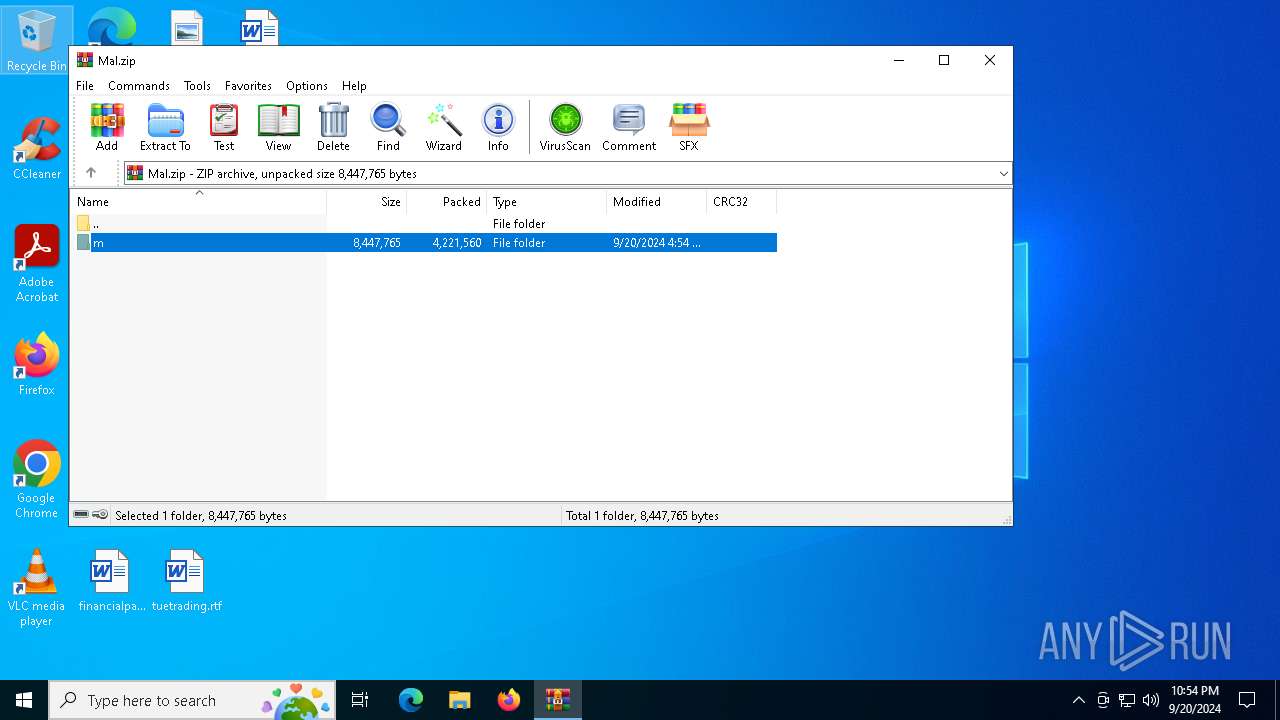
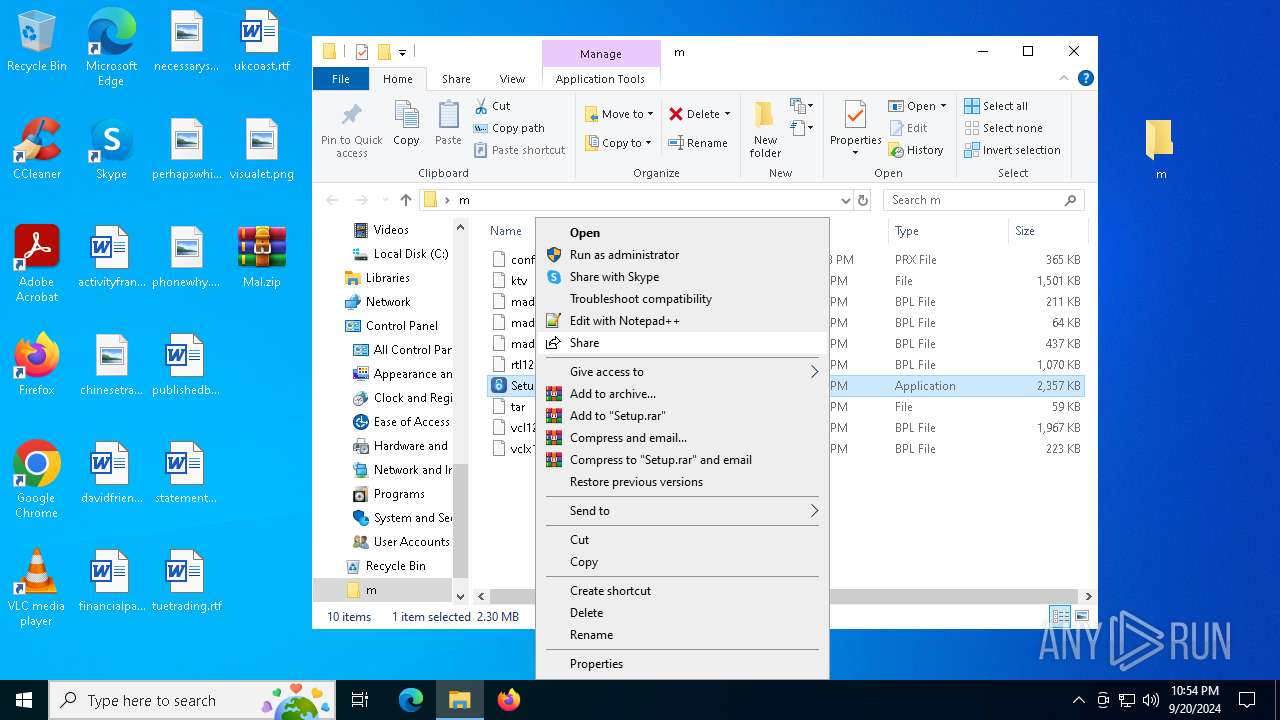
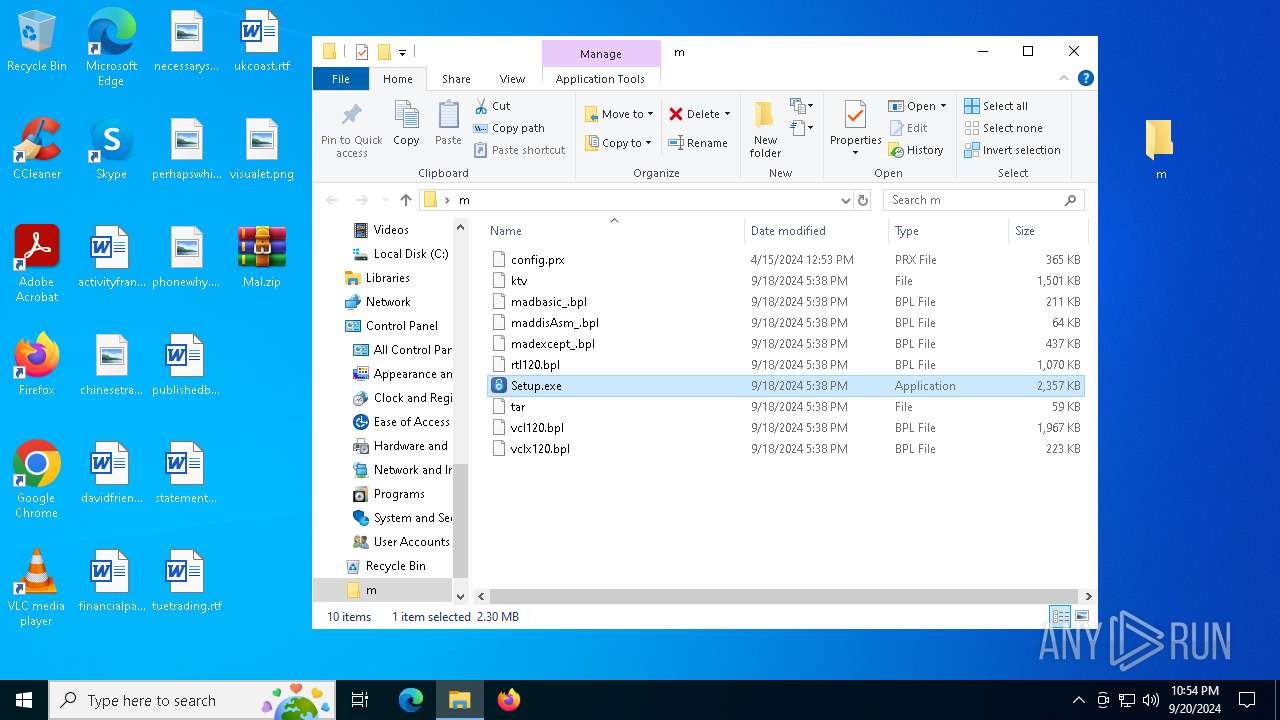
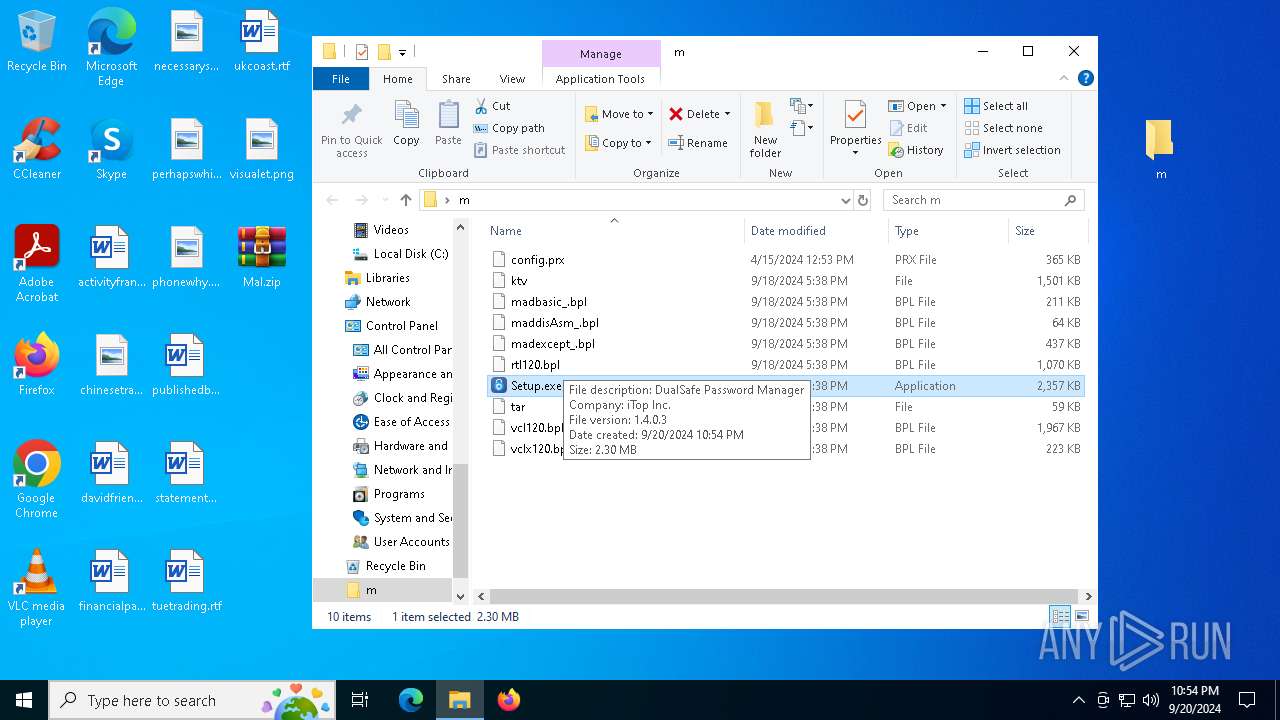
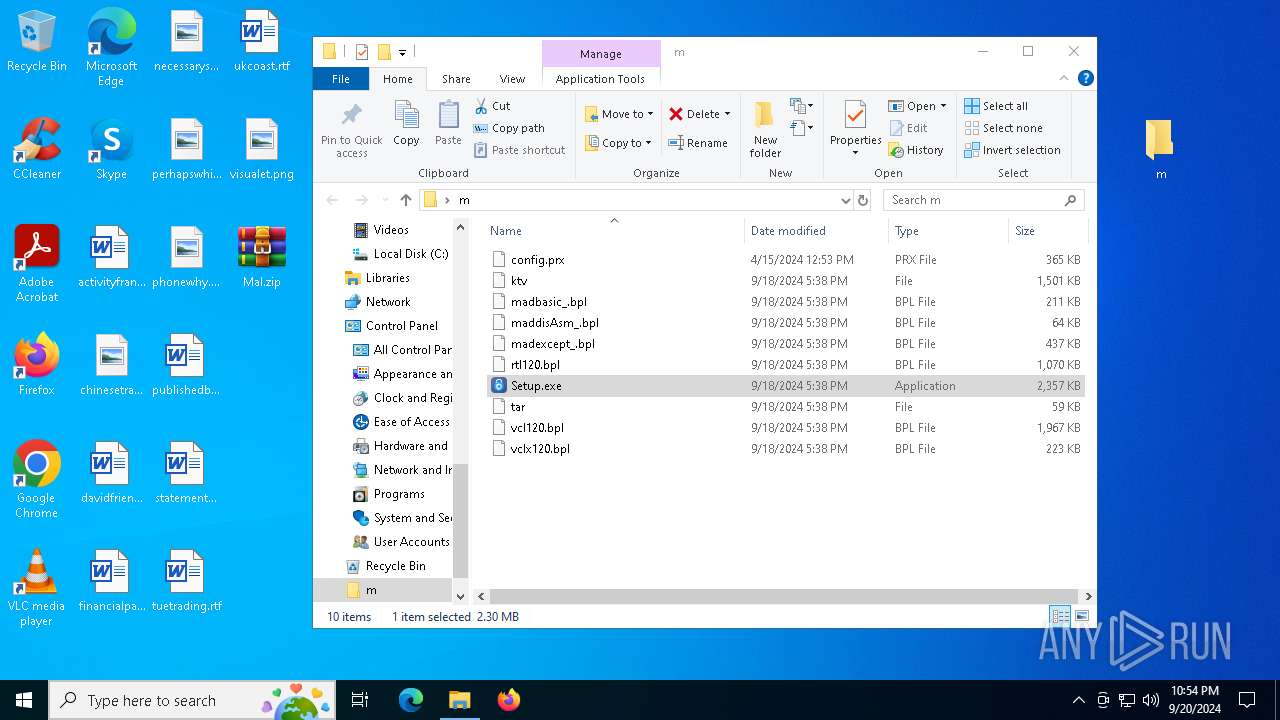
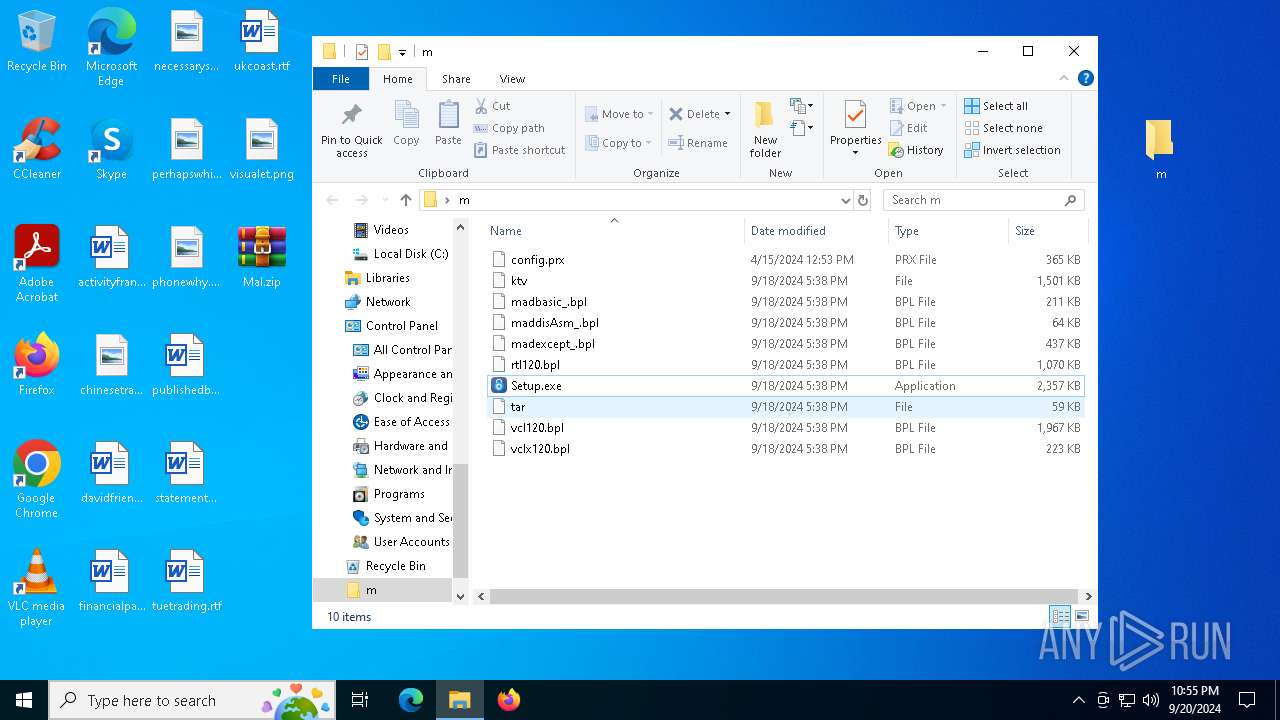
| File name: | Mal.zip |
| Full analysis: | https://app.any.run/tasks/5ad8bfda-d020-48bc-9ebb-2d7528ee170b |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 22:53:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 682D8CA66EDF276A327E64D2E3CC800E |
| SHA1: | EE25B7E00AE19CE0643A1DD7BF91A57B688849EE |
| SHA256: | 3E4F0EA2EFE8FACF91AEB75F0F53AF775B958F8701D0A95EF2E9B8203BB9CCA1 |
| SSDEEP: | 98304:l5YiZoA8PRaoyXuweyAePOz7nOkP9zOJdxplhtwP23UApFbDldPSX7jent5ive0C:EAj6Dc3nv |
MALICIOUS
No malicious indicators.SUSPICIOUS
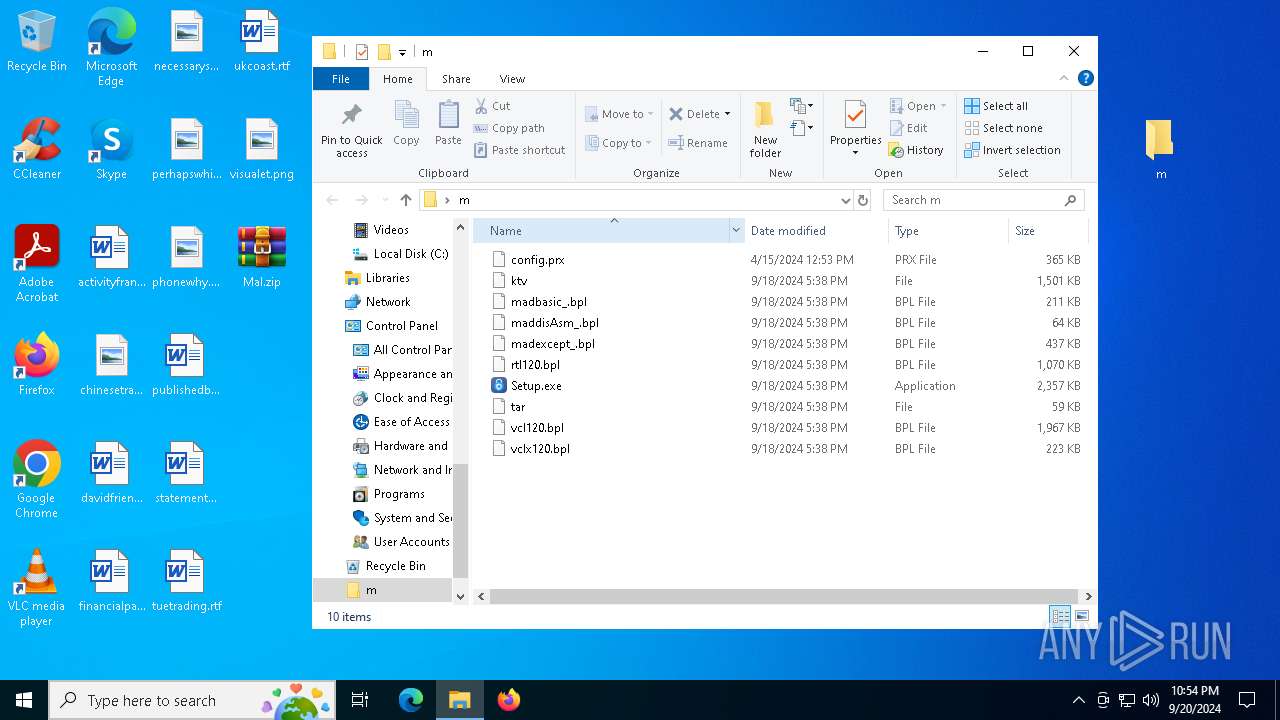
Executable content was dropped or overwritten
- more.com (PID: 4288)
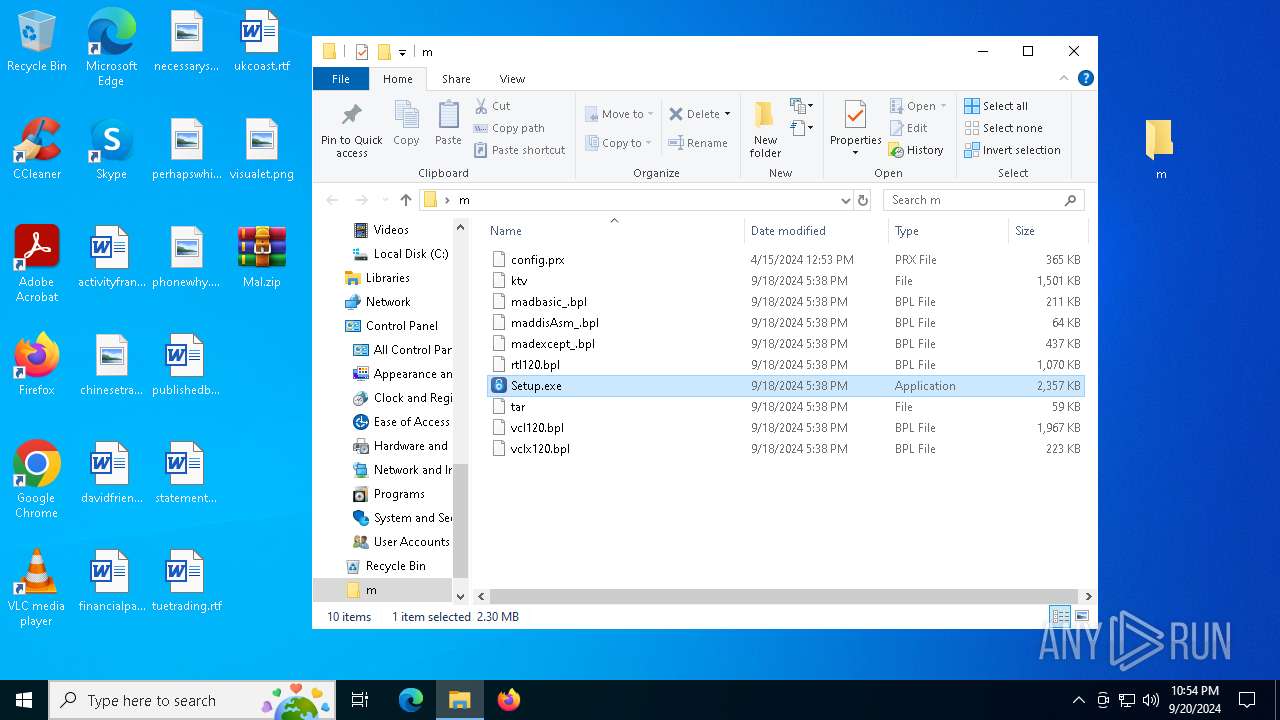
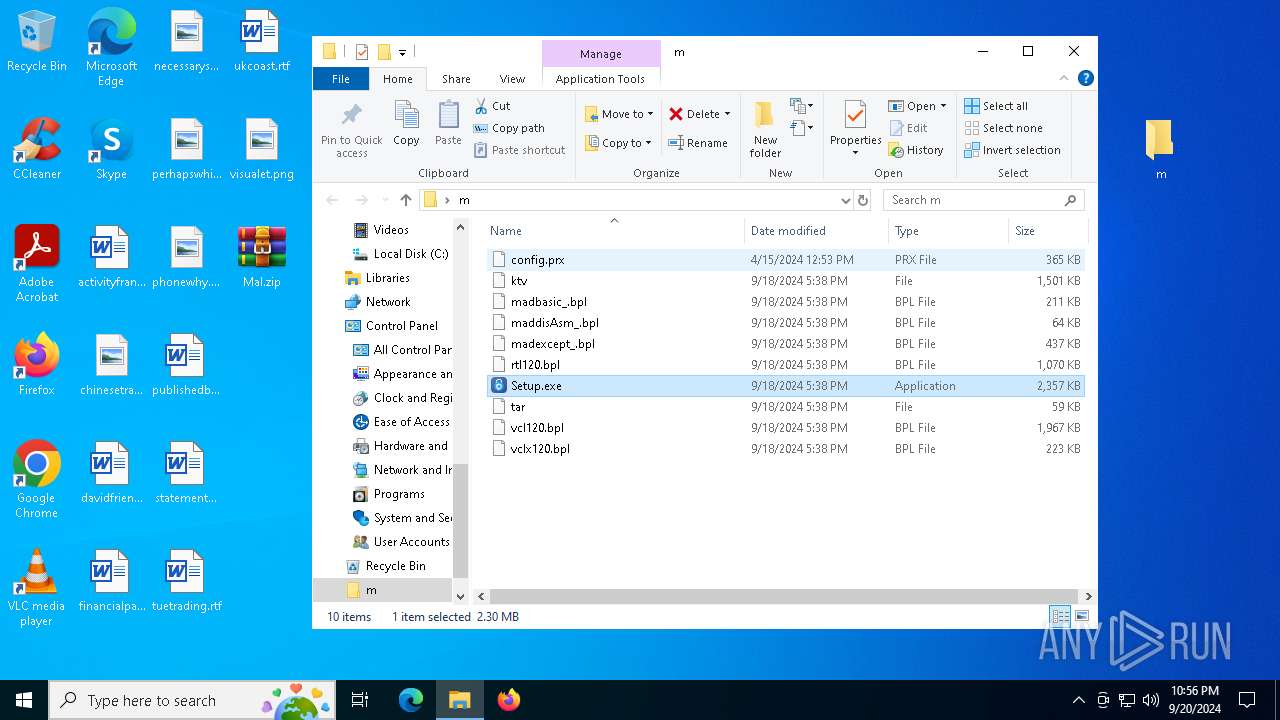
- Setup.exe (PID: 1360)
Starts application with an unusual extension
- Setup.exe (PID: 1360)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 6252)
Manual execution by a user
- Setup.exe (PID: 1360)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:20 12:54:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | m/ |
Total processes
137
Monitored processes
7
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1360 | "C:\Users\admin\Desktop\m\Setup.exe" | C:\Users\admin\Desktop\m\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: HIGH Description: DualSafe Password Manager Exit code: 1 Version: 1.4.0.3 Modules
| |||||||||||||||
| 3476 | C:\ProgramData\updater.exe | C:\ProgramData\updater.exe | more.com | ||||||||||||
User: admin Company: Caphyon Integrity Level: HIGH Description: updater 18.0 Exit code: 0 Version: 18.0 Modules
| |||||||||||||||
| 3784 | C:\Users\admin\AppData\Roaming\lWI\UGZUEUOZFSXEDZIPIPLKZ\StrCmp.exe | C:\Users\admin\AppData\Roaming\lWI\UGZUEUOZFSXEDZIPIPLKZ\StrCmp.exe | — | Setup.exe | |||||||||||
User: admin Company: aaa Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 4288 | C:\WINDOWS\SysWOW64\more.com | C:\Windows\SysWOW64\more.com | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: More Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
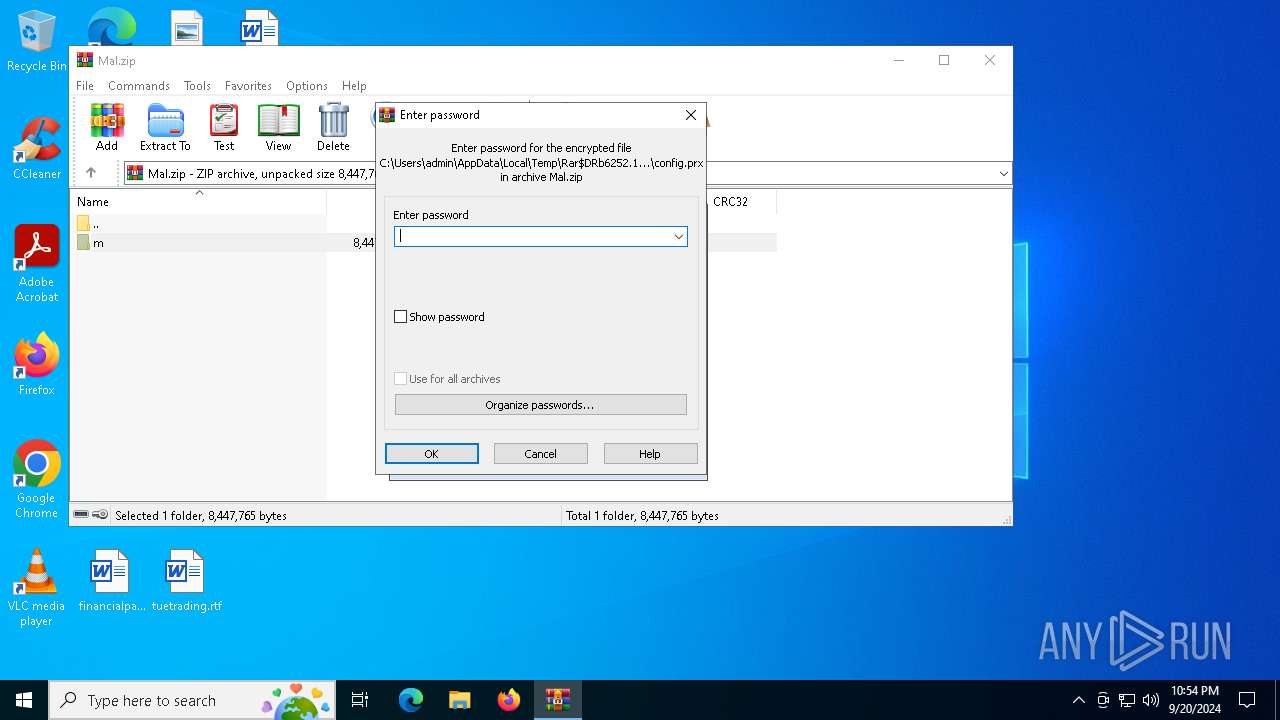
| 6252 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Mal.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6760 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 716
Read events
1 694
Write events
21
Delete events
1
Modification events
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Mal.zip | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6252) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
14
Suspicious files
6
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6252.16327\m\rtl120.bpl | executable | |
MD5:36CA2CA5DDC4998AFE36AA1C52EE67D7 | SHA256:3C0D39726A2404A62C7CF331F5E5FE5C879DEC6AFD2923CEC2E25999A23CC28B | |||
| 4288 | more.com | C:\Users\admin\AppData\Local\Temp\gmxfelqbxk | — | |
MD5:— | SHA256:— | |||
| 6252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6252.16327\m\madexcept_.bpl | executable | |
MD5:98E59596EDD9B888D906C5409E515803 | SHA256:A6CA13AF74A64E4AB5EBB2D12B757CECF1A683CB9CD0AE7906DB1B4B2C8A90C0 | |||
| 6252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6252.16327\m\maddisAsm_.bpl | executable | |
MD5:EF3B47B2EA3884914C13C778FF29EB5B | SHA256:475F7CDFFD8ED4D6F52BD98AE2BB684F1C923A1BE2A692757A9AF788A39B1D87 | |||
| 6252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6252.16327\m\Setup.exe | executable | |
MD5:5D52EF45B6E5BF144307A84C2AF1581B | SHA256:26A24D3B0206C6808615C7049859C2FE62C4DCD87E7858BE40AE8112B0482616 | |||
| 6252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6252.16327\m\vcl120.bpl | binary | |
MD5:13A2734BB2249010514386EBC856B8DA | SHA256:713C21D009000D504D9BCF3CE95D50E74D3933083783DE144DB0A16E2425EBCC | |||
| 6252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6252.16327\m\tar | abr | |
MD5:3B88903619DA3D2041A92839CA686D8F | SHA256:0DBB9F74C850B649951AF0BB4911BF6C5BEEDECB666664202B30BAA5F88FD520 | |||
| 1360 | Setup.exe | C:\Users\admin\AppData\Roaming\lWI\tar | abr | |
MD5:3B88903619DA3D2041A92839CA686D8F | SHA256:0DBB9F74C850B649951AF0BB4911BF6C5BEEDECB666664202B30BAA5F88FD520 | |||
| 1360 | Setup.exe | C:\Users\admin\AppData\Roaming\lWI\madbasic_.bpl | executable | |
MD5:E03A0056E75D3A5707BA199BC2EA701F | SHA256:7826395127E791A883359EA81308174700DA0AF8052CC9853B19FD29C2E4BADB | |||
| 1360 | Setup.exe | C:\Users\admin\AppData\Roaming\lWI\rtl120.bpl | executable | |
MD5:36CA2CA5DDC4998AFE36AA1C52EE67D7 | SHA256:3C0D39726A2404A62C7CF331F5E5FE5C879DEC6AFD2923CEC2E25999A23CC28B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
35
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3180 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5376 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1952 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1952 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3180 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2096 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.176:443 | — | Akamai International B.V. | DE | unknown |
— | — | 52.182.143.210:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3180 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5376 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
helipoctrerow.shop |
| unknown |
keennylrwmqlw.shop |
| malicious |