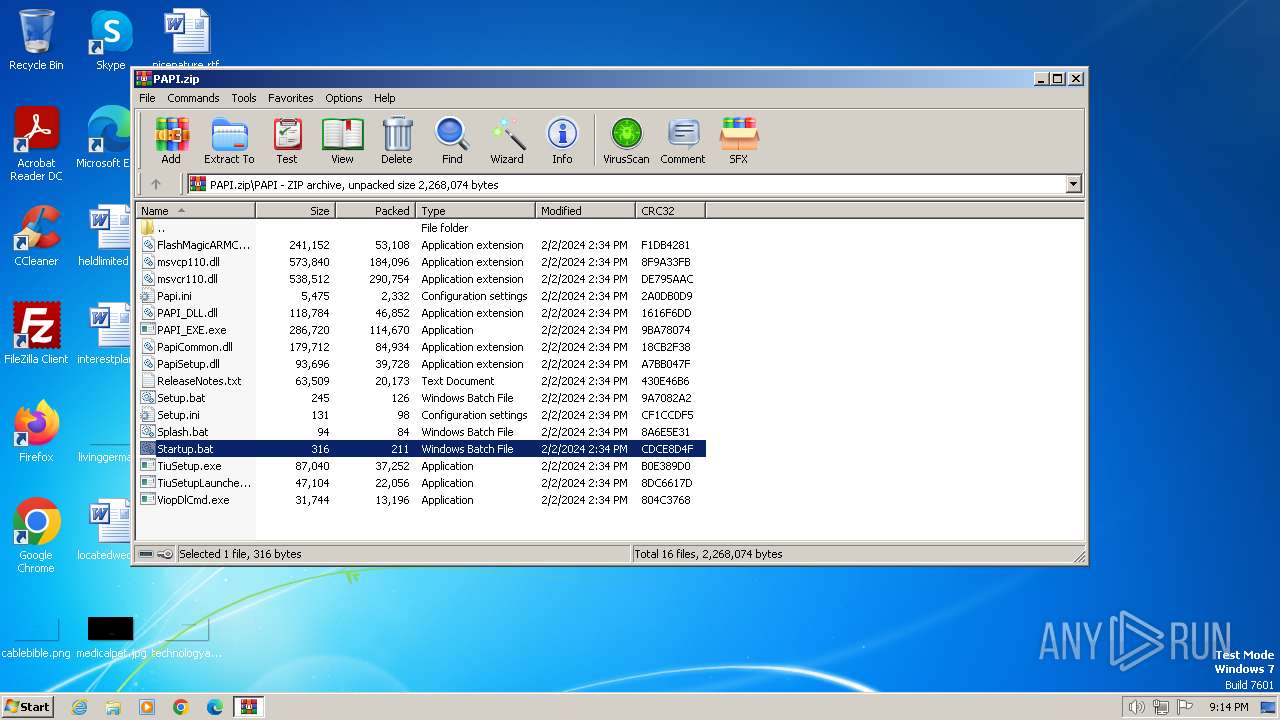
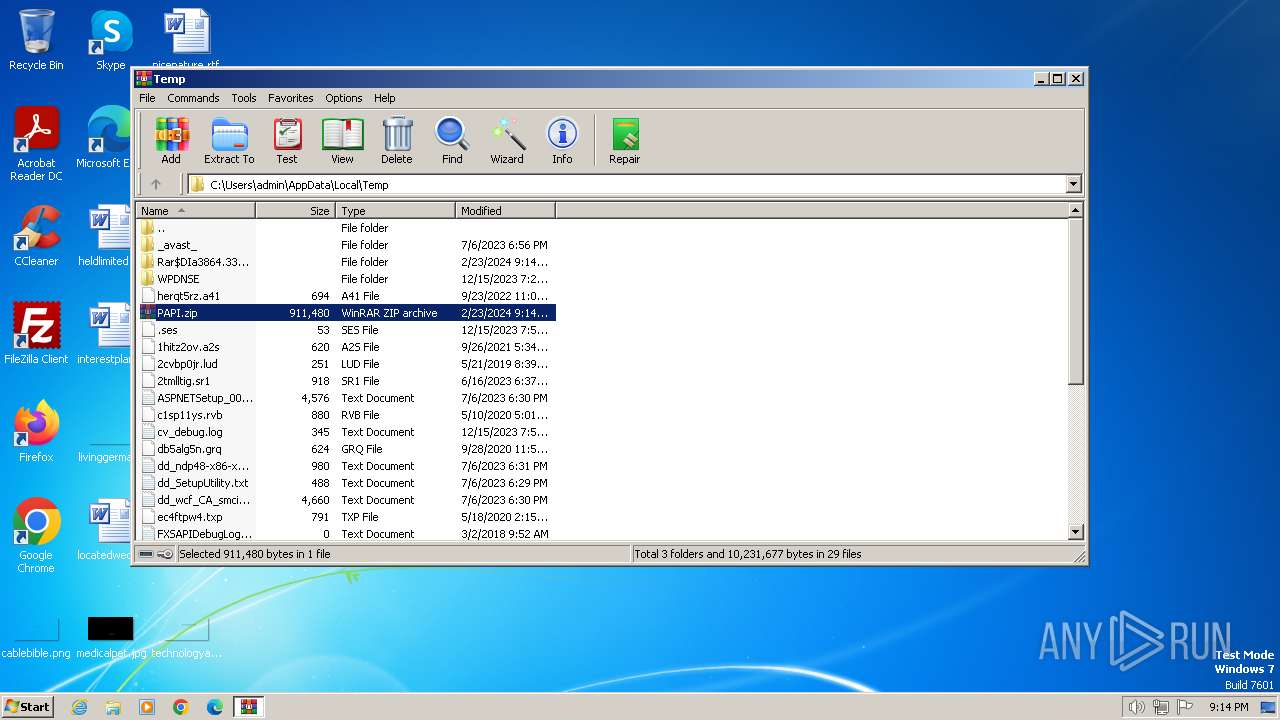
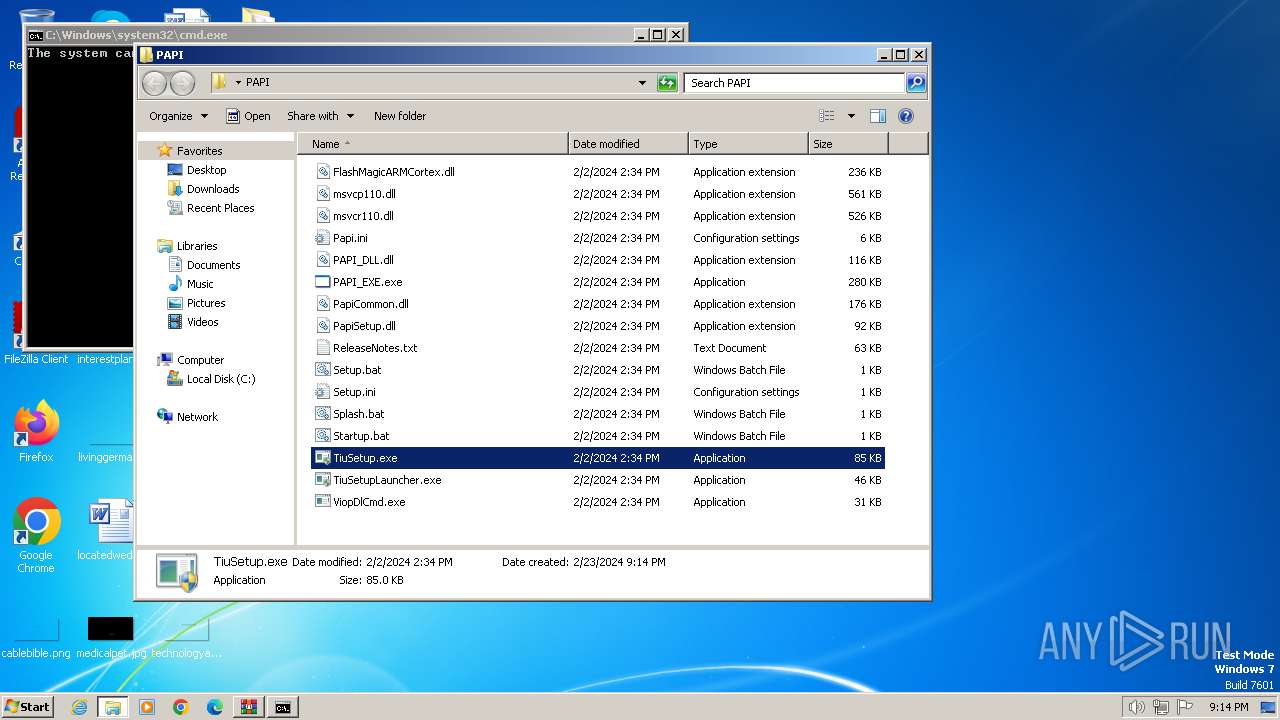
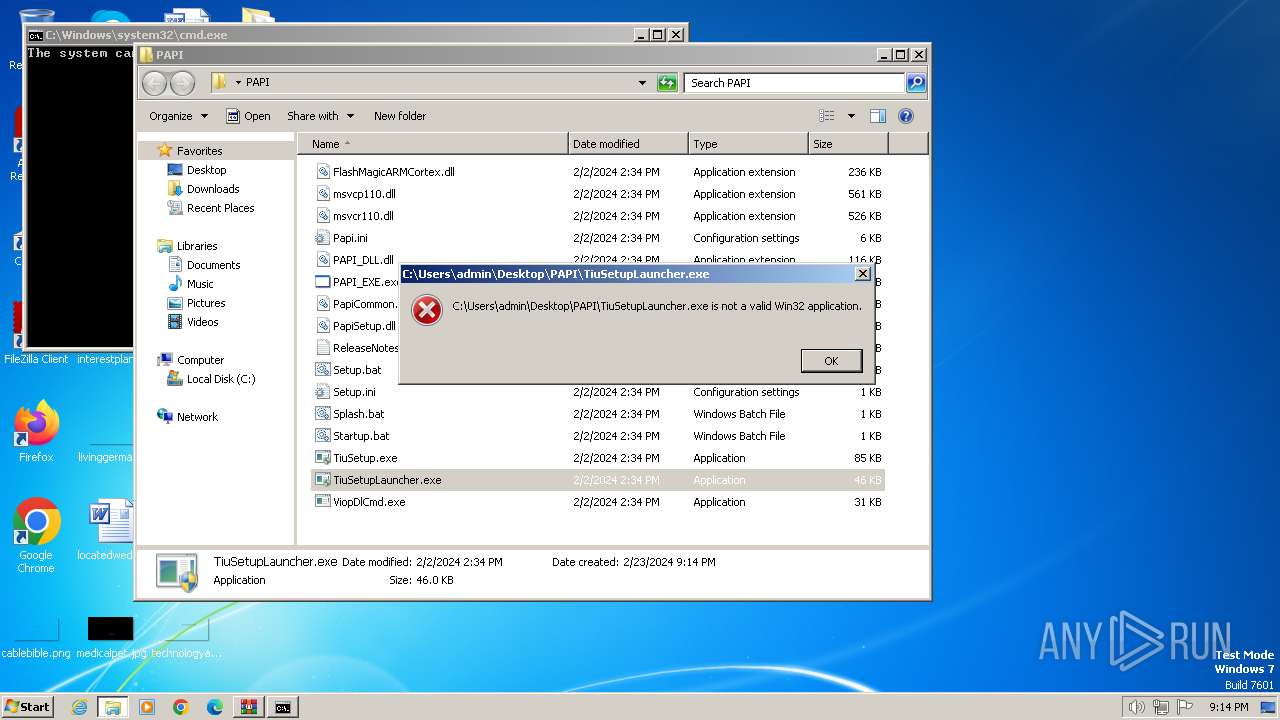
| File name: | PAPI.zip |
| Full analysis: | https://app.any.run/tasks/1d7cab73-cd34-4511-9095-14cffae83520 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 21:13:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 228A2BADE48E32A44B230ECBA61AE258 |
| SHA1: | 85158973A6A7CBCC1455419662367ECF6A443867 |
| SHA256: | 3D7895C3D5439B349053DF853951A4F49A089C7E7C0B9D20952C1E096799BD89 |
| SSDEEP: | 49152:41m4oAHxoR7WKxuHU4915ncVRFz4UYP5PJBJes6DyhrQJjA8qlVXXzYdAL9tsYHd:Im4oAHx47Wm0U4915ncVPz4vXBkzm5Qo |
MALICIOUS
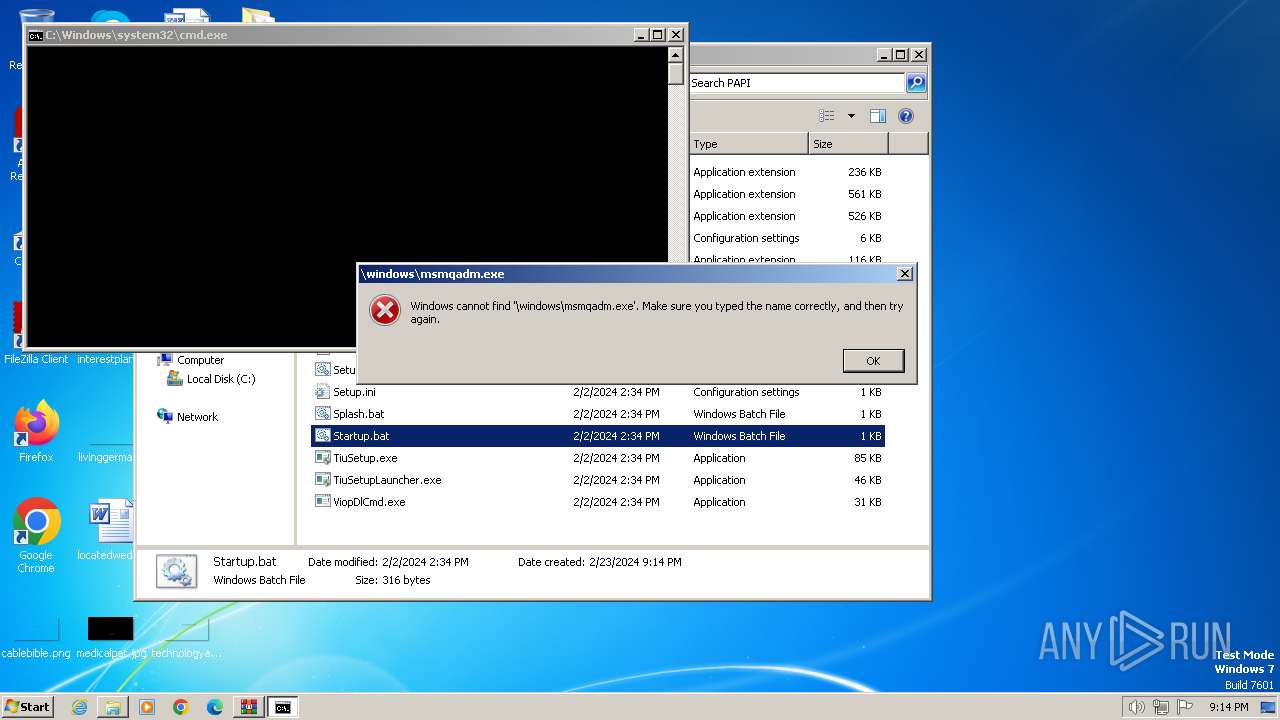
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3864)
SUSPICIOUS
The process drops C-runtime libraries
- WinRAR.exe (PID: 3864)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3864)
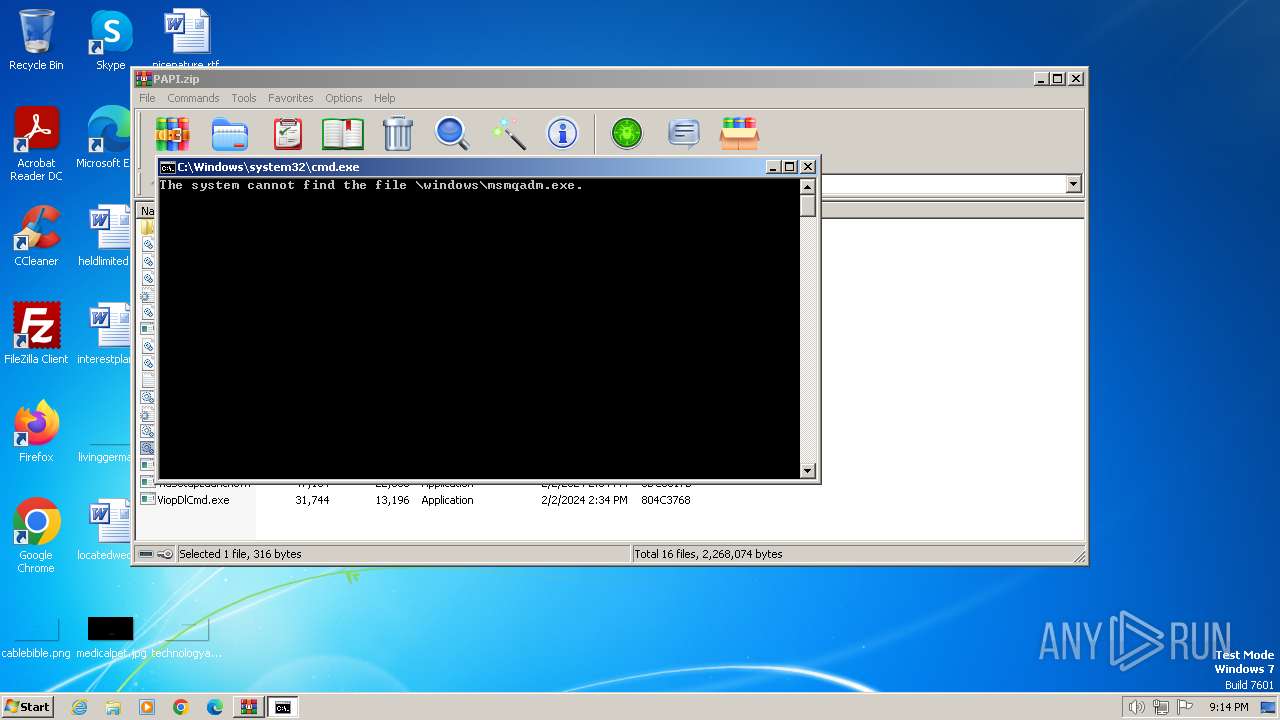
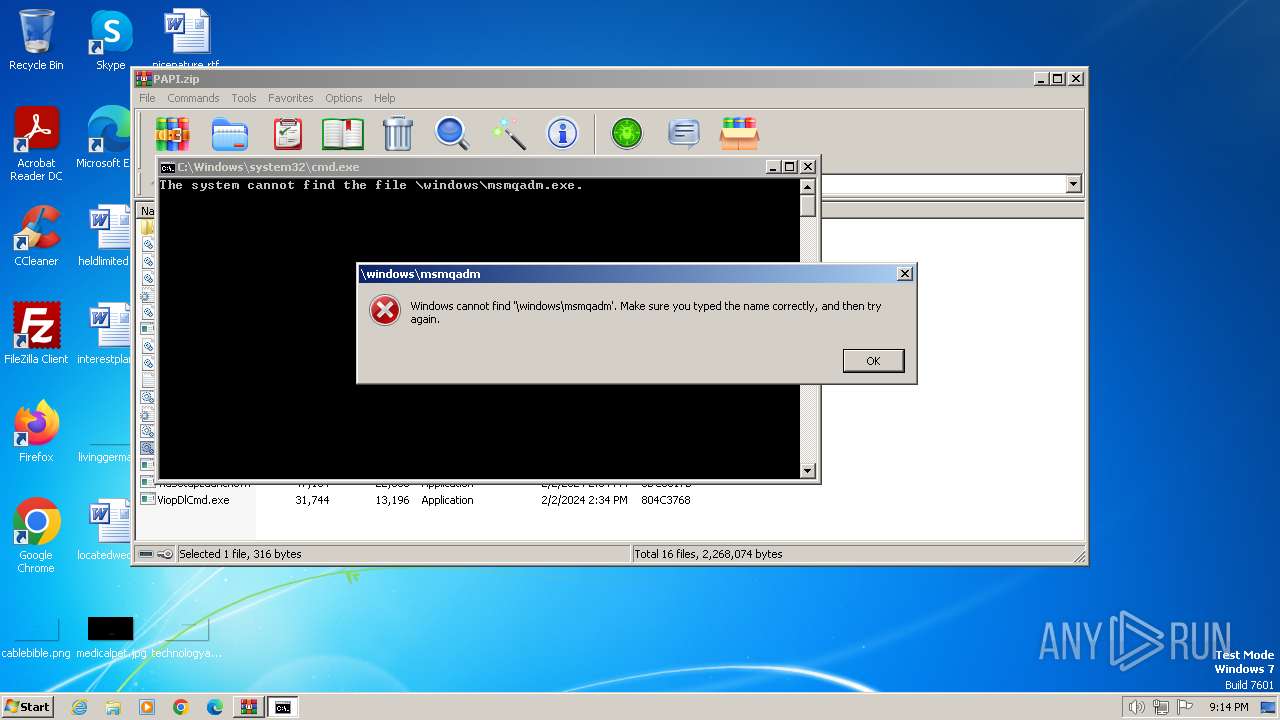
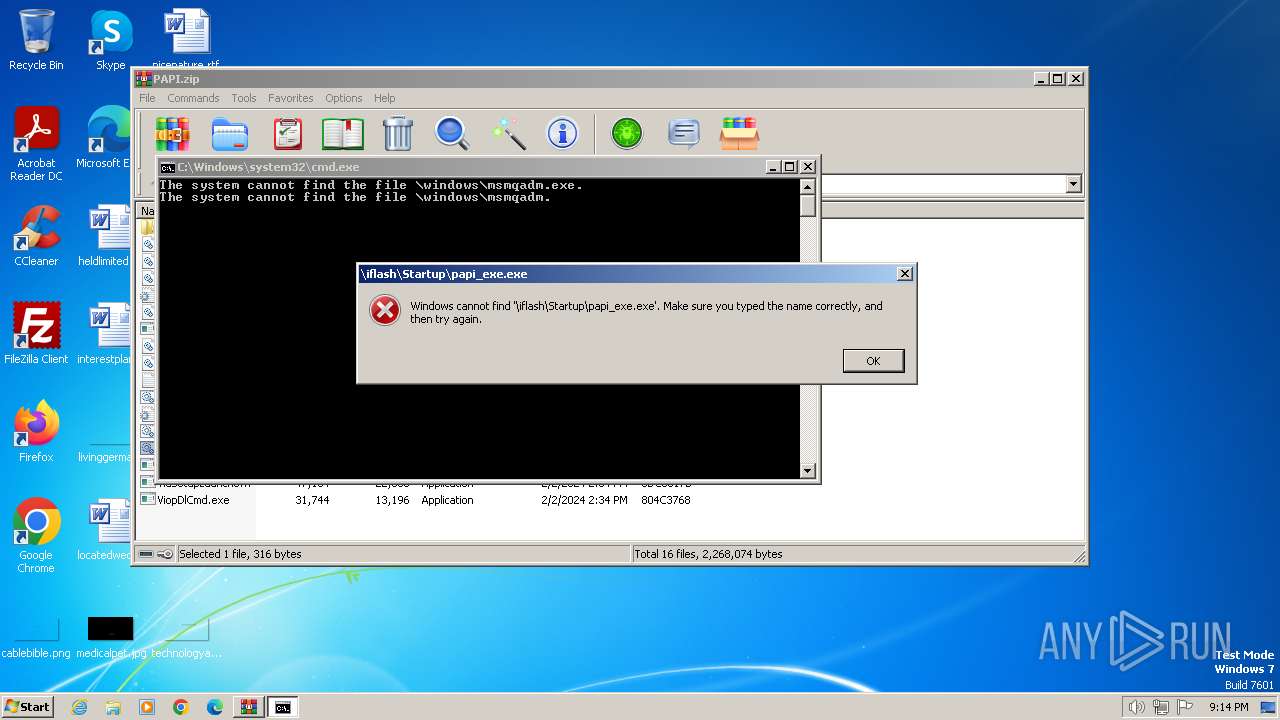
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3864)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3864)
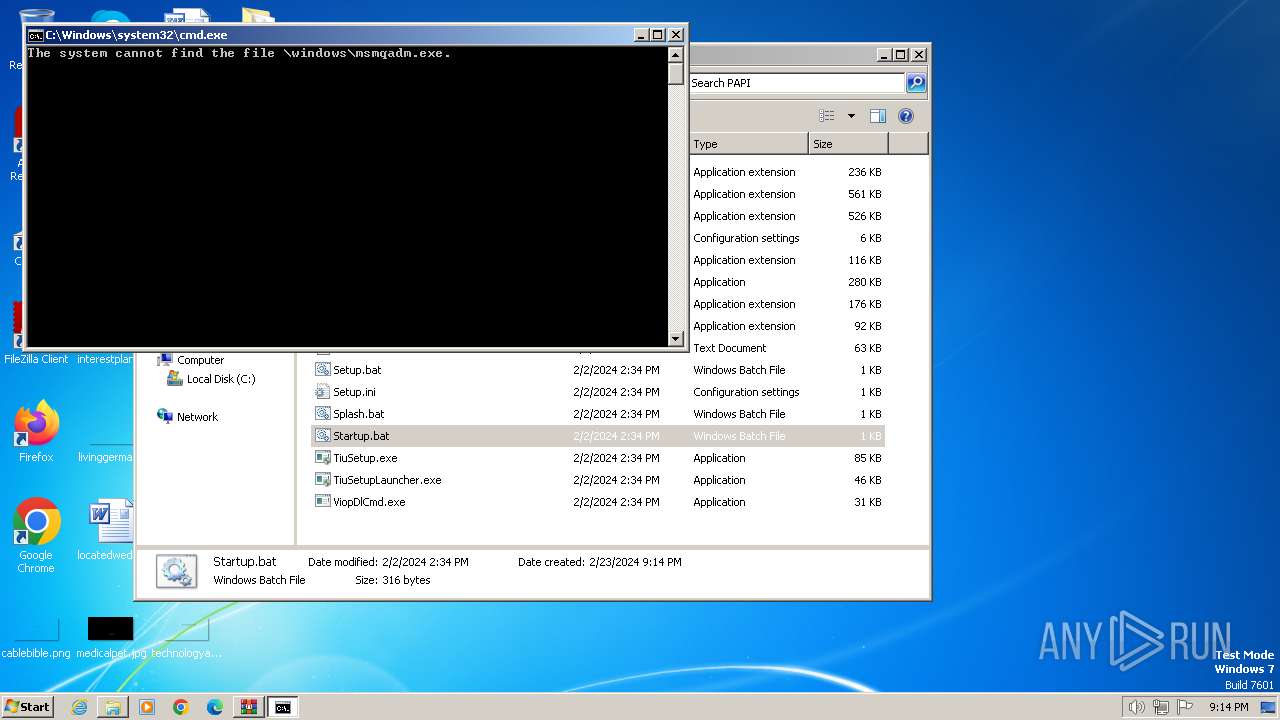
Executing commands from a ".bat" file
- WinRAR.exe (PID: 3864)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3536)
- cmd.exe (PID: 4008)
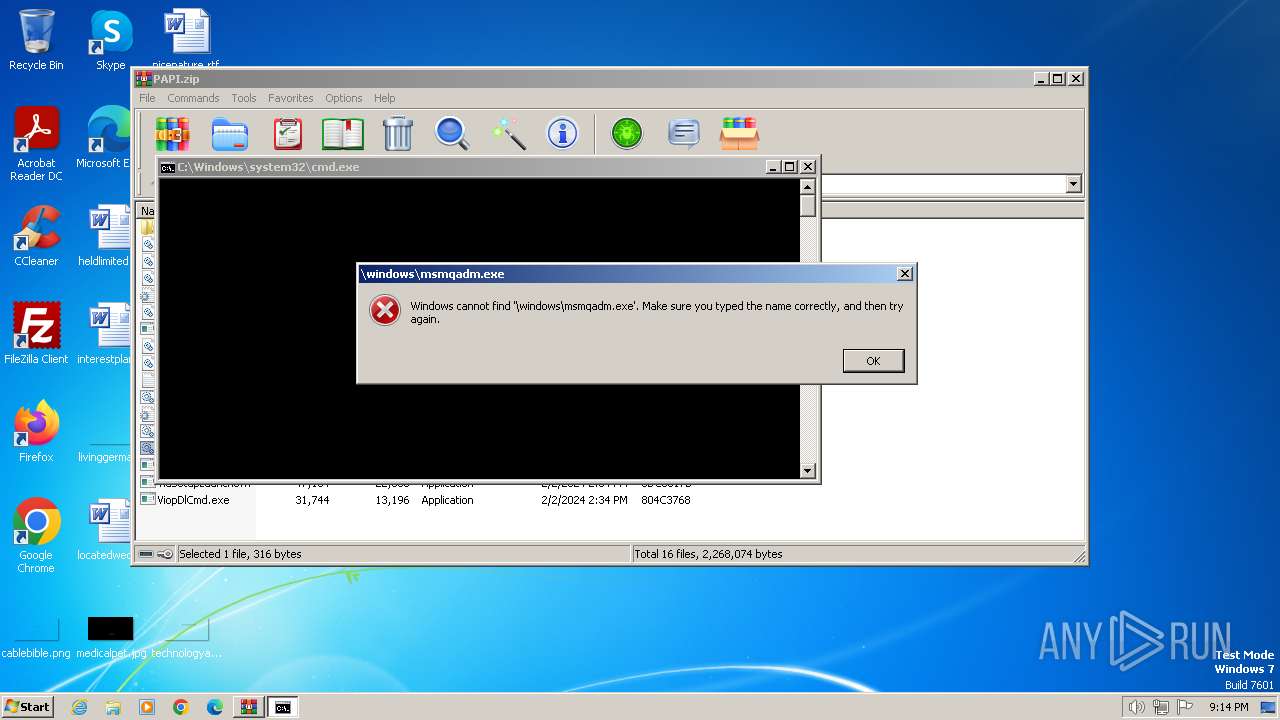
The process creates files with name similar to system file names
- WinRAR.exe (PID: 3864)
INFO
Manual execution by a user
- cmd.exe (PID: 4008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:02 14:34:02 |
| ZipCRC: | 0xf1db4281 |
| ZipCompressedSize: | 53108 |
| ZipUncompressedSize: | 241152 |
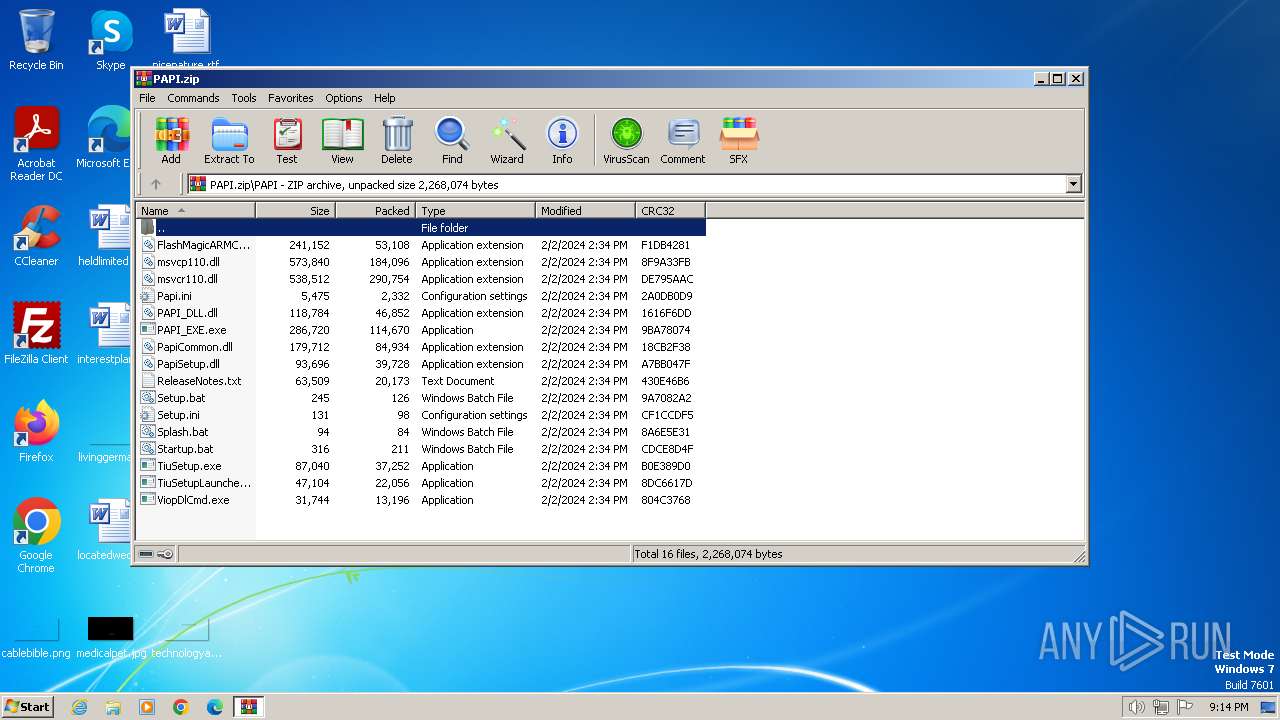
| ZipFileName: | PAPI\FlashMagicARMCortex.dll |
Total processes
44
Monitored processes
5
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2856 | ping 127.0.0.1 -n 2 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3536 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3864.33312\Startup.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 9059 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PAPI.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3892 | ping 127.0.0.1 -n 2 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4008 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\PAPI\Startup.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 143
Read events
6 106
Write events
37
Delete events
0
Modification events
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PAPI.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
10
Suspicious files
1
Text files
6
Unknown types
0
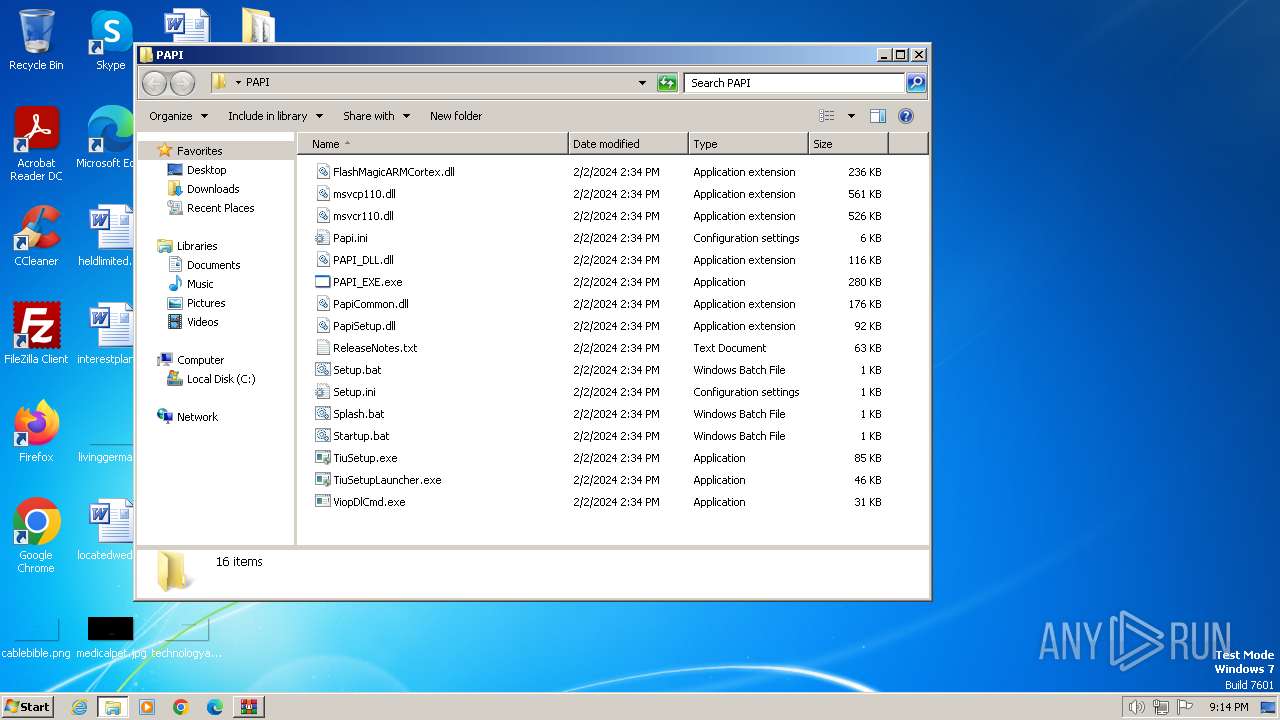
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\msvcr110.dll | executable | |
MD5:3C01E0EABEE765E8AE8E10D6342EF7B4 | SHA256:015FBB2D6B4E56C1776FDAB2CFF929984C1D51273A38DC8AB1FE55318DBC7072 | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\PapiCommon.dll | executable | |
MD5:1643DC51796324EEC488DC5DBFA62A5B | SHA256:1F7105832C33DD967DC3B7371A06D05D423C53605D96A93560DB42A5A1A42712 | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\PapiSetup.dll | executable | |
MD5:879CC17279ABE3EA3A90F0E4199C696C | SHA256:4DE5011A9303CD1141386C31A89258FB84CF7FAB7B0D063C60E52BF69F46D8B5 | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\Papi.ini | binary | |
MD5:9F0CC42D60E75A087C6F327154A07772 | SHA256:31C24891E5BFDAF1613CED1B9332DF8CD09615D3D6B8FC2B54065FB5DC06984F | |||
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3864.33312\Startup.bat | text | |
MD5:0A859B3B685A182CCB02D71415A08217 | SHA256:063839D552364720B42AB70636D0CB5DC26EE18AF320DE0275B3828CDE7E5CA5 | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\msvcp110.dll | executable | |
MD5:4ECB783551D537CB2F556CBCB88BB65F | SHA256:5BCC0573A91F9A3D86FD474A135A69CE3F469F38ED899DC00FD40BF14B73C847 | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\Setup.ini | ini | |
MD5:901E3B635FEB86266037D1CD577C7B73 | SHA256:E36EF413915AE2B22A2937B537A68DF58B77EACA9D8D6475C447478C140EE46C | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\TiuSetup.exe | executable | |
MD5:418F4EC1FC08B9D826A067E1D303BE76 | SHA256:0084F07251D3BEBEF8DB783971D07CB81014C7B80B9E7394FA25860D481AC41E | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\Startup.bat | text | |
MD5:0A859B3B685A182CCB02D71415A08217 | SHA256:063839D552364720B42AB70636D0CB5DC26EE18AF320DE0275B3828CDE7E5CA5 | |||
| 3864 | WinRAR.exe | C:\Users\admin\Desktop\PAPI\Splash.bat | text | |
MD5:5497BA71592767D9F40B86A0C91E9B64 | SHA256:CCCEF7198657C550AA05B2C9778F618418E75FDB161F5E0134C4CC37476A2CF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |