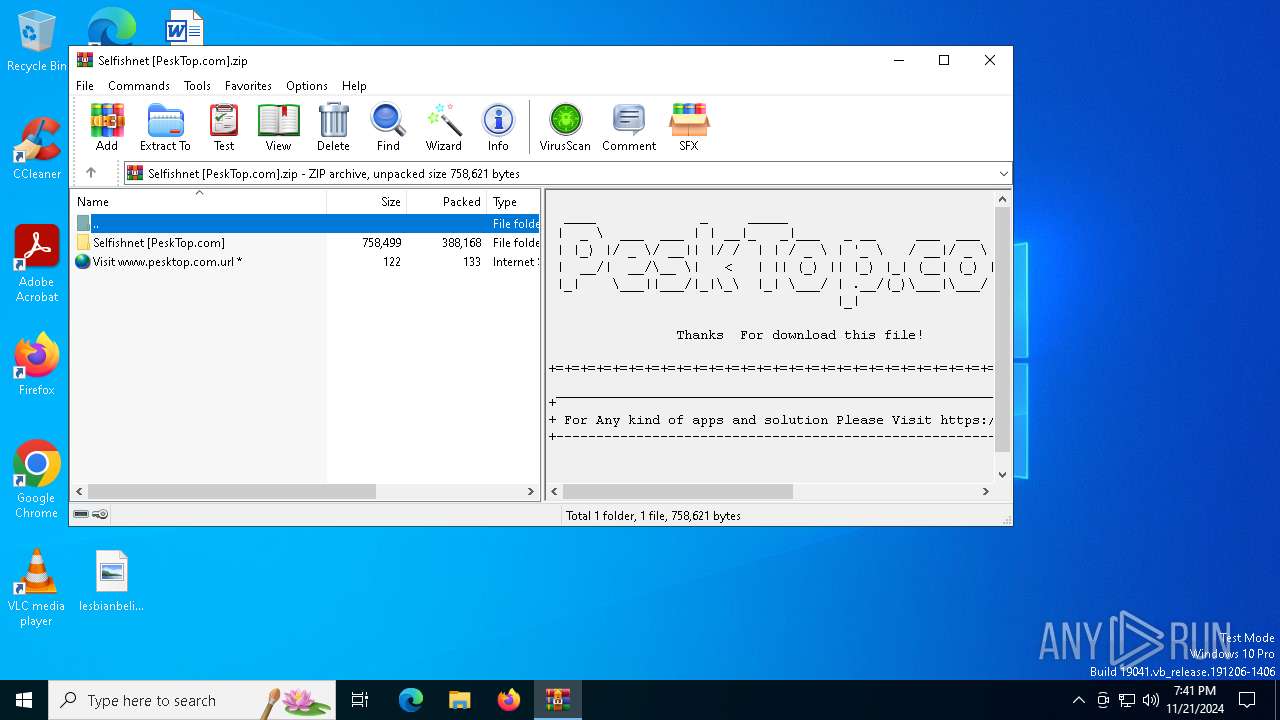
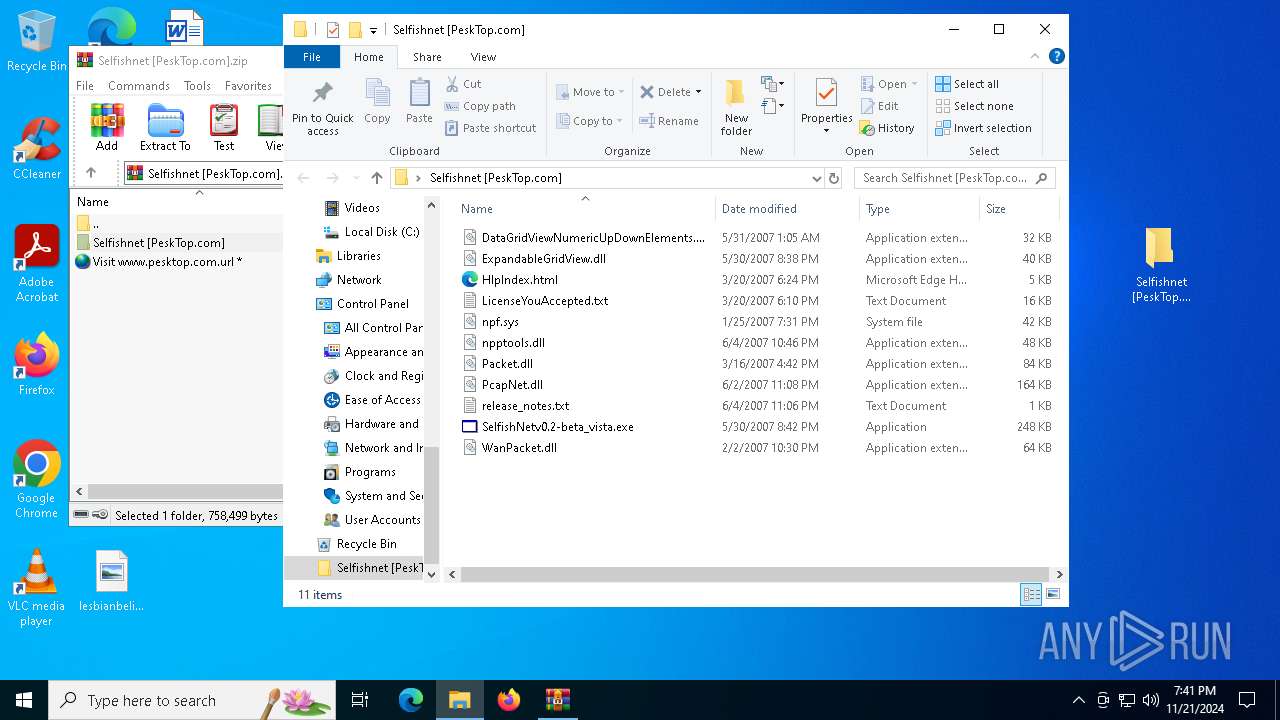
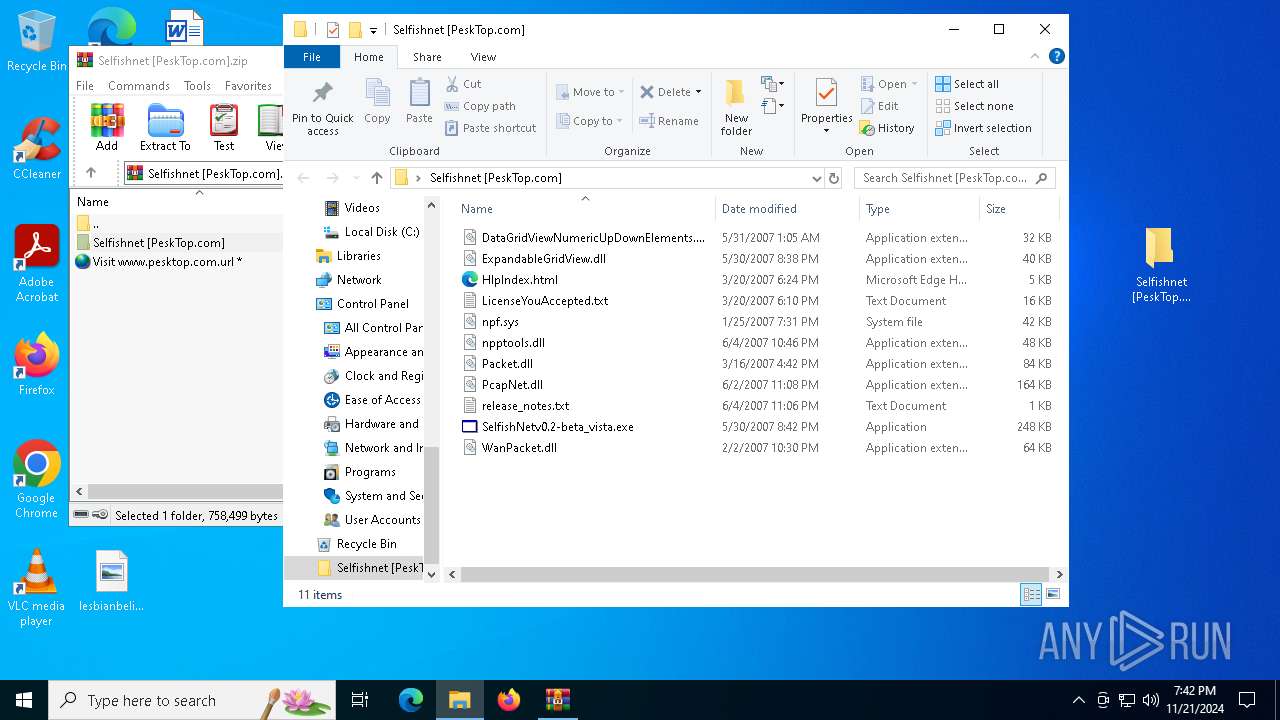
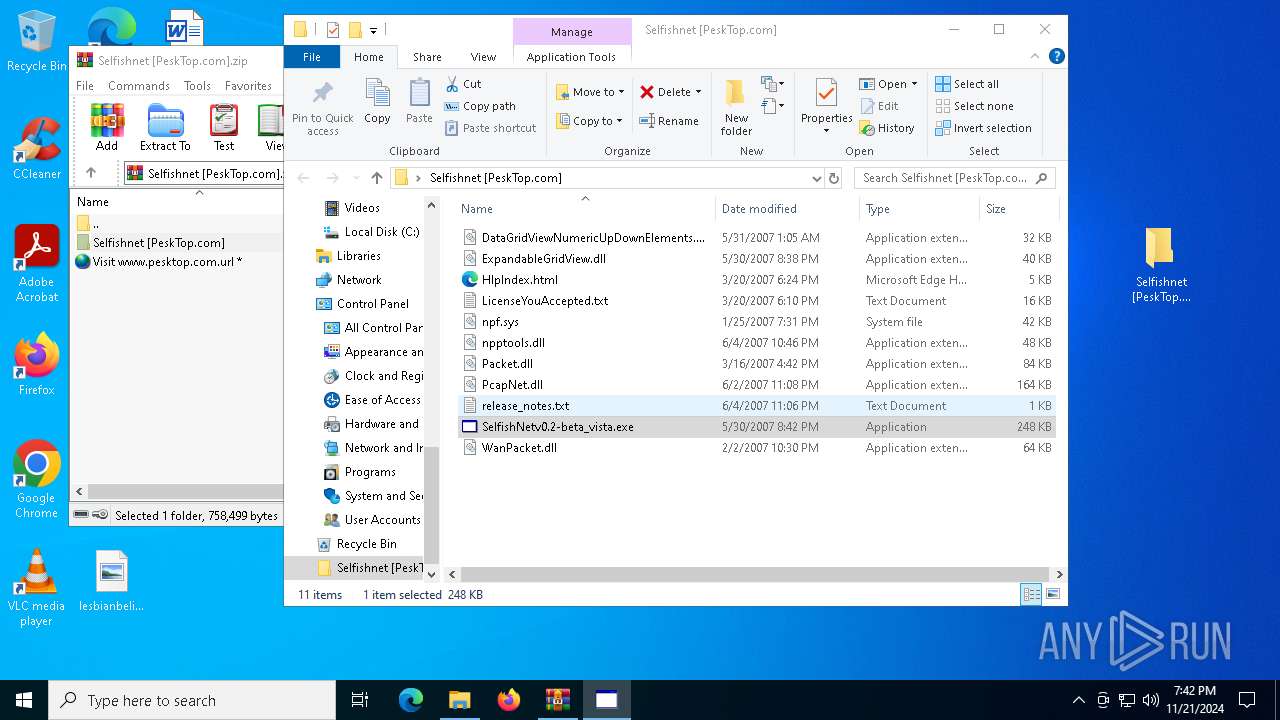
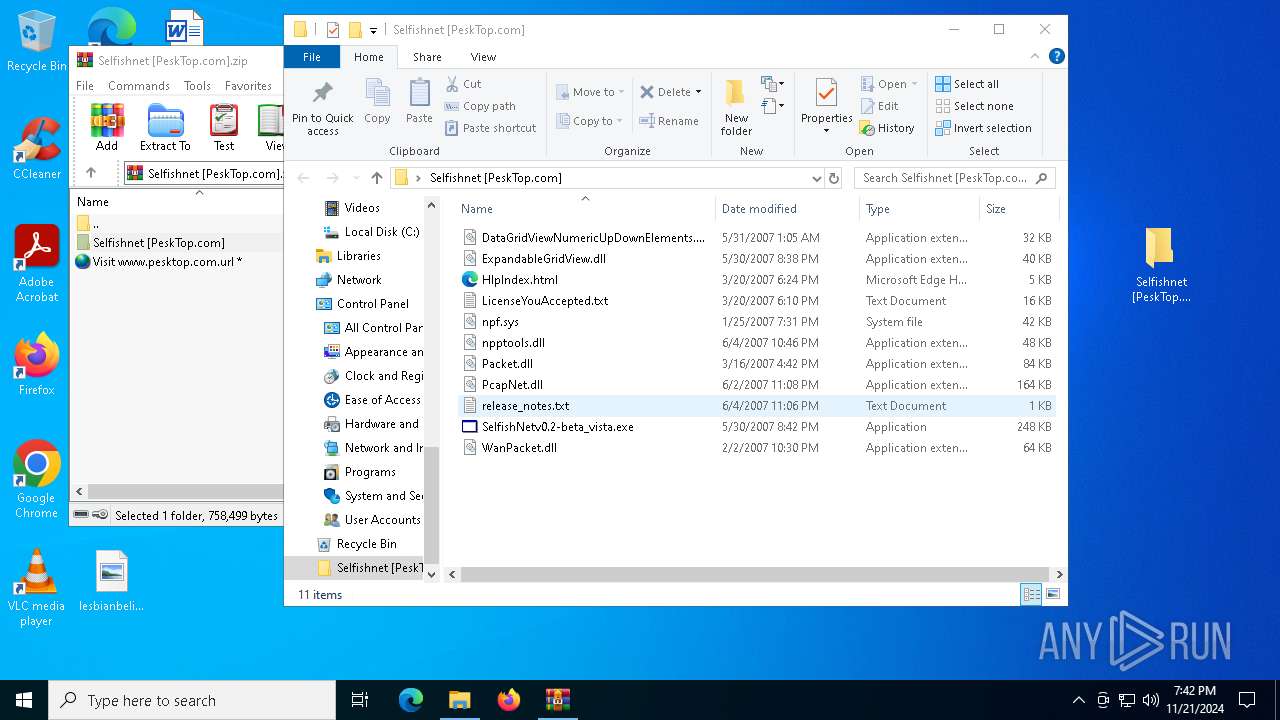
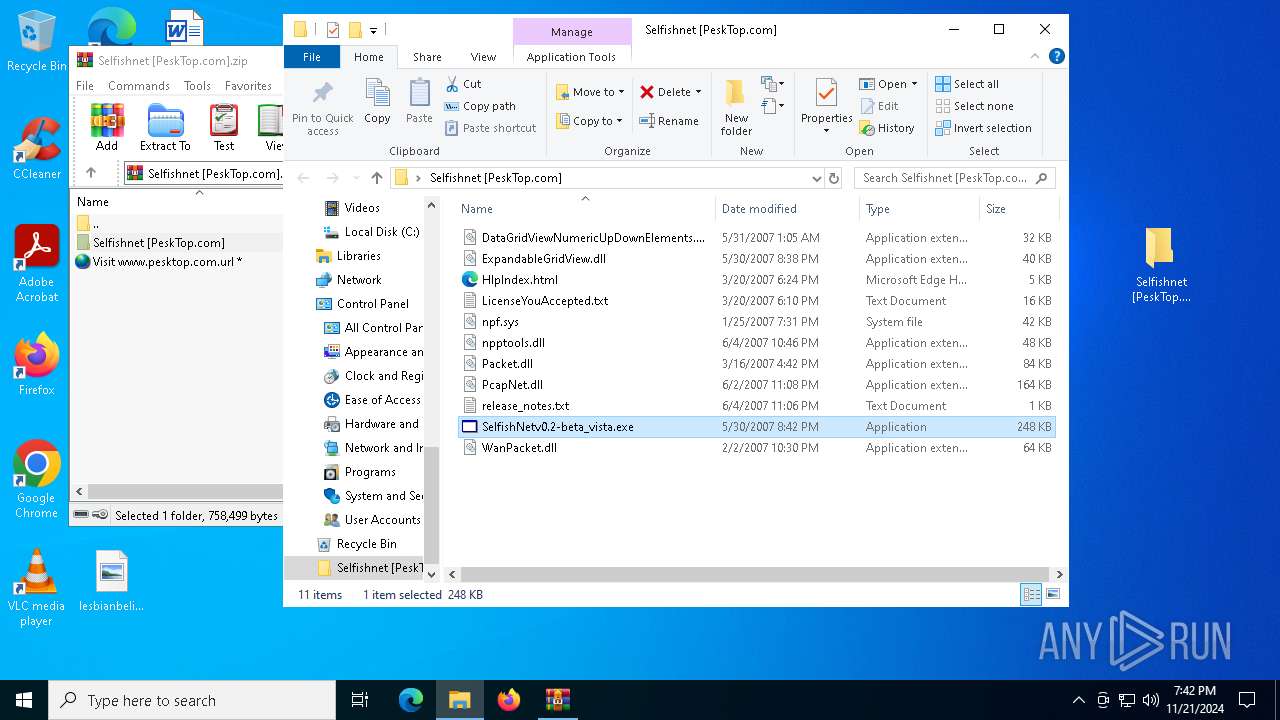
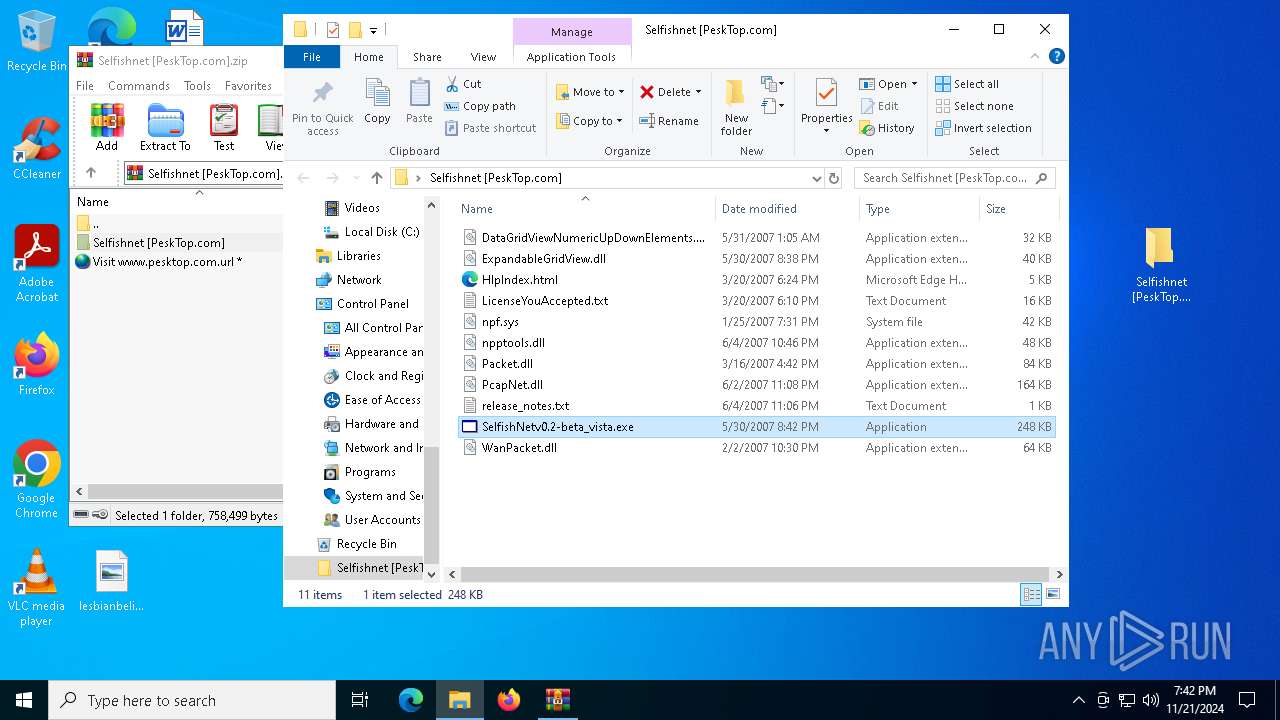
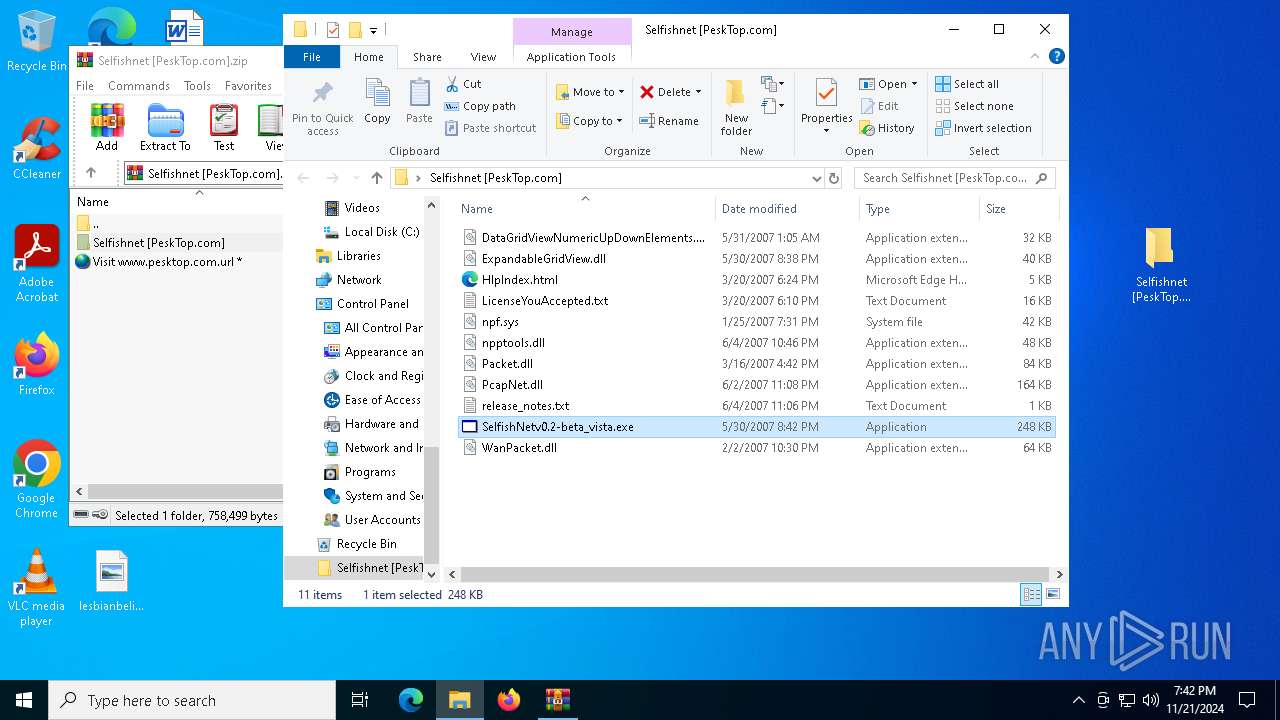
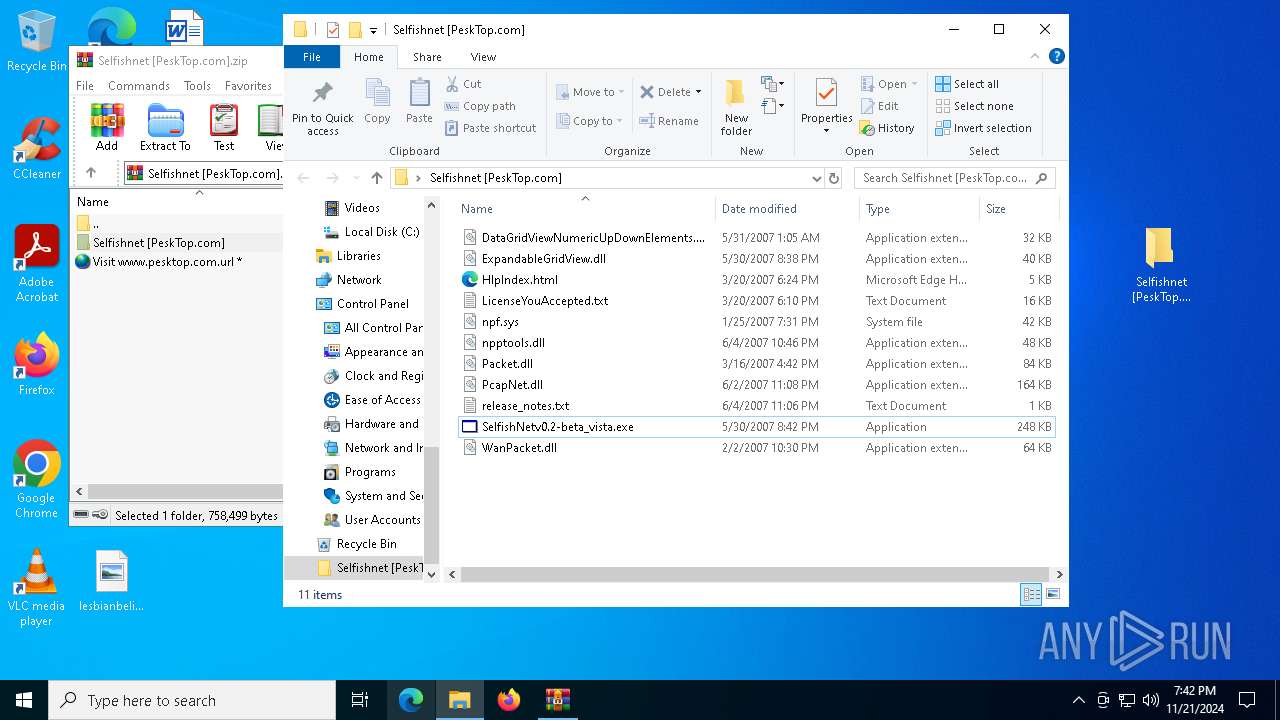
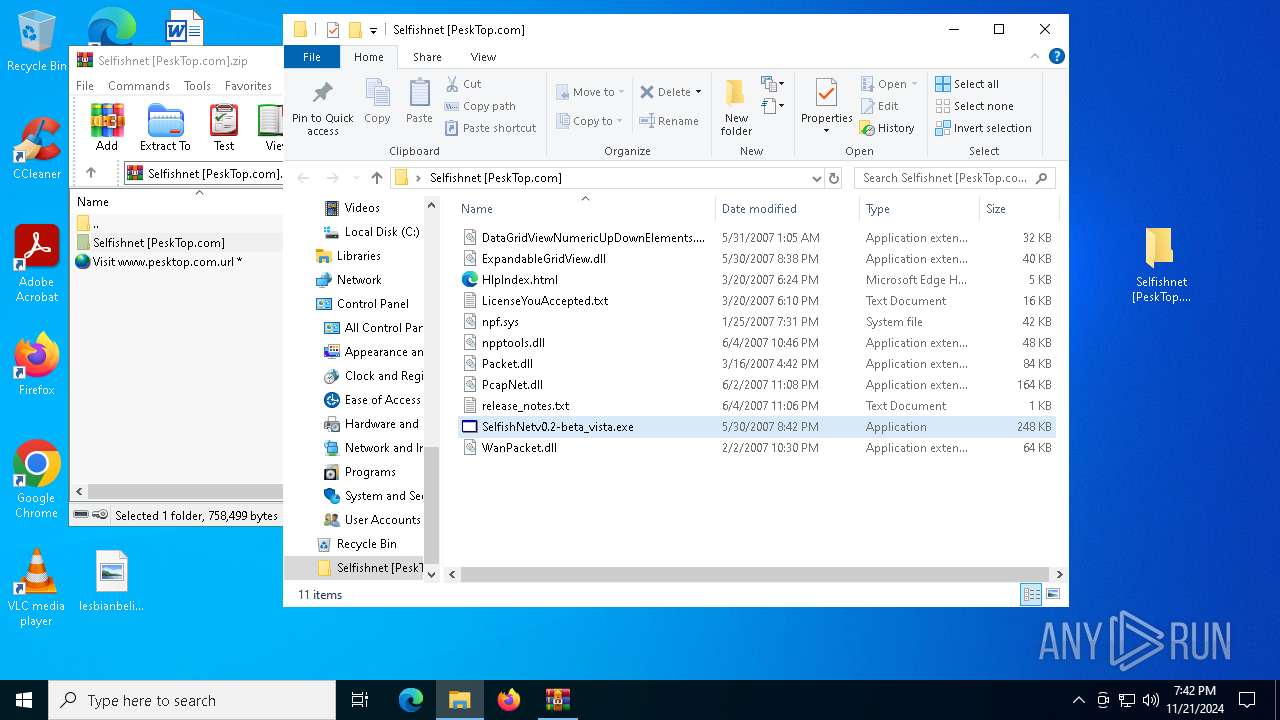
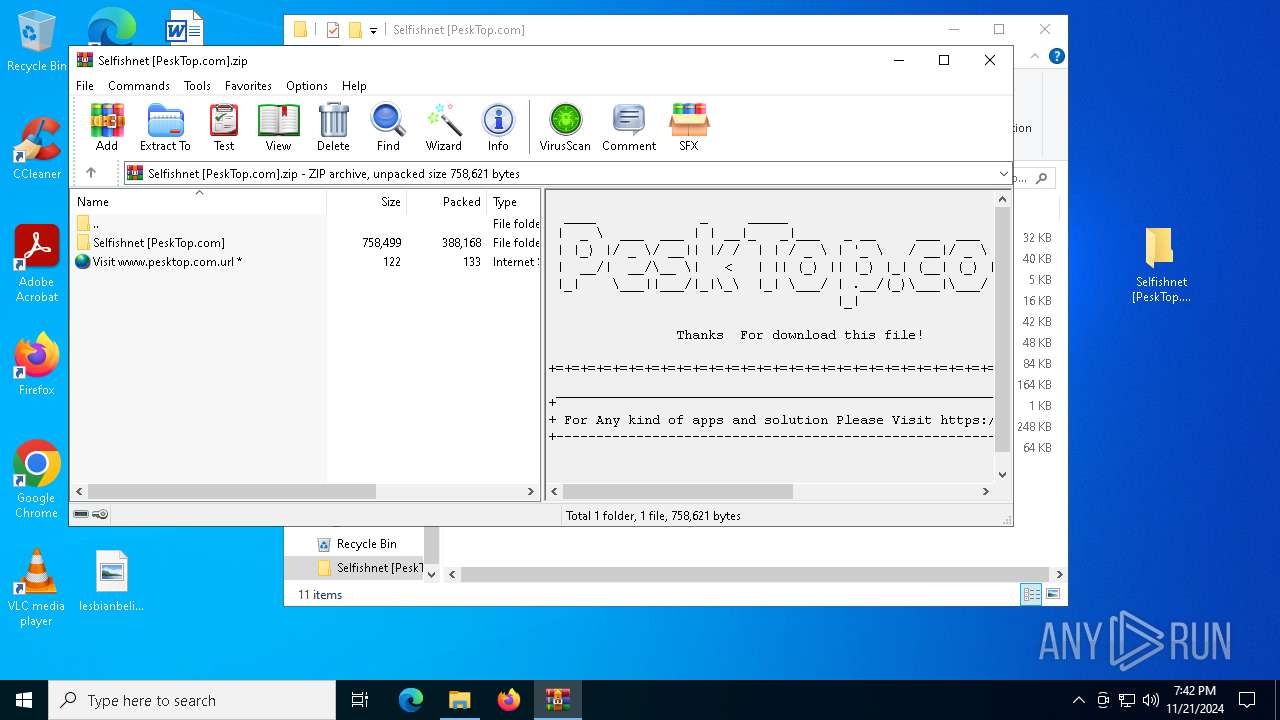
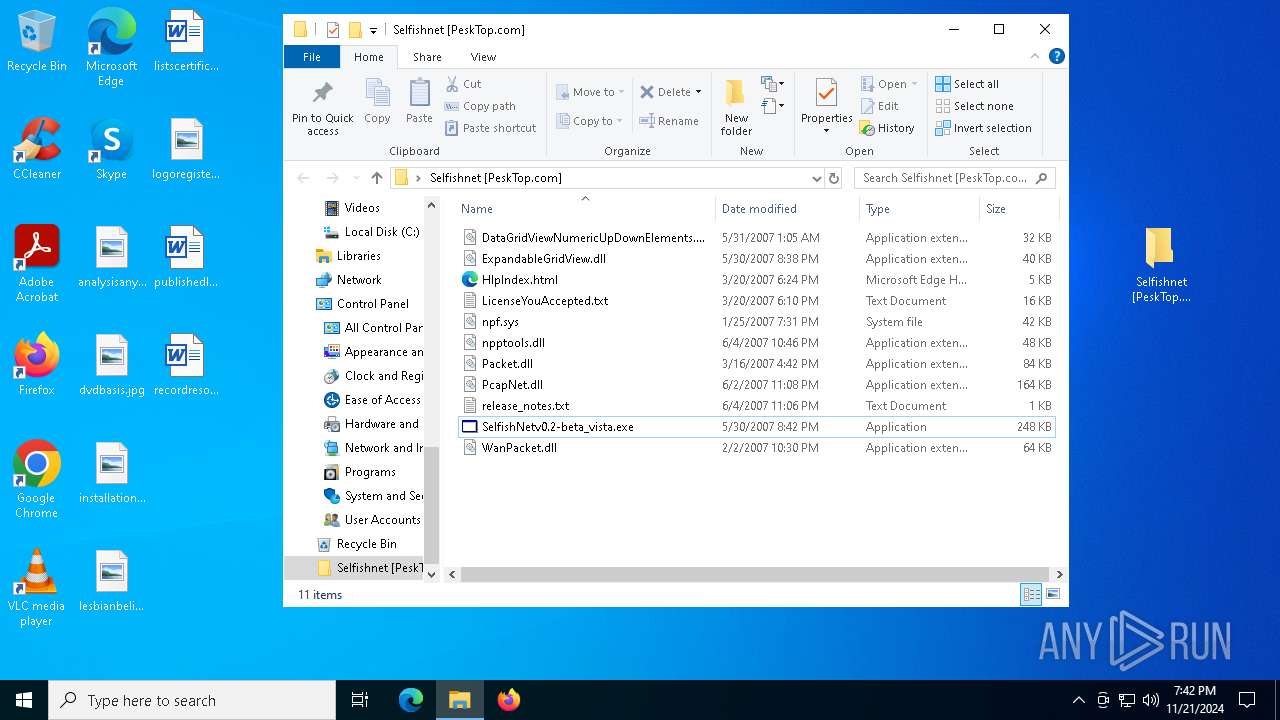
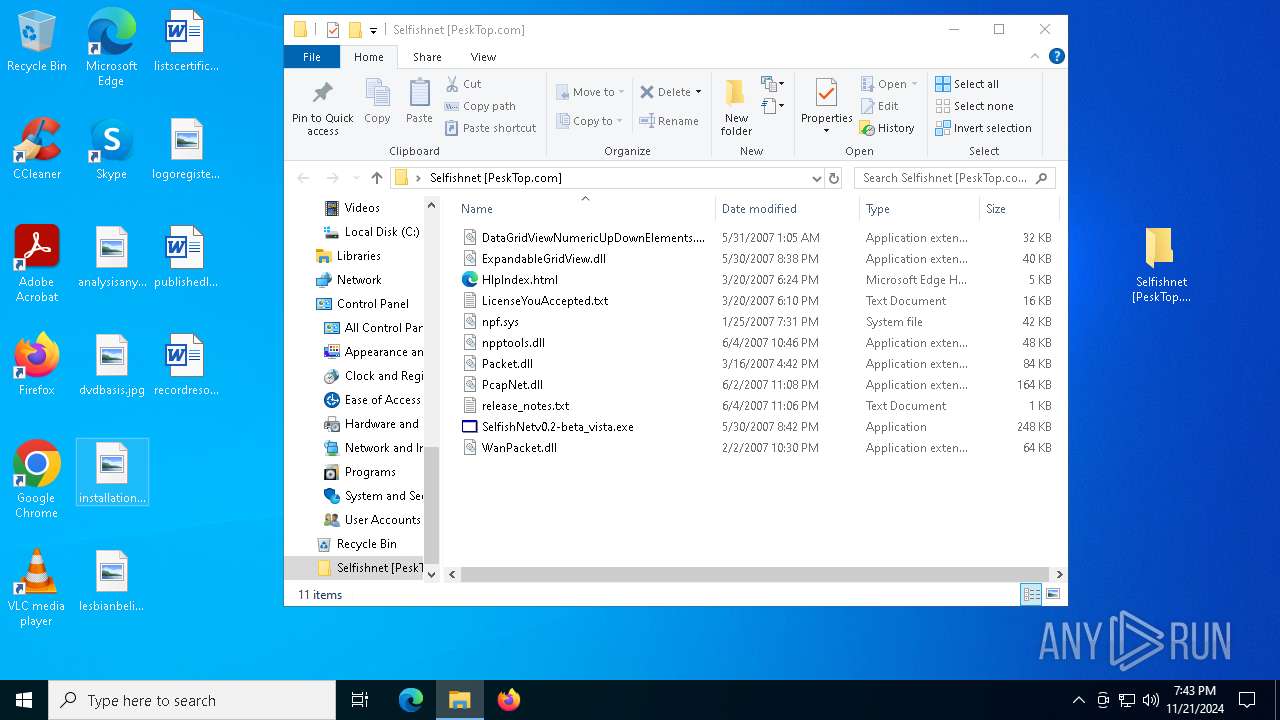
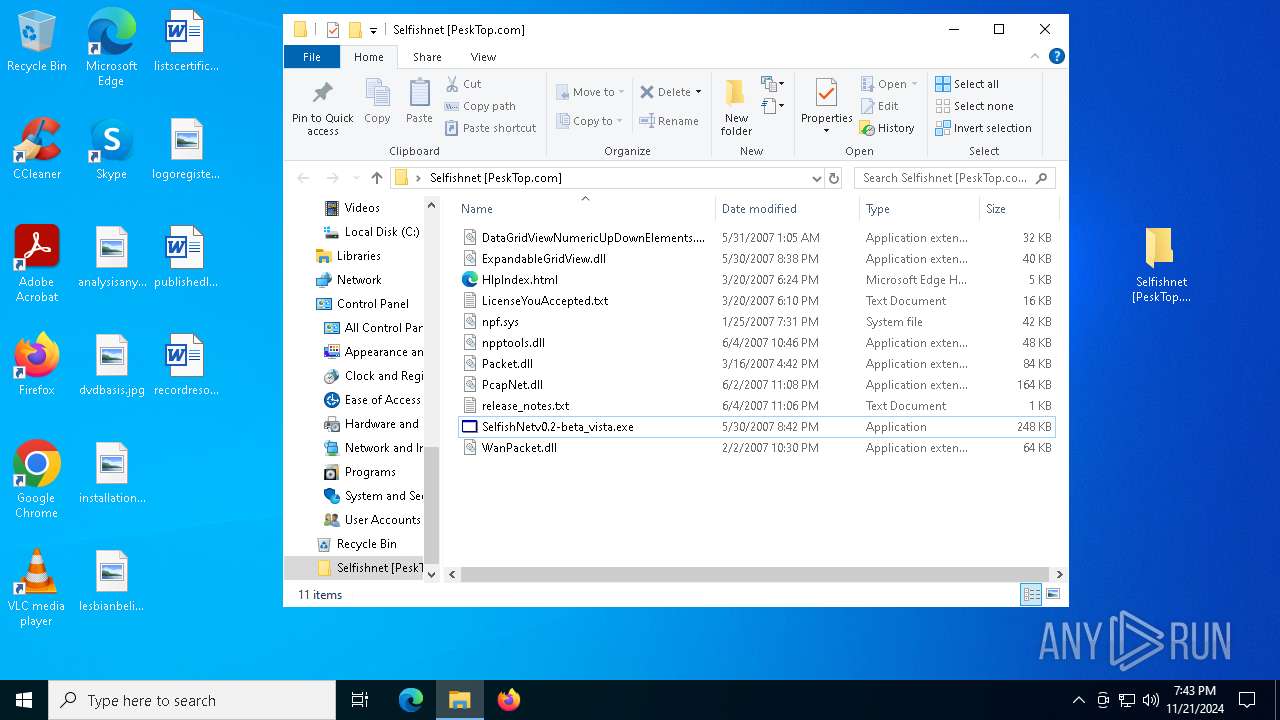
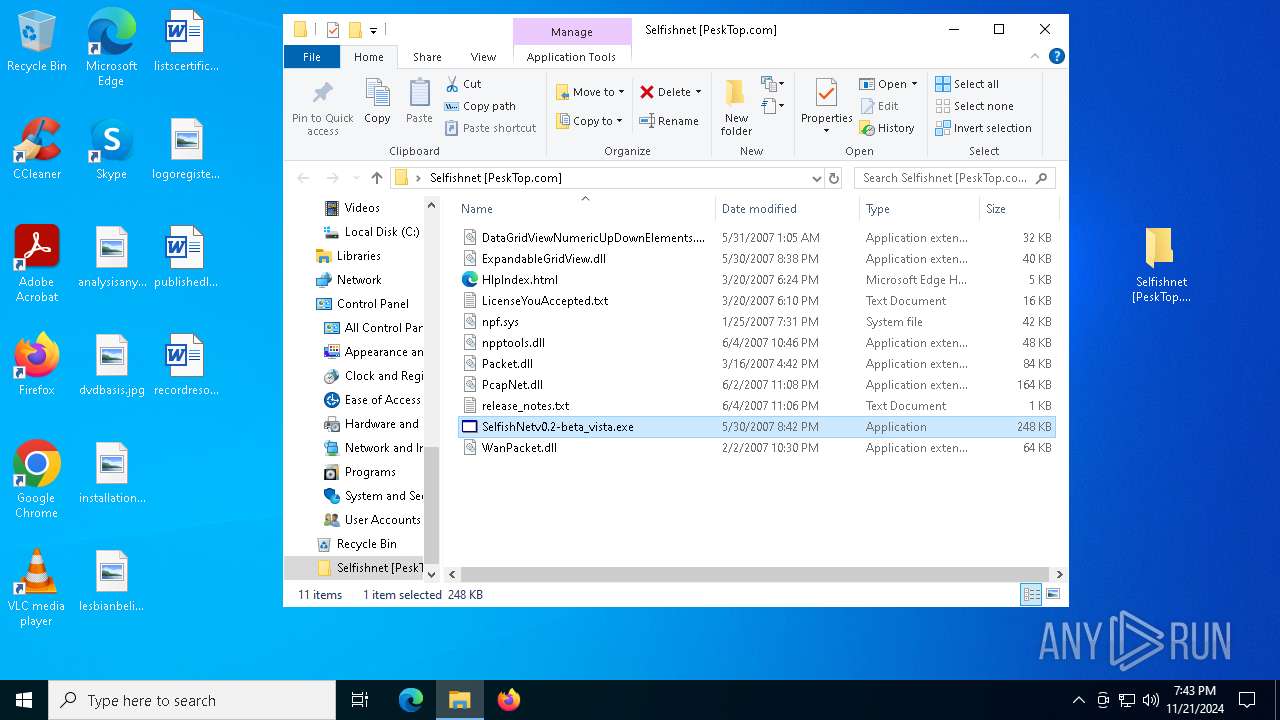
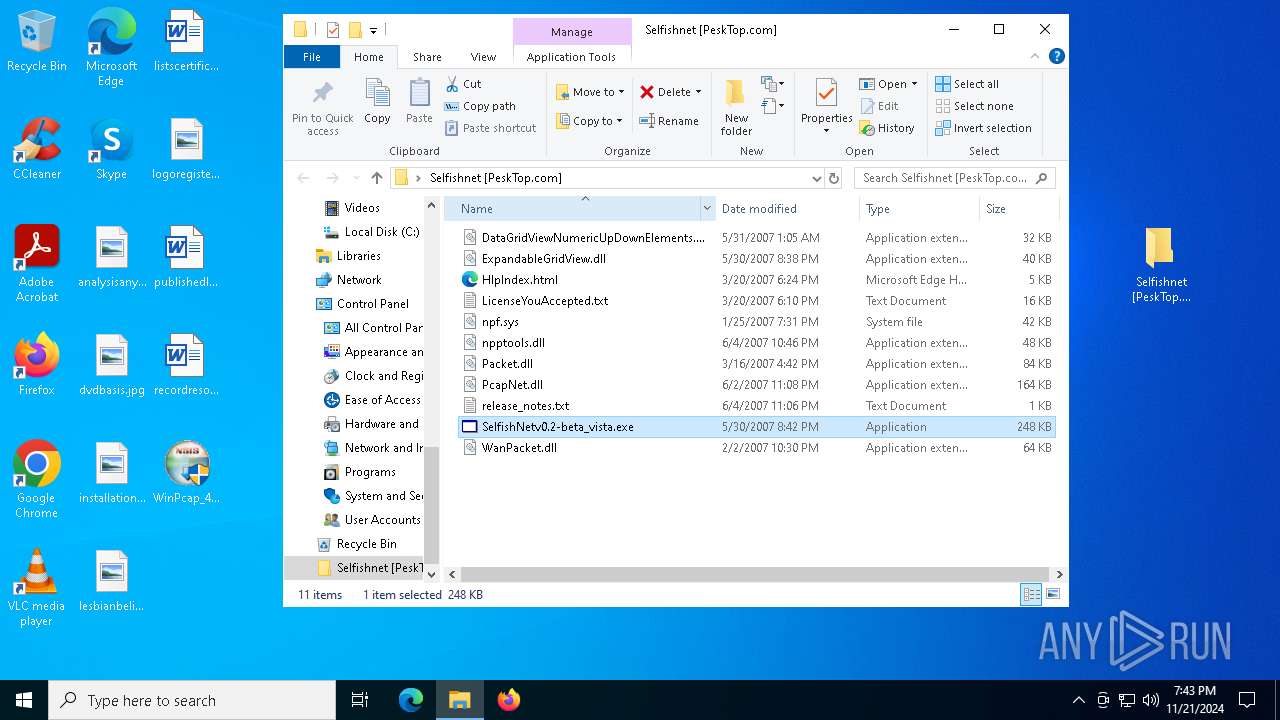
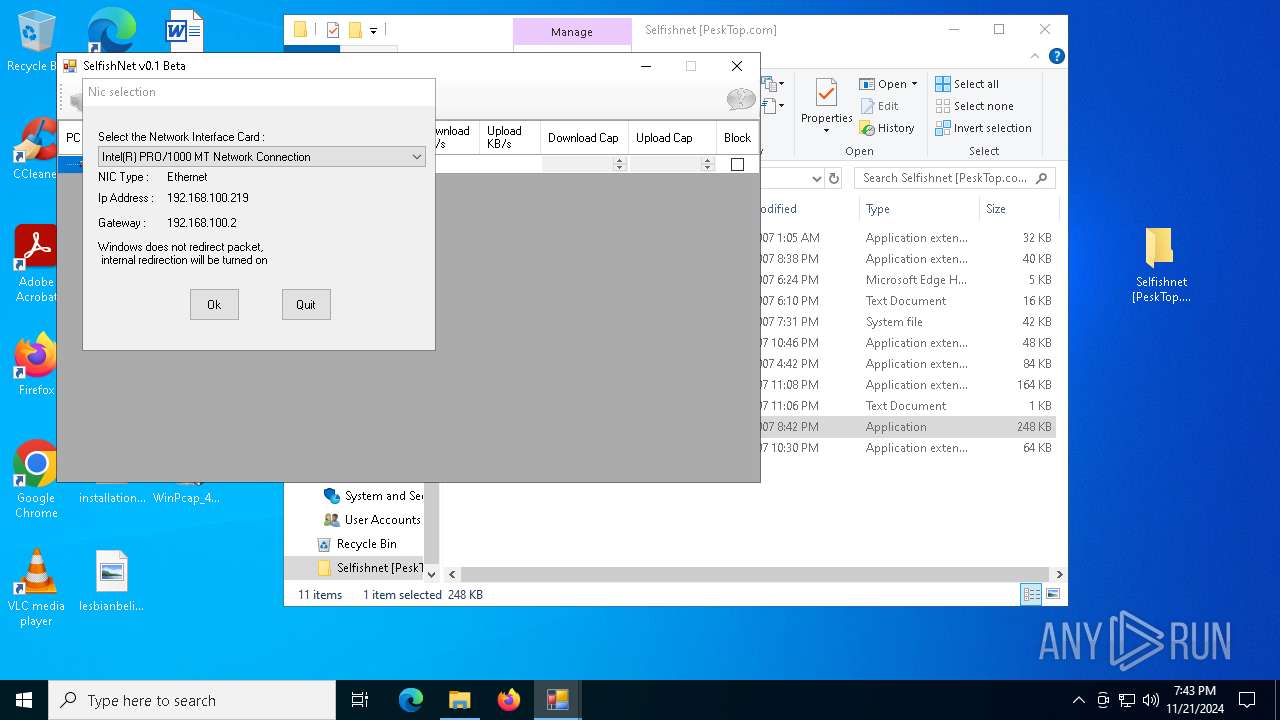
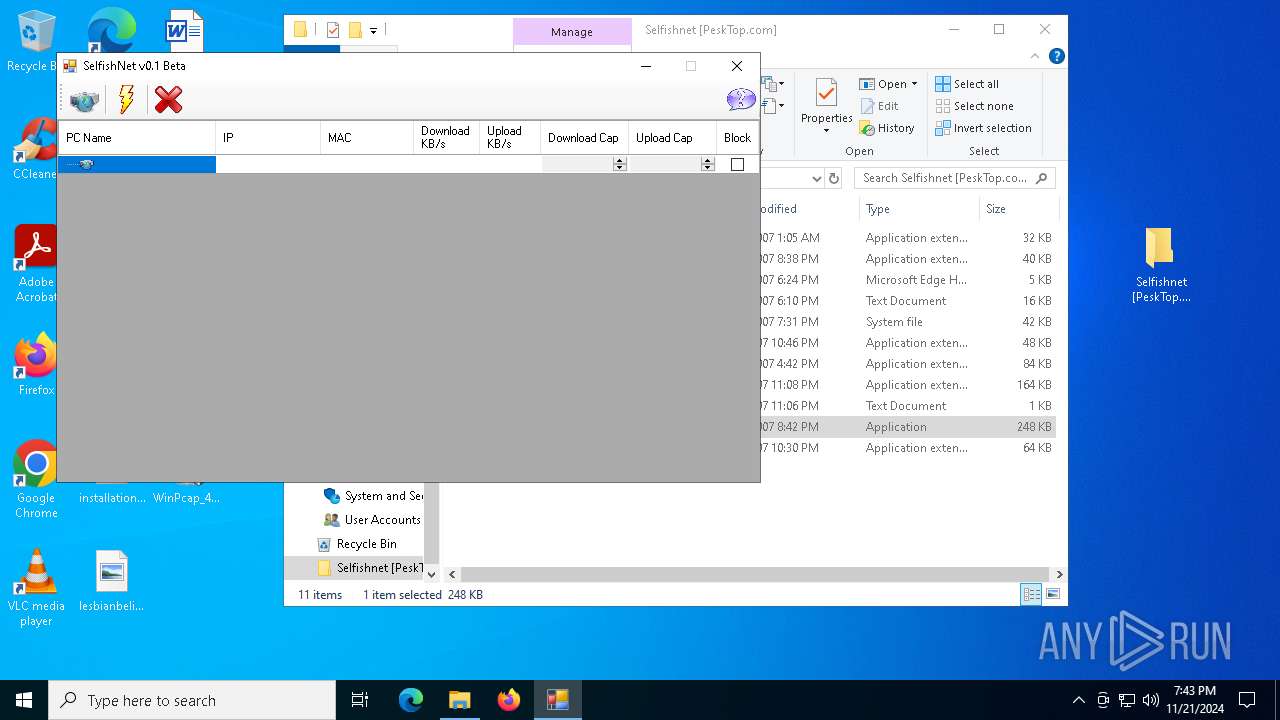
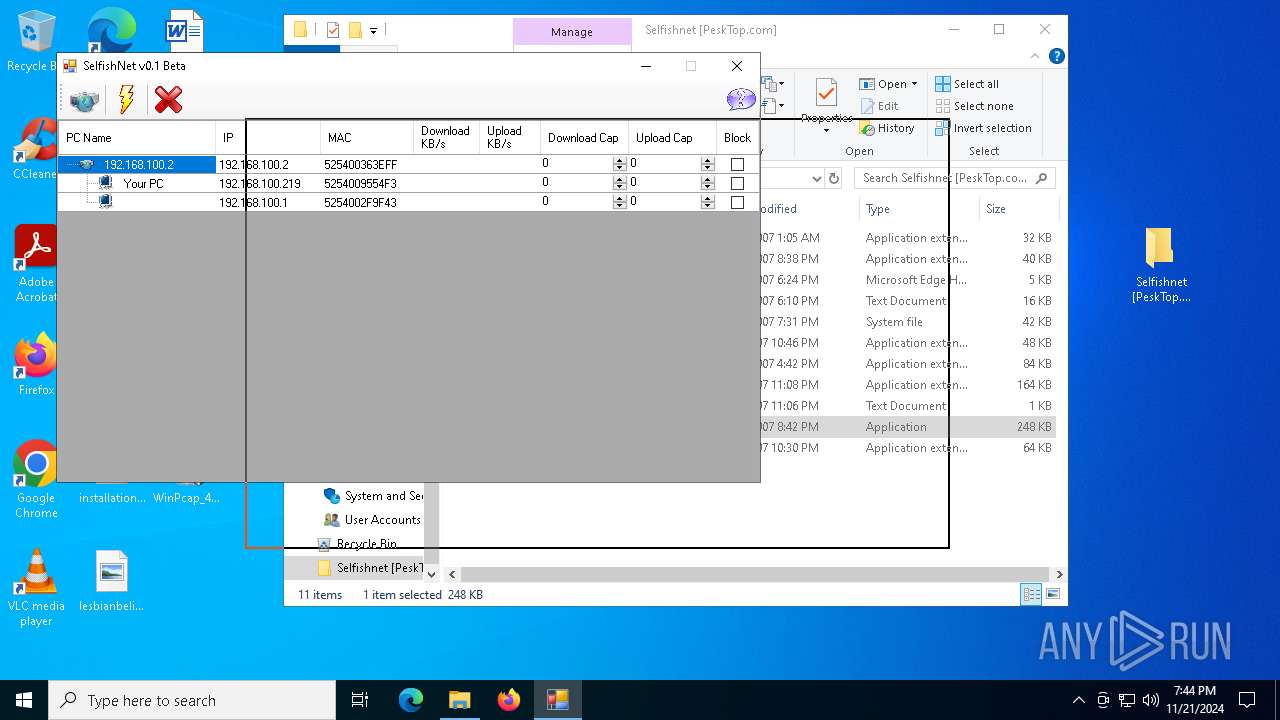
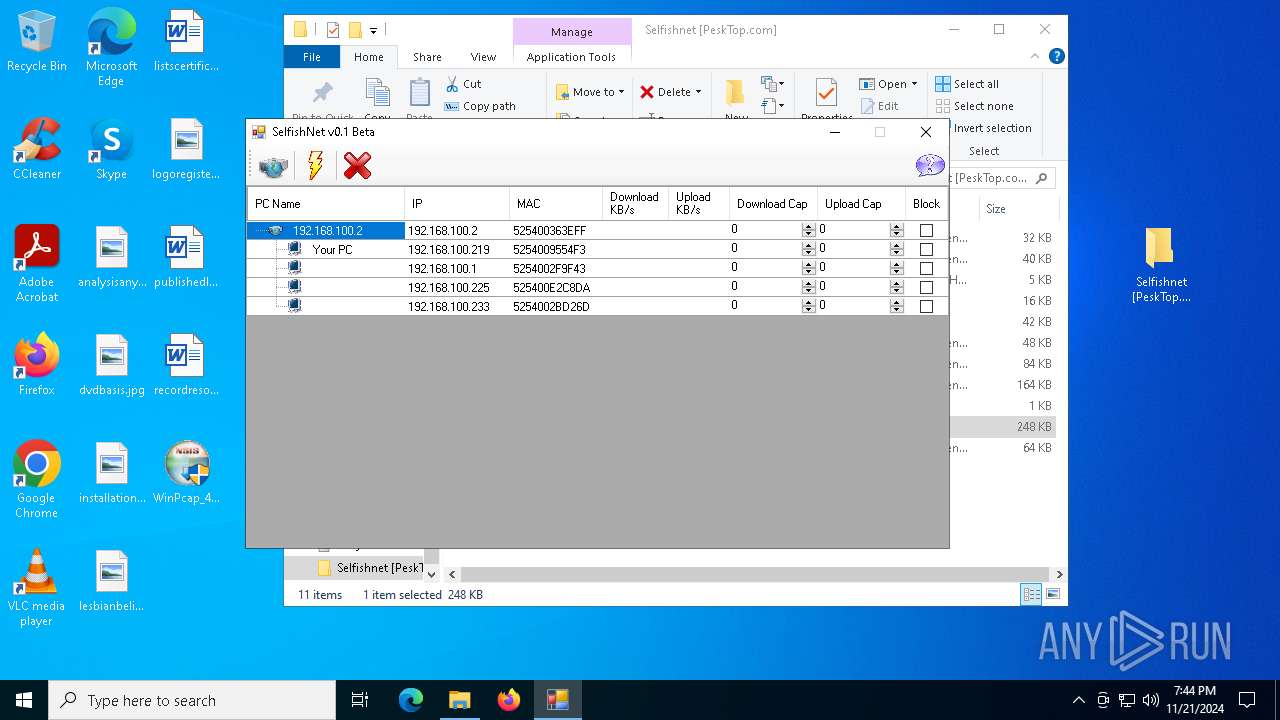
| File name: | Selfishnet [PeskTop.com].zip |
| Full analysis: | https://app.any.run/tasks/6016121c-a2da-44d7-83bd-18ce2731f39c |
| Verdict: | Malicious activity |
| Analysis date: | November 21, 2024, 19:41:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 9E8B5A7C51D7A6A3C32E6C0F125963ED |
| SHA1: | A0DBE8875B72F9DC3AC1D4A1FA8FCEBD510C4385 |
| SHA256: | 3DE721C86A984221E1CB6B7AAE779B2C726F471C0112774D3C739CD2C9A7170D |
| SSDEEP: | 12288:TMJqttc+5pJVZp8TLV4H9eSre+cEF57w513U3:TMJqtu+rnZILV4deSre+XM5dU3 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2420)
Starts NET.EXE for service management
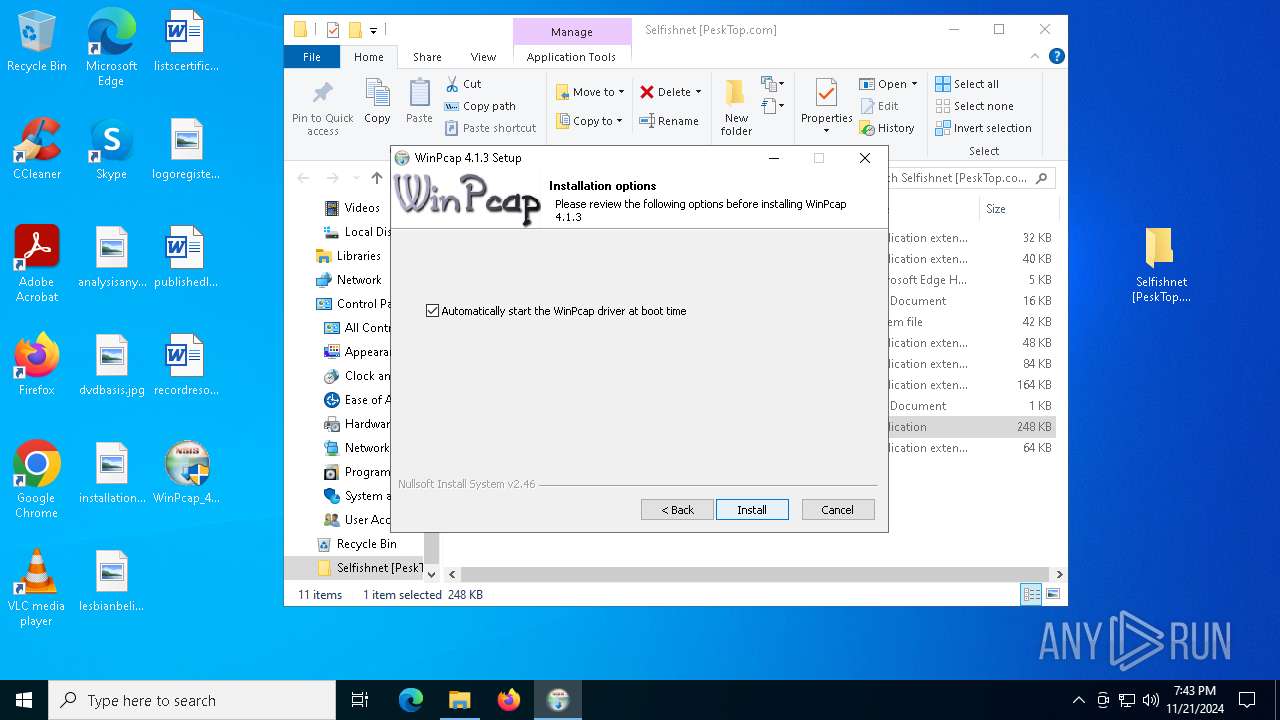
- WinPcap_4_1_3.exe (PID: 6688)
- net.exe (PID: 6780)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2420)
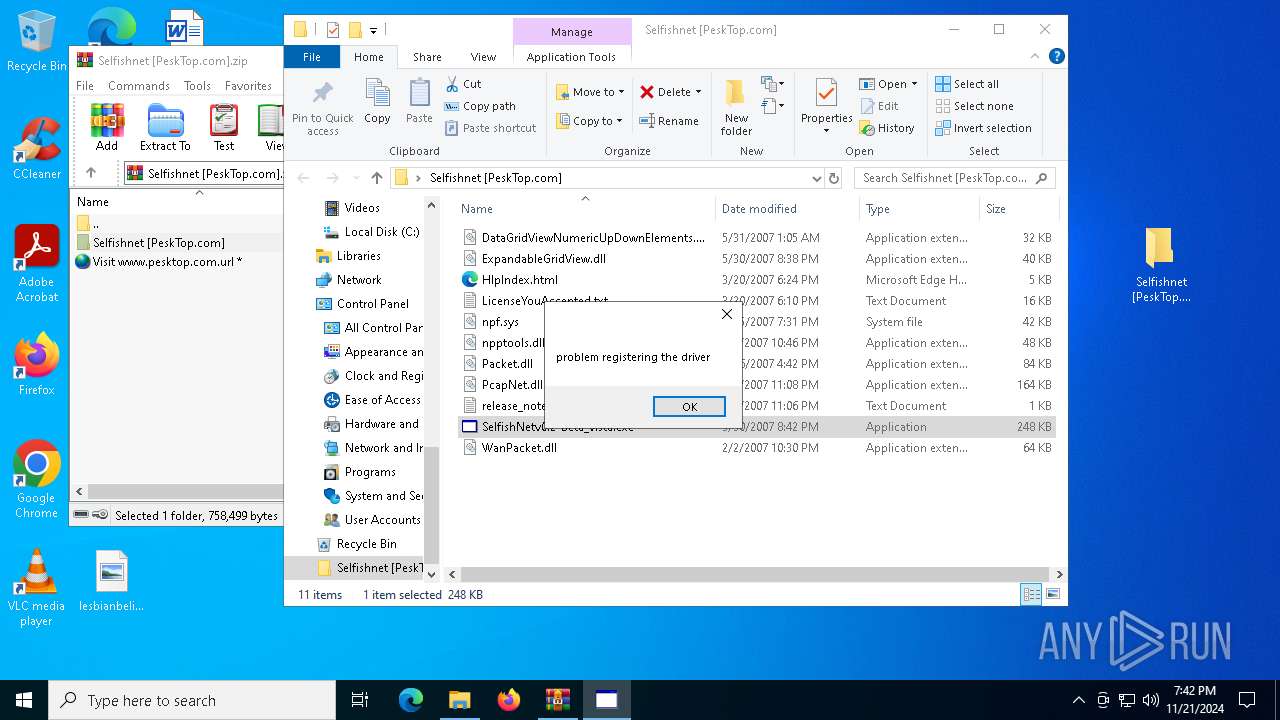
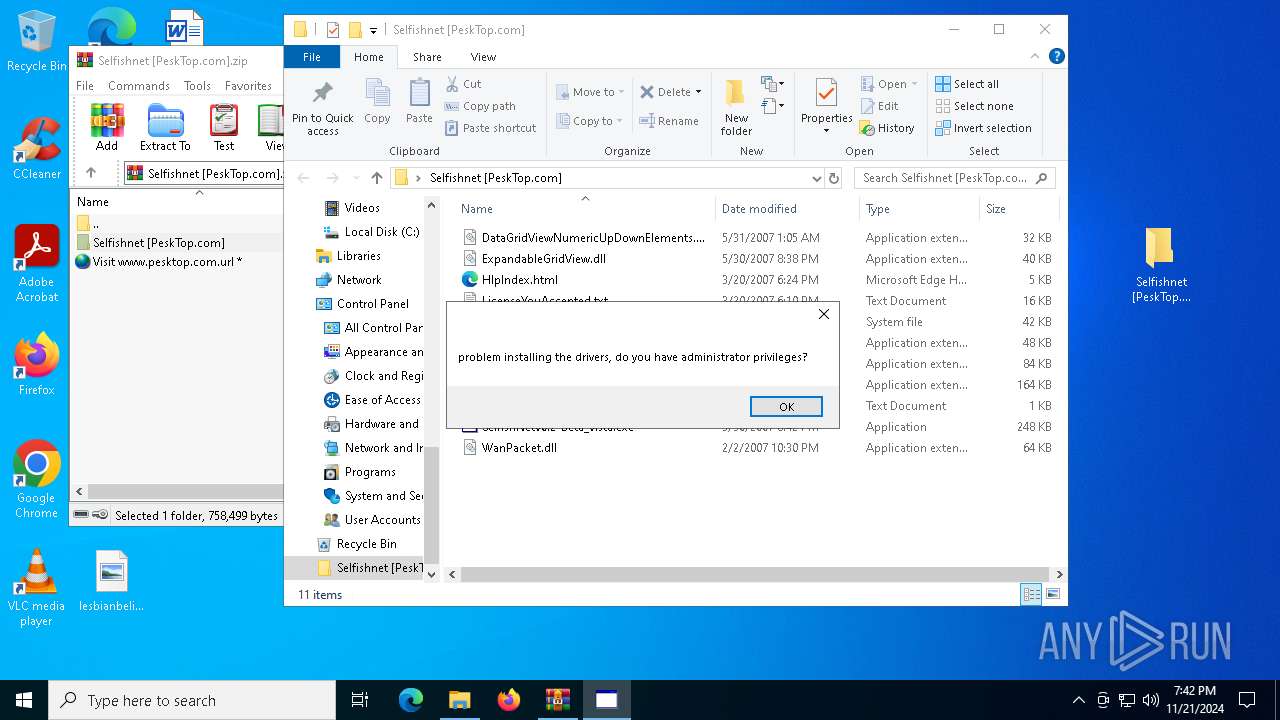
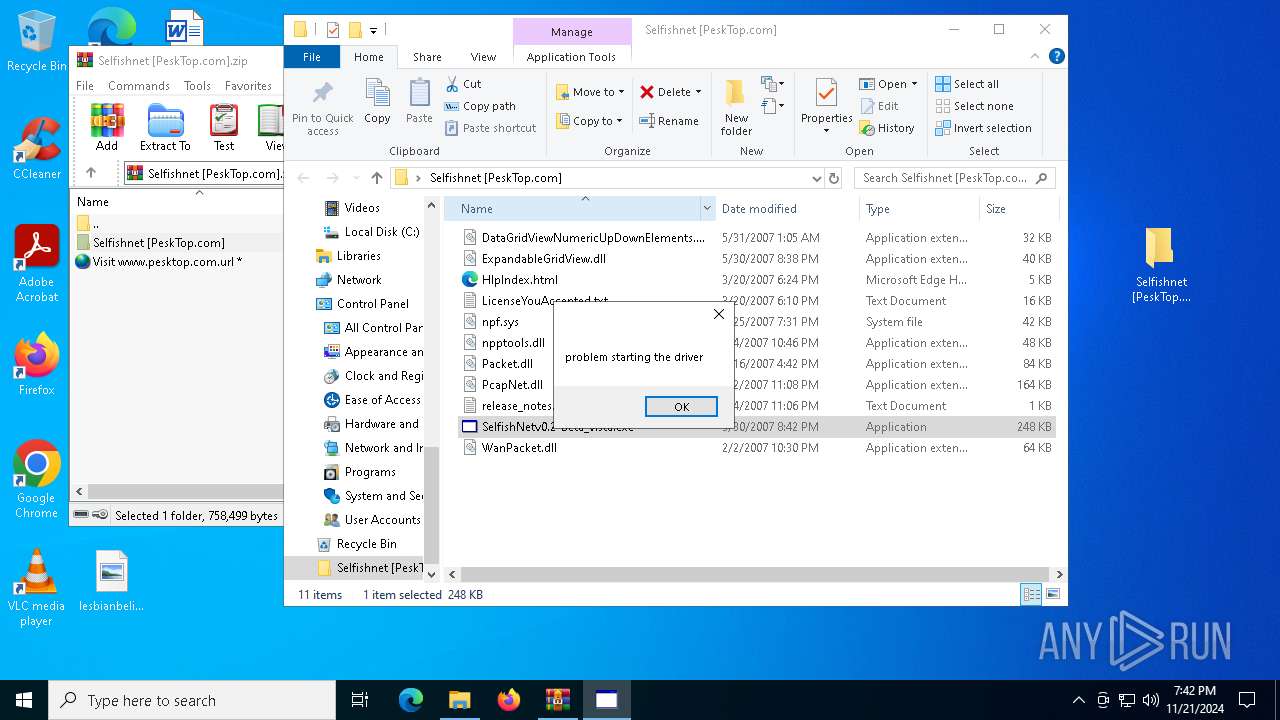
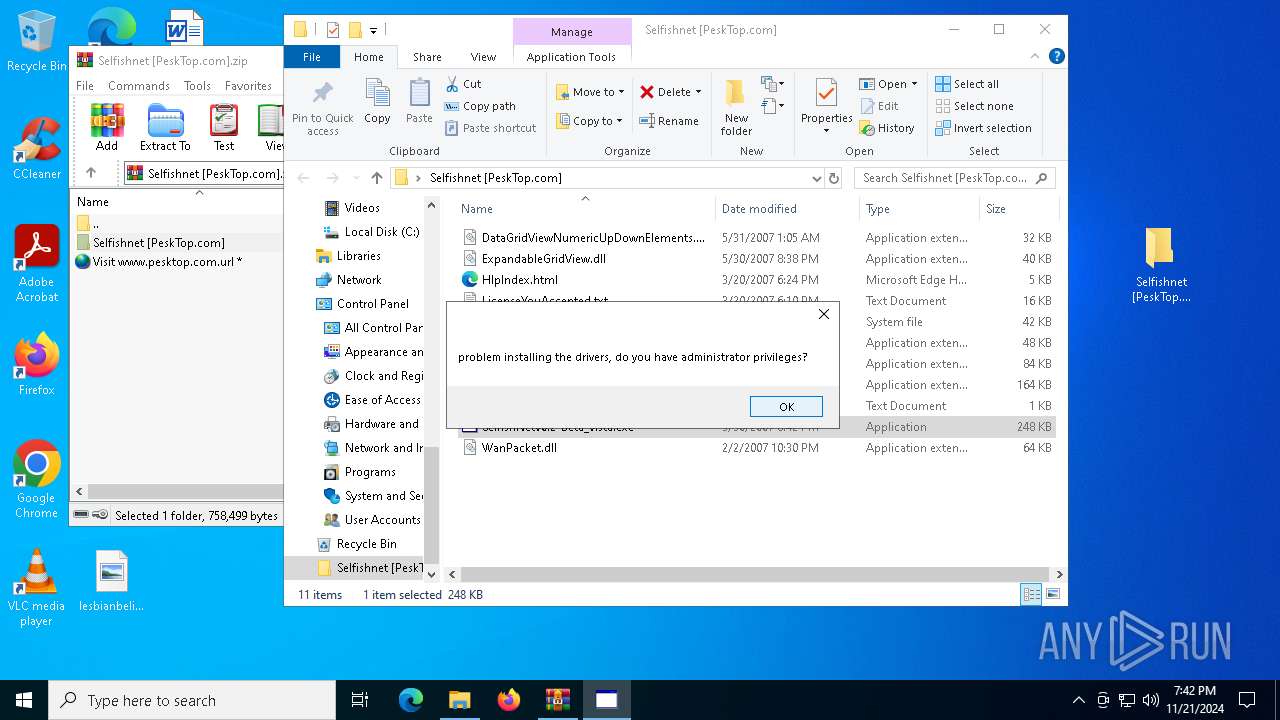
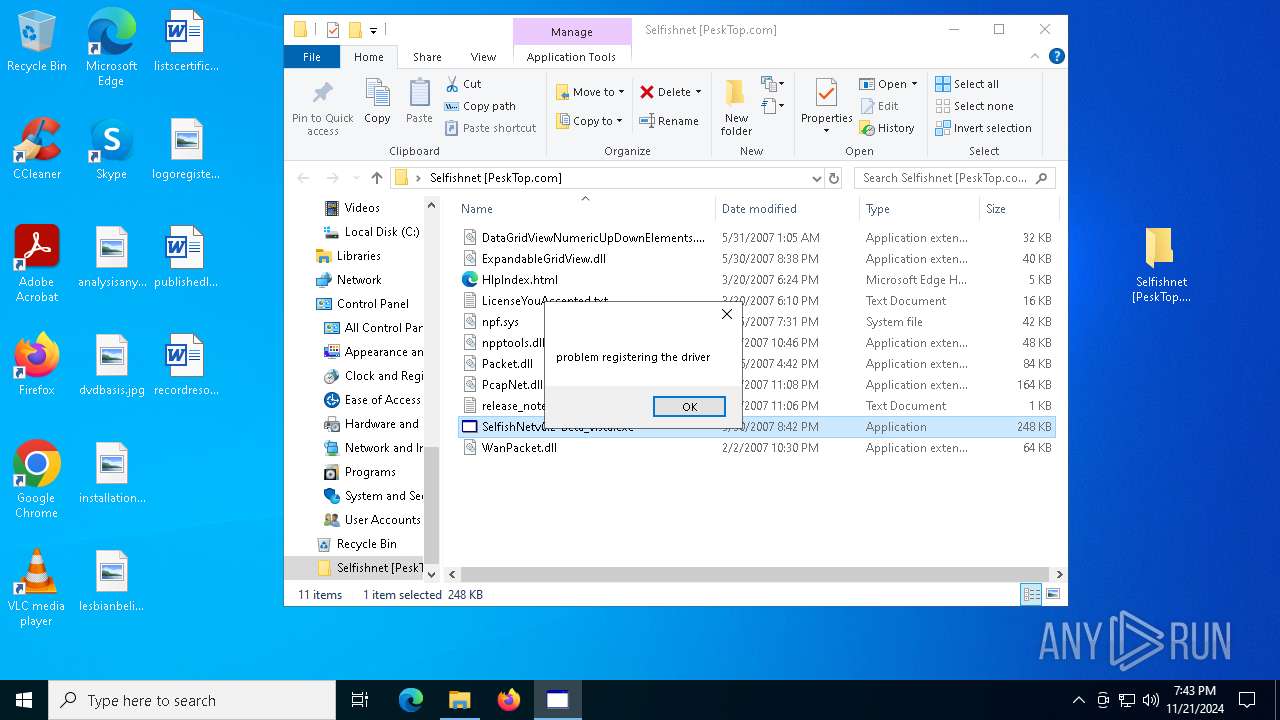
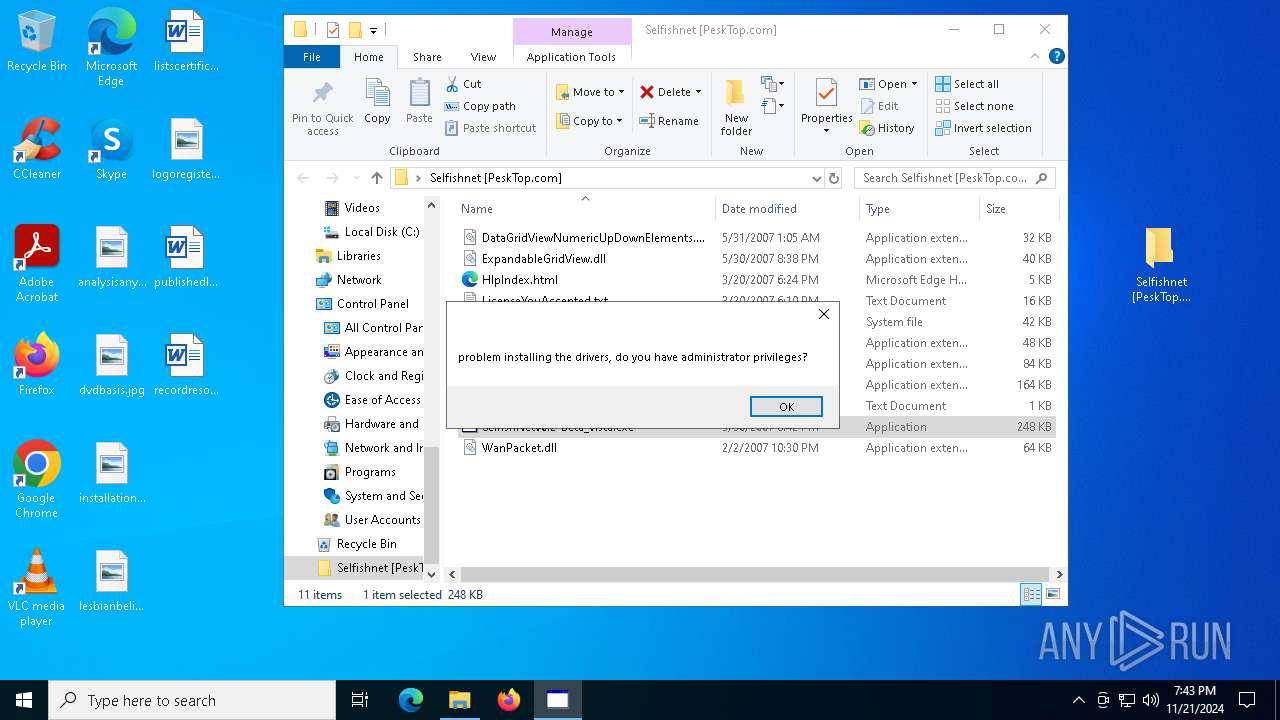
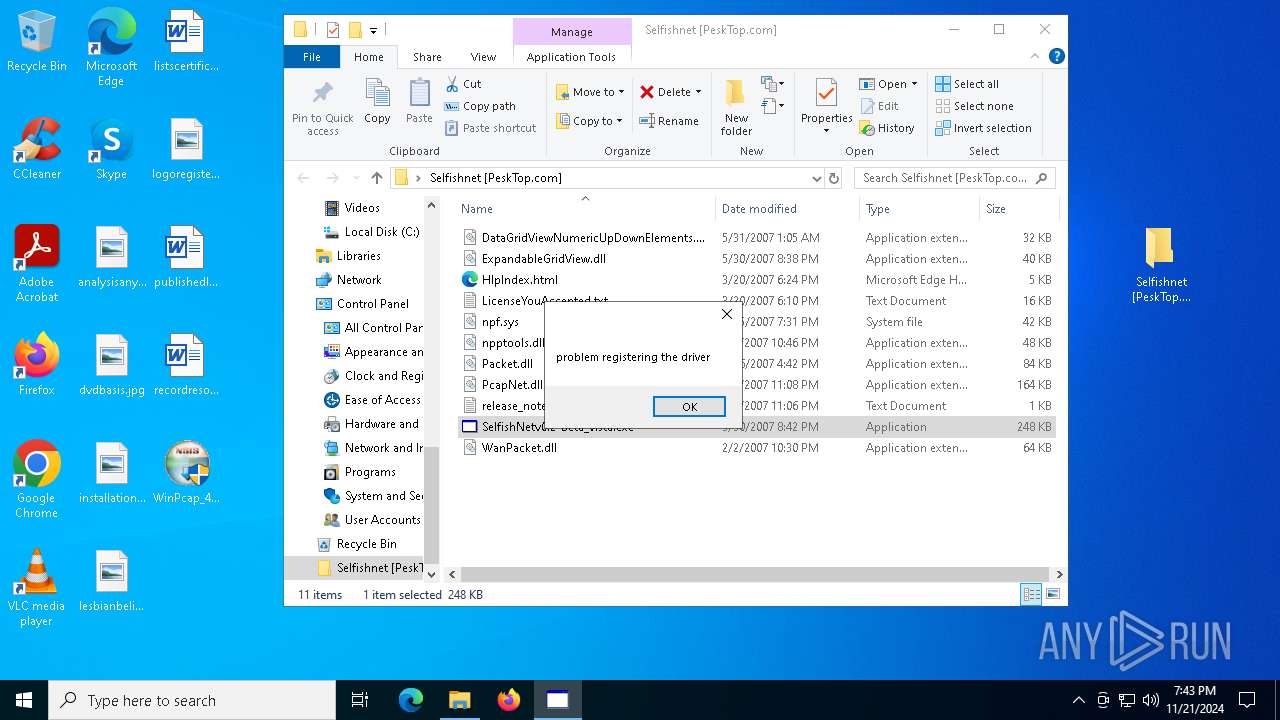
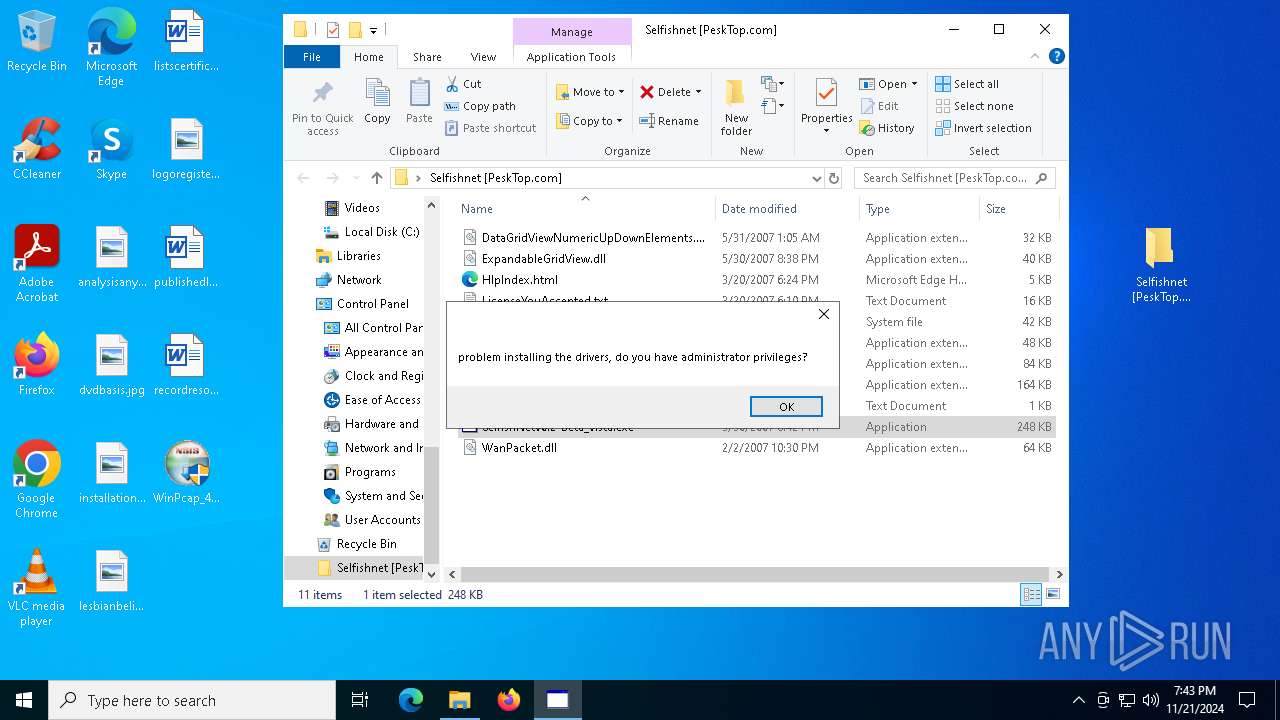
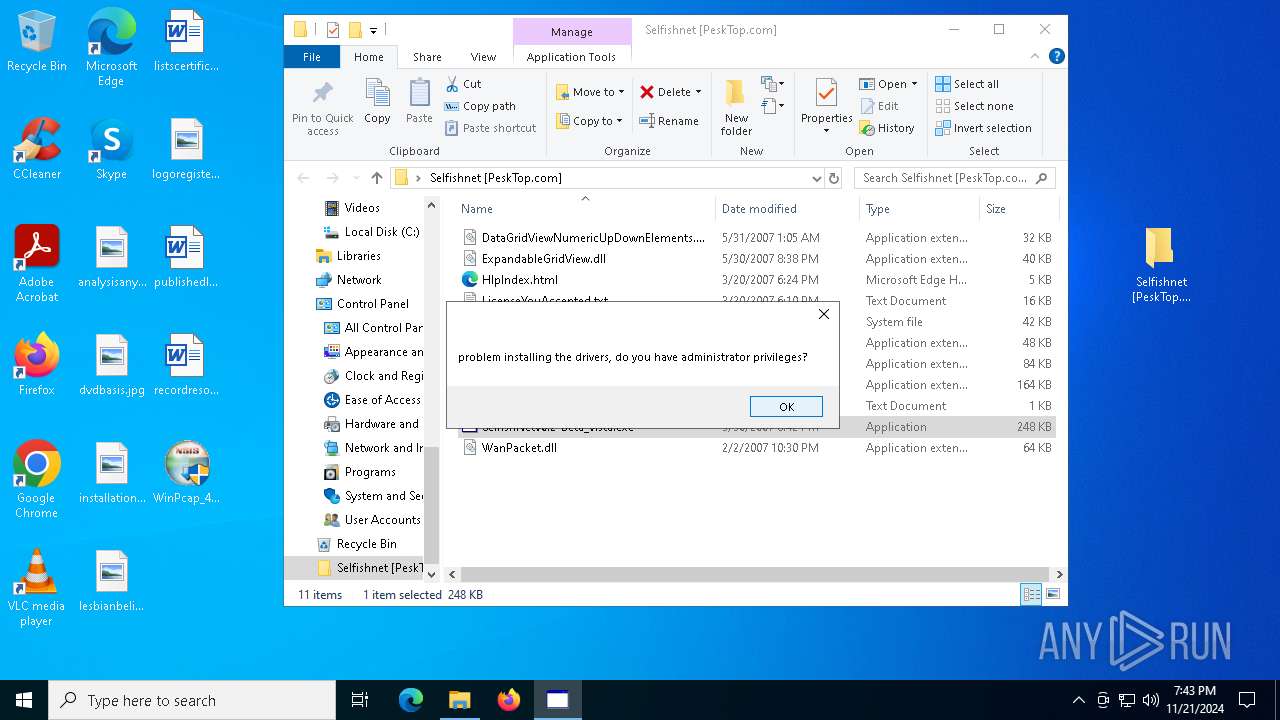
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2420)
- WinPcap_4_1_3.exe (PID: 6688)
Malware-specific behavior (creating "System.dll" in Temp)
- WinPcap_4_1_3.exe (PID: 6688)
Executable content was dropped or overwritten
- WinPcap_4_1_3.exe (PID: 6688)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2420)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2420)
Manual execution by a user
- mspaint.exe (PID: 6324)
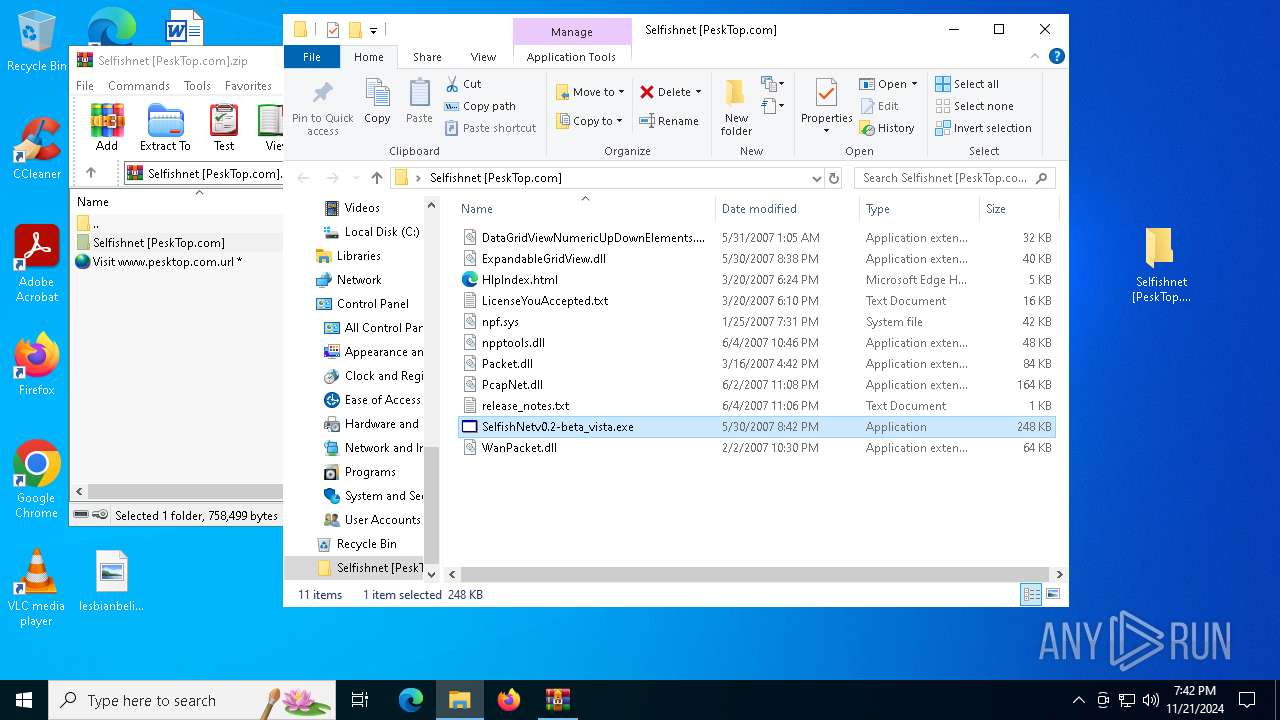
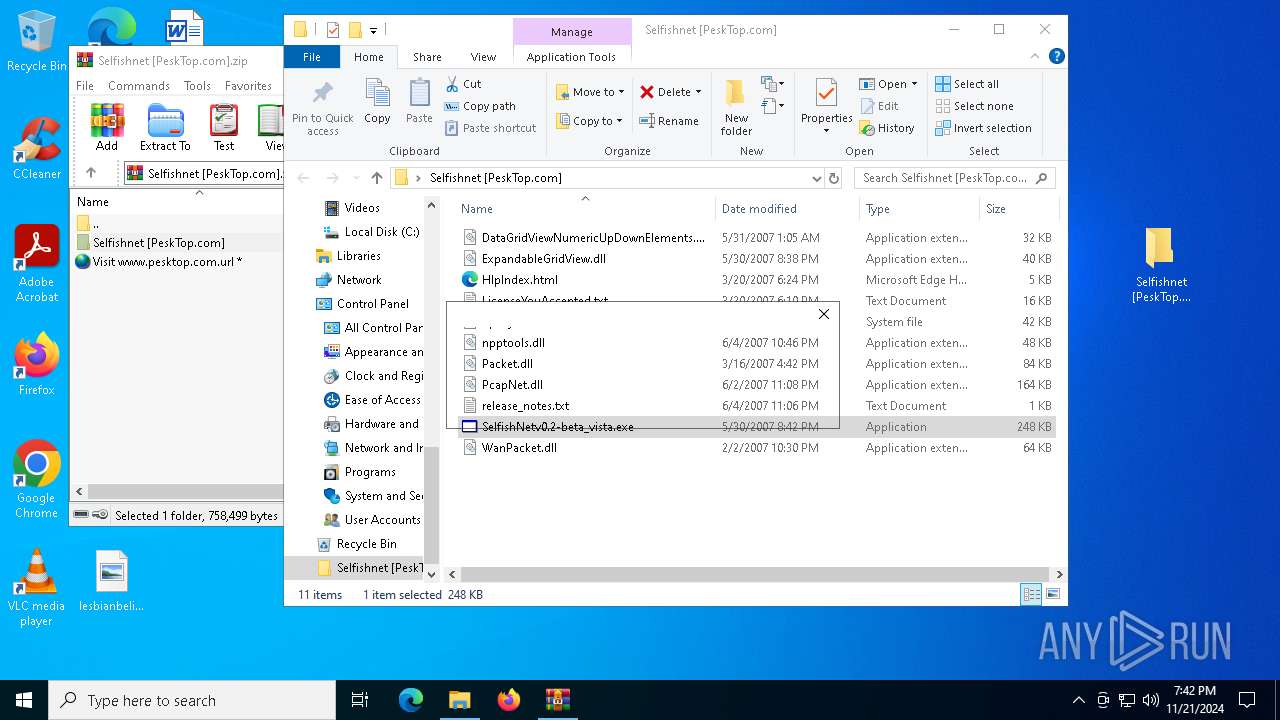
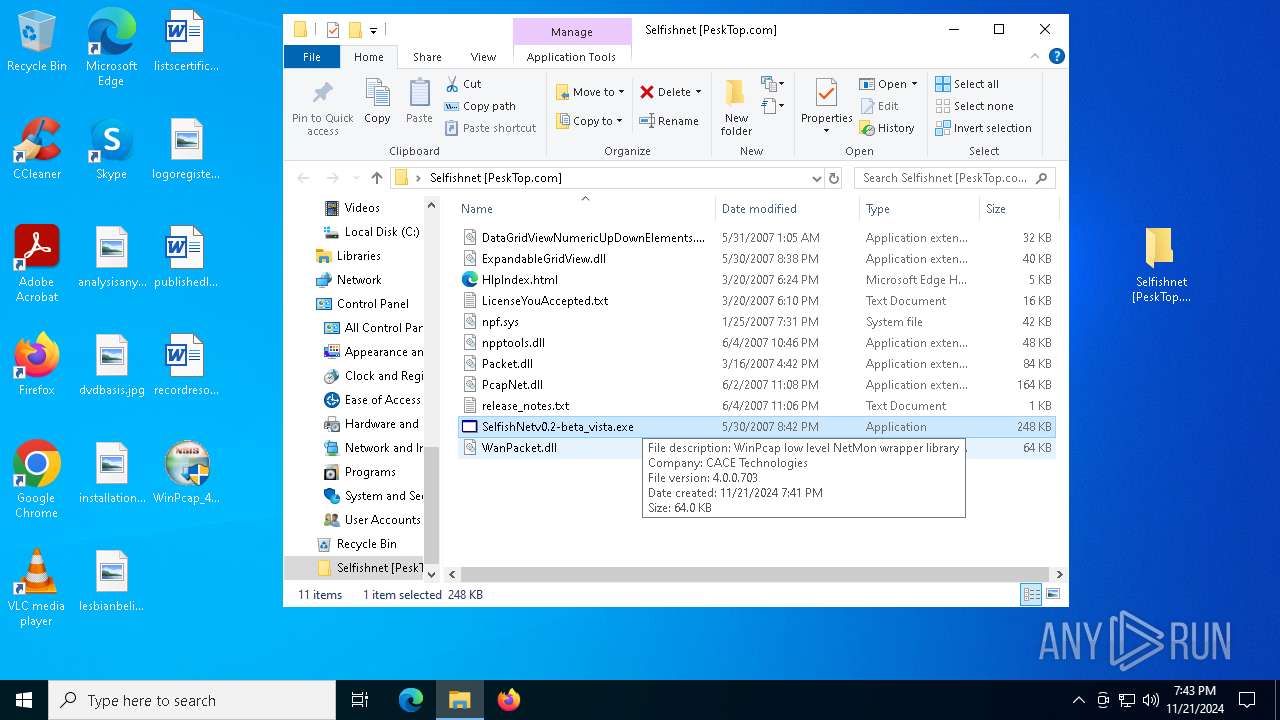
- SelfishNetv0.2-beta_vista.exe (PID: 6924)
- SelfishNetv0.2-beta_vista.exe (PID: 7164)
- SelfishNetv0.2-beta_vista.exe (PID: 6468)
- SelfishNetv0.2-beta_vista.exe (PID: 5340)
- WinPcap_4_1_3.exe (PID: 6688)
- WinPcap_4_1_3.exe (PID: 6640)
- SelfishNetv0.2-beta_vista.exe (PID: 6172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2016:03:06 15:12:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Selfishnet [PeskTop.com]/ |
Total processes
145
Monitored processes
13
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Selfishnet [PeskTop.com].zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5340 | "C:\Users\admin\Desktop\Selfishnet [PeskTop.com]\SelfishNetv0.2-beta_vista.exe" | C:\Users\admin\Desktop\Selfishnet [PeskTop.com]\SelfishNetv0.2-beta_vista.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6172 | "C:\Users\admin\Desktop\Selfishnet [PeskTop.com]\SelfishNetv0.2-beta_vista.exe" | C:\Users\admin\Desktop\Selfishnet [PeskTop.com]\SelfishNetv0.2-beta_vista.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6324 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\installationcountries.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6468 | "C:\Users\admin\Desktop\Selfishnet [PeskTop.com]\SelfishNetv0.2-beta_vista.exe" | C:\Users\admin\Desktop\Selfishnet [PeskTop.com]\SelfishNetv0.2-beta_vista.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
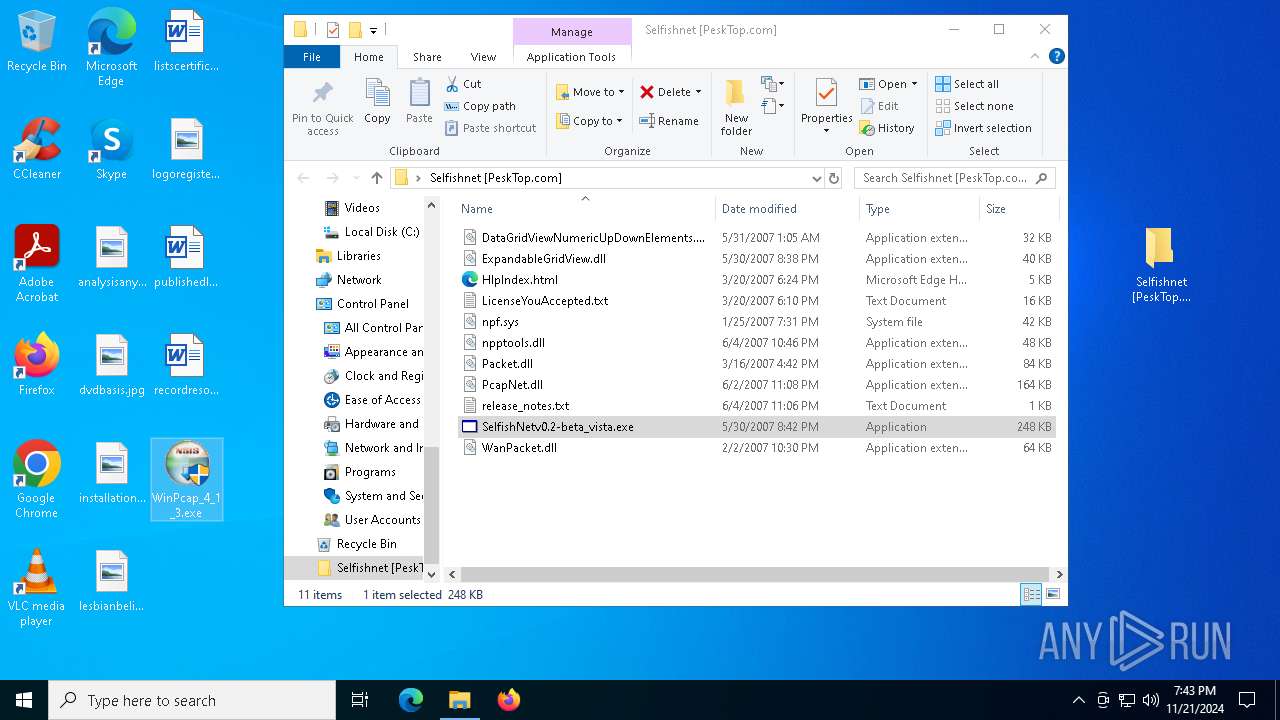
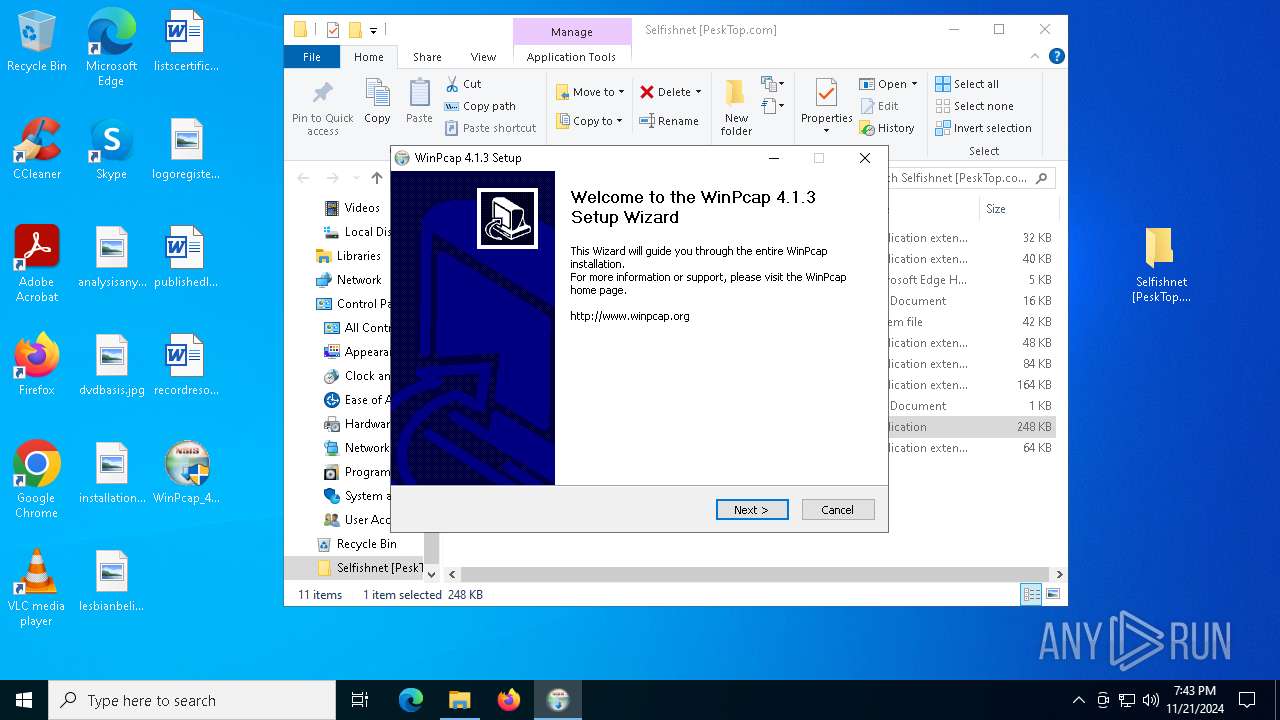
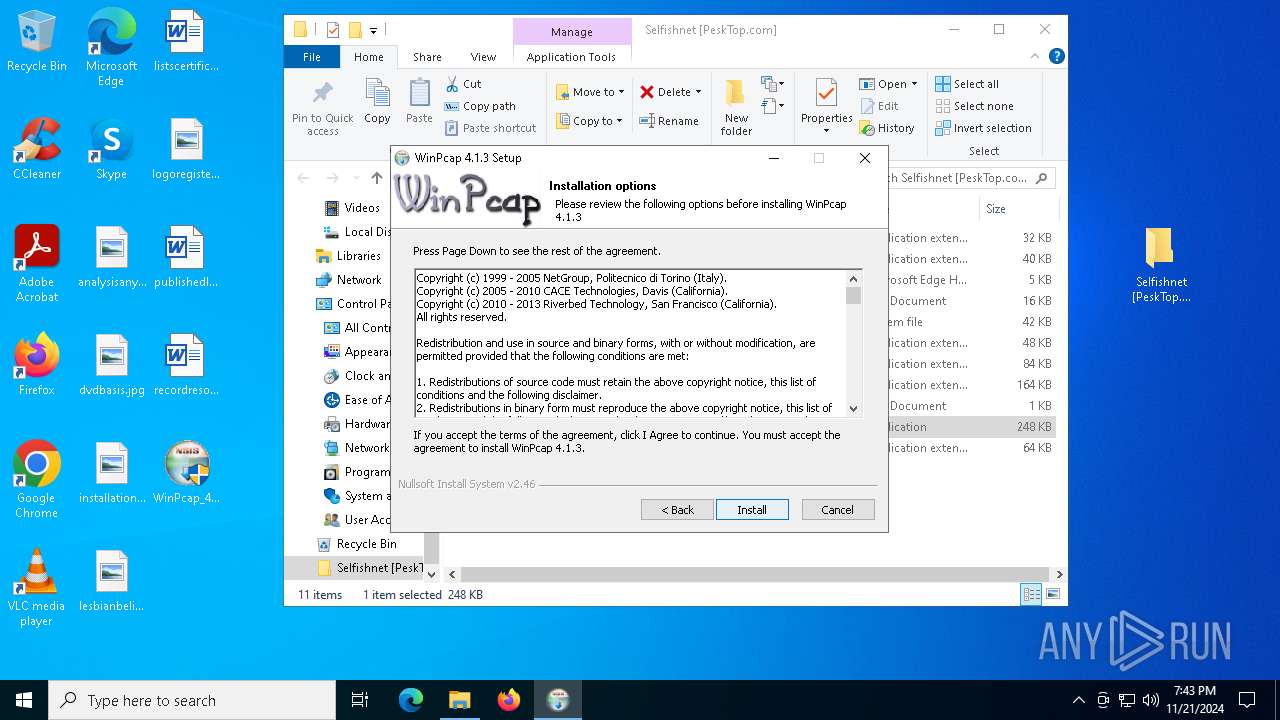
| 6640 | "C:\Users\admin\Desktop\WinPcap_4_1_3.exe" | C:\Users\admin\Desktop\WinPcap_4_1_3.exe | — | explorer.exe | |||||||||||
User: admin Company: Riverbed Technology, Inc. Integrity Level: MEDIUM Description: WinPcap 4.1.3 installer Exit code: 3221226540 Version: 4.1.0.2980 Modules
| |||||||||||||||
| 6688 | "C:\Users\admin\Desktop\WinPcap_4_1_3.exe" | C:\Users\admin\Desktop\WinPcap_4_1_3.exe | explorer.exe | ||||||||||||
User: admin Company: Riverbed Technology, Inc. Integrity Level: HIGH Description: WinPcap 4.1.3 installer Exit code: 0 Version: 4.1.0.2980 Modules
| |||||||||||||||
| 6780 | net start npf | C:\Windows\SysWOW64\net.exe | — | WinPcap_4_1_3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 866
Read events
3 808
Write events
57
Delete events
1
Modification events
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Selfishnet [PeskTop.com].zip | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (2420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
22
Suspicious files
3
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
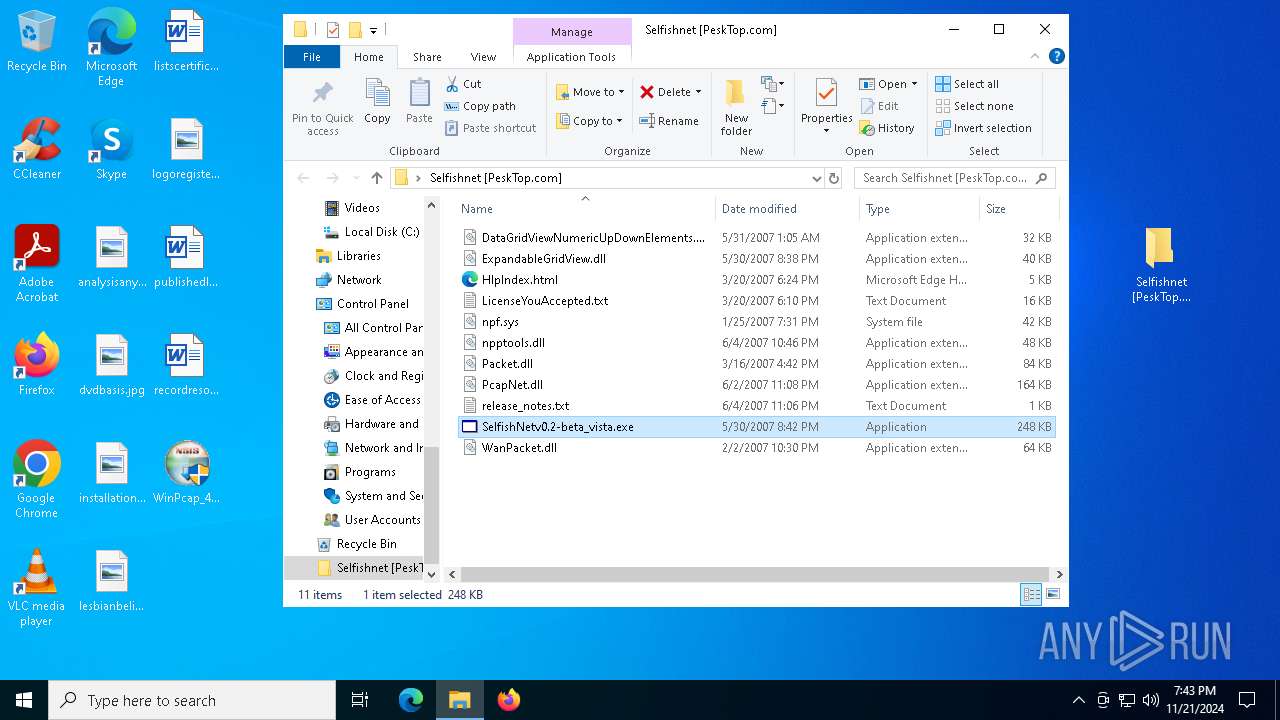
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\ExpandableGridView.dll | executable | |
MD5:3843D2CD531F8271A6A220DDE8B24905 | SHA256:957071214A373708DEDD9B30914D3776B49C0142D71010045763C5BFD2EA1726 | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\HlpIndex.html | xml | |
MD5:C9C4B7A22300961C3A06800C8E803A86 | SHA256:764C863CE6DC8A8EA9A74FDCA182394467022EEA7B0942DAA59CE4596F9A10E4 | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\DataGridViewNumericUpDownElements.dll | executable | |
MD5:BBE2E524FFC4250AE70BCFE2CC95BDB0 | SHA256:01A7841D39EA83444195F3BEF985342D99DCD925200FA1003F413A07F551D2FC | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\npf.sys | executable | |
MD5:B15E0180C43D8B5219196D76878CC2DD | SHA256:A4A102AAB8F91A5B452AE2C9A40F5EBC07BC62AF892AF57D6E3AD1F4340486AB | |||
| 6688 | WinPcap_4_1_3.exe | C:\Users\admin\AppData\Local\Temp\nsj282C.tmp\modern-header.bmp | image | |
MD5:D8F59A707B2A5000C7903595EDDC3D48 | SHA256:C0E284FDE834FE8A6F90504DBA7ABFF25B1E7DD4611483341203FD3EFC5DE8A6 | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\LicenseYouAccepted.txt | text | |
MD5:B8616F7EB5808DD404CCEA903459F848 | SHA256:A7EB88A3CB8FDFB2A874BF4E283AC3ED3BEEB3BCA7F7E05EBCA6D60DB0DDF236 | |||
| 6688 | WinPcap_4_1_3.exe | C:\Users\admin\AppData\Local\Temp\nsj282C.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\release_notes.txt | text | |
MD5:4B2878DFDE66E4BD503F0F894D99AC7E | SHA256:C40825BBB89A58C2FCE41CDC9801A8527F259F51548623BFE662DB32F80C40ED | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\PcapNet.dll | executable | |
MD5:54DBC0A3028ABA8C8D23E1AEE623331C | SHA256:0422466D93EA14C71A7C2A471FDAF092AD87E5B57F6BD3662E1F01D43339E4CE | |||
| 2420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2420.42590\Selfishnet [PeskTop.com]\npptools.dll | executable | |
MD5:48311B5A88816C6560A10D9FDA75DC7A | SHA256:4B722FFBE7F9211A08013318674DEBFBEC33FE66B812D697EE1072D57A01597F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
40
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6024 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6024 | RUXIMICS.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3760 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5656 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3760 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6024 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6024 | RUXIMICS.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6024 | RUXIMICS.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |