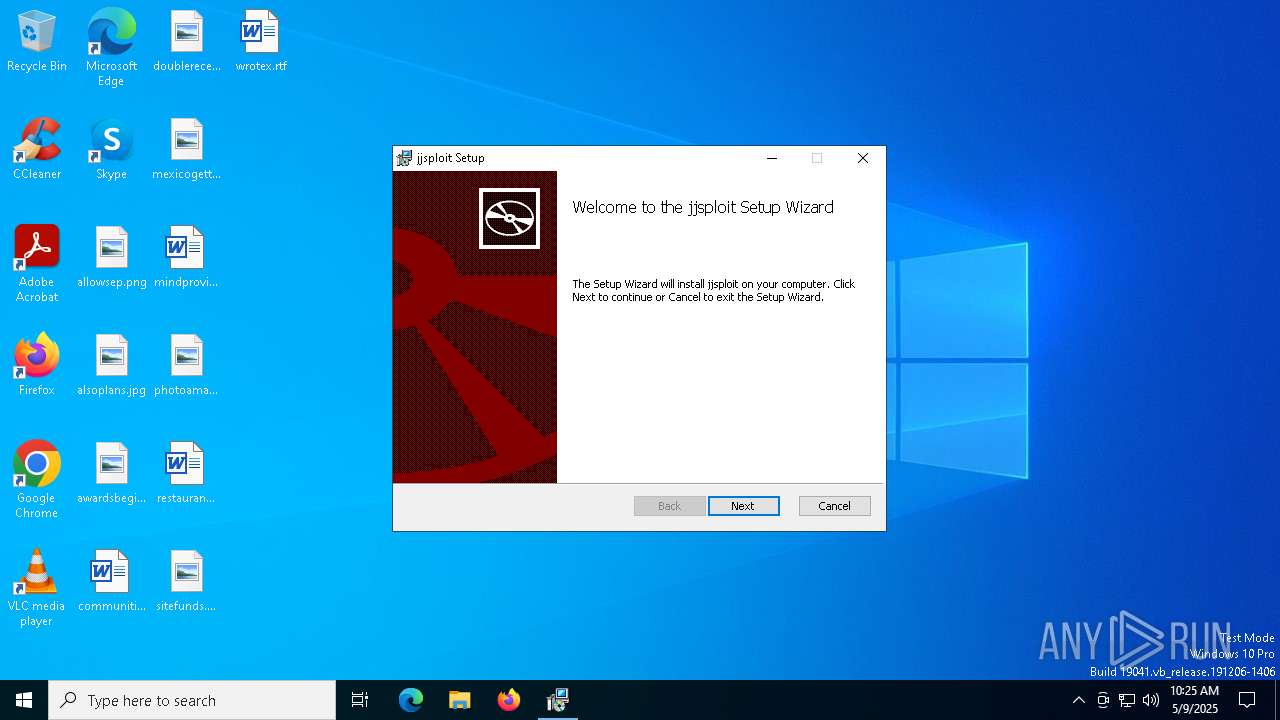
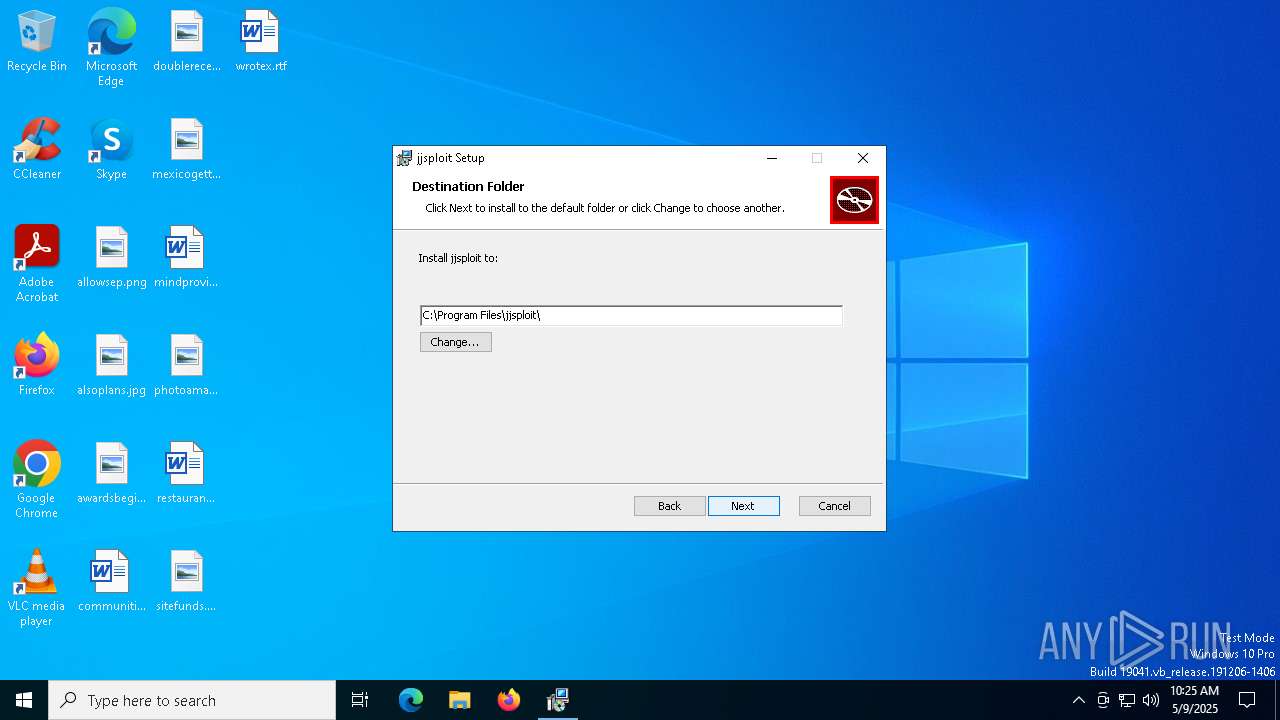
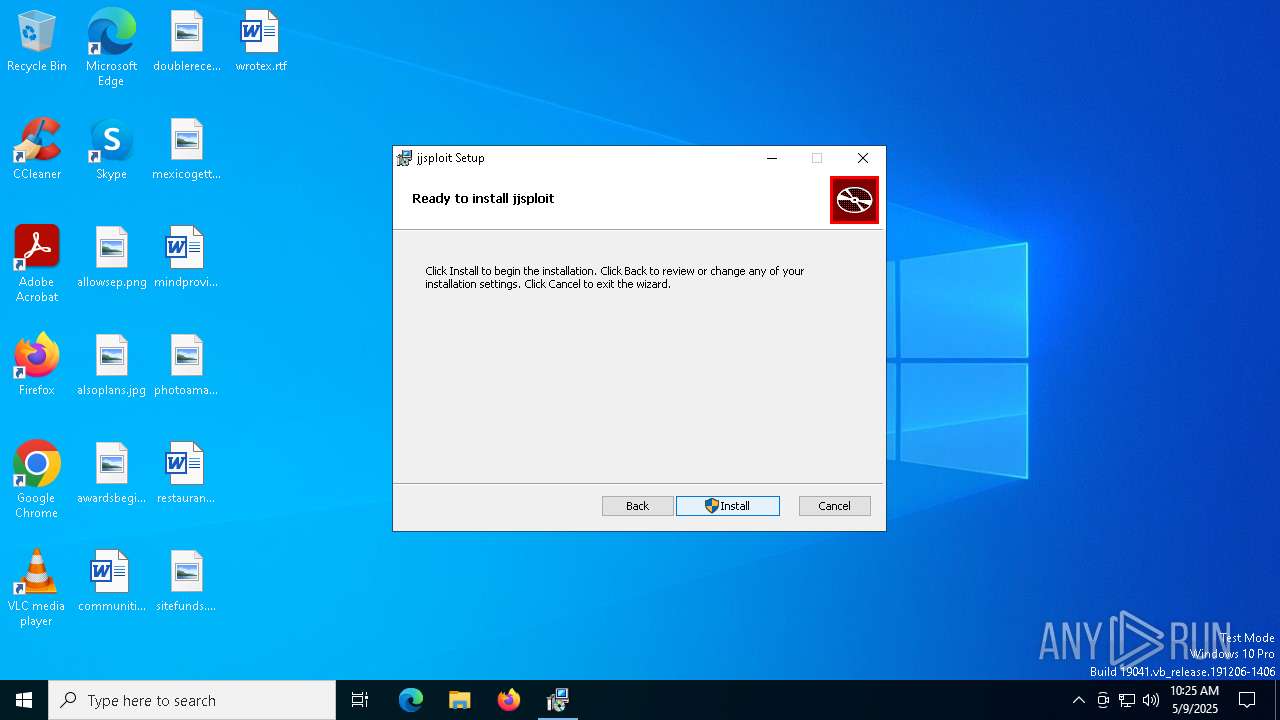
| File name: | jjsploit_8.14.2_x64_en-US.msi |
| Full analysis: | https://app.any.run/tasks/68c3c5bb-b63a-46bd-b943-27582d394214 |
| Verdict: | Malicious activity |
| Analysis date: | May 09, 2025, 10:25:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Code page: 1252, Title: Installation Database, Subject: jjsploit, Author: wearedevs, Keywords: Installer, Comments: This installer database contains the logic and data required to install jjsploit., Template: x64;0, Revision Number: {3B8D9B77-8221-4055-90CE-EB65FF216C95}, Create Time/Date: Mon May 5 10:59:52 2025, Last Saved Time/Date: Mon May 5 10:59:52 2025, Number of Pages: 450, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.14.1.8722), Security: 2 |
| MD5: | 8001072DDACC259CC365A68D2F6EF4D4 |
| SHA1: | 5E4FAE602B978AC963406E870201E287104A9008 |
| SHA256: | 3DC41A510C75CE7CFAFC58870BA766430B04A3A2C0E4EA4ABBFD998635ACDEC6 |
| SSDEEP: | 98304:e08tTHSF4YTcUrouly+4hIeN5N7/3eyt6Bf9YkMUNSfvXxs6dKnzrho/4PCXP8NA:wPfGzBQf+e6xU |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 1676)
SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 4896)
Downloads file from URI via Powershell
- powershell.exe (PID: 1676)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 7000)
Manipulates environment variables
- powershell.exe (PID: 1676)
Starts process via Powershell
- powershell.exe (PID: 1676)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 7000)
Executable content was dropped or overwritten
- powershell.exe (PID: 1676)
- MicrosoftEdgeWebview2Setup.exe (PID: 1328)
- MicrosoftEdgeUpdate.exe (PID: 6800)
Process drops legitimate windows executable
- powershell.exe (PID: 1676)
- MicrosoftEdgeWebview2Setup.exe (PID: 1328)
- MicrosoftEdgeUpdate.exe (PID: 6800)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 1328)
- MicrosoftEdgeUpdate.exe (PID: 6800)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 6800)
INFO
An automatically generated document
- msiexec.exe (PID: 2136)
Checks supported languages
- msiexec.exe (PID: 6476)
- msiexec.exe (PID: 7000)
Reads the computer name
- msiexec.exe (PID: 7000)
- msiexec.exe (PID: 6476)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2136)
- msiexec.exe (PID: 7000)
Manages system restore points
- SrTasks.exe (PID: 6876)
The executable file from the user directory is run by the Powershell process
- MicrosoftEdgeWebview2Setup.exe (PID: 1328)
The sample compiled with english language support
- powershell.exe (PID: 1676)
- MicrosoftEdgeWebview2Setup.exe (PID: 1328)
- MicrosoftEdgeUpdate.exe (PID: 6800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | jjsploit |
| Author: | wearedevs |
| Keywords: | Installer |
| Comments: | This installer database contains the logic and data required to install jjsploit. |
| Template: | x64;0 |
| RevisionNumber: | {3B8D9B77-8221-4055-90CE-EB65FF216C95} |
| CreateDate: | 2025:05:05 10:59:52 |
| ModifyDate: | 2025:05:05 10:59:52 |
| Pages: | 450 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.14.1.8722) |
| Security: | Read-only recommended |
Total processes
154
Monitored processes
19
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1328 | "C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe" /silent /install | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Setup Version: 1.3.195.57 Modules
| |||||||||||||||
| 1676 | powershell.exe -NoProfile -windowstyle hidden try { [Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12 } catch {}; Invoke-WebRequest -Uri "https://go.microsoft.com/fwlink/p/?LinkId=2124703" -OutFile "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" ; Start-Process -FilePath "$env:TEMP\MicrosoftEdgeWebview2Setup.exe" -ArgumentList ('/silent', '/install') -Wait | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /handoff "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=false" /installsource otherinstallcmd /sessionid "{1A9DF4E1-22F4-4353-91FB-63E1883DF89C}" /silent | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.57 Modules
| |||||||||||||||
| 2136 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\jjsploit_8.14.2_x64_en-US.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3024 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" -Embedding | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.57 Modules
| |||||||||||||||
| 4172 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuNTciIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuNTciIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7MUE5REY0RTEtMjJGNC00MzUzLTkxRkItNjNFMTg4M0RGODlDfSIgdXNlcmlkPSJ7Q0E4NjU5QkUtNUE1RS00RjJDLUFFM0MtOUUwMDNBRENDQzIxfSIgaW5zdGFsbHNvdXJjZT0ib3RoZXJpbnN0YWxsY21kIiByZXF1ZXN0aWQ9InszRDVBREE2RC0wQjczLTQ5OEQtQjkyQy1EMUU5NzBGOTE3NDF9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IGxvZ2ljYWxfY3B1cz0iNCIgcGh5c21lbW9yeT0iNCIgZGlza190eXBlPSIyIiBzc2U9IjEiIHNzZTI9IjEiIHNzZTM9IjEiIHNzc2UzPSIxIiBzc2U0MT0iMSIgc3NlNDI9IjEiIGF2eD0iMSIvPjxvcyBwbGF0Zm9ybT0id2luIiB2ZXJzaW9uPSIxMC4wLjE5MDQ1LjQwNDYiIHNwPSIiIGFyY2g9Ing2NCIgcHJvZHVjdF90eXBlPSI0OCIgaXNfd2lwPSIwIiBpc19pbl9sb2NrZG93bl9tb2RlPSIwIi8-PG9lbSBwcm9kdWN0X21hbnVmYWN0dXJlcj0iREVMTCIgcHJvZHVjdF9uYW1lPSJERUxMIi8-PGV4cCBldGFnPSIiLz48YXBwIGFwcGlkPSJ7RjNDNEZFMDAtRUZENS00MDNCLTk1NjktMzk4QTIwRjFCQTRBfSIgdmVyc2lvbj0iIiBuZXh0dmVyc2lvbj0iMS4zLjE5NS41NyIgbGFuZz0iIiBicmFuZD0iIiBjbGllbnQ9IiI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgc3lzdGVtX3VwdGltZV90aWNrcz0iMTAwNTQ4OTg5MjkiIGluc3RhbGxfdGltZV9tcz0iNzc3Ii8-PC9hcHA-PC9yZXF1ZXN0Pg | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.57 Modules
| |||||||||||||||
| 4220 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.57\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.57\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.57 Modules
| |||||||||||||||
| 4244 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.57\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.57\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.57 Modules
| |||||||||||||||
| 4408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 687
Read events
10 722
Write events
922
Delete events
43
Modification events
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000F81069C2CCC0DB01581B000088060000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000F81069C2CCC0DB01581B000088060000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000023ED59C3CCC0DB01581B000088060000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000344F5CC3CCC0DB01581B000088060000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000CAB45EC3CCC0DB01581B000088060000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000766E63C3CCC0DB01581B000088060000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000F7EC45C4CCC0DB01581B000088060000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7000) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000FE5048C4CCC0DB01581B000090130000E80300000100000000000000000000009A3C97A92AB2E34C9FC4C50C274D8FC100000000000000000000000000000000 | |||
| (PID) Process: | (4896) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000289856C4CCC0DB012013000018020000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
204
Suspicious files
20
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7000 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7000 | msiexec.exe | C:\Windows\Installer\1127f7.msi | — | |
MD5:— | SHA256:— | |||
| 7000 | msiexec.exe | C:\Program Files\jjsploit\jjsploit.exe | executable | |
MD5:2CD9D9D57D80308A0CE9A5D64DD5ABC9 | SHA256:5672C78E5B61456936D266820769C53BEEFA33851AE569288C12DA318DA744A1 | |||
| 7000 | msiexec.exe | C:\Windows\Temp\~DF7F5E70E0E150771A.TMP | binary | |
MD5:D56A4666C21975AD59EAB2851E8CE5F7 | SHA256:82AB9BE0988B4679E1680F3D438F1CB06C9DA00FA47CAC3F62AB07B4AE6EFF60 | |||
| 7000 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{a9973c9a-b22a-4ce3-9fc4-c50c274d8fc1}_OnDiskSnapshotProp | binary | |
MD5:F56E9149853C4C7006D1AE56F8D0E044 | SHA256:C65457210A09DAF33D79947C2DBAD27B01A0603A4EBFF374BE412A088E1C4ABF | |||
| 7000 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:D56A4666C21975AD59EAB2851E8CE5F7 | SHA256:82AB9BE0988B4679E1680F3D438F1CB06C9DA00FA47CAC3F62AB07B4AE6EFF60 | |||
| 7000 | msiexec.exe | C:\Program Files\jjsploit\resources\luascripts\animations\dab.lua | text | |
MD5:EE91641376E1217DE57AD17EA74DA5CB | SHA256:EFD5E7407C3FC69338237D3C9686596F78BB5FE3181ED10640EFAD5839F6112A | |||
| 7000 | msiexec.exe | C:\Program Files\jjsploit\resources\luascripts\animations\jumpland.lua | text | |
MD5:2899EC217AEF73B127C9328785012EEF | SHA256:7D4CA7B02C90B0B21D64C2BAA6E5940DCCE895DB5BC125D0E993A5A883186721 | |||
| 7000 | msiexec.exe | C:\Program Files\jjsploit\resources\luascripts\animations\energizegui.lua | text | |
MD5:70B51C18FBF11B73271E552FBB224396 | SHA256:7E7579AC512265FC6508B7B4D025EE923BCA7F23937ED10F41BEFDC440C28761 | |||
| 2136 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC9BA.tmp | executable | |
MD5:CFBB8568BD3711A97E6124C56FCFA8D9 | SHA256:7F47D98AB25CFEA9B3A2E898C3376CC9BA1CD893B4948B0C27CAA530FD0E34CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5408 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5408 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7208 | svchost.exe | HEAD | 200 | 2.22.242.227:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d030d76f-35e6-4c51-9279-28644aa334bb?P1=1747391198&P2=404&P3=2&P4=T7wRfh1xTLqA786%2fp7fYbTSuR2MEw6cUpjSts1oLXw3qwXWT1nZetqey%2fDNqQKLNgvXvlQ%2fPLuwGA5a3nlJUZw%3d%3d | unknown | — | — | whitelisted |
7208 | svchost.exe | GET | — | 2.22.242.227:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d030d76f-35e6-4c51-9279-28644aa334bb?P1=1747391198&P2=404&P3=2&P4=T7wRfh1xTLqA786%2fp7fYbTSuR2MEw6cUpjSts1oLXw3qwXWT1nZetqey%2fDNqQKLNgvXvlQ%2fPLuwGA5a3nlJUZw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2564 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7208 | svchost.exe | Misc activity | ET INFO Packed Executable Download |