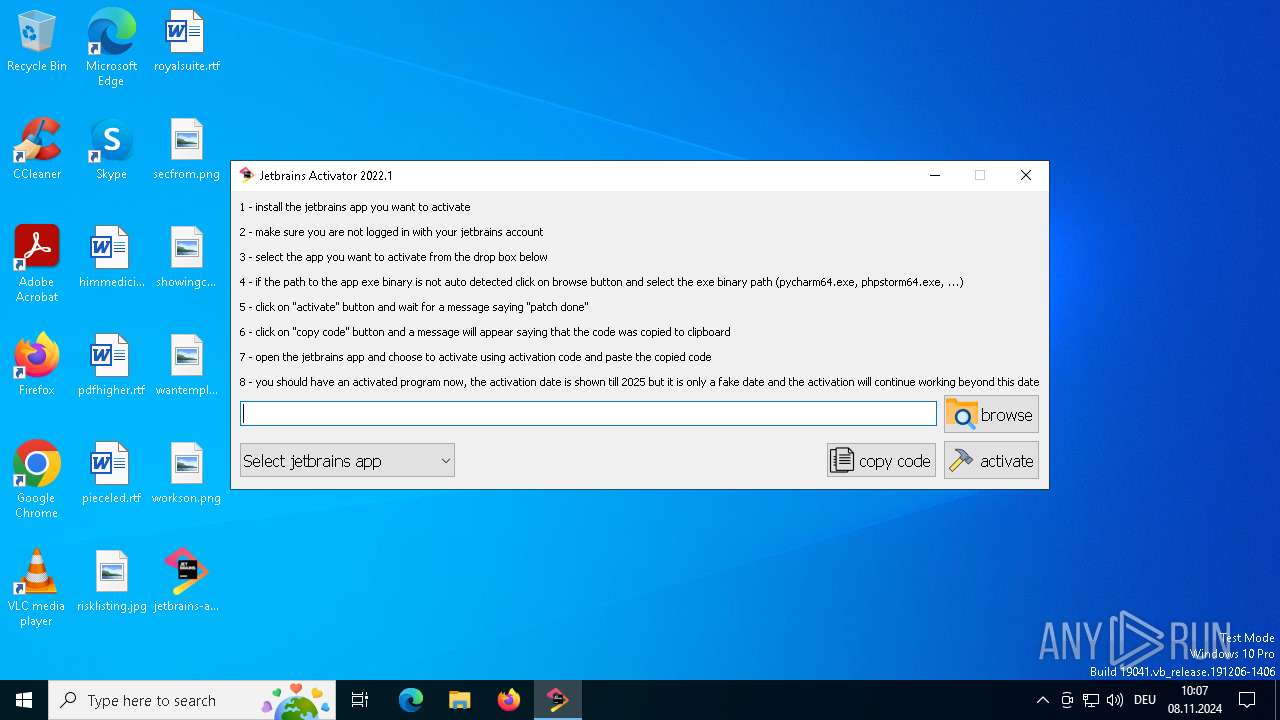
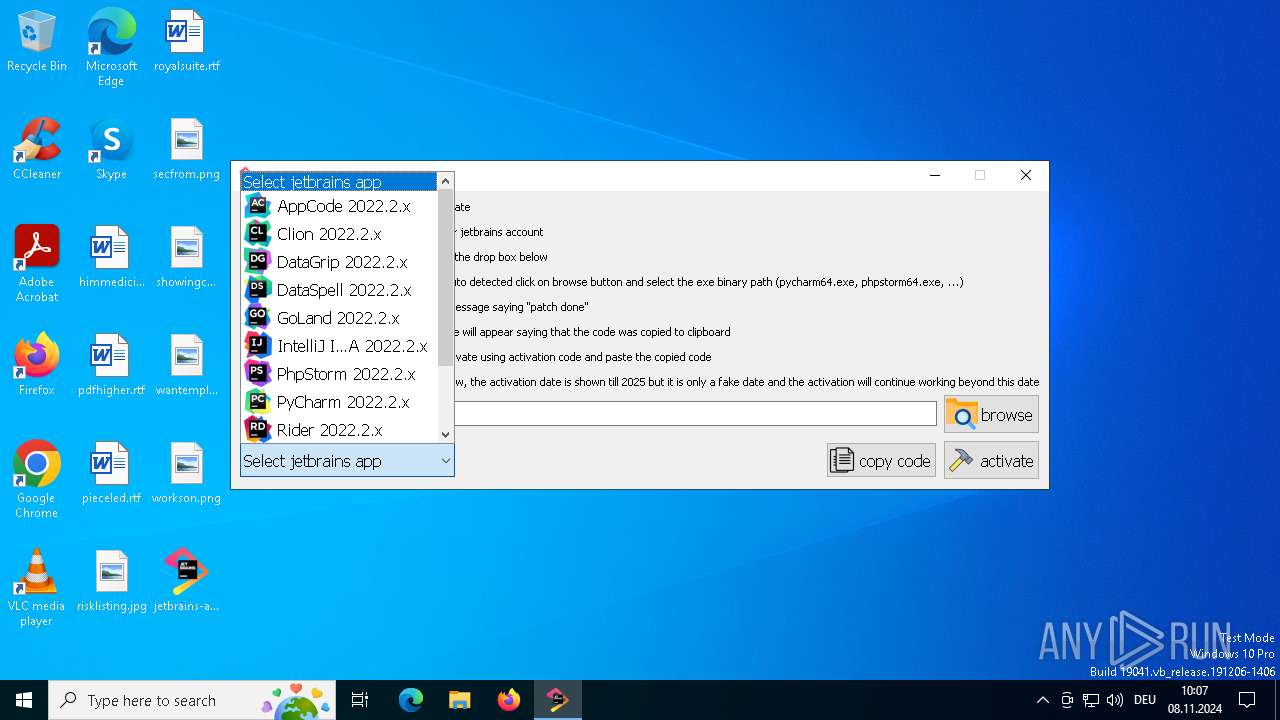
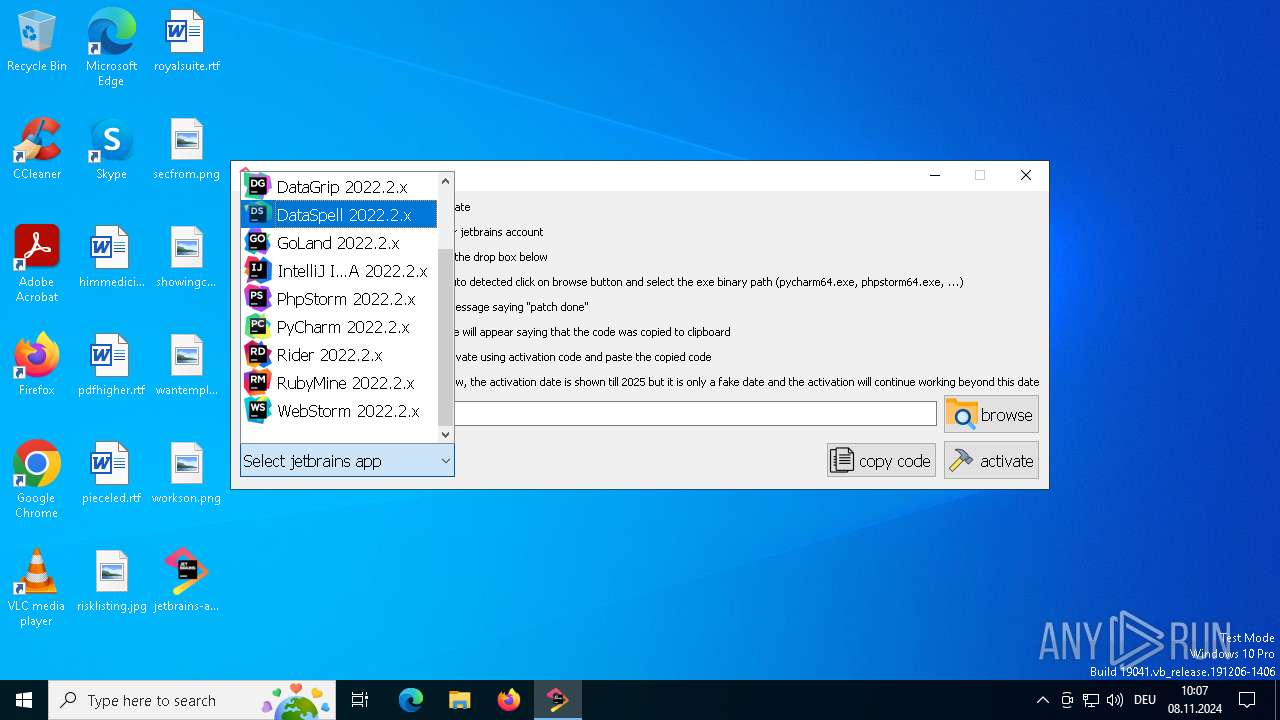
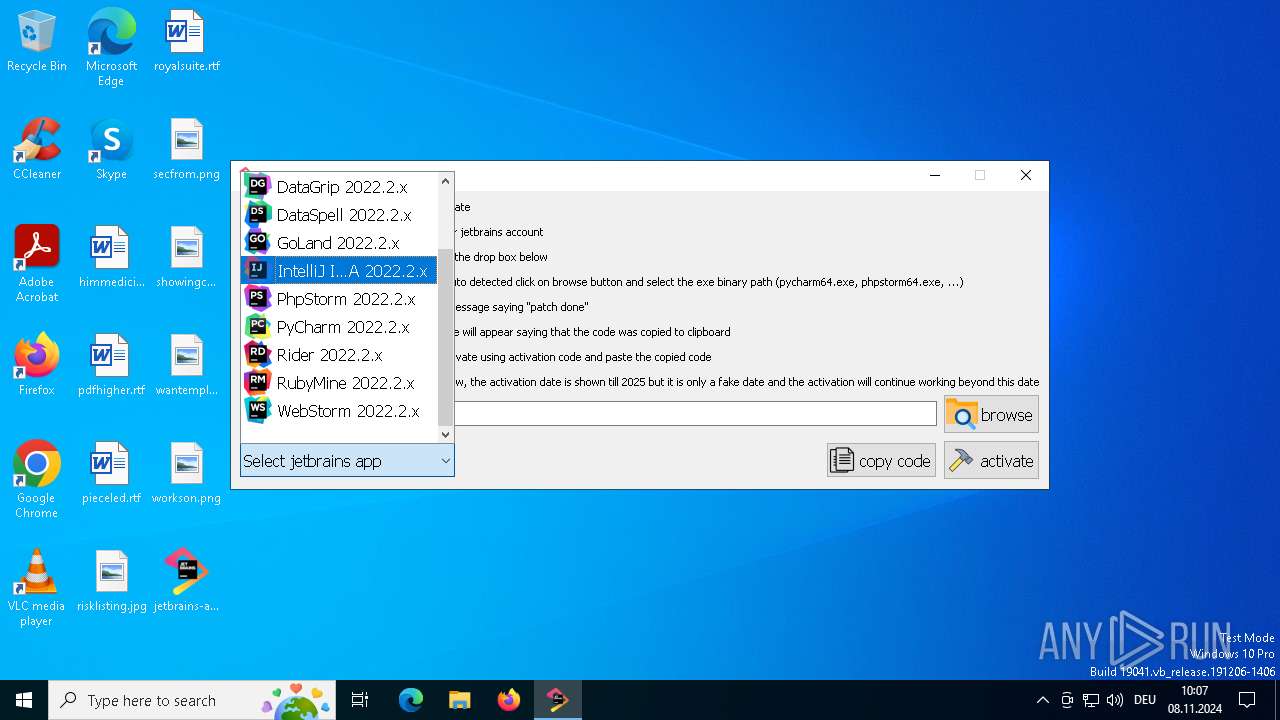
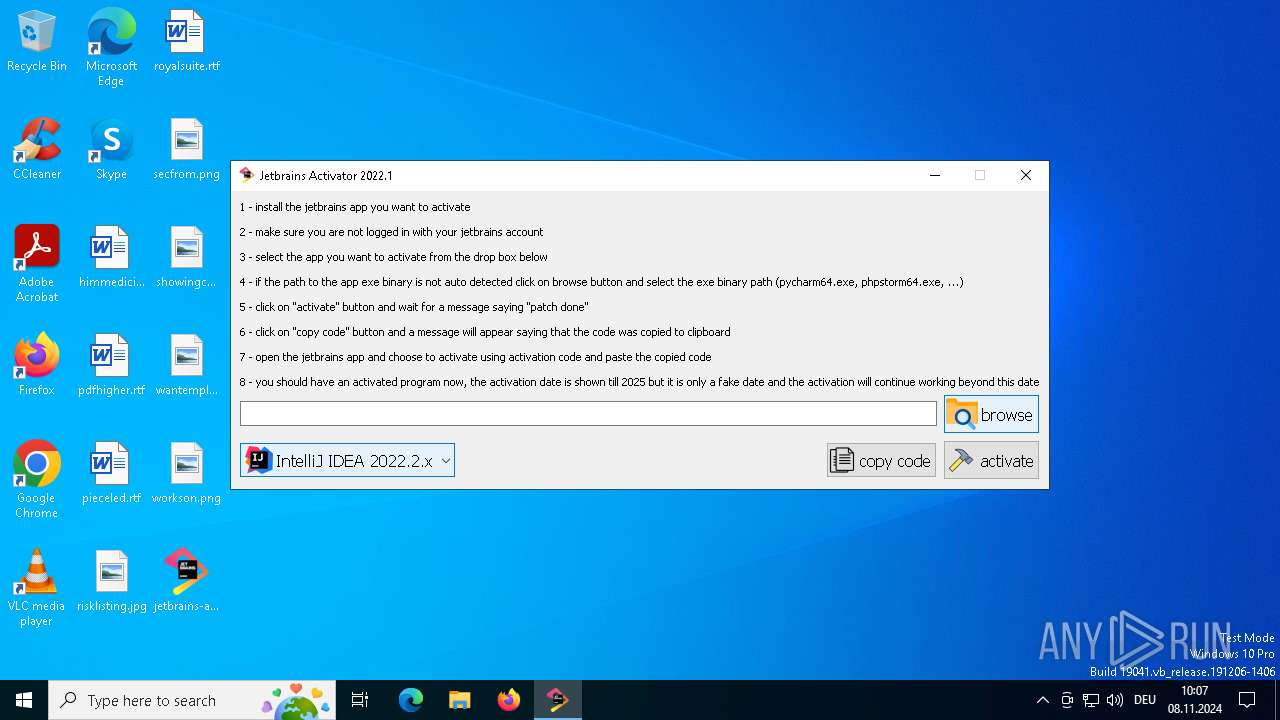
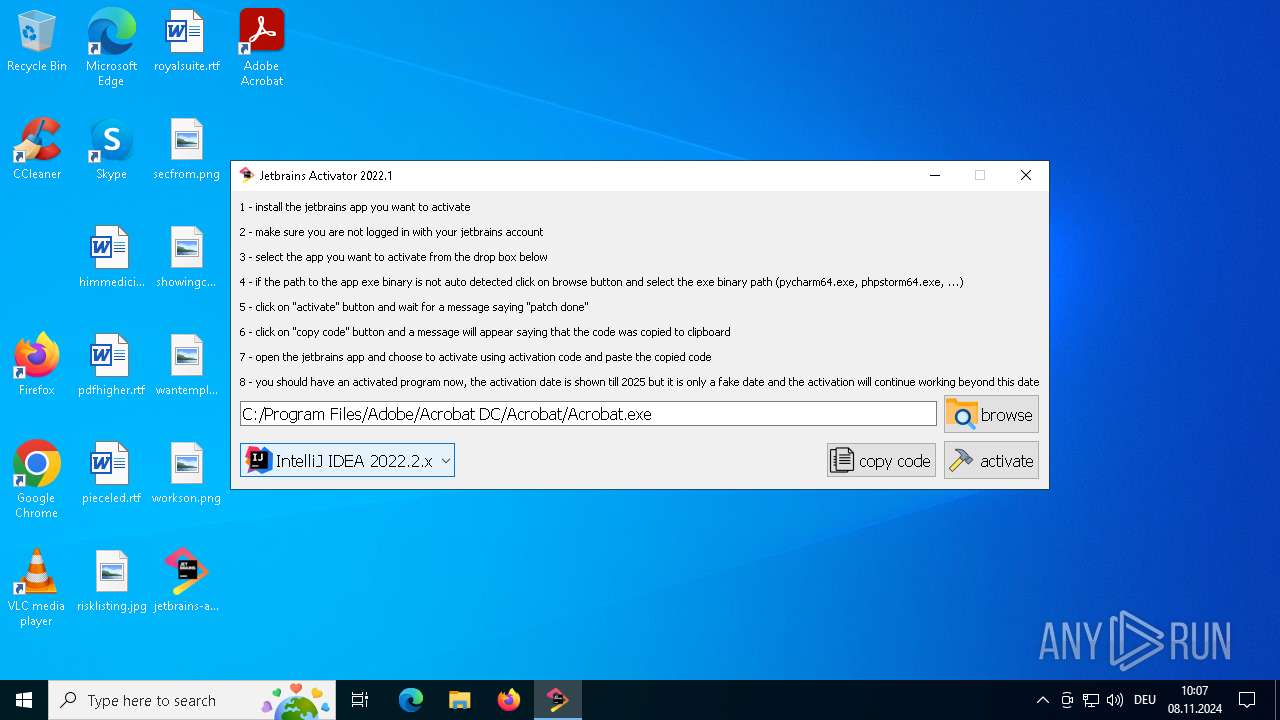
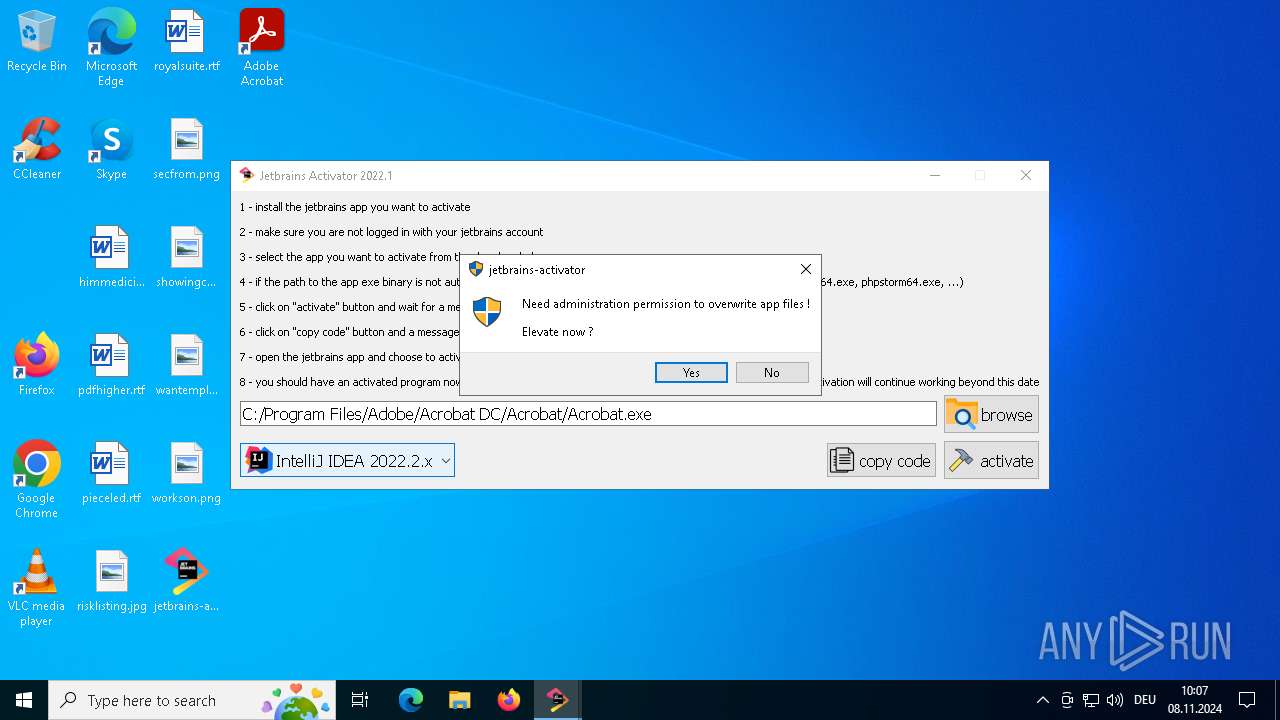
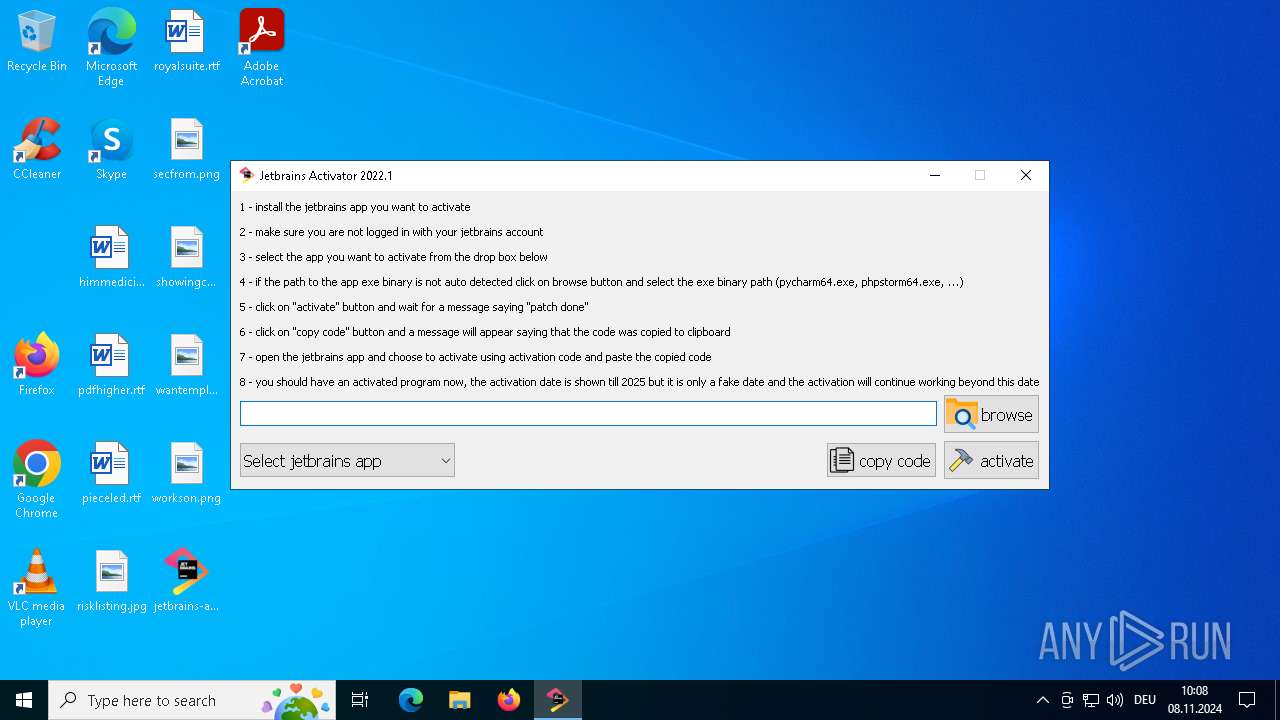
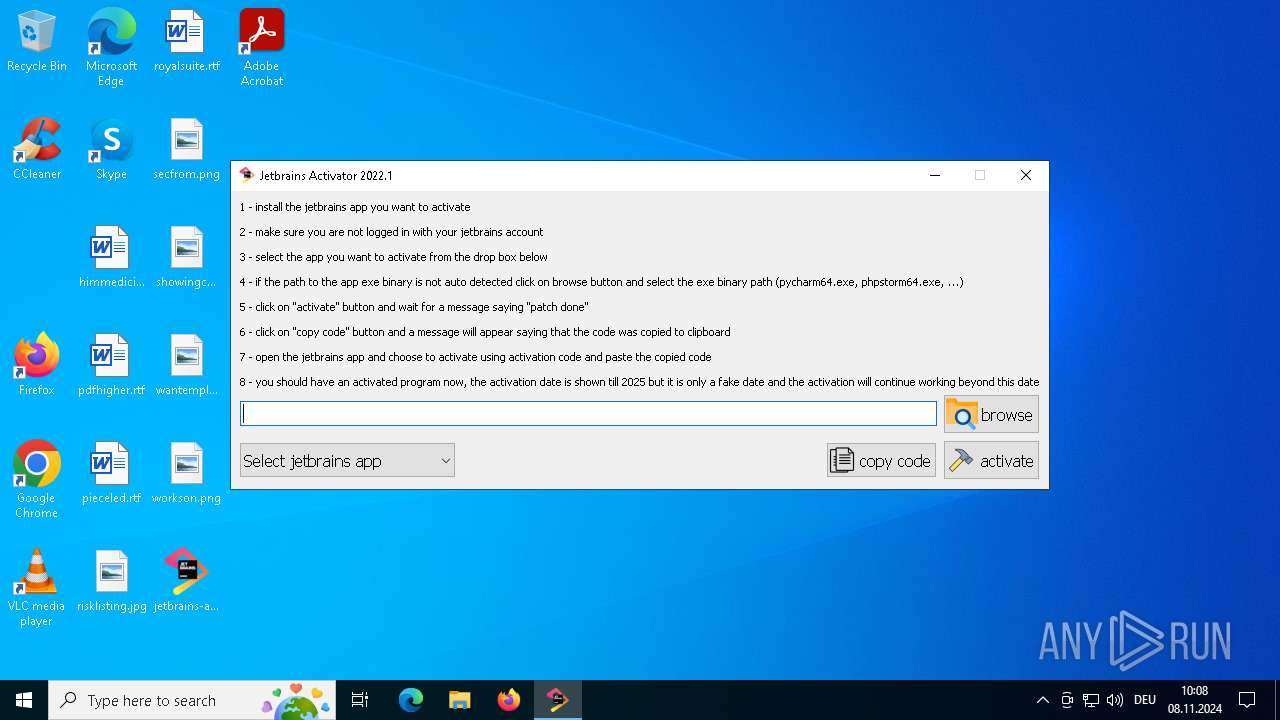
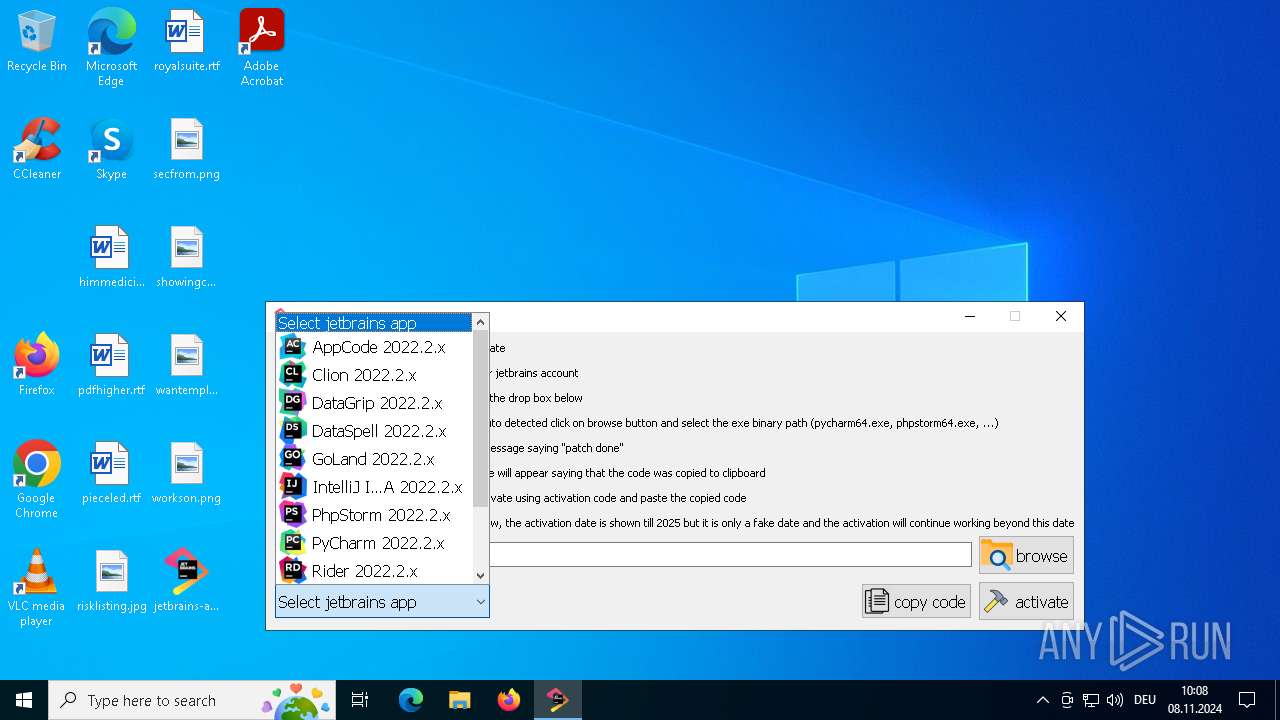
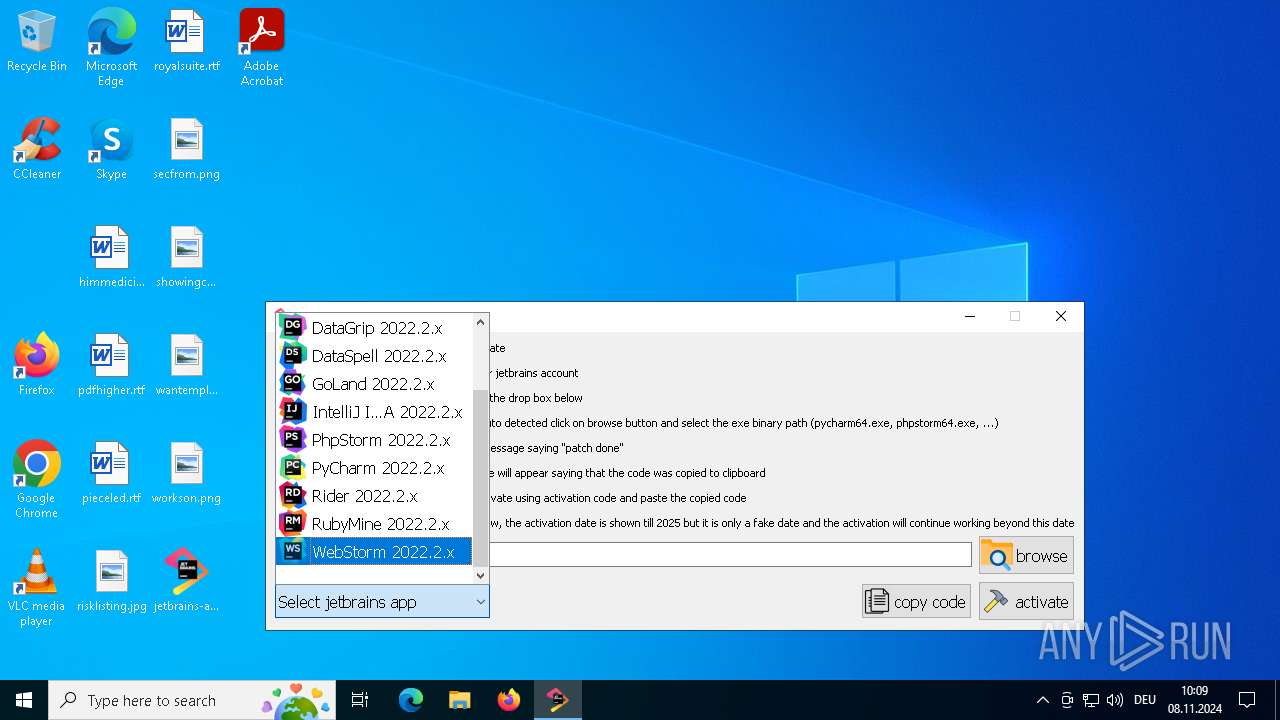
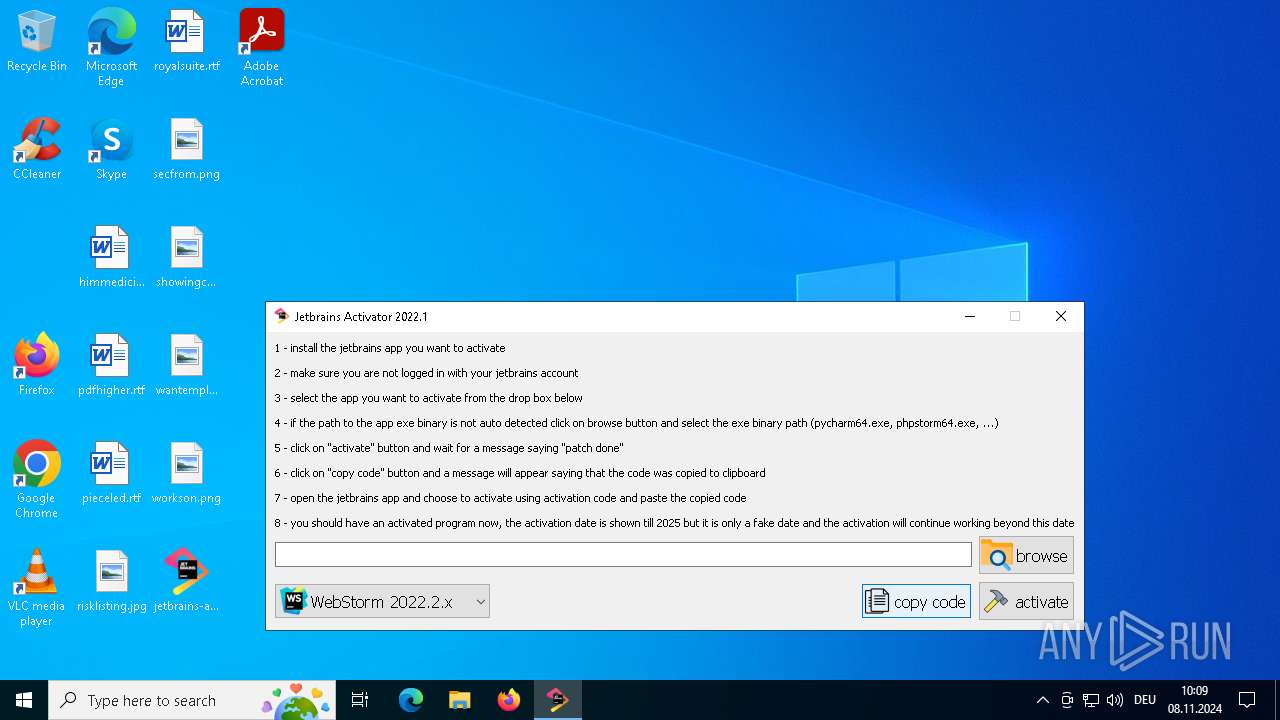
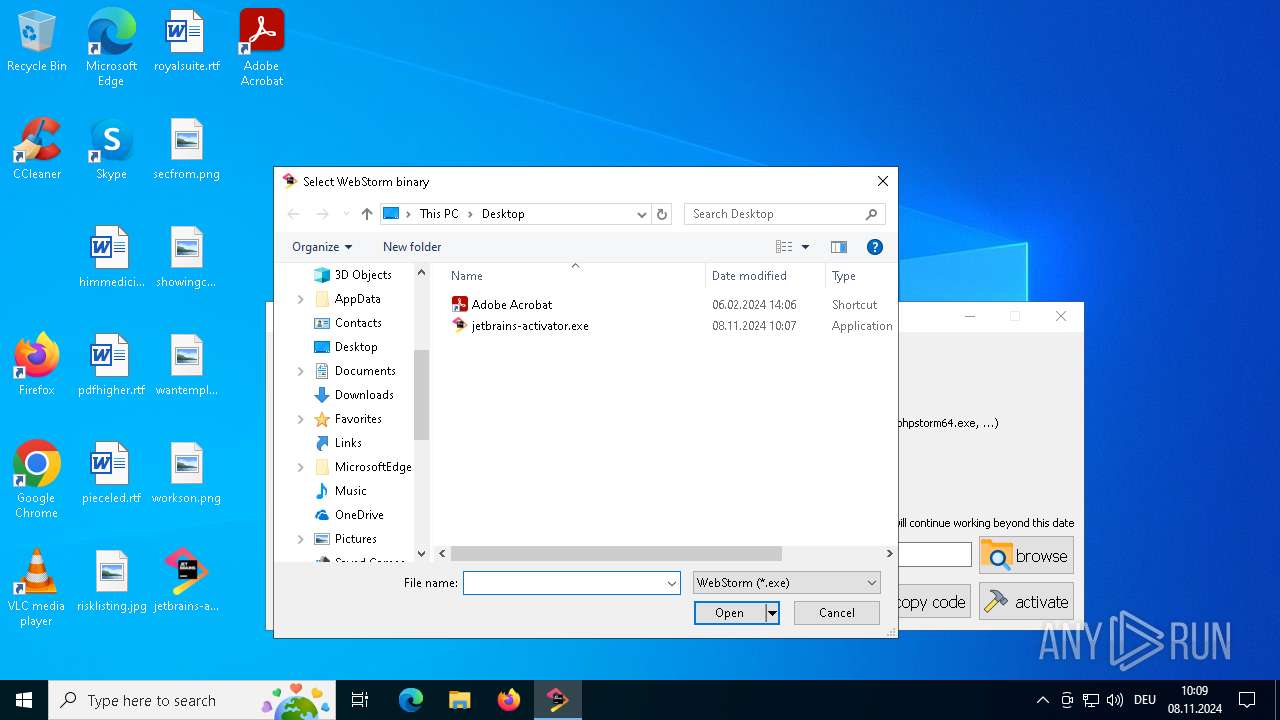
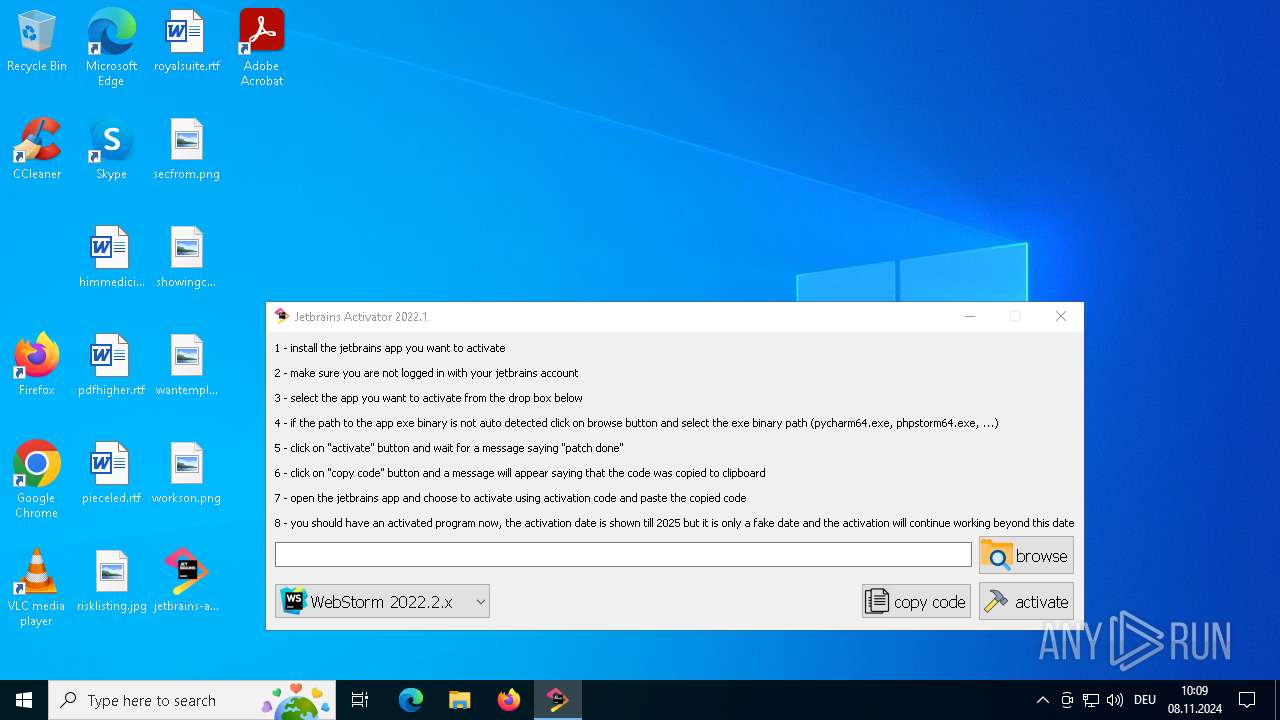
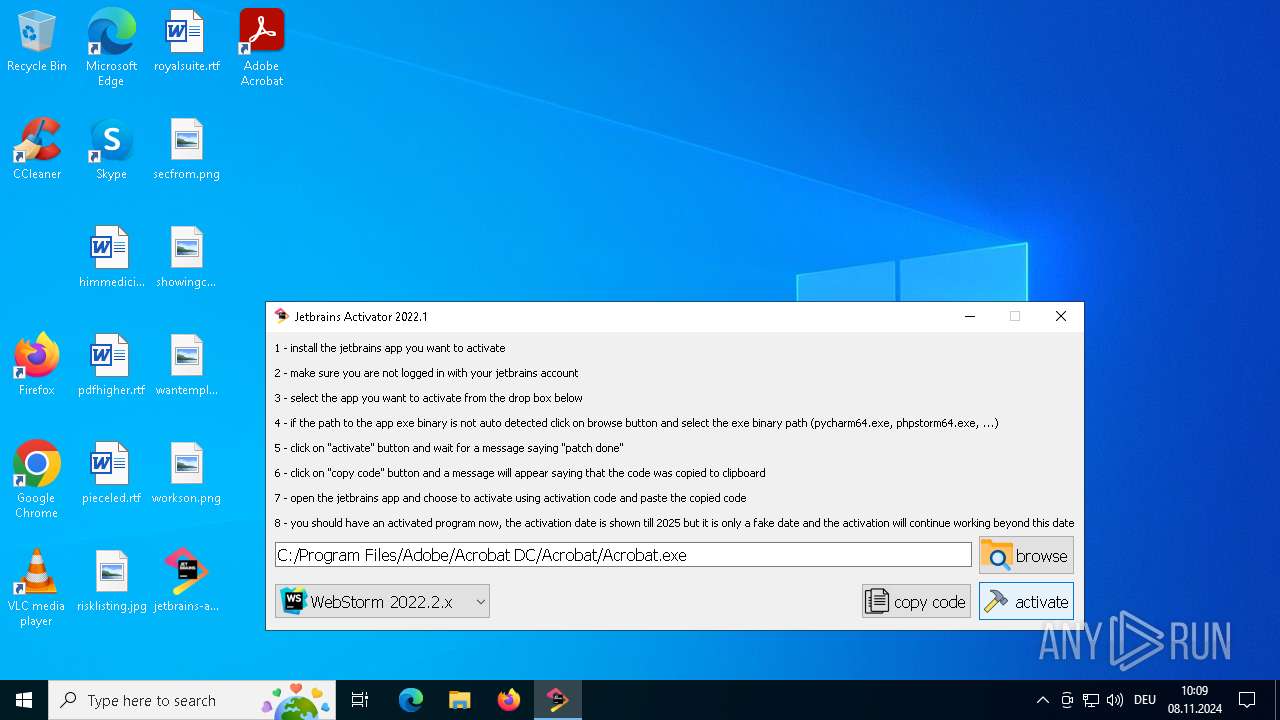
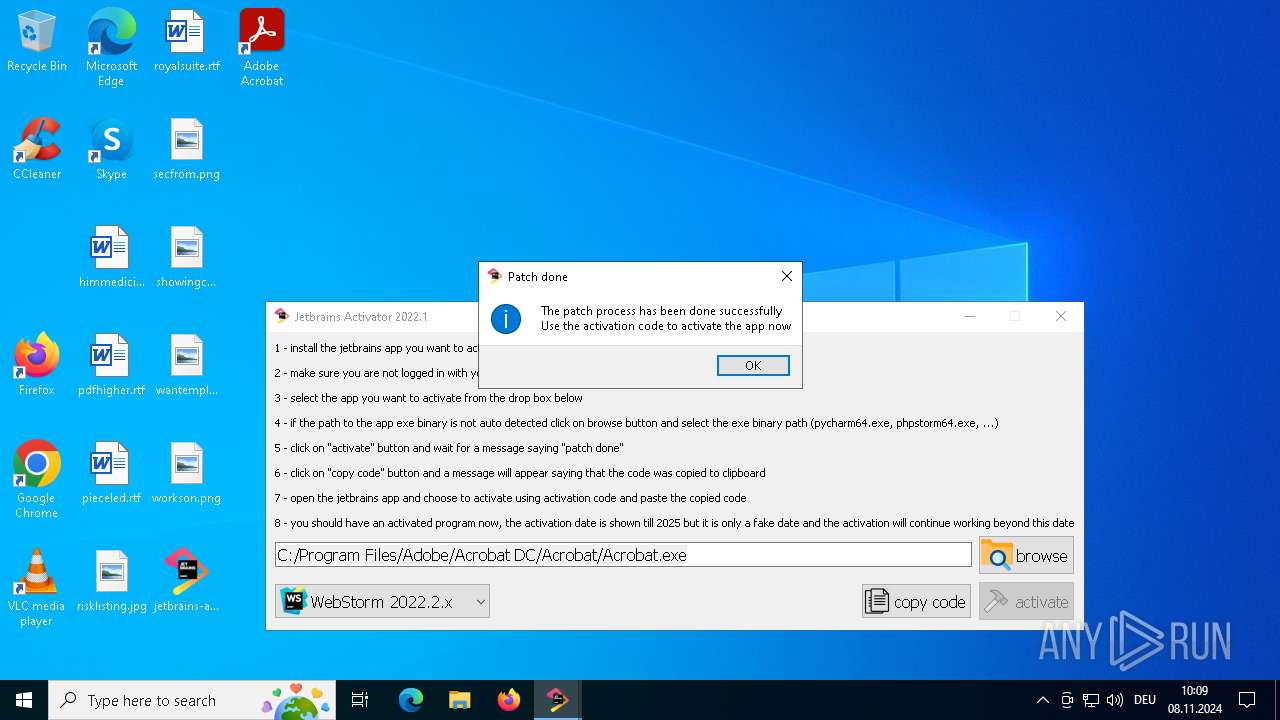
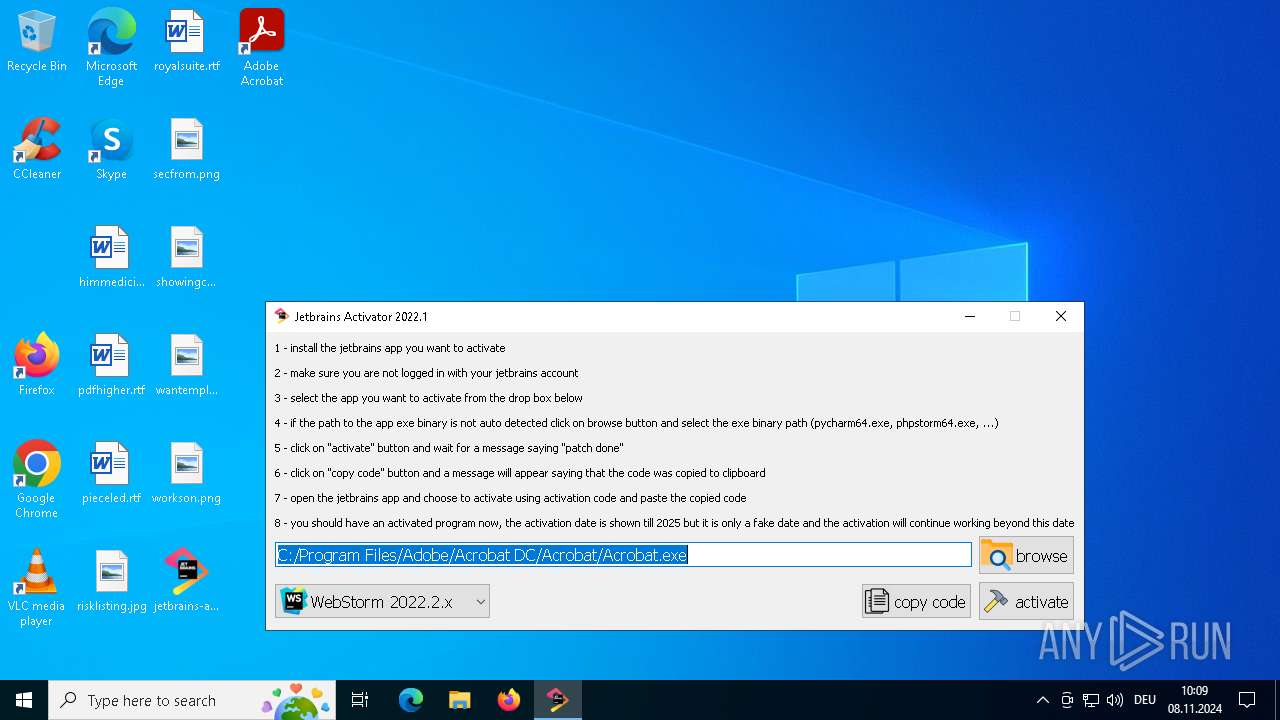
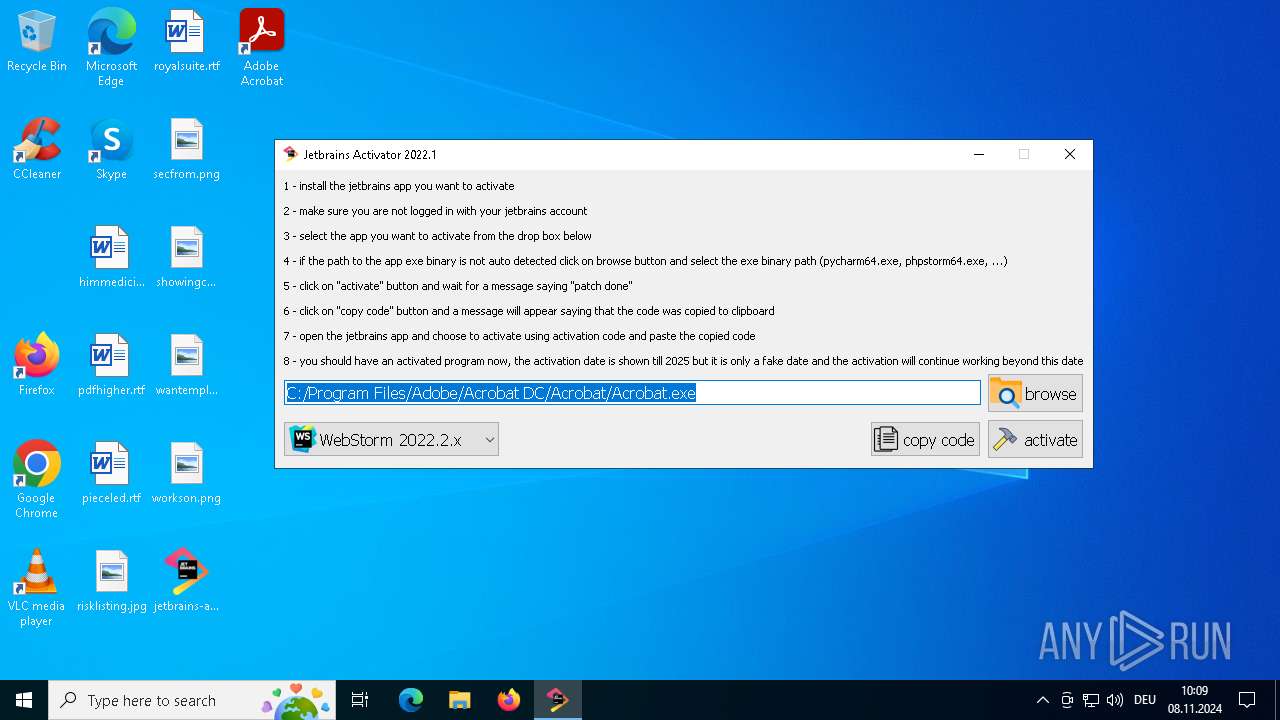
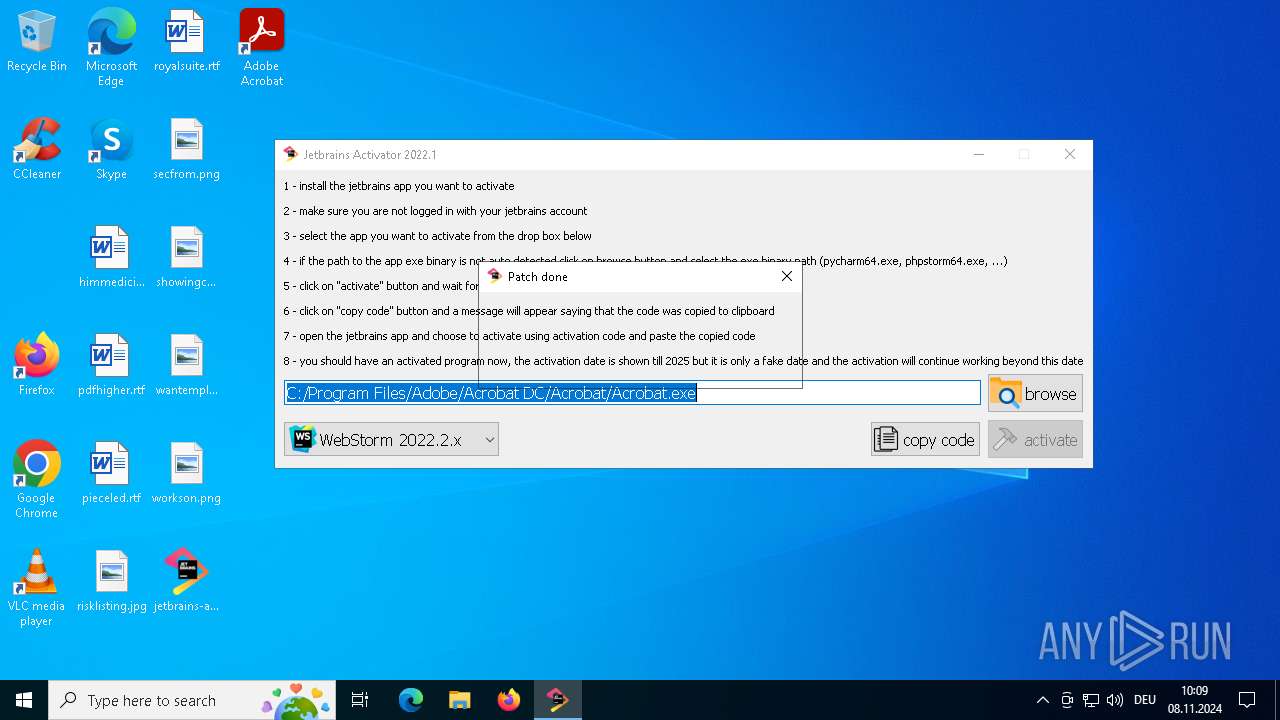
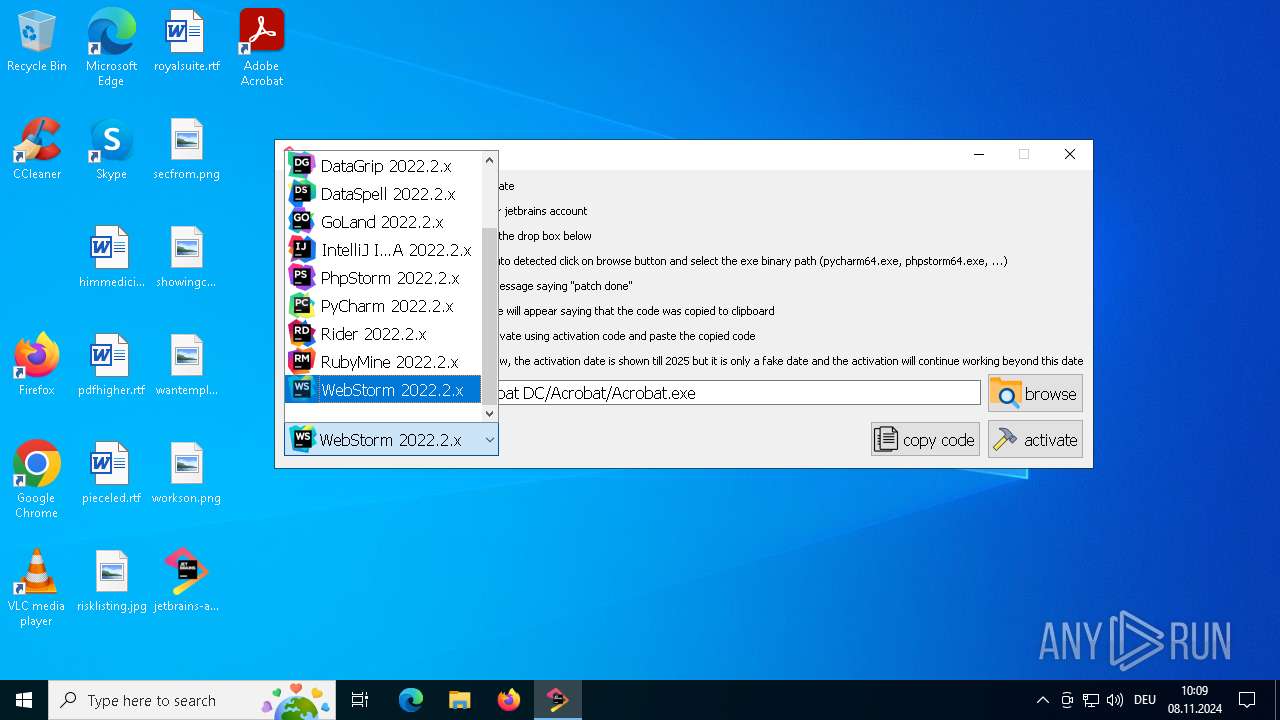
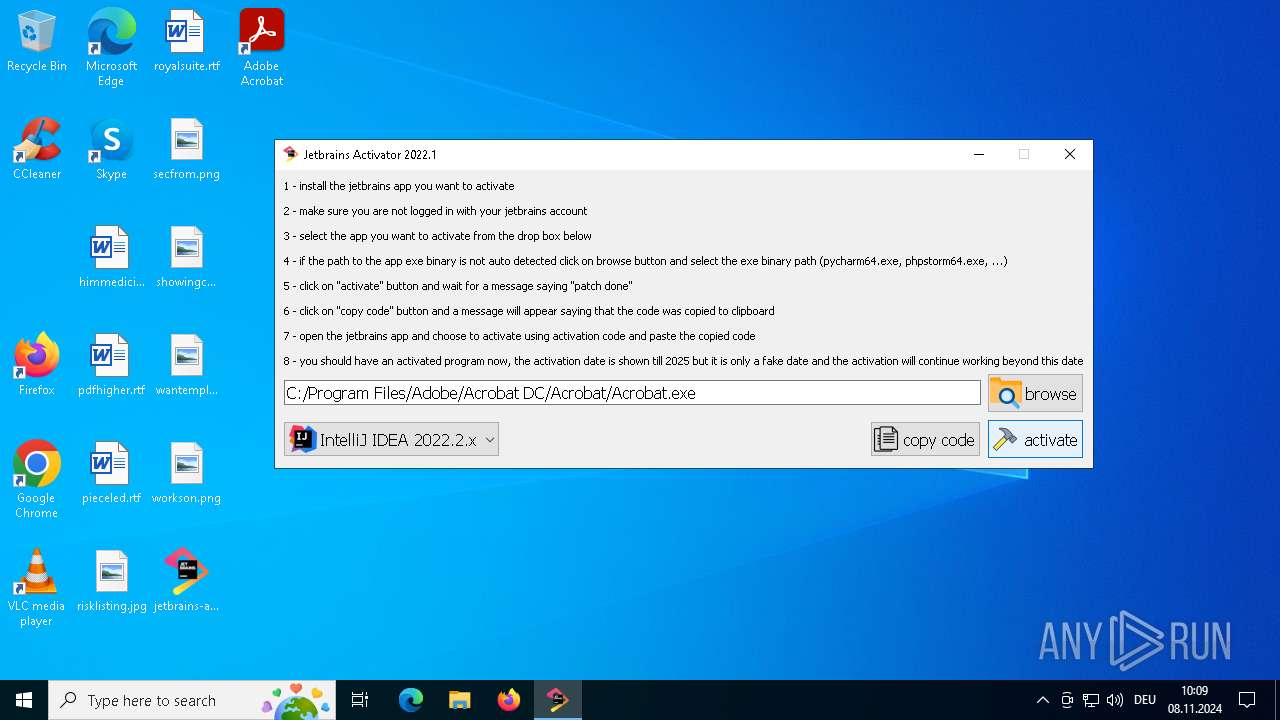
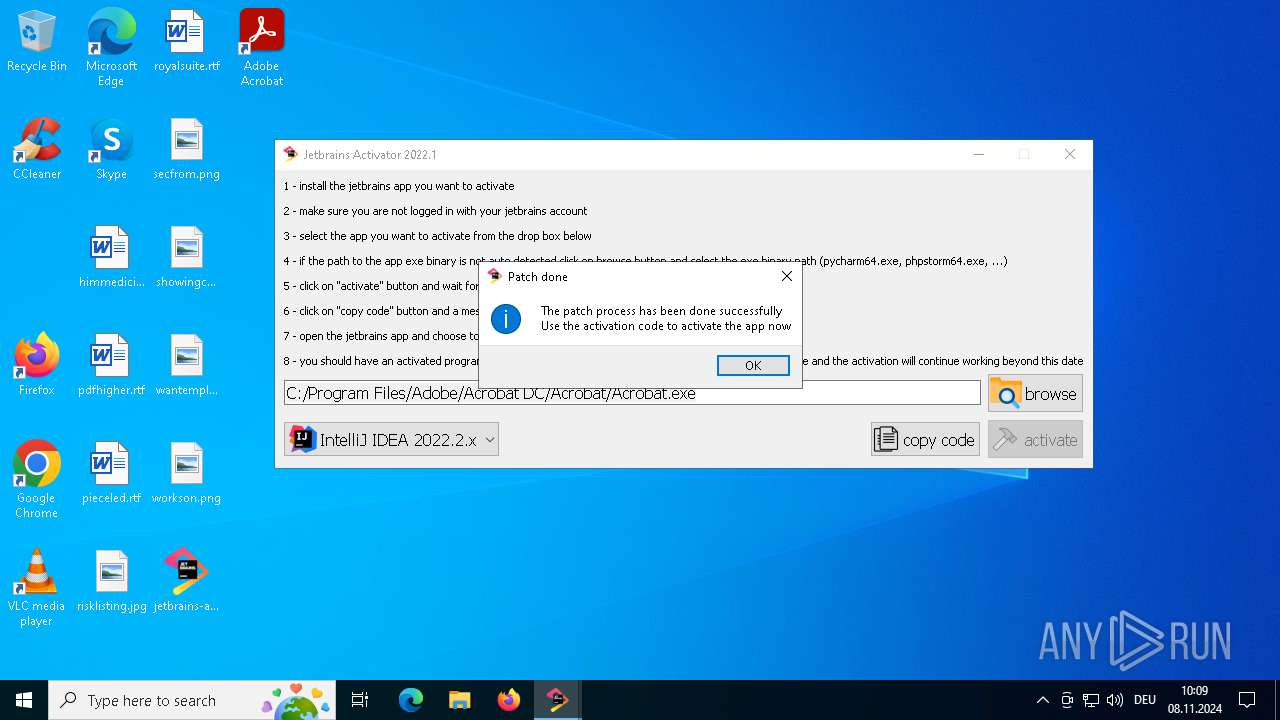
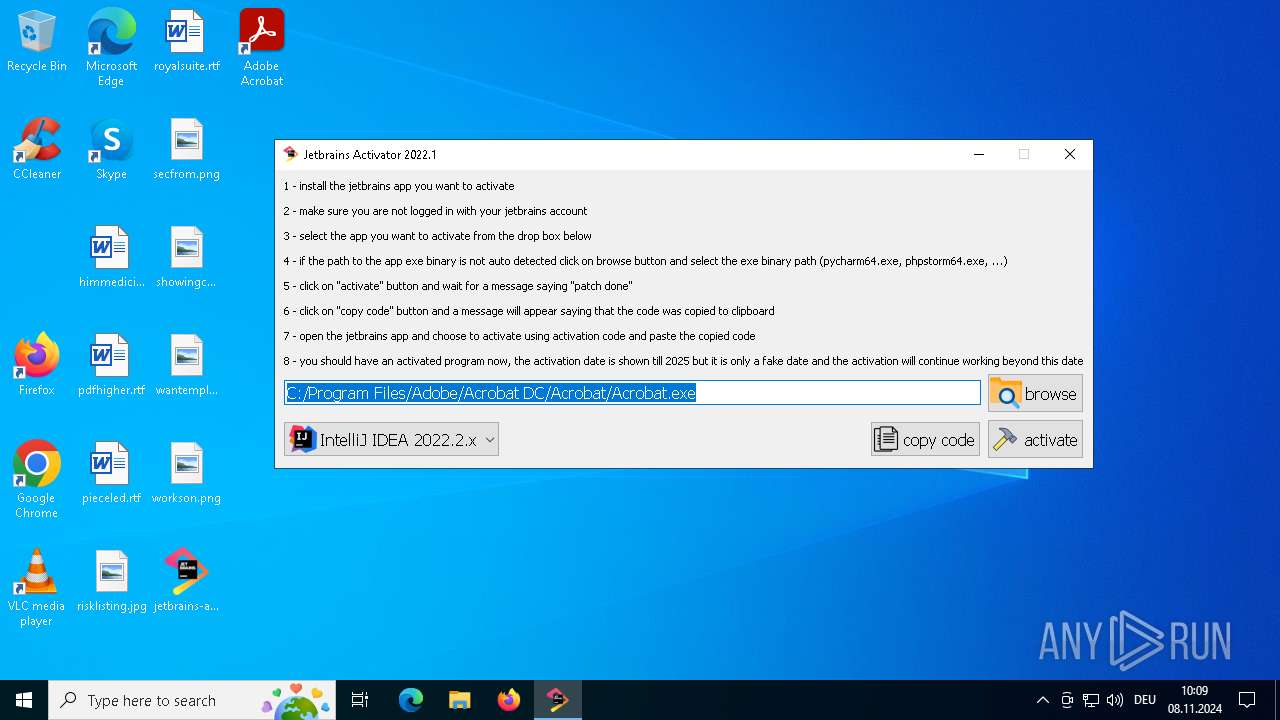
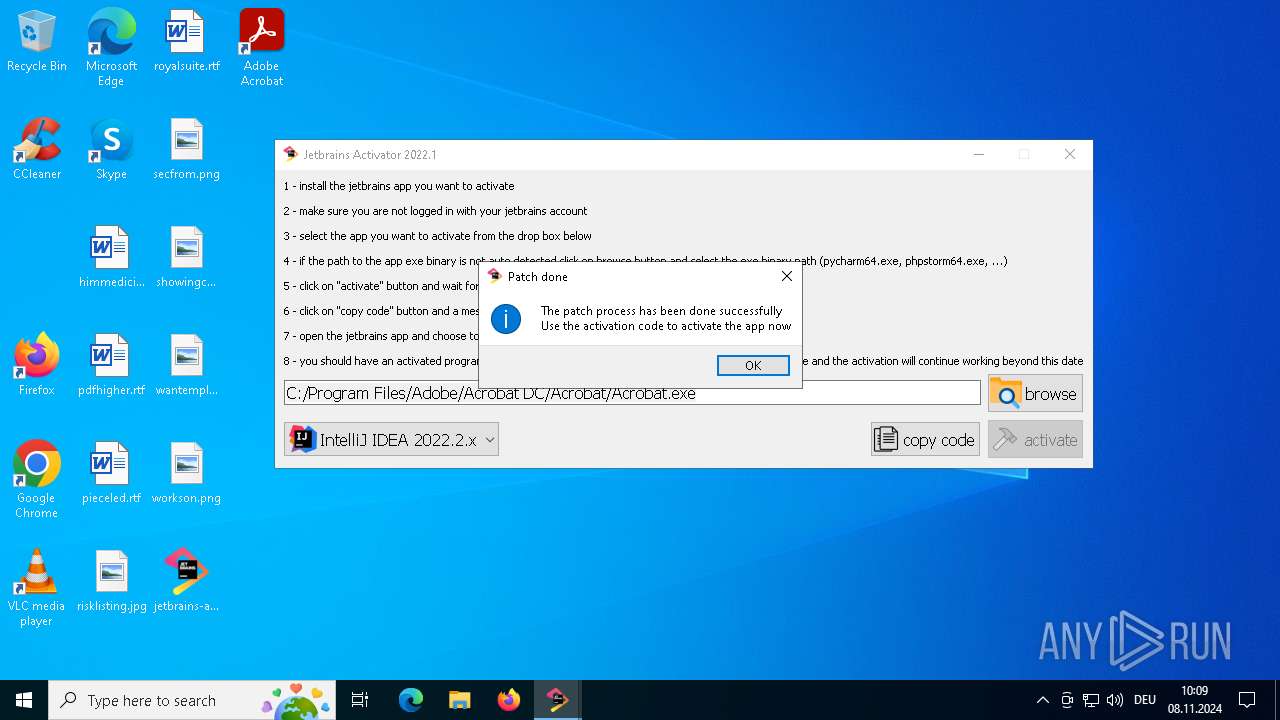
| File name: | jetbrains-activator.exe |
| Full analysis: | https://app.any.run/tasks/a59da2ce-931f-48a9-8569-6e4e60d384f9 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2024, 09:07:18 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 8 sections |
| MD5: | 9DFF2CDB371334619B15372AA3F6085C |
| SHA1: | EA651AF34BFE2052668E37BCD3F60696EBAFFA1C |
| SHA256: | 3E52C0B97F67287C212E5BC779B0E7DD843FB0DF2EF11B74E1891898D492782C |
| SSDEEP: | 98304:ScTE9EF5E3hzztBDbkGp2RIUR9gdK615JLeHmi+l4m08qqo0VBjLt3fFV4Ar2IIi:C+693MbDJIxny/h9CM/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- jetbrains-activator.exe (PID: 6660)
Reads security settings of Internet Explorer
- jetbrains-activator.exe (PID: 6660)
Executes as Windows Service
- AGSService.exe (PID: 7164)
- AGSService.exe (PID: 3732)
- AGSService.exe (PID: 5660)
- AGSService.exe (PID: 2000)
Executable content was dropped or overwritten
- jetbrains-activator.exe (PID: 1764)
INFO
Reads the computer name
- jetbrains-activator.exe (PID: 6660)
Checks supported languages
- jetbrains-activator.exe (PID: 6660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:02:01 22:17:42+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 9542656 |
| InitializedDataSize: | 9126400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8d77e8 |
| OSVersion: | 6 |
| ImageVersion: | 11 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.0.49893 |
| ProductVersionNumber: | 11.0.0.49893 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 11.0.0.49893 |
| LegalCopyright: | - |
| OriginalFileName: | jetbrains-activator.exe |
| ProductName: | jetbrains-activator |
| ProductVersion: | 11.0.0.49893 |
Total processes
119
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1764 | "C:\Users\admin\Desktop\jetbrains-activator.exe" "C:\Users\admin\Desktop\jetbrains-activator.exe" | C:\Users\admin\Desktop\jetbrains-activator.exe | jetbrains-activator.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 11.0.0.49893 Modules
| |||||||||||||||
| 2000 | "C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe" | C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 4294967295 Modules
| |||||||||||||||
| 3732 | "C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe" | C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 4294967295 Modules
| |||||||||||||||
| 5660 | "C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe" | C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 4294967295 Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\Desktop\jetbrains-activator.exe" | C:\Users\admin\Desktop\jetbrains-activator.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 11.0.0.49893 Modules
| |||||||||||||||
| 7164 | "C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe" | C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 4294967295 Modules
| |||||||||||||||
Total events
7 099
Read events
7 021
Write events
76
Delete events
2
Modification events
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 010000000000000004000000050000000200000003000000FFFFFFFF | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Generic | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 96 | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\lnk |
| Operation: | write | Name: | 1 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C641700032000D0800004658D968200041444F4245417E312E4C4E4B0000540009000400EFBE4658D9686859FB482E0000000168000000000F0000000000000000000000000000001C452400410064006F006200650020004100630072006F006200610074002E006C006E006B0000001C000000 | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\lnk |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | 7 |
Value: 14001F50E04FD020EA3A6910A2D808002B30309D14002E803ACCBFB42CDB4C42B0297FE99A87C641700032000D0800004658D968200041444F4245417E312E4C4E4B0000540009000400EFBE4658D9686859FB482E0000000168000000000F0000000000000000000000000000001C452400410064006F006200650020004100630072006F006200610074002E006C006E006B0000001C000000 | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 0700000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (6660) jetbrains-activator.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\34\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
Executable files
7
Suspicious files
2
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1764 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\hideme.jar | java | |
MD5:CDAB6A30B0949A741F13935F5483C303 | SHA256:FA14C735AB9FED3F3A5DF0DC78A5D38AE0A146099DDC858197E9F528BD996C40 | |||
| 1764 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\url.jar | java | |
MD5:6B181E5B8255DB4CD9BEB1C6AF5F420E | SHA256:CE5A83AEE31153CCA30274AC94467B316EDEA8CB28ACF72F52F5A72D455B1B43 | |||
| 1764 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\native.jar | java | |
MD5:D53081E7676F669061695827209B0FBD | SHA256:88E419764B31134E74E4A968015F6F80DA497EEFCD4AEFF77D7C2CE57CB5EFCD | |||
| 6660 | jetbrains-activator.exe | C:\Users\admin\Desktop\Adobe Acrobat.lnk | binary | |
MD5:2EE9DED37A2985C8F8D2FFB99F8C16AA | SHA256:B1F06C0DC671BC0E6F75B7A14A7A639E3346E4999652E5C5F4F3FAE7FC34F3F1 | |||
| 1764 | jetbrains-activator.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe.vmoptions | text | |
MD5:178940502D8B29091B03E6D10A762FF9 | SHA256:3F892713005DCFF187EA3E5EDBF7EDBAA259B225AA4A0E37B6D597BF5E94C909 | |||
| 1764 | jetbrains-activator.exe | C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe | executable | |
MD5:F67837CE349FEB9C14F4F6277130F666 | SHA256:DF061B9812E2A2C3FC8500A353779826F823F45A21CF4BD78181645679890724 | |||
| 1764 | jetbrains-activator.exe | C:\ja-netfilter-files\config-jetbrains\power.conf | text | |
MD5:25E529ACCB85415C8C2B40FCE1AB65F5 | SHA256:05C70700CB0A3E8E7C596205CEBE7284B2F7FBDF5F6BEEB4424730A753239701 | |||
| 6660 | jetbrains-activator.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:4D643DB4298B89A00B469DA51B91DEC4 | SHA256:6162746DB4889FBACE2C12174A9EF329058748F0E37D4B012DB14BA589C47CBA | |||
| 1764 | jetbrains-activator.exe | C:\ja-netfilter-files\plugins-jetbrains\power.jar | java | |
MD5:D8711B73BC0507DBDC841B098AF99787 | SHA256:7819E5B968CE5EA2E638E53D84089D35E89E9EA3088F18F8DBF6DD38D14AB25A | |||
| 1764 | jetbrains-activator.exe | C:\ja-netfilter-files\config-jetbrains\url.conf | text | |
MD5:FEA2BFBEDDA20D5AD9429F537E15F4CE | SHA256:88E1DCA8019AD412CF2C6FBD947A83786CFFC7B32F1EE35594D25D1F38FAE5F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
23
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.162:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |