| URL: | https://www.sharebutton.co |
| Full analysis: | https://app.any.run/tasks/ab4e83b8-8216-4d1f-89d1-859cb903ee94 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 09:58:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C1EC8170888D6A60CA966729FA0552C3 |
| SHA1: | BF5405E96772972900104B5A661DD6DC53808C64 |
| SHA256: | 3D730BCE6CC55B226D217EABEE18F009A13959E287D587EE1F957065959FD49B |
| SSDEEP: | 3:N8DSL7RRKl:2OL7Rsl |
MALICIOUS
Connects to CnC server
- chrome.exe (PID: 356)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 356)
INFO
Application launched itself
- chrome.exe (PID: 356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12409821344159588819 --mojo-platform-channel-handle=5532 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.sharebutton.co | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=2935386745726888837 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2935386745726888837 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2596 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=2821026160076367957 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2821026160076367957 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2696 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --service-pipe-token=12572622948825182206 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12572622948825182206 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1996 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=12616417358777807420 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12616417358777807420 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2732 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1840 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --service-pipe-token=6070717384415034799 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6070717384415034799 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2180 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=12365716441345540533 --mojo-platform-channel-handle=2784 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2840 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,9332770073607561232,3046645075391327176,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=5530053799662343659 --mojo-platform-channel-handle=948 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
573
Read events
476
Write events
92
Delete events
5
Modification events
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 356-13200659922416625 |
Value: 259 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (356) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
98
Text files
140
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b4734bf0-918c-49ec-89a3-d1393bc60ea3.tmp | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 356 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
67
DNS requests
55
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
356 | chrome.exe | GET | 302 | 103.224.212.241:80 | http://park.above.com/jr.php?gz=oq1yWCn1wkGHmlWbzHd1AefgC24OMfHi0YGV%2FaaP1BbJjP7h33ccQyLxsg3WuoZbV3ZZOLrZ%2Fh9LhlX8pwAhrs10KpU4cqnVg62D%2B4FssXRC71%2Fm1GmZGrl6PlhXBP4srFJfCtlMaSlFWtMjYRn44brUG1YJvm%2FdonAEh2Yn9ETxR9Bi45iwps56v7MpZd08TJf1iHZ66FRhA6P8g6sk4S5nHB5g8gRyZYQCq5lQi%2FRP2b3K3CUT9Cu9LofRIZEe2VLfkDKzzxtNIAHsM45TdysF1Al2WZ9kE8nxIuCi3rbJ3xRRKy7Pd4eGLpcDksK8Ebx%2BgtOBytC%2FSrXaPbHZGiiTK88PyfooF%2B36kqU1R7rl0z%2FaowaKYVdnUUj4h03w2P7hIzAnahfw2WEnjTwSPyBDR7k0rq%2B0MUBP8SmC2meYBHHIKtWgWAwEK25xPL2RLtWj1f7tUX%2F8CkNDGZh8kfF%2Bu5xOoO9gJhCpCh2hBfgyst9VGco0%2B52nKph05BdQNluqmQhvI3HZmNamPTmI7qzWzFwZmI4J82MxigbwgioDrhIpPK9dkVjP80ZglVePNuP%2FhAUBMn41pNdAynJVhqTo3y3y9ZDhdig8vismiV6pm7EzqhEPlG9RCNYK%2BJP5Nxiq8JeSBodeZ6vrnuEHDFDFLa6lIFOIVpGBo9haDtjZBXZ4q4L2rA%3D%3D&vs=1280:572&ds=1280:720&sl=0:0&os=f&nos=f&swfV=0.0.0&if=f&sc=f | AU | — | — | whitelisted |
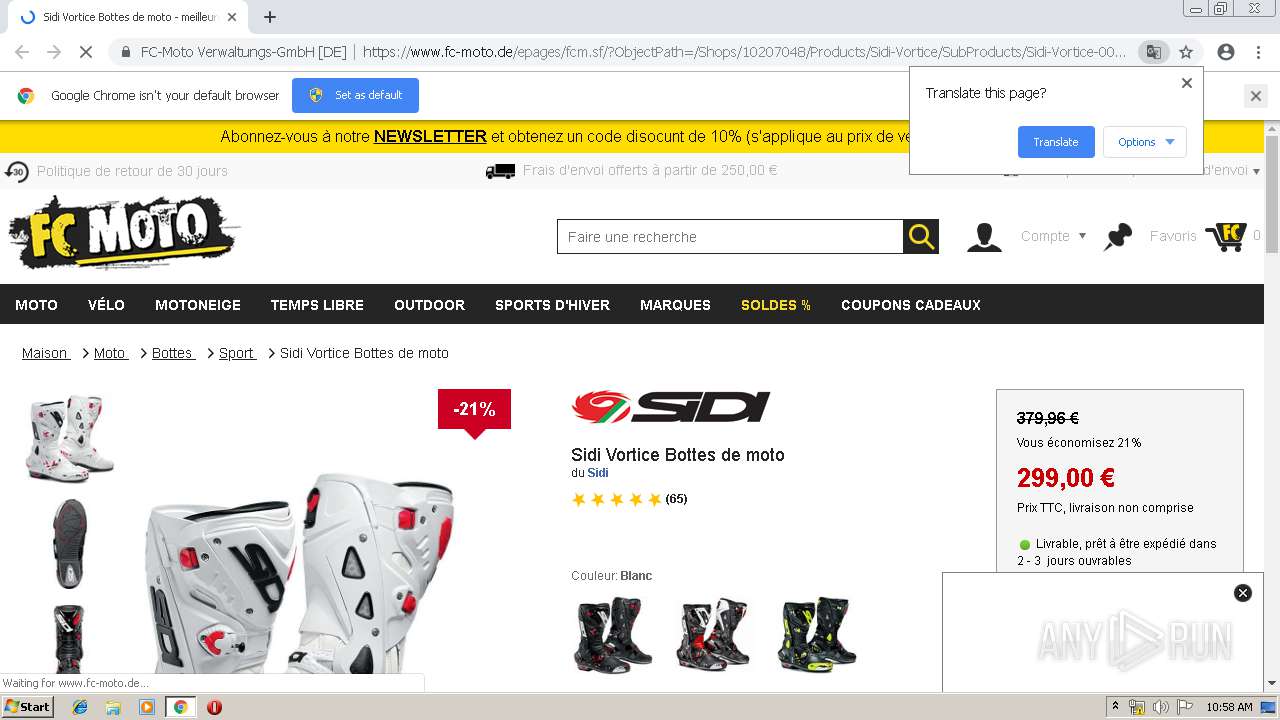
356 | chrome.exe | GET | 302 | 195.78.111.92:80 | http://rd.shopzilla.fr/rd?t=https%3A%2F%2Fwww.fc-moto.de%2Fepages%2Ffcm.sf%2F%3FObjectPath%3D%2FShops%2F10207048%2FProducts%2FSidi-Vortice%2FSubProducts%2FSidi-Vortice-0031%26Currency%3DEUR%26Locale%3Dfr_FR%26utm_source%3Dconnexity%26utm_medium%3Dproductlisting%26utm_campaign%3DCON_FR%26iccm%3DCON_FR&mid=284262&cat_id=100000280&atom=100000289&prod_id=&oid=9706325451&pos=1&b_id=18&bid_type=2&bamt=dd6acf5bafc6003d&ppr=ddb0b49cd234b0c0&rf=af1&af_assettype_id=12&af_creative_id=2974&af_id=616725&af_placement_id=284262&dv=adc7414bbd8e620d89e0174094416ded5339036a24a45188 | GB | — | — | unknown |
356 | chrome.exe | GET | 200 | 103.224.212.241:80 | http://park.above.com/jr.php?gz=oq1yWCn1wkGHmlWbzHd1AefgC24OMfHi0YGV%2FaaP1BbJjP7h33ccQyLxsg3WuoZbV3ZZOLrZ%2Fh9LhlX8pwAhrs10KpU4cqnVg62D%2B4FssXRC71%2Fm1GmZGrl6PlhXBP4srFJfCtlMaSlFWtMjYRn44brUG1YJvm%2FdonAEh2Yn9ETxR9Bi45iwps56v7MpZd08TJf1iHZ66FRhA6P8g6sk4S5nHB5g8gRyZYQCq5lQi%2FRP2b3K3CUT9Cu9LofRIZEe2VLfkDKzzxtNIAHsM45TdysF1Al2WZ9kE8nxIuCi3rbJ3xRRKy7Pd4eGLpcDksK8Ebx%2BgtOBytC%2FSrXaPbHZGiiTK88PyfooF%2B36kqU1R7rl0z%2FaowaKYVdnUUj4h03w2P7hIzAnahfw2WEnjTwSPyBDR7k0rq%2B0MUBP8SmC2meYBHHIKtWgWAwEK25xPL2RLtWj1f7tUX%2F8CkNDGZh8kfF%2Bu5xOoO9gJhCpCh2hBfgyst9VGco0%2B52nKph05BdQNluqmQhvI3HZmNamPTmI7qzWzFwZmI4J82MxigbwgioDrhIpPK9dkVjP80ZglVePNuP%2FhAUBMn41pNdAynJVhqTo3y3y9ZDhdig8vismiV6pm7EzqhEPlG9RCNYK%2BJP5Nxiq8JeSBodeZ6vrnuEHDFDFLa6lIFOIVpGBo9haDtjZBXZ4q4L2rA%3D%3D&vs=1280%3A572&ds=1280%3A720&sl=0%3A0&os=f&nos=f&swfV=0.0.0&if=f&sc=f&ckReS=1556186326.2346169 | AU | html | 254 b | whitelisted |
356 | chrome.exe | GET | 200 | 66.165.243.151:80 | http://r.ealeo.com/go?e=NA-pFFutFr9blF9xmX7tQM9AUsW13FvZ2XyjQL8uFr5bFWv8SsuMPLeHPCt13F90Gr_xUCuHPCwkKL0OJsuIaBeHPBsgvq9cws2k3L-IPAt53pjyHsmE3FeHPAw1KL55Gr_xaCutFBsImqjI2rXuTFdxFrQgaC1cmZvgFC75GsUAQWbWRA6DTFlpUpjfvLNu2ZvEKF2pFAmAmB1WzZsIQrmtFFcblCOu3XmIKpetlX_VlF49IWsOzCxLUCVuvW1tFryxaqdtFqvjaW5cQW-RxV9STBYkKL9gwWc0Qs2pKs_jUL1N2ZtSxBafGsltPCbkUA9NHC8kmXN5aWWO0Z1umL0pKAkWmq5gRsyR3r0HaWscvL1M0W-DGL8kwV9jUC491V_03FbHKrm13F01Qs8fFE8MFASuPC1b0ZmgvVmLKBdVFCj9SAvyaqx4mXmIwqW1aXa0UEw0GAsIPXOgvW-Z2K9MKrXqvW0xRXzRHLmDvWXAvCwp0Z8HKqlZKreZmB9H3W3yQW-MFrO13paRHAvS3F9IlXu13KtuRX-VPF-I3V6glB1SRW1OHL9kmXxVQq0SzWmymC99GsQ1Kq8O2Z8xwp9uPAwgPL5ETX90mVvVTqtAGq1SHryxaqz0QpXclB9gUss13WaZKCmIGW9j3ZugPWxpFD1gFW5uFW2glDwDKEyMmC58IW80GpxpKs913paLlX31mFwfGqkAmp5yPX70mDwHFBTMQq9NzVukmF04Gr6kaL5DvW8HRM9OJp80aqapKW3S3BwLKEYElF5HaX_tGC8kGr_HQqbWaAcZlp5IFr2MvL5cvXaRaBxHKD3WQX9LPWYumLzpKC-ZGLbMKryxap8g0XQEmWzxxW7HwFmZKpyyKW5MaXbtzLdLFEepvCwL0WapvD9MUBVkaL0bxWmIQDxxFDkAwC1O0X_DwFa81WTWGCwVzWtSUMvjmVx0KLRuRA_DKC8kQrVIlWaVaWmyGWmLPsXAQXafvV8xQrxLFEsqFL1xvVcHGqxfRrtMGqkkUs9xUs1HKAPkUXdVJA1qvX5IFr25Uq9AHW8Zlqb4QBwWGLeLKryxap1HlWwIFLbSvsbHwrlDKsVWFL4bxZ0yaCeVJCYImp9tlVu13E8WaWXWlBzb0Z8HRFlZUptWvCwZFW-xRL0tPLwVmqexUssywZmLPM5ZmWkMlZzjwL0xFDcLQCeVTX-NJr9EUDwkUCtAzZbHwB1RJAOAmKwbxZ01QFzDUExgvqSuvZ9N3L8IKD_ZGqe0wW0ETLzVaWXAvC5R3WzxKsmfwVWEQqxkwVc0wEx0mXNEmWwpRsvkmF2HFClZvq5jwZbDmL14GCYAQX9tFs_RKE991WyEQX5HaW2y0q-qFrmIFC9fKryxapx0QptIlC5RRAyxwrepFslAGLw0QX7fFL04QMtAvW5D3V8ZvqyLUquAQq9LKWs1QX0DKAlAmF9NxXzZlKl0GDluFqN9SAyZPs89GrkyKW9EKry0Uq59mXYSFW0cxsmOKC89Sqt13F45mX3kUn8IPrwkapzfxVyDwF8W3XYAmpsuHry0Kp8W3XUEmFt5Gr-D2E0fRL-x3C9W2X9bPn8W3LVg3Bj5wZbbPnebmXYclFt5Gr-03Dz4mWyRFW0OJsybFF-AaXYk3BdLRs7j3K9gQqu5UWeLHVytUM-AUpX13FzbRsmcvCdRTEbAmCaD0ZlgvE0V2VXSFW4yHr-NTC9yFssEmBsgxXYMPMeLUsV13p50wsmuQL8AUrskKL51wsmOaL-uPqtclF081XmOaL-ElXYcvL5WJVyDaF-AUp-DGL9cxZm9SL9gRr-Hmpt9SA_pFC | US | html | 2.04 Kb | shared |
356 | chrome.exe | GET | 200 | 195.78.111.103:80 | http://rd2szfr.bizrate.com/rd?t=https%3A%2F%2Fwww.fc-moto.de%2Fepages%2Ffcm.sf%2F%3FObjectPath%3D%2FShops%2F10207048%2FProducts%2FSidi-Vortice%2FSubProducts%2FSidi-Vortice-0031%26Currency%3DEUR%26Locale%3Dfr_FR%26utm_source%3Dconnexity%26utm_medium%3Dproductlisting%26utm_campaign%3DCON_FR%26iccm%3DCON_FR&mid=284262&cat_id=100000280&atom=100000289&prod_id=&oid=9706325451&pos=1&b_id=18&bid_type=2&bamt=dd6acf5bafc6003d&ppr=ddb0b49cd234b0c0&rf=af1&af_assettype_id=12&af_creative_id=2974&af_id=616725&af_placement_id=284262&dv=adc7414bbd8e620d89e0174094416ded5339036a24a45188&rdrSerial=a681df52-7aae-42e1-9954-eb2ea2be454c | GB | html | 512 b | unknown |
356 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA0HeCoTP8b5pXKW4TH%2F0Xk%3D | US | der | 471 b | whitelisted |
356 | chrome.exe | GET | 302 | 172.217.18.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
356 | chrome.exe | GET | 200 | 173.194.164.140:80 | http://r6---sn-4g5e6nle.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.217.119.8&mm=28&mn=sn-4g5e6nle&ms=nvh&mt=1556186265&mv=m&pl=24&shardbypass=yes | US | crx | 842 Kb | whitelisted |
356 | chrome.exe | GET | 200 | 66.165.243.151:80 | http://r.ealeo.com/favicon.ico | US | html | 2.04 Kb | shared |
356 | chrome.exe | GET | 200 | 8.248.119.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
356 | chrome.exe | 54.230.93.148:443 | cdn.scarabresearch.com | Amazon.com, Inc. | US | unknown |
356 | chrome.exe | 54.230.93.61:443 | widget.trustpilot.com | Amazon.com, Inc. | US | unknown |
356 | chrome.exe | 172.217.16.194:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
356 | chrome.exe | 172.217.22.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
356 | chrome.exe | 103.224.182.250:443 | www.sharebutton.co | Trellian Pty. Limited | AU | unknown |
356 | chrome.exe | 103.224.212.241:80 | park.above.com | Trellian Pty. Limited | AU | unknown |
356 | chrome.exe | 172.217.22.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
356 | chrome.exe | 195.78.111.92:80 | rd.shopzilla.fr | Shopzilla Europe Ltd | GB | unknown |
356 | chrome.exe | 195.78.111.103:80 | rd2szfr.bizrate.com | Shopzilla Europe Ltd | GB | unknown |
356 | chrome.exe | 66.165.243.151:80 | r.ealeo.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.sharebutton.co |
| suspicious |
accounts.google.com |
| shared |
park.above.com |
| whitelisted |
r.ealeo.com |
| unknown |
api.adrenalads.com |
| unknown |
www.google-analytics.com |
| whitelisted |
rd.shopzilla.fr |
| unknown |
rd2szfr.bizrate.com |
| unknown |
www.fc-moto.de |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
356 | chrome.exe | A Network Trojan was detected | ET CNC Ransomware Tracker Reported CnC Server group 1 |