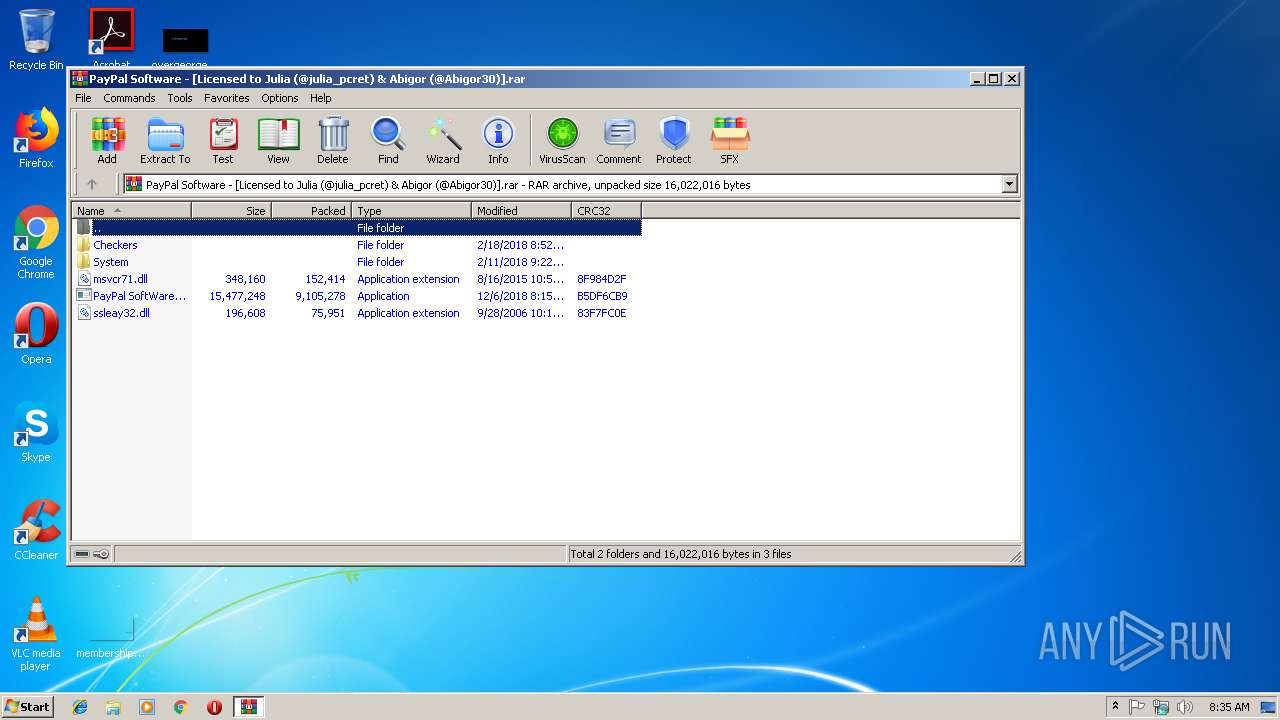
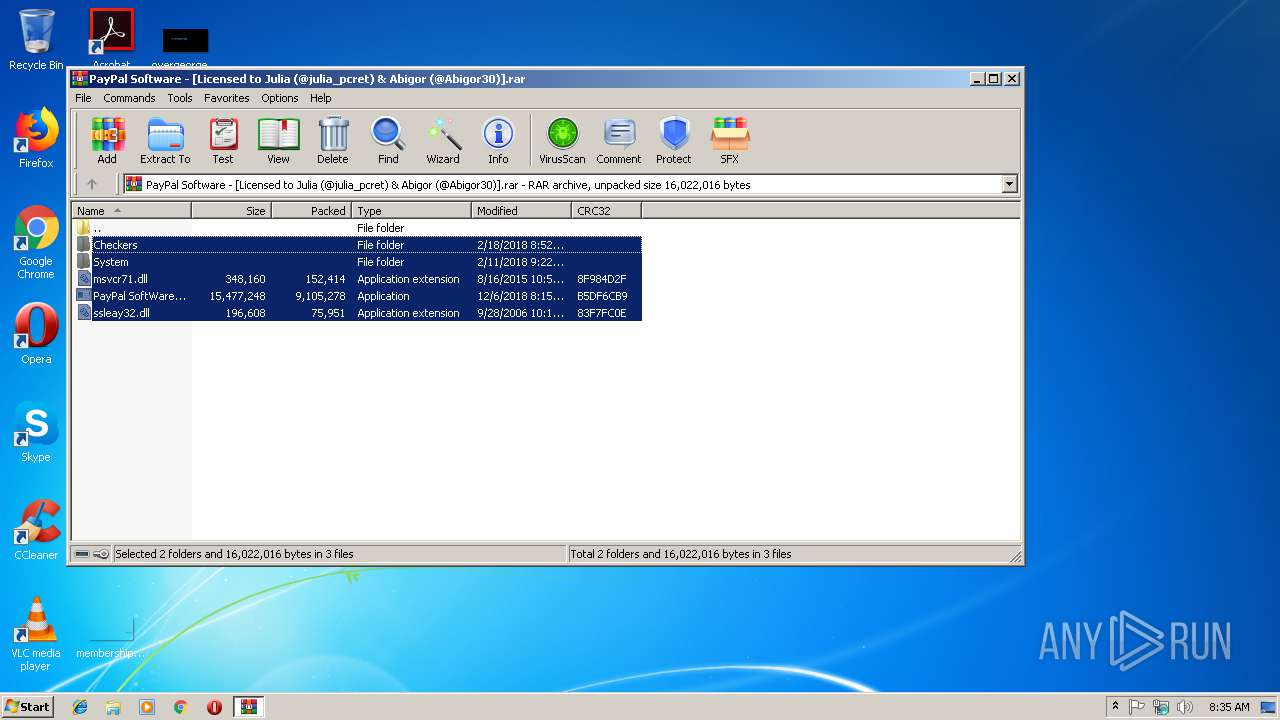
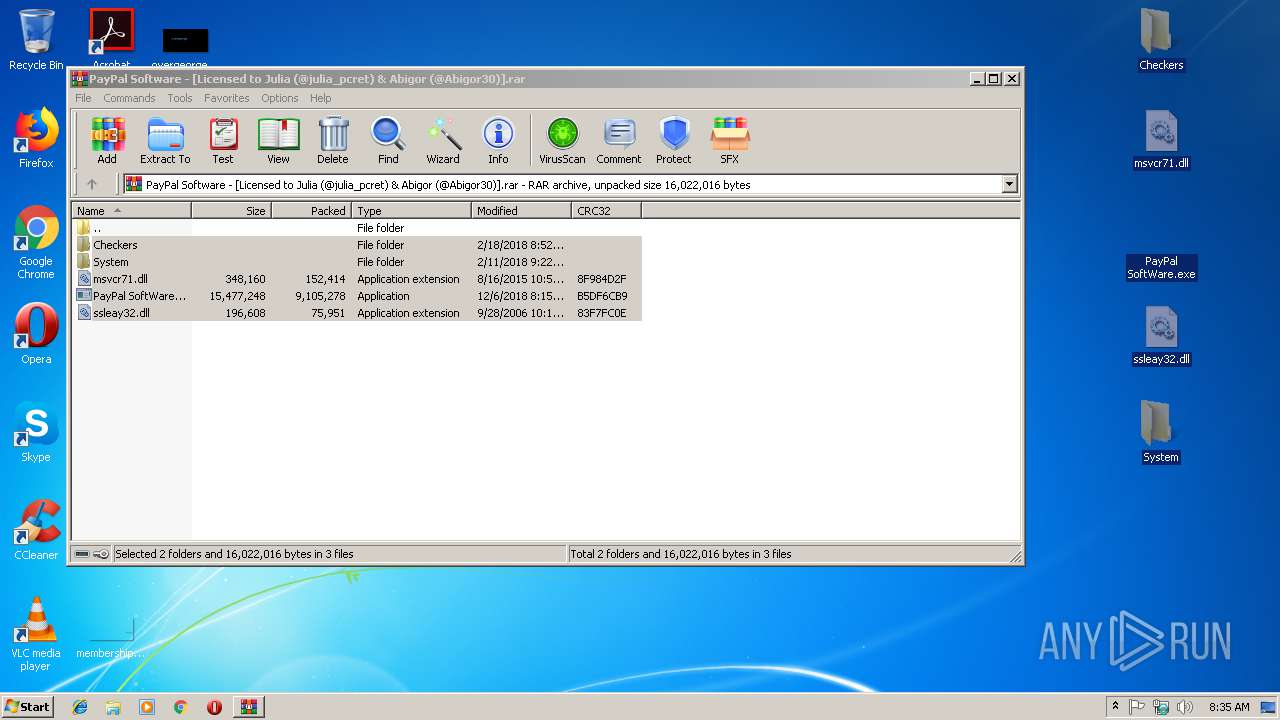
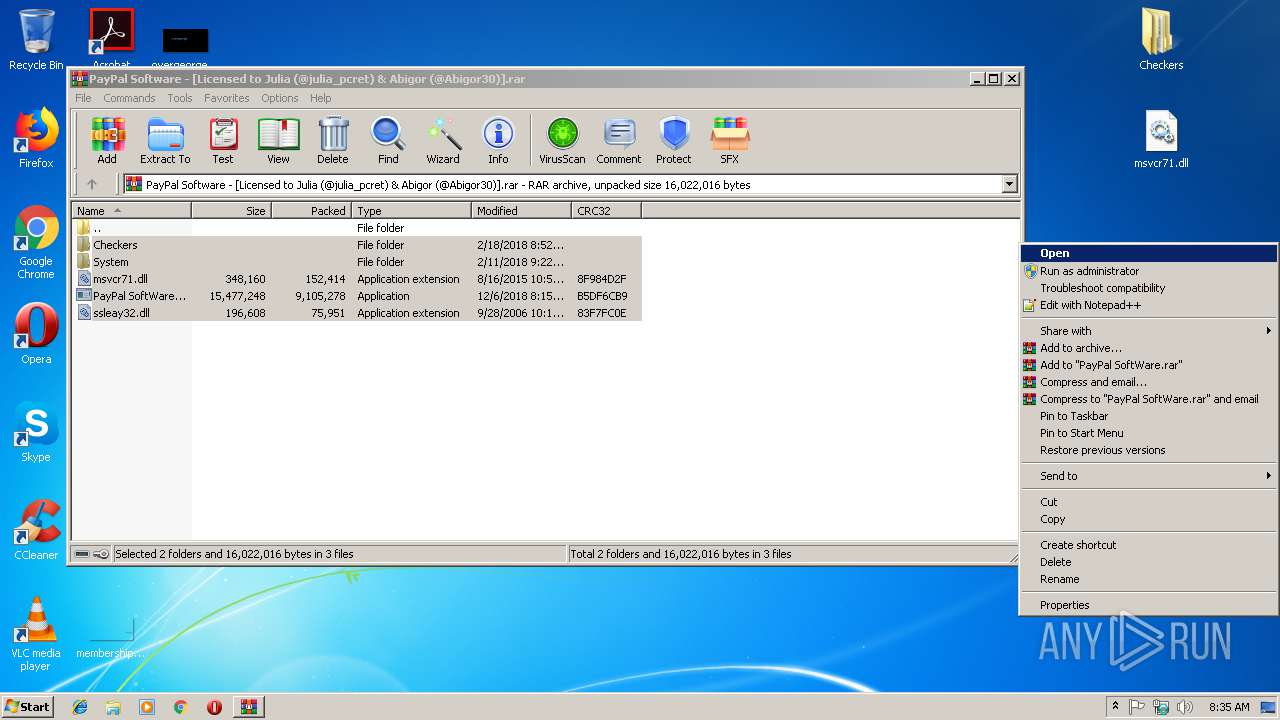
| File name: | PayPal Software - [Licensed to Julia (@julia_pcret) & Abigor (@Abigor30)].rar |
| Full analysis: | https://app.any.run/tasks/4c98a88e-c31e-4381-a748-f9ed147851f5 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 08:35:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F5443739B05DEA5665AB259FB1B3AD3B |
| SHA1: | 3786C7E93F802E9D0F97613D03EE6F3C5560D226 |
| SHA256: | 3E515765A83C99F0E63237F8F982DCEE15FA1F6BEF4F58CBF9061C42CF6B07A3 |
| SSDEEP: | 196608:1tXnmIgTaa+QiGppEzVwV3siXhHWylbizhFSe1iBRE+5OI0MhD:1MI8d9ft3siRHWAeQRl5D5hD |
MALICIOUS
Application was dropped or rewritten from another process
- PayPal SoftWare.exe (PID: 3724)
- PayPal SoftWare.exe (PID: 3764)
- explorer.exe (PID: 3812)
- SeafkoAgent.exe (PID: 4068)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1904)
SUSPICIOUS
Executable content was dropped or overwritten
- SeafkoAgent.exe (PID: 4068)
- PayPal SoftWare.exe (PID: 3764)
- explorer.exe (PID: 3812)
Starts itself from another location
- SeafkoAgent.exe (PID: 4068)
Creates executable files which already exist in Windows
- SeafkoAgent.exe (PID: 4068)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
38
Monitored processes
6
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1904 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3096 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PayPal Software - [Licensed to Julia (@julia_pcret) & Abigor (@Abigor30)].rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3724 | "C:\Users\admin\AppData\Local\Temp\PayPal SoftWare.exe" | C:\Users\admin\AppData\Local\Temp\PayPal SoftWare.exe | — | PayPal SoftWare.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3764 | "C:\Users\admin\Desktop\PayPal SoftWare.exe" | C:\Users\admin\Desktop\PayPal SoftWare.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 3812 | "C:\Users\admin\AppData\Local\explorer.exe" | C:\Users\admin\AppData\Local\explorer.exe | SeafkoAgent.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4068 | "C:\Users\admin\AppData\Local\Temp\SeafkoAgent.exe" | C:\Users\admin\AppData\Local\Temp\SeafkoAgent.exe | PayPal SoftWare.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 488
Read events
1 470
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PayPal Software - [Licensed to Julia (@julia_pcret) & Abigor (@Abigor30)].rar | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1904) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1904) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
9
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.34212\msvcr71.dll | — | |
MD5:— | SHA256:— | |||
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.34212\PayPal SoftWare.exe | — | |
MD5:— | SHA256:— | |||
| 3096 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3096.34212\ssleay32.dll | — | |
MD5:— | SHA256:— | |||
| 3764 | PayPal SoftWare.exe | C:\Users\admin\AppData\Local\Temp\PayPal SoftWare.exe | executable | |
MD5:— | SHA256:— | |||
| 3764 | PayPal SoftWare.exe | C:\Users\admin\AppData\Local\Temp\SeafkoAgent.exe | executable | |
MD5:— | SHA256:— | |||
| 3812 | explorer.exe | C:\Users\admin\AppData\Local\CommonData.dll | executable | |
MD5:— | SHA256:— | |||
| 4068 | SeafkoAgent.exe | C:\Users\admin\AppData\Local\explorer.exe | executable | |
MD5:— | SHA256:— | |||
| 3812 | explorer.exe | C:\Users\admin\AppData\Local\sqlite3.dll | executable | |
MD5:87F9E5A6318AC1EC5EE05AA94A919D7A | SHA256:7705B87603E0D772E1753441001FCF1AC2643EE41BF14A8177DE2C056628665C | |||
| 3812 | explorer.exe | C:\Users\admin\AppData\Local\AForge.Video.dll | executable | |
MD5:0BD34AA29C7EA4181900797395A6DA78 | SHA256:BAFA6ED04CA2782270074127A0498DDE022C2A9F4096C6BB2B8E3C08BB3D404D | |||
| 3812 | explorer.exe | C:\Users\admin\AppData\Local\Newtonsoft.Json.dll | executable | |
MD5:83222120C8095B8623FE827FB70FAF6B | SHA256:EFF79DE319CA8941A2E62FB573230D82B79B80958E5A26AB1A4E87193EB13503 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
25
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
3812 | explorer.exe | GET | 404 | 172.217.21.238:80 | http://clients3.google.com/generate_204 | US | xml | 345 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3812 | explorer.exe | 172.217.21.238:80 | clients3.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients3.google.com |
| whitelisted |