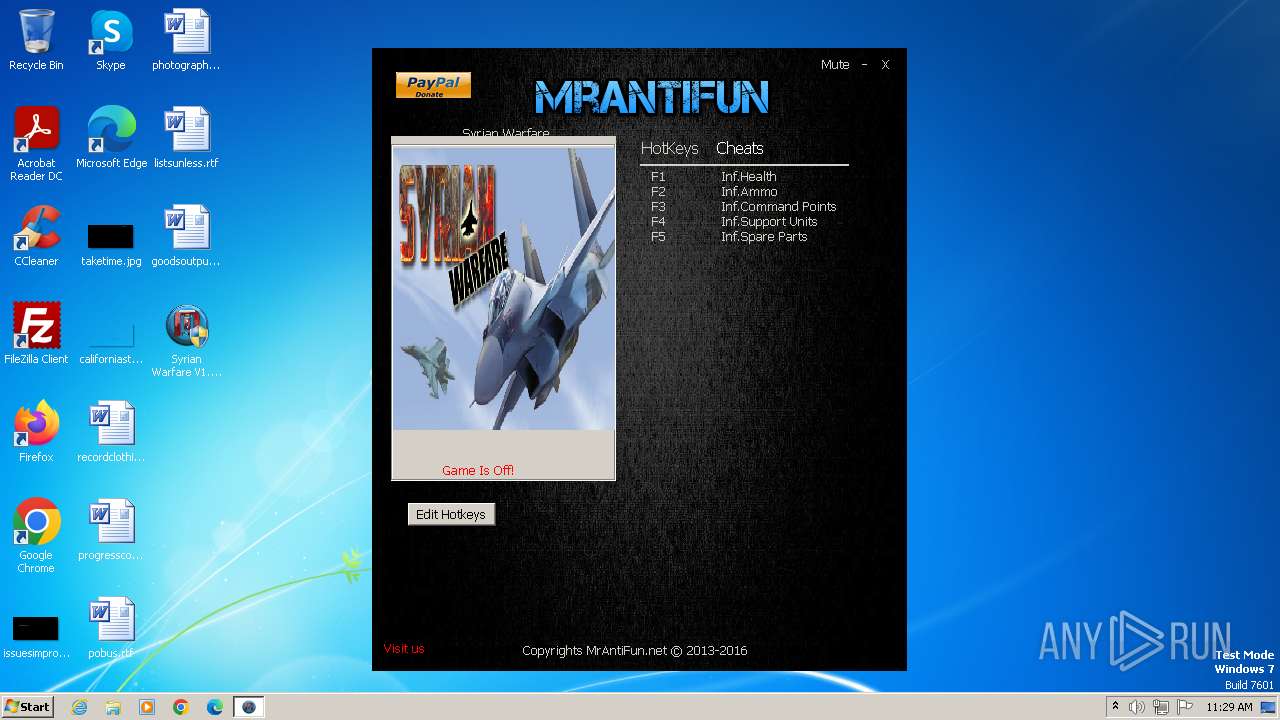
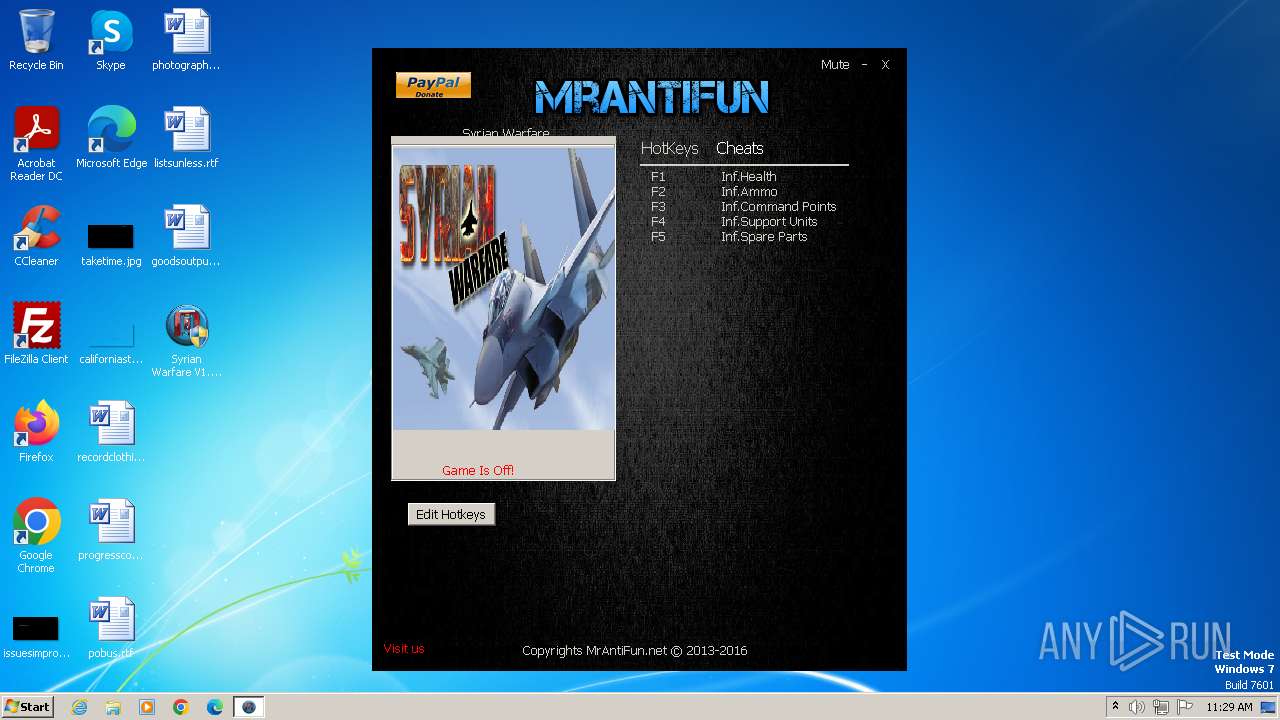
| File name: | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE |
| Full analysis: | https://app.any.run/tasks/6adf89dc-48f5-4467-9c77-331e0bcc6dbe |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2023, 11:28:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F76D2B9676E433FA099DEF4A46614AE9 |
| SHA1: | 5503AAC9761D708E8380492BC95DE5731969BFFB |
| SHA256: | 3DFAF324E84C432798678665EF48E43240A97A9F16FFC52BDBD95B19864551A2 |
| SSDEEP: | 98304:WiqxzZ4p+cvSk+y5o+442AKkvozdhG5fIdgL623nYRLc12BoR/elD6A2uRE8nLvM:RCsC |
MALICIOUS
Drops the executable file immediately after the start
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3508)
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3468)
SUSPICIOUS
Process drops legitimate windows executable
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3468)
INFO
Reads the computer name
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3508)
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3480)
- wmpnscfg.exe (PID: 3276)
Checks supported languages
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3508)
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3468)
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3480)
- wmpnscfg.exe (PID: 3276)
Create files in a temporary directory
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3508)
- Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE (PID: 3468)
Manual execution by a user
- wmpnscfg.exe (PID: 3276)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:06:28 16:45:44+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 36352 |
| InitializedDataSize: | 4887552 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15eb |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3128 | "C:\Users\admin\Desktop\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE" | C:\Users\admin\Desktop\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3276 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3468 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE" -ORIGIN:"C:\Users\admin\Desktop\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | — | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE" "C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\CET_TRAINER.CETRAINER" "-ORIGIN:C:\Users\admin\Desktop\" | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 6.5.0.4555 Modules
| |||||||||||||||
| 3508 | "C:\Users\admin\Desktop\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE" | C:\Users\admin\Desktop\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
231
Read events
228
Write events
0
Delete events
3
Modification events
| (PID) Process: | (3276) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{AD3A9E24-E25E-4DD5-8F37-A2A27174071B}\{0577F9E8-3209-4937-9454-ACE05ED3A507} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3276) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{AD3A9E24-E25E-4DD5-8F37-A2A27174071B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3276) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{7935C721-396C-41FF-A0D5-CCDBB0FD22E7} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
4
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3508 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\CET_Archive.dat | — | |
MD5:— | SHA256:— | |||
| 3508 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | executable | |
MD5:6852660B8CBB67EE3F1E31BF2F1E0AFD | SHA256:CD86234CF14DFC0E66AE9E575326FD0CF74723A5A60337F7079C0540B6DA5C8B | |||
| 3468 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\lua53-32.dll | executable | |
MD5:C8F47A0E750E07D86A47B3296FB59A97 | SHA256:DCFD91F21DEE9E70179337A85D21B3CA925F1A6C21DE9576AA5219732B7C7A86 | |||
| 3468 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\defines.lua | text | |
MD5:1DC41A0A351E745085FCC98A3933D91F | SHA256:A2E02DD32F0245FF31190288B368B3EFBBE7C48A95DD22C321231C2F46597D9B | |||
| 3468 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\win32\dbghelp.dll | executable | |
MD5:9139604740814E53298A5E8428BA29D7 | SHA256:150782FCA5E188762A41603E2D5C7AAD6B6419926BCADF350EBF84328E50948F | |||
| 3468 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | executable | |
MD5:7FD341BC6D65A263627DEF33B1657A1A | SHA256:FB416F9301C9528EE3FED2A5AF3B209C0A7F2FA710198F9C07AB8EE96A4CFA96 | |||
| 3468 | Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | C:\Users\admin\AppData\Local\Temp\cetrainers\CET7CC6.tmp\extracted\CET_TRAINER.CETRAINER | binary | |
MD5:E17BF3D84FC9D0977C810C0E7E15A329 | SHA256:309D43FF1C05F8ED5D66AA4ADD0B5BB6FE4FBBF3F42145DC6F216C68B1EADD9E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | Offset of LBR_Count=760 |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | sizeof fxstate = 512 |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymbolListHandler.create exit |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymbolListHandler.create 1 |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymhandler.create |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymbolListHandler.create 2 |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymhandler.create exit |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymhandler.create 3 |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymhandler.create 1 |
Syrian Warfare V1.2.0.43 Trainer +5 MrAntiFun.EXE | TSymbolListHandler.create 1 |