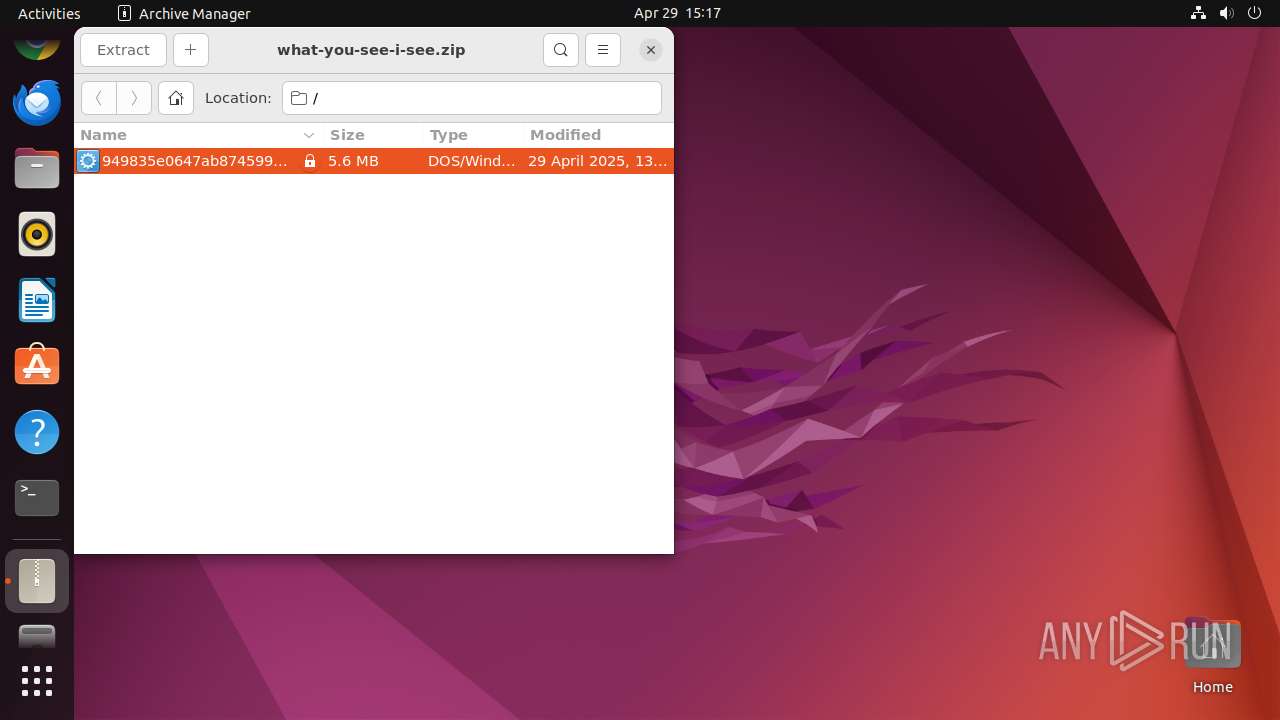
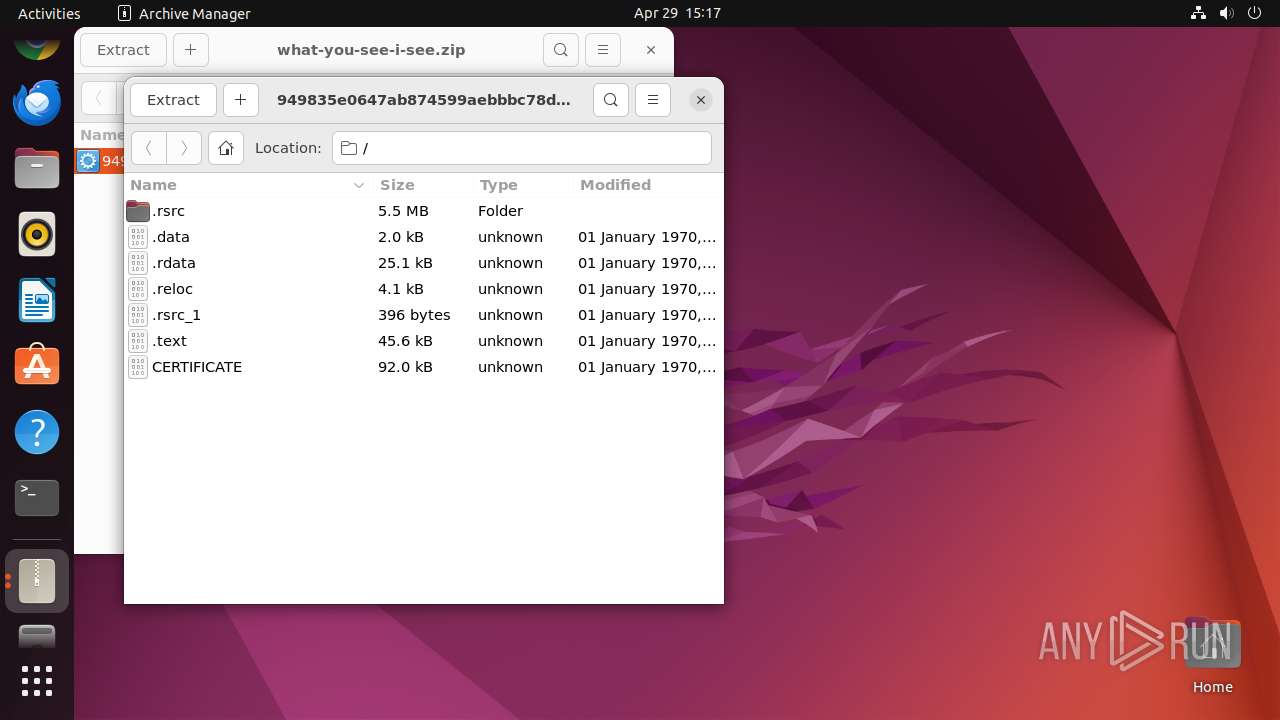
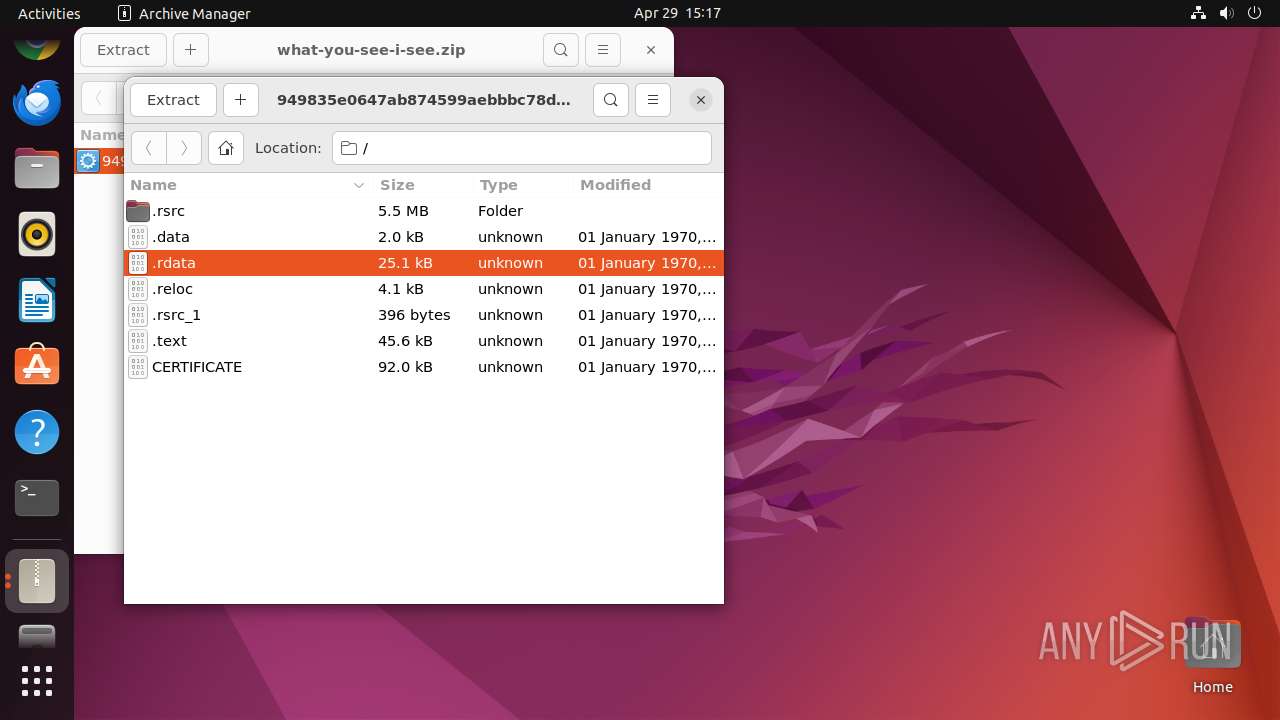
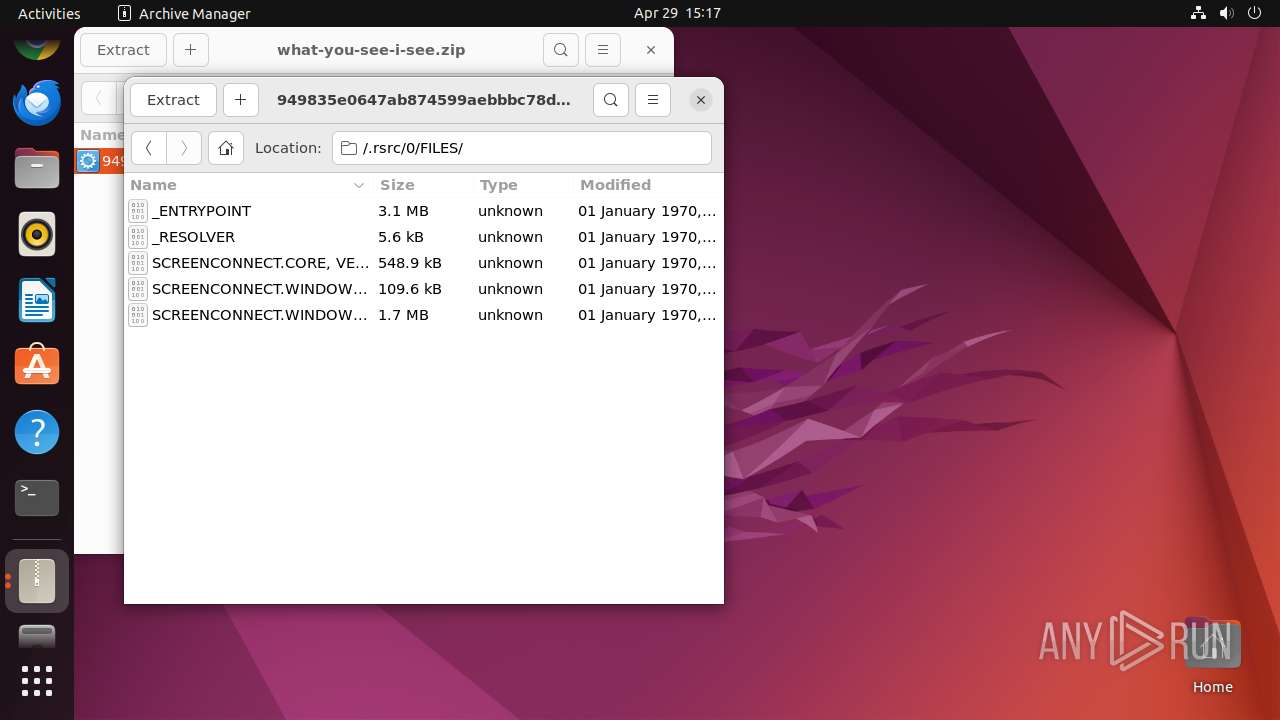
| File name: | what-you-see-i-see.zip |
| Full analysis: | https://app.any.run/tasks/fc936ace-eed3-44cd-ac6e-b40c0f6a1236 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 14:16:59 |
| OS: | Ubuntu 22.04.2 |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | F623B9F82F498C974430522193518C2C |
| SHA1: | 82F41711F8C0F82E5268629BE1D79557FECABEFD |
| SHA256: | 3D878AE061BFFEAC2417FB1A860F14B8F21425AED8A4CF895D3B46B216B8E5EC |
| SSDEEP: | 98304:iti4ySWTU3hdmWP0uggjJ/OO1/2cQCqIwK8t/hizzAl8FyV1Z8ScFIV4jX+pKqZM:wQUkom/U |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes commands using command-line interpreter
- sudo (PID: 39500)
- file-roller (PID: 39545)
- chrome (PID: 39546)
Reads passwd file
- file-roller (PID: 39502)
Reads profile file
- file-roller (PID: 39502)
Executable content was dropped or overwritten
- 7z (PID: 39534)
- 7z (PID: 39741)
- 7z (PID: 39763)
INFO
Checks timezone
- file-roller (PID: 39502)
- 7z (PID: 39517)
- 7z (PID: 39528)
- 7z (PID: 39542)
- 7z (PID: 39534)
- 7z (PID: 39544)
- chrome (PID: 39546)
- 7z (PID: 39741)
- 7z (PID: 39749)
- 7z (PID: 39754)
- 7z (PID: 39763)
- 7z (PID: 39771)
- 7z (PID: 39773)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:29 13:56:26 |
| ZipCRC: | 0x0e462689 |
| ZipCompressedSize: | 3987539 |
| ZipUncompressedSize: | 5622144 |
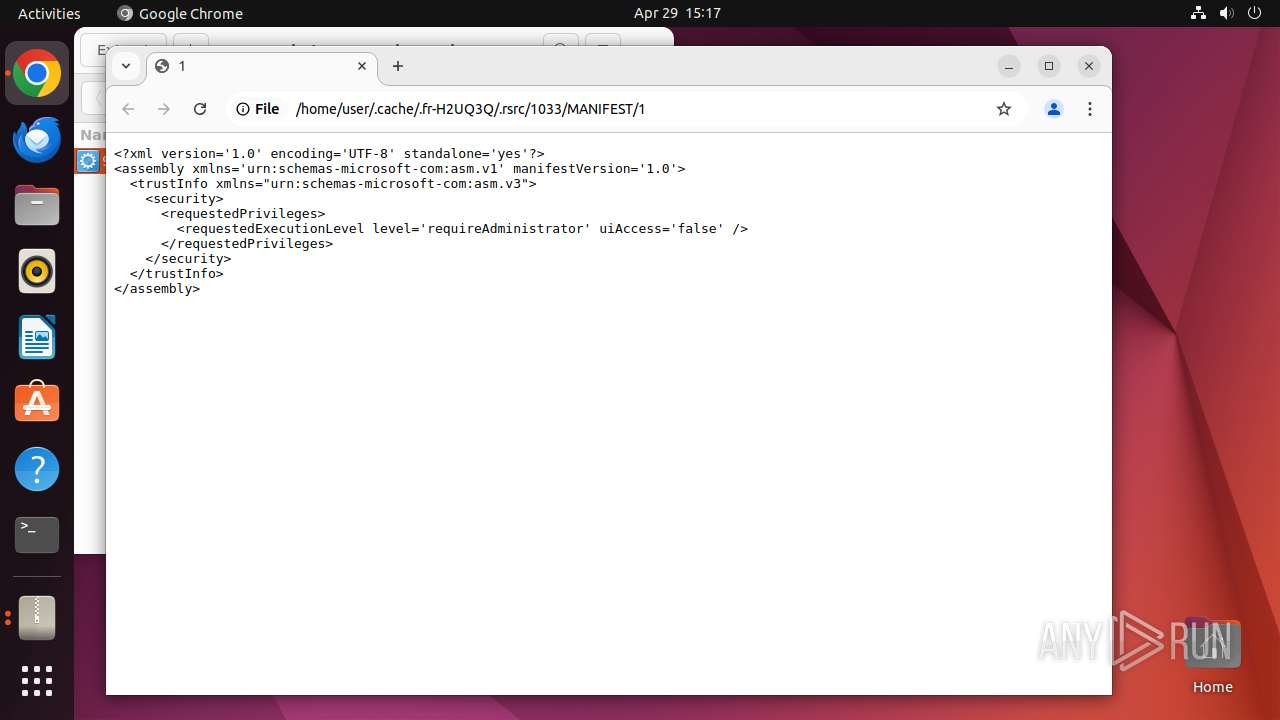
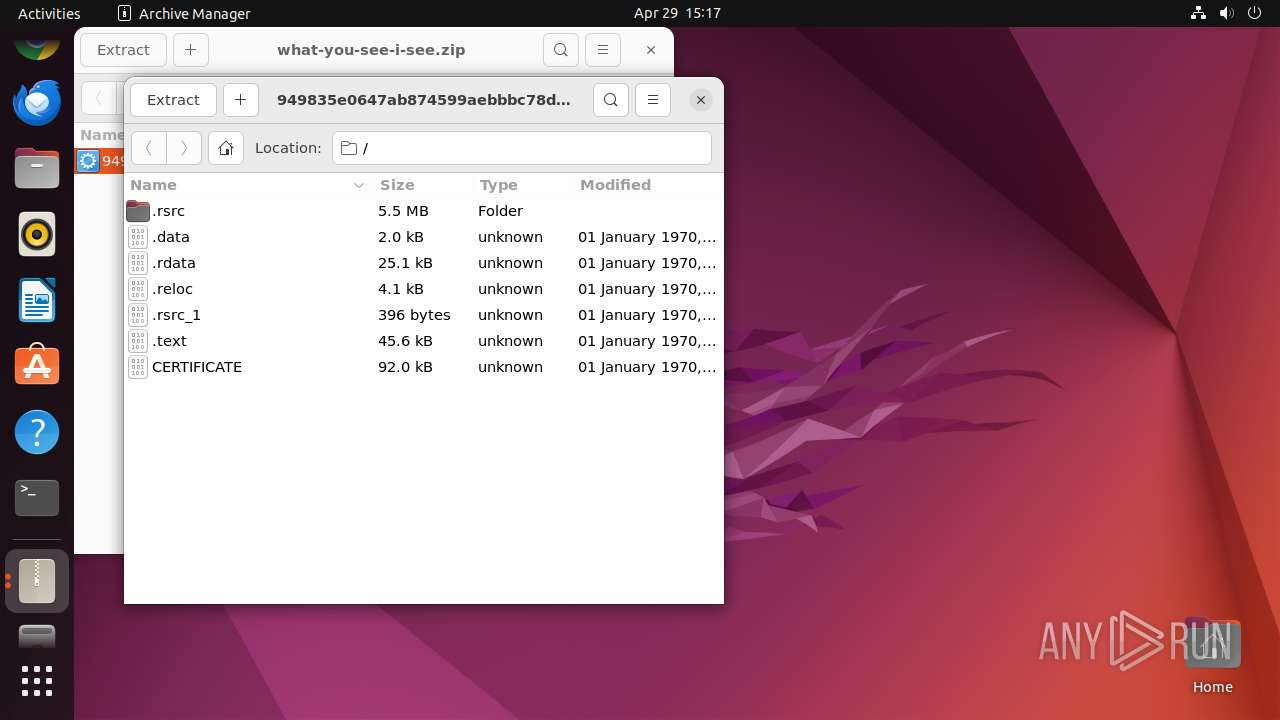
| ZipFileName: | 949835e0647ab874599aebbbc78d82cf8aed862e1576db59d1bcff058b35bd55.exe |
Total processes
320
Monitored processes
97
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 39499 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller /tmp/what-you-see-i-see\.zip " | /usr/bin/dash | — | any-guest-agent |
User: user Integrity Level: UNKNOWN | ||||
| 39500 | sudo -iu user file-roller /tmp/what-you-see-i-see.zip | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 39501 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39502 | file-roller /tmp/what-you-see-i-see.zip | /usr/bin/file-roller | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 39503 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39517 | /usr/lib/p7zip/7z l -slt -bd -y -- /tmp/what-you-see-i-see.zip | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39528 | /usr/lib/p7zip/7z x -bd -bb1 -y -o/home/user/.cache/.fr-SqFae3 -- /tmp/what-you-see-i-see.zip 949835e0647ab874599aebbbc78d82cf8aed862e1576db59d1bcff058b35bd55.exe | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 512 | ||||
| 39534 | /usr/lib/p7zip/7z x -bd -bb1 -y -pinfected -o/home/user/.cache/.fr-6jH5Dy -- /tmp/what-you-see-i-see.zip 949835e0647ab874599aebbbc78d82cf8aed862e1576db59d1bcff058b35bd55.exe | /usr/lib/p7zip/7z | file-roller | |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39535 | file-roller /tmp/what-you-see-i-see.zip | /usr/bin/file-roller | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39536 | file-roller /home/user/.cache/.fr-6jH5Dy/949835e0647ab874599aebbbc78d82cf8aed862e1576db59d1bcff058b35bd55.exe | /usr/bin/file-roller | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
3
Suspicious files
56
Text files
13
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 39546 | chrome | /home/user/.config/google-chrome/ShaderCache/data_3 | vxd | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/ShaderCache/data_2 | vxd | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/ShaderCache/data_0 | vxd | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/Default/Sync Data/LevelDB/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/Default/shared_proto_db/metadata/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/Default/Extension State/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/Default/shared_proto_db/MANIFEST-000001 | binary | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/GrShaderCache/data_3 | vxd | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/GrShaderCache/data_2 | vxd | |
MD5:— | SHA256:— | |||
| 39546 | chrome | /home/user/.config/google-chrome/GrShaderCache/data_0 | vxd | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
13
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
— | — | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.98:80 | — | Canonical Group Limited | GB | unknown |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 212.102.56.179:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
512 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
39591 | chrome | 142.250.184.195:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
39591 | chrome | 216.58.212.138:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
39591 | chrome | 108.177.119.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
odrs.gnome.org |
| whitelisted |
google.com |
| whitelisted |
api.snapcraft.io |
| whitelisted |
9.100.168.192.in-addr.arpa |
| unknown |
clientservices.googleapis.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
connectivity-check.ubuntu.com |
| whitelisted |