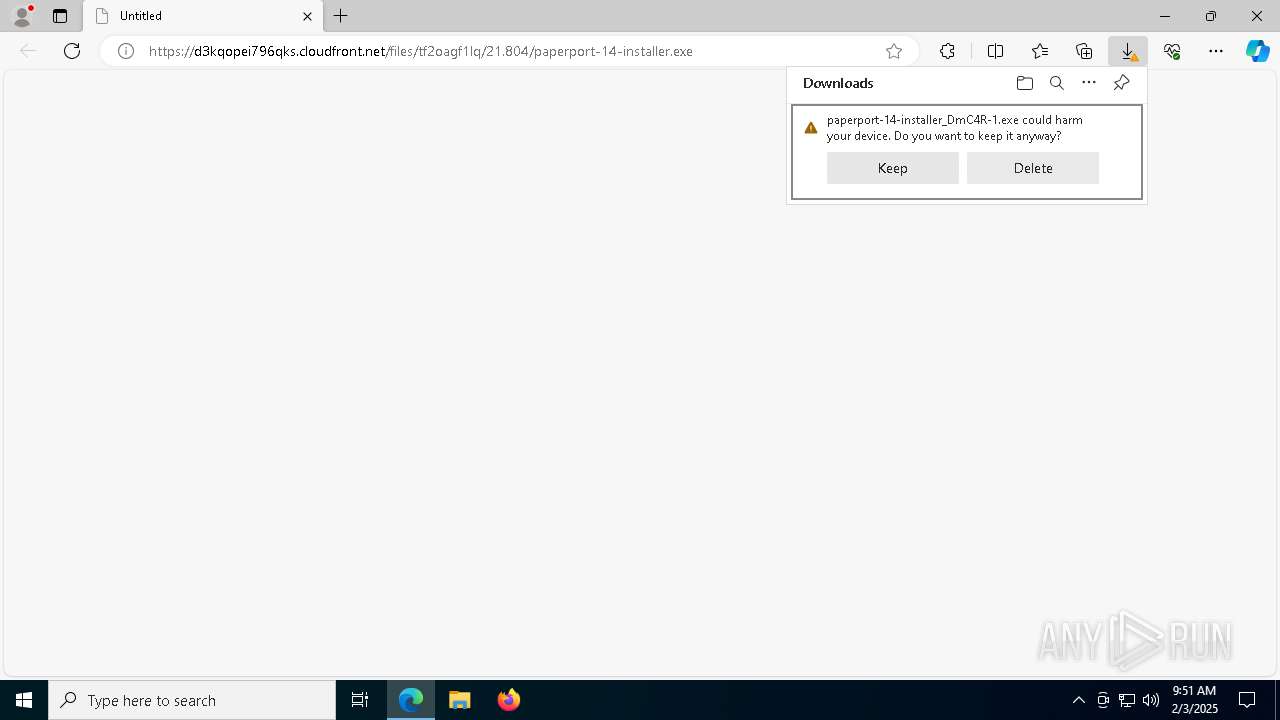
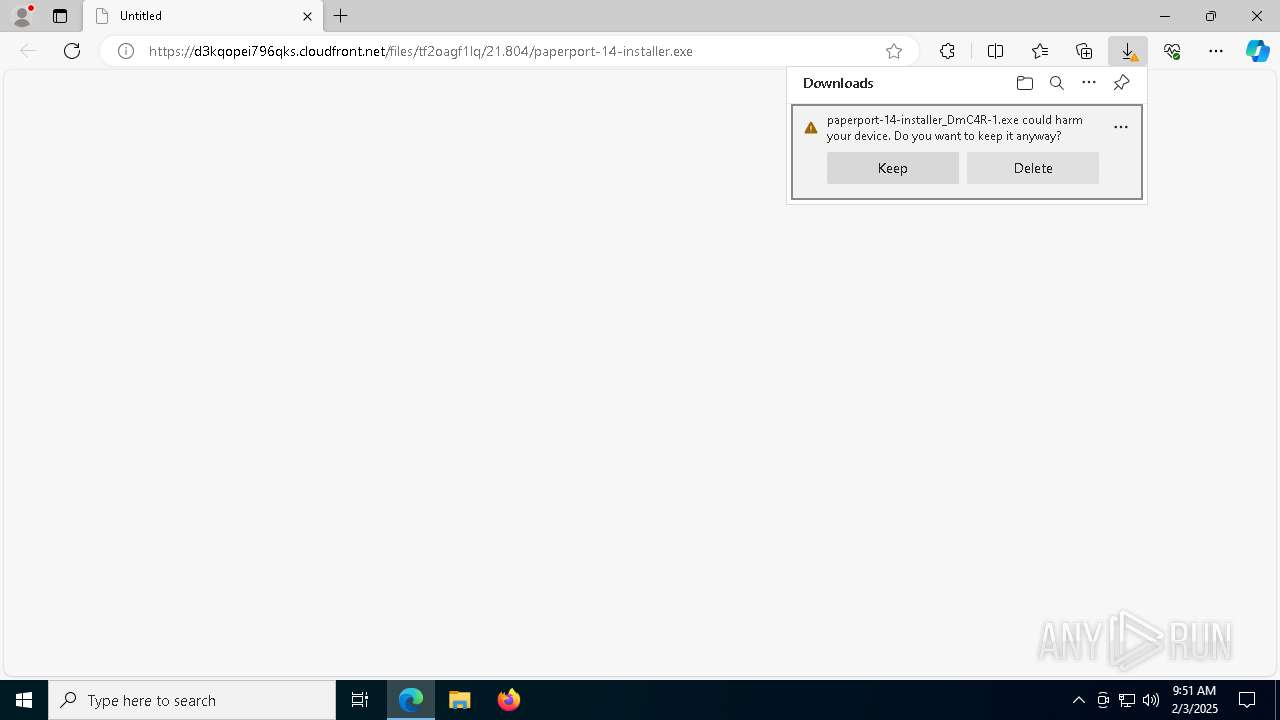
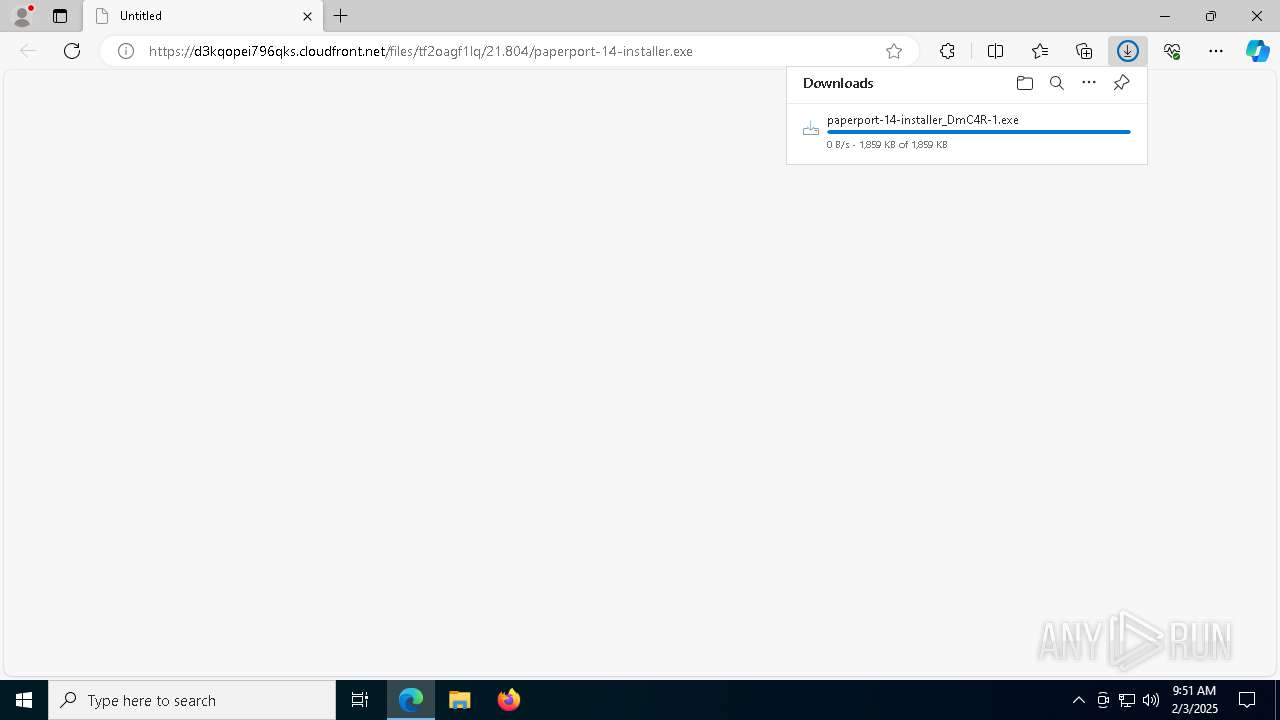
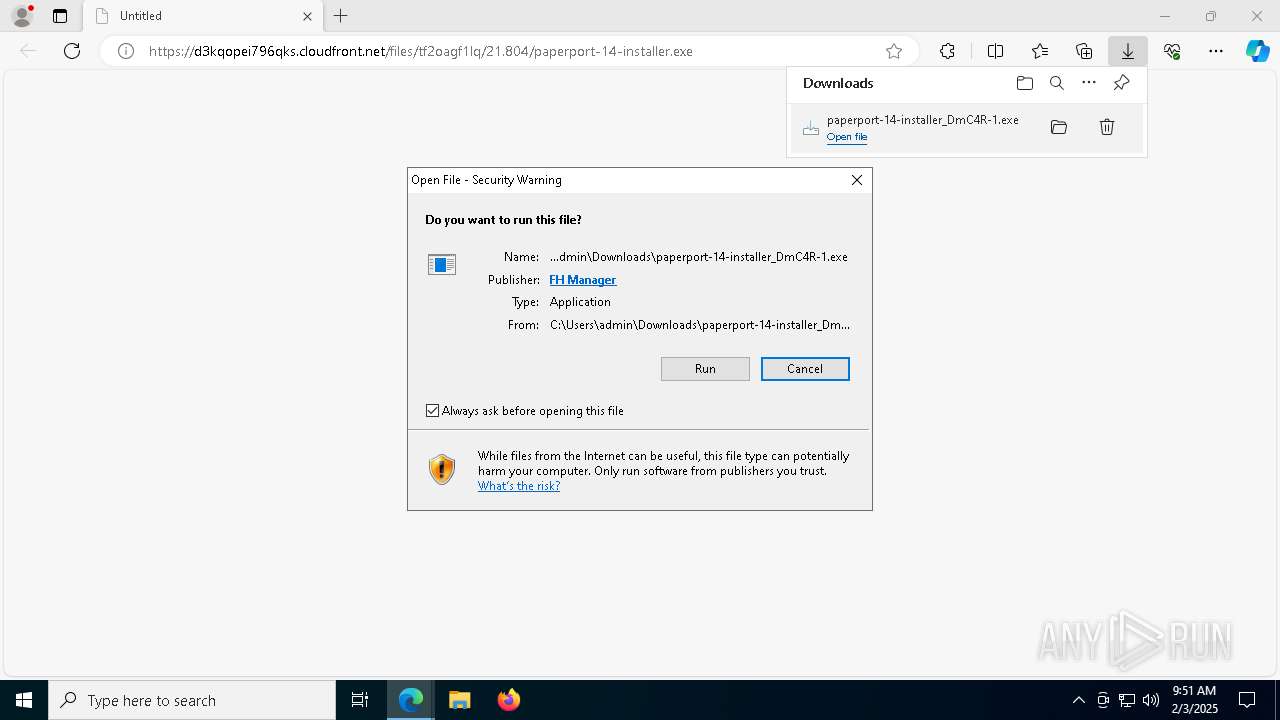
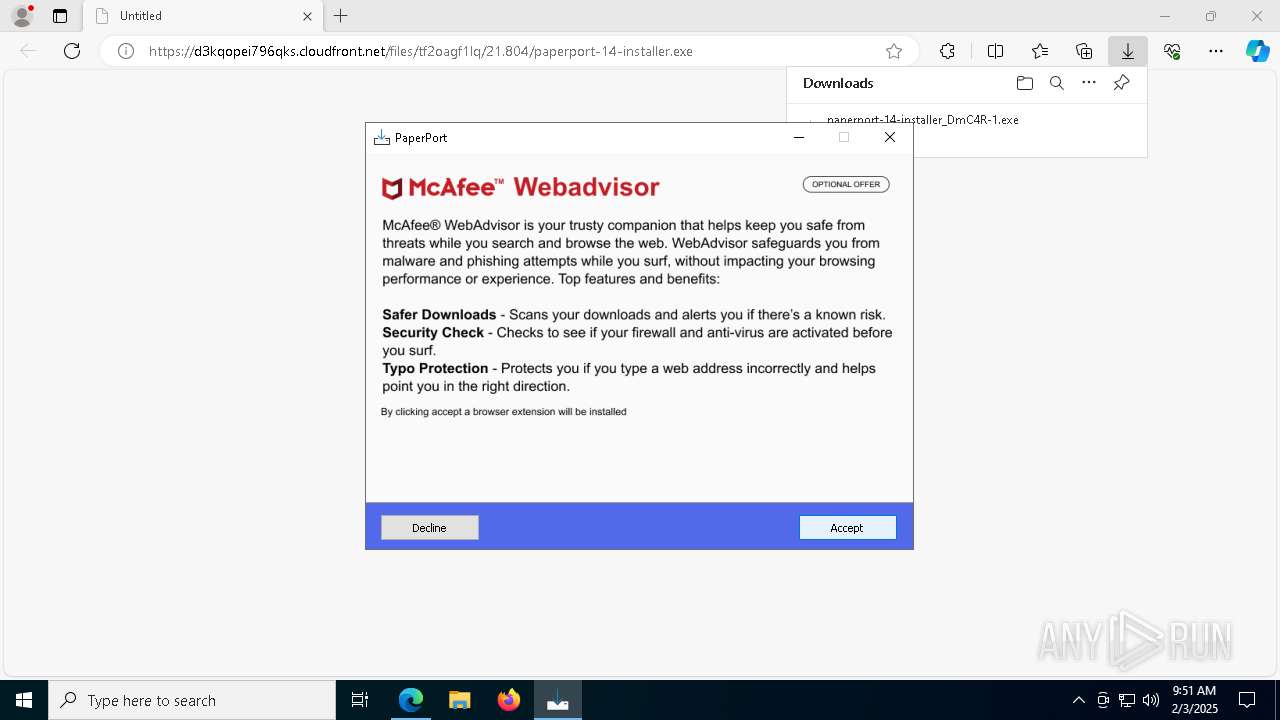
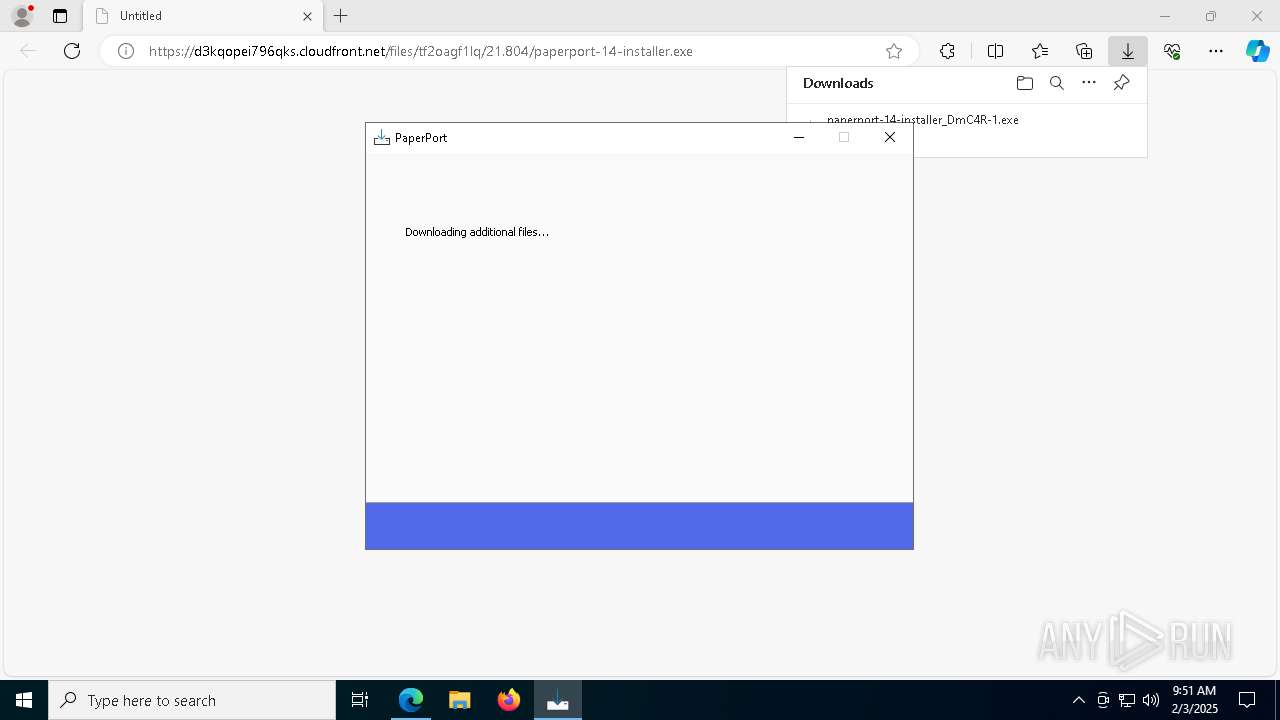
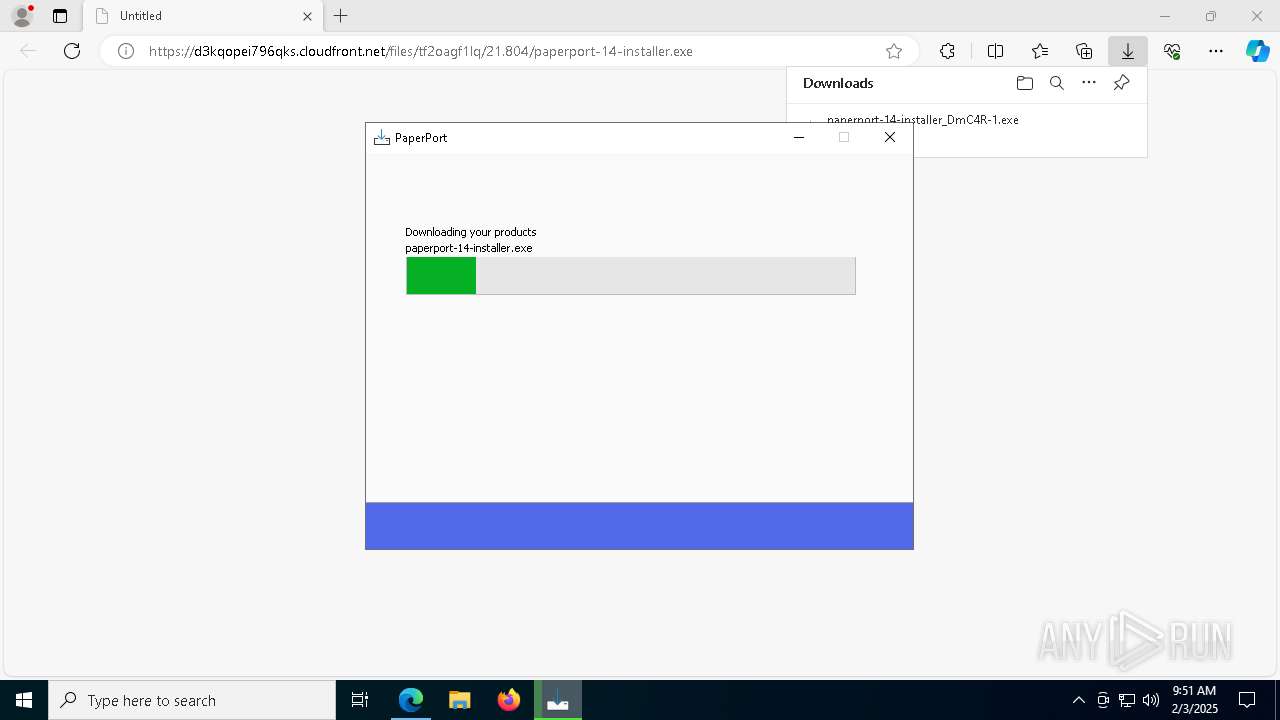
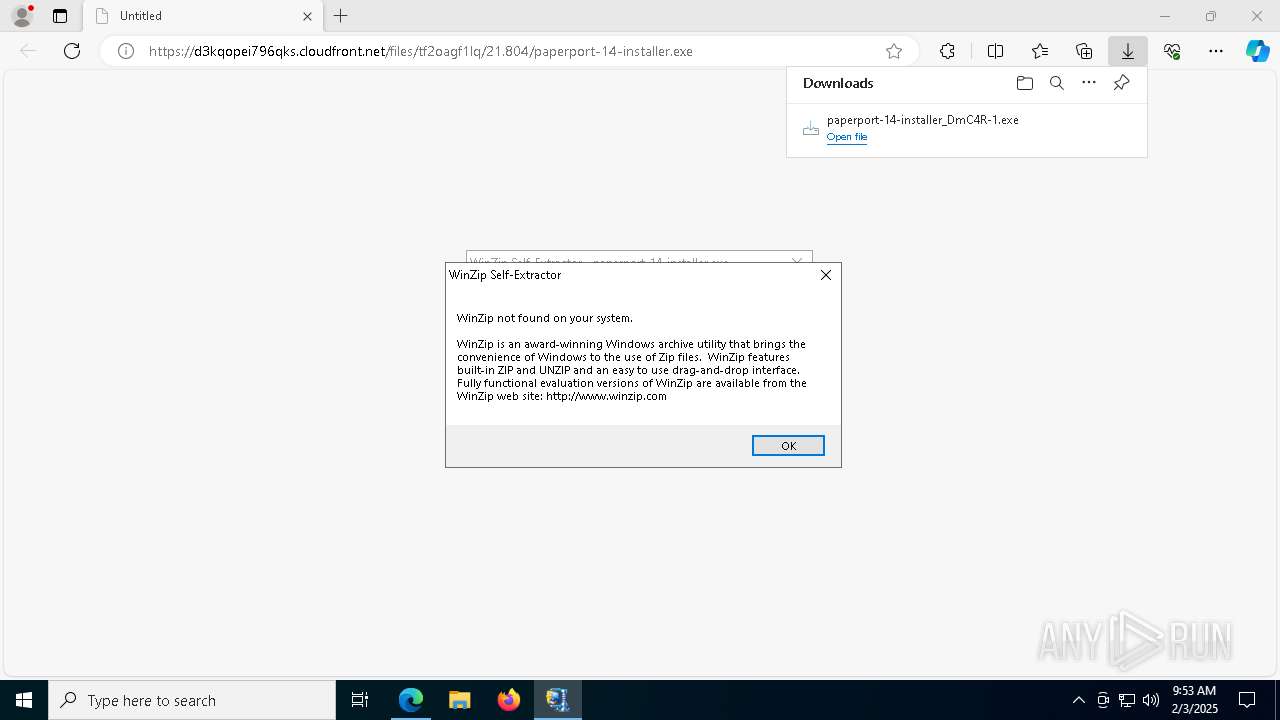
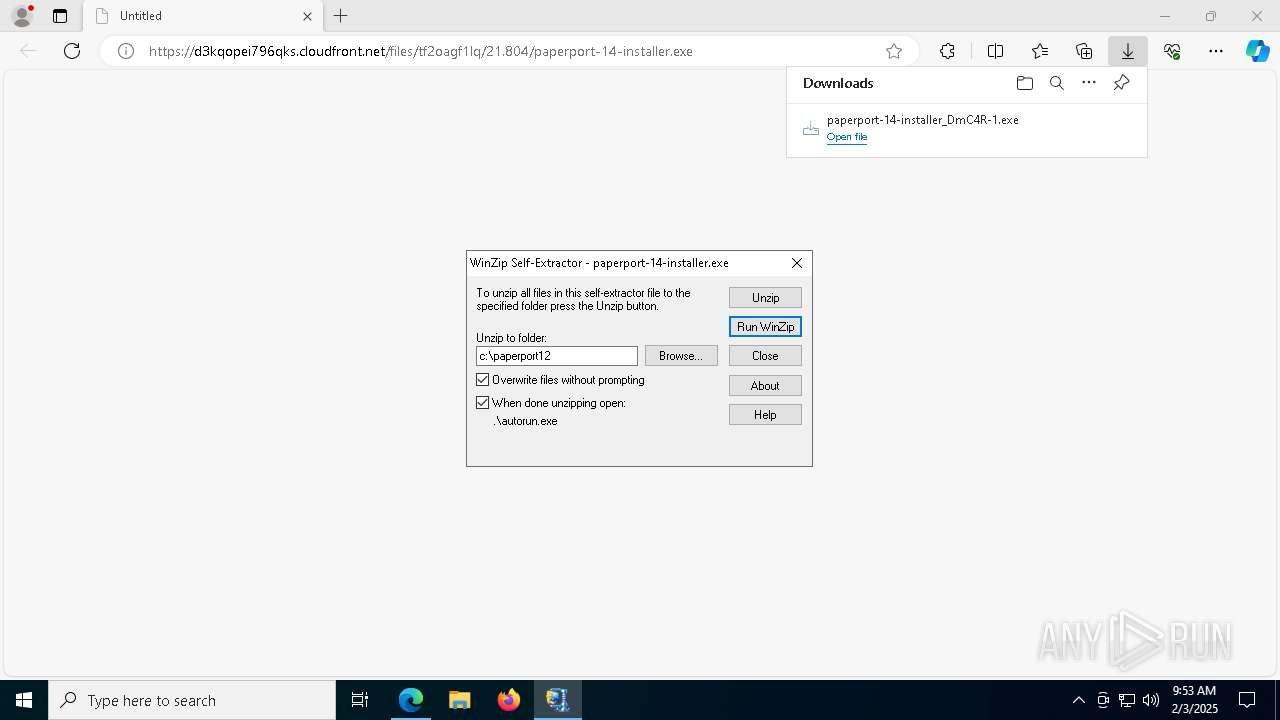
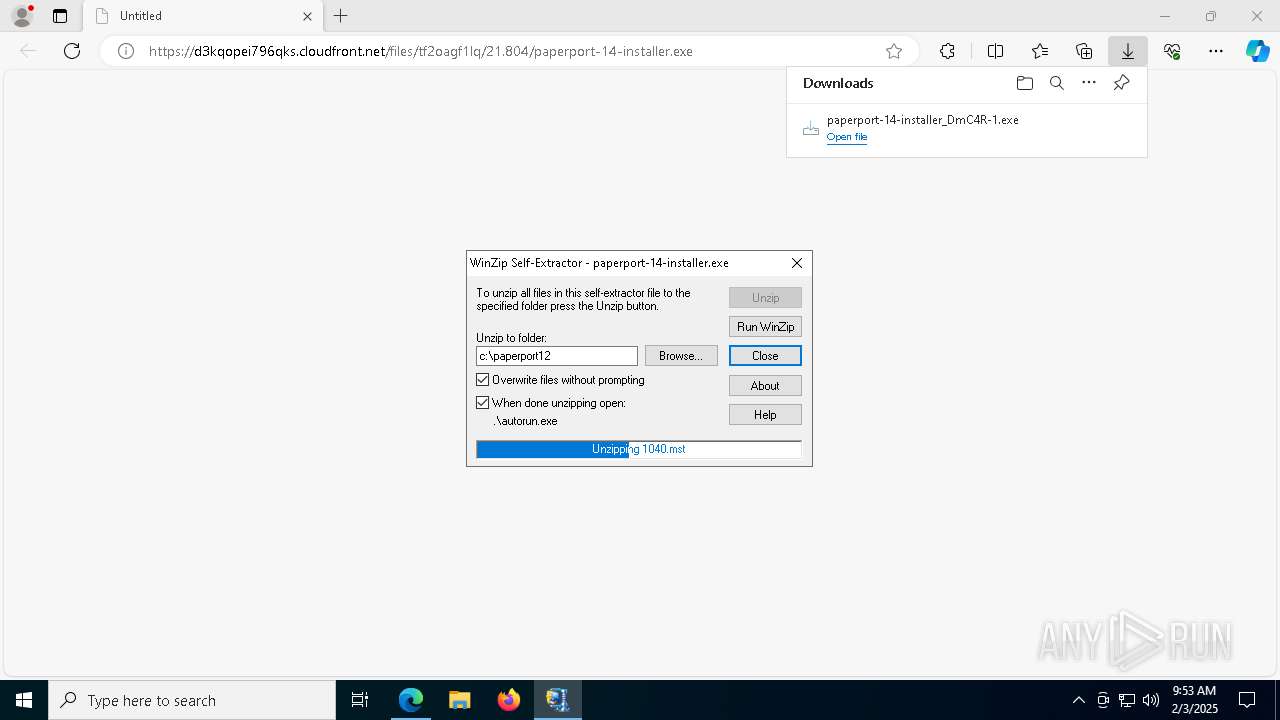
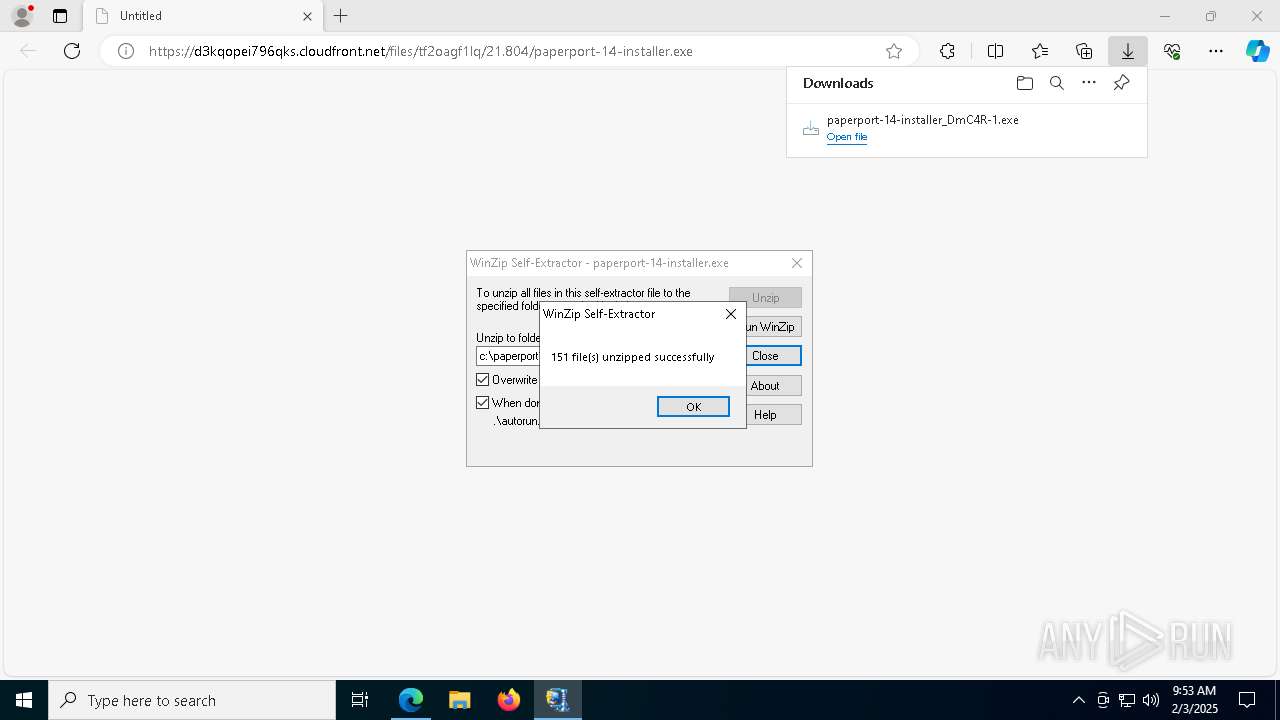
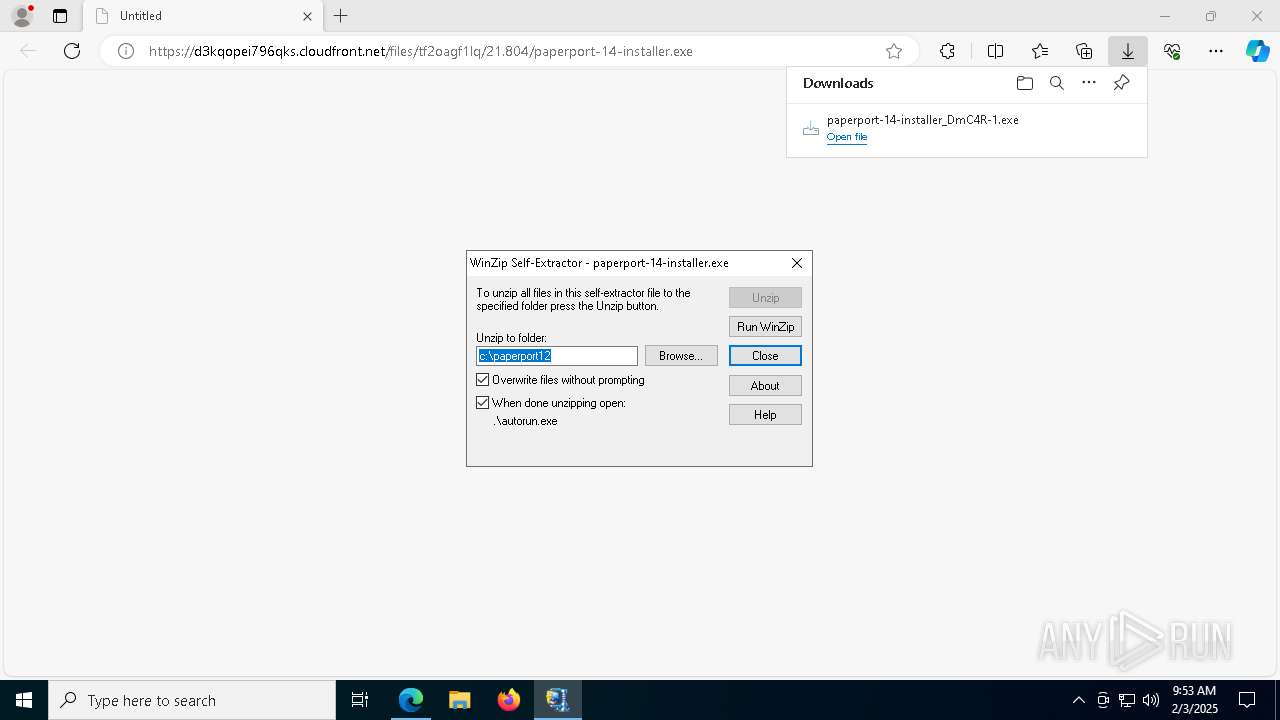
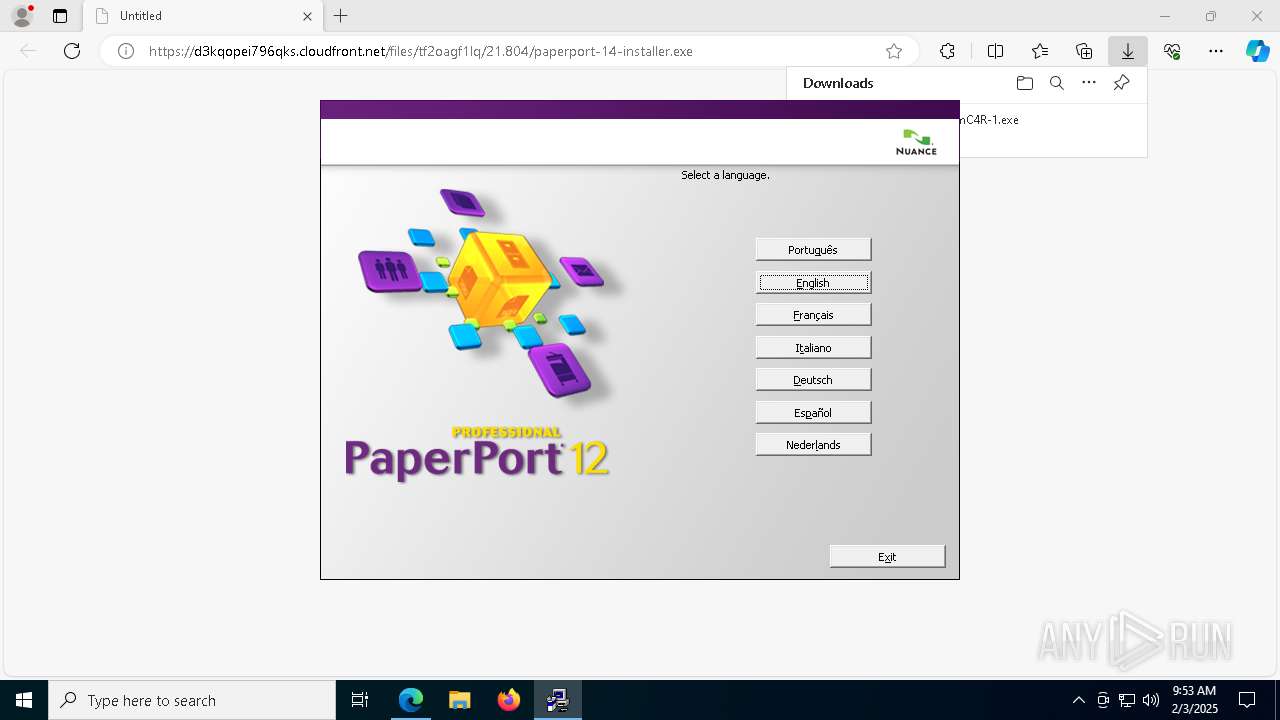
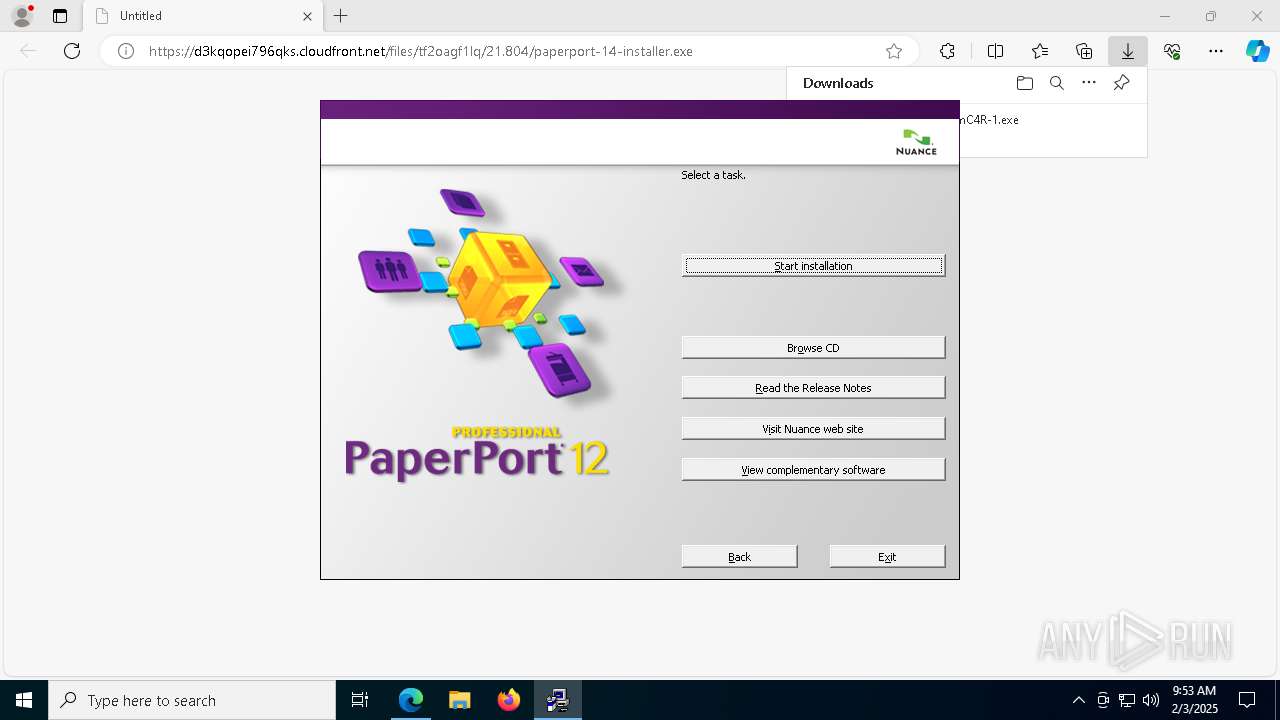
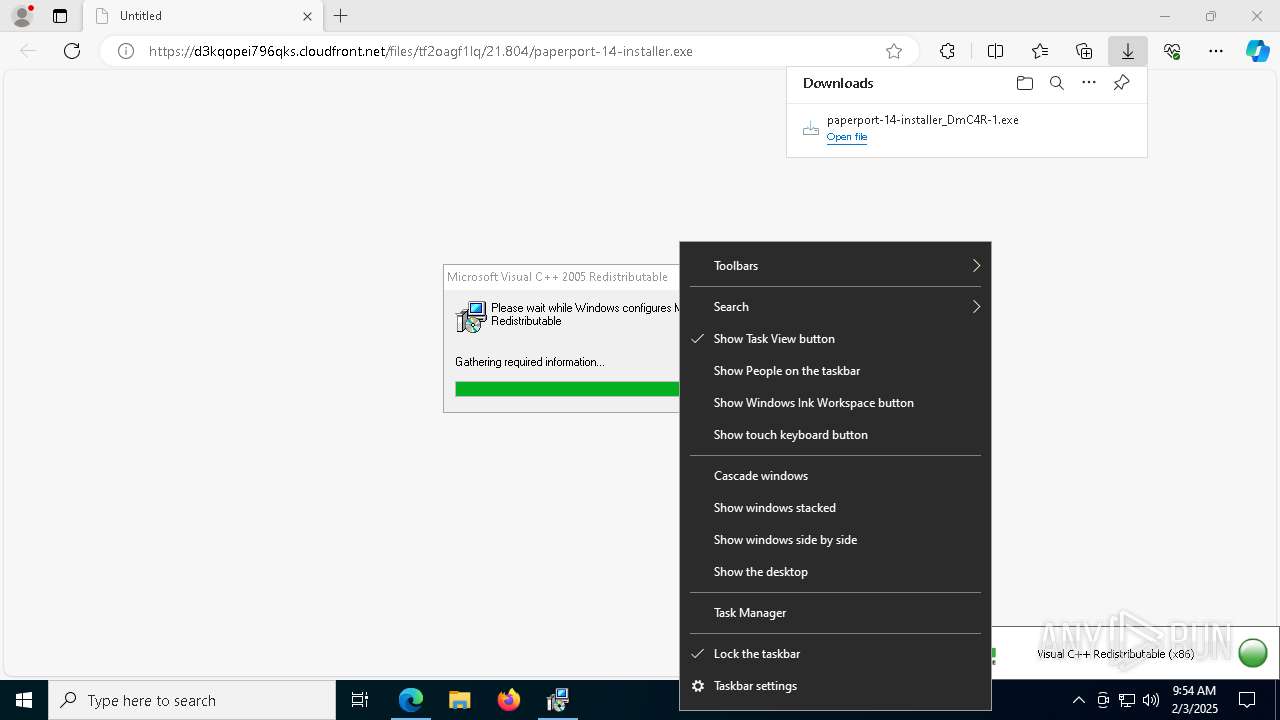
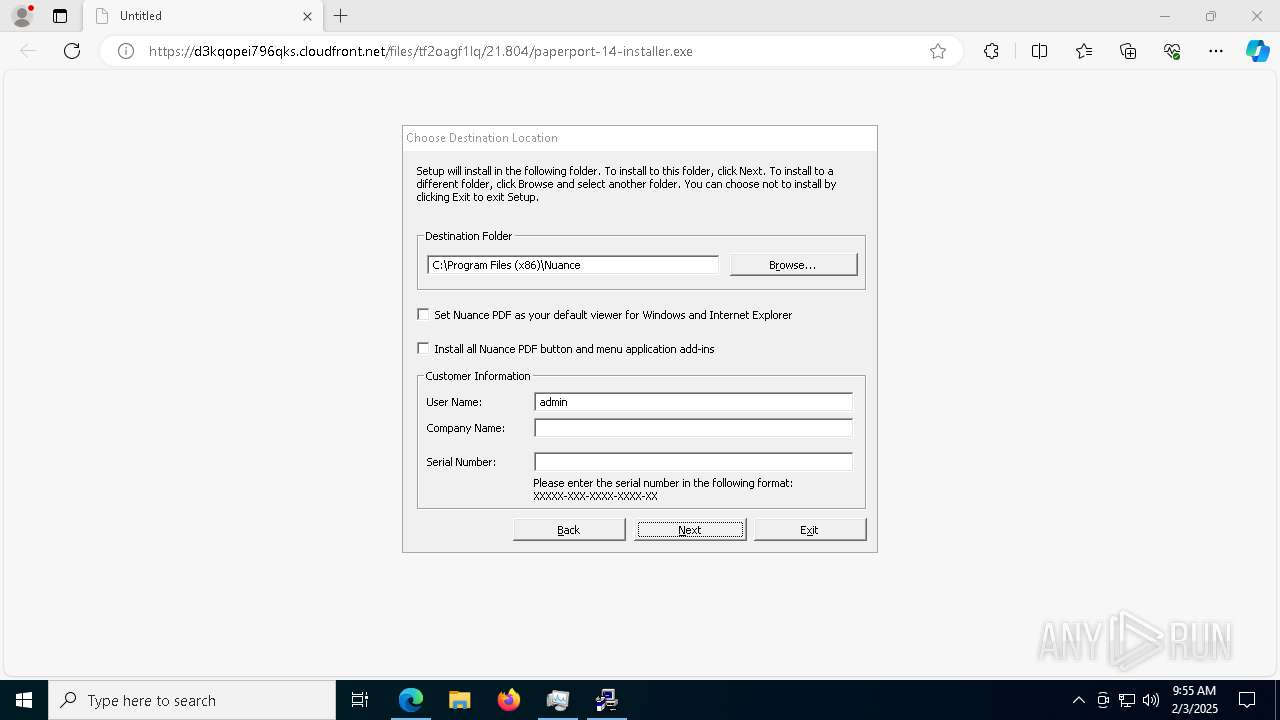
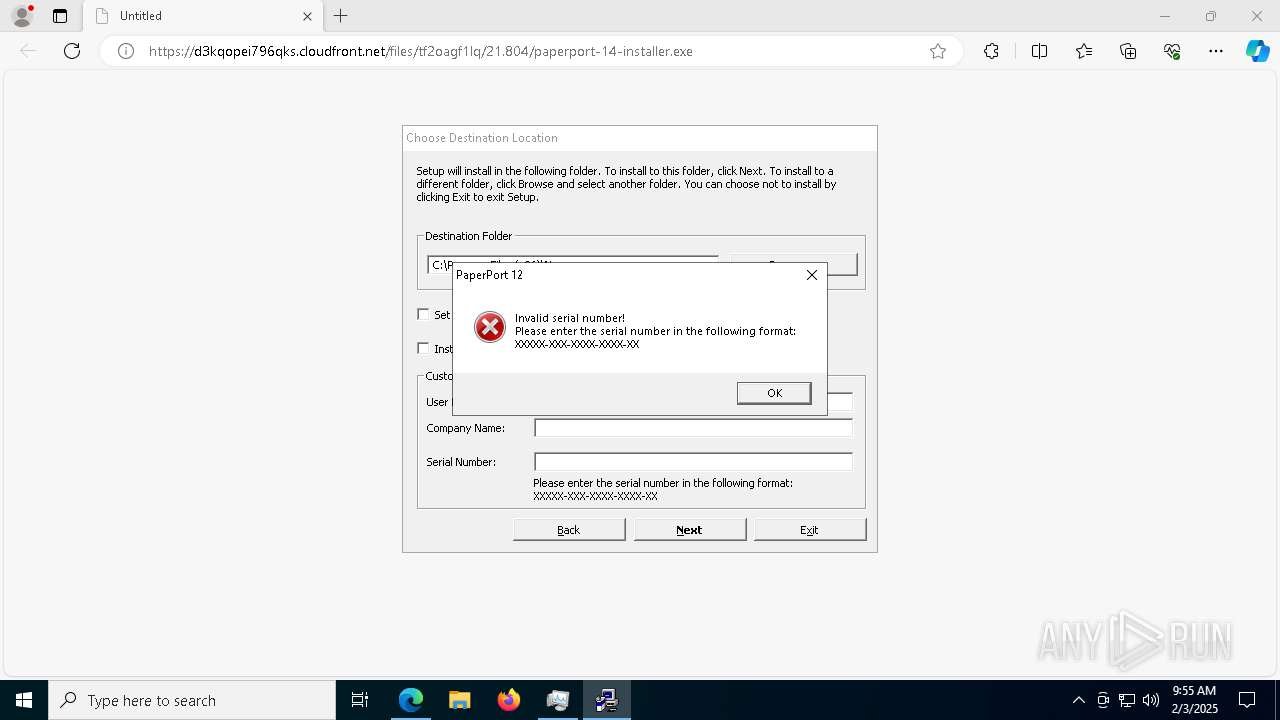
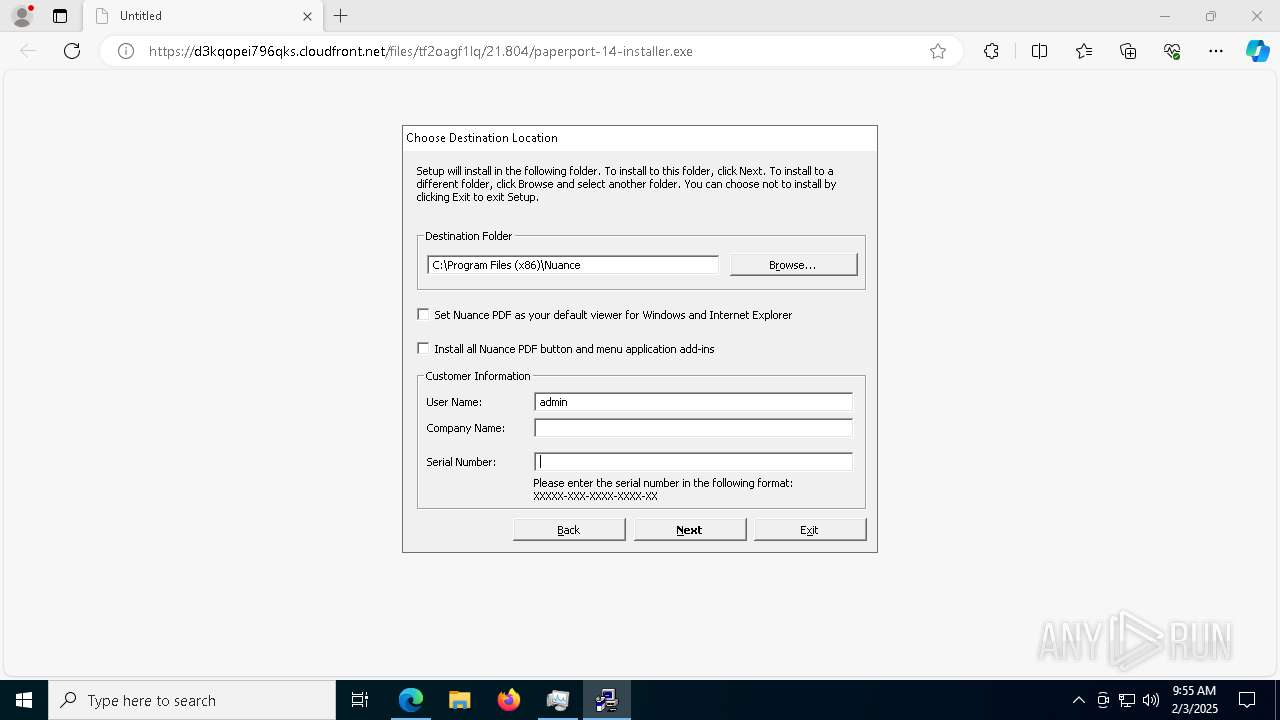
| URL: | https://d3kqopei796qks.cloudfront.net/files/tf2oagf1lq/21.804/paperport-14-installer.exe |
| Full analysis: | https://app.any.run/tasks/de2b6291-6610-4aef-be34-2d67e7592621 |
| Verdict: | Malicious activity |
| Analysis date: | February 03, 2025, 09:50:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 39FD684E6551607015D8E07B19EA8999 |
| SHA1: | 42D980CE0D3AA2C0A9E15DAEF63176A23F3A0FE8 |
| SHA256: | 3D939F59C08A5EEB6EF6E3665CBC1AB197FA92B747BC7B8C48DF8B55750A9334 |
| SSDEEP: | 3:N8O6iOWa1+l/0LKYEJUKiXsVEVyVK+UsXLNn:2OP5a1nSnEsgIXLN |
MALICIOUS
Executing a file with an untrusted certificate
- paperport-14-installer.exe (PID: 1448)
- AUTORUN.exe (PID: 2828)
Changes the autorun value in the registry
- vcredist_x86.exe (PID: 1740)
- vcredist_x64.exe (PID: 6320)
SUSPICIOUS
Executable content was dropped or overwritten
- paperport-14-installer_DmC4R-1.exe (PID: 7780)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- paperport-14-installer_DmC4R-1.exe (PID: 1064)
- paperport-14-installer.exe (PID: 1448)
- vcredist_x86.exe (PID: 1740)
- TiWorker.exe (PID: 4036)
- vcredist_x64.exe (PID: 6320)
Reads security settings of Internet Explorer
- paperport-14-installer_DmC4R-1.tmp (PID: 5564)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- AUTORUN.exe (PID: 2828)
- paperport-14-installer.exe (PID: 1448)
Reads the Windows owner or organization settings
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- msiexec.exe (PID: 7140)
Process drops legitimate windows executable
- paperport-14-installer.exe (PID: 1448)
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
Creates file in the systems drive root
- paperport-14-installer.exe (PID: 1448)
- AUTORUN.exe (PID: 2828)
Executes as Windows Service
- VSSVC.exe (PID: 7480)
Checks Windows Trust Settings
- msiexec.exe (PID: 7140)
The process drops C-runtime libraries
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
There is functionality for taking screenshot (YARA)
- AUTORUN.exe (PID: 2828)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7140)
INFO
Checks supported languages
- identity_helper.exe (PID: 7860)
- paperport-14-installer_DmC4R-1.exe (PID: 7780)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- paperport-14-installer_DmC4R-1.tmp (PID: 5564)
- paperport-14-installer_DmC4R-1.exe (PID: 1064)
- paperport-14-installer.exe (PID: 1448)
- vcredist_x86.exe (PID: 1740)
- AUTORUN.exe (PID: 2828)
- msiexec.exe (PID: 7140)
- msiexec.exe (PID: 308)
- vcredist_x64.exe (PID: 6320)
- msiexec.exe (PID: 7176)
- msiexec.exe (PID: 5000)
Reads the computer name
- paperport-14-installer_DmC4R-1.exe (PID: 7780)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- paperport-14-installer_DmC4R-1.tmp (PID: 5564)
- identity_helper.exe (PID: 7860)
- paperport-14-installer.exe (PID: 1448)
- msiexec.exe (PID: 7140)
- AUTORUN.exe (PID: 2828)
- msiexec.exe (PID: 308)
- msiexec.exe (PID: 7176)
- msiexec.exe (PID: 5000)
Reads Environment values
- identity_helper.exe (PID: 7860)
Create files in a temporary directory
- paperport-14-installer_DmC4R-1.exe (PID: 1064)
- paperport-14-installer_DmC4R-1.exe (PID: 7780)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- vcredist_x86.exe (PID: 1740)
- vcredist_x64.exe (PID: 6320)
Executable content was dropped or overwritten
- msedge.exe (PID: 6368)
- msedge.exe (PID: 6740)
- msedge.exe (PID: 4908)
- msiexec.exe (PID: 7140)
Process checks computer location settings
- paperport-14-installer_DmC4R-1.tmp (PID: 5564)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- paperport-14-installer.exe (PID: 1448)
- AUTORUN.exe (PID: 2828)
Checks proxy server information
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
Application launched itself
- msedge.exe (PID: 6368)
Reads the software policy settings
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
Reads the machine GUID from the registry
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- msiexec.exe (PID: 7140)
Compiled with Borland Delphi (YARA)
- paperport-14-installer_DmC4R-1.exe (PID: 1064)
- paperport-14-installer_DmC4R-1.exe (PID: 7780)
- paperport-14-installer_DmC4R-1.tmp (PID: 5564)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
Detects InnoSetup installer (YARA)
- paperport-14-installer_DmC4R-1.tmp (PID: 5564)
- paperport-14-installer_DmC4R-1.exe (PID: 1064)
- paperport-14-installer_DmC4R-1.tmp (PID: 6332)
- paperport-14-installer_DmC4R-1.exe (PID: 7780)
The sample compiled with english language support
- paperport-14-installer.exe (PID: 1448)
- msedge.exe (PID: 4908)
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
Manual execution by a user
- Taskmgr.exe (PID: 5256)
- Taskmgr.exe (PID: 6092)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6092)
The sample compiled with chinese language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
Manages system restore points
- SrTasks.exe (PID: 6160)
- SrTasks.exe (PID: 5836)
- SrTasks.exe (PID: 4968)
The sample compiled with french language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
The sample compiled with german language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
The sample compiled with japanese language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
The sample compiled with spanish language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
The sample compiled with korean language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
The sample compiled with Italian language support
- msiexec.exe (PID: 7140)
- TiWorker.exe (PID: 4036)
Creates a software uninstall entry
- msiexec.exe (PID: 7140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
214
Monitored processes
74
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | C:\Windows\syswow64\MsiExec.exe -Embedding 8038E3986DF583157290A18B63B7A3B4 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | "C:\Users\admin\Downloads\paperport-14-installer_DmC4R-1.exe" | C:\Users\admin\Downloads\paperport-14-installer_DmC4R-1.exe | msedge.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: FH Managеr Exit code: 0 Version: 12.11.2371.8174 Modules
| |||||||||||||||
| 1448 | "C:\Users\admin\Downloads\paperport-14-installer.exe" | C:\Users\admin\Downloads\paperport-14-installer.exe | paperport-14-installer_DmC4R-1.tmp | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1476 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=7220 --field-trial-handle=2328,i,433734262962248382,3616417582023639638,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7196 --field-trial-handle=2328,i,433734262962248382,3616417582023639638,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1740 | "C:\paperport12\Prerequisite\vcredist_x86.exe" /q:a /c:"msiexec /i vcredist.msi /qb!" | C:\paperport12\Prerequisite\vcredist_x86.exe | AUTORUN.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IExpress Setup Exit code: 0 Version: 2.0.50727.4053 Modules
| |||||||||||||||
| 1796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7416 --field-trial-handle=2328,i,433734262962248382,3616417582023639638,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5228 --field-trial-handle=2328,i,433734262962248382,3616417582023639638,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
28 233
Read events
25 935
Write events
2 105
Delete events
193
Modification events
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: C2E4FC1CD08B2F00 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: F0470E1DD08B2F00 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328532 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E237CDBD-3F87-4B16-8CD9-A8E674EC03D5} | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328532 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {349A2083-FE88-4BD1-99E2-8C28A93B76AA} | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 47D5561DD08B2F00 | |||
| (PID) Process: | (6368) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
177
Suspicious files
624
Text files
282
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF136555.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF136555.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF136564.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF136564.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF136564.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
59
TCP/UDP connections
77
DNS requests
76
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6368 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEQDBOCr9OqmctqAaukvLVR0m | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6368 | msedge.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
2260 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2260 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6272 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6004 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6ca9004c-2afd-40c0-a9b1-4fec460952e5?P1=1738729874&P2=404&P3=2&P4=DNiUnQqWhP6DYVLzM%2bfhj5wDicqE12CnZ97MIncKLL6COvJ8jH%2fdcnNbxpXOWQrCkBCsx90pepJmum%2bBbg1PSw%3d%3d | unknown | — | — | whitelisted |
2380 | svchost.exe | GET | 200 | 2.16.164.40:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2380 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2380 | svchost.exe | 2.16.164.40:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2380 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
6368 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6740 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
d3kqopei796qks.cloudfront.net |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |