Desktop\jetbrains-activator.exe" "C:\Users\admin\Desktop\jetbrains-activator.exe" | C:\Users\admin\Desktop\jetbrains-activator.exe | jetbrains-activator.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 11.0.0.49893 Modules
| |||||||||||||||
| 760 | consent.exe 6864 316 00000236E4428CC0 | C:\Windows\System32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 772 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s WpnUserService | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | "C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe" | C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 4294967295 Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s StorSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1608 --field-trial-handle=1624,i,1501462349425259782,7362436772716291313,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1584 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1772 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s BITS | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1980 | C:\WINDOWS\system32\svchost.exe -k LocalServiceAndNoImpersonation -p -s SSDPSRV | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 614
Read events
66 903
Write events
612
Delete events
99
Modification events
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 96 | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 000000000100000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (2576) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
Executable files
7
Suspicious files
181
Text files
28
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2960 | svchost.exe | C:\Windows\System32\sru\SRUDB.dat | — | |
MD5:— | SHA256:— | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\ja-netfilter.jar | java | |
MD5:2FA1B1364515DCE93EB67C423B570DEB | SHA256:3ACC4E9D91793F6909458A4761B75B6DA45C8868E75DCA33C9FEC63659202995 | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\dns.jar | java | |
MD5:4F3C516C1704A5569725246D57DD1AE7 | SHA256:D1150B1831B112B93D74A34A10CE6C11606E0D2255D532C29F91F1D92B40A552 | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\power.jar | java | |
MD5:D8711B73BC0507DBDC841B098AF99787 | SHA256:7819E5B968CE5EA2E638E53D84089D35E89E9EA3088F18F8DBF6DD38D14AB25A | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\hideme.jar | java | |
MD5:CDAB6A30B0949A741F13935F5483C303 | SHA256:FA14C735AB9FED3F3A5DF0DC78A5D38AE0A146099DDC858197E9F528BD996C40 | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\url.jar | java | |
MD5:6B181E5B8255DB4CD9BEB1C6AF5F420E | SHA256:CE5A83AEE31153CCA30274AC94467B316EDEA8CB28ACF72F52F5A72D455B1B43 | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\config-jetbrains\power.conf | text | |
MD5:25E529ACCB85415C8C2B40FCE1AB65F5 | SHA256:05C70700CB0A3E8E7C596205CEBE7284B2F7FBDF5F6BEEB4424730A753239701 | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\config-jetbrains\dns.conf | text | |
MD5:0C730E2E849916568D7F519306777A95 | SHA256:B9BE9C700786B411395A66DEF0B259670074C32BCED59B33BE2DDD486ABCBE06 | |||
| 540 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\native.jar | java | |
MD5:D53081E7676F669061695827209B0FBD | SHA256:88E419764B31134E74E4A968015F6F80DA497EEFCD4AEFF77D7C2CE57CB5EFCD | |||
| 1208 | svchost.exe | C:\Users\admin\AppData\Local\ConnectedDevicesPlatform\CDPGlobalSettings.cdp | text | |
MD5:1611F17FF81F9C9BC5C9F1D9A6B4F483 | SHA256:7D131594BD87C139CBFF9BE8627FCFFA915EC02CC3422551FE7911A2045CA1EE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
88
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3572 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4640 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7044 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6664 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4952 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7044 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2660 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.204.143:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6384 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6384 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
780 | svchost.exe | 23.218.210.69:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |