| File name: | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc |
| Full analysis: | https://app.any.run/tasks/a9c5176a-8c35-4f67-ad0e-a2cbef24ad8a |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 02:37:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | C8BECD5202DBFB5B1F6F6A06112391F0 |
| SHA1: | 9BCEC14E0FC8B292E851DDC4E33EC6292A1DA157 |
| SHA256: | 3E0B56DB0AD5317073B24553E67CBD7CAE09ACBEB9CBEF26DF46CED7C52F87FF |
| SSDEEP: | 98304:kB4RiX/7+xK76JL2yt/KmP7B+LdhVOxRBAaiKc36/srnQpgGmcmGDhrHM:oR |
MALICIOUS
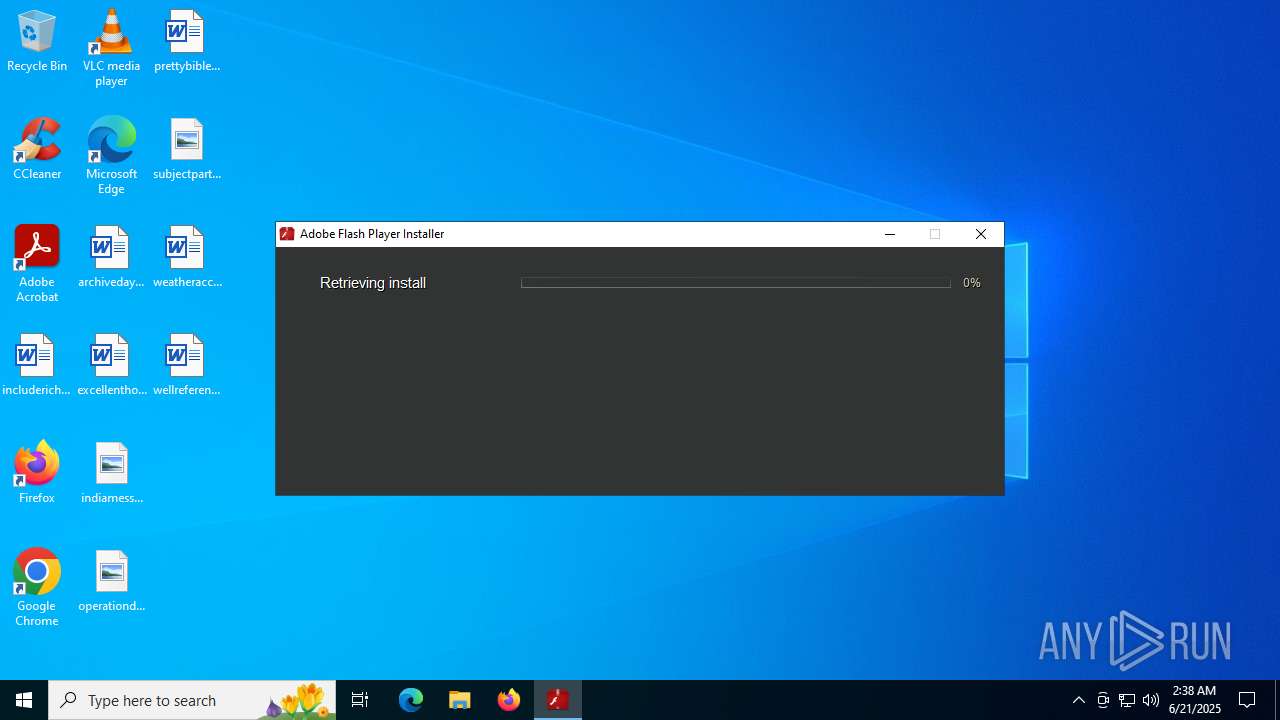
Executing a file with an untrusted certificate
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
- 6AC0.tmp (PID: 6620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Starts itself from another location
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
Starts application with an unusual extension
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
Reads security settings of Internet Explorer
- 6AC0.tmp (PID: 6620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Application launched itself
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
Adds/modifies Windows certificates
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
There is functionality for taking screenshot (YARA)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Reads Microsoft Outlook installation path
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Reads Internet Explorer settings
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
INFO
Reads the computer name
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
- 6AC0.tmp (PID: 6620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
The sample compiled with english language support
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
- 6AC0.tmp (PID: 6620)
Checks supported languages
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
- 6AC0.tmp (PID: 6620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
Reads the machine GUID from the registry
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 3652)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Process checks computer location settings
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
- 6AC0.tmp (PID: 6620)
Reads the software policy settings
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
- slui.exe (PID: 5628)
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 4476)
Checks proxy server information
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
- slui.exe (PID: 5628)
Creates files or folders in the user directory
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Mpress packer has been detected
- 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe (PID: 620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2006:10:19 18:35:31+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 172032 |
| InitializedDataSize: | 2598912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d311 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.5.4.24 |
| ProductVersionNumber: | 2.0.2.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Adobe |
| FileDescription: | Adobe Installation Helper |
| FileVersion: | 3.5.4.24 |
| InternalName: | host.exe |
| LegalCopyright: | Copyright © Adobe Systems Incorporated |
| OriginalFileName: | host.exe |
| ProductName: | Adobe Installation Helper |
| ProductVersion: | 2.0.2.4 |
Total processes
137
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | "C:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe" -Elevated | C:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | ||||||||||||
User: admin Company: Adobe Integrity Level: HIGH Description: Adobe Installation Helper Version: 3.5.4.24 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe" | C:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe Installation Helper Exit code: 0 Version: 3.5.4.24 Modules
| |||||||||||||||
| 4476 | "C:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe" | C:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | — | 6AC0.tmp | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe Installation Helper Exit code: 0 Version: 3.5.4.24 Modules
| |||||||||||||||
| 5628 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6620 | "C:\Users\admin\AppData\Local\Temp\6AC0.tmp" --pingC:\Users\admin\Desktop\2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe 5D480C0879DC326ABE50C635527652C40FA1C0AFB6BCCF718EA96136B6F7E6A773860AC1885EACEA701B107DA9799AAA39930F3CE5139F5BD9D0E5467B370A28 | C:\Users\admin\AppData\Local\Temp\6AC0.tmp | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | ||||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe Installation Helper Exit code: 0 Version: 3.5.4.24 Modules
| |||||||||||||||
Total events
12 394
Read events
12 385
Write events
6
Delete events
3
Modification events
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 742C3192E607E424EB4549542BE1BBC53E6174E2 |
Value: | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\742C3192E607E424EB4549542BE1BBC53E6174E2 |
| Operation: | write | Name: | Blob |
Value: 04000000010000001000000010FC635DF6263E0DF325BE5F79CD67677E0000000100000008000000000010C51E92D2011D000000010000001000000027B3517667331CE2C1E74002B5FF2298620000000100000020000000E7685634EFACF69ACE939A6B255B7B4FABEF42935B50A265ACB5CB6027E44E7009000000010000002A000000302806082B0601050507030206082B0601050507030306082B0601050507030406082B0601050507030119000000010000001000000091161B894B117ECDC257628DB460CC04030000000100000014000000742C3192E607E424EB4549542BE1BBC53E6174E20F0000000100000010000000D7C63BE0837DBABF881D4FBF5F986AD80B000000010000004600000056006500720069005300690067006E00200043006C006100730073002000330020005000750062006C006900630020005000720069006D00610072007900200043004100000053000000010000002400000030223020060A2B0601040182375E010130123010060A2B0601040182373C0101030200C0140000000100000014000000E27F7BD877D5DF9E0A3F9EB4CB0E2EA9EFDB69777A000000010000000E000000300C060A2B0601040182375E010268000000010000000800000000003DB65BD9D5012000000001000000400200003082023C308201A5021070BAE41D10D92934B638CA7B03CCBABF300D06092A864886F70D0101020500305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479301E170D3936303132393030303030305A170D3238303830313233353935395A305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F7269747930819F300D06092A864886F70D010101050003818D0030818902818100C95C599EF21B8A0114B410DF0440DBE357AF6A45408F840C0BD133D9D911CFEE02581F25F72AA84405AAEC031F787F9E93B99A00AA237DD6AC85A26345C77227CCF44CC67571D239EF4F42F075DF0A90C68E206F980FF8AC235F702936A4C986E7B19A20CB53A585E73DBE7D9AFE244533DC7615ED0FA271644C652E816845A70203010001300D06092A864886F70D010102050003818100BB4C122BCF2C26004F1413DDA6FBFC0A11848CF3281C67922F7CB6C5FADFF0E895BC1D8F6C2CA851CC73D8A4C053F04ED626C076015781925E21F1D1B1FFE7D02158CD6917E3441C9C194439895CDC9C000F568D0299EDA290454CE4BB10A43DF032030EF1CEF8E8C9518CE6629FE69FC07DB7729CC9363A6B9F4EA8FF640D64 | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\742C3192E607E424EB4549542BE1BBC53E6174E2 |
| Operation: | write | Name: | Blob |
Value: 5C00000001000000040000000004000068000000010000000800000000003DB65BD9D5017A000000010000000E000000300C060A2B0601040182375E0102140000000100000014000000E27F7BD877D5DF9E0A3F9EB4CB0E2EA9EFDB697753000000010000002400000030223020060A2B0601040182375E010130123010060A2B0601040182373C0101030200C00B000000010000004600000056006500720069005300690067006E00200043006C006100730073002000330020005000750062006C006900630020005000720069006D0061007200790020004300410000000F0000000100000010000000D7C63BE0837DBABF881D4FBF5F986AD8030000000100000014000000742C3192E607E424EB4549542BE1BBC53E6174E219000000010000001000000091161B894B117ECDC257628DB460CC0409000000010000002A000000302806082B0601050507030206082B0601050507030306082B0601050507030406082B06010505070301620000000100000020000000E7685634EFACF69ACE939A6B255B7B4FABEF42935B50A265ACB5CB6027E44E701D000000010000001000000027B3517667331CE2C1E74002B5FF22987E0000000100000008000000000010C51E92D20104000000010000001000000010FC635DF6263E0DF325BE5F79CD67672000000001000000400200003082023C308201A5021070BAE41D10D92934B638CA7B03CCBABF300D06092A864886F70D0101020500305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479301E170D3936303132393030303030305A170D3238303830313233353935395A305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F7269747930819F300D06092A864886F70D010101050003818D0030818902818100C95C599EF21B8A0114B410DF0440DBE357AF6A45408F840C0BD133D9D911CFEE02581F25F72AA84405AAEC031F787F9E93B99A00AA237DD6AC85A26345C77227CCF44CC67571D239EF4F42F075DF0A90C68E206F980FF8AC235F702936A4C986E7B19A20CB53A585E73DBE7D9AFE244533DC7615ED0FA271644C652E816845A70203010001300D06092A864886F70D010102050003818100BB4C122BCF2C26004F1413DDA6FBFC0A11848CF3281C67922F7CB6C5FADFF0E895BC1D8F6C2CA851CC73D8A4C053F04ED626C076015781925E21F1D1B1FFE7D02158CD6917E3441C9C194439895CDC9C000F568D0299EDA290454CE4BB10A43DF032030EF1CEF8E8C9518CE6629FE69FC07DB7729CC9363A6B9F4EA8FF640D64 | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 4F65566336DB6598581D584A596C87934D5F2AB4 |
Value: | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\4F65566336DB6598581D584A596C87934D5F2AB4 |
| Operation: | write | Name: | Blob |
Value: 5C00000001000000040000000004000019000000010000001000000091161B894B117ECDC257628DB460CC040300000001000000140000004F65566336DB6598581D584A596C87934D5F2AB41D000000010000001000000027B3517667331CE2C1E74002B5FF2298140000000100000014000000E27F7BD877D5DF9E0A3F9EB4CB0E2EA9EFDB697709000000010000002A000000302806082B0601050507030406082B0601050507030206082B0601050507030306082B060105050703010B000000010000003800000056006500720069005300690067006E00200043006C006100730073002000330020005000720069006D006100720079002000430041000000040000000100000010000000782A02DFDB2E14D5A75F0ADFB68E9C5D0F0000000100000010000000F1BBAC2D9038DDEC8DB173C53BC72A2A2000000001000000410200003082023D308201A6021100E49EFDF33AE80ECFA5113E19A4240232300D06092A864886F70D0101020500305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F72697479301E170D3936303132393030303030305A170D3034303130373233353935395A305F310B300906035504061302555331173015060355040A130E566572695369676E2C20496E632E31373035060355040B132E436C6173732033205075626C6963205072696D6172792043657274696669636174696F6E20417574686F7269747930819F300D06092A864886F70D010101050003818D0030818902818100C95C599EF21B8A0114B410DF0440DBE357AF6A45408F840C0BD133D9D911CFEE02581F25F72AA84405AAEC031F787F9E93B99A00AA237DD6AC85A26345C77227CCF44CC67571D239EF4F42F075DF0A90C68E206F980FF8AC235F702936A4C986E7B19A20CB53A585E73DBE7D9AFE244533DC7615ED0FA271644C652E816845A70203010001300D06092A864886F70D0101020500038181006170EC2F3F9EFD2BE6685421B06779080C2096318A0D7ABEB626DF792C22694936E397776261A232D77A542136BA02C934E725DA4435B0D25C805DB394F8F9ACEEA460752A1F954923B14A7CF4B34772215B7E97AB54AC62E75DECAE9BD2C9B224FB82ADE967154BBAAAA6F097A0F6B0975700C80C3C09A08204BA41DAF799A4 | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (620) 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
5
Suspicious files
1
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\icon-complete-error[1].gif | image | |
MD5:9C0FB23D2B2F05454E4CE898B2F79052 | SHA256:DEFF98C9B6E64B7BBC2516EAE50E5BEAB2C2A4EC8C3942525B5197C7F5BA6166 | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\icon-complete[1].gif | image | |
MD5:17667B07D2444A37AC55753434371AAB | SHA256:E1061FB7966D14C69DF93A15BDDD6D0331A79B162D9D788632B4E35FA5406A7F | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\mainwindow[1].css | text | |
MD5:263326825DF0644CC94694B9709A5F4C | SHA256:F4397303A819A98CB2DA22C2B960E34D42ECC8CBAA555C5B968D12B727846B6E | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\compact.min[1].js | binary | |
MD5:270FAD4C7A848ABBA47DA44EFE9B78C0 | SHA256:396D96CFD7F81E04FF79BA1194066765334FE932D9A6A1F590074F35E4982C8C | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\icon-blank[1].gif | image | |
MD5:047722E6940449B36DC7507352170004 | SHA256:E749A443EF9436DB67B0FF16DBB3BBBF4CC7E3BA3424EA83F1EE9181B74DCFAA | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\logo-adobe[1].gif | image | |
MD5:2D32D489B011C582232B70FEBFC866B0 | SHA256:3829F33115FF4CD0FC3EC2505FB4603578F040FEBEABAFFF16C9446D53E68A3B | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\bg-close-program[1].png | image | |
MD5:7B5E8F1FFFE864DE7B1F916D2D036904 | SHA256:50C0578EFC9C2E4AF433860BAF9BB6E24C6E1C948186382F7AEA2871A8B7DD62 | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\button-left[1].png | image | |
MD5:1BA47DCDFDFD441272C7194499AB3368 | SHA256:97FDDBD8DEAD2451387D2E50D0991BB78BEBB86B4A4C2CF504BB6F23CD1D4302 | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\bg-download-bar-full[1].png | image | |
MD5:90A9AFFBB7538CBB4E09AA3D96F15BA9 | SHA256:6969C34E593E50249C6E4D53305AC58B556F0F33AEF3F05D789CB103ABEB37B2 | |||
| 620 | 2025-06-21_c8becd5202dbfb5b1f6f6a06112391f0_amadey_elex_gcleaner_smoke-loader_stealc.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\bg-header-error[1].gif | image | |
MD5:3A05B98BBC864762A5CFC1C2EF14AE54 | SHA256:7785156C3B5B7DD395260C85DE82A5DD3435322376F85E9E98693B083FBFD770 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
26
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1488 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1488 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1488 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1488 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
get.adobe.com |
| whitelisted |
www.adobe.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |