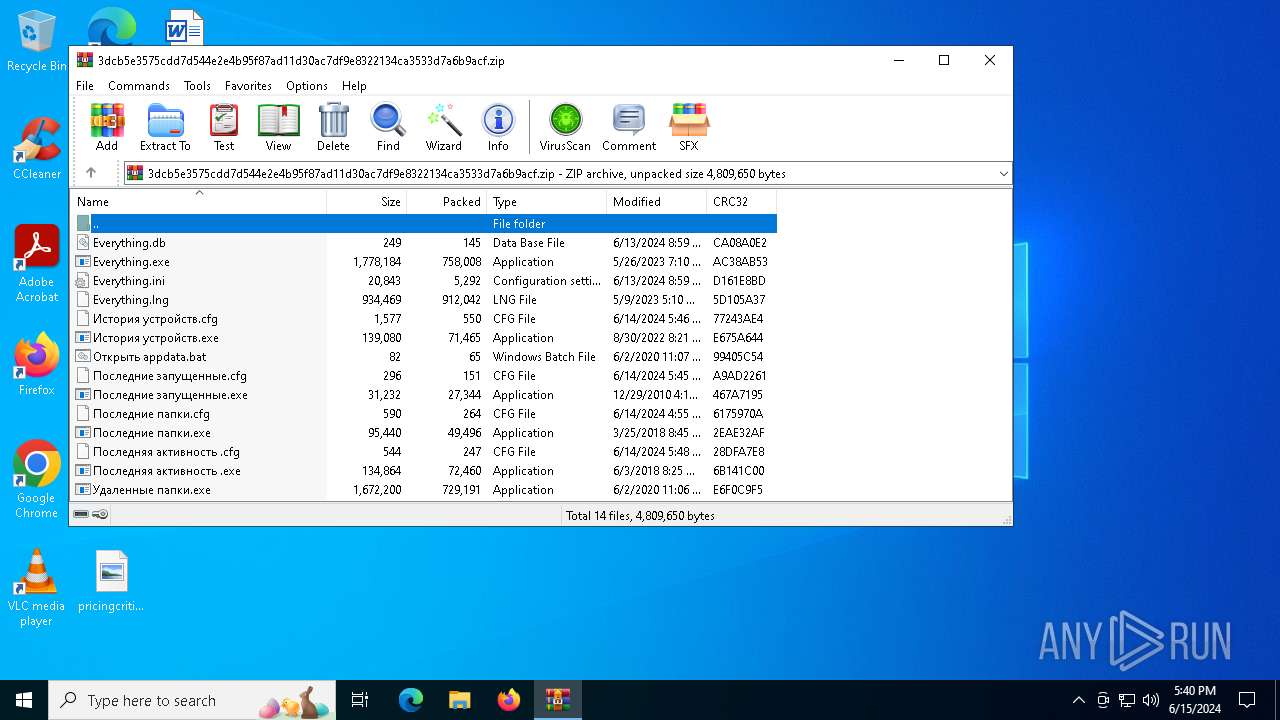
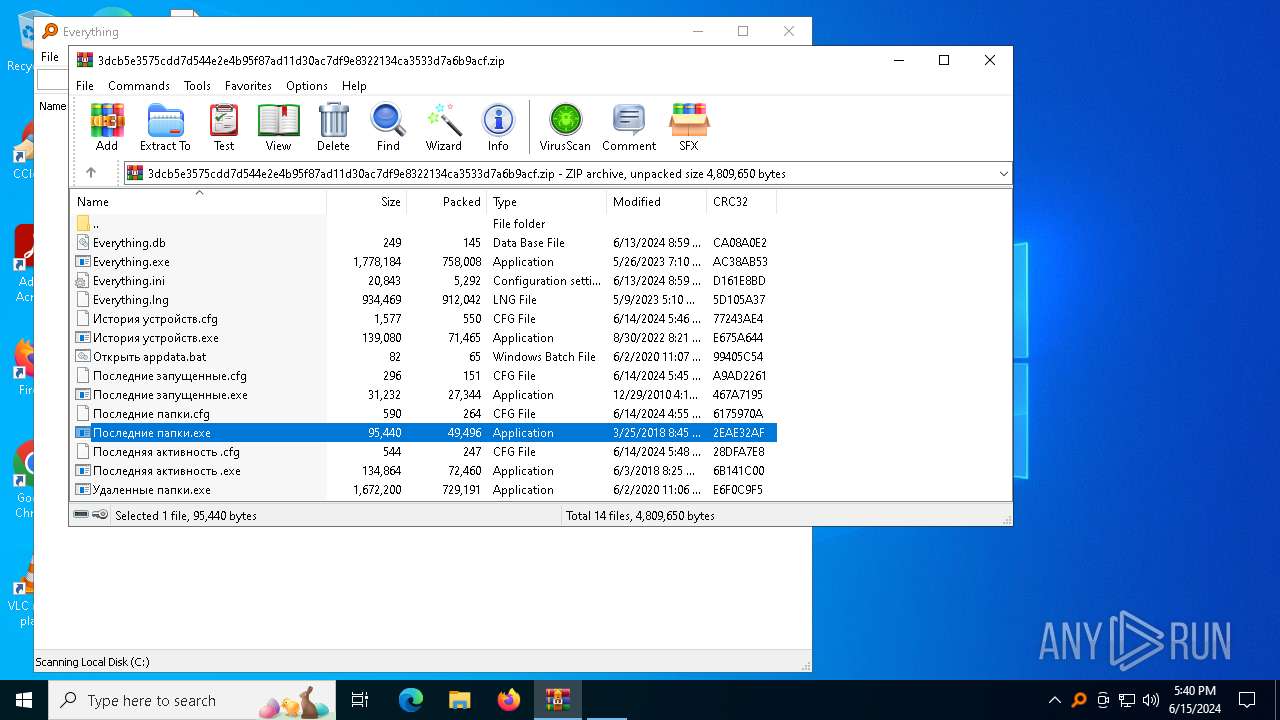
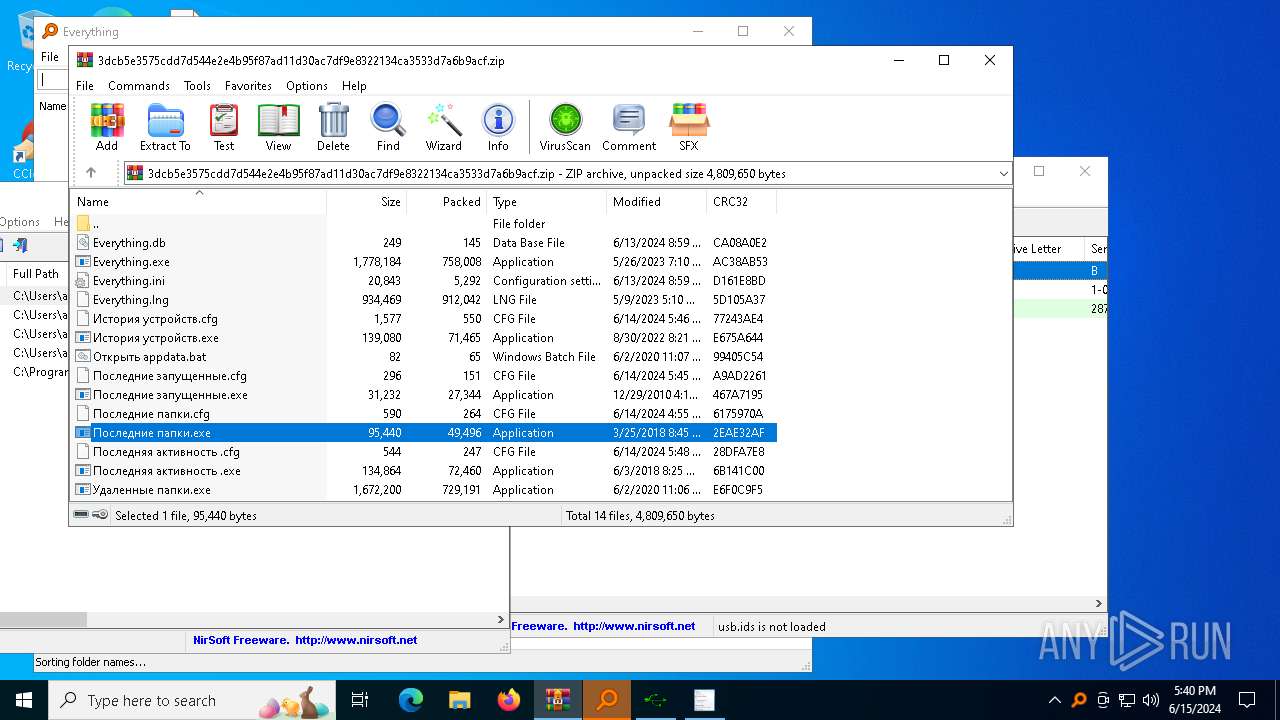
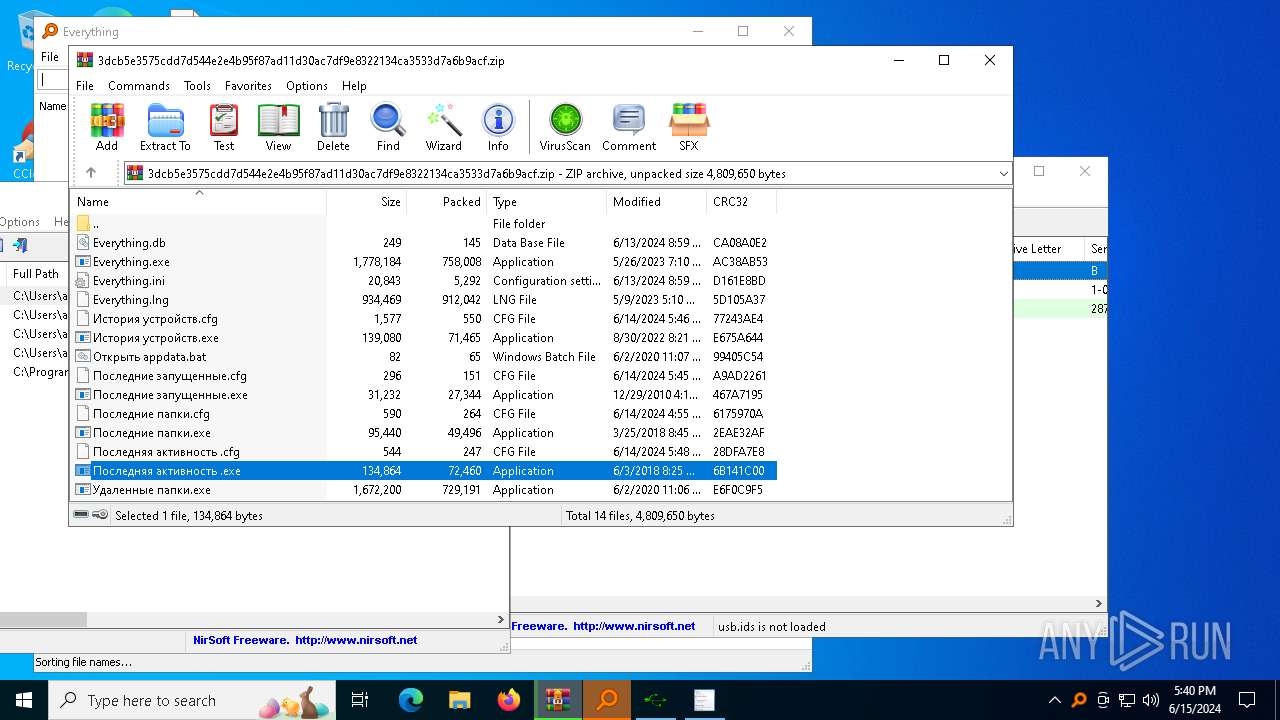
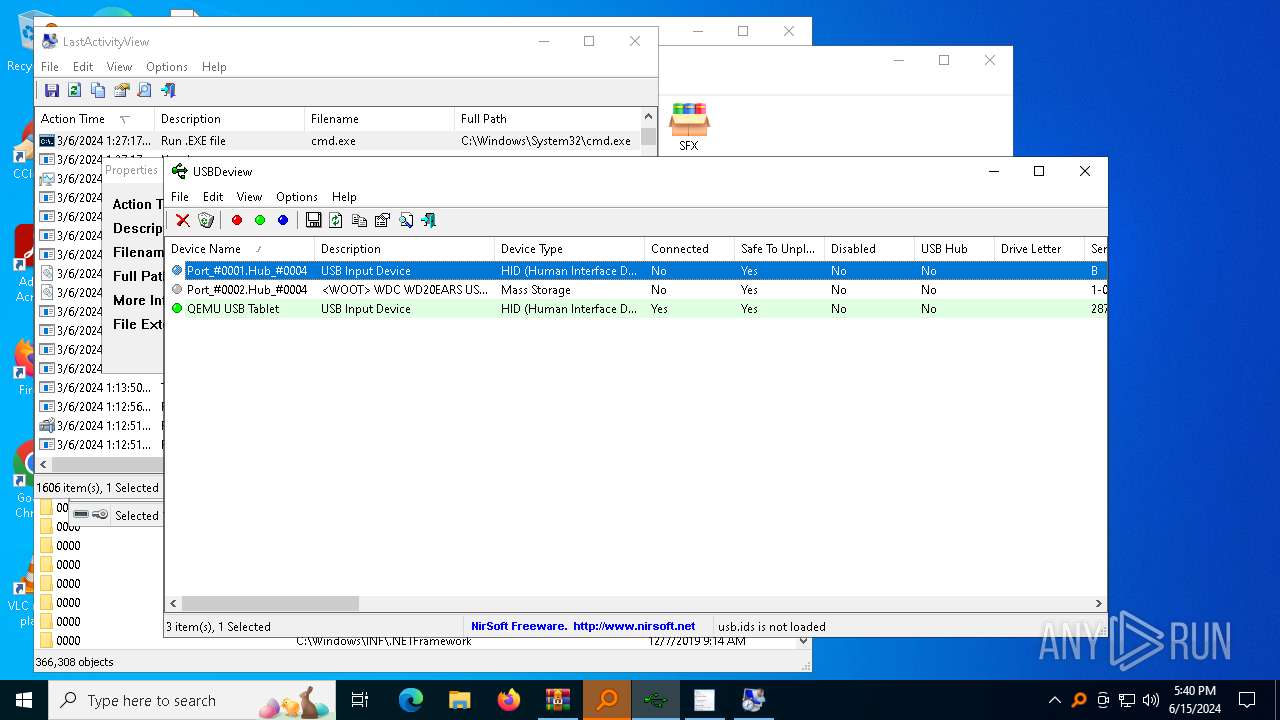
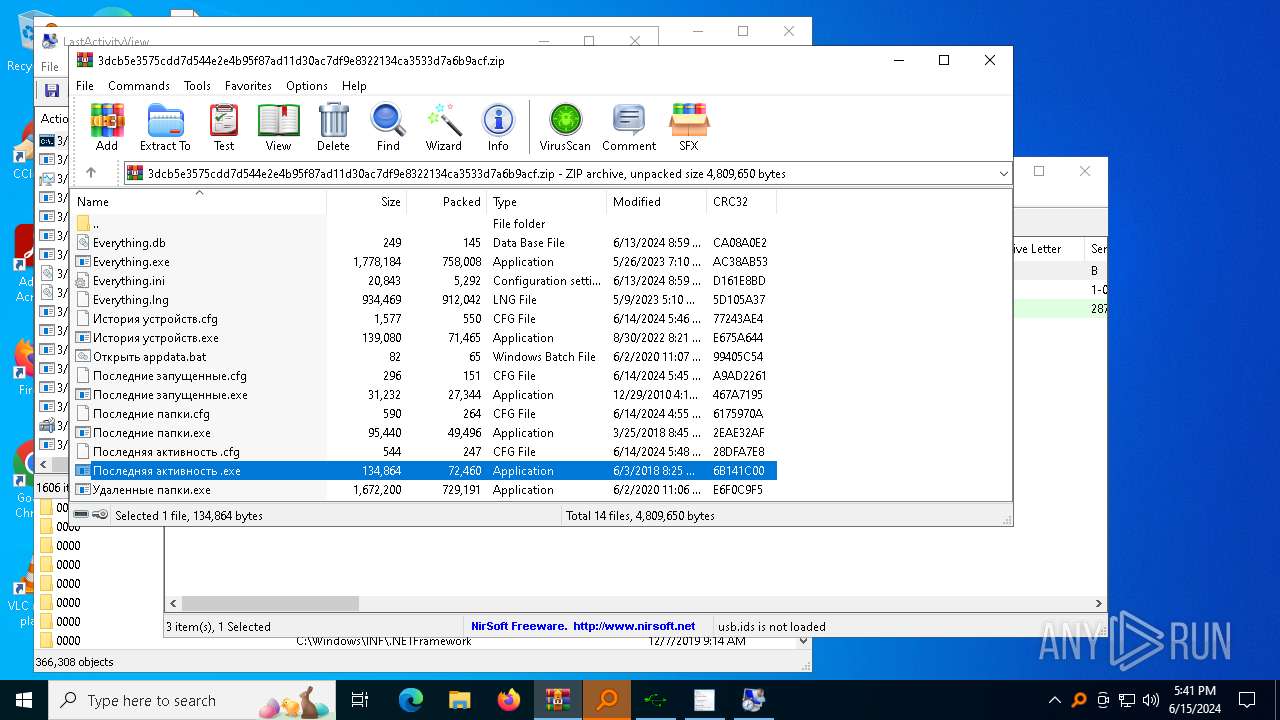
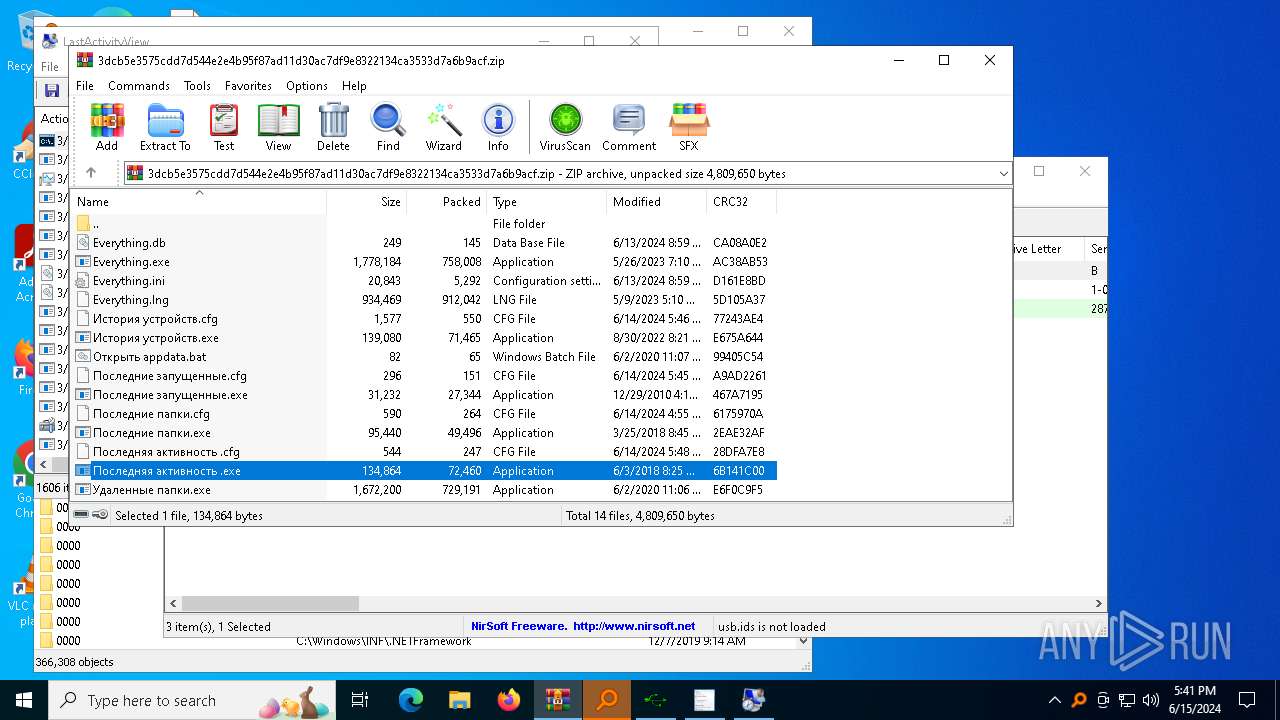
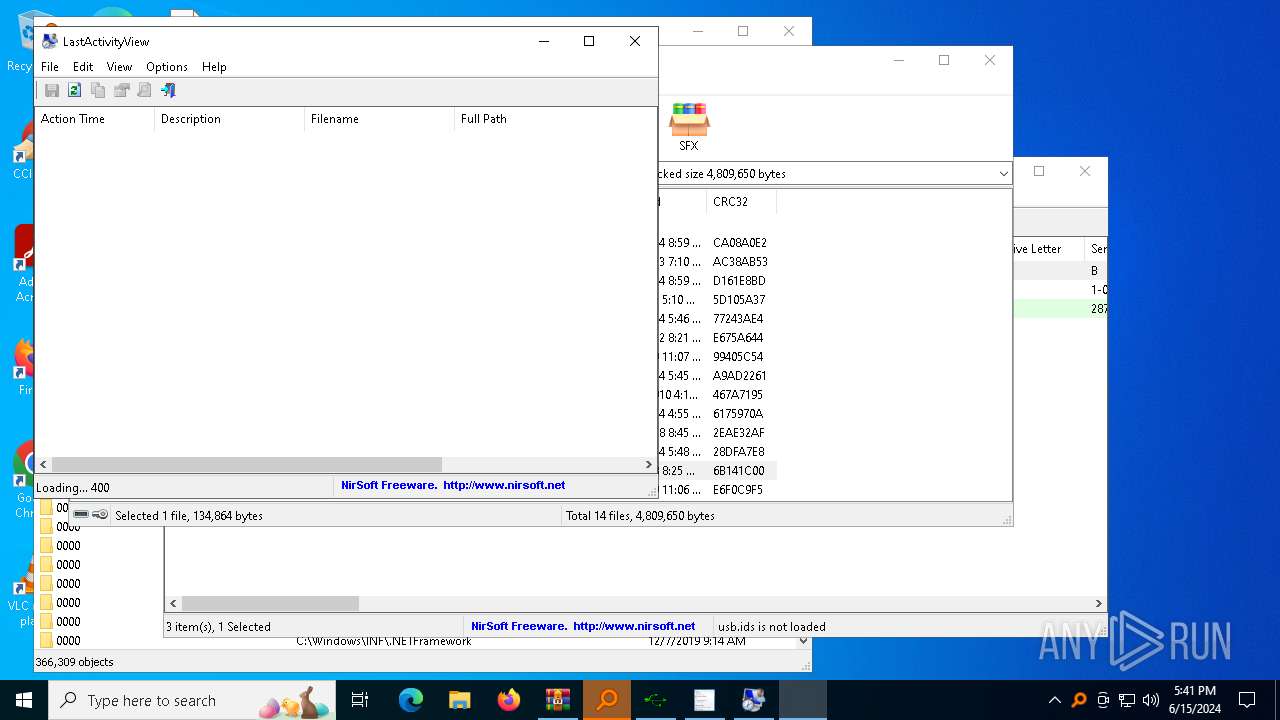
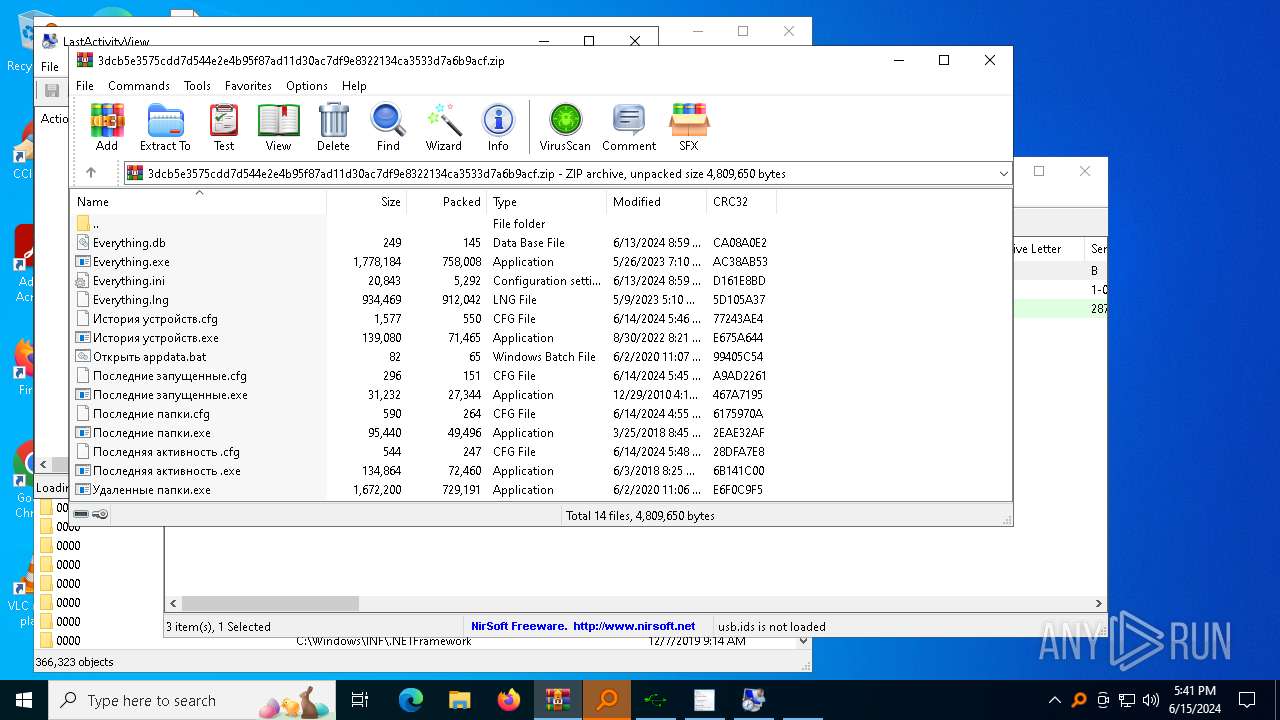
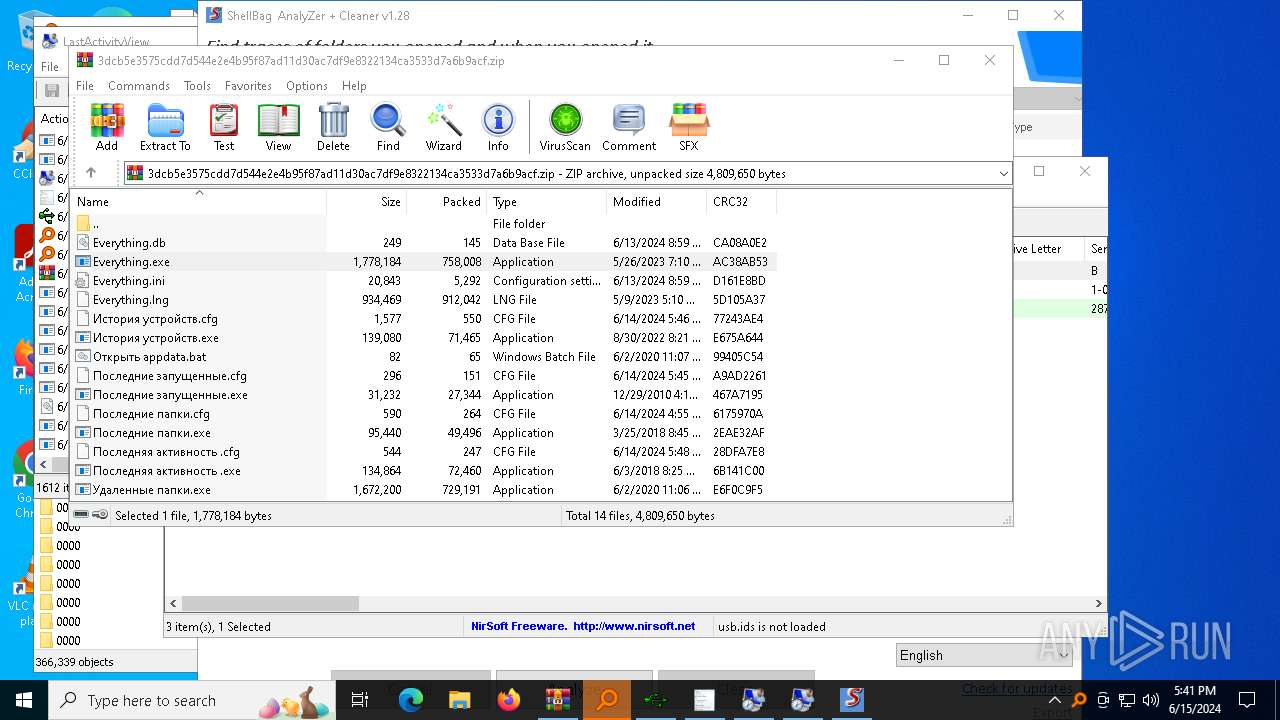
| File name: | 3dcb5e3575cdd7d544e2e4b95f87ad11d30ac7df9e8322134ca3533d7a6b9acf.zip |
| Full analysis: | https://app.any.run/tasks/1f6514aa-41d1-42ae-8d90-5161686f799f |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2024, 17:40:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AF69B92083813D541E38E2B750168A8F |
| SHA1: | 16397C26380BFA8DD7FA27D271398A0090188EA1 |
| SHA256: | 3DCB5E3575CDD7D544E2E4B95F87AD11D30AC7DF9E8322134CA3533D7A6B9ACF |
| SSDEEP: | 98304:9e1GSRkz61AC5/FM0gl8ICun3xUdQnvWqMHvIU0YG8knEVpwktWCtuuJxldgi7aE:QO3qxIw |
MALICIOUS
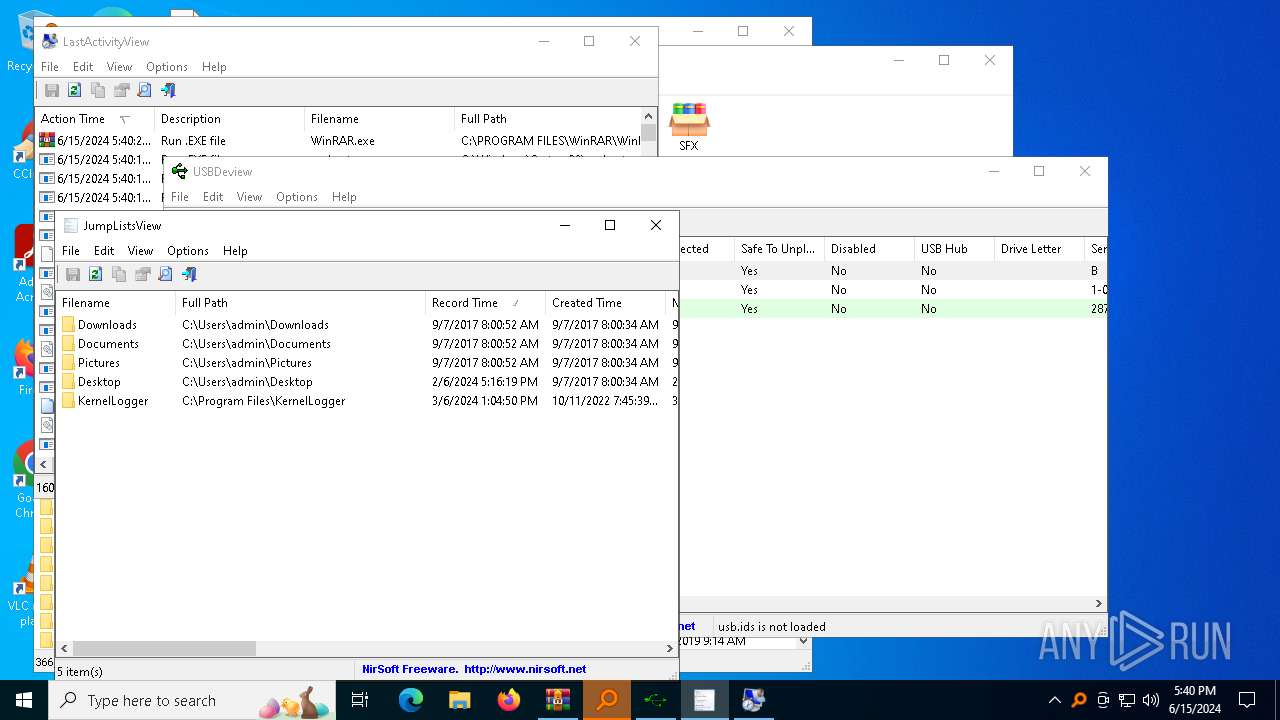
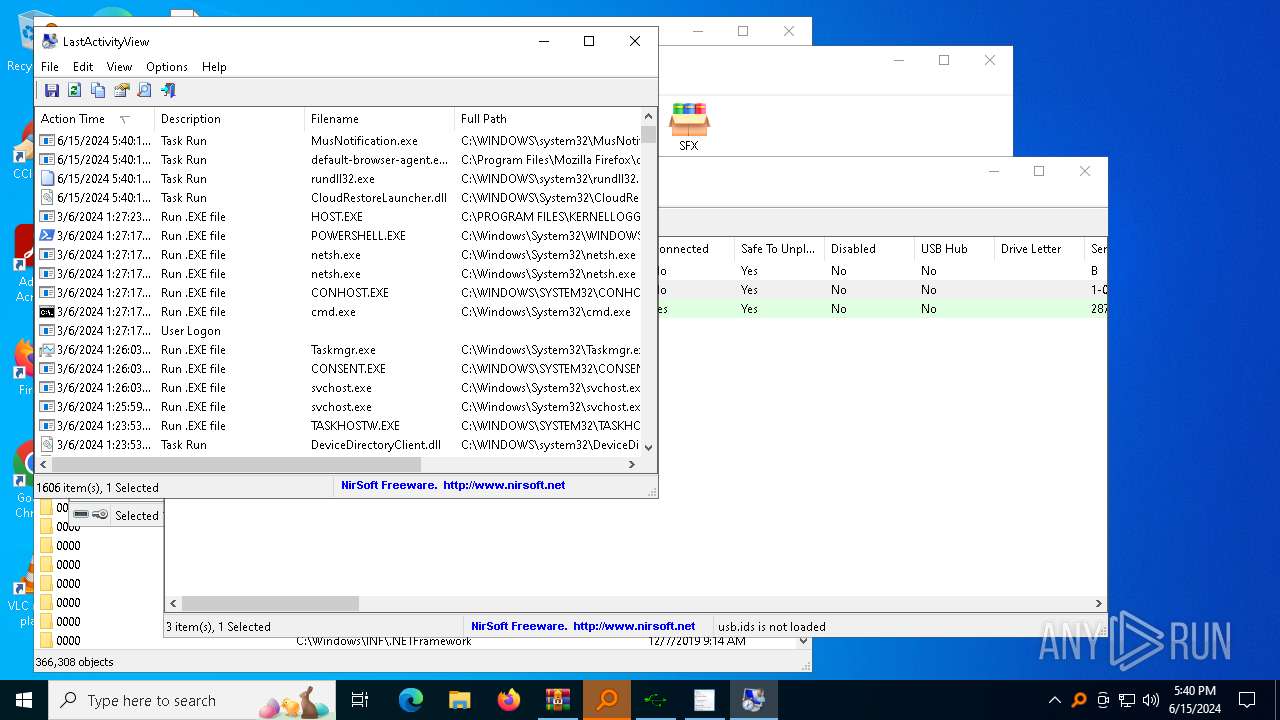
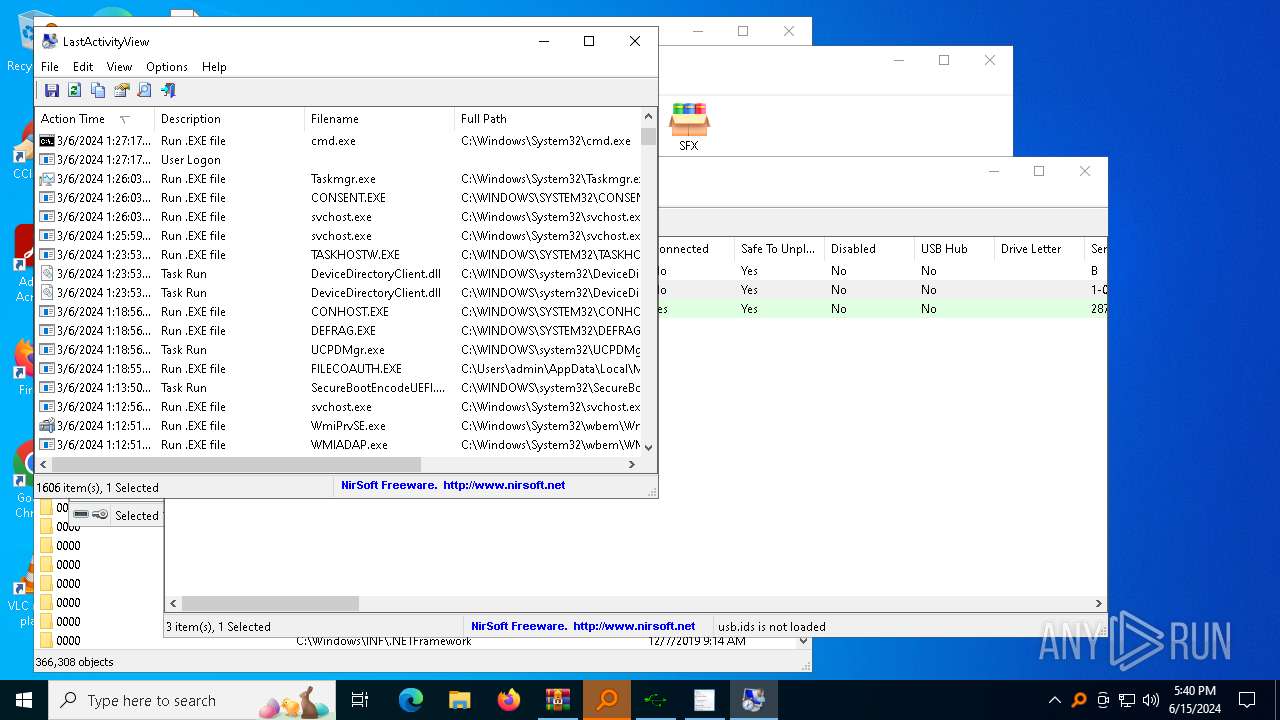
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5620)
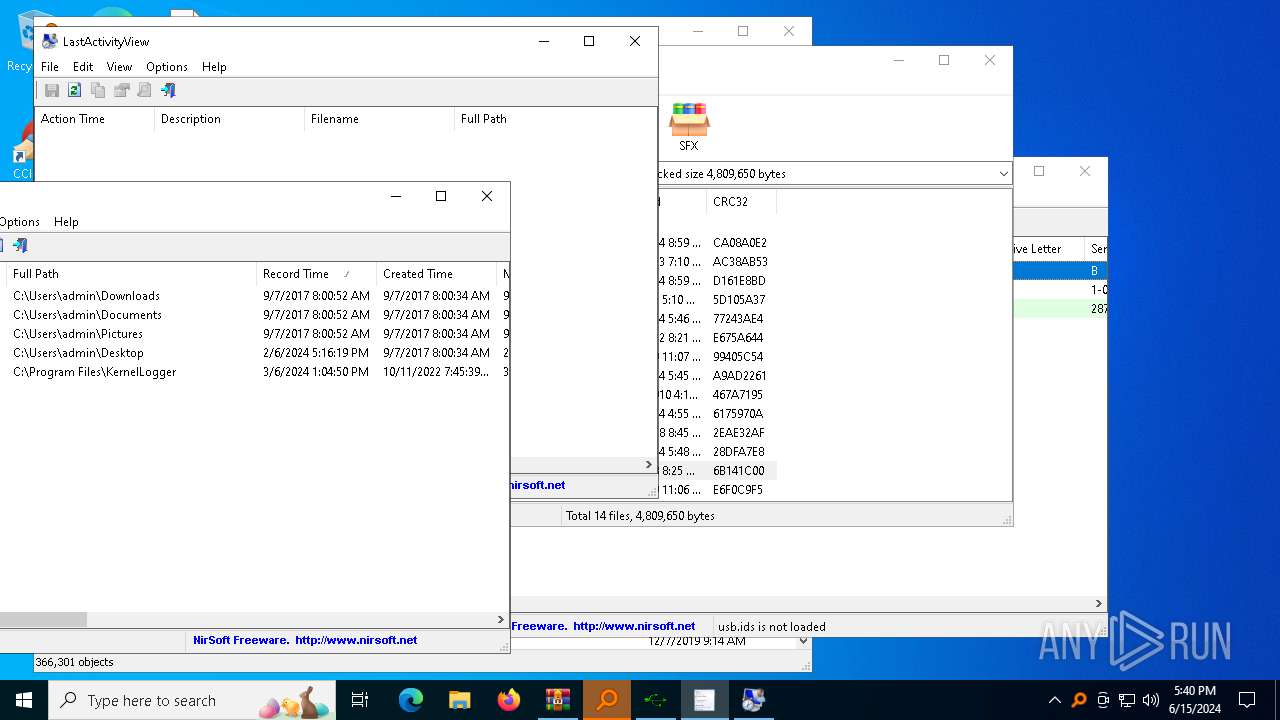
Actions looks like stealing of personal data
- Everything.exe (PID: 2084)
- Последняя активность .exe (PID: 2312)
- Последняя активность .exe (PID: 3196)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5620)
- Everything.exe (PID: 3644)
- Последняя активность .exe (PID: 2312)
- Последняя активность .exe (PID: 3196)
- Everything.exe (PID: 4424)
- Everything.exe (PID: 2084)
Application launched itself
- Everything.exe (PID: 3644)
- Everything.exe (PID: 4424)
Reads the date of Windows installation
- Everything.exe (PID: 3644)
- Everything.exe (PID: 4424)
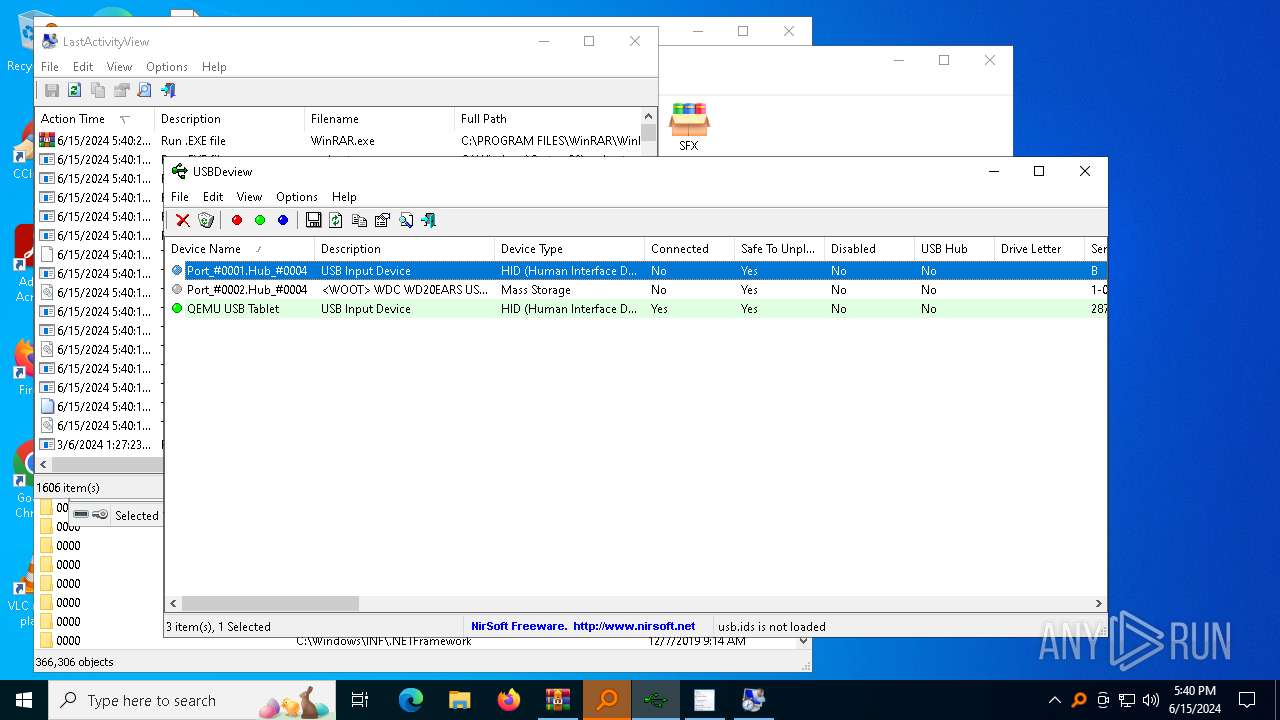
Read disk information to detect sandboxing environments
- История устройств.exe (PID: 708)
Searches for installed software
- Последняя активность .exe (PID: 2312)
- Последняя активность .exe (PID: 3196)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5620)
Reads the computer name
- Everything.exe (PID: 3644)
- Everything.exe (PID: 2084)
- История устройств.exe (PID: 708)
- Последние папки.exe (PID: 5528)
- Последняя активность .exe (PID: 3196)
- Удаленные папки.exe (PID: 1120)
- Everything.exe (PID: 4424)
- Everything.exe (PID: 472)
- Последняя активность .exe (PID: 2312)
Checks supported languages
- Everything.exe (PID: 3644)
- История устройств.exe (PID: 708)
- Последние папки.exe (PID: 5528)
- Everything.exe (PID: 2084)
- Последняя активность .exe (PID: 2312)
- Последняя активность .exe (PID: 3196)
- Everything.exe (PID: 4424)
- Удаленные папки.exe (PID: 1120)
- Everything.exe (PID: 472)
Process checks computer location settings
- Everything.exe (PID: 3644)
- Everything.exe (PID: 4424)
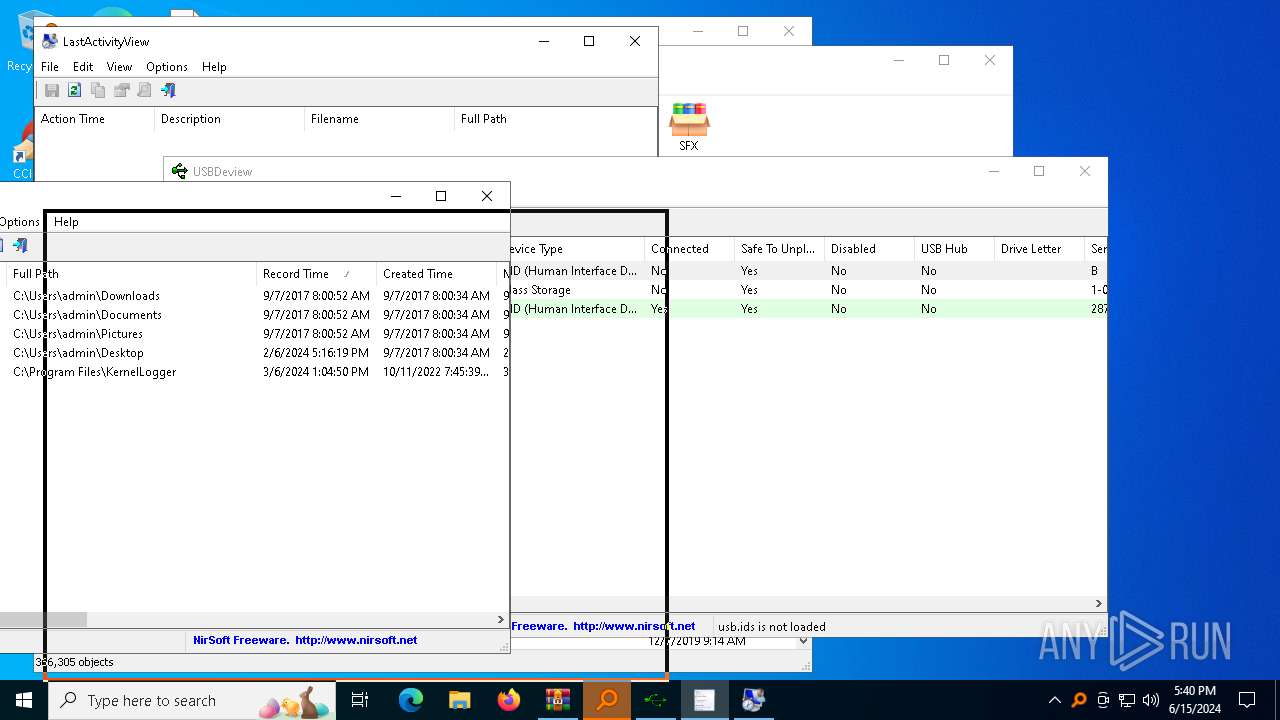
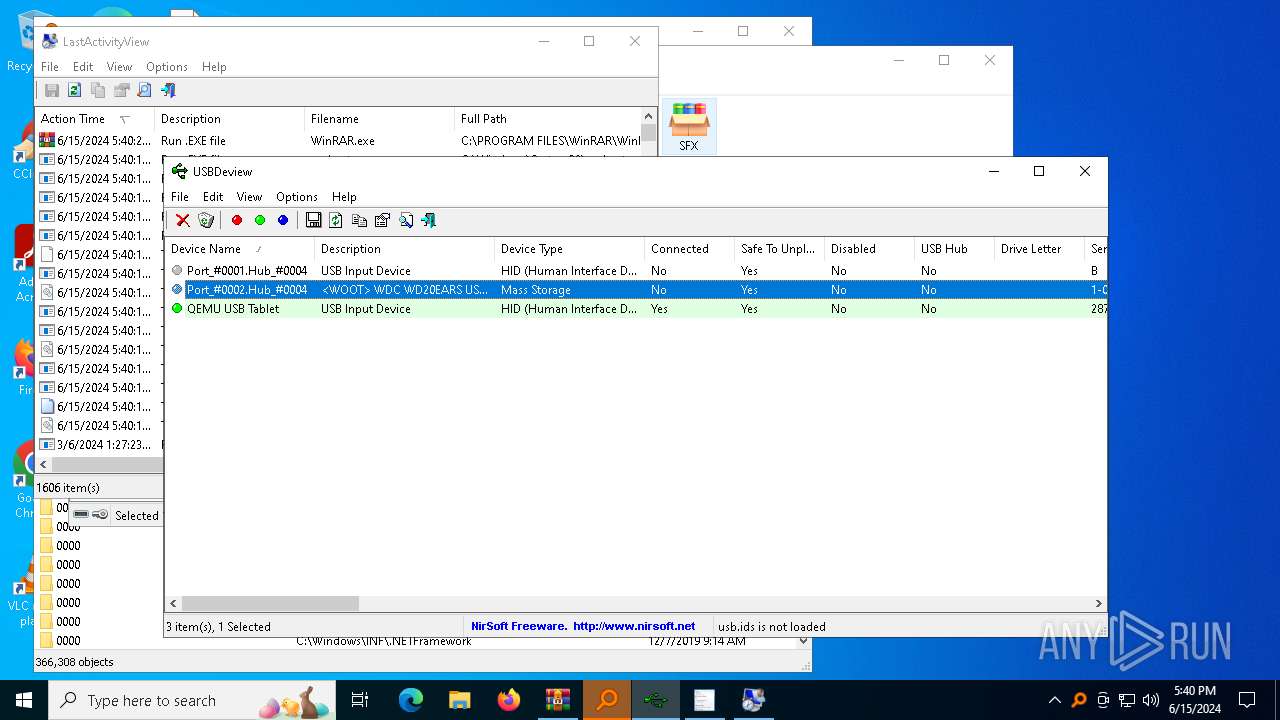
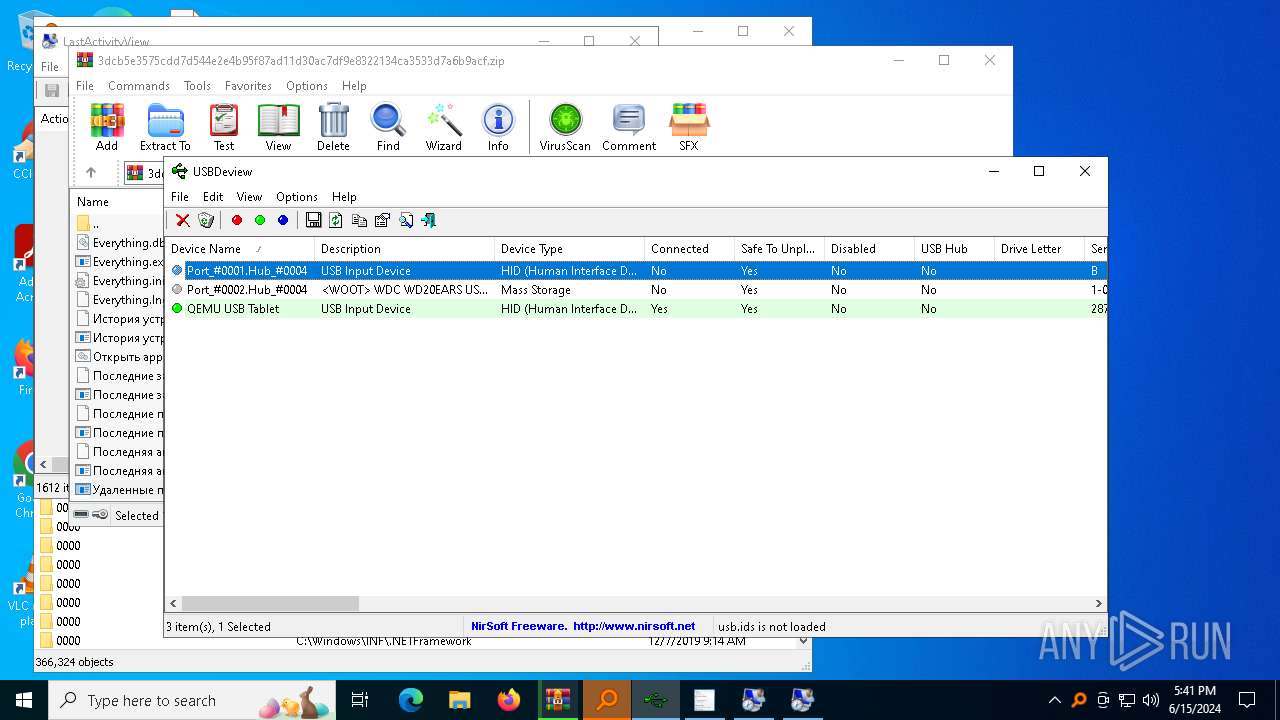
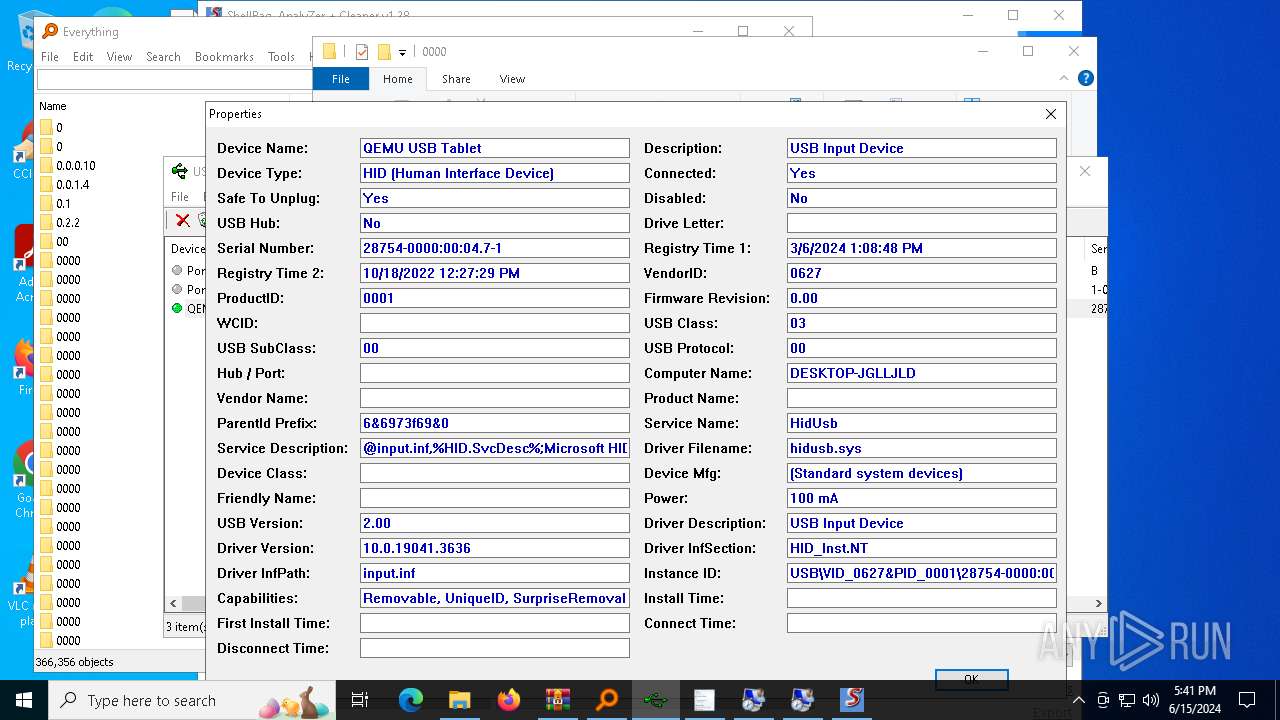
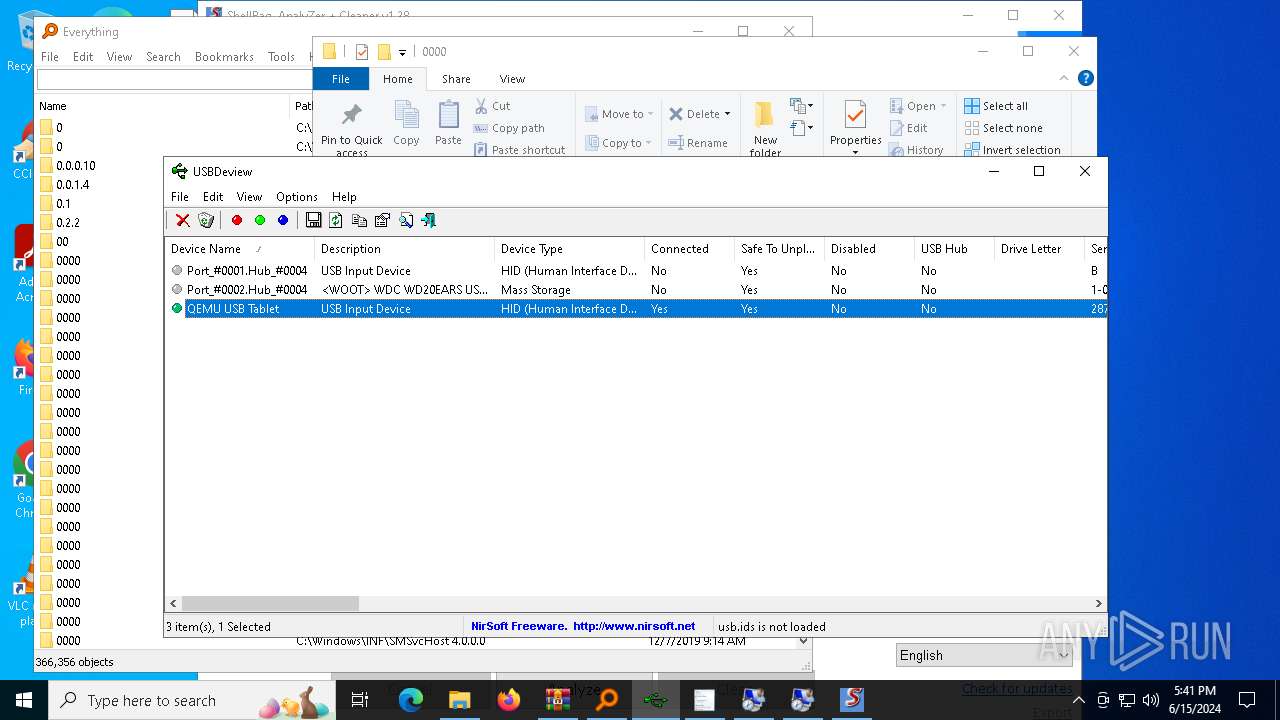
NirSoft software is detected
- История устройств.exe (PID: 708)
- Последняя активность .exe (PID: 2312)
- Последние папки.exe (PID: 5528)
- Последняя активность .exe (PID: 4936)
- Последняя активность .exe (PID: 624)
- Последняя активность .exe (PID: 3196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:05:26 10:10:00 |
| ZipCRC: | 0xac38ab53 |
| ZipCompressedSize: | 758008 |
| ZipUncompressedSize: | 1778184 |
| ZipFileName: | Everything.exe |
Total processes
133
Monitored processes
14
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7933\Everything.exe" -isrunas | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7933\Everything.exe | Everything.exe | ||||||||||||
User: admin Company: voidtools Integrity Level: HIGH Description: Everything Exit code: 0 Version: 1.4.1.1024 Modules
| |||||||||||||||
| 624 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7281\Последняя активность .exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7281\Последняя активность .exe | — | WinRAR.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: LastActivityView Exit code: 3221226540 Version: 1.32 Modules
| |||||||||||||||
| 708 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4255\История устройств.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4255\История устройств.exe | — | WinRAR.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: MEDIUM Description: Lists USB Devices Version: 3.06 Modules
| |||||||||||||||
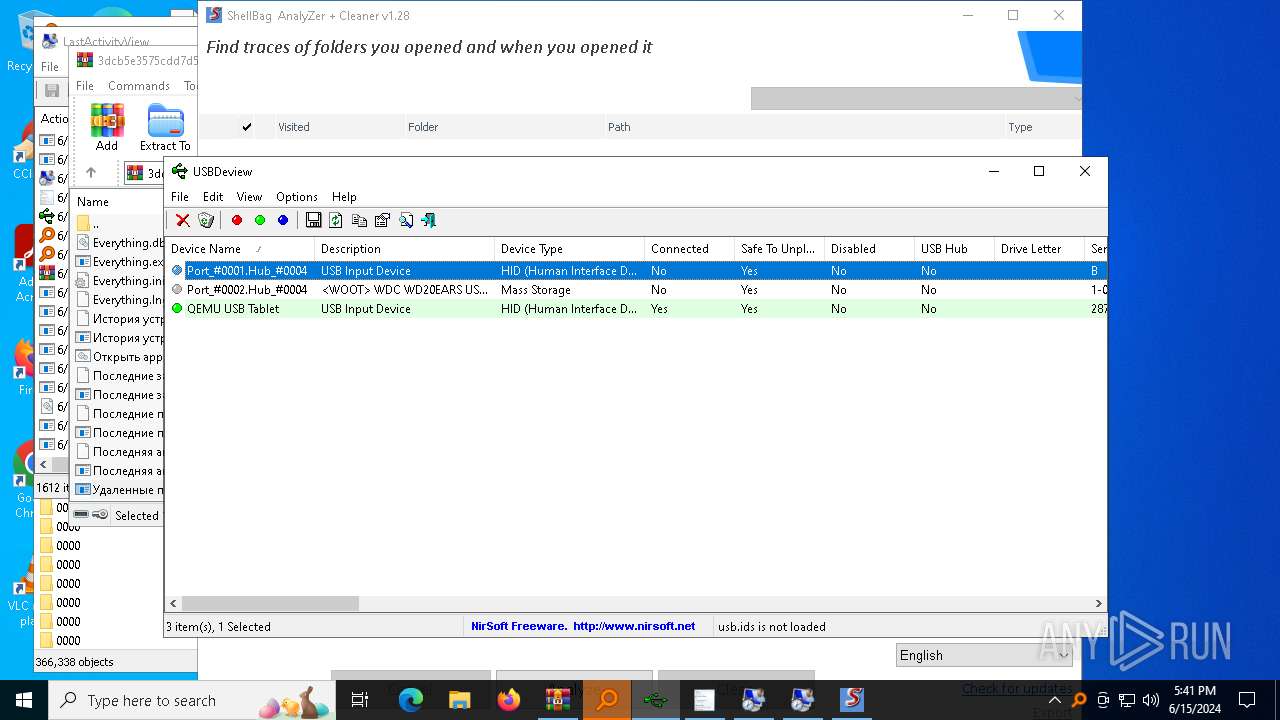
| 1120 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7539\Удаленные папки.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7539\Удаленные папки.exe | WinRAR.exe | ||||||||||||
User: admin Company: Goversoft LLC Integrity Level: HIGH Description: ShellBag AnalyZer & Cleaner Version: 1.28.0.0 Modules
| |||||||||||||||
| 1864 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2084 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.exe" -isrunas | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.exe | Everything.exe | ||||||||||||
User: admin Company: voidtools Integrity Level: HIGH Description: Everything Version: 1.4.1.1024 Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4939\Последняя активность .exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4939\Последняя активность .exe | WinRAR.exe | ||||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: LastActivityView Version: 1.32 Modules
| |||||||||||||||
| 3196 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7281\Последняя активность .exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7281\Последняя активность .exe | WinRAR.exe | ||||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: LastActivityView Version: 1.32 Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.exe | — | WinRAR.exe | |||||||||||
User: admin Company: voidtools Integrity Level: MEDIUM Description: Everything Version: 1.4.1.1024 Modules
| |||||||||||||||
| 4424 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7933\Everything.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.7933\Everything.exe | — | WinRAR.exe | |||||||||||
User: admin Company: voidtools Integrity Level: MEDIUM Description: Everything Exit code: 0 Version: 1.4.1.1024 Modules
| |||||||||||||||
Total events
25 308
Read events
25 275
Write events
33
Delete events
0
Modification events
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\3dcb5e3575cdd7d544e2e4b95f87ad11d30ac7df9e8322134ca3533d7a6b9acf.zip | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (5620) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
42
Suspicious files
14
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
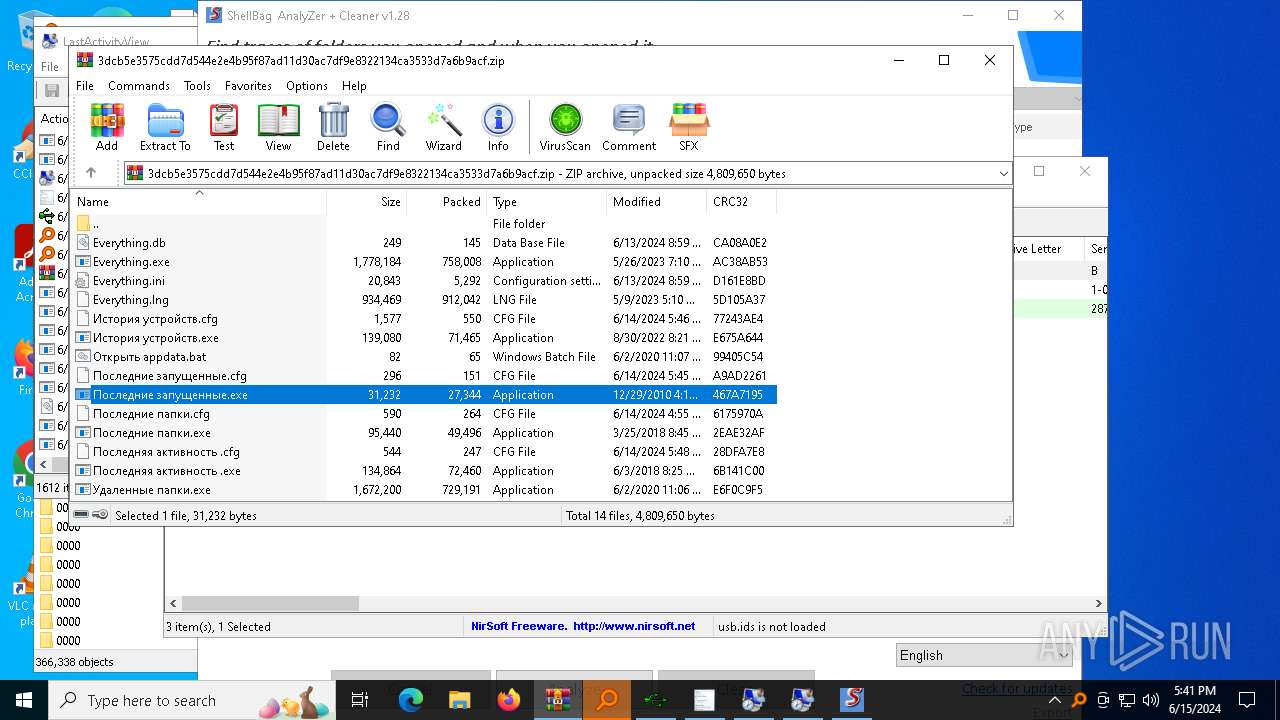
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Последние запущенные.exe | executable | |
MD5:F36530F46A34516BE38521EE9A134D28 | SHA256:BC11C4150BBC6F8B2CF7BC96BEDBB183C61D53AB8E4052B15D58BAD6B6D1BEFA | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.db | binary | |
MD5:BBF1481A2ED8C3962AC70078528E5B3B | SHA256:990586DE8EA7CF0571F6BBB0590C9D2AA831950D217760BB100345BCADF57F32 | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Удаленные папки.exe | executable | |
MD5:FAAFF4148DB8CDA4068234F5D5110C60 | SHA256:58304B1ED9A66D44938F1E04767D1219194693BC918750388F259B1D0D251DC1 | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.exe | executable | |
MD5:A7067594451CAB167A4F463BE9D0209C | SHA256:D3A6ED07BD3B52C62411132D060560F9C0C88CE183851F16B632A99B4D4E7581 | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4255\История устройств.exe | executable | |
MD5:D0D19F2CCCACF70BC84846076ACC11C8 | SHA256:63012EA9CE8ED335DB7BDD33FA7BB449AA1BA31755C6845C1E79C11CB60DC908 | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Последние папки.exe | executable | |
MD5:1A7524A3F7443C3E041774D5F372142C | SHA256:E000C782AF989E016EFCEF1664B9D652B0FEE59B011E28154072F7B6001B124D | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Последние запущенные.cfg | text | |
MD5:1E9E77443C463D23A8BCB4CEF89EF955 | SHA256:F7A266A952AE664AFEBAABDFFAA4F89B4A5FF2682BF17D882FBB33AB52062298 | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Последние папки.cfg | text | |
MD5:840E1058B02140D7AA7571F2E04CCB79 | SHA256:4285482D34EFA6D063B1D68169F47068D80B42C449303940F16DCABA477276F8 | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4155\Everything.ini | text | |
MD5:CF7245F338A37A9B847FBA3538AF838C | SHA256:AB87022901C654B5D38D05F105E16DEB7DFFE894E06892B41CF20DD63F372D2B | |||
| 5620 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5620.4255\Открыть appdata.bat | text | |
MD5:200AADBF80CEABC021F7AE98213CF3DE | SHA256:04FAC8CB5297EEA5CB8FB5F645D53682F429D5E4D86DB62D9FF4106E88AAEEE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5960 | RUXIMICS.exe | GET | 200 | 23.200.213.221:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5380 | svchost.exe | GET | 200 | 92.123.236.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 23.200.213.221:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5380 | svchost.exe | GET | 200 | 23.200.213.221:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5960 | RUXIMICS.exe | GET | 200 | 92.123.236.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | POST | — | 20.42.65.84:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5380 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5960 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5140 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5960 | RUXIMICS.exe | 92.123.236.192:80 | crl.microsoft.com | Akamai International B.V. | FR | unknown |
5380 | svchost.exe | 92.123.236.192:80 | crl.microsoft.com | Akamai International B.V. | FR | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
5380 | svchost.exe | 23.200.213.221:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
5960 | RUXIMICS.exe | 23.200.213.221:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
5140 | MoUsoCoreWorker.exe | 23.200.213.221:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |