| File name: | telegramgroupscraper.com_Setup.exe |
| Full analysis: | https://app.any.run/tasks/8b7e3cca-60cf-4f32-a717-ef271cbc7f44 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 01:25:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9BFE06B6D19F1AB32CE9CEA7C38F455E |
| SHA1: | 39A32C1BE053DDA7A8E2BB38D9F4CF601A213D74 |
| SHA256: | 3E2C7630BC24CE949233704478E4E49B8EE48416AAA29EE2F9F16137F1FD837C |
| SSDEEP: | 98304:cSi6ve4zOknJ2rBiy/w61r2M1drHGZCR+DidXvh6d204OOR5qHW:vve4FnGBiYt5nrHGsegJ6M8YY2 |
MALICIOUS
Drops the executable file immediately after the start
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Application was dropped or rewritten from another process
- telegramgroupscraper.com.exe (PID: 3360)
SUSPICIOUS
Reads the Windows owner or organization settings
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Executable content was dropped or overwritten
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Changes default file association
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Reads the Internet Settings
- telegramgroupscraper.com.exe (PID: 3360)
INFO
Application was dropped or rewritten from another process
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Checks supported languages
- telegramgroupscraper.com_Setup.exe (PID: 856)
- telegramgroupscraper.com_Setup.tmp (PID: 548)
- telegramgroupscraper.com.exe (PID: 3360)
Reads the computer name
- telegramgroupscraper.com_Setup.tmp (PID: 548)
- telegramgroupscraper.com.exe (PID: 3360)
Drops a file that was compiled in debug mode
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Creates a software uninstall entry
- telegramgroupscraper.com_Setup.tmp (PID: 548)
Application launched itself
- iexplore.exe (PID: 3808)
Manual execution by a user
- explorer.exe (PID: 3316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2020-Nov-15 09:48:30 |
| Detected languages: |
|
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | telegramgroupscraper.com |
| FileDescription: | telegramgroupscraper.com Setup |
| FileVersion: | - |
| LegalCopyright: | - |
| OriginalFileName: | - |
| ProductName: | telegramgroupscraper.com |
| ProductVersion: | telegramgroupscraper.com |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 80 |
| e_cp: | 2 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | 15 |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | 26 |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 10 |
| TimeDateStamp: | 2020-Nov-15 09:48:30 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 734748 | 735232 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.35606 |
.itext | 741376 | 5768 | 6144 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.97275 |
.data | 749568 | 14244 | 14336 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.0444 |
.bss | 765952 | 28136 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.idata | 794624 | 3894 | 4096 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.8987 |
.didata | 798720 | 420 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.75636 |
.edata | 802816 | 154 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.87222 |
.tls | 806912 | 24 | 0 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rdata | 811008 | 93 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.38389 |
.rsrc | 815104 | 18432 | 18432 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.42143 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.25755 | 296 | UNKNOWN | Dutch - Netherlands | RT_ICON |
2 | 3.47151 | 1384 | UNKNOWN | Dutch - Netherlands | RT_ICON |
3 | 3.91708 | 744 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4 | 3.91366 | 2216 | UNKNOWN | Dutch - Netherlands | RT_ICON |
4086 | 3.16547 | 864 | UNKNOWN | UNKNOWN | RT_STRING |
4087 | 3.40938 | 608 | UNKNOWN | UNKNOWN | RT_STRING |
4088 | 3.31153 | 1116 | UNKNOWN | UNKNOWN | RT_STRING |
4089 | 3.33977 | 1036 | UNKNOWN | UNKNOWN | RT_STRING |
4090 | 3.36723 | 724 | UNKNOWN | UNKNOWN | RT_STRING |
4091 | 3.33978 | 184 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
kernel32.dll (delay-loaded) |
netapi32.dll |
oleaut32.dll |
user32.dll |
version.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
dbkFCallWrapperAddr | 1 | 779836 |
__dbk_fcall_wrapper | 2 | 53408 |
TMethodImplementationIntercept | 3 | 344160 |
Total processes
40
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
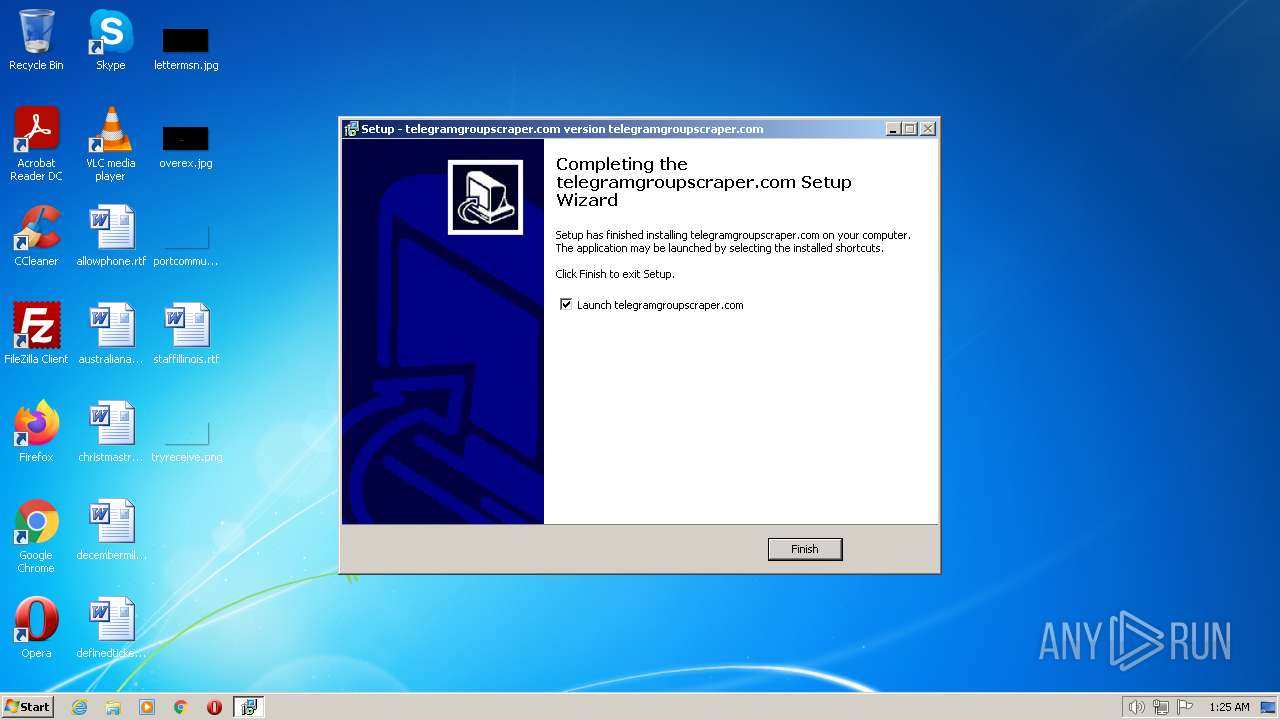
| 548 | "C:\Users\admin\AppData\Local\Temp\is-HNIQI.tmp\telegramgroupscraper.com_Setup.tmp" /SL5="$50198,3328045,780800,C:\Users\admin\AppData\Local\Temp\telegramgroupscraper.com_Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-HNIQI.tmp\telegramgroupscraper.com_Setup.tmp | telegramgroupscraper.com_Setup.exe | ||||||||||||
User: admin Company: telegramgroupscraper.com Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 856 | "C:\Users\admin\AppData\Local\Temp\telegramgroupscraper.com_Setup.exe" | C:\Users\admin\AppData\Local\Temp\telegramgroupscraper.com_Setup.exe | — | Explorer.EXE | |||||||||||
User: admin Company: telegramgroupscraper.com Integrity Level: MEDIUM Description: telegramgroupscraper.com Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3808 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3316 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
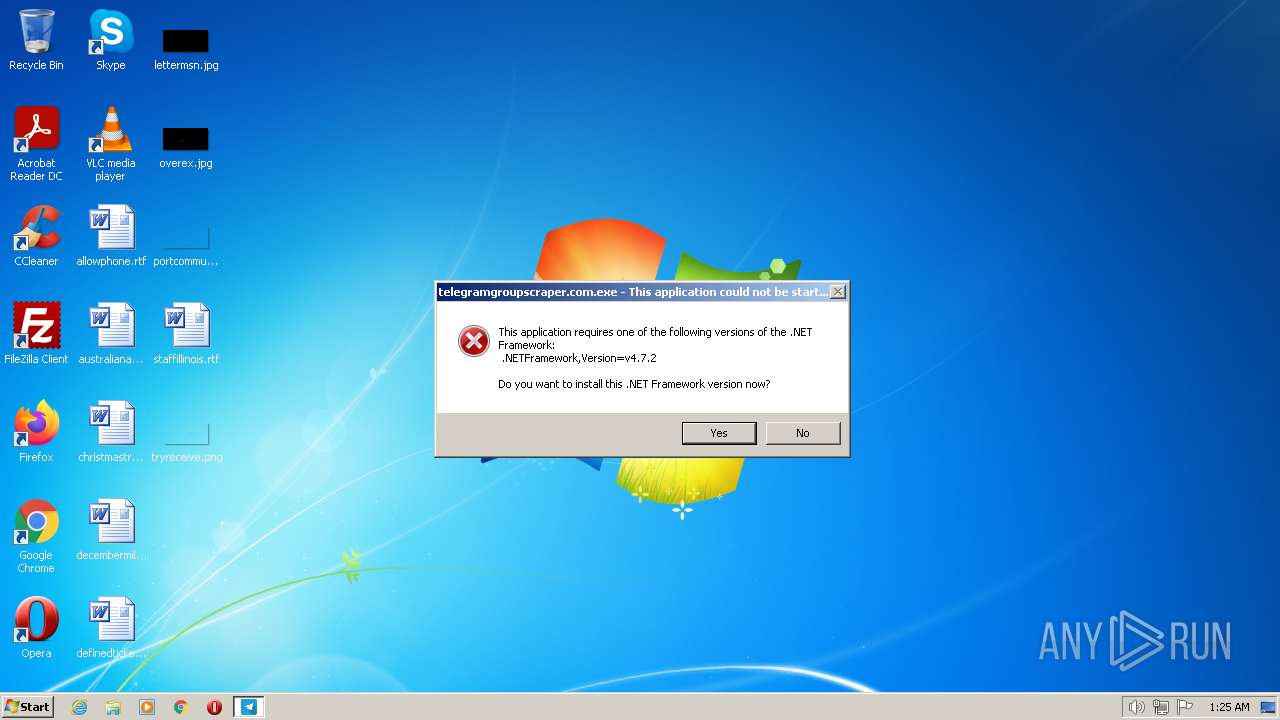
| 3360 | "C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\telegramgroupscraper.com.exe" | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\telegramgroupscraper.com.exe | — | telegramgroupscraper.com_Setup.tmp | |||||||||||
User: admin Integrity Level: MEDIUM Description: telegramgroupscraper.com Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
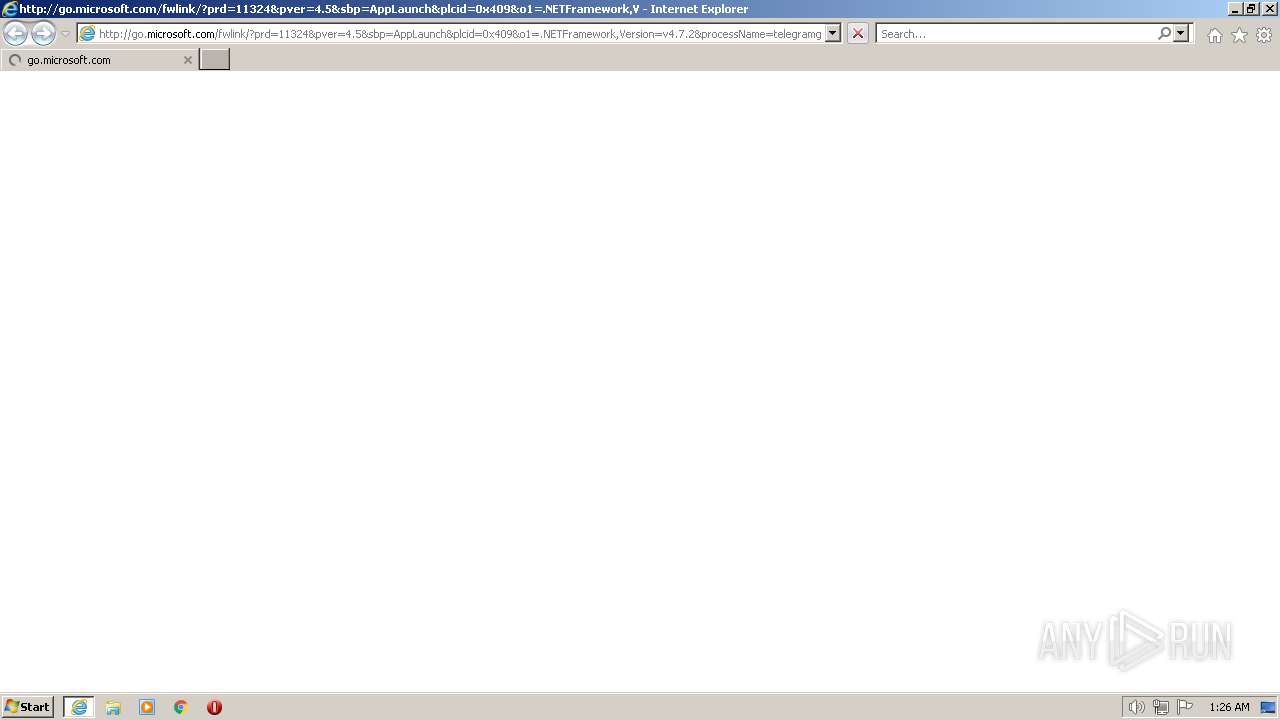
| 3808 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=telegramgroupscraper.com.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | telegramgroupscraper.com.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
11 952
Read events
11 823
Write events
122
Delete events
7
Modification events
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 240200005AC838A51109D901 | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: EC73CC7EDF2546CFCF735FC5374C37D0C33A8911CFA6F31A27C58BF7240399CA | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\telegramgroupscraper.com.exe | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 8219484DFF65C033446881F7C13640758DCC6E3FE2BC0828DFBCC4D538A5FF9E | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CLASSES_ROOT\.myp\OpenWithProgids |
| Operation: | write | Name: | telegramgroupscraper.comFile.myp |
Value: | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CLASSES_ROOT\telegramgroupscraper.comFile.myp |
| Operation: | write | Name: | (default) |
Value: telegramgroupscraper.com File | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CLASSES_ROOT\telegramgroupscraper.comFile.myp\DefaultIcon |
| Operation: | write | Name: | (default) |
Value: C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\telegramgroupscraper.com.exe,0 | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CLASSES_ROOT\telegramgroupscraper.comFile.myp\shell\open\command |
| Operation: | write | Name: | (default) |
Value: "C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\telegramgroupscraper.com.exe" "%1" | |||
| (PID) Process: | (548) telegramgroupscraper.com_Setup.tmp | Key: | HKEY_CLASSES_ROOT\Applications\telegramgroupscraper.com.exe\SupportedTypes |
| Operation: | write | Name: | .myp |
Value: | |||
Executable files
41
Suspicious files
12
Text files
33
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\is-PBRRG.tmp | executable | |
MD5:— | SHA256:— | |||
| 856 | telegramgroupscraper.com_Setup.exe | C:\Users\admin\AppData\Local\Temp\is-HNIQI.tmp\telegramgroupscraper.com_Setup.tmp | executable | |
MD5:— | SHA256:— | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\unins000.exe | executable | |
MD5:— | SHA256:— | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\telegramgroupscraper.com.exe | executable | |
MD5:— | SHA256:— | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\is-3NGID.tmp | executable | |
MD5:2402C4F4AF67AC863292AE95FE40BFF4 | SHA256:AAAE75E3FAA1FCCF0DE0B33B1A4EF6FE2DABB0F3B05E046CCE31ECACD49CB6E9 | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\is-0S1LI.tmp | binary | |
MD5:027432065A3C483883BEFB13F8F162FB | SHA256:AB8143C0C0876BC285F208B85BDE0E2C5C54343B1139BD25B570B3D6B52912CF | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\HtmlAgilityPack.xml | xml | |
MD5:1C935C8213A5DDAFFD71838B76C4FDFB | SHA256:AEC148366FE5CCD4F5C8DEBD53F718C8B3720B7BEE9F1E531001327053483AB5 | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\is-EHDB1.tmp | pdb | |
MD5:9002EF1EDC7ED8BA88CCF58AFD89CA69 | SHA256:5EC04202765C637FAFD7BF443A1BB486A289E17130567E34402203252A5C076C | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\is-JT5KK.tmp | executable | |
MD5:— | SHA256:— | |||
| 548 | telegramgroupscraper.com_Setup.tmp | C:\Users\admin\AppData\Local\Programs\telegramgroupscraper.com\is-91TO7.tmp | executable | |
MD5:6D6423834A78BED27700A095FACAA678 | SHA256:4183655DE0B44E42B1A177C86A0042376AEA2025AF9923EAE147E74DE2FAD7E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
15
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3808 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
2668 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?09d5eccd6ad25f4d | US | compressed | 4.70 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?18d8ceee3bd64f70 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2668 | iexplore.exe | 96.16.143.41:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
2668 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2668 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
3808 | iexplore.exe | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3808 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | EDGECAST | GB | whitelisted |
2668 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |