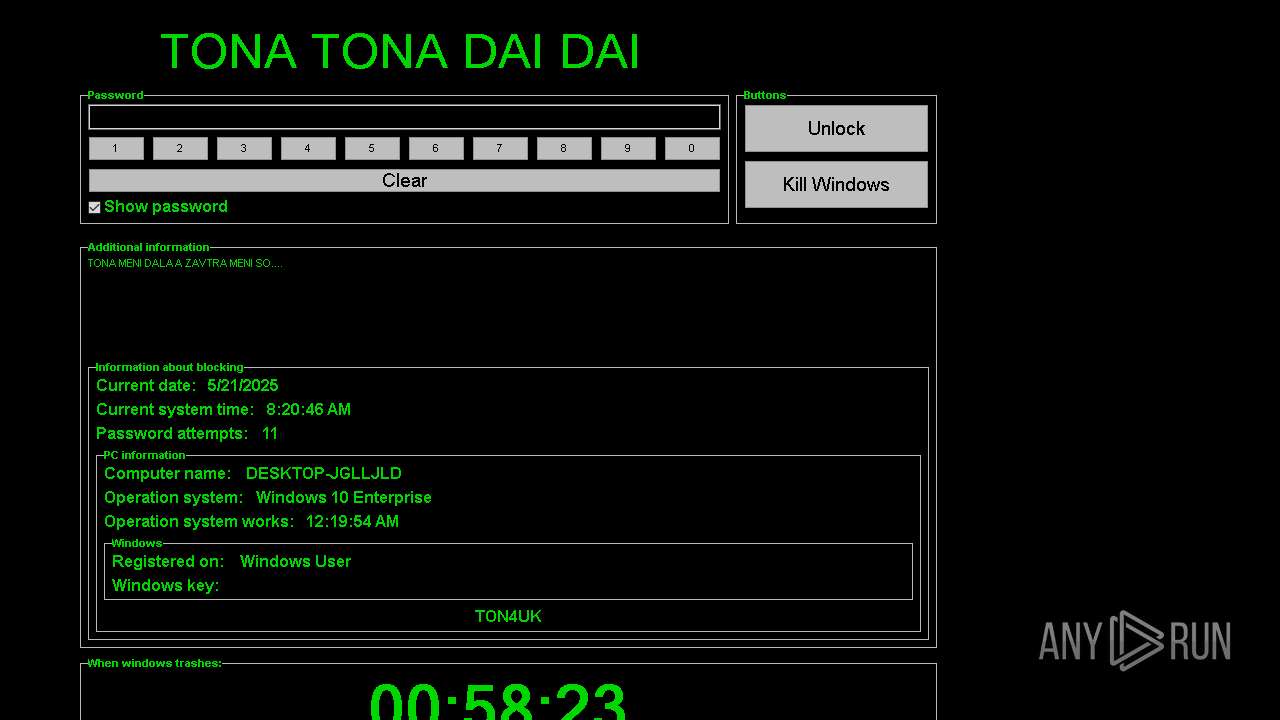
| File name: | 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock |
| Full analysis: | https://app.any.run/tasks/13568d77-e317-4dd0-a641-ce6ba88df773 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 08:19:03 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 4 sections |
| MD5: | FF8D30DA13138D575ECABB6262BAF2C9 |
| SHA1: | 1EAE1714A6430CD9F1FE518F713B130C9CC2FDB6 |
| SHA256: | 3D92FF3FC306EA3FAE649C7A66393A3B40E37EC96FDE0E98FB456B60F6725BDB |
| SSDEEP: | 49152:fg/q1q56N/+X1YQ/Lbv8quQ6+IIgg4KgVji4y:qq1q560Xh/LWQ6VIgg2Vy |
MALICIOUS
FRAGTOR mutex has been found
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Changes Windows Defender settings
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Adds path to the Windows Defender exclusion list
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
UAC/LUA settings modification
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Disables Windows Defender
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Disables the Shutdown in the Start menu
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Changes the autorun value in the registry
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Disables the Run the Start menu
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Disables the Find the Start menu
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Changes image file execution options
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Disables the LogOff the Start menu
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
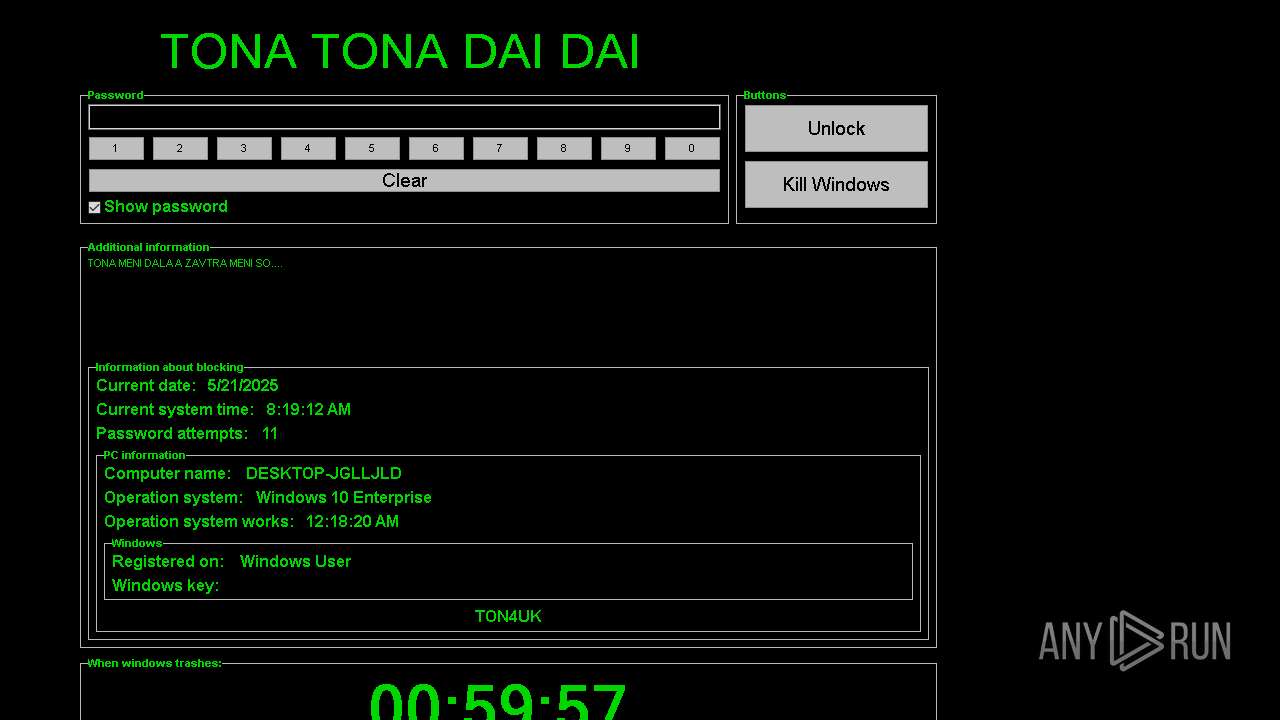
WINLOCKER has been detected (YARA)
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
SUSPICIOUS
Reads security settings of Internet Explorer
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Script adds exclusion path to Windows Defender
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Starts CMD.EXE for commands execution
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Starts POWERSHELL.EXE for commands execution
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
There is functionality for VM detection VirtualBox (YARA)
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
There is functionality for taking screenshot (YARA)
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
There is functionality for VM detection VMWare (YARA)
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
INFO
Reads the computer name
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Checks supported languages
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Process checks computer location settings
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Auto-launch of the file from Registry key
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Create files in a temporary directory
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3836)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3836)
Mpress packer has been detected
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
Compiled with Borland Delphi (YARA)
- 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe (PID: 6728)
- slui.exe (PID: 4340)
Checks proxy server information
- slui.exe (PID: 4340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, No debug, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1172992 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11f5b8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
141
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2100 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe" | C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4340 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4892 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 2147945463 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6624 | "C:\Windows\System32\cmd.exe" /c schtasks /create /tn "GoogleUpdateTaskMachineUK" /sc MINUTE /mo 1 /tr "C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe" /rl HIGHEST /f | C:\Windows\System32\cmd.exe | — | 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6728 | "C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe" | C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
6 625
Read events
6 591
Write events
34
Delete events
0
Modification events
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Qwe |
Value: C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utilman.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\reg.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | |||
| (PID) Process: | (6728) 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmd.exe |
| Operation: | write | Name: | Debugger |
Value: "cmd.exe","C:\Users\admin\Desktop\2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe" | |||
Executable files
0
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3836 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:D96093FD3F85FD9C9F44AA48FDA1B12C | SHA256:390EC90281E41492997F64F9930B3D20E832480E3A8B939F60C71282A31CA3AE | |||
| 6728 | 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | C:\Users\admin\AppData\Local\Temp\Time2.ini | text | |
MD5:EE71EF7E930722B5B29011DD13C1F0BE | SHA256:0DCB9642194F08F6EC65920AB26F5BC10653983CDE9F3A82505E297E44E15C3C | |||
| 3836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_k52dthv5.lmn.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3836 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ajjf3kzr.31r.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6728 | 2025-05-21_ff8d30da13138d575ecabb6262baf2c9_darkgate_elex_gcleaner_ransomlock.exe | C:\Users\admin\AppData\Local\Temp\Time.ini | text | |
MD5:EB13B7EAF7F30D348E471F0907B31AAC | SHA256:94BA214735774FB4E68BE906C3E181D29C71DBBCD10540E70BA7021FCF5EA3AA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
38
DNS requests
18
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2656 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6112 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |