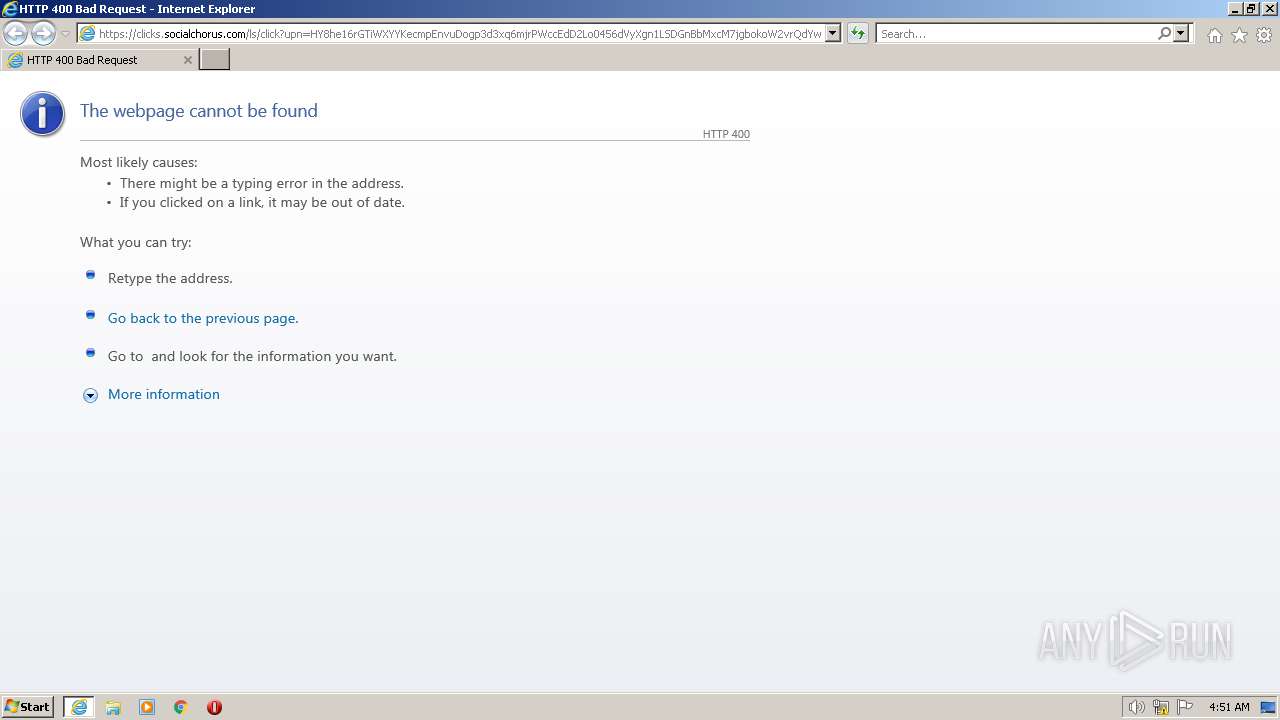
| URL: | https://clicks.socialchorus.com/ls/click?upn=HY8he16rGTiWXYYKecmpEnvuDogp3d3xq6mjrPWccEdD2Lo0456dVyXgn1LSDGnBbMxcM7jgbokoW2vrQdYwUsDAoZFqY5MgBwlsk5RS8L8R2C6w0pCON2DBIkPwJor-2FFZ45n5Ew-2FJXSNgCIU6UlLA-3D-3Dvxg5_7GwCjOJBrWRYNtBUIx8j5XbxNtKBdR6WaxX0Qu-2FF5FT-2Bji05mD7WxohFF-2BGjZLIgbDenKuzZhhQArJLWYnHKVA24Q62AgZeDaKOUGUx |
| Full analysis: | https://app.any.run/tasks/7d86cb22-ec89-4de0-86a8-6c36246d0869 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2023, 03:51:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 05673F064B26C022845C7DA2575DF592 |
| SHA1: | C13E9036B0EA931E8C1EF485F292B089A85173CD |
| SHA256: | 3E3DE5FB296FE68344B9867CEDD6E160EE324FF24D8BD72DA914959069C2A738 |
| SSDEEP: | 6:2UYhXGKIl6x6E8uDYUHB0eMJEolQbpaSxqWh0pT5x/TuoBZ9VIOhBIS86IiVFsXw:2UuNISXDYYMJE4ipzSpT5JTuoBZ9Vbh7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3064 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://clicks.socialchorus.com/ls/click?upn=HY8he16rGTiWXYYKecmpEnvuDogp3d3xq6mjrPWccEdD2Lo0456dVyXgn1LSDGnBbMxcM7jgbokoW2vrQdYwUsDAoZFqY5MgBwlsk5RS8L8R2C6w0pCON2DBIkPwJor-2FFZ45n5Ew-2FJXSNgCIU6UlLA-3D-3Dvxg5_7GwCjOJBrWRYNtBUIx8j5XbxNtKBdR6WaxX0Qu-2FF5FT-2Bji05mD7WxohFF-2BGjZLIgbDenKuzZhhQArJLWYnHKVA24Q62AgZeDaKOUGUx" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3204 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3064 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 554
Read events
14 461
Write events
93
Delete events
0
Modification events
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3064) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
15
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:D7F3C778780A7FD32E1F1F92CB5E1A3A | SHA256:EAA393BA5ABC8840F2F32A2AFEF21B1BC9BFB049A766B15092BE43F99FA73FE7 | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:EEBCBC71A2E48578DFB53363D764B8A4 | SHA256:F3B32F901733ED6BA5F4449B0AB4B4BA5015E6494F21D8C01DA8965B579956B0 | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:CBB6833B69DE5F34206E3E838E908A08 | SHA256:997578250A373CE12E0C022D3185BC4422190D5D2DEF5C0446440C7C3DA0FB89 | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:74EE9EF991116280C6F834DE5A67072F | SHA256:B4A39B3EED0511715943F50719C923AF319BEA7C0A4A50FEAB68F701BC58527B | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:3D7E284DDE1A2E397DD55C4999BB2282 | SHA256:CD7A51A5913934B11965C57B0770D0274AD50798BEADE9641C388912200FC33A | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:85C2C8496C2FD46F909A872891D3BEEF | SHA256:324AB70DCBA95B40C8B0BF21EB1461837D175018AE1931817169D6C54F1D1D71 | |||
| 3064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:261DCA059FFF13A772A89217345F6B8C | SHA256:6F613A7D532496858B28765063FEB2312335B41E7B0E8A38AC8ED1A4C5F68690 | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | binary | |
MD5:677146F5A1998BBC2C8CE07B17EFB918 | SHA256:E0C19CD470B104C1D11B26AFFD95FF067AE0A500DCA5EB5B4C1135830CC437FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
19
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | iexplore.exe | GET | 200 | 52.222.250.185:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3204 | iexplore.exe | GET | 200 | 108.138.2.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 2.02 Kb | whitelisted |
3204 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?82980a2303850cb2 | US | compressed | 4.70 Kb | whitelisted |
3204 | iexplore.exe | GET | 200 | 8.248.149.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?51eb58a6e764e2e9 | US | compressed | 4.70 Kb | whitelisted |
3204 | iexplore.exe | GET | 200 | 52.222.226.205:80 | http://ocsp.r2m02.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRmbQtwnInkvkvr7BNFR%2BS2lTYPjAQUwDFSzVpQw4J8dHHOy%2Bmc%2BXrrguICEAnwVRgaTfWPsO0HguFTIQk%3D | US | der | 471 b | whitelisted |
3204 | iexplore.exe | GET | 200 | 52.222.250.42:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | US | der | 1.39 Kb | shared |
3064 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3064 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2472 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3204 | iexplore.exe | 108.138.17.73:443 | clicks.socialchorus.com | AMAZON-02 | US | unknown |
3204 | iexplore.exe | 52.222.250.185:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
3204 | iexplore.exe | 52.222.250.42:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
3204 | iexplore.exe | 52.222.226.205:80 | ocsp.r2m02.amazontrust.com | AMAZON-02 | US | unknown |
3064 | iexplore.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
3064 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
3064 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clicks.socialchorus.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m02.amazontrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |