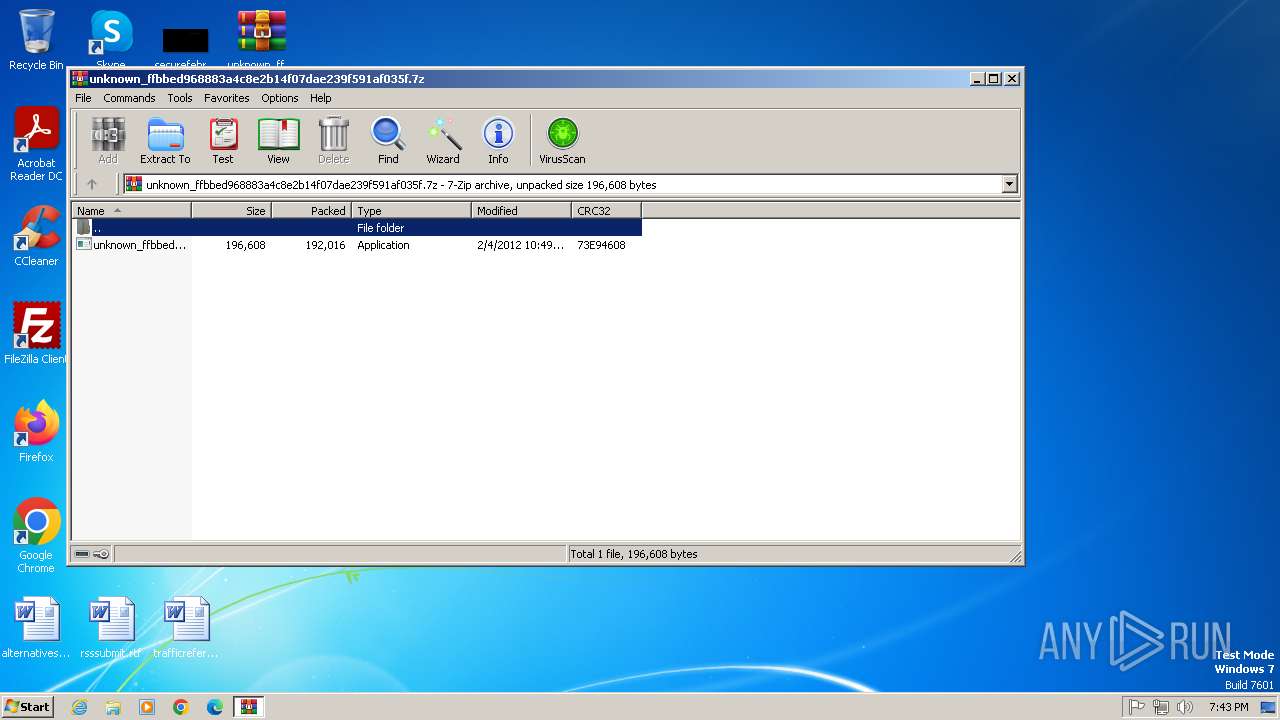
| File name: | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.7z |
| Full analysis: | https://app.any.run/tasks/49bfd6ea-c855-45eb-b616-15e284ffc230 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 18:43:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 1AB15F71B81F098D9E5E55BE9BC813F8 |
| SHA1: | 6CBA7921A947F285A808ADEEBDA62CD9897583B8 |
| SHA256: | 3E341B2F12166E52187CAF8F6173A01EA9D29DA57093FB2719140C309282CA25 |
| SSDEEP: | 6144:to9877A9OV8ZI6CACVB7hVQ7iynyM/MbAGNvFVEv+0:6jwyZI6L+B7hVEiynYAGNnw |
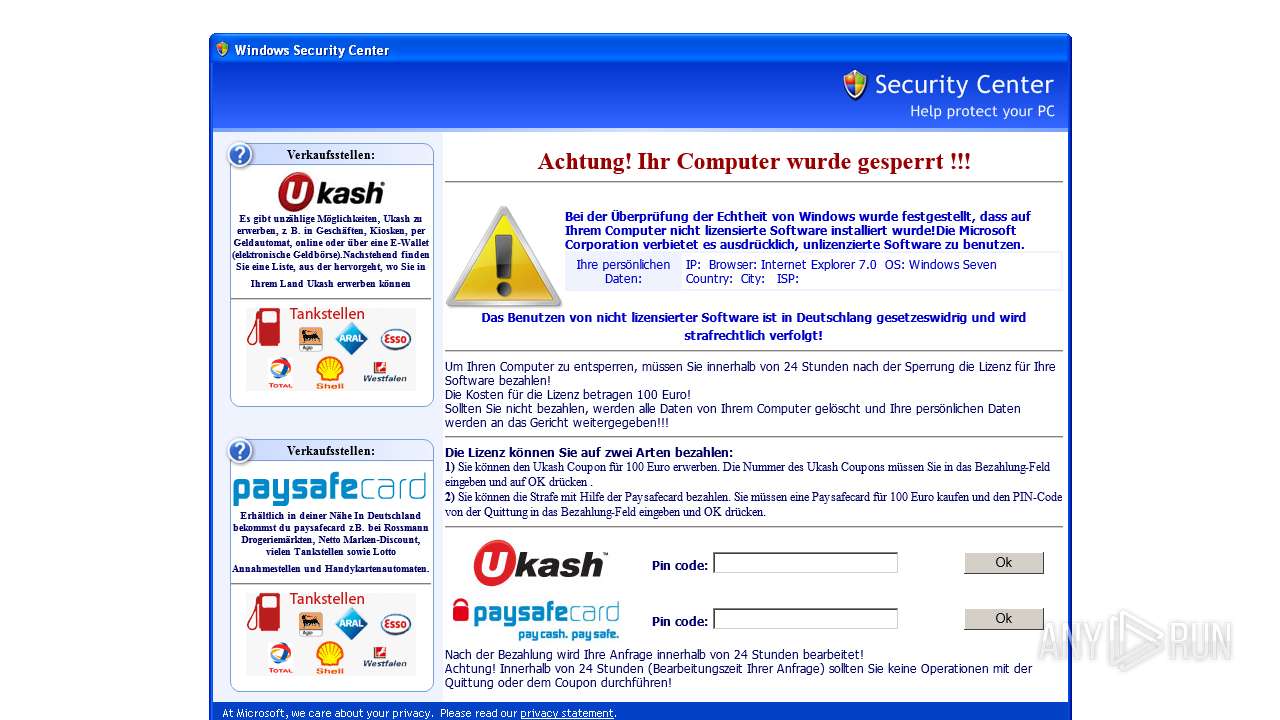
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2624)
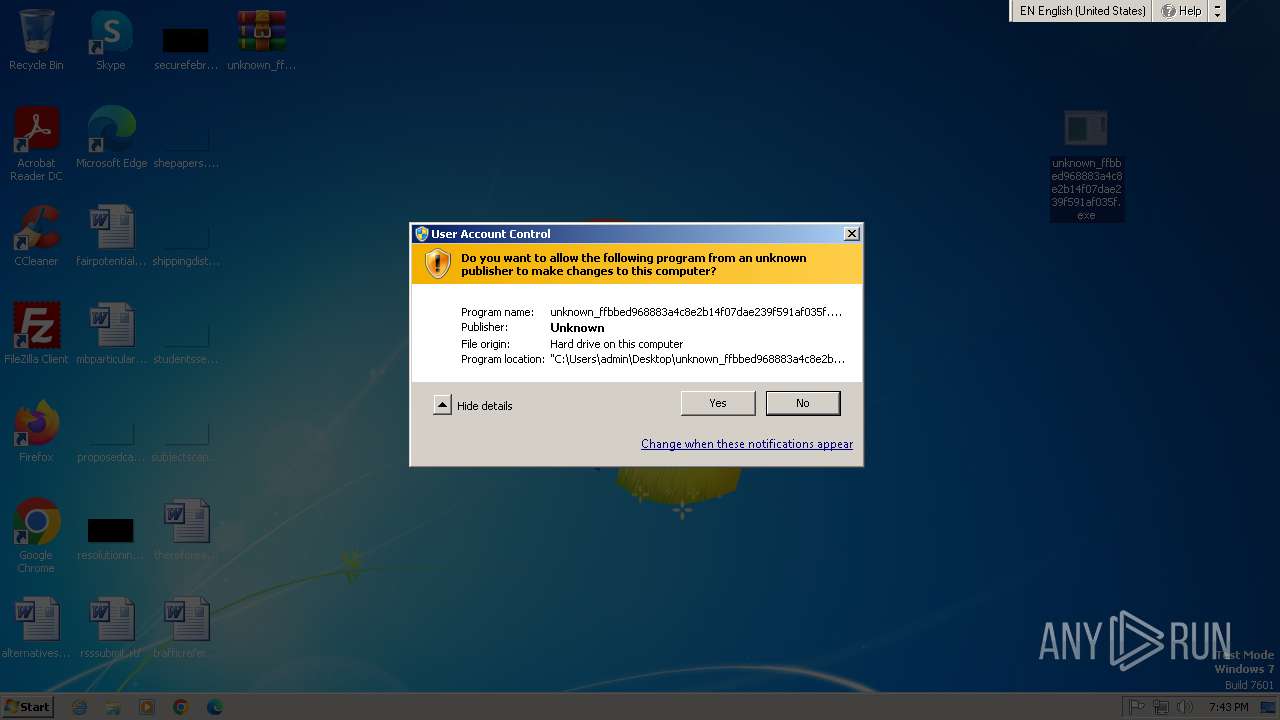
Changes the autorun value in the registry
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
SUSPICIOUS
Reads Microsoft Outlook installation path
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Reads the Internet Settings
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Reads security settings of Internet Explorer
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Reads Internet Explorer settings
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Connects to the server without a host name
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Checks for external IP
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
INFO
Reads the computer name
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
The sample compiled with english language support
- WinRAR.exe (PID: 2624)
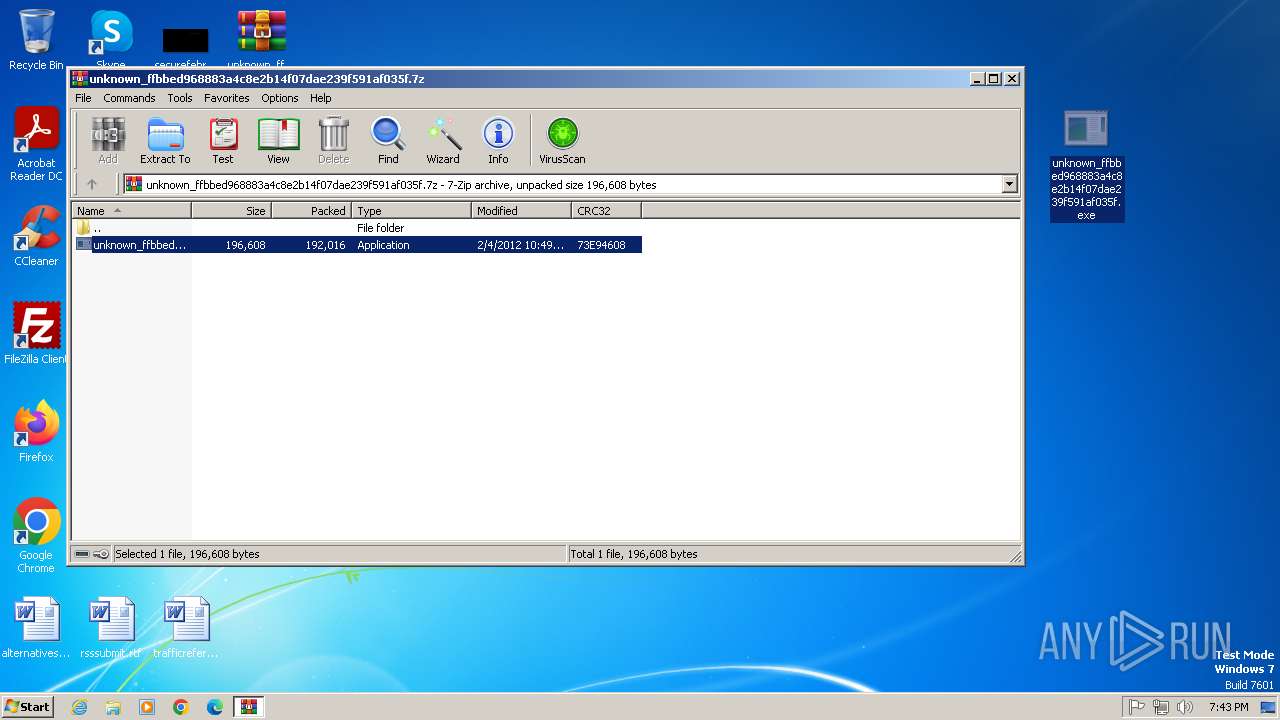
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2624)
Checks supported languages
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Reads the machine GUID from the registry
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Checks proxy server information
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Manual execution by a user
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Creates files or folders in the user directory
- unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe (PID: 1400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2012:02:04 10:49:44+00:00 |
| ArchivedFileName: | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe |
Total processes
40
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1400 | "C:\Users\admin\Desktop\unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe" | C:\Users\admin\Desktop\unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | explorer.exe | ||||||||||||
User: admin Company: Orb Networks Integrity Level: HIGH Description: Ether Proxy Darken Version: 4.9 Modules
| |||||||||||||||
| 2624 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
3 887
Read events
3 393
Write events
488
Delete events
6
Modification events
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.7z | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2624) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2624 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2624.41028\unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | executable | |
MD5:879E2599BD02078024900E3E61EF93E6 | SHA256:3387570FDE0116D0599BF4C7823CDD18A66943E91C49B2226E33649A3D12D927 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
8
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1400 | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | GET | 404 | 95.215.63.95:80 | http://95.215.63.95/i.php?a=106 | unknown | — | — | malicious |
1400 | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | GET | 404 | 149.248.7.185:80 | http://tools.ip2location.com/ib2/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1400 | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | 95.215.63.95:80 | — | Briod SA | ES | malicious |
1400 | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | 149.248.7.185:80 | tools.ip2location.com | AS-CHOOPA | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
tools.ip2location.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1400 | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | A Network Trojan was detected | ET MALWARE Fake Variation of Mozilla 4.0 - Likely Trojan |
1400 | unknown_ffbbed968883a4c8e2b14f07dae239f591af035f.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - ip2location.com |