| File name: | 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn |
| Full analysis: | https://app.any.run/tasks/c0c08e41-5555-4c52-93f2-54d855d32966 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 04:02:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | D90F03BE6A4DE6636FA9719865A4213C |
| SHA1: | 3BCF4948358379CE2EBAD3314F49D6BC99D47E03 |
| SHA256: | 3CEB25B665734B851238C0B926E35889471DFC578AFA96E529BF1EFCD4D8C5F6 |
| SSDEEP: | 6144:i0/1Thw5w4qjPRrf2VrRZHMrbLcPNot2IuaJEM/Jt1zJR+c0mbOoDTdu1hVs9zEh:5cPNot2IuaJEiH+cBdDZu1hVR4k |
MALICIOUS
JEEFO has been detected
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
- icsys.icn.exe (PID: 7524)
- explorer.exe (PID: 7544)
- svchost.exe (PID: 7604)
Changes the autorun value in the registry
- explorer.exe (PID: 7544)
- svchost.exe (PID: 7604)
SUSPICIOUS
Starts application with an unusual extension
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
Executable content was dropped or overwritten
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
- icsys.icn.exe (PID: 7524)
- explorer.exe (PID: 7544)
- spoolsv.exe (PID: 7580)
Starts itself from another location
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
- icsys.icn.exe (PID: 7524)
- explorer.exe (PID: 7544)
- spoolsv.exe (PID: 7580)
- svchost.exe (PID: 7604)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 7524)
- spoolsv.exe (PID: 7580)
Creates or modifies Windows services
- svchost.exe (PID: 7604)
INFO
The sample compiled with english language support
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
Create files in a temporary directory
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
- icsys.icn.exe (PID: 7524)
- explorer.exe (PID: 7544)
- spoolsv.exe (PID: 7672)
- spoolsv.exe (PID: 7580)
- svchost.exe (PID: 7604)
Checks supported languages
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7480)
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7456)
- icsys.icn.exe (PID: 7524)
- explorer.exe (PID: 7544)
- spoolsv.exe (PID: 7580)
- spoolsv.exe (PID: 7672)
- svchost.exe (PID: 7604)
Reads the machine GUID from the registry
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7480)
Reads the computer name
- 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe (PID: 7480)
- svchost.exe (PID: 7604)
Auto-launch of the file from Registry key
- svchost.exe (PID: 7604)
- explorer.exe (PID: 7544)
Manual execution by a user
- explorer.exe (PID: 7832)
- svchost.exe (PID: 7816)
Checks proxy server information
- slui.exe (PID: 5512)
Reads the software policy settings
- slui.exe (PID: 5512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
140
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5512 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7352 | "C:\Users\admin\Desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe" | C:\Users\admin\Desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7456 | "C:\Users\admin\Desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe" | C:\Users\admin\Desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
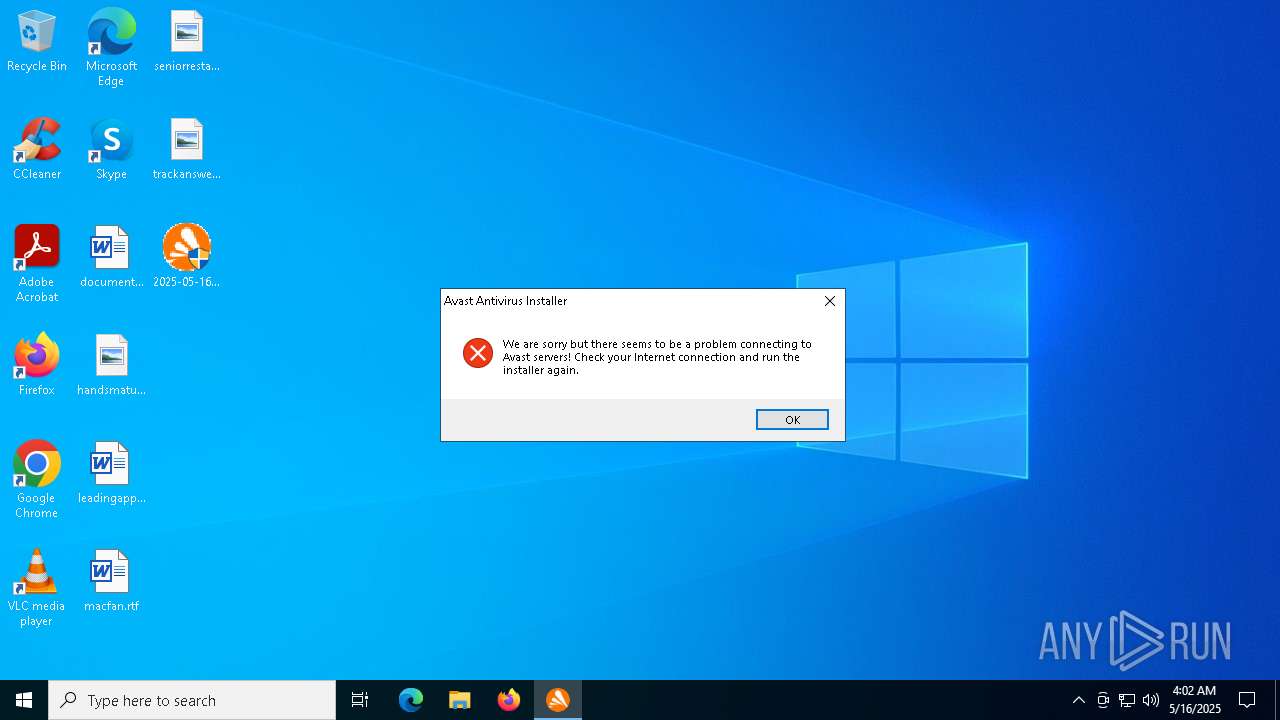
| 7480 | c:\users\admin\desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | C:\Users\admin\Desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | — | 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | |||||||||||
User: admin Company: Gen Digital Inc. Integrity Level: HIGH Description: Avast Installer Version: 2.1.133.0 Modules
| |||||||||||||||
| 7524 | C:\Windows\Resources\Themes\icsys.icn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7544 | c:\windows\resources\themes\explorer.exe | C:\Windows\Resources\Themes\explorer.exe | icsys.icn.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 7580 | c:\windows\resources\spoolsv.exe SE | C:\Windows\Resources\spoolsv.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7604 | c:\windows\resources\svchost.exe | C:\Windows\Resources\svchost.exe | spoolsv.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 7672 | c:\windows\resources\spoolsv.exe PR | C:\Windows\Resources\spoolsv.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 7816 | c:\windows\resources\svchost.exe RO | C:\Windows\Resources\svchost.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
Total events
3 789
Read events
3 770
Write events
15
Delete events
4
Modification events
| (PID) Process: | (7544) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7544) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7544) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7544) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (7456) 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7524) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7604) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7604) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7604) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7604) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
5
Suspicious files
4
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7524 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:6405C677302B0BD503CBB91985AF6928 | SHA256:F0F83BE3AF1C7A0EE96AD6806A27AA2E3EFE0A524067540BDA732FAD50C5216E | |||
| 7580 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:50F70905A78CB9E172C387CC38169089 | SHA256:43BD9D5C46440D30E9F87C5B384073C1999E685525A91F9EF6651F31316D10BE | |||
| 7580 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF6EBD2BDD1A226C0A.TMP | binary | |
MD5:BA44DB6F7E803A8A4E5B6AB400EF0612 | SHA256:4C167A83965B3C1E313D53B8720A8E4D1C9F9A3DEAF7A1ED7FEE72211EC7E899 | |||
| 7672 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF36D448FAFF8F2E84.TMP | binary | |
MD5:27FC3D13A21934370646713ECFA51B3E | SHA256:81A59EEAFF8175CE4F6FA91B88F2E0CD8091FAA72C795B33ED4AE8DD3918EAD5 | |||
| 7544 | explorer.exe | C:\Windows\Resources\spoolsv.exe | executable | |
MD5:746B9EC9A5A7AF20F372D8266800BD12 | SHA256:2D724ED54B30EB6162C23D50C584E29726D6176E425EBCEF8FE8FFD863E4888D | |||
| 7456 | 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | C:\Users\admin\AppData\Local\Temp\~DF4B83477FAC5CA783.TMP | binary | |
MD5:4EBE01ABDEE0FD2E25A9E76B62D89315 | SHA256:926BDEF0998B39026E532950492743D9D14C74F051199888129B7C04C9C0D714 | |||
| 7456 | 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:987BD60EC86C5D423DEF793E9FD2FB9C | SHA256:D2DBB543D265C4DABC69A9FD3FA2B7894E2F3076BE8A6375D9C2F6CFC36F058F | |||
| 7456 | 2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | C:\Users\admin\Desktop\2025-05-16_d90f03be6a4de6636fa9719865a4213c_amadey_black-basta_cobalt-strike_elex_luca-stealer_swisyn.exe | executable | |
MD5:15027411FC70283A0134DE5A57540C57 | SHA256:28E8B02EFE16C0FA7B085AB24976AA6C313403DC4C7BFD0C8AAFEDE2CB4EA5D8 | |||
| 7524 | icsys.icn.exe | C:\Users\admin\AppData\Local\Temp\~DFC6F26D38DCFC89BD.TMP | binary | |
MD5:B921D562F736781E70B0EA0E0AA20B83 | SHA256:B79EB1C17A07902884CE15548F7E2AAC1FD73B458D10561345F464152E146295 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
50
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6708 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6708 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8088 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6708 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6708 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6708 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |