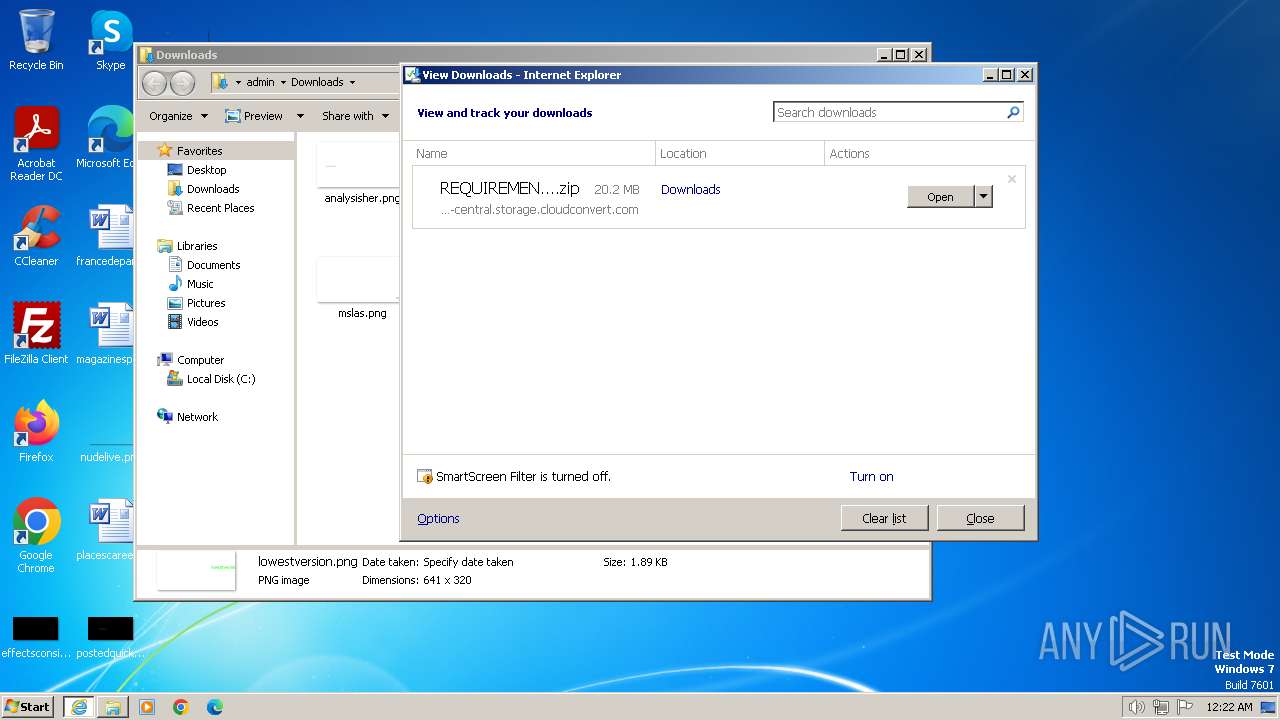
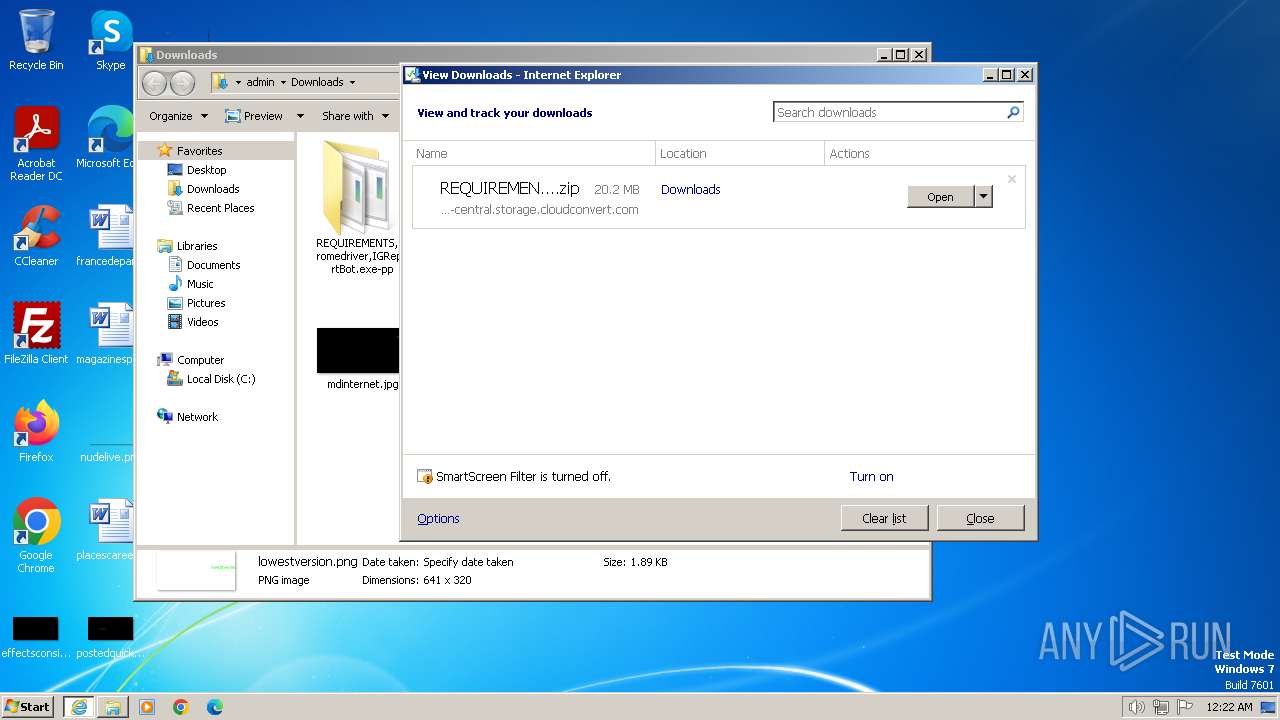
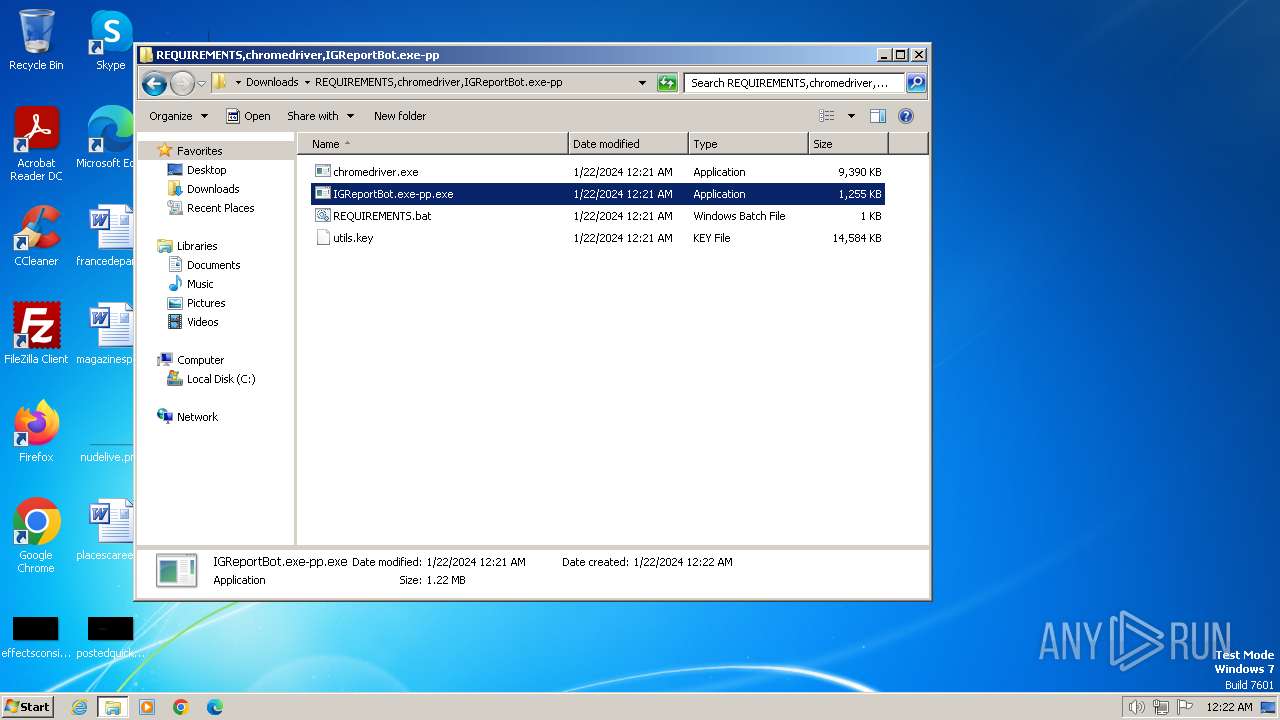
| URL: | https://eu-central.storage.cloudconvert.com/tasks/c41fe965-9cfb-4f09-9543-6746a4a73795/REQUIREMENTS%2Cchromedriver%2CIGReportBot.exe-pp.zip?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Content-Sha256=UNSIGNED-PAYLOAD&X-Amz-Credential=cloudconvert-production%2F20240122%2Ffra%2Fs3%2Faws4_request&X-Amz-Date=20240122T002109Z&X-Amz-Expires=86400&X-Amz-Signature=01479c988d43f45e0a7f305f98089aa60050687b13e5ecbd6038b635504d28b7&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3B%20filename%3D%22REQUIREMENTS%2Cchromedriver%2CIGReportBot.exe-pp.zip%22&response-content-type=application%2Fzip&x-id=GetObject |
| Full analysis: | https://app.any.run/tasks/cddb5240-5a2e-4115-a2d3-ca4b0f1decd4 |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2024, 00:21:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 91D6C6ECE3854D6A5F9945B983DE25DC |
| SHA1: | FC580161491EDA798E8E92ED431C7E677702E0C6 |
| SHA256: | 3D5AC35917A1C541CBE1B61FCBD842EC739E24651B1E3A348FA06CB0B4D6D4EB |
| SSDEEP: | 12:2mFFmoPHpe5DVWQLvttru8JHgABRCmVyD6TUte5DVWwLVnnlR84G:2lvP5rJHnimGyUkPNxnL84G |
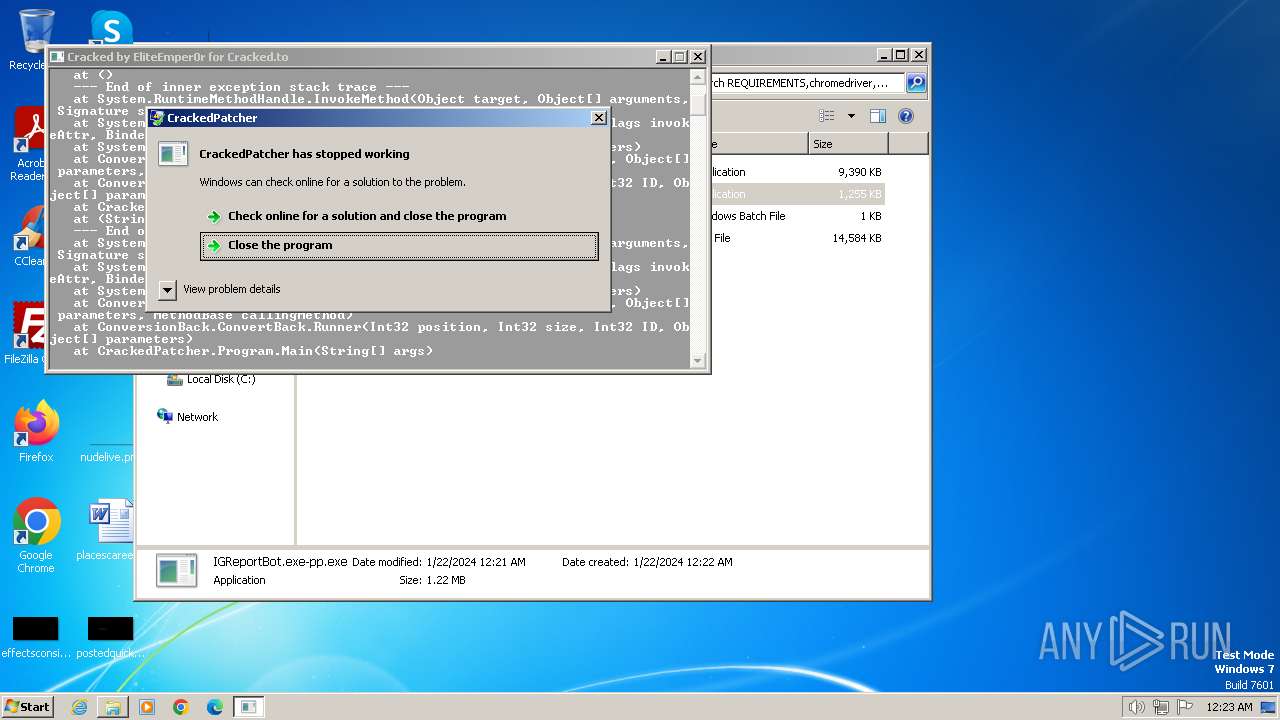
MALICIOUS
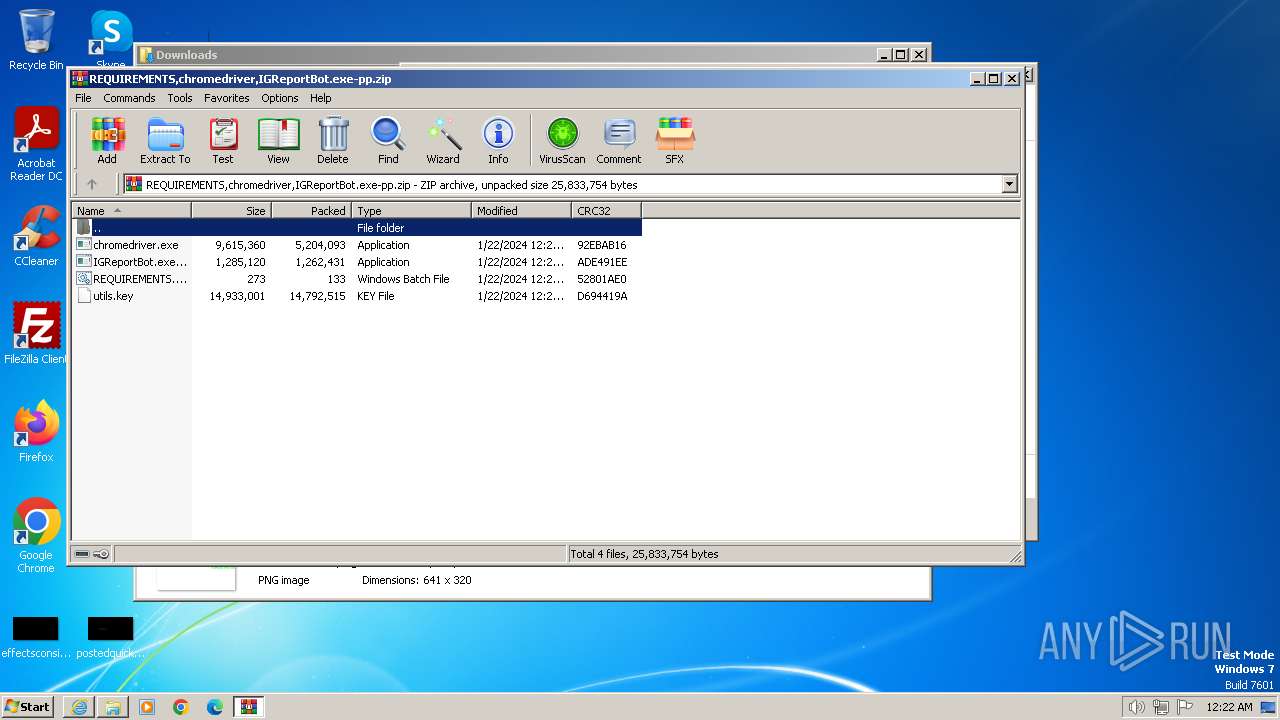
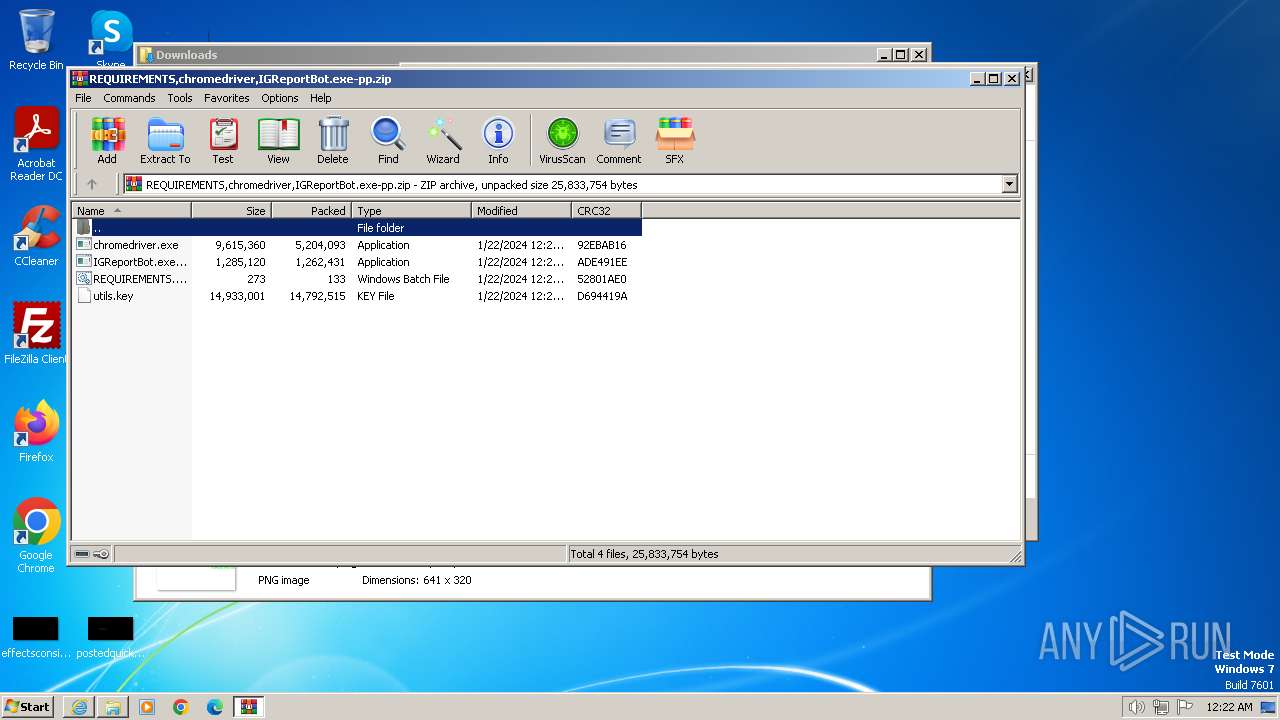
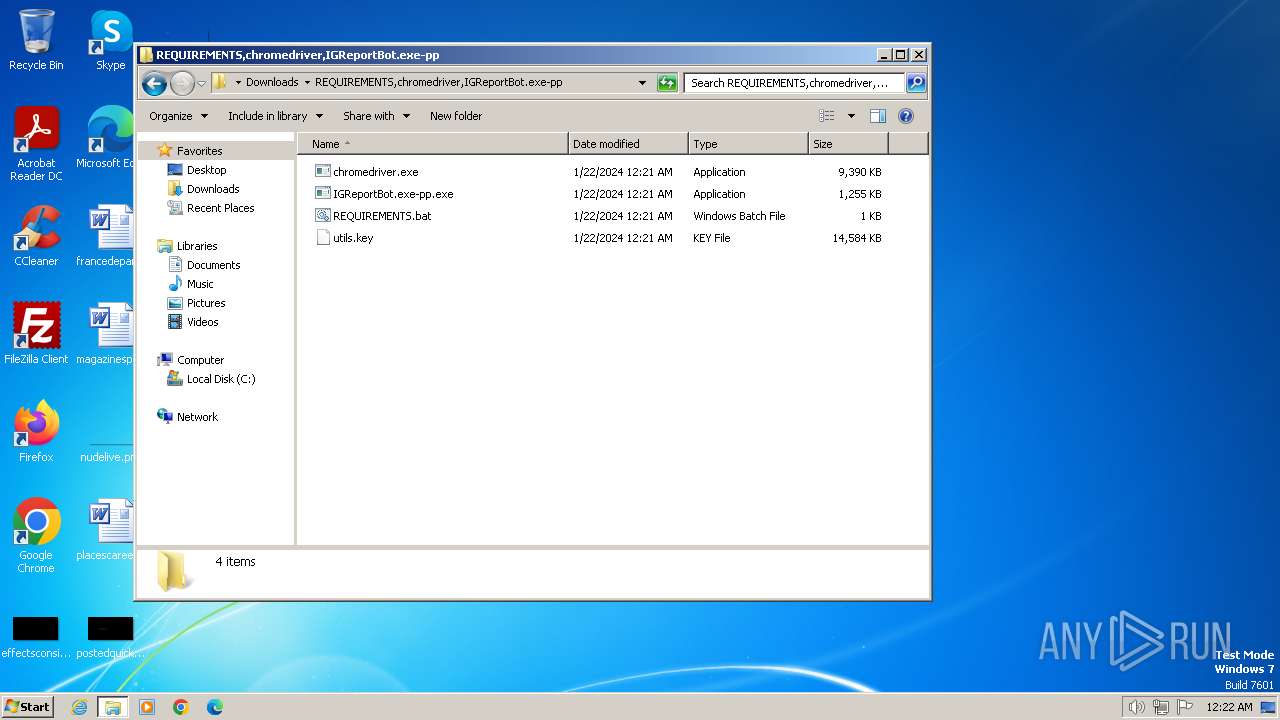
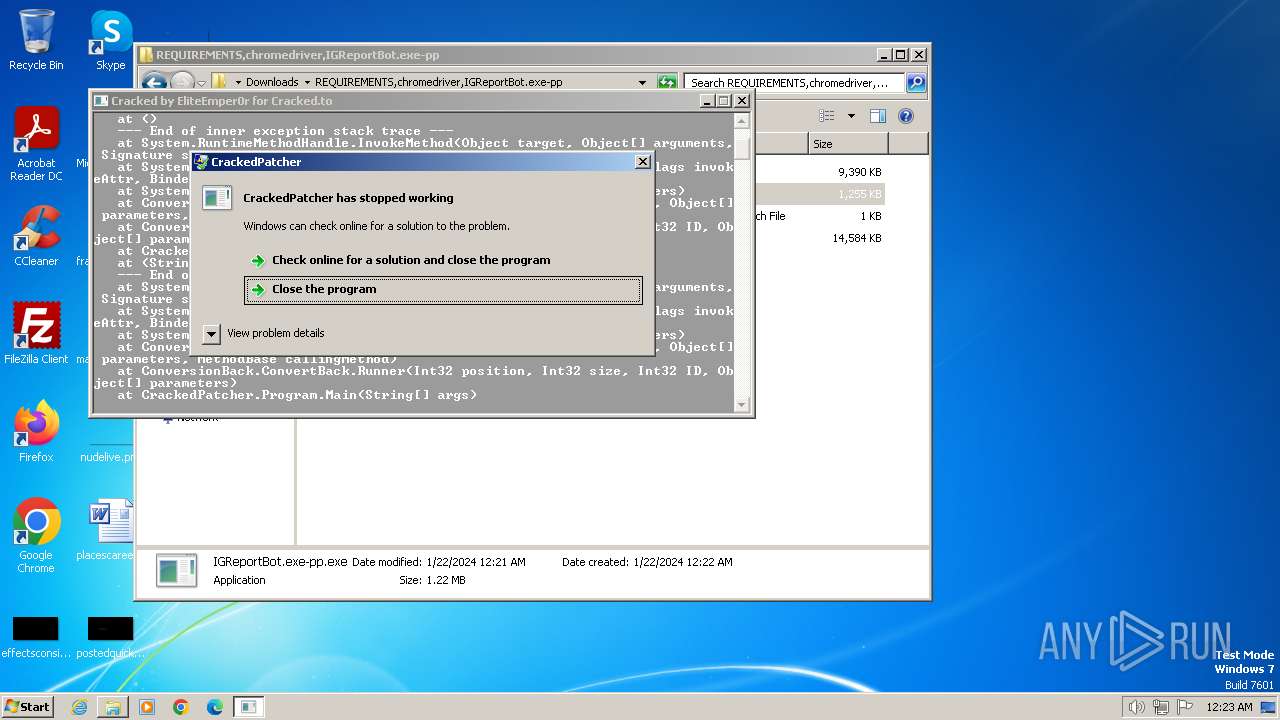
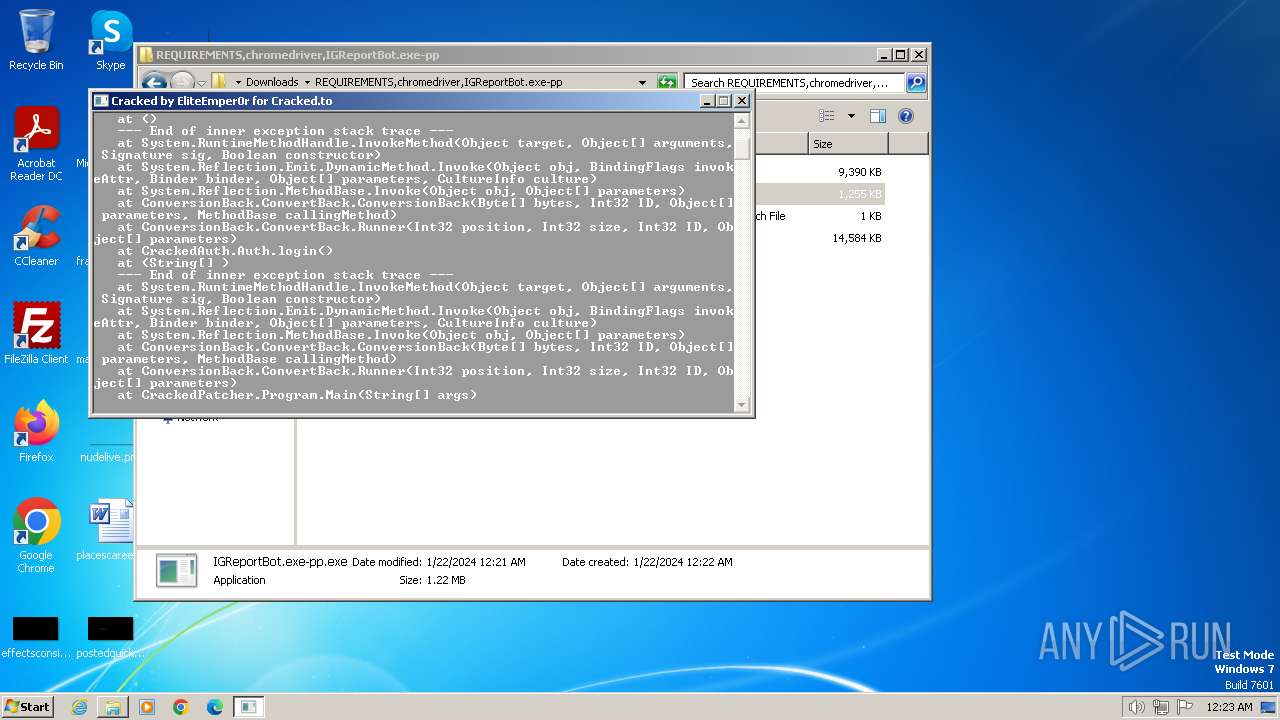
Drops the executable file immediately after the start
- IGReportBot.exe-pp.exe (PID: 2388)
SUSPICIOUS
Executable content was dropped or overwritten
- IGReportBot.exe-pp.exe (PID: 2388)
Reads the Internet Settings
- IGReportBot.exe-pp.exe (PID: 2388)
- IGReportBot.exe-pp.exe (PID: 3112)
- IGReportBot.exe-pp.exe (PID: 900)
INFO
Application launched itself
- iexplore.exe (PID: 2184)
The process uses the downloaded file
- WinRAR.exe (PID: 2348)
- iexplore.exe (PID: 2184)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2348)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2348)
Checks supported languages
- IGReportBot.exe-pp.exe (PID: 2388)
- chromedriver.exe (PID: 2544)
- IGReportBot.exe-pp.exe (PID: 3112)
- IGReportBot.exe-pp.exe (PID: 900)
Reads the computer name
- IGReportBot.exe-pp.exe (PID: 2388)
- IGReportBot.exe-pp.exe (PID: 900)
- IGReportBot.exe-pp.exe (PID: 3112)
- chromedriver.exe (PID: 2544)
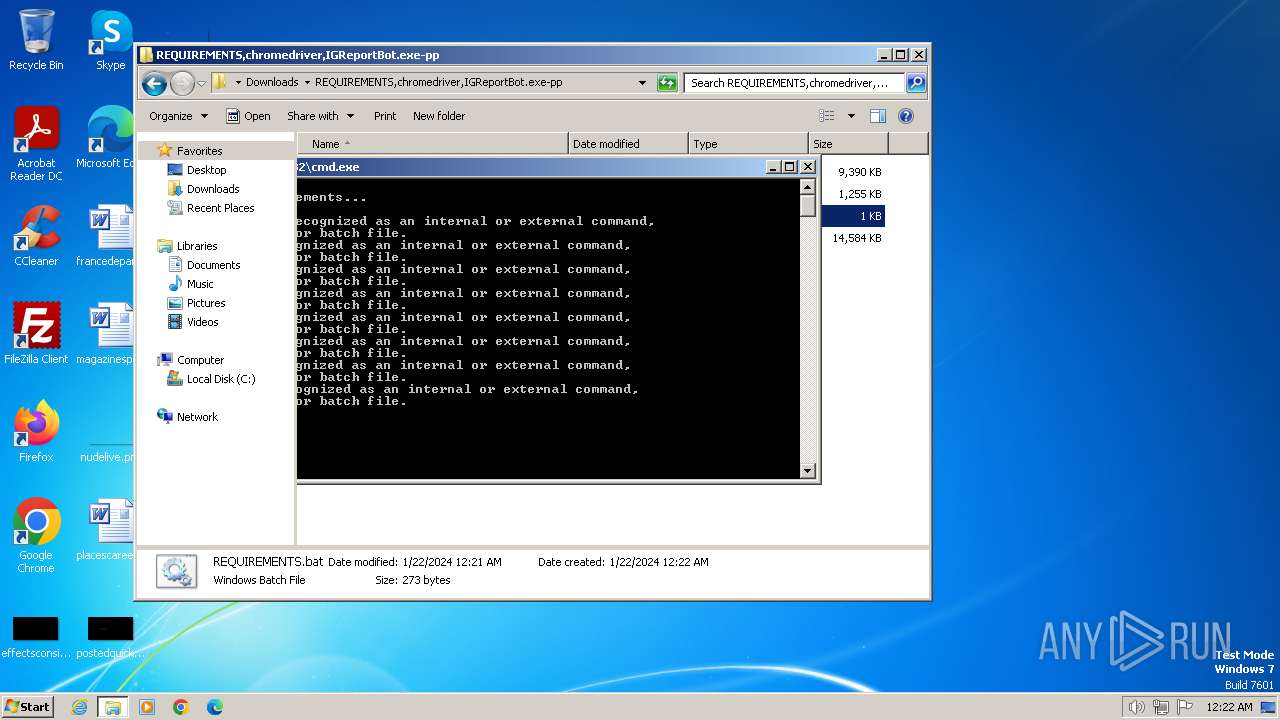
Manual execution by a user
- cmd.exe (PID: 2404)
- IGReportBot.exe-pp.exe (PID: 2388)
- chromedriver.exe (PID: 2544)
- IGReportBot.exe-pp.exe (PID: 3112)
- cmd.exe (PID: 3212)
- IGReportBot.exe-pp.exe (PID: 900)
Create files in a temporary directory
- IGReportBot.exe-pp.exe (PID: 2388)
Reads the machine GUID from the registry
- IGReportBot.exe-pp.exe (PID: 2388)
- IGReportBot.exe-pp.exe (PID: 900)
- IGReportBot.exe-pp.exe (PID: 3112)
Reads Environment values
- IGReportBot.exe-pp.exe (PID: 2388)
- IGReportBot.exe-pp.exe (PID: 900)
- IGReportBot.exe-pp.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
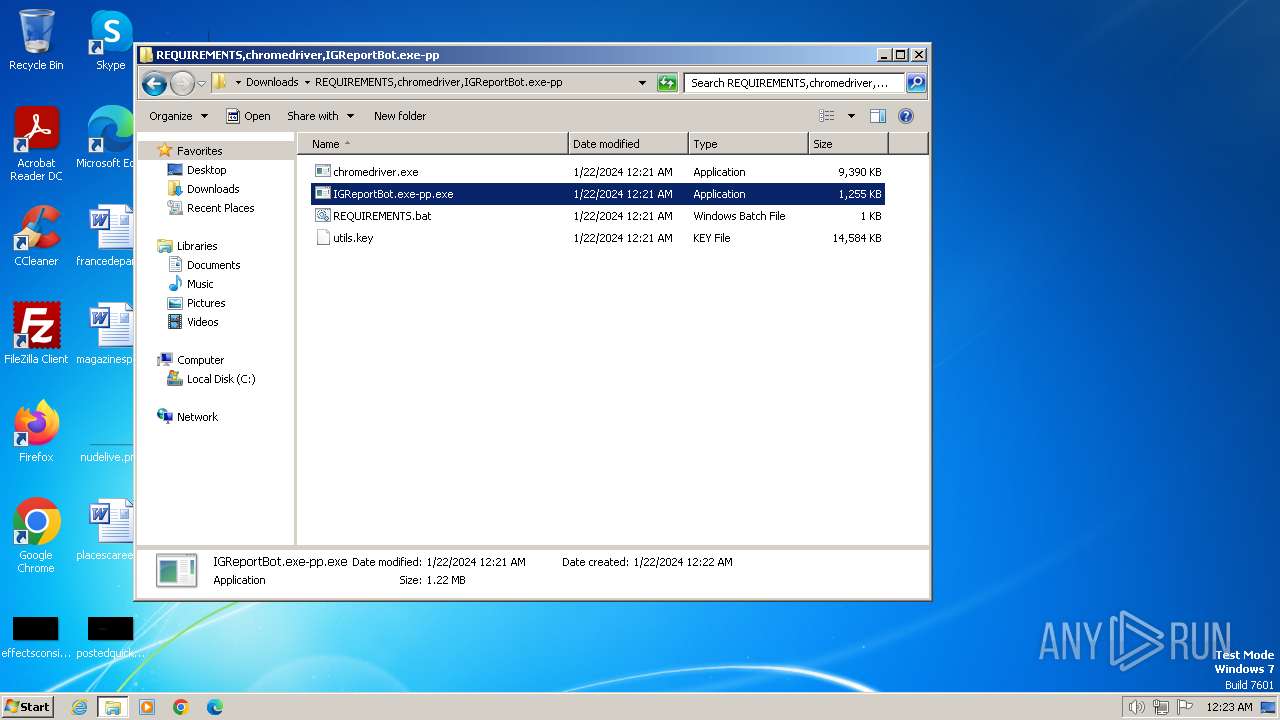
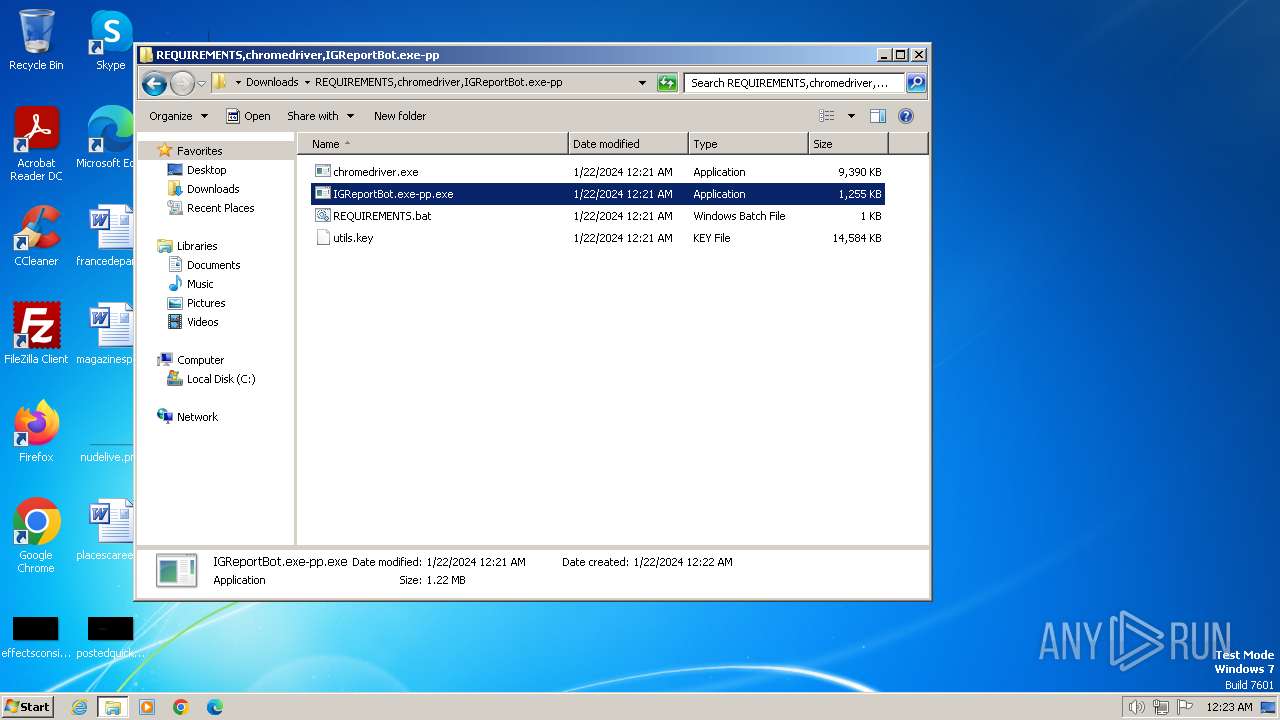
| 900 | "C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\IGReportBot.exe-pp.exe" | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\IGReportBot.exe-pp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: CrackedPatcher Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2184 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1832 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://eu-central.storage.cloudconvert.com/tasks/c41fe965-9cfb-4f09-9543-6746a4a73795/REQUIREMENTS%2Cchromedriver%2CIGReportBot.exe-pp.zip?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Content-Sha256=UNSIGNED-PAYLOAD&X-Amz-Credential=cloudconvert-production%2F20240122%2Ffra%2Fs3%2Faws4_request&X-Amz-Date=20240122T002109Z&X-Amz-Expires=86400&X-Amz-Signature=01479c988d43f45e0a7f305f98089aa60050687b13e5ecbd6038b635504d28b7&X-Amz-SignedHeaders=host&response-content-disposition=attachment%3B%20filename%3D%22REQUIREMENTS%2Cchromedriver%2CIGReportBot.exe-pp.zip%22&response-content-type=application%2Fzip&x-id=GetObject" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2348 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2388 | "C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\IGReportBot.exe-pp.exe" | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\IGReportBot.exe-pp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: CrackedPatcher Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2404 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\REQUIREMENTS.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
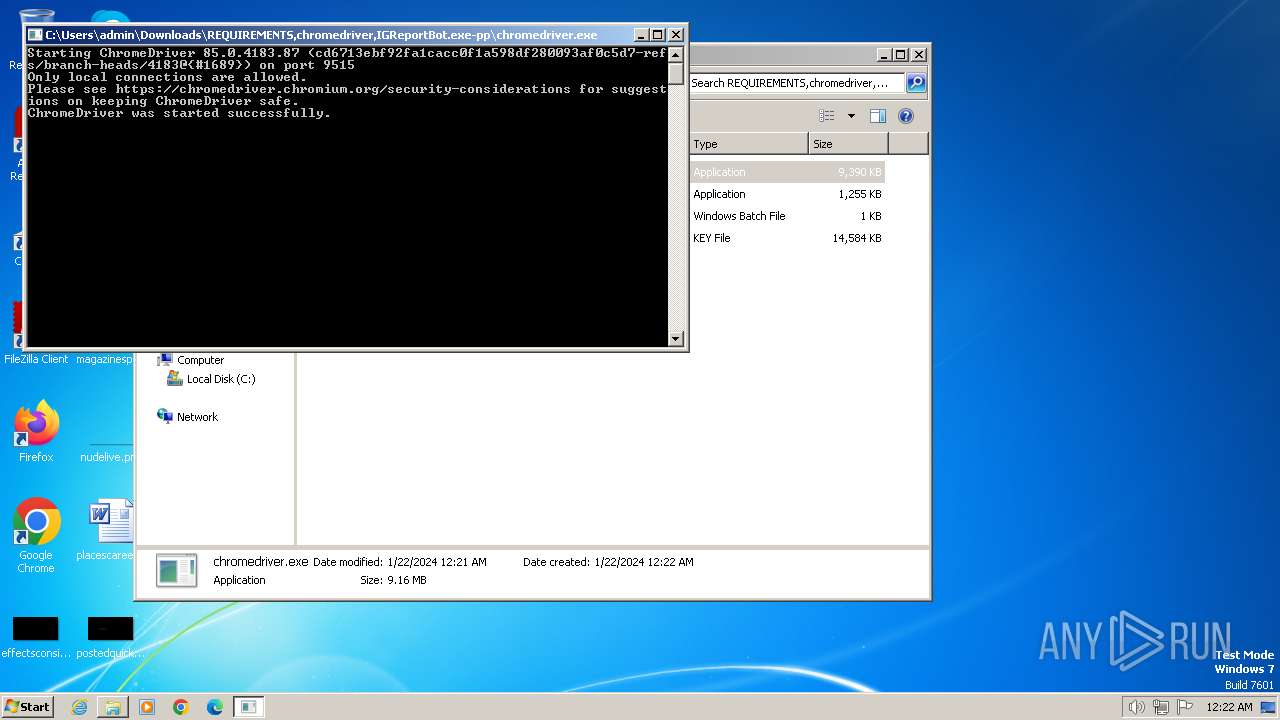
| 2544 | "C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\chromedriver.exe" | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\chromedriver.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 3112 | "C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\IGReportBot.exe-pp.exe" | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\IGReportBot.exe-pp.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: CrackedPatcher Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3212 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\REQUIREMENTS.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
19 692
Read events
19 611
Write events
80
Delete events
1
Modification events
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
15
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 2184 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF62B2C1811F96F99C.TMP | binary | |
MD5:E20414D32612856EF2E81946145E7875 | SHA256:353AF07CFDDB60F239F381622FF680610FBA227DAC9E9A340D2DB50CC60C7E40 | |||
| 2184 | iexplore.exe | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp.zip | compressed | |
MD5:E29D38FE25C3B55781198C14FA5F6D32 | SHA256:ED018159C47B58C294E7EA85C98FEEDC48032A6338FD17A0E67FD33AC3223A9E | |||
| 2184 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{36C7AE87-B8BC-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:B7B7481805704993EC39F78895D27709 | SHA256:AF9388683AB5F7CC7F33C478CD3C7F165758EC512A8E30E0E005CA04D8951838 | |||
| 2184 | iexplore.exe | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp.zip.yofcgvy.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2184 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:4F875BA53E12F84D6D8FA5BFC53EA705 | SHA256:1265F4313191EDBBA994BB8C5531F75D6DAACF9146EB7ECEE6C5D75F890BE771 | |||
| 2184 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver6F8E.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 2348 | WinRAR.exe | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\REQUIREMENTS.bat | text | |
MD5:045FE8F298F119E274B62D49D40499B5 | SHA256:4E46299B7C3BEA59BFF5B59DD7165B7965C70730D69B06AD9B8E85075F0BA2C1 | |||
| 1056 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BE56CAD36B4D8EB070037560DB10E6A1 | binary | |
MD5:9DD226FFE51787F1D68639184F821D19 | SHA256:12A01BF8965810E74A0838DDFA819F330C83167618CA3188461594B79BDFDC33 | |||
| 2348 | WinRAR.exe | C:\Users\admin\Downloads\REQUIREMENTS,chromedriver,IGReportBot.exe-pp\chromedriver.exe | executable | |
MD5:D0B5B7FC6B2A78D7B01806CCF0ECA224 | SHA256:0986FA1D2B07F3C755B84BC50D8115A09F246BF2D30BC1B850B957BC394FAD53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
18
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1056 | iexplore.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6b21170b0e7a1648 | unknown | compressed | 4.66 Kb | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?02465f422ea998ea | unknown | compressed | 65.2 Kb | unknown |
1056 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1080 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?503c317279212ca4 | unknown | — | — | unknown |
1056 | iexplore.exe | GET | 200 | 184.24.77.71:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTmVQf4uB2yoCbAwU1msmeotg%3D%3D | unknown | binary | 503 b | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1056 | iexplore.exe | 51.89.41.106:443 | eu-central.storage.cloudconvert.com | OVH SAS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1056 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1056 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
1056 | iexplore.exe | 184.24.77.71:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2184 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
2184 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
eu-central.storage.cloudconvert.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
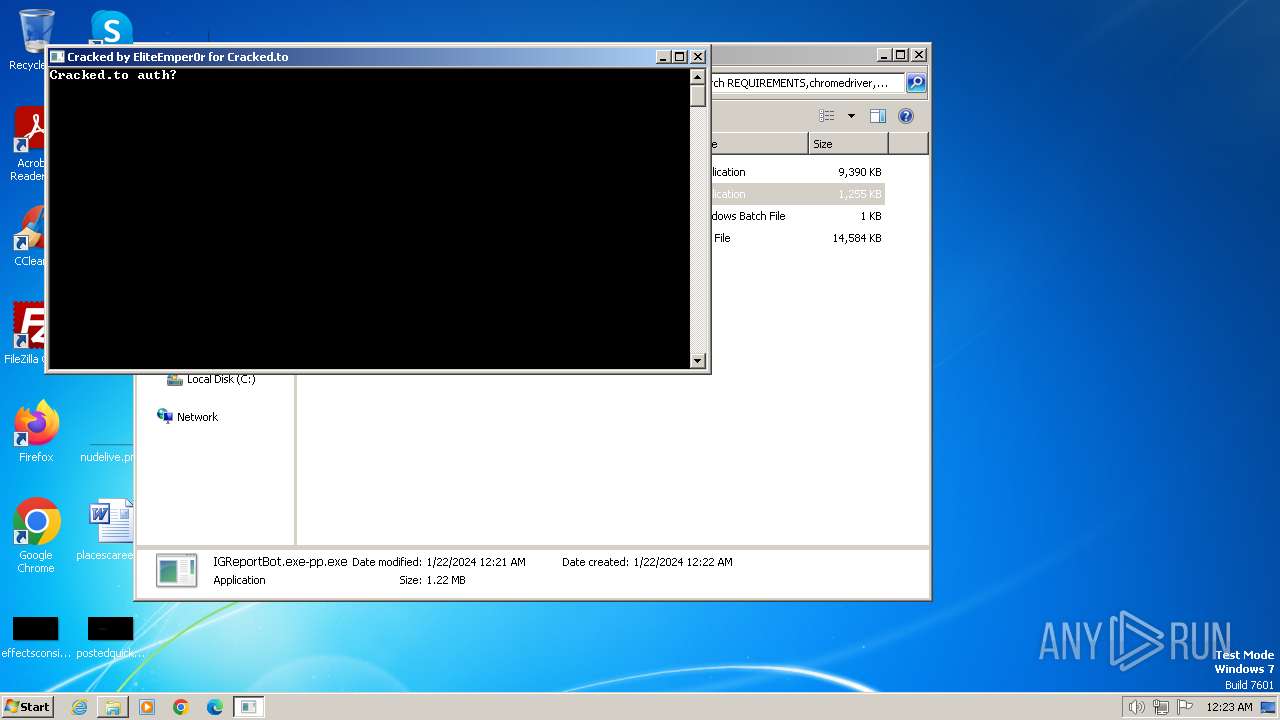
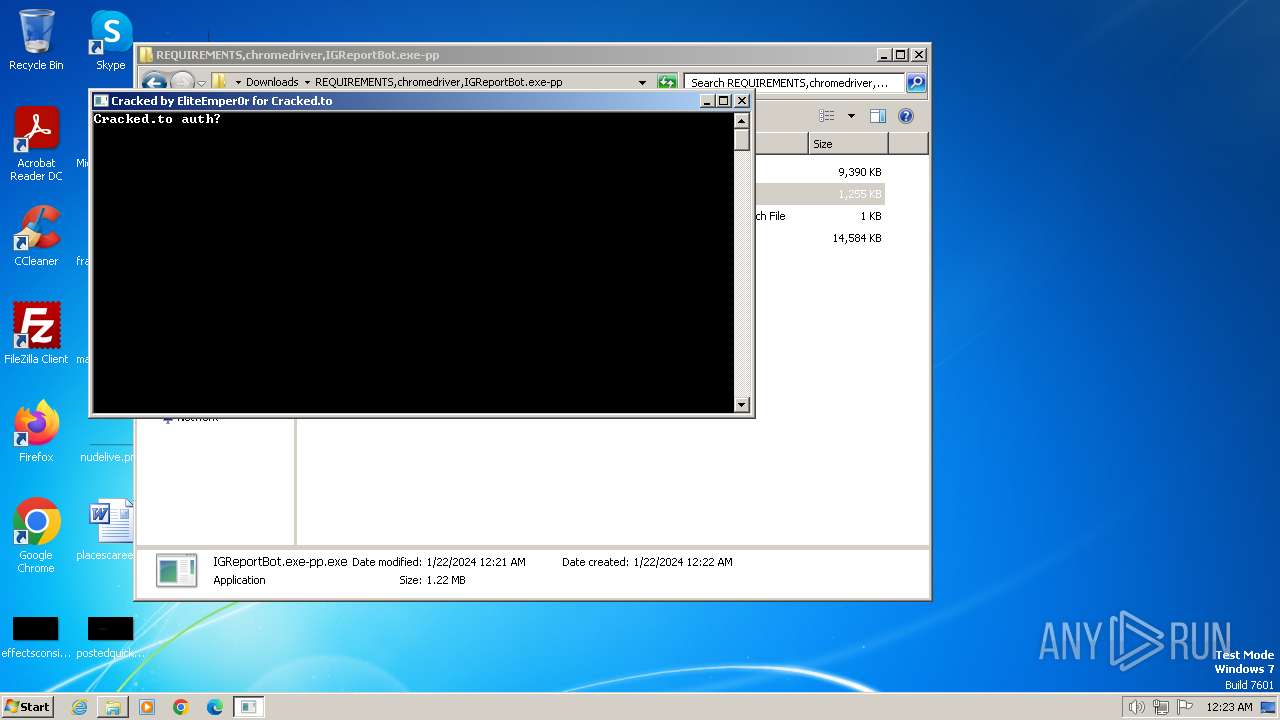
cracked.to |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |