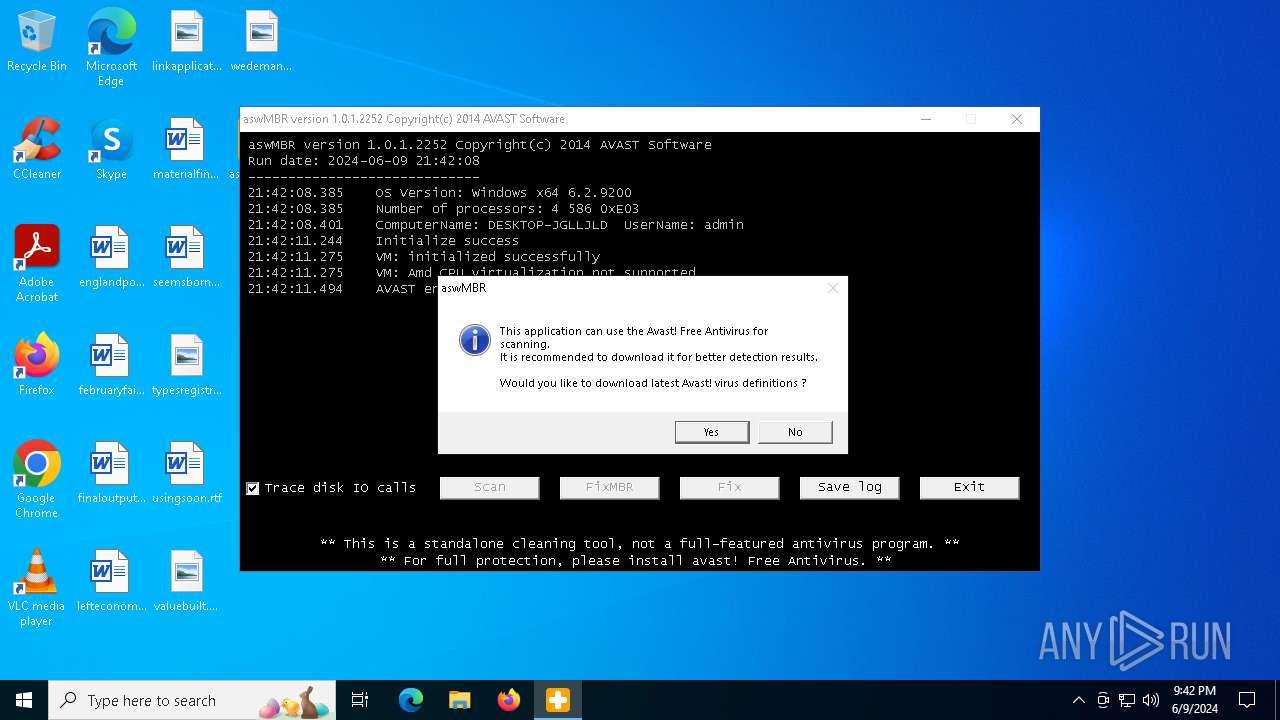
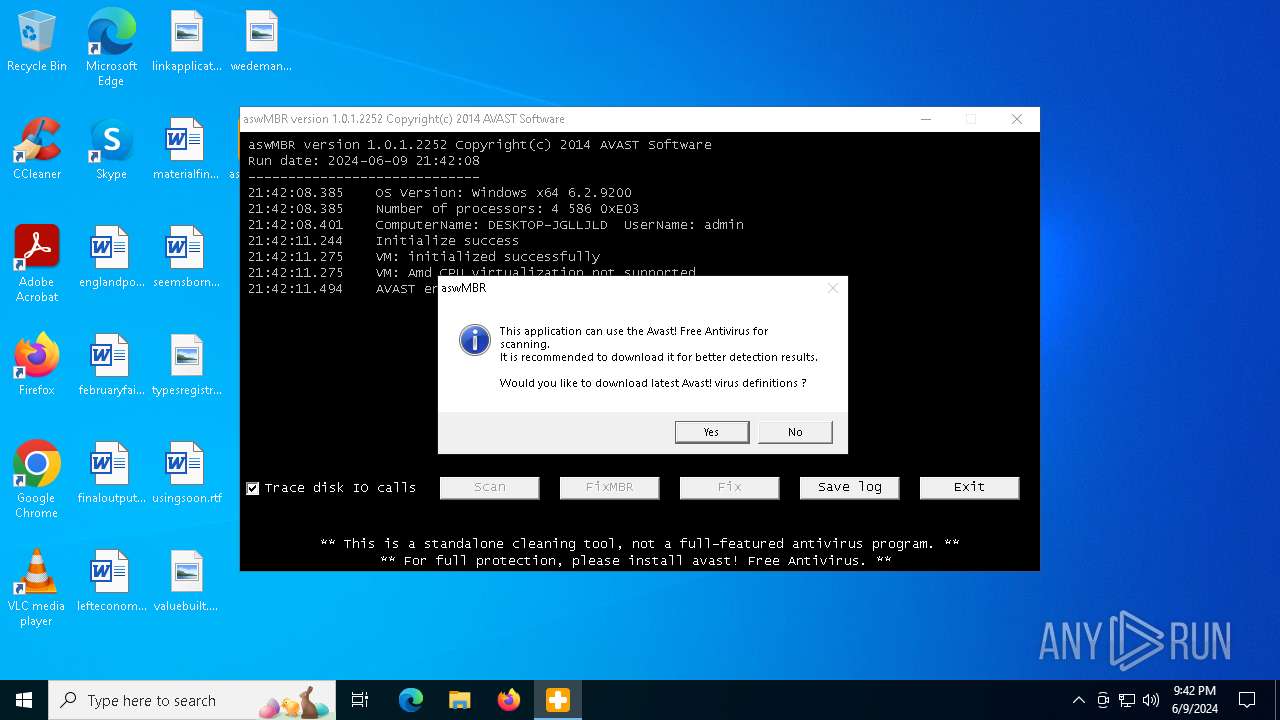
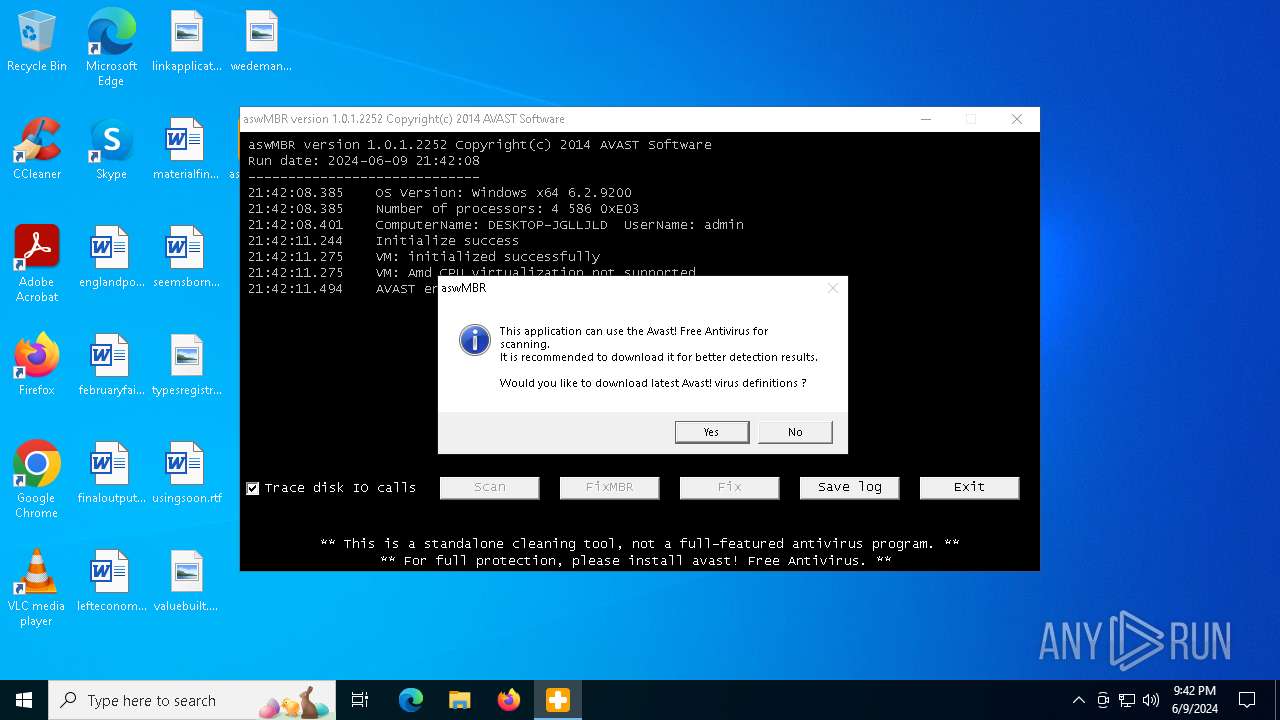
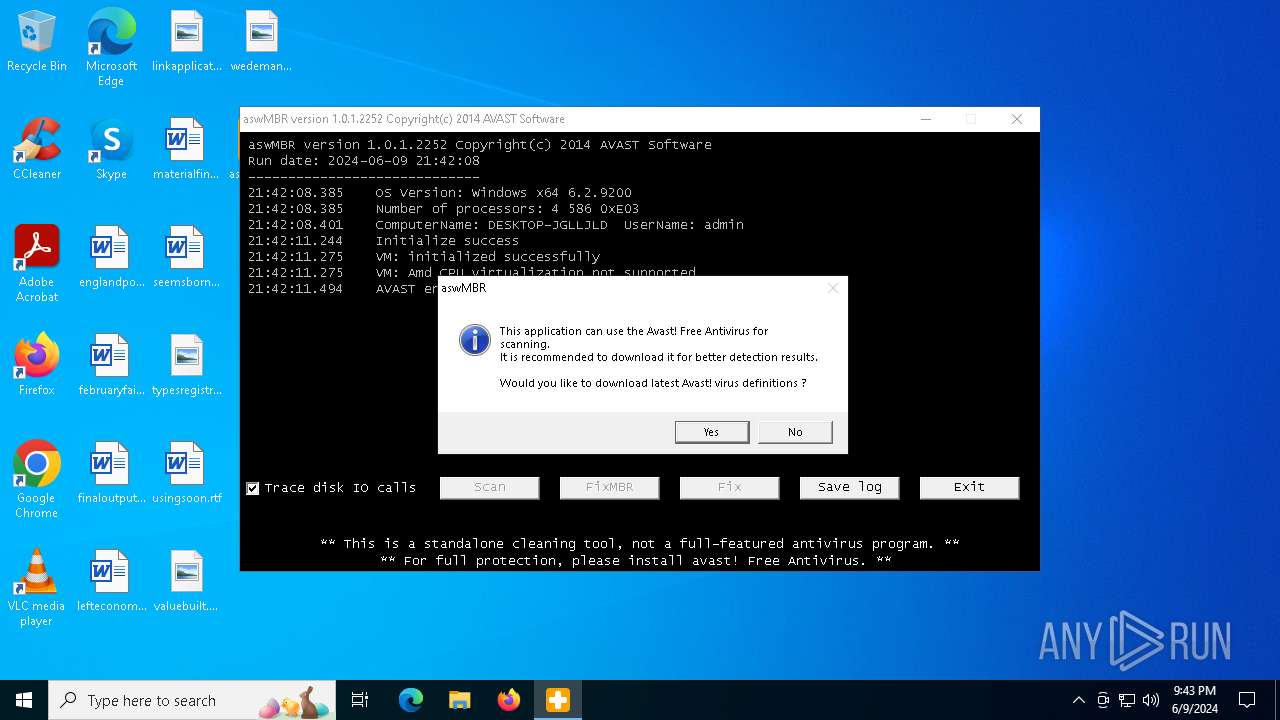
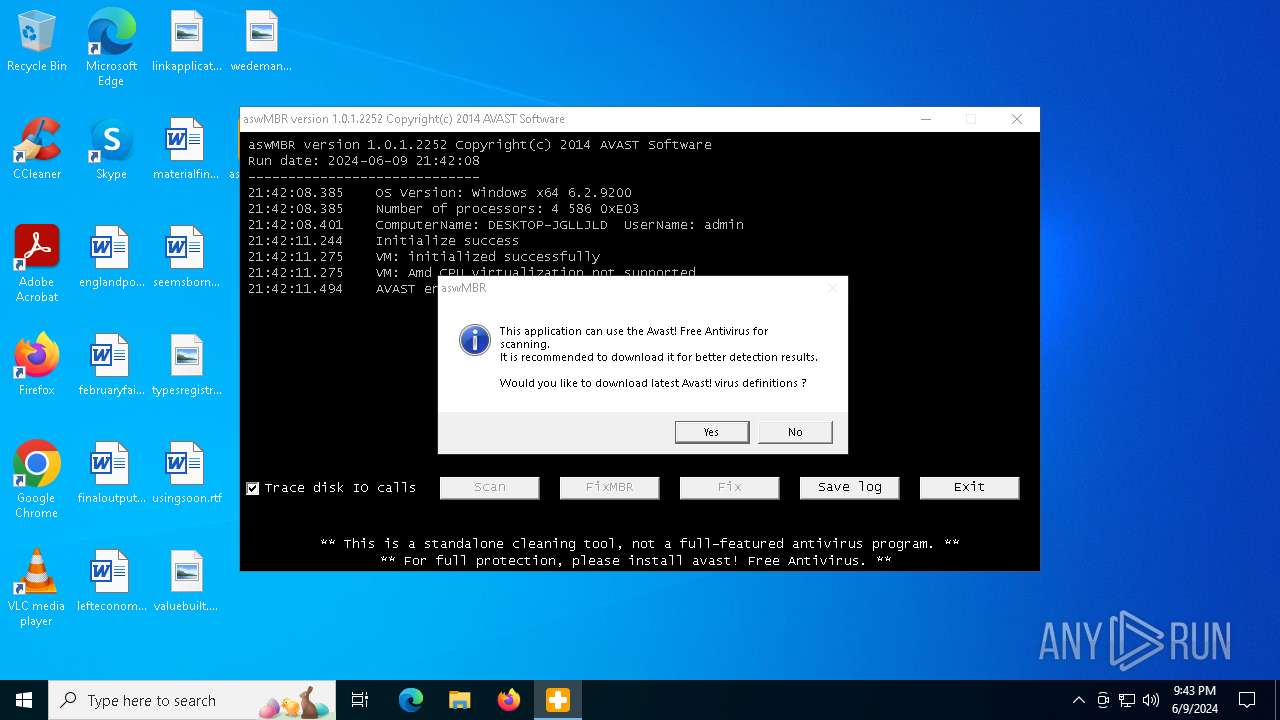
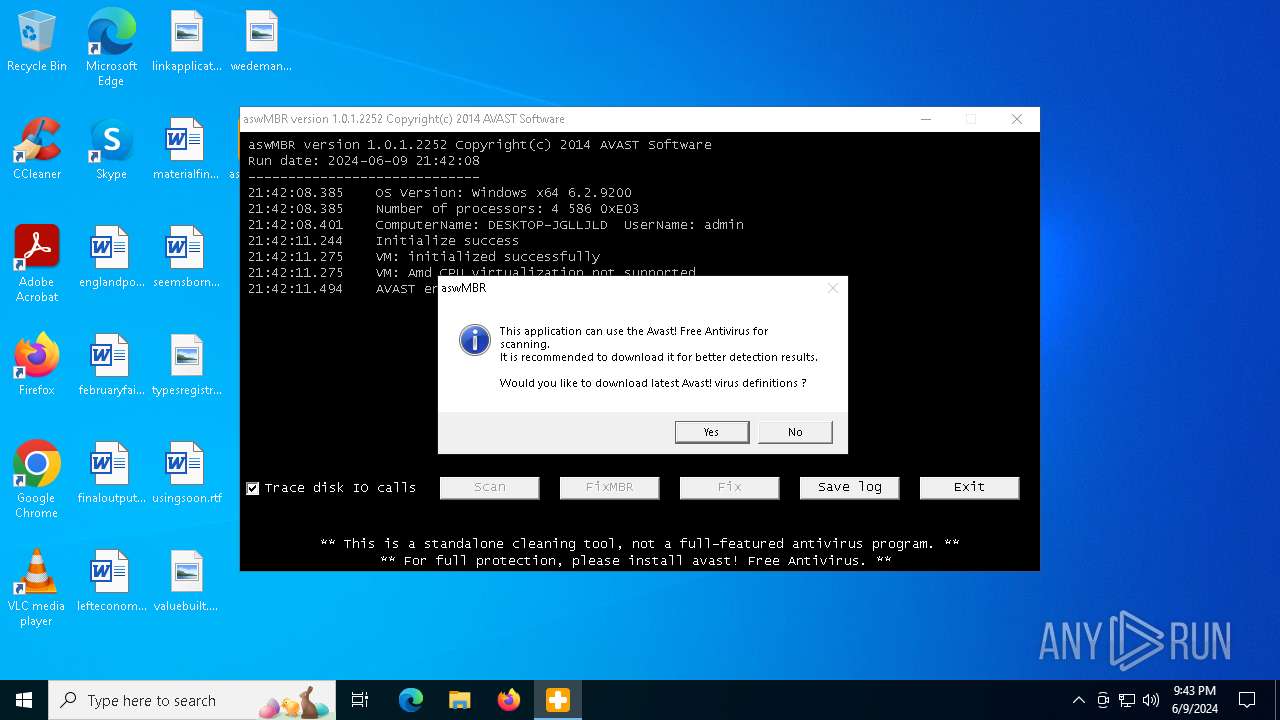
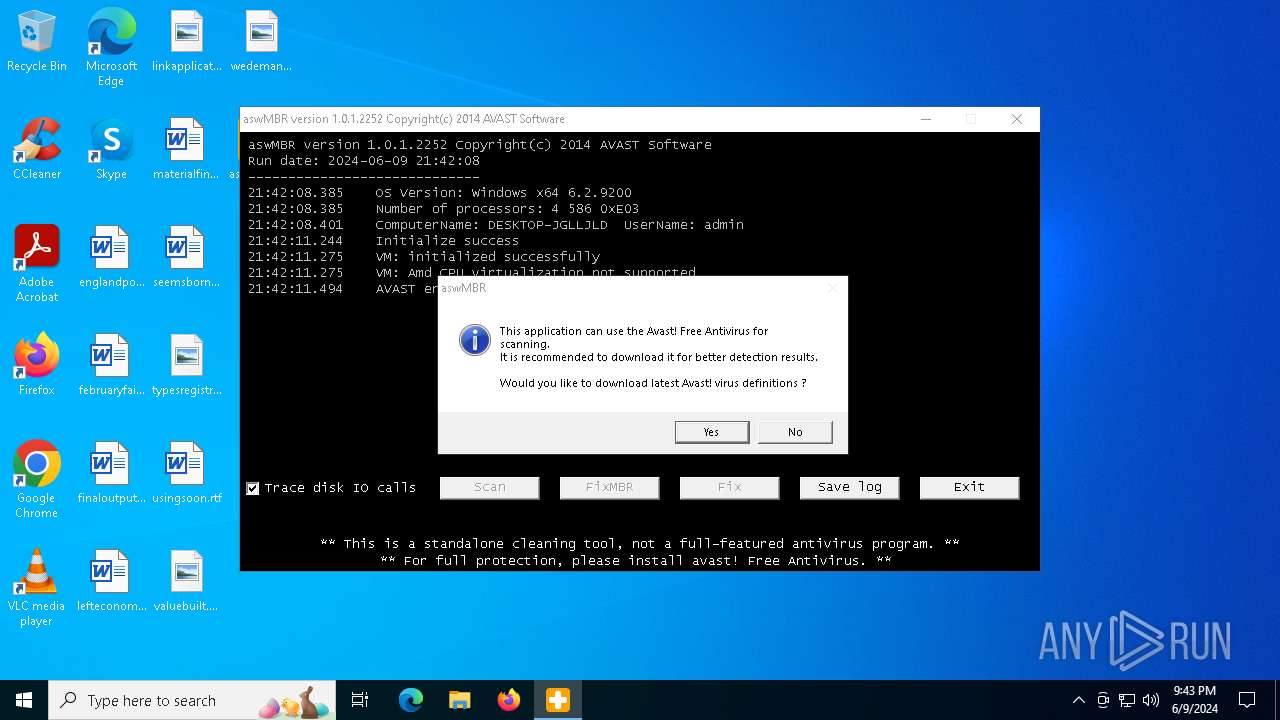
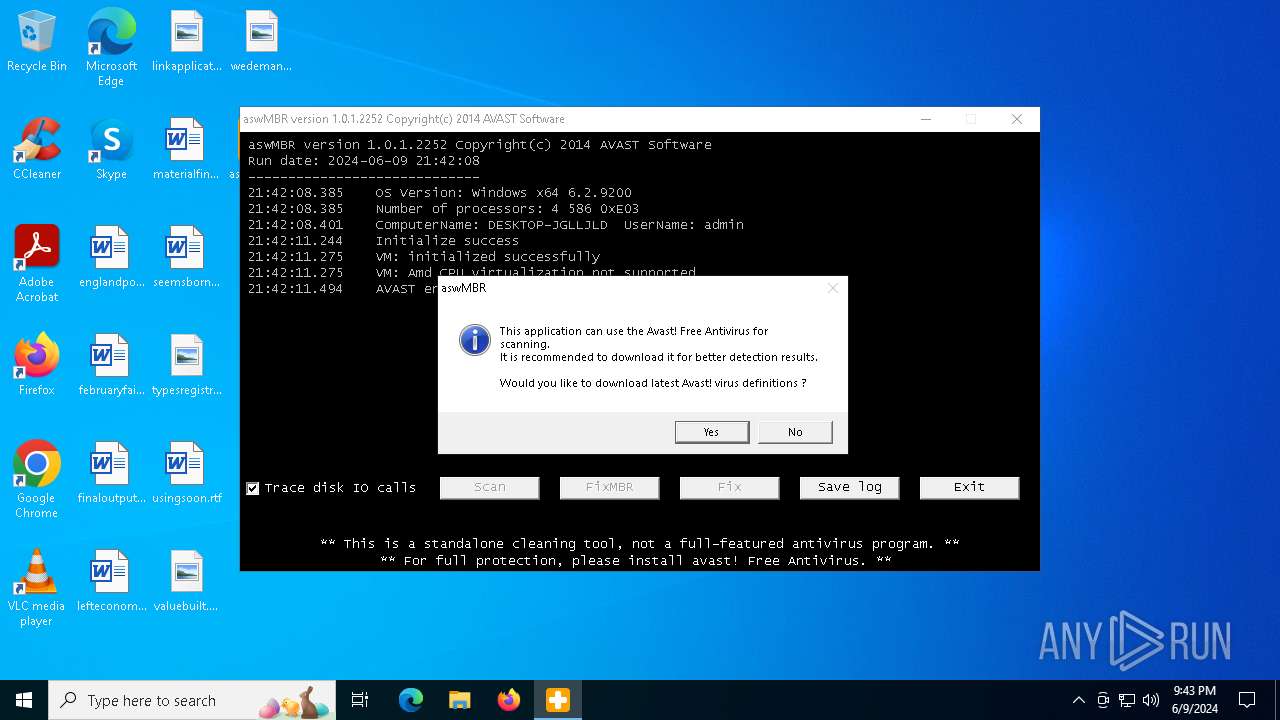
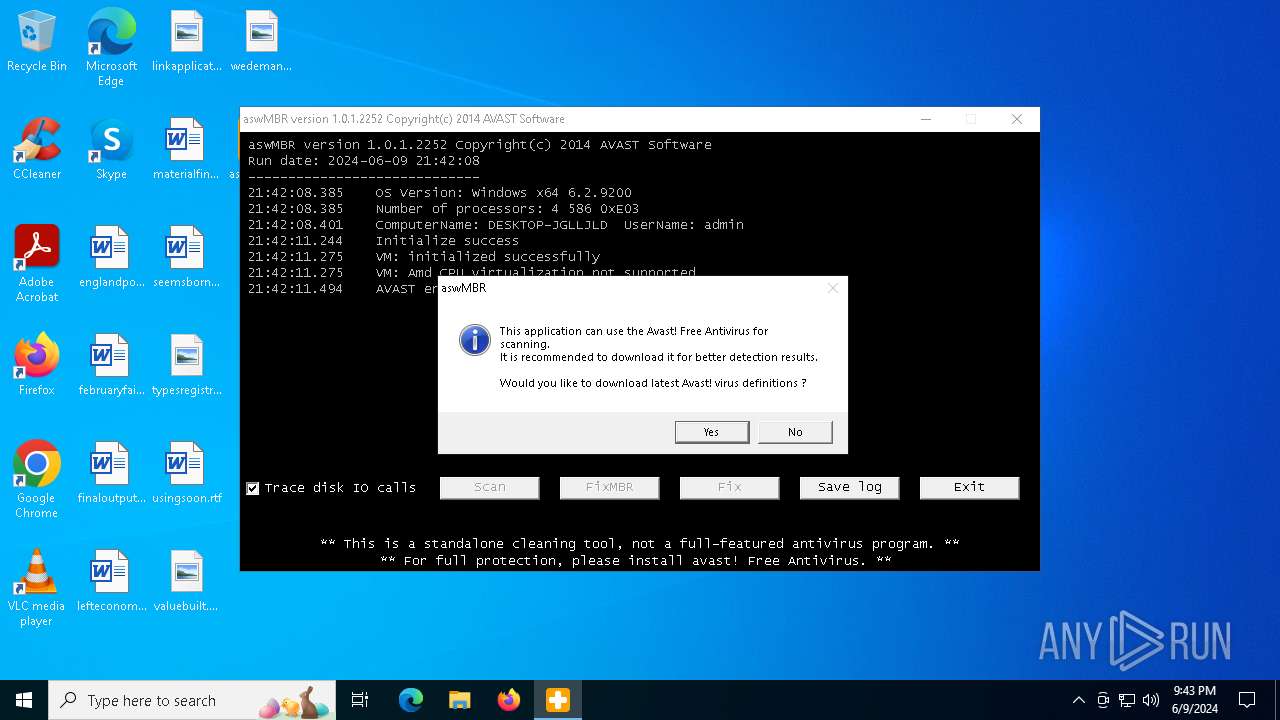
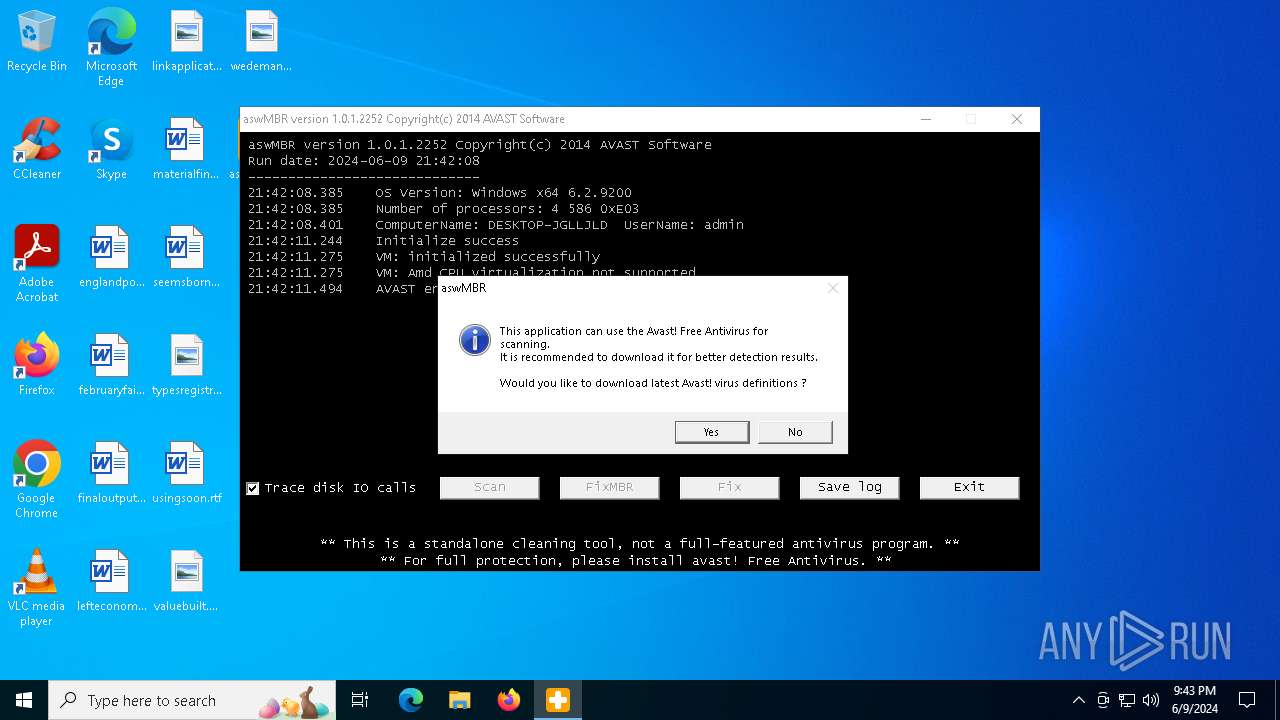
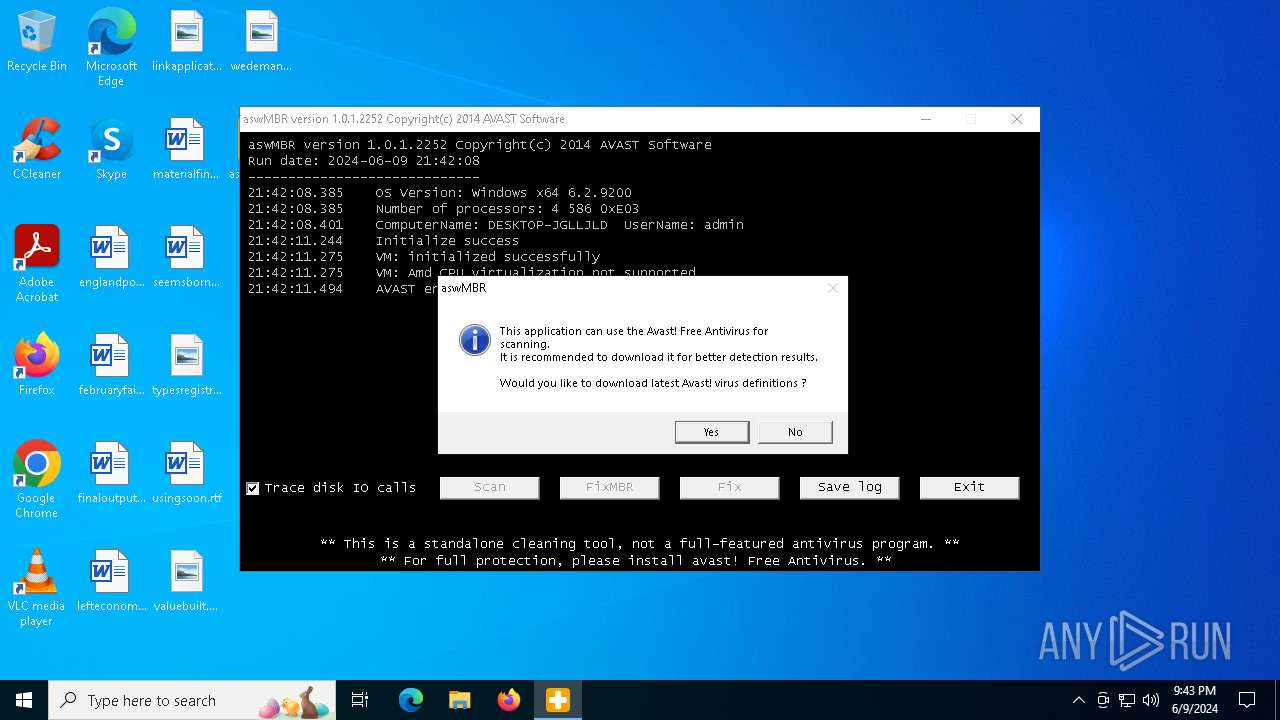
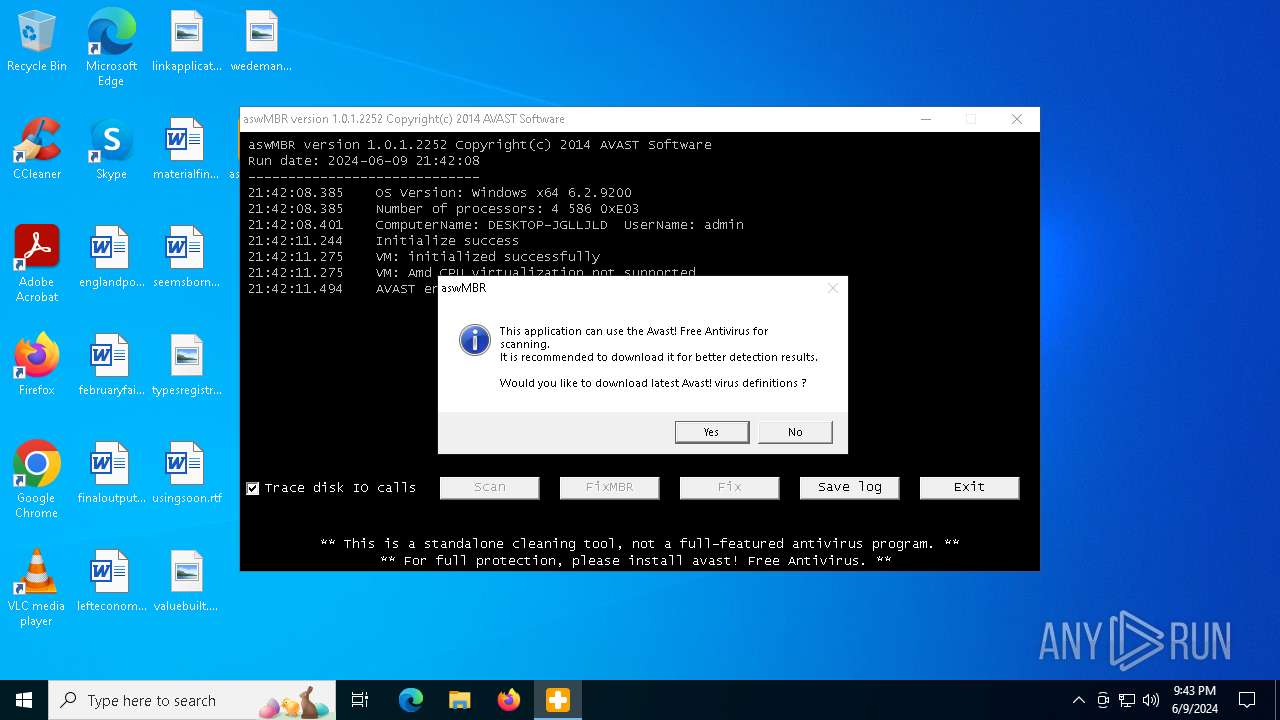
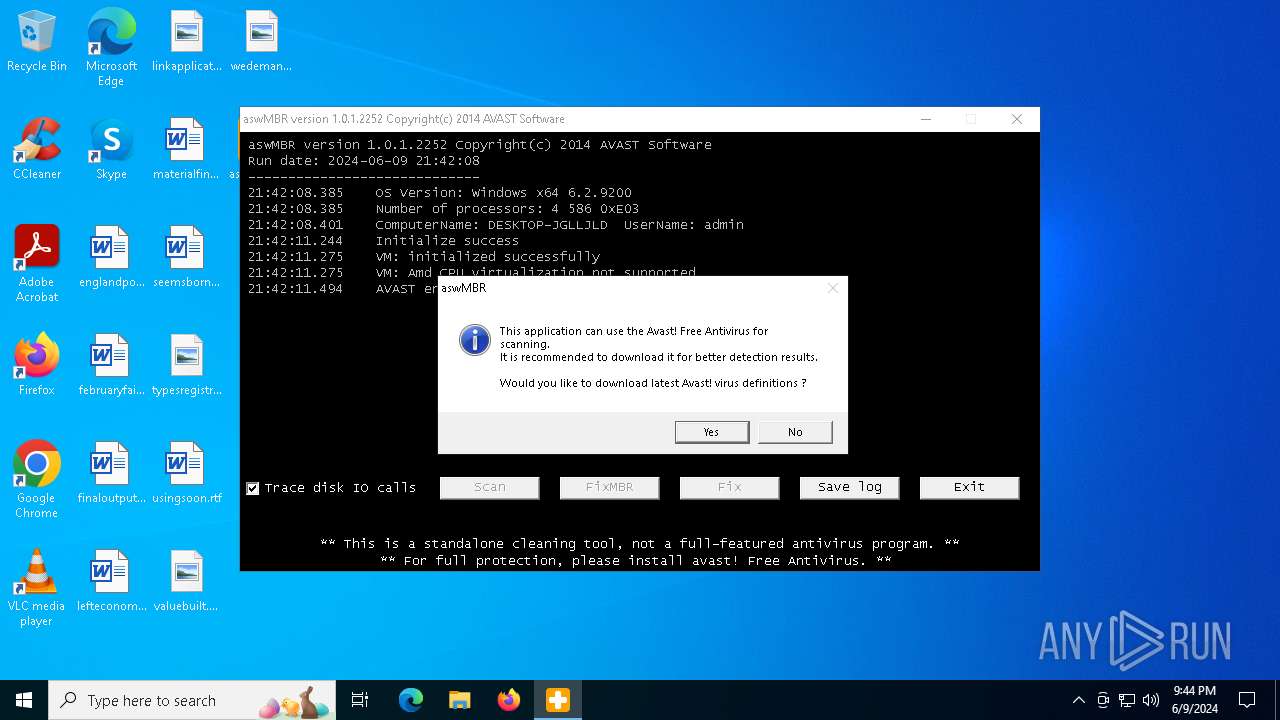
| File name: | aswMBR.exe |
| Full analysis: | https://app.any.run/tasks/9537ed5e-bf48-4479-912e-b9bb5c9f20fd |
| Verdict: | Malicious activity |
| Analysis date: | June 09, 2024, 21:41:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8E3384C7A0CF27B15D786E665CE74308 |
| SHA1: | D9AA0EF8013810FE52130CCC91CEBA16D7686CC6 |
| SHA256: | 3D212B0B8BE4D354150FF30B39A6349F7B6693A3021348D24A98FC3F8BABDB62 |
| SSDEEP: | 98304:MXPr6FwonZHZpdjD0+zNe7jsWi4IzcrPDuzGHi/rH6YdOfi8vWrVfhs/OEVRwxVA:708Y |
MALICIOUS
Drops the executable file immediately after the start
- aswMBR.exe (PID: 4080)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- aswMBR.exe (PID: 4080)
The process drops C-runtime libraries
- aswMBR.exe (PID: 4080)
Executable content was dropped or overwritten
- aswMBR.exe (PID: 4080)
Creates or modifies Windows services
- aswMBR.exe (PID: 4080)
Process drops legitimate windows executable
- aswMBR.exe (PID: 4080)
INFO
Checks supported languages
- aswMBR.exe (PID: 4080)
Create files in a temporary directory
- aswMBR.exe (PID: 4080)
Reads the computer name
- aswMBR.exe (PID: 4080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (23.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (22.3) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (16.8) |
| .exe | | | Win64 Executable (generic) (14.8) |
| .exe | | | UPX compressed Win32 Executable (14.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:11:14 08:16:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 459776 |
| InitializedDataSize: | 4748800 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4c31d |
| OSVersion: | 5 |
| ImageVersion: | 5 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.2252 |
| ProductVersionNumber: | 1.0.1.2252 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | AVAST Software |
| FileDescription: | avast! Antirootkit |
| FileVersion: | 1, 0, 1, 2252 |
| InternalName: | aswMBR.exe |
| LegalCopyright: | Copyright (c) 2010 AVAST Software. All rights reserved. |
| OriginalFileName: | aswMBR.exe |
| ProductName: | avast! Antirootkit |
| ProductVersion: | 1, 0, 1, 2252 |
Total processes
116
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3700 | "C:\Users\admin\Desktop\aswMBR.exe" | C:\Users\admin\Desktop\aswMBR.exe | — | explorer.exe | |||||||||||
User: admin Company: AVAST Software Integrity Level: MEDIUM Description: avast! Antirootkit Exit code: 3221226540 Version: 1, 0, 1, 2252 Modules
| |||||||||||||||
| 4080 | "C:\Users\admin\Desktop\aswMBR.exe" | C:\Users\admin\Desktop\aswMBR.exe | explorer.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: HIGH Description: avast! Antirootkit Version: 1, 0, 1, 2252 Modules
| |||||||||||||||
Total events
224
Read events
214
Write events
10
Delete events
0
Modification events
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswMBR |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswMBR |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswMBR |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswMBR |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Users\admin\AppData\Local\Temp\aswMBR.sys | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswMBR |
| Operation: | write | Name: | Group |
Value: Base | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswVmm |
| Operation: | write | Name: | Type |
Value: 1 | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswVmm |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswVmm |
| Operation: | write | Name: | Start |
Value: 3 | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswVmm |
| Operation: | write | Name: | ImagePath |
Value: \??\C:\Users\admin\AppData\Local\Temp\aswVmm.sys | |||
| (PID) Process: | (4080) aswMBR.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\aswVmm |
| Operation: | write | Name: | Group |
Value: Base | |||
Executable files
16
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\aswMBR.sys | executable | |
MD5:AE358AA704ED7BD4A592053426237065 | SHA256:3507BA0C32B6EBBACBDDD46D6A65309D75A6926243B6A78B406F5514C32AA120 | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\aswCmnS.dll | executable | |
MD5:13EEB998A123530809BFBC16A6BE580E | SHA256:947EE660EAB27FB77B982073A28EEC1C1099E8018193CCD32F177A4976E1D852 | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\msvcp71.dll | executable | |
MD5:561FA2ABB31DFA8FAB762145F81667C2 | SHA256:DF96156F6A548FD6FE5672918DE5AE4509D3C810A57BFFD2A91DE45A3ED5B23B | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\ashBase.dll | executable | |
MD5:54C458A07FA6D44EE640777013E92A15 | SHA256:CE2795E25220EA2D147A7AA96372A5B3E6DB44569B2044AEA74C25EF40758718 | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\ashSXML.dll | executable | |
MD5:ACA1DF15A75F066837525FAEA5E2BE46 | SHA256:708BC1BC8864A12E575E3A5068F2913ACA666757293FEE4D1DCBB73A8BBDC0C8 | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\aswCmnOS.dll | executable | |
MD5:01033EDA5F63E4BA48C25099CE9D6BDD | SHA256:FF511070EFAD9FA5E3273FF06289C904E0A4F9491A802AB8153B09FB7A81E5B2 | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\data\Avast4.ini | ini | |
MD5:6623F79B5E704BAA8DFA6952F52D4DBB | SHA256:AD99D9412F3B82B8B102E34000ECFBD06223536014D22462BC29CE2E815BCDAE | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\msvcr71.dll | executable | |
MD5:86F1895AE8C5E8B17D99ECE768A70732 | SHA256:8094AF5EE310714CAEBCCAEEE7769FFB08048503BA478B879EDFEF5F1A24FEFE | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\_av4_\english\Base.dll | executable | |
MD5:55A3768099D89870A77BC93CB37E08B4 | SHA256:B59BEC05FC740465254E434CE3E89E38079A7DAAD93973F9086011228738B2F3 | |||
| 4080 | aswMBR.exe | C:\Users\admin\AppData\Local\Temp\aswVmm.sys | executable | |
MD5:A6542A6E95461458FD386D4A40417F31 | SHA256:5073CAF44064F7716F68A2803DA57B1C75F39A45D8F8DEC72A14080320BE05BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5228 | svchost.exe | GET | 200 | 95.100.242.144:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1964 | RUXIMICS.exe | GET | 200 | 95.100.242.144:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 95.100.242.144:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5228 | svchost.exe | GET | 200 | 23.200.213.221:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1964 | RUXIMICS.exe | GET | 200 | 23.200.213.221:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | POST | 200 | 20.189.173.28:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
5228 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1964 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5228 | svchost.exe | 95.100.242.144:80 | crl.microsoft.com | Akamai International B.V. | IT | unknown |
1964 | RUXIMICS.exe | 95.100.242.144:80 | crl.microsoft.com | Akamai International B.V. | IT | unknown |
5140 | MoUsoCoreWorker.exe | 95.100.242.144:80 | crl.microsoft.com | Akamai International B.V. | IT | unknown |
1964 | RUXIMICS.exe | 23.200.213.221:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
5228 | svchost.exe | 23.200.213.221:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |