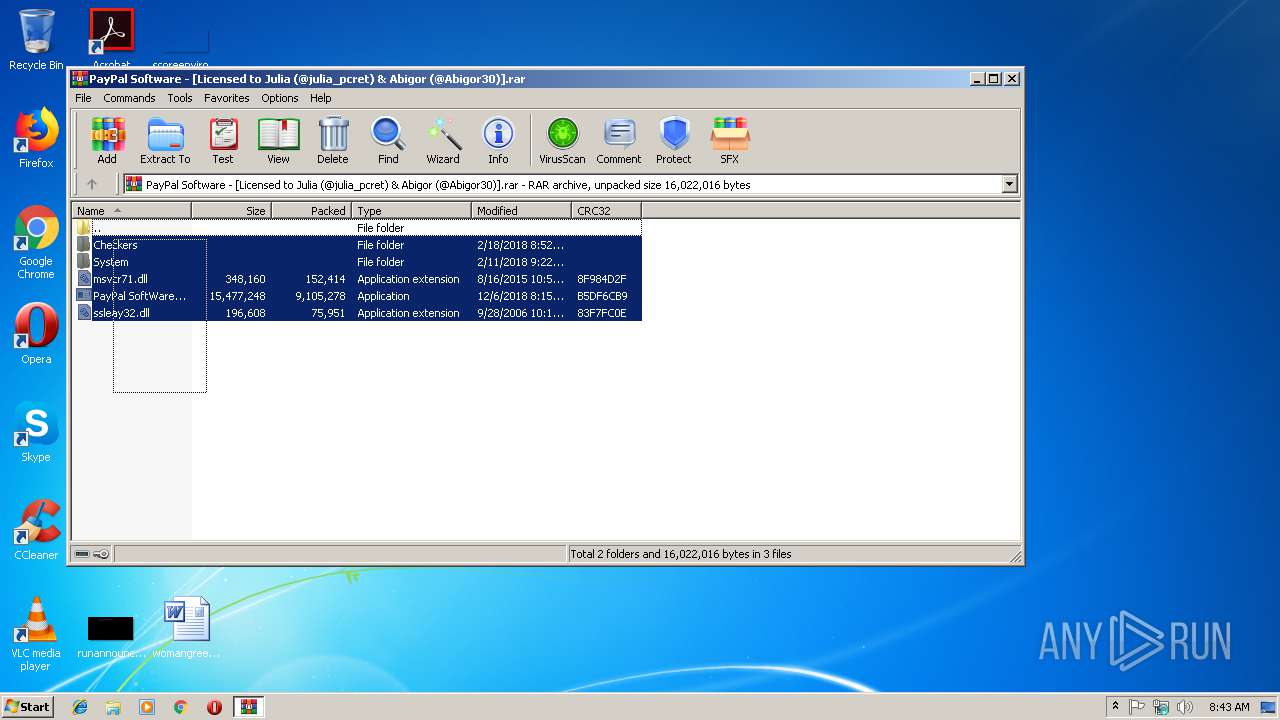
| File name: | PayPal Software - [Licensed to Julia (@julia_pcret) & Abigor (@Abigor30)].rar |
| Full analysis: | https://app.any.run/tasks/ecaba16c-aff0-47de-83fe-c2c9f51a9b95 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 08:43:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F5443739B05DEA5665AB259FB1B3AD3B |
| SHA1: | 3786C7E93F802E9D0F97613D03EE6F3C5560D226 |
| SHA256: | 3E515765A83C99F0E63237F8F982DCEE15FA1F6BEF4F58CBF9061C42CF6B07A3 |
| SSDEEP: | 196608:1tXnmIgTaa+QiGppEzVwV3siXhHWylbizhFSe1iBRE+5OI0MhD:1MI8d9ft3siRHWAeQRl5D5hD |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1520)
- explorer.exe (PID: 3648)
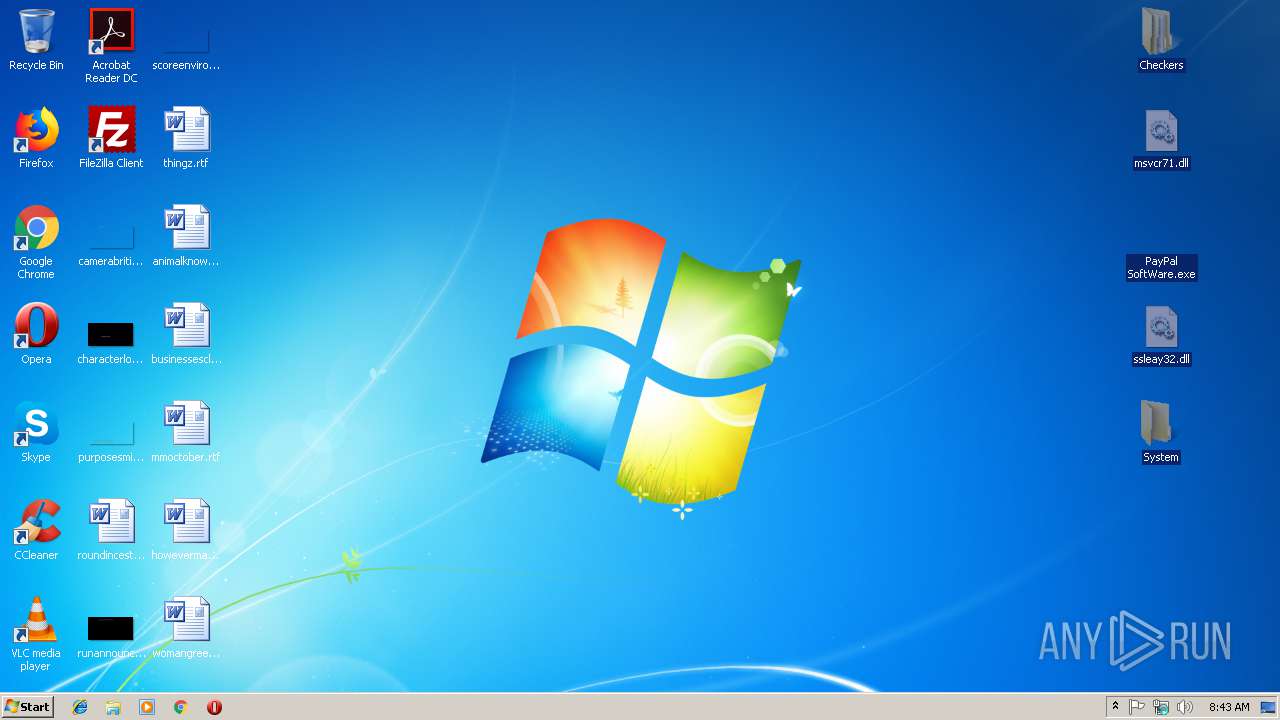
Application was dropped or rewritten from another process
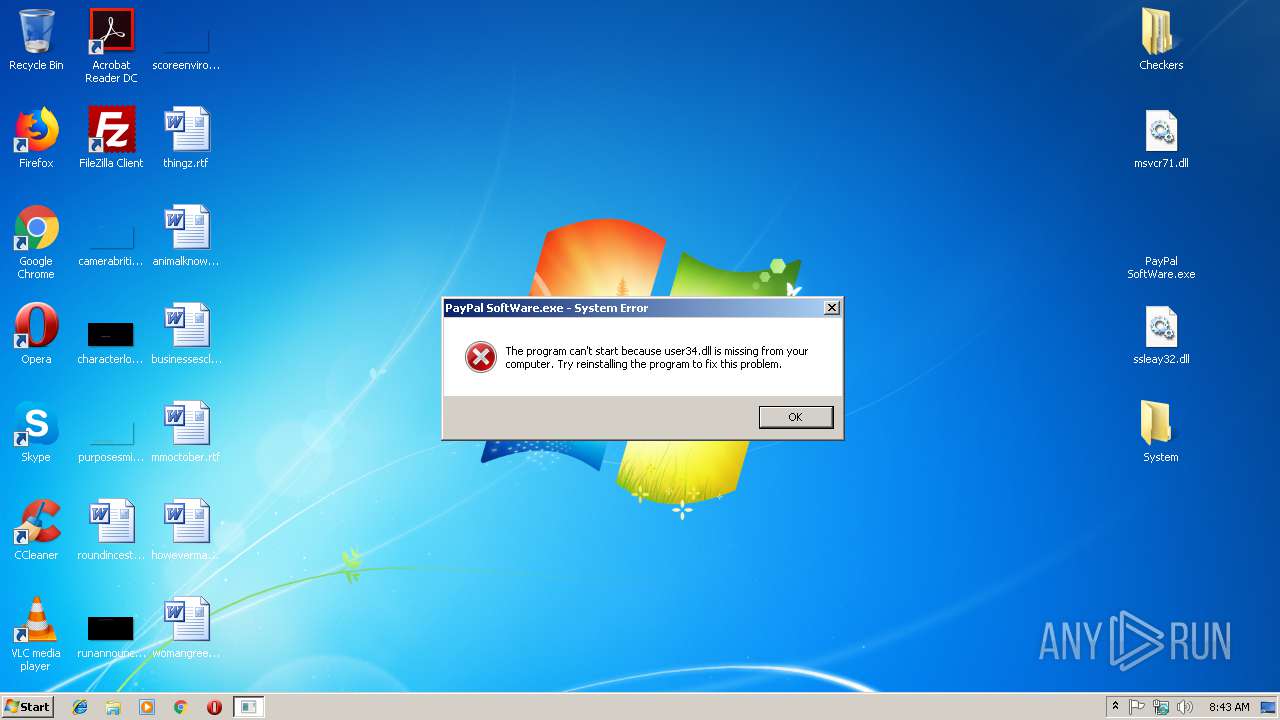
- PayPal SoftWare.exe (PID: 3072)
- PayPal SoftWare.exe (PID: 3760)
- SeafkoAgent.exe (PID: 3976)
- explorer.exe (PID: 3648)
Changes the autorun value in the registry
- explorer.exe (PID: 3648)
SUSPICIOUS
Creates executable files which already exist in Windows
- SeafkoAgent.exe (PID: 3976)
- explorer.exe (PID: 3648)
Executable content was dropped or overwritten
- explorer.exe (PID: 3648)
- SeafkoAgent.exe (PID: 3976)
- PayPal SoftWare.exe (PID: 3072)
- WinRAR.exe (PID: 3220)
Starts itself from another location
- SeafkoAgent.exe (PID: 3976)
Checks for external IP
- explorer.exe (PID: 3648)
Connects to unusual port
- explorer.exe (PID: 3648)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
35
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1520 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3072 | "C:\Users\admin\Desktop\PayPal SoftWare.exe" | C:\Users\admin\Desktop\PayPal SoftWare.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3220 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PayPal Software - [Licensed to Julia (@julia_pcret) & Abigor (@Abigor30)].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3648 | "C:\Users\admin\AppData\Local\explorer.exe" | C:\Users\admin\AppData\Local\explorer.exe | SeafkoAgent.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3760 | "C:\Users\admin\AppData\Local\Temp\PayPal SoftWare.exe" | C:\Users\admin\AppData\Local\Temp\PayPal SoftWare.exe | — | PayPal SoftWare.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\AppData\Local\Temp\SeafkoAgent.exe" | C:\Users\admin\AppData\Local\Temp\SeafkoAgent.exe | PayPal SoftWare.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 646
Read events
1 606
Write events
40
Delete events
0
Modification events
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PayPal Software - [Licensed to Julia (@julia_pcret) & Abigor (@Abigor30)].rar | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3220) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
12
Suspicious files
4
Text files
2
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Temp\CabFC86.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TarFC87.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Temp\CabFC98.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TarFC99.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Temp\CabFD84.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Temp\TarFD95.tmp | — | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\explorer.exe_Url_ngrhffohuwb5vq4wdkmha13b4xo42qkl\1.0.0.0\uy2ghvms.newcfg | — | |
MD5:— | SHA256:— | |||
| 3220 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3220.33483\PayPal SoftWare.exe | executable | |
MD5:— | SHA256:— | |||
| 3072 | PayPal SoftWare.exe | C:\Users\admin\AppData\Local\Temp\PayPal SoftWare.exe | executable | |
MD5:— | SHA256:— | |||
| 3648 | explorer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94308059B57B3142E455B38A6EB92015 | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
9
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3648 | explorer.exe | GET | 204 | 216.58.215.238:80 | http://clients3.google.com/generate_204 | US | — | — | whitelisted |
3648 | explorer.exe | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
3648 | explorer.exe | GET | 200 | 13.107.4.50:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/DF3C24F9BFD666761B268073FE06D1CC8D4F82A4.crt | US | der | 914 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3648 | explorer.exe | 62.113.237.211:6667 | irc.enterthegame.com | 23media GmbH | DE | unknown |
3648 | explorer.exe | 178.63.3.16:6669 | irc.chat4all.org | Hetzner Online GmbH | DE | unknown |
3648 | explorer.exe | 35.162.131.249:6667 | irc.austnet.org | Amazon.com, Inc. | US | unknown |
3648 | explorer.exe | 216.239.36.21:443 | ipinfo.io | Google Inc. | US | whitelisted |
3648 | explorer.exe | 178.62.28.241:6667 | irc.cyberarmy.net | Digital Ocean, Inc. | GB | unknown |
3648 | explorer.exe | 91.217.189.5:6667 | irc.efnet.org | Portlane AB | SE | unknown |
3648 | explorer.exe | 13.107.4.50:80 | www.download.windowsupdate.com | Microsoft Corporation | US | whitelisted |
3648 | explorer.exe | 216.58.215.238:80 | clients3.google.com | Google Inc. | US | whitelisted |
3648 | explorer.exe | 145.14.144.19:443 | a-rat.000webhostapp.com | Hostinger International Limited | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients3.google.com |
| whitelisted |
ipinfo.io |
| shared |
a-rat.000webhostapp.com |
| shared |
www.download.windowsupdate.com |
| whitelisted |
irc.chat4all.org |
| unknown |
irc.enterthegame.com |
| unknown |
irc.efnet.org |
| malicious |
irc.austnet.org |
| unknown |
irc.cyberarmy.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3648 | explorer.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3648 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
3648 | explorer.exe | A Network Trojan was detected | SC BACKDOOR TeleRAT webhook using attempt |
3648 | explorer.exe | Misc activity | ET CHAT IRC authorization message |
3648 | explorer.exe | Misc activity | ET CHAT IRC PONG response |
3648 | explorer.exe | Misc activity | ET CHAT IRC PONG response |
3648 | explorer.exe | Misc activity | ET CHAT IRC PING command |
3648 | explorer.exe | Misc activity | ET CHAT IRC authorization message |
3648 | explorer.exe | Misc activity | ET CHAT IRC PING command |
3648 | explorer.exe | Misc activity | ET CHAT IRC authorization message |
4 ETPRO signatures available at the full report