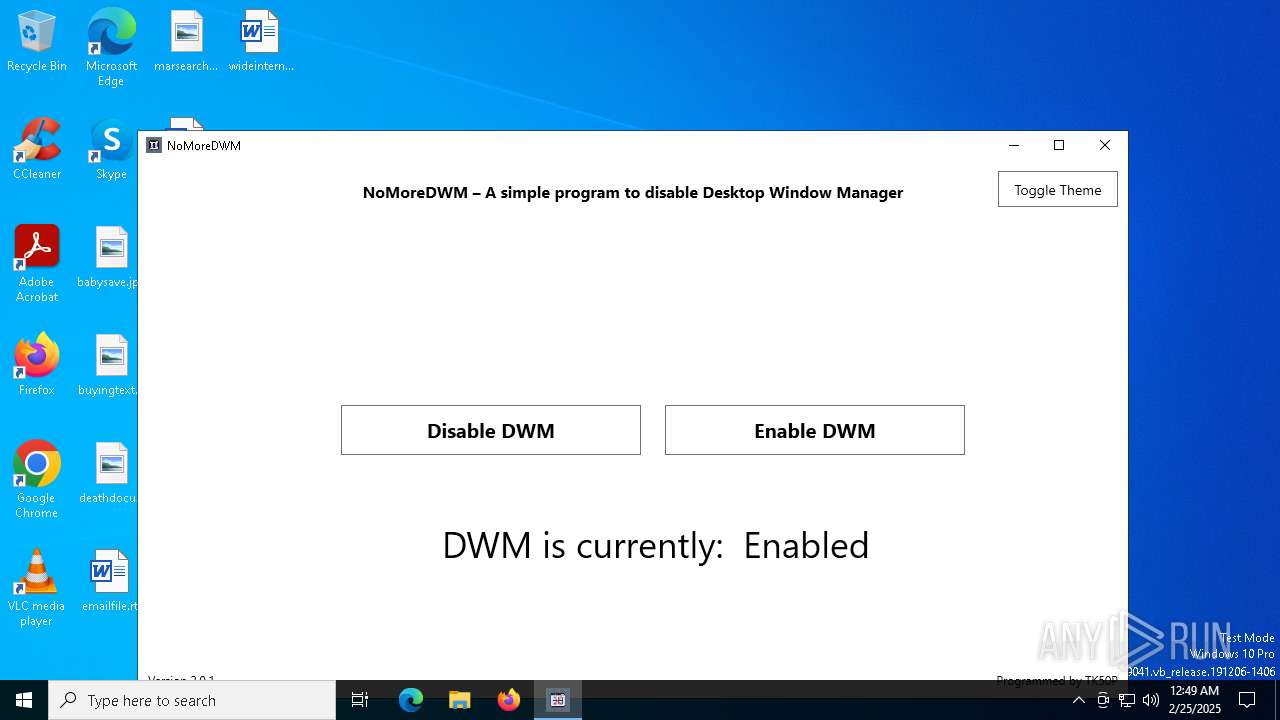
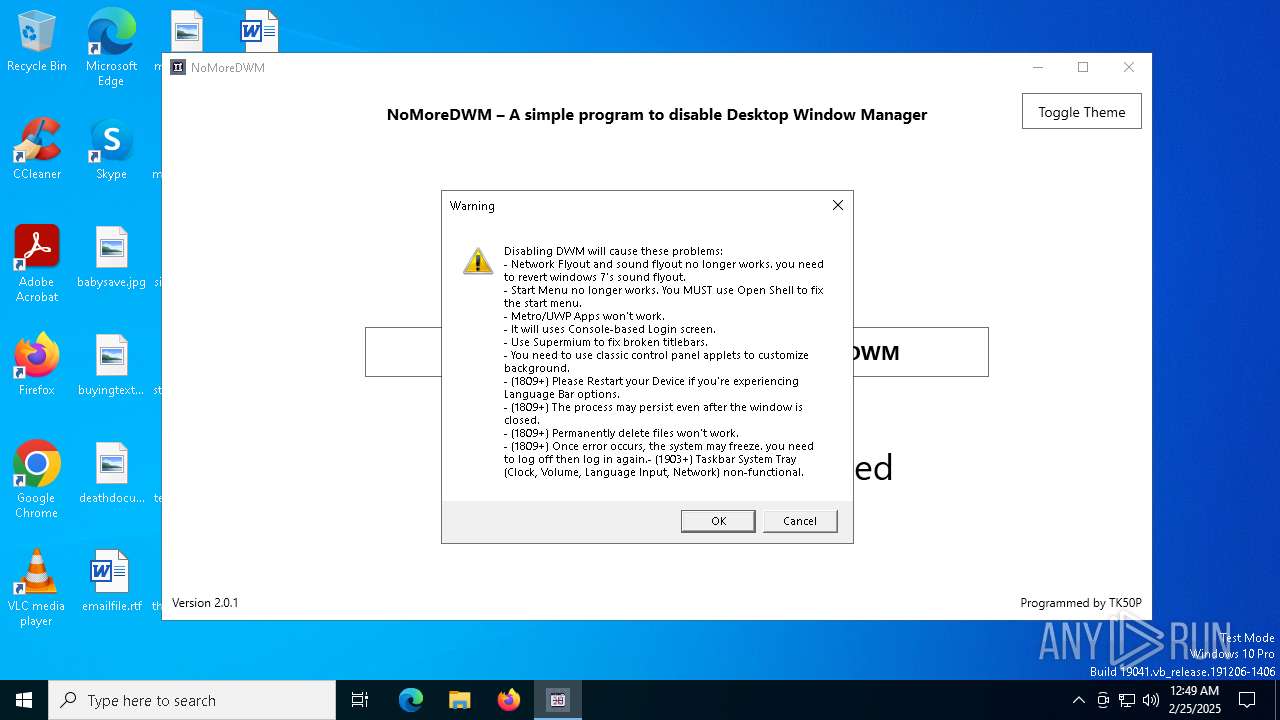
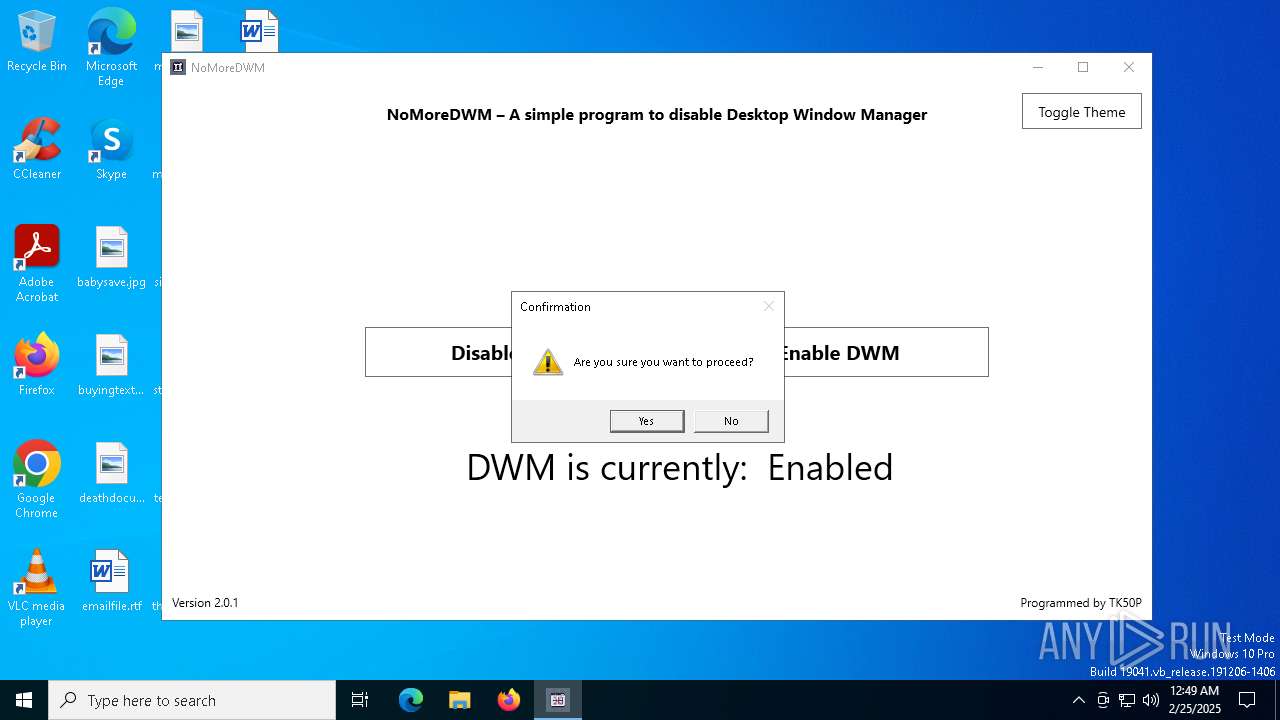
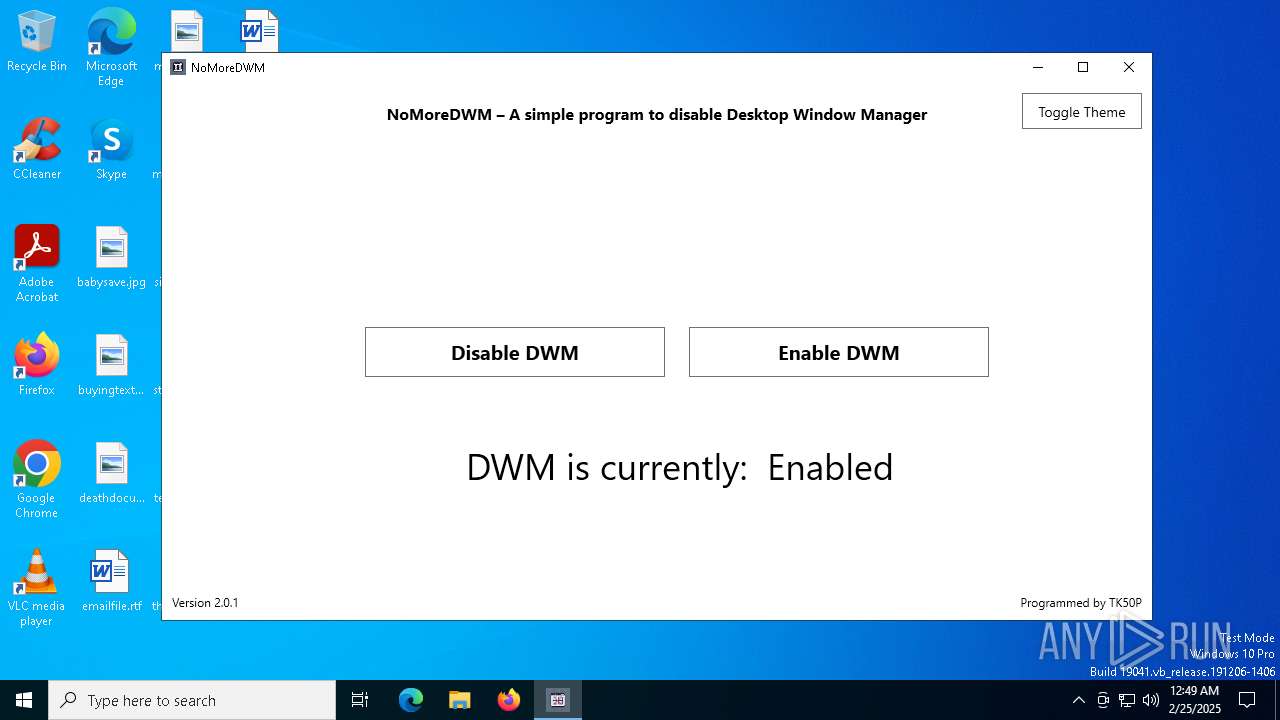
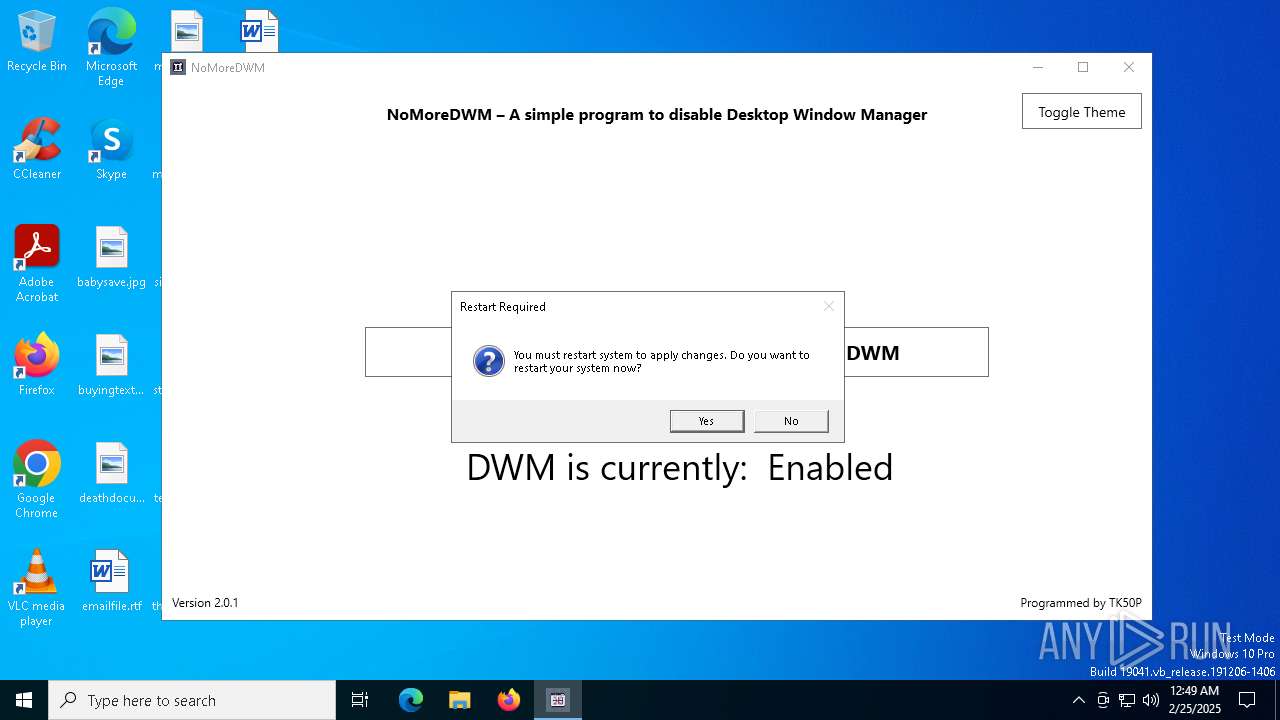
| download: | /TK50P/NoMoreDWM/releases/download/v2.0.1/NoMoreDWM.exe |
| Full analysis: | https://app.any.run/tasks/34bed1f7-a016-498c-a1f4-9e5a80ba4c78 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2025, 00:49:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 0BF119255915A986AF6D6EB307195DB3 |
| SHA1: | 72CBEFFF62F3EB276B003DFB8CD5A6C31B7EEE29 |
| SHA256: | 3CCBE205977B4CBF55913593A0F6930CE36A4C5837282F4CB57E55427AE0B99F |
| SSDEEP: | 6144:Fb2hbTkk77k7aRpwNbBN9OybTkk77k7aRpwNbBN9Ot:chbQk77k+RCNnMybQk77k+RCNnMt |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- cmd.exe (PID: 7032)
- cmd.exe (PID: 2008)
Executable content was dropped or overwritten
- cmd.exe (PID: 2008)
- cmd.exe (PID: 7032)
Reads security settings of Internet Explorer
- NoMoreDWM.exe (PID: 6444)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7032)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7032)
- NoMoreDWM.exe (PID: 6444)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7032)
Application launched itself
- cmd.exe (PID: 7032)
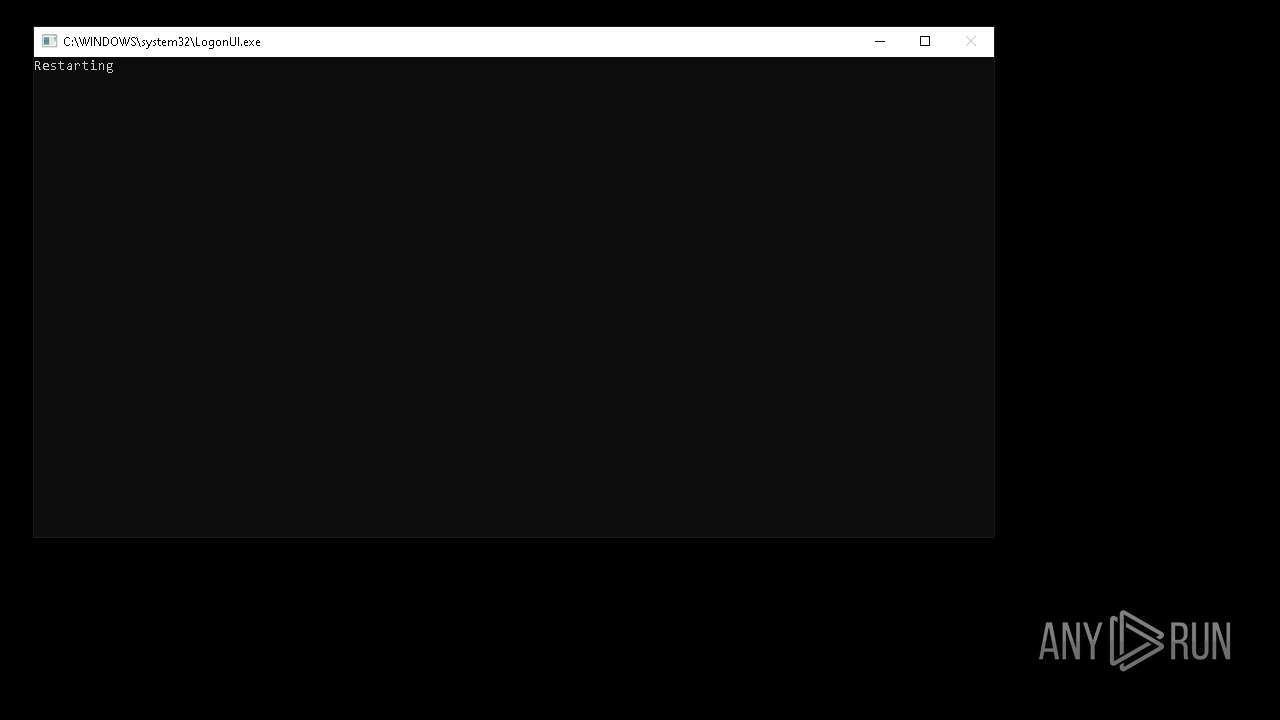
The system shut down or reboot
- NoMoreDWM.exe (PID: 6444)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 3904)
Reads the date of Windows installation
- NoMoreDWM.exe (PID: 6444)
Executing commands from a ".bat" file
- NoMoreDWM.exe (PID: 6444)
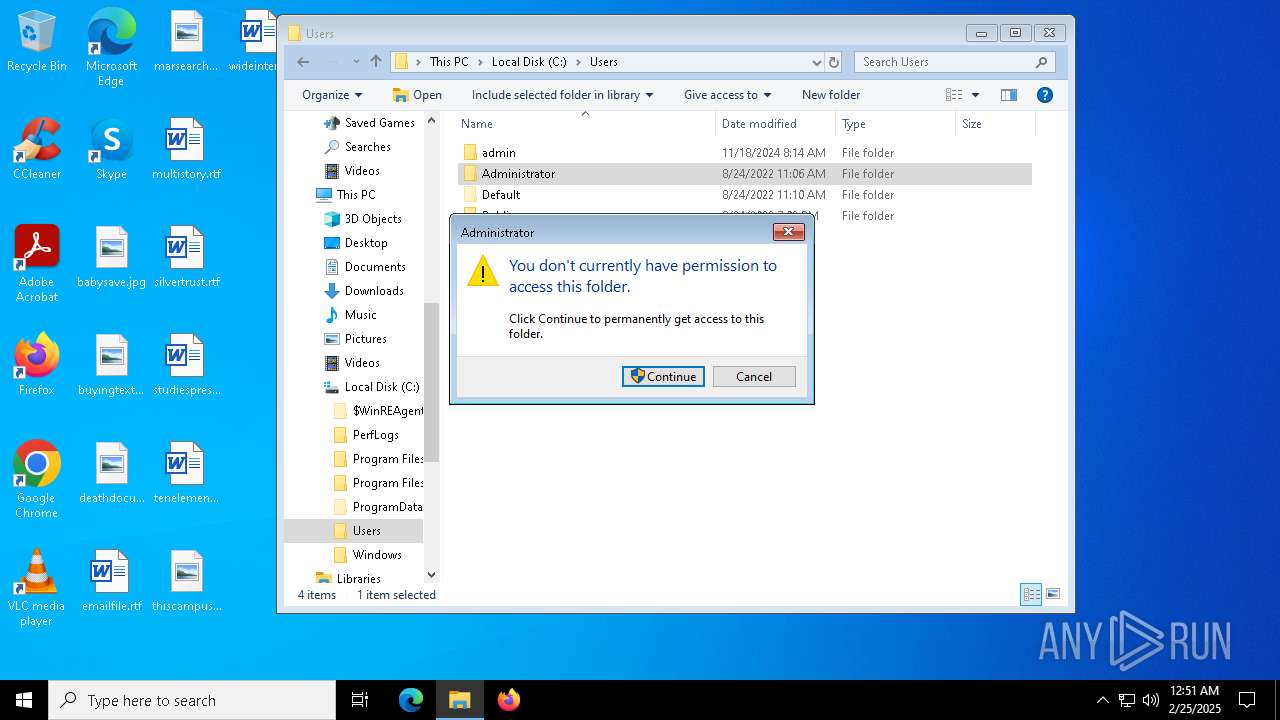
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 7032)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 7032)
INFO
Create files in a temporary directory
- NoMoreDWM.exe (PID: 6444)
Reads the computer name
- NoMoreDWM.exe (PID: 6444)
- PLUGScheduler.exe (PID: 3904)
- NoMoreDWM.exe (PID: 5680)
Checks supported languages
- NoMoreDWM.exe (PID: 6444)
- PLUGScheduler.exe (PID: 3904)
- NoMoreDWM.exe (PID: 5680)
Reads the machine GUID from the registry
- NoMoreDWM.exe (PID: 6444)
- NoMoreDWM.exe (PID: 5680)
Process checks computer location settings
- NoMoreDWM.exe (PID: 6444)
Creates files in the program directory
- PLUGScheduler.exe (PID: 3904)
The sample compiled with english language support
- cmd.exe (PID: 2008)
- cmd.exe (PID: 7032)
Manual execution by a user
- NoMoreDWM.exe (PID: 5588)
- NoMoreDWM.exe (PID: 5680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2055:06:01 20:42:54+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 189440 |
| InitializedDataSize: | 115200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x302a2 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | NoMoreDWM |
| FileVersion: | 1.0.0.0 |
| InternalName: | NoMoreDWM.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | NoMoreDWM.exe |
| ProductName: | NoMoreDWM |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
273
Monitored processes
39
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | takeown /F C:\WINDOWS\System32\dwm.exe /A | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | icacls C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy /grant Administrators:(F) /T | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | takeown /F C:\WINDOWS\System32\UiRibbonRes.dll /A | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | C:\WINDOWS\system32\cmd.exe /S /D /c" copy/-Y "C:\WINDOWS\System32\rundll32.exe" "C:\WINDOWS\System32\dwm.exe"" | C:\Windows\System32\cmd.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2380 | taskkill /F /IM RuntimeBroker.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo N" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2736 | icacls C:\WINDOWS\System32\UiRibbon.dll /grant Administrators:(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3508 | icacls C:\WINDOWS\System32\dwm.exe /grant Administrators:(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | icacls C:\WINDOWS\System32\UIRibbonRes.dll /grant Administrators:(F) | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3808 | takeown /F C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy /R /A | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 196
Read events
2 189
Write events
7
Delete events
0
Modification events
| (PID) Process: | (6444) NoMoreDWM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6444) NoMoreDWM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
| (PID) Process: | (6012) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | AltTabSettings |
Value: 0 | |||
| (PID) Process: | (6508) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\TestHooks |
| Operation: | write | Name: | ConsoleMode |
Value: 1 | |||
| (PID) Process: | (6488) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI\TestHooks |
| Operation: | write | Name: | XamlCredUIAvailable |
Value: 0 | |||
| (PID) Process: | (5680) NoMoreDWM.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Left |
Value: 0 | |||
| (PID) Process: | (5680) NoMoreDWM.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\CTF\CUAS\DefaultCompositionWindow |
| Operation: | write | Name: | Top |
Value: 0 | |||
Executable files
6
Suspicious files
38
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3904 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.038.etl | binary | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 7032 | cmd.exe | C:\Windows\System32\dwm.exe.old | executable | |
MD5:C8B1DADBE021E9EC3117036496183FE3 | SHA256:8C2B5D9628BD615C09050B1BC3FD5874045CB037652CB2842A5E25CB1EB9DFBE | |||
| 6444 | NoMoreDWM.exe | C:\Users\admin\AppData\Local\Temp\DisableDWM.bat | text | |
MD5:EF81533A5FA6E4A177F9AFF19541913F | SHA256:DA57F47E2DA4B1F71C80D5AF1DBFF47714C310C755C26D358AFE34034B15E245 | |||
| 7032 | cmd.exe | C:\Windows\System32\windows.immersiveshell.serviceprovider.dll.old | executable | |
MD5:852219DDA6D42FFC101AFECE286B61E0 | SHA256:9C1E80C1B56185152D2FD2F6060916CBC0446866294592D021C1F16813D72AEE | |||
| 7032 | cmd.exe | C:\Windows\System32\Windows.UI.Logon.dll.old | executable | |
MD5:7DA4C534DC7A5A82923B25C24F8A3C73 | SHA256:F5D0FF9203DBE362CE25CFC08409CCFC758F7E618FF32D564B7AC90F06408CB4 | |||
| 3904 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:673727AF7C6805E869C9F8BE1E468F4A | SHA256:6B16B7DE97F397BCEC36EB3F18C7B64CD3DB6D2974DDF319A251CE27B80D837B | |||
| 2008 | cmd.exe | C:\Windows\System32\dwm.exe | executable | |
MD5:100F56A73211E0B2BCD076A55E6393FD | SHA256:00BE065F405E93233CC2F0012DEFDCBB1D6817B58969D5FFD9FD72FC4783C6F4 | |||
| 3904 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.041.etl | binary | |
MD5:44A0E917AD0C126931B1BCD959285A9A | SHA256:DDFBE47E7DFD6D8B7517F2F6FF9808ECF3C0A25F588A9F96D04F4E2B4A578573 | |||
| 3904 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.044.etl | binary | |
MD5:079890A8EC8D5CB6523FCEC2209780AA | SHA256:0E12D2D76DD738CE196BED522E35F75E2CC91294F78CDDCBE8CE7787AAA70049 | |||
| 3904 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:2F36C598EBFF5B5CDD898C9691D6BCCB | SHA256:8900C5931ED8E0D1B68082B45CF2F4E8C1025D36825508E0804C916D781B9F50 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
45
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6644 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1356 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1356 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4424 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5776 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1200 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3976 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |