| File name: | 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware |
| Full analysis: | https://app.any.run/tasks/31bac9ee-1710-495b-8fe8-cfa1d4f1b14c |
| Verdict: | Malicious activity |
| Analysis date: | August 23, 2022, 22:39:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 56AC9E72644A8DAE8C1968D63A26E58A |
| SHA1: | D0349D04F33400541898426438D9E036D21DECC5 |
| SHA256: | 3DB0E385EB53A32D61A5A35908A99317868B571E4CF7079DB67FD68604DA662C |
| SSDEEP: | 24576:mq5TfcdHj4fmbi2q+0MmV0VMXeyrtoT1GokHTQoCwsC+Y:mUTsamOx9RoBVoCwT |
MALICIOUS
Drops executable file immediately after starts
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
Application was dropped or rewritten from another process
- dmr_72.exe (PID: 2352)
SUSPICIOUS
Checks Windows language
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
Reads mouse settings
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
Checks supported languages
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
- dmr_72.exe (PID: 2352)
Executable content was dropped or overwritten
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
Reads the computer name
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
- dmr_72.exe (PID: 2352)
Drops a file with a compile date too recent
- 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe (PID: 2132)
Reads Environment values
- dmr_72.exe (PID: 2352)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (30.7) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (30.1) |
| .exe | | | Win32 EXE Yoda's Crypter (29.5) |
| .exe | | | Win32 Executable (generic) (5) |
| .exe | | | Generic Win/DOS Executable (2.2) |
Total processes
41
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2132 | "C:\Users\admin\AppData\Local\Temp\3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe" | C:\Users\admin\AppData\Local\Temp\3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: CHIP Secured Installer Exit code: 0 Version: 1.0.7.4 Modules
| |||||||||||||||
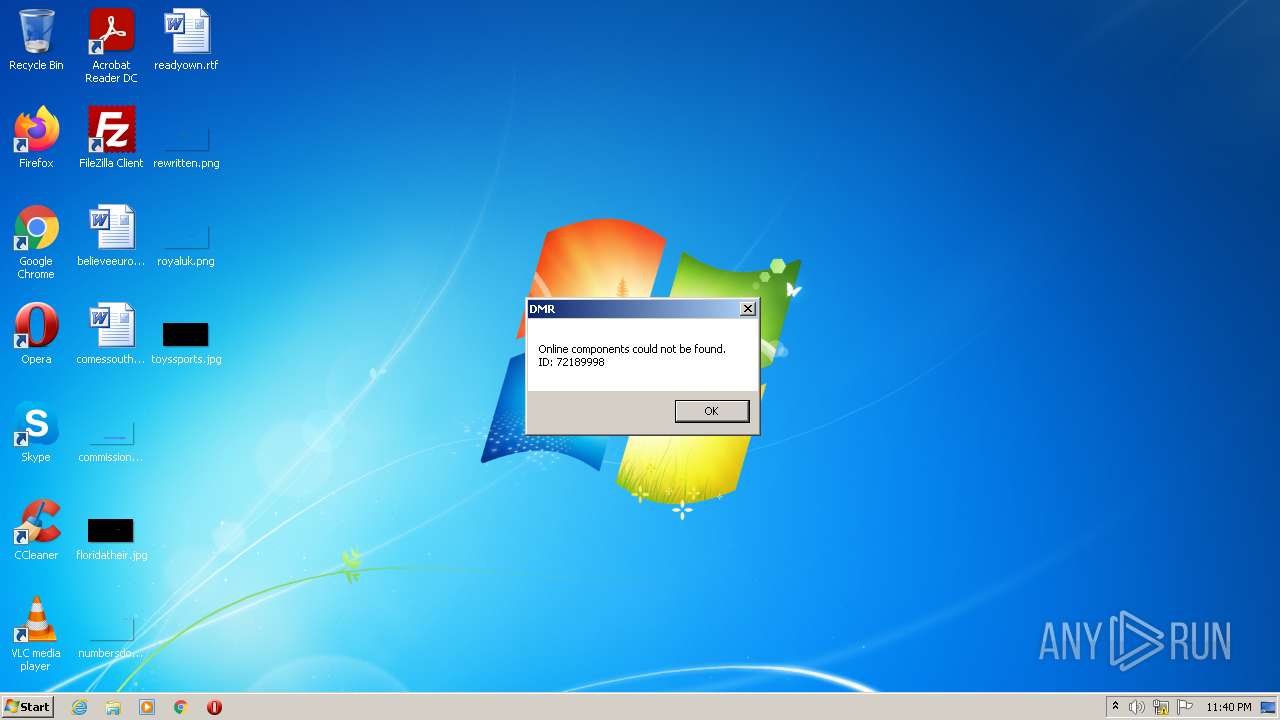
| 2352 | "C:\Users\admin\AppData\Local\Temp\DMR\dmr_72.exe" -install -72189998 -chipde -e37278fe332e42d1af33e4480ad52248 - -BLUB2 -ebqpumucuifmqiyr -2132 | C:\Users\admin\AppData\Local\Temp\DMR\dmr_72.exe | 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | ||||||||||||
User: admin Company: Chip Digital GmbH Integrity Level: HIGH Description: DMR Exit code: 0 Version: 1.0.7.4 Modules
| |||||||||||||||
| 3380 | "C:\Users\admin\AppData\Local\Temp\3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe" | C:\Users\admin\AppData\Local\Temp\3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: CHIP Secured Installer Exit code: 3221226540 Version: 1.0.7.4 Modules
| |||||||||||||||
Total events
1 290
Read events
1 267
Write events
23
Delete events
0
Modification events
| (PID) Process: | (2132) 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2132) 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2132) 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2132) 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2352) dmr_72.exe | Key: | HKEY_CURRENT_USER\Software\OCS |
| Operation: | write | Name: | CID |
Value: bbc70a90-0e6f-46fa-8783-d3f96aaefa83 | |||
| (PID) Process: | (2352) dmr_72.exe | Key: | HKEY_CURRENT_USER\Software\OCS |
| Operation: | write | Name: | PID |
Value: chipde | |||
| (PID) Process: | (2352) dmr_72.exe | Key: | HKEY_CURRENT_USER\Software\OCS |
| Operation: | write | Name: | lastPID |
Value: chipde | |||
| (PID) Process: | (2352) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2352) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2352) dmr_72.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dmr_72_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
Executable files
1
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | C:\Users\admin\AppData\Local\Temp\DMR\ebqpumucuifmqiyr.dat | text | |
MD5:8C934B48A05955C6CC934925F4C01E7D | SHA256:51BE55DD44A7D2C782EF432971878A64040AEC99C5EC0B53AC92D72BB2645992 | |||
| 2132 | 3db0e385eb53a32d61a5a35908a99317868b571e4cf7079db67fd68604da662cmalware.exe | C:\Users\admin\AppData\Local\Temp\DMR\dmr_72.exe | executable | |
MD5:1B81FA48134378F2B8D54A41FCFCF0CA | SHA256:5E2931D27098E63B67126EC2E036D8E2F4E46814D8C777C0307E3EEC3B947707 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2352 | dmr_72.exe | GET | 200 | 116.203.169.158:80 | http://api.chip-secured-download.de/geoip/geoip.php?ip=322e3234342e3130302e323535 | IN | text | 2 b | unknown |
2352 | dmr_72.exe | GET | 200 | 116.203.169.158:80 | http://api.chip-secured-download.de/dotnet/com | IN | text | 22 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2352 | dmr_72.exe | 116.203.169.158:80 | api.chip-secured-download.de | 334,Udyog Vihar | IN | unknown |
2352 | dmr_72.exe | 116.203.169.153:80 | ocs2.chdi-server.de | 334,Udyog Vihar | IN | unknown |
— | — | 192.168.100.2:53 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
api.chip-secured-download.de |
| unknown |
ocs2.chdi-server.de |
| unknown |