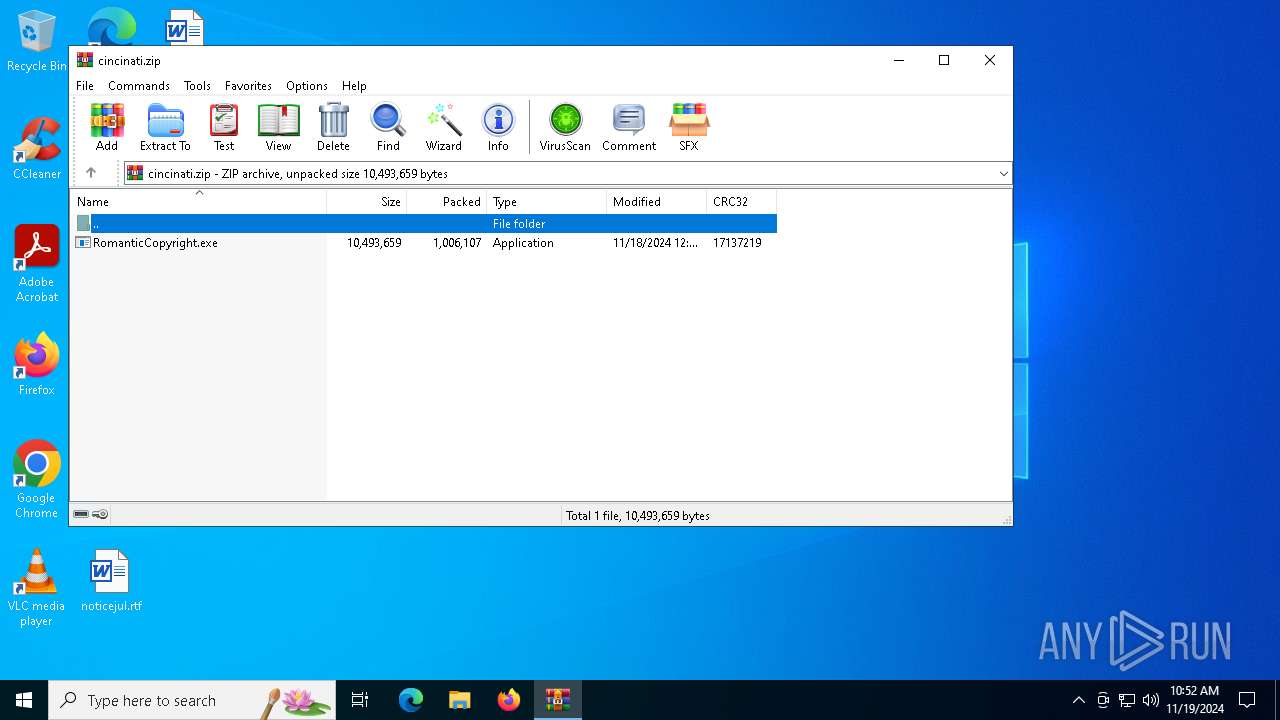
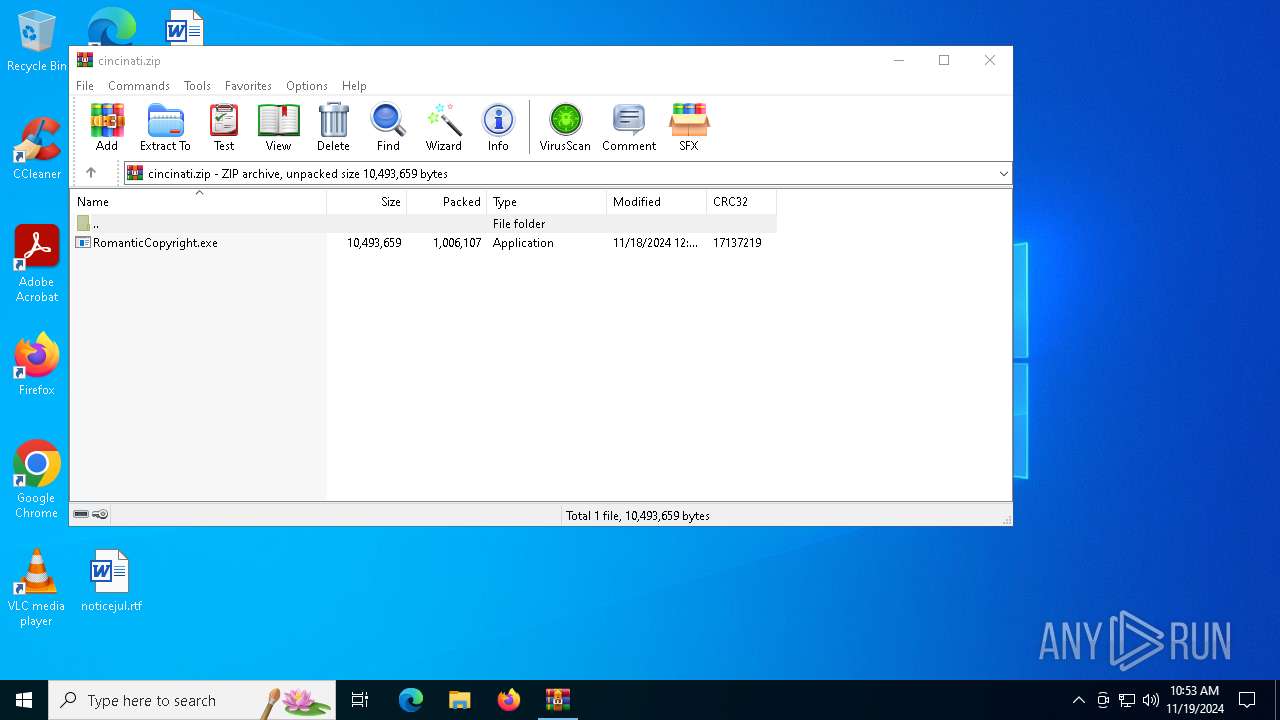
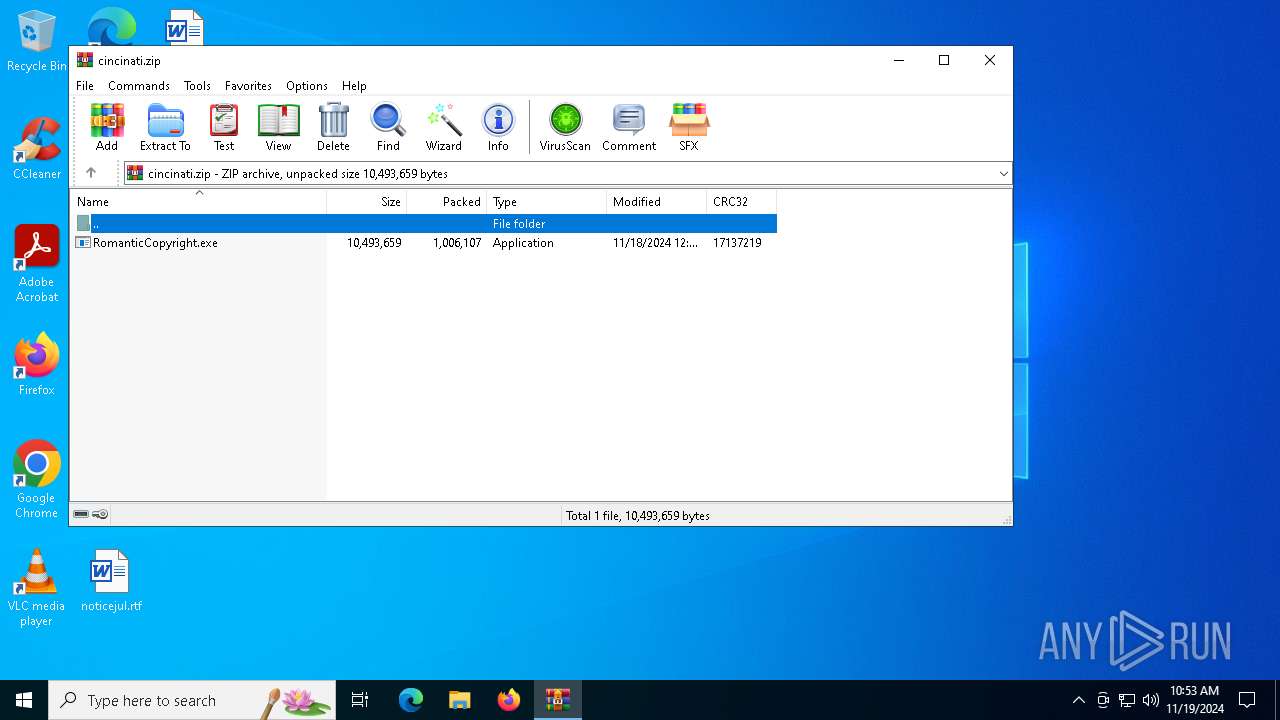
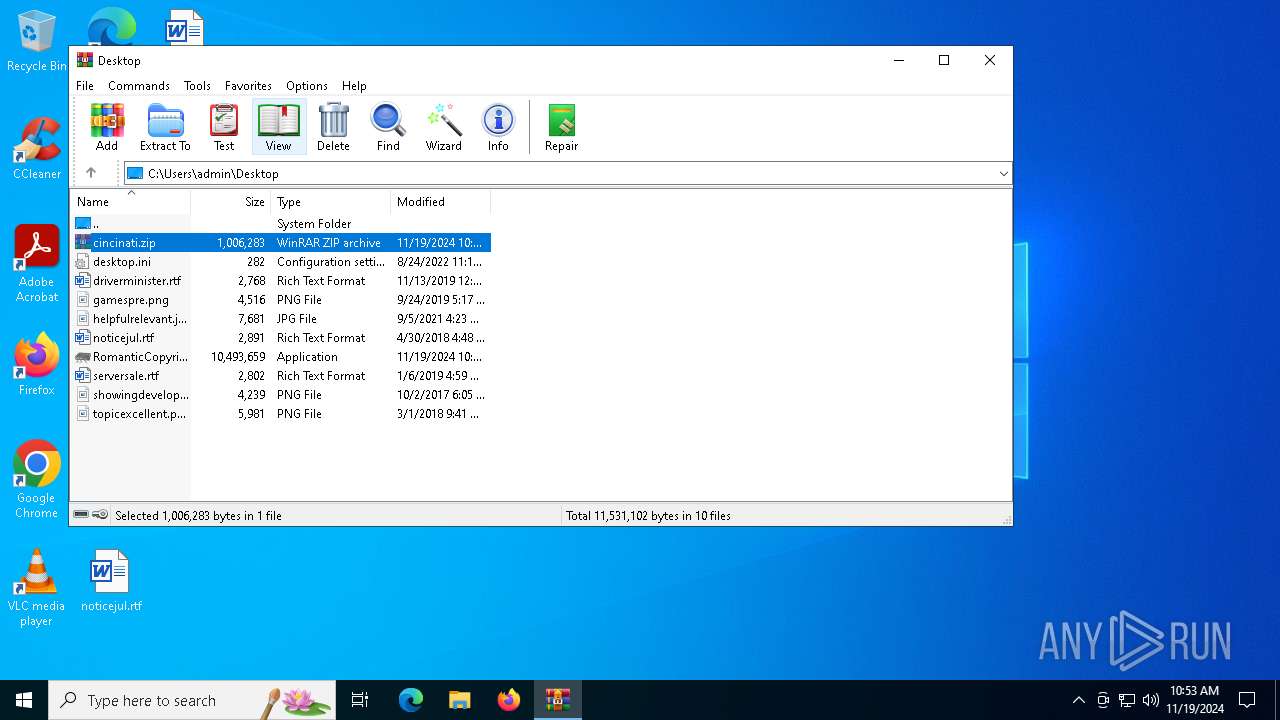
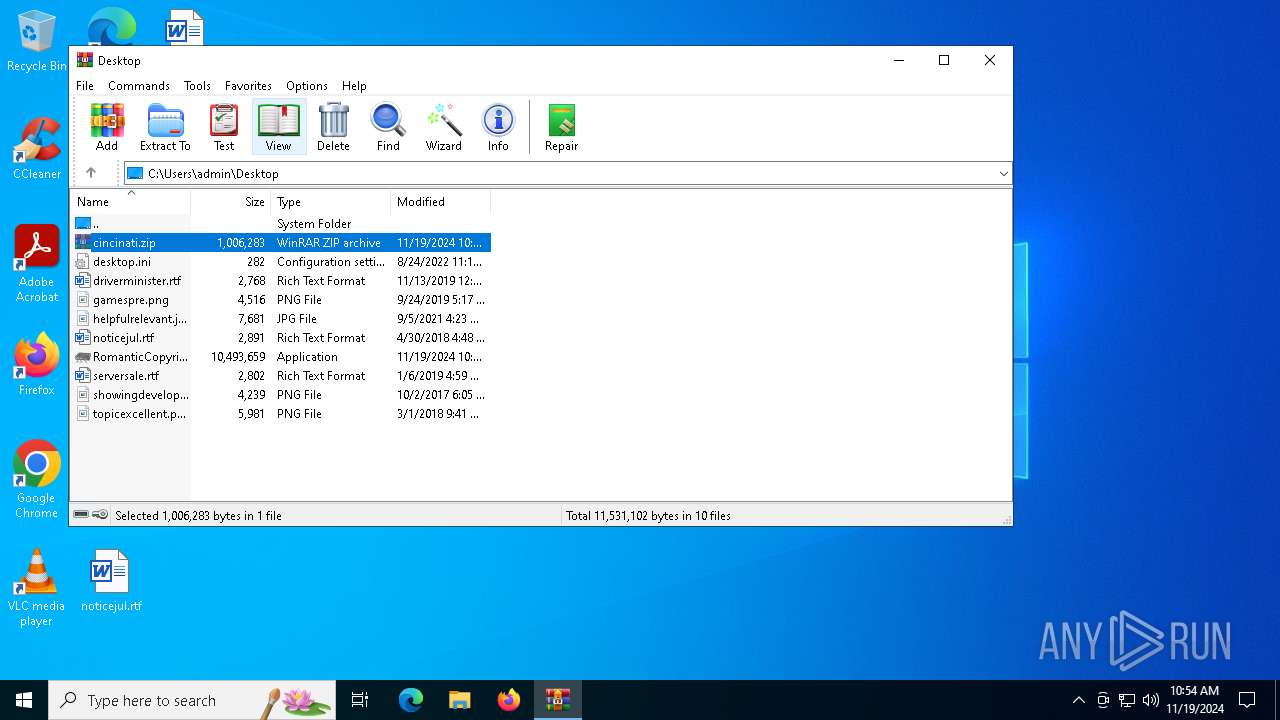
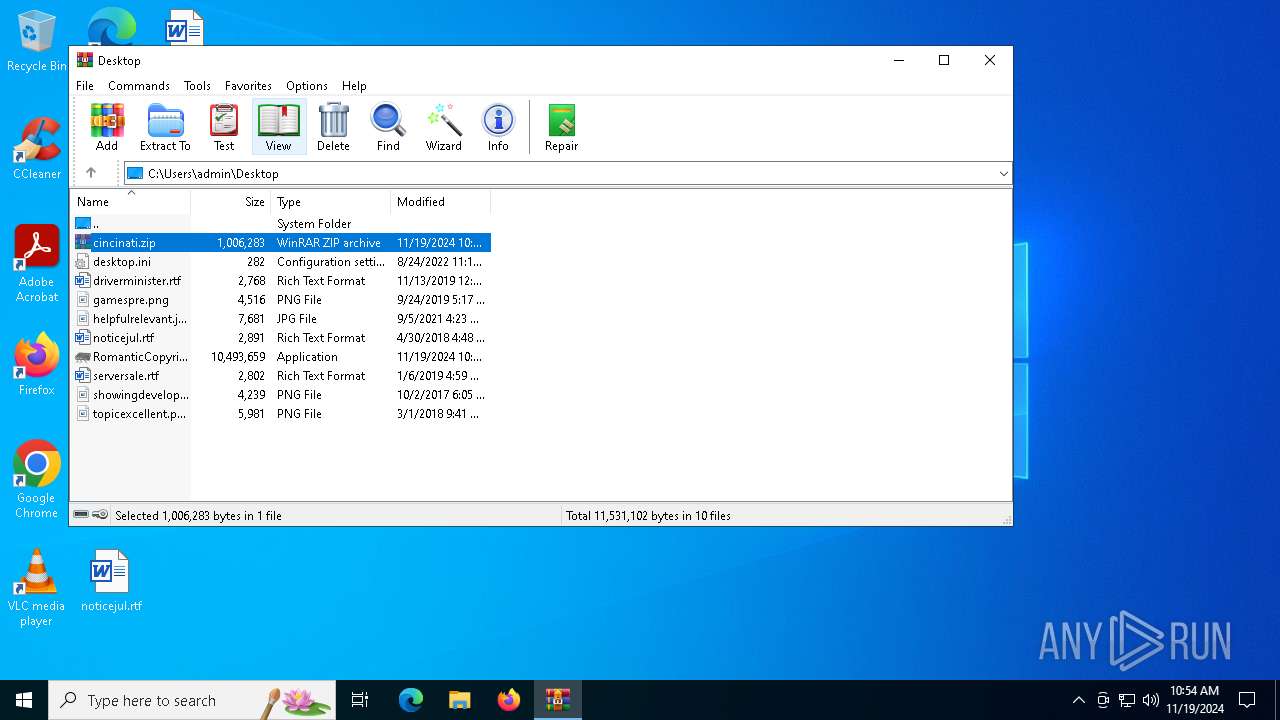
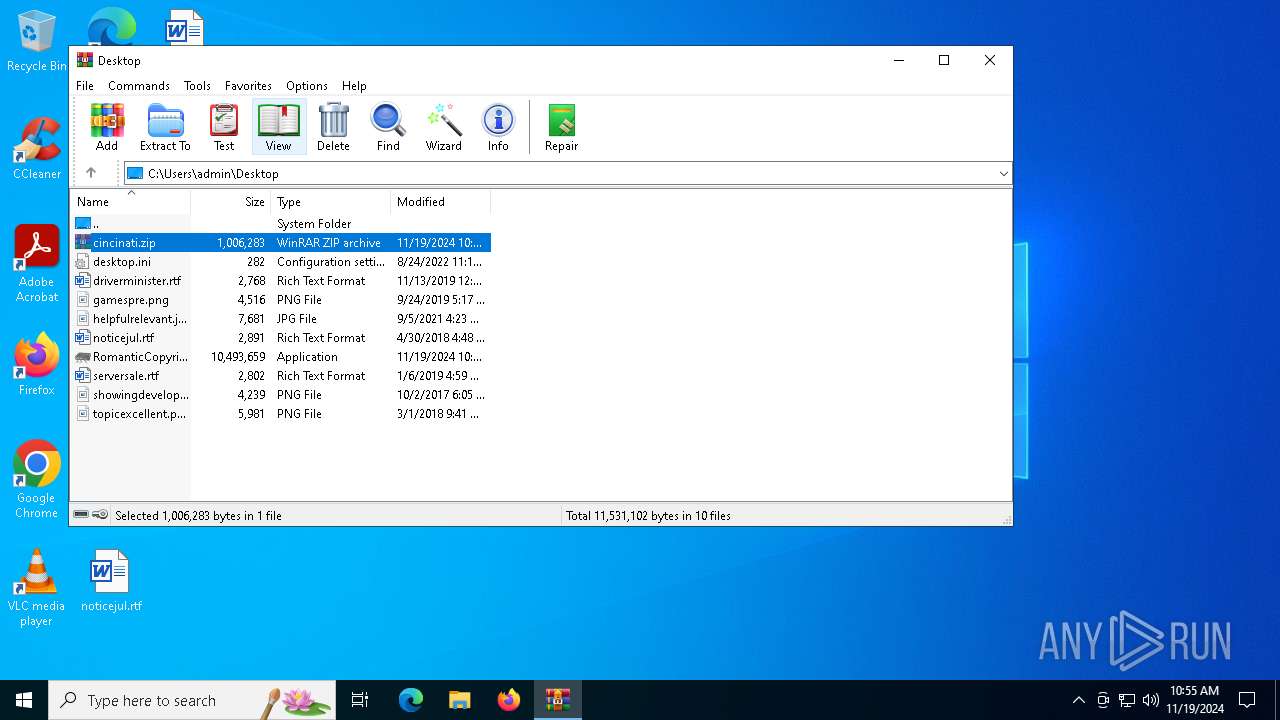
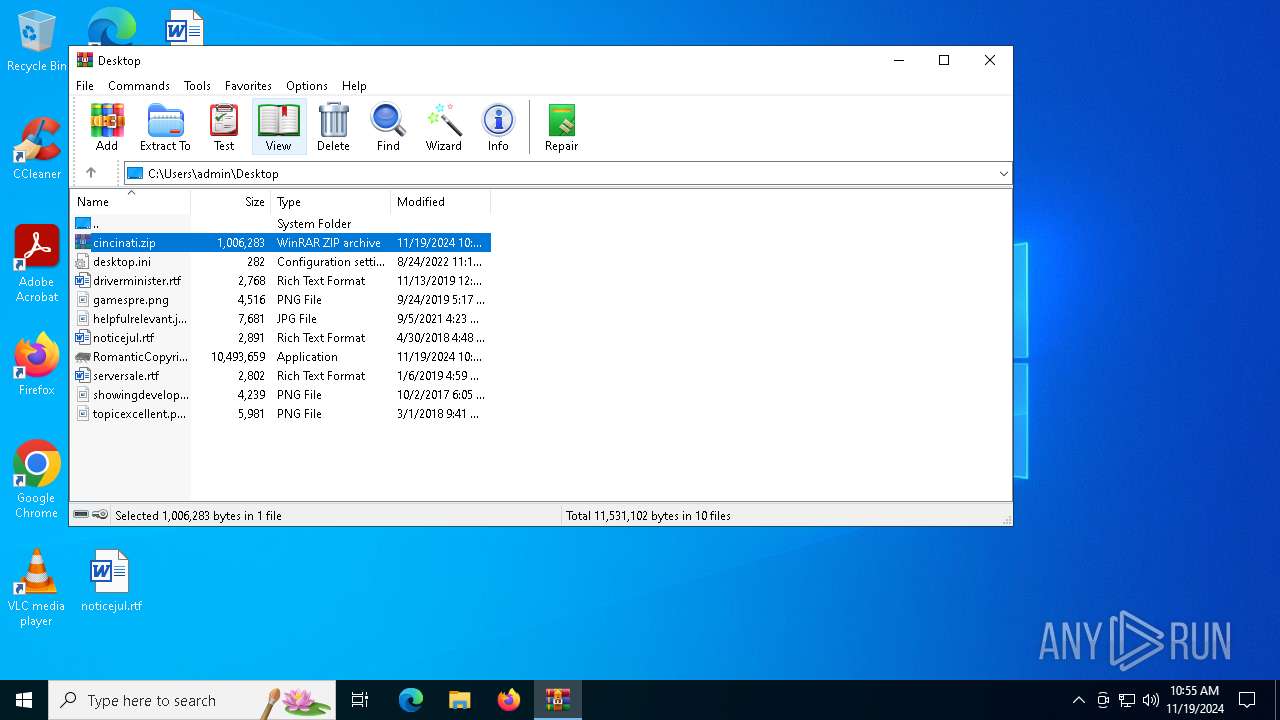
| File name: | cincinati.zip |
| Full analysis: | https://app.any.run/tasks/0b0a56a8-6c7a-41c5-a7d1-3eeb81841419 |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2024, 10:52:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4B1EEE4AB5A46F1215F7397A650E385F |
| SHA1: | 93104208B9A3E25900E2C6489C398EC1AE07DB56 |
| SHA256: | 3D36C412F3E9BD9983629B45CC34DC5AC1D48CEC7232A3D8ACE19AE1181F7649 |
| SSDEEP: | 49152:LN34juluzmCDEujGSHMGbMRJCOtbxi7SqJUh8wtcv51WZFm00N93R42aqkFwDpce:LNIjsGmCDnHMqOt0xUh8t51kw00NE2aM |
MALICIOUS
Executing a file with an untrusted certificate
- RomanticCopyright.exe (PID: 6060)
Generic archive extractor
- WinRAR.exe (PID: 648)
AutoIt loader has been detected (YARA)
- Dept.com (PID: 5104)
SUSPICIOUS
Reads security settings of Internet Explorer
- RomanticCopyright.exe (PID: 6060)
Executing commands from ".cmd" file
- RomanticCopyright.exe (PID: 6060)
Starts CMD.EXE for commands execution
- RomanticCopyright.exe (PID: 6060)
- cmd.exe (PID: 6120)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6120)
Executable content was dropped or overwritten
- cmd.exe (PID: 6120)
The executable file from the user directory is run by the CMD process
- Dept.com (PID: 5104)
Starts application with an unusual extension
- cmd.exe (PID: 6120)
Get information on the list of running processes
- cmd.exe (PID: 6120)
Starts the AutoIt3 executable file
- cmd.exe (PID: 6120)
Application launched itself
- cmd.exe (PID: 6120)
INFO
Reads the computer name
- RomanticCopyright.exe (PID: 6060)
The process uses the downloaded file
- RomanticCopyright.exe (PID: 6060)
Create files in a temporary directory
- RomanticCopyright.exe (PID: 6060)
Manual execution by a user
- RomanticCopyright.exe (PID: 6060)
Checks supported languages
- RomanticCopyright.exe (PID: 6060)
Process checks computer location settings
- RomanticCopyright.exe (PID: 6060)
Creates a new folder
- cmd.exe (PID: 2564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
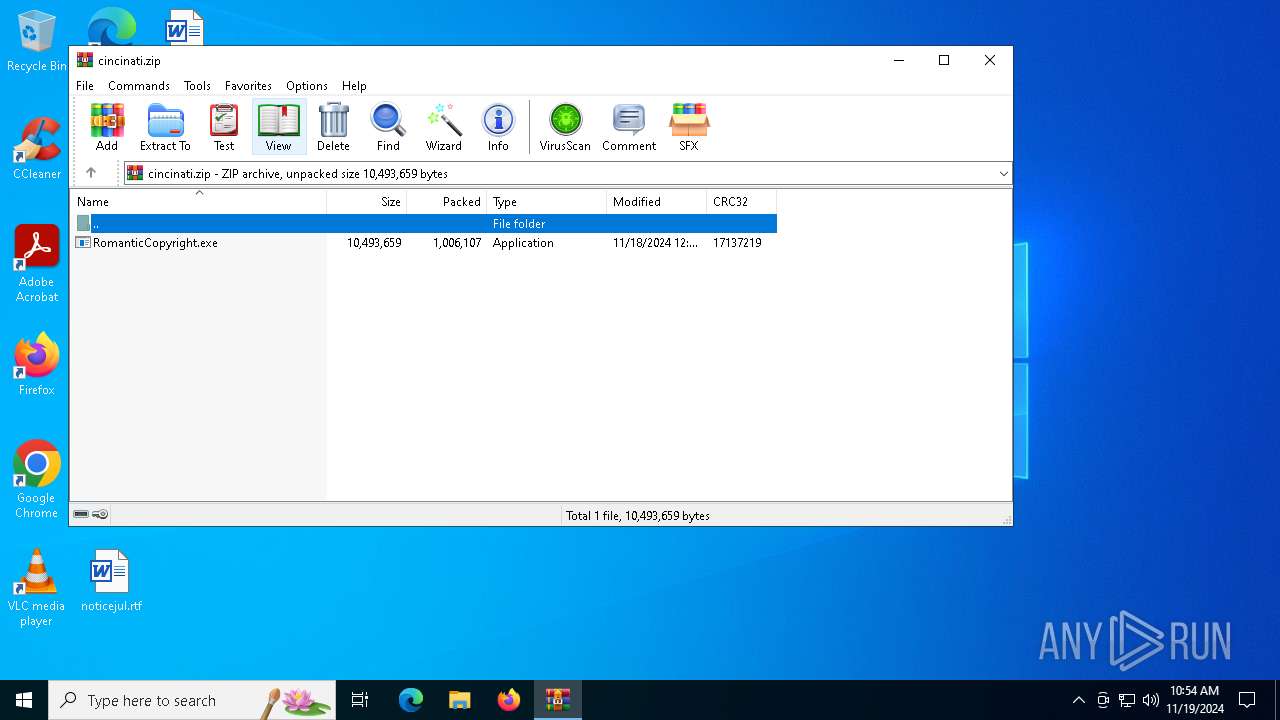
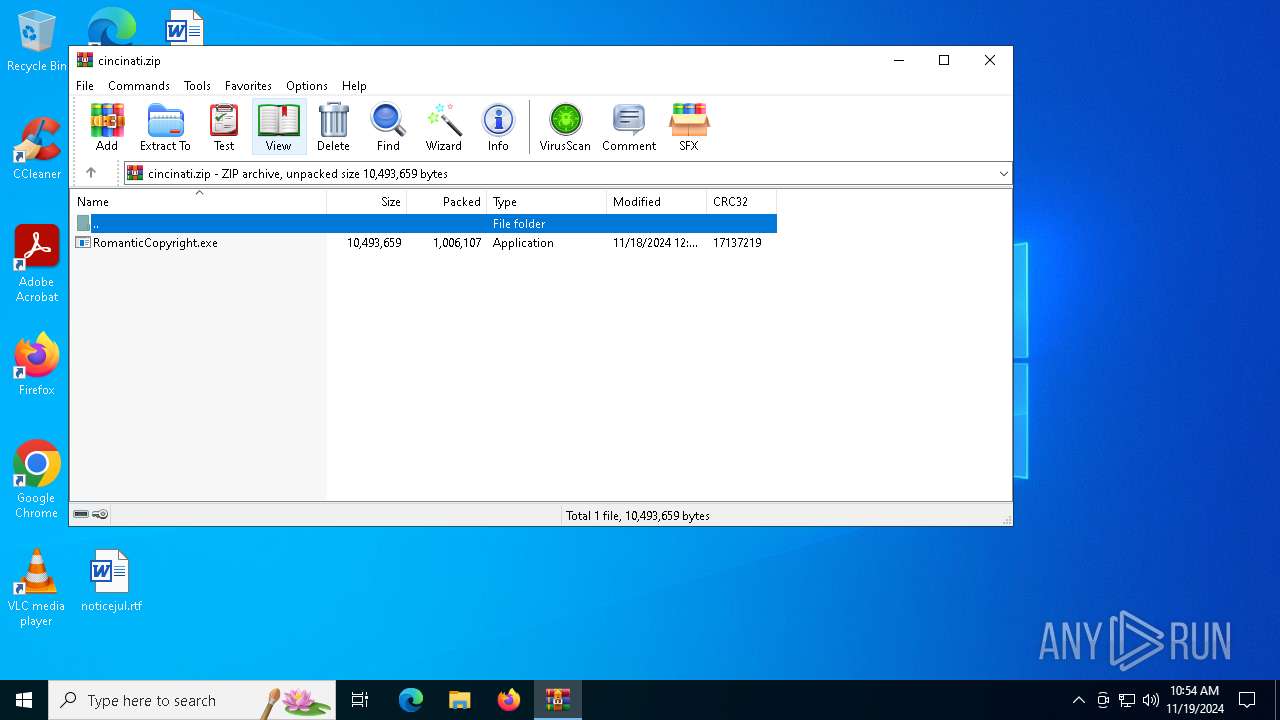
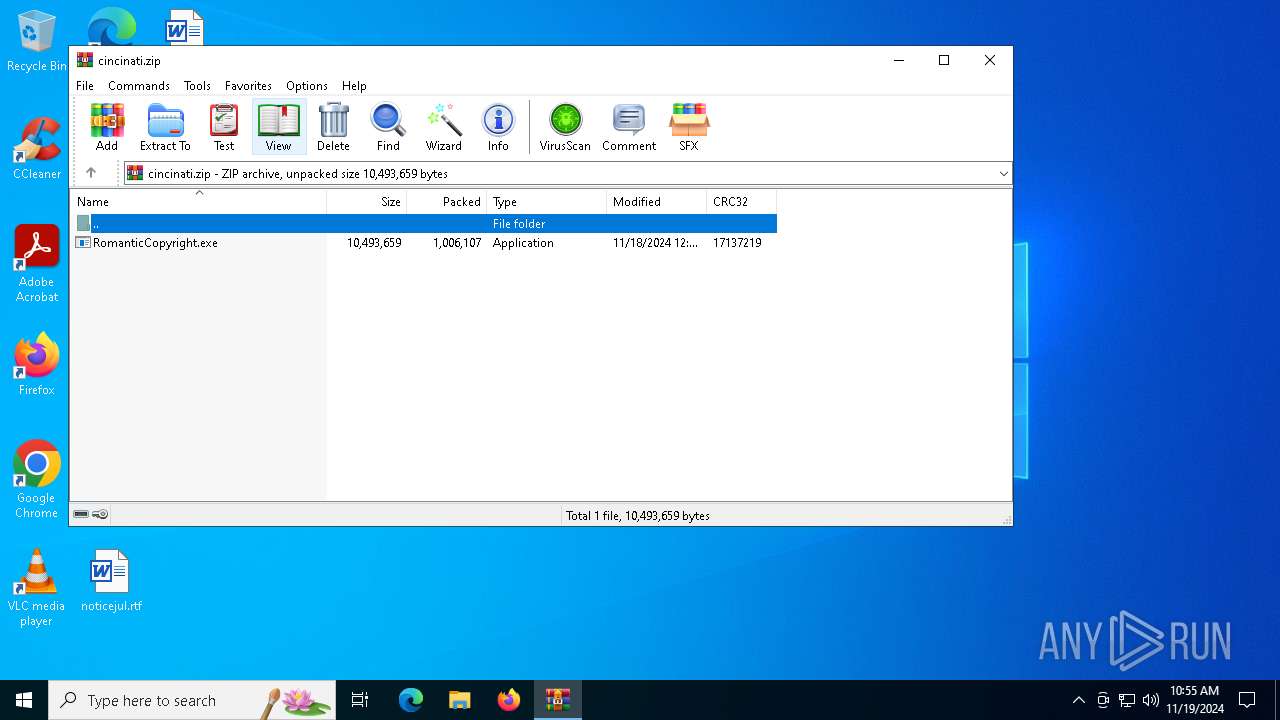
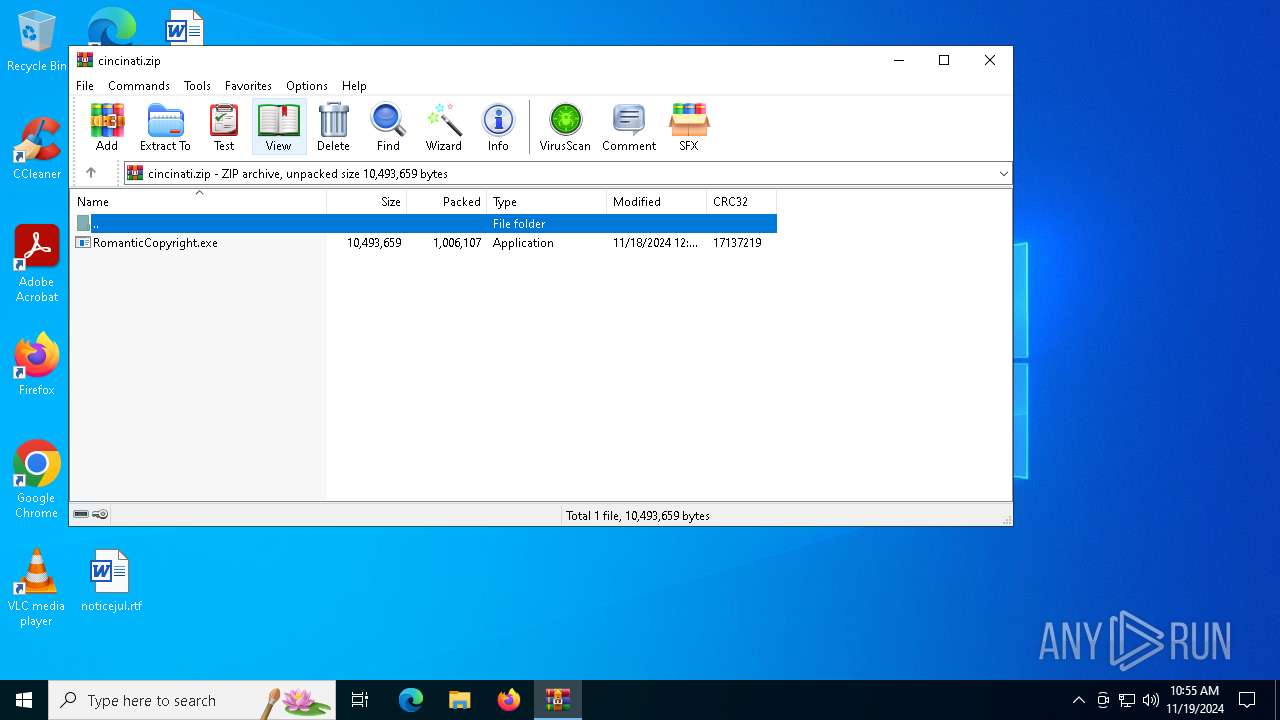
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:18 04:19:12 |
| ZipCRC: | 0x17137219 |
| ZipCompressedSize: | 1006107 |
| ZipUncompressedSize: | 10493659 |
| ZipFileName: | RomanticCopyright.exe |
Total processes
126
Monitored processes
13
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\cincinati.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 720 | findstr "AvastUI AVGUI bdservicehost nsWscSvc ekrn SophosHealth" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2564 | cmd /c md 796989 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2860 | findstr /V "SigConsumptionDisciplinesSong" Envelope | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3852 | cmd /c copy /b ..\Wan + ..\Module + ..\Is + ..\Read + ..\Bibliography + ..\Match + ..\Qld I | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5104 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5104 | Dept.com I | C:\Users\admin\AppData\Local\Temp\796989\Dept.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 3 Modules
| |||||||||||||||
| 5348 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 877
Read events
5 819
Write events
58
Delete events
0
Modification events
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\cincinati.zip | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (648) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
10
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Uni | text | |
MD5:DF066C1E3038FF1C556A50A0782E0DE1 | SHA256:CB4CA6CF393C39F6FFFAB51F095518826E38D4EFF4FB0F42AA1FB9A4D7EF0B3A | |||
| 3852 | cmd.exe | C:\Users\admin\AppData\Local\Temp\796989\I | binary | |
MD5:35431B1F719E5F8EDD3EE4C56D590BC9 | SHA256:427536F6A144672B8C5CD873D89C0374DAB2C6383256347EEF80B291729B99B0 | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Match | binary | |
MD5:CCE2E35FCD13802B894592BFA8BC4832 | SHA256:49C9F0A08D446AC52E26EC0A79578D6E8CD0363ADCE44AF727C537C2C127F278 | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Bibliography | binary | |
MD5:0124E182E6AB32C597551F987C8EFC9E | SHA256:6484DD9A145B3178A2534DD802441A7B8D08A679C3241C11395C22BFA6BA6826 | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Read | binary | |
MD5:B09B69FFBBB1C92BEB55C7FD798C8C66 | SHA256:4B54975D3405EA89C477DAA9802D93B4A56683A901039D31E8EB1218DEB742FA | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Wan | binary | |
MD5:CF96668F1C4973C8B43A72D90221E4D3 | SHA256:720160BB915923D8CF54BE5D580AC5C13E67A261DAF3AE65F972435DD716CD07 | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Qld | binary | |
MD5:47B8C8360718381BEB75B78CAD9989D4 | SHA256:0D7C733985EFC3042C41B2B26C32B7B8CE65FF9071EBDD872C3D0520A18351ED | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Standing | binary | |
MD5:4414FE8F2635B6344106903D0F52455D | SHA256:578F765C46F2B2842F3455C37549326A9EA665AEEDF5B86F6C3FF0BE1A5F1244 | |||
| 6060 | RomanticCopyright.exe | C:\Users\admin\AppData\Local\Temp\Module | binary | |
MD5:C3A23AA50702BAADCFFDB632C0781EAF | SHA256:E27AEC3FC7086AF2906FBF8D5A1A17E3F6871651F2663F8E5A3F5B44DD1E7D61 | |||
| 6120 | cmd.exe | C:\Users\admin\AppData\Local\Temp\796989\Dept.com | executable | |
MD5:92711F8BA644F8A5CE975DA8D0CD0700 | SHA256:2F10E6C875501B0F53D03C3040397393749F6AF4DAE0CE4974404BB739900048 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
25
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5448 | RUXIMICS.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 104.21.41.246:443 | https://smooth-reason.cyou/api | unknown | text | 2 b | unknown |
— | — | POST | 200 | 172.67.167.210:443 | https://smooth-reason.cyou/api | unknown | text | 48 b | unknown |
— | — | POST | 200 | 104.21.41.246:443 | https://smooth-reason.cyou/api | unknown | text | 14 b | unknown |
4932 | svchost.exe | GET | 200 | 23.48.23.193:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 172.67.167.210:443 | https://smooth-reason.cyou/api | unknown | text | 14 b | unknown |
— | — | POST | 200 | 104.21.41.246:443 | https://smooth-reason.cyou/api | unknown | text | 14 b | unknown |
4932 | svchost.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5448 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4932 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4932 | svchost.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5448 | RUXIMICS.exe | 23.48.23.193:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5448 | RUXIMICS.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
4932 | svchost.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
iJGgjIyQxn.iJGgjIyQxn |
| unknown |
smooth-reason.cyou |
| unknown |
self.events.data.microsoft.com |
| whitelisted |