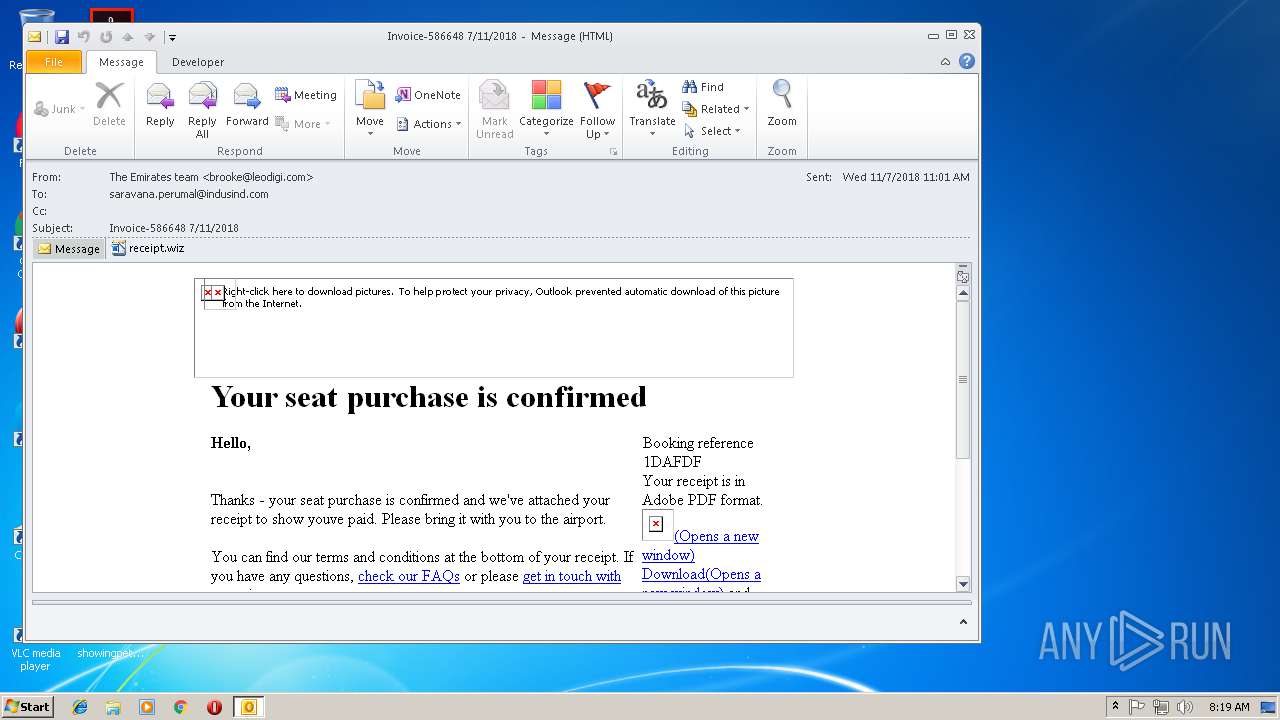
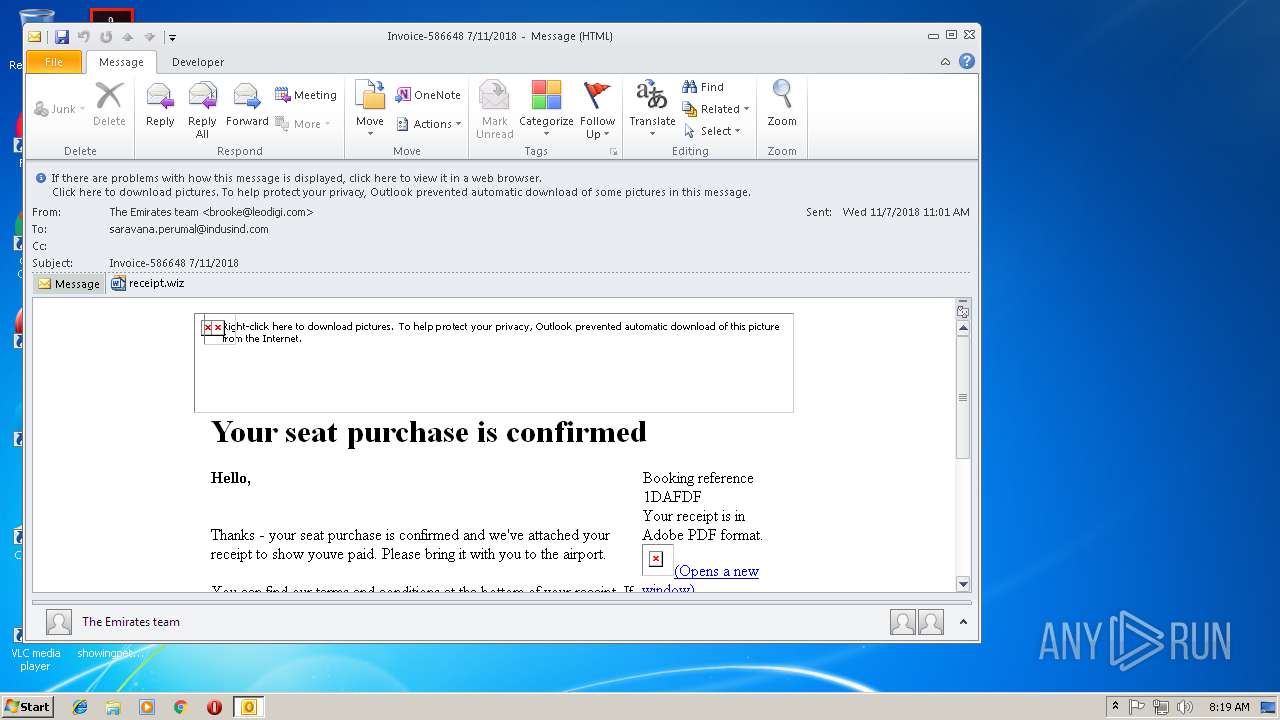
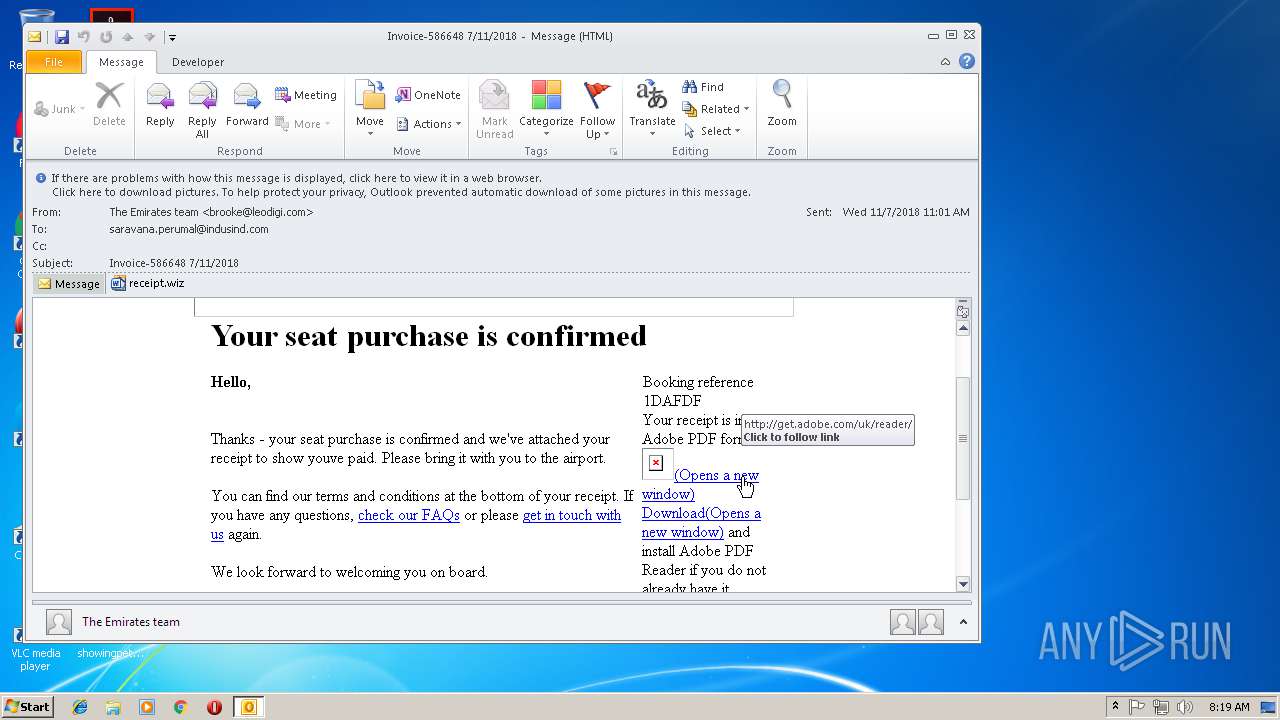
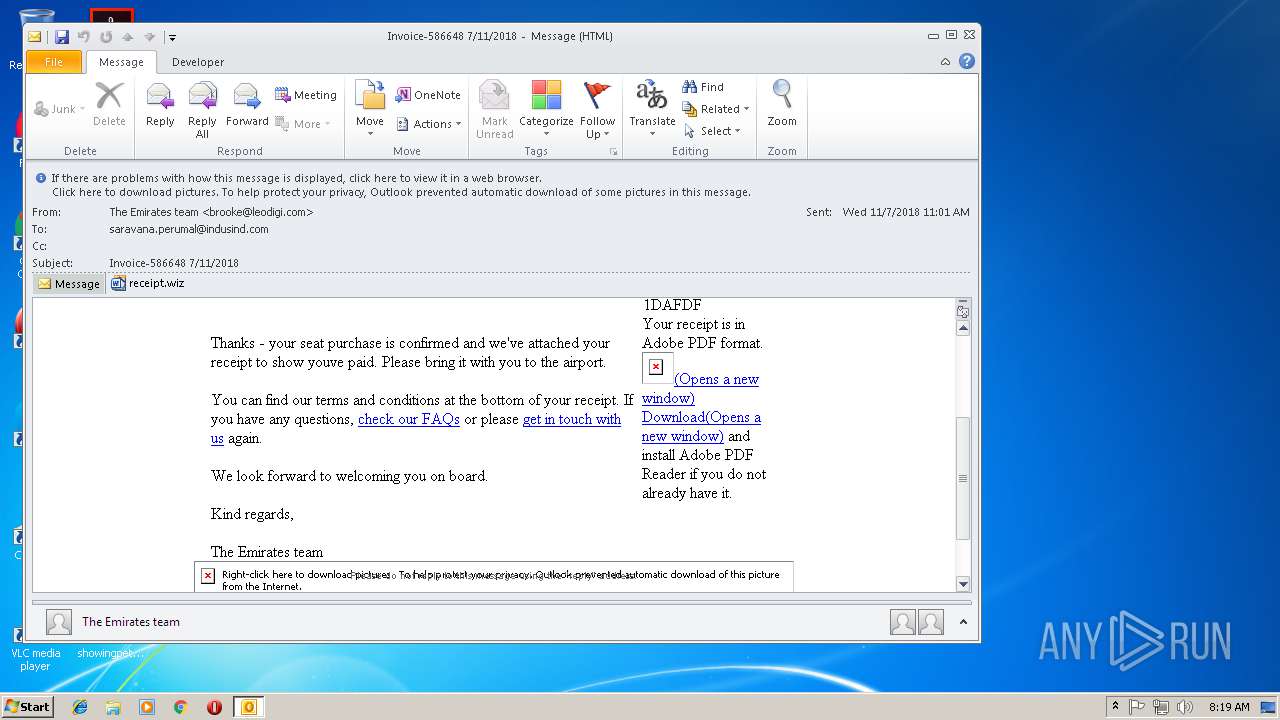
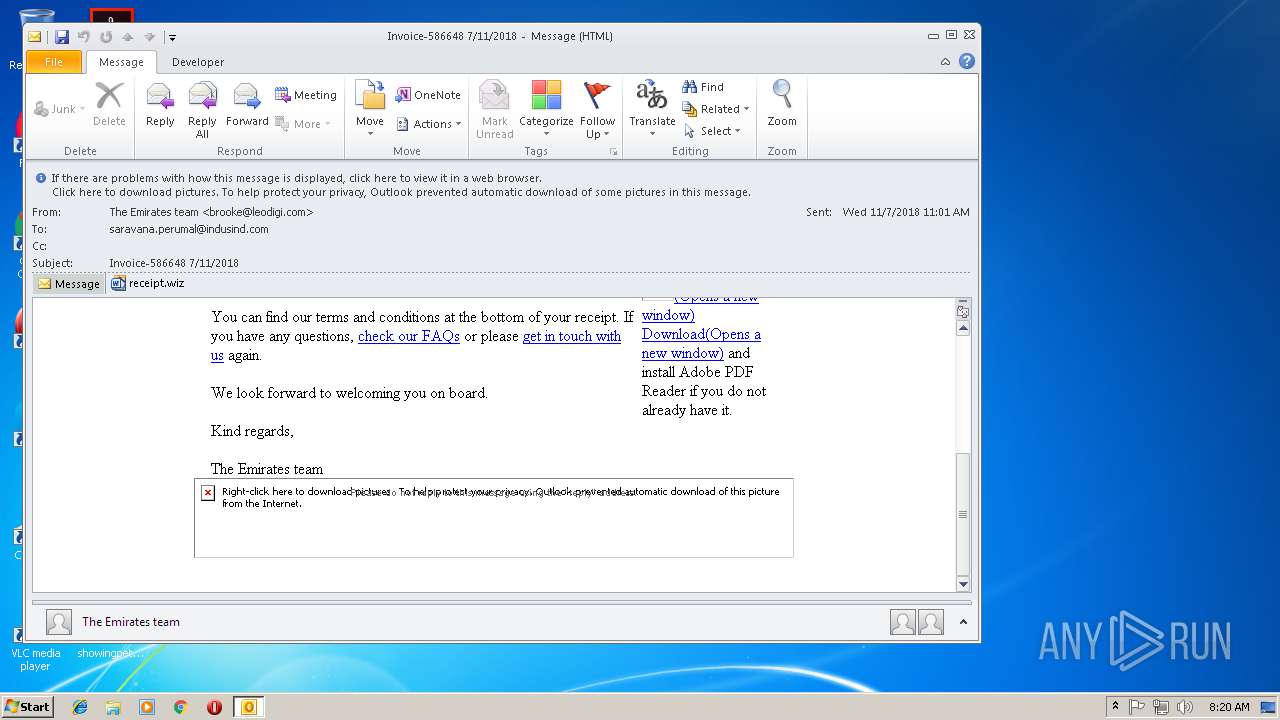
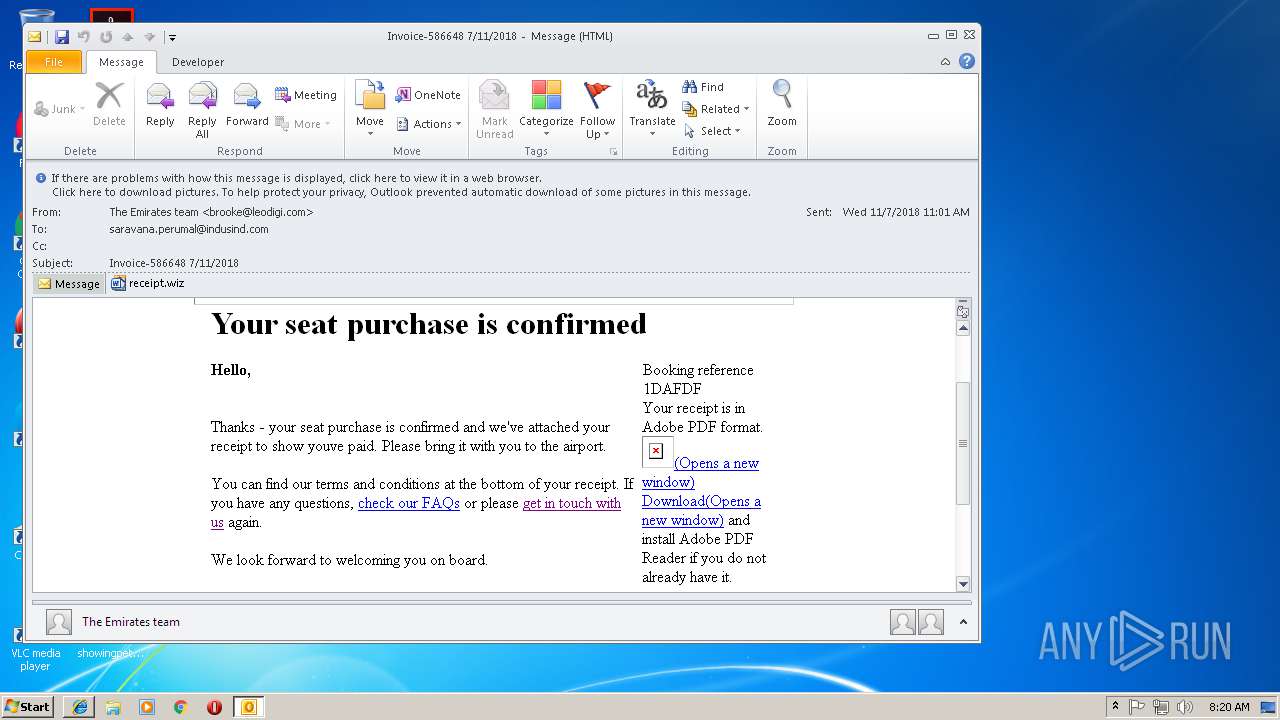
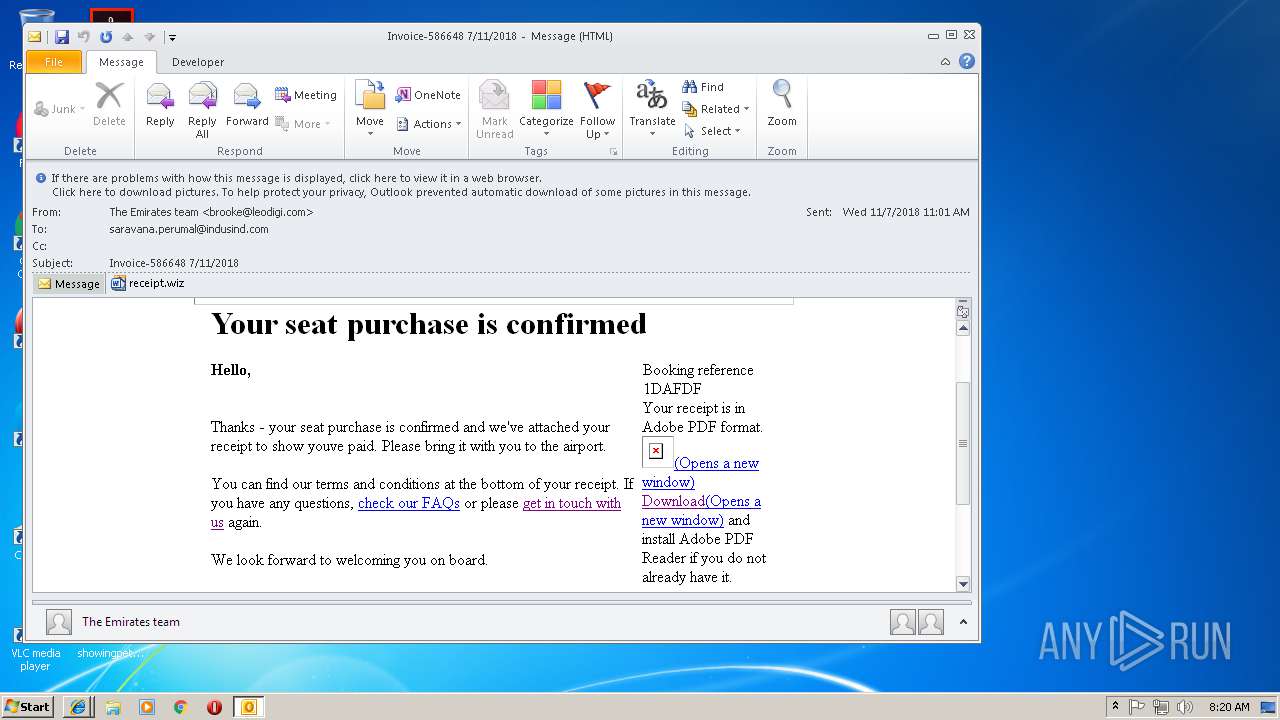
| File name: | 6a4e_8016_421f020c_bd80_4a05_9ddc_5080cfd9198f.eml (71.8 KB).msg |
| Full analysis: | https://app.any.run/tasks/ee142021-049b-4c08-9935-d308adf467d2 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 08:19:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 482AFFA819443F64816BA4B64B22A00A |
| SHA1: | 536BD5EF19B3CFDBB55BF5967BFB8FD52098D0DE |
| SHA256: | 3D7761E9CB3AE42588EE4E7504ED3D4EDE033883E737755762CD122D7778B6C1 |
| SSDEEP: | 1536:xaPWIxyc128S5GxvSt3y83D2hjNxqb8Ni:xaPHxnzKt3R4jXS8N |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3008)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3008)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3008)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3008)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3008)
Changes internet zones settings
- iexplore.exe (PID: 2400)
Application launched itself
- iexplore.exe (PID: 2400)
Reads Internet Cache Settings
- iexplore.exe (PID: 2044)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 3760)
Creates files in the user directory
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2936)
- iexplore.exe (PID: 2044)
- iexplore.exe (PID: 2400)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 3760)
Reads settings of System Certificates
- iexplore.exe (PID: 2044)
- iexplore.exe (PID: 2400)
- iexplore.exe (PID: 3760)
Reads internet explorer settings
- iexplore.exe (PID: 2044)
- iexplore.exe (PID: 3000)
- iexplore.exe (PID: 3760)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2400)
Changes settings of System certificates
- iexplore.exe (PID: 2400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (38.9) |
|---|---|---|
| .oft | | | Outlook Form Template (22.7) |
| .doc | | | Microsoft Word document (17.5) |
| .xls | | | Microsoft Excel sheet (16.4) |
Total processes
39
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2400 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2400 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.emirates.com/system/aspx/link.aspx?id=tcm:233-194385 | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2400 CREDAT:6403 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\6a4e_8016_421f020c_bd80_4a05_9ddc_5080cfd9198f.eml (71.8 KB).msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3760 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2400 CREDAT:6406 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 274
Read events
1 691
Write events
562
Delete events
21
Modification events
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | u}l |
Value: 757D6C00C00B0000010000000000000000000000 | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: C00B0000982C5FCB3B77D40100000000 | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219768480 | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3008) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1298661397 | |||
Executable files
0
Suspicious files
3
Text files
192
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9D45.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2400 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@emirates[2].txt | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\offices[1].txt | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@emirates[1].txt | text | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\747071d1[1] | text | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\responsive-main[1].js | text | |
MD5:— | SHA256:— | |||
| 3008 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3008 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
90
DNS requests
43
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3760 | iexplore.exe | GET | 304 | 184.30.209.229:80 | http://cdn.ek.aero/qubit/opentag-93989-1321710.js | NL | — | — | whitelisted |
3008 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2044 | iexplore.exe | GET | 200 | 184.30.209.229:80 | http://cdn.ek.aero/qubit/opentag-93989-1321710.js | NL | text | 36.3 Kb | whitelisted |
3000 | iexplore.exe | GET | 301 | 193.104.215.66:80 | http://get.adobe.com/uk/reader/ | unknown | html | 244 b | whitelisted |
2044 | iexplore.exe | GET | 200 | 52.222.161.53:80 | http://cdn.appdynamics.com/adrum/adrum-4.5.0.773.js?r=cib-767a | US | text | 23.3 Kb | whitelisted |
3000 | iexplore.exe | GET | 200 | 52.222.163.164:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2400 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3008 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2044 | iexplore.exe | 184.30.209.229:443 | www.emirates.com | Akamai International B.V. | NL | whitelisted |
2400 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2044 | iexplore.exe | 184.30.209.229:80 | www.emirates.com | Akamai International B.V. | NL | whitelisted |
2044 | iexplore.exe | 23.111.8.154:443 | oss.maxcdn.com | netDNA | US | unknown |
2044 | iexplore.exe | 104.111.224.144:443 | libs.de.coremetrics.com | Akamai International B.V. | NL | whitelisted |
2400 | iexplore.exe | 184.30.209.229:443 | www.emirates.com | Akamai International B.V. | NL | whitelisted |
2044 | iexplore.exe | 104.244.46.16:443 | static.ads-twitter.com | Twitter Inc. | US | unknown |
2044 | iexplore.exe | 52.222.173.197:443 | script.crazyegg.com | Amazon.com, Inc. | US | unknown |
2044 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.emirates.com |
| unknown |
www.bing.com |
| whitelisted |
cdn.ek.aero |
| unknown |
oss.maxcdn.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
cdn.appdynamics.com |
| whitelisted |
api.boxever.com |
| unknown |