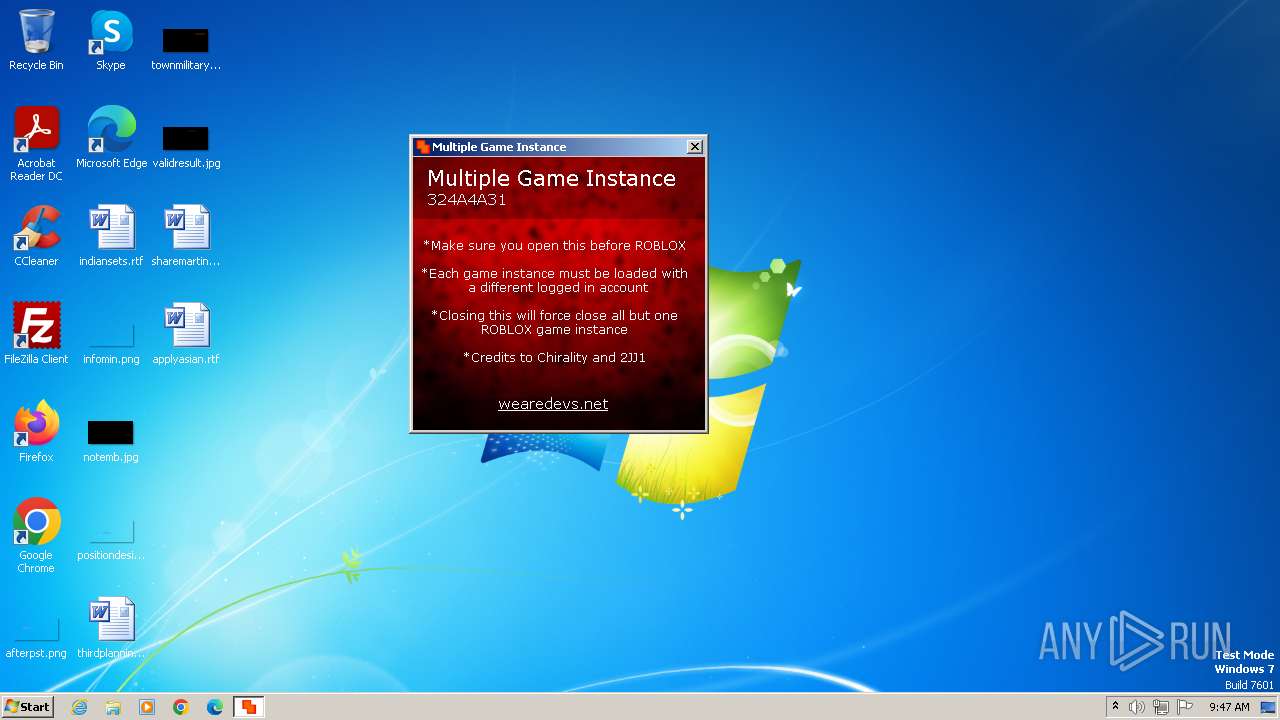
| File name: | Multiple_ROBLOX.exe |
| Full analysis: | https://app.any.run/tasks/7b6193f0-43ea-48e6-8d74-bba3a7e604db |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2023, 09:47:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | AED655395747A6602479F6032D3C099F |
| SHA1: | 5FCBD5735ED0E4A013667652F4C1382ABB45203A |
| SHA256: | 3D6123DC6FFBD1A11D73229988203052809BD17617B24A034C1122C8F4983DB4 |
| SSDEEP: | 6144:PIUUUFEiCVrw4RVJsp0oFP+dkM+i1g0UhCVrw4RuJsp0oFP+dkM+i1g0Uc:PB3gWCEBg5CE8 |
MALICIOUS
Drops the executable file immediately after the start
- CCleaner.exe (PID: 3072)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3072)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 3072)
SUSPICIOUS
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 3072)
Reads settings of System Certificates
- CCleaner.exe (PID: 3072)
Searches for installed software
- CCleaner.exe (PID: 3072)
Application launched itself
- CCleaner.exe (PID: 2848)
Reads the Internet Settings
- CCleaner.exe (PID: 2848)
- CCleaner.exe (PID: 3072)
Checks Windows Trust Settings
- CCleaner.exe (PID: 3072)
Reads Internet Explorer settings
- CCleaner.exe (PID: 3072)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 3072)
INFO
Manual execution by a user
- CCleaner.exe (PID: 2848)
- wmpnscfg.exe (PID: 1380)
Checks supported languages
- Multiple_ROBLOX.exe (PID: 2876)
- CCleaner.exe (PID: 2848)
- CCleaner.exe (PID: 3072)
- wmpnscfg.exe (PID: 1380)
Reads the computer name
- Multiple_ROBLOX.exe (PID: 2876)
- CCleaner.exe (PID: 2848)
- CCleaner.exe (PID: 3072)
- wmpnscfg.exe (PID: 1380)
Reads Environment values
- CCleaner.exe (PID: 3072)
- CCleaner.exe (PID: 2848)
Reads the machine GUID from the registry
- Multiple_ROBLOX.exe (PID: 2876)
- CCleaner.exe (PID: 3072)
- wmpnscfg.exe (PID: 1380)
Reads product name
- CCleaner.exe (PID: 3072)
Reads CPU info
- CCleaner.exe (PID: 3072)
Creates files in the program directory
- CCleaner.exe (PID: 3072)
Creates files or folders in the user directory
- CCleaner.exe (PID: 3072)
Checks proxy server information
- CCleaner.exe (PID: 3072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:12:07 04:55:10+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 409088 |
| InitializedDataSize: | 372736 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x65cfe |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Multiple ROBLOX |
| FileVersion: | 1.0.0.0 |
| InternalName: | Multiple ROBLOX.exe |
| LegalCopyright: | Copyright © 2016 |
| LegalTrademarks: | - |
| OriginalFileName: | Multiple ROBLOX.exe |
| ProductName: | Multiple ROBLOX |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
44
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1380 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 2876 | "C:\Users\admin\AppData\Local\Temp\Multiple_ROBLOX.exe" | C:\Users\admin\AppData\Local\Temp\Multiple_ROBLOX.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Multiple ROBLOX Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3072 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
Total events
16 115
Read events
15 941
Write events
121
Delete events
53
Modification events
| (PID) Process: | (2848) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3072) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | DAST |
Value: 07/06/2023 15:07:35 | |||
| (PID) Process: | (3072) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | T8062 |
Value: 1 | |||
| (PID) Process: | (3072) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 0 | |||
| (PID) Process: | (3072) CCleaner.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3072) CCleaner.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | SystemRestorePointCreationFrequency |
Value: 0 | |||
| (PID) Process: | (3072) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | FTU |
Value: 02/11/2020|9|1 | |||
Executable files
3
Suspicious files
26
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3072 | CCleaner.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F637D5D3C3A60FDDB5DD397556FE9B1D | SHA256:641B843CB6EE7538EC267212694C9EF0616B9AC9AB14A0ABD7CF020678D50B02 | |||
| 3072 | CCleaner.exe | C:\Program Files\CCleaner\gcapi_17009920493072.dll | executable | |
MD5:F637D5D3C3A60FDDB5DD397556FE9B1D | SHA256:641B843CB6EE7538EC267212694C9EF0616B9AC9AB14A0ABD7CF020678D50B02 | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ed7a5cc3cca8d52a.customDestinations-ms | binary | |
MD5:66A01DAA2E03B7F3BC291204D8D4C5EC | SHA256:3F2B8DFA9B9C7E097536D2D10A1945A1D25E86B4AB6BAF0B34A58B122FF79BC8 | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:037AE8164352CA91E80AD33054D1906D | SHA256:07C018EB07002663D5248DAA8A65EAF587955E3DB45735E7E3AC9CB13D7D664E | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:8F1057DC194EF891FF8B7666146C2C7E | SHA256:A41C669A11552272176A6B64B59EEA6E615CCF29AD68B06A495DB45F5FB2FFCB | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\18VVYN75K3Z0N7P80YUH.temp | binary | |
MD5:66A01DAA2E03B7F3BC291204D8D4C5EC | SHA256:3F2B8DFA9B9C7E097536D2D10A1945A1D25E86B4AB6BAF0B34A58B122FF79BC8 | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:32D18A6D2E20A1CB547501DF41221A4F | SHA256:136A60CB0CD229CB319E46D9904E6E3E227612C0A32AA12C125A655617C3A7B1 | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:D9CB9BA8CA8A50EDD32452F08C0031A8 | SHA256:1CE6A2895E80D095F37D0BD79DB38CC4FA7BC1E38F02F0DA7D348C7FE550EEC0 | |||
| 3072 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C35FF021F54C8E12643FC011A0DD1864_4373F076AA98CFDF5460D564DECA51C0 | binary | |
MD5:E1B3336F8C0828C1A119DF604ED614B2 | SHA256:5505CD43E9C335165AAB5114CC8DD2BCEE7DE682B9E0DA34C7ADA3C23AE28A93 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
22
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3072 | CCleaner.exe | GET | 200 | 2.22.242.105:80 | http://ncc.avast.com/ncc.txt | unknown | text | 26 b | unknown |
3072 | CCleaner.exe | GET | 200 | 8.241.122.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3a66026fd093380d | unknown | compressed | 4.66 Kb | unknown |
3072 | CCleaner.exe | GET | 200 | 8.241.122.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4008a18164441107 | unknown | compressed | 4.66 Kb | unknown |
3072 | CCleaner.exe | GET | 200 | 8.241.122.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c22e6b2005d70fb1 | unknown | compressed | 4.66 Kb | unknown |
3072 | CCleaner.exe | GET | 200 | 8.241.122.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?06ca94e53c833f00 | unknown | compressed | 4.66 Kb | unknown |
1080 | svchost.exe | GET | 304 | 8.241.122.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?20da42ca9bb40799 | unknown | — | — | unknown |
3072 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3072 | CCleaner.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3072 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
3072 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/s/gts1d4/VcE3oVK8Y7w/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQCazWGSsgPbSQnI0sPJ6DzW | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3072 | CCleaner.exe | 2.22.242.105:80 | ncc.avast.com | Akamai International B.V. | DE | unknown |
3072 | CCleaner.exe | 34.117.223.223:443 | analytics.ff.avast.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3072 | CCleaner.exe | 34.149.149.62:443 | ip-info.ff.avast.com | GOOGLE | US | unknown |
3072 | CCleaner.exe | 34.111.24.1:443 | ipm-provider.ff.avast.com | GOOGLE | US | unknown |
3072 | CCleaner.exe | 34.160.176.28:443 | shepherd.ff.avast.com | GOOGLE | US | unknown |
3072 | CCleaner.exe | 23.35.237.21:443 | www.ccleaner.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ipmcdn.avast.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CCleaner.exe | [2023-11-26 09:47:29.203] [error ] [settings ] [ 3072: 824] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | [2023-11-26 09:47:29.891] [error ] [settings ] [ 3072: 3188] [9434E9: 359] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2023-11-26 09:47:29.906] [error ] [Burger ] [ 3072: 3188] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | [2023-11-26 09:47:29.906] [error ] [Burger ] [ 3072: 3188] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|