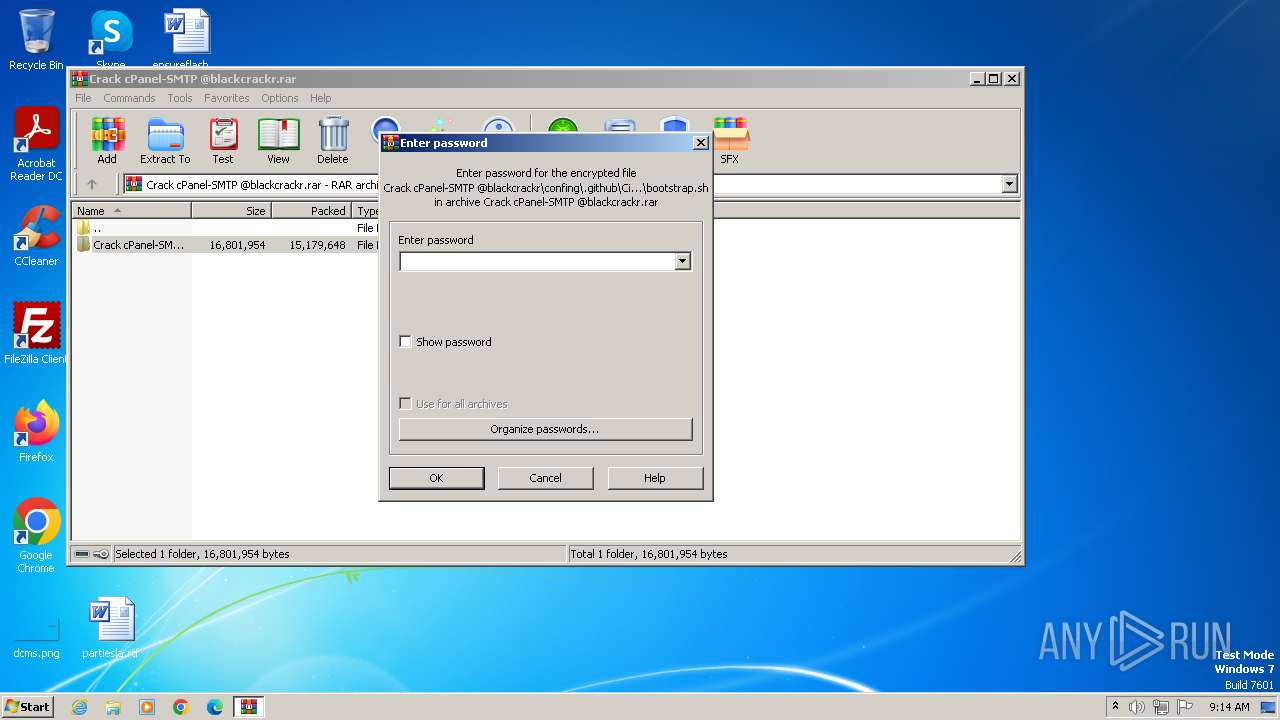
| File name: | Crack cPanel-SMTP @blackcrackr.rar |
| Full analysis: | https://app.any.run/tasks/c4a4446c-7de7-42f7-a4e7-bc0ff6cf1da2 |
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2023, 08:13:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 3F24ADD64DF442112545AD57BBAD1076 |
| SHA1: | 1ED0CEC1CEFD2A65286F8E6B0FF6AD2A38E78372 |
| SHA256: | 3DD6D7B74ADF0B6D5221F9F8CB45140C687446F26D0B8BA3D13224480ED25E14 |
| SSDEEP: | 98304:y4uubfRY/WD25KSDFeKolv7ke4TEYA3yatljqBdGChsY5ABcP5p7igTcMmOmxpCG:U74AXALUyJWfWMHP3S5Z0kBfJ4MUa |
MALICIOUS
Application was dropped or rewritten from another process
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
STORMKITTY has been detected (YARA)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
Drops the executable file immediately after the start
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
Steals credentials
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
Starts CMD.EXE for commands execution
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
Starts application with an unusual extension
- cmd.exe (PID: 2756)
- cmd.exe (PID: 1992)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 2756)
- cmd.exe (PID: 1992)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2756)
INFO
Checks supported languages
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
Reads the computer name
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
Manual execution by a user
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- explorer.exe (PID: 124)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
- notepad.exe (PID: 1656)
Reads Environment values
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2260)
Reads the machine GUID from the registry
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3592)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3884)
Creates files or folders in the user directory
- Crack cPanel-SMTP @blackcrackr.exe (PID: 2960)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 4008)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1904)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 1332)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3120)
- Crack cPanel-SMTP @blackcrackr.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
StormKitty
(PID) Process(2960) Crack cPanel-SMTP @blackcrackr.exe
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send
Token5800603586:AAEQALtYjWlWxGJKxTd_tkViM_h_6KdEMT0
ChatId5901231421
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignaturefO0qB0gf/MpKaM5U2A7opVj1fT5LkspjCd4YgDAcyNqm0Za3UYVjOOgwZzBofZp6kRl7cT8O2XYe2B+blFZgRx7SFwdPSYL76LaybqPZljDFMWnoVZExHC5XeE5GYwITqnTp/TDVoPo1nPMXnvlDO3XTlvj+GaR6ESEtw0m9k/h+wgr2p+FNjMEYrCDbJ2seqNA93eDzw/dLELe/u2jJcdGj/mt0bzSle75QTgY6y2sFek+KjrpF4lhiwrhiefa7CKyFq7gV8z6MkHyLLLx1WYyNQ7oy62zpoW0eprRhd8+t...
Keys
AES712658663e0bd7e5fcbbd395a6cef5cc91477688a440ea7b61c16c014d049472
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
(PID) Process(4008) Crack cPanel-SMTP @blackcrackr.exe
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send
Token5800603586:AAEQALtYjWlWxGJKxTd_tkViM_h_6KdEMT0
ChatId5901231421
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignaturefO0qB0gf/MpKaM5U2A7opVj1fT5LkspjCd4YgDAcyNqm0Za3UYVjOOgwZzBofZp6kRl7cT8O2XYe2B+blFZgRx7SFwdPSYL76LaybqPZljDFMWnoVZExHC5XeE5GYwITqnTp/TDVoPo1nPMXnvlDO3XTlvj+GaR6ESEtw0m9k/h+wgr2p+FNjMEYrCDbJ2seqNA93eDzw/dLELe/u2jJcdGj/mt0bzSle75QTgY6y2sFek+KjrpF4lhiwrhiefa7CKyFq7gV8z6MkHyLLLx1WYyNQ7oy62zpoW0eprRhd8+t...
Keys
AES712658663e0bd7e5fcbbd395a6cef5cc91477688a440ea7b61c16c014d049472
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
61
Monitored processes
18
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1228 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 1332 | "C:\Users\admin\Desktop\Crack cPanel-SMTP @blackcrackr\Crack cPanel-SMTP @blackcrackr.exe" | C:\Users\admin\Desktop\Crack cPanel-SMTP @blackcrackr\Crack cPanel-SMTP @blackcrackr.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1656 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Crack cPanel-SMTP @blackcrackr\socks5proxy.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | "C:\Users\admin\Desktop\Crack cPanel-SMTP @blackcrackr\Crack cPanel-SMTP @blackcrackr.exe" | C:\Users\admin\Desktop\Crack cPanel-SMTP @blackcrackr\Crack cPanel-SMTP @blackcrackr.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Client Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1992 | "cmd.exe" /C chcp 65001 && netsh wlan show networks mode=bssid | C:\Windows\System32\cmd.exe | — | Crack cPanel-SMTP @blackcrackr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 2232 | netsh wlan show networks mode=bssid | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 2260 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Crack cPanel-SMTP @blackcrackr.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2504 | netsh wlan show profile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 2756 | "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All | C:\Windows\System32\cmd.exe | — | Crack cPanel-SMTP @blackcrackr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
Total events
3 504
Read events
3 399
Write events
105
Delete events
0
Modification events
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2960) Crack cPanel-SMTP @blackcrackr.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
2
Suspicious files
97
Text files
7 710
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Doc\config.rar | — | |
MD5:— | SHA256:— | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Cinder\module\cinder.cpp | text | |
MD5:8E6D746C4789A1FB2E371E05CAD82917 | SHA256:9655473F55F78C78D3E96F85C75B8508077DCFA34C604259925029257EE672CD | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Doc\faq\python-video-icon.png | image | |
MD5:685483151682142455A104C0A2850379 | SHA256:4F395910793AB07158609755B4C4C401380243757E08B680B411BF7D14A88E12 | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Doc\includes\custom4.c | text | |
MD5:199F383FF69327B716B9648F7B0DBA95 | SHA256:E9BB866D72AD739C943F6D4C92A2F8C7E0B6B553438A3891FE06C821AB0EF13F | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Cinder\module\bootstrap.sh | text | |
MD5:1BBC7A86DFE1ABB36E680DCB44AEE01B | SHA256:959D78B75BB6C4B82E861F6F7D4234CFAC7F3A4D2F2FE1D0052FF6DCB266CE1C | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Doc\includes\custom3.c | text | |
MD5:7C5CC39E9F40C73EC1BAA230E36F2040 | SHA256:DD0EAABD1A73A6E54309F7120240BFAC48AD88C71B6685D5FD0791C5B67008CC | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\CinderDoc\images\Cinder-Logo-Dark.svg | image | |
MD5:F186CD90DF3D8C03682CFA0346A8E64C | SHA256:5F88E1302977661E04A013E627B5158252F1664660FB9B75A637EC75879CD2B7 | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\CinderDoc\images\Cinder-Logo-White.svg | image | |
MD5:8424F05EFB4DFCA2D7042E98C7559089 | SHA256:06A140AA7928D80F157BC9939B22D429366430794AC25A6297707B3366BA6627 | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Cinder\module\build.sh | text | |
MD5:7F61039372909AADDE0C1E89ED23FD7E | SHA256:146A03A19072099F4EA50C61E2871745FFA9D6BE7DBE9F728B317E2612908B83 | |||
| 2260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2260.32827\Crack cPanel-SMTP @blackcrackr\confing\.github\Cinder\module\make-current-symbols.sh | text | |
MD5:0089C7D095EF05173A07BB4D13DDCB5D | SHA256:FFAE12089B9EEB61C811E2B8FB03EE972A6AAE9C93A67D0475CDD73F47C63161 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |