| File name: | Aimbot Dragonbot Gitz.exe |
| Full analysis: | https://app.any.run/tasks/aa23fafe-bd1d-4e78-aae3-531e82241f25 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2024, 15:12:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1F59C96BC461957F8A868201B9BCE44D |
| SHA1: | A1CD43B4E4BAE6BD406E53EE3EF1E260194A268A |
| SHA256: | 3D3B951A5EB00D713423A70B1C2D7888D03432CA25B2E08FAD8950EA4C62D7BD |
| SSDEEP: | 49152:tvamSo5a6uaqGLVPJaZ74yaoDtziyjcU20qtCTpJHb+bmwLNYf0e+l8pAi2G0Vtw:timpu7taoDdGt4pJHb35pSG0zx4z/bh7 |
MALICIOUS
Drops the executable file immediately after the start
- Aimbot Dragonbot Gitz.exe (PID: 2040)
SUSPICIOUS
Reads the Internet Settings
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Reads Microsoft Outlook installation path
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Reads Internet Explorer settings
- Aimbot Dragonbot Gitz.exe (PID: 2040)
INFO
Reads the computer name
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Checks supported languages
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Checks proxy server information
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Create files in a temporary directory
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Reads the machine GUID from the registry
- Aimbot Dragonbot Gitz.exe (PID: 2040)
Creates files or folders in the user directory
- Aimbot Dragonbot Gitz.exe (PID: 2040)
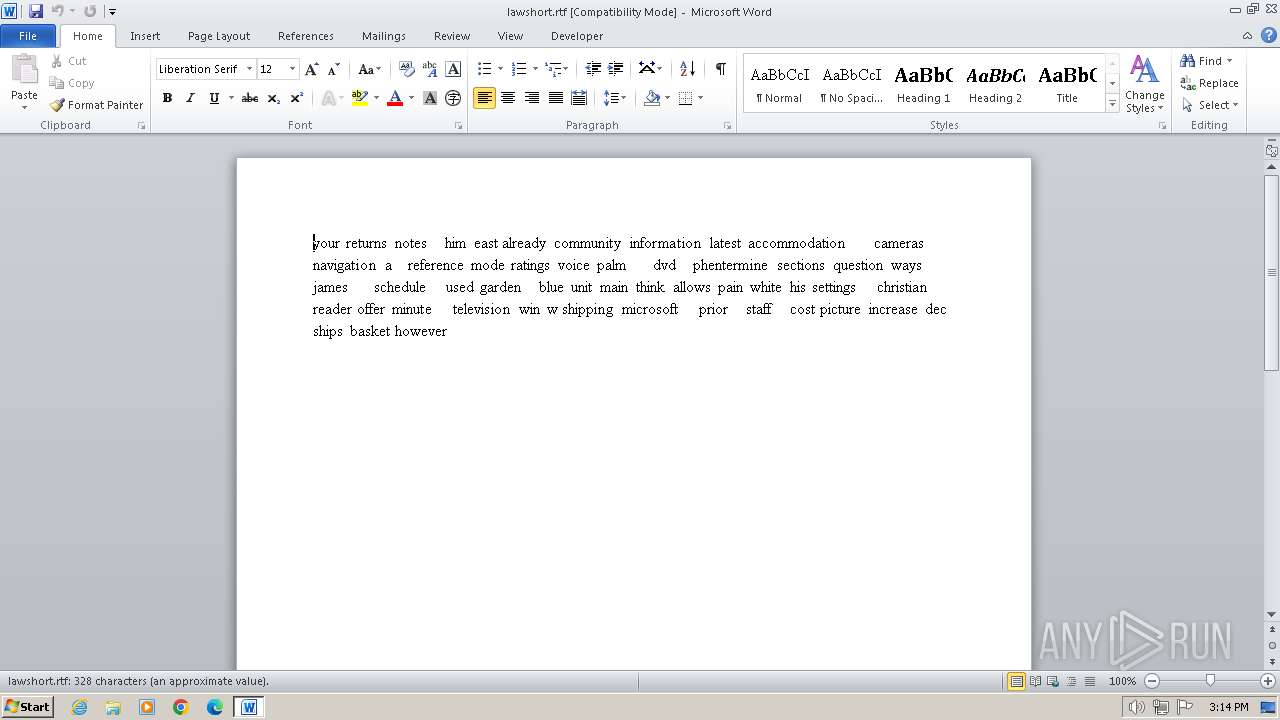
Manual execution by a user
- WINWORD.EXE (PID: 2320)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1265136 |
| InitializedDataSize: | 674304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e1334 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
42
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2040 | "C:\Users\admin\AppData\Local\Temp\Aimbot Dragonbot Gitz.exe" | C:\Users\admin\AppData\Local\Temp\Aimbot Dragonbot Gitz.exe | explorer.exe | ||||||||||||
User: admin Company: www.GamerzTools.net Integrity Level: MEDIUM Description: gamerzcoderz@gmail.com Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\lawshort.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 122
Read events
1 928
Write events
55
Delete events
139
Modification events
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
| (PID) Process: | (2040) Aimbot Dragonbot Gitz.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionTime |
Value: 64B7E8A65749DA01 | |||
Executable files
1
Suspicious files
7
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE51C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:329F969260D4F0C75AEE9C7BE704E8FD | SHA256:121B05D6521242D38447A48BABA5E0645286E011CF0B2BA683FFDDEE515D743D | |||
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{69A52593-7769-46A6-9871-C244F4573237}.tmp | binary | |
MD5:0FD8F6AF72D49BE04808541B251236CF | SHA256:121E99008D2DC615C17412F2A5412187CC12468A5D27F8445FCA7D66325B0532 | |||
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{5BBFA249-BAB1-4E3E-A753-2F45DE7FBD72}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{B3EC0BB6-E2CD-409E-8B9F-28771389A28F}.tmp | binary | |
MD5:FF6625B49D9D77F1125F67374DCEB747 | SHA256:826E6C22C80C3A03A9AA42AEA3EE44F5511E13C913955D6B9B9D11789F54AA24 | |||
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\lawshort.rtf.LNK | binary | |
MD5:0C9AF5EB4CEEED197C34BB9206272BAB | SHA256:331C573889A087BBFCBEC1D0B0850A33F659E5D821C3D0C508CECC5D9E689CD4 | |||
| 2040 | Aimbot Dragonbot Gitz.exe | C:\Users\admin\AppData\Local\Temp\gitz002.txt | text | |
MD5:DEA76A89D60A1E0FA669119C4BE5B741 | SHA256:58D11EC01EA6F64A9CE4E64F2A19B668FCAAAA4C4DEED12C1146FD9F4199BAAC | |||
| 2320 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:974B4A57591A7735D85A1E5D7A140B1C | SHA256:6E688A852556D98CEC3FCF2E8F897383C2576B991EFA9C6BBB32E3EAA71A1442 | |||
| 2320 | WINWORD.EXE | C:\Users\admin\Desktop\~$wshort.rtf | binary | |
MD5:C44108C28B7B7C418943EA545B0B68BF | SHA256:E07C96FCB88F222FF34AA4D5AB1FD7BF6C229B507D618FF87F1AA1FF3B16EBA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.hack.foroperu.org |
| unknown |
Threats
Process | Message |
|---|---|
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |
Aimbot Dragonbot Gitz.exe | %s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s%s |