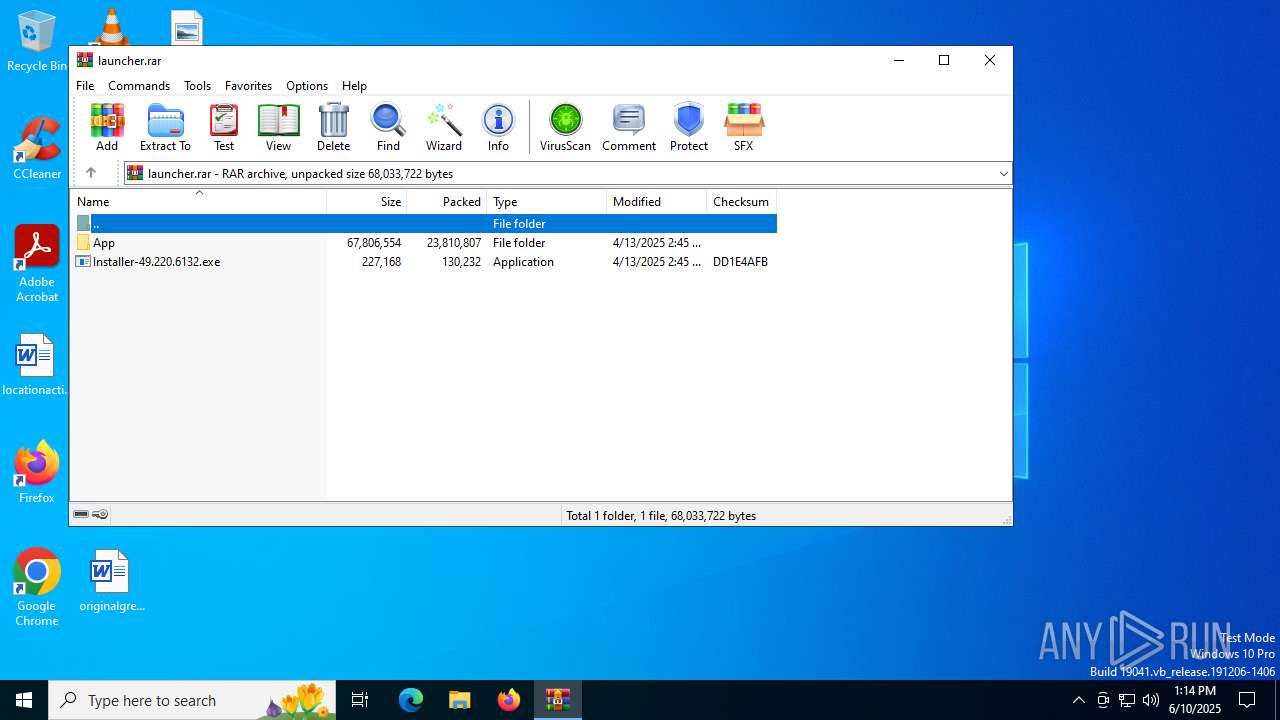
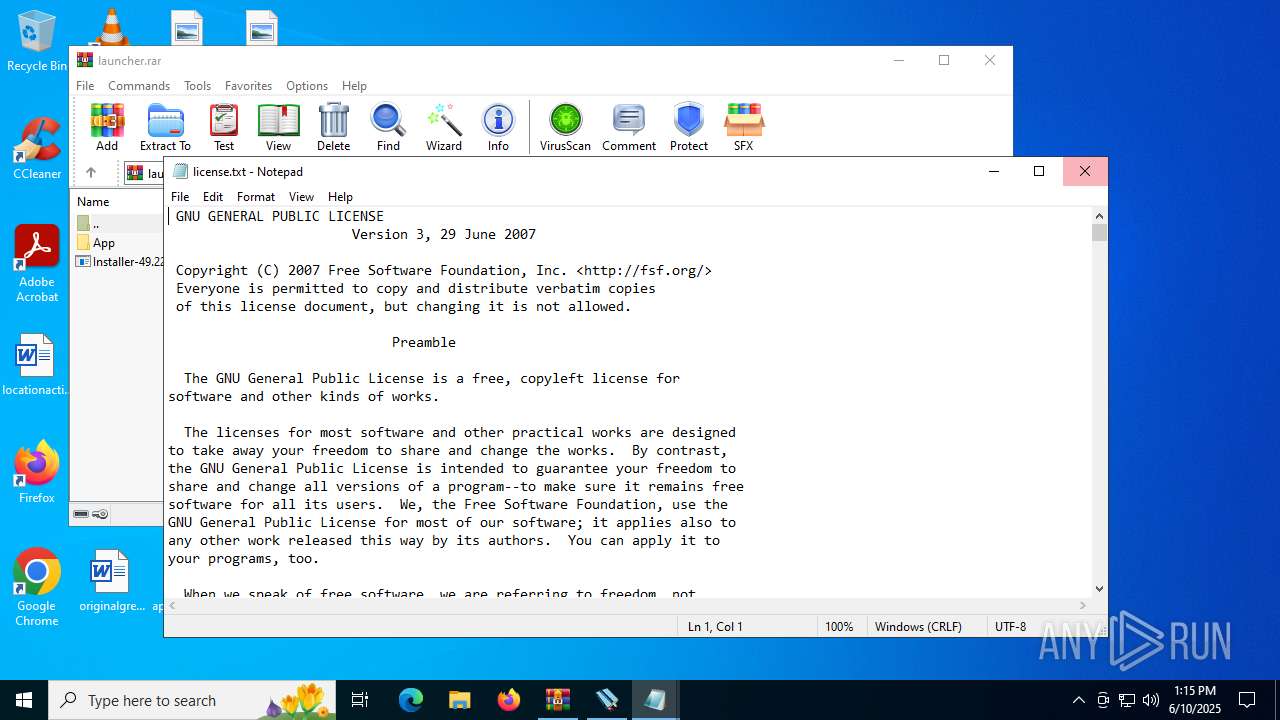
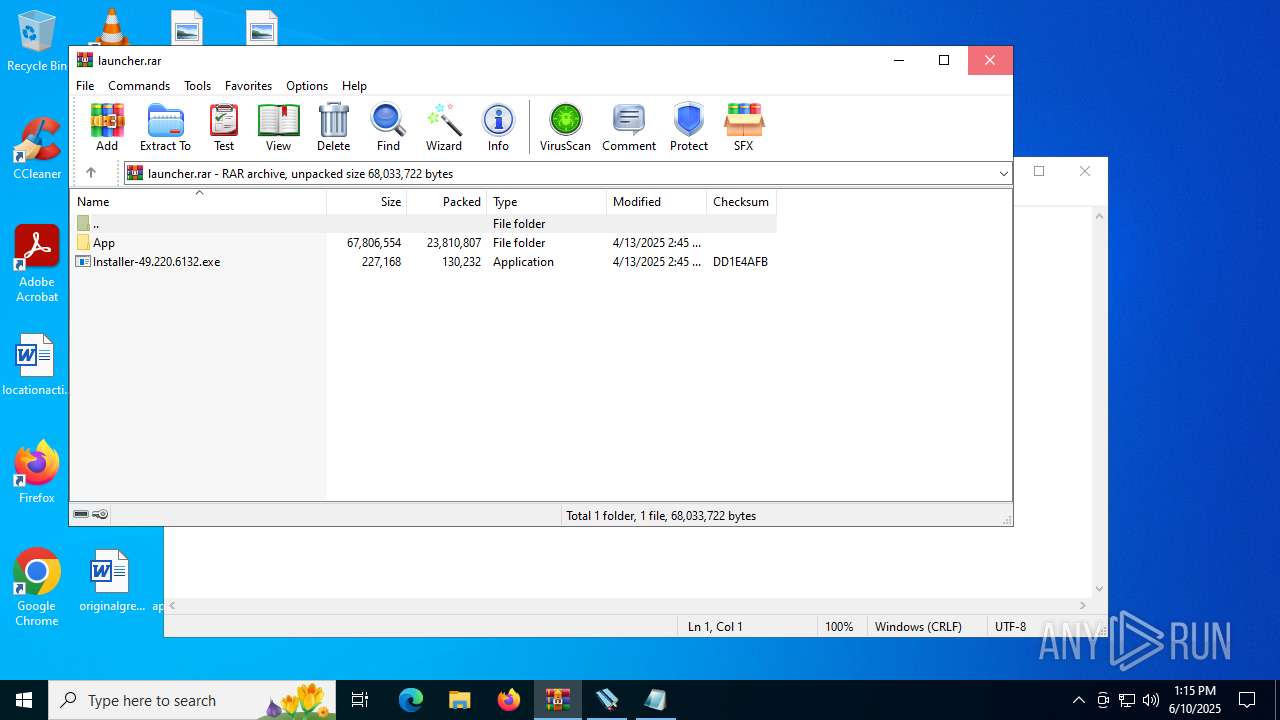
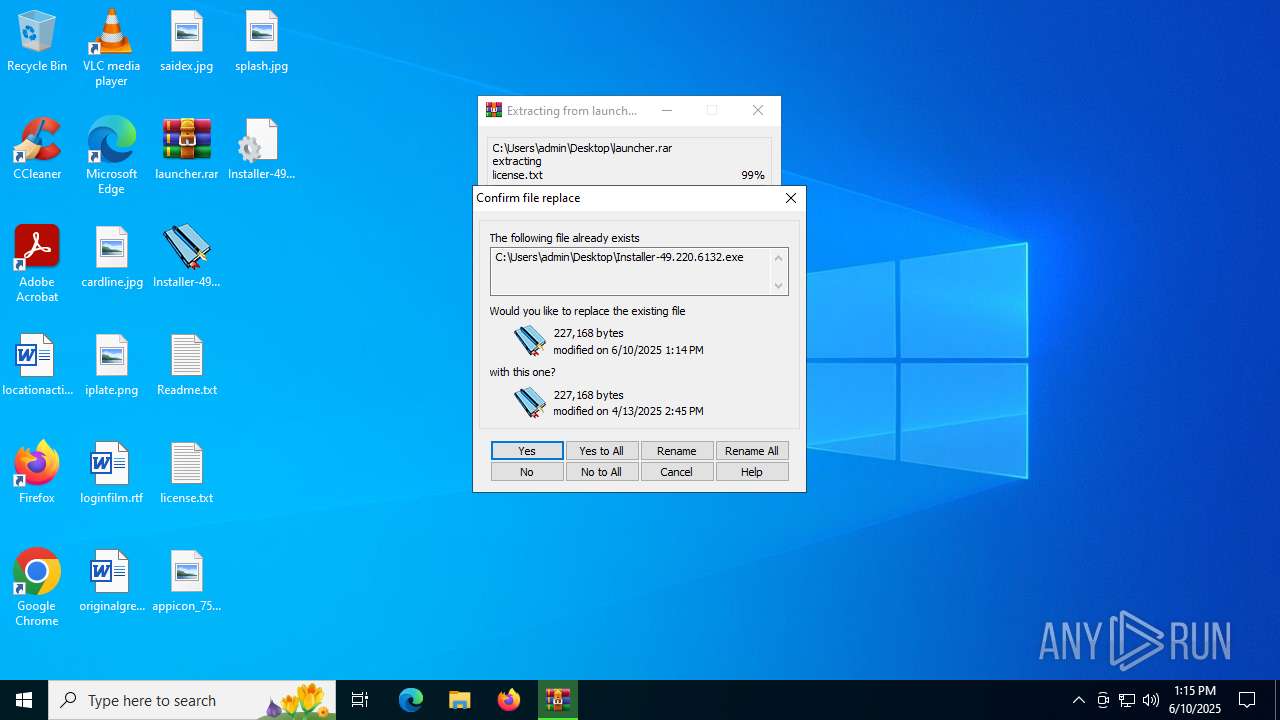
| File name: | launcher.rar |
| Full analysis: | https://app.any.run/tasks/331b6289-841e-499c-b8a5-846cb00605f0 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2025, 13:14:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 03664FA60EABED6180FD0A02BD5E06E1 |
| SHA1: | 0E64574DF8BDEB0213C090BE35D22DB529763BB9 |
| SHA256: | 3CBC4A0C2F0714959A4B972B0DF38F33E76C18153A3F9C4D5544232B82F6778B |
| SSDEEP: | 196608:eC8wgsBk0afJ7mj5pLjQ7GKwgOFV698nk4XcVlDZtnbrfgnNm9v:eC8Lz0EJk5pLjQ7Wj3nkhttvfgnQ |
MALICIOUS
Executing a file with an untrusted certificate
- Installer-49.220.6132.exe (PID: 2212)
- Installer-49.220.6132.exe (PID: 4576)
Generic archive extractor
- WinRAR.exe (PID: 1604)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Installer-49.220.6132.exe (PID: 2212)
The process creates files with name similar to system file names
- Installer-49.220.6132.exe (PID: 4576)
Starts POWERSHELL.EXE for commands execution
- Installer.49.220.6132.exe (PID: 1896)
Malware-specific behavior (creating "System.dll" in Temp)
- Installer-49.220.6132.exe (PID: 4576)
Reads security settings of Internet Explorer
- Installer-49.220.6132.exe (PID: 4576)
Executable content was dropped or overwritten
- Installer-49.220.6132.exe (PID: 4576)
Possibly malicious use of IEX has been detected
- Installer.49.220.6132.exe (PID: 1896)
INFO
Checks supported languages
- Installer-49.220.6132.exe (PID: 2212)
- Installer.49.220.6132.exe (PID: 1896)
- Installer-49.220.6132.exe (PID: 4576)
Create files in a temporary directory
- Installer-49.220.6132.exe (PID: 2212)
- Installer-49.220.6132.exe (PID: 4576)
Manual execution by a user
- Installer-49.220.6132.exe (PID: 2212)
- notepad.exe (PID: 7004)
- notepad.exe (PID: 5532)
- rundll32.exe (PID: 620)
- rundll32.exe (PID: 1132)
- notepad.exe (PID: 2188)
- WinRAR.exe (PID: 2028)
- Installer-49.220.6132.exe (PID: 4576)
Reads the computer name
- Installer-49.220.6132.exe (PID: 2212)
- Installer-49.220.6132.exe (PID: 4576)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7004)
- notepad.exe (PID: 5532)
- notepad.exe (PID: 2188)
- rundll32.exe (PID: 1132)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 1132)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2028)
Creates files in the program directory
- Installer.49.220.6132.exe (PID: 1896)
Disables trace logs
- powershell.exe (PID: 4800)
Checks proxy server information
- powershell.exe (PID: 4800)
- slui.exe (PID: 4760)
Reads the software policy settings
- slui.exe (PID: 4760)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 23702139 |
| UncompressedSize: | 67532316 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | App/AppData/Installer.49.220.6132.exe |
Total processes
154
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\appicon_75.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\splash.jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\launcher.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1700 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1896 | "C:\Users\admin\Desktop\App\AppData\Installer.49.220.6132.exe" | C:\Users\admin\Desktop\App\AppData\Installer.49.220.6132.exe | — | Installer-49.220.6132.exe | |||||||||||
User: admin Company: ConsoleApp1 Integrity Level: MEDIUM Description: ConsoleApp1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\launcher.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2188 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Installer-49.220.6132.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
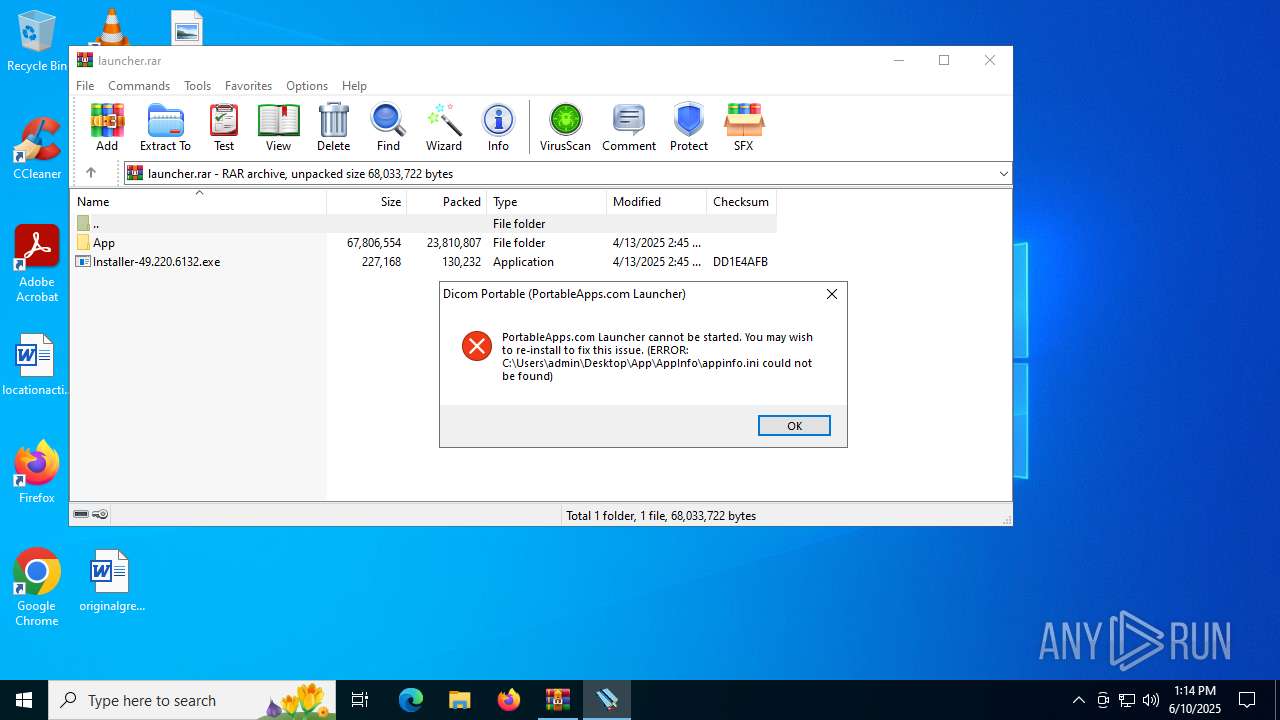
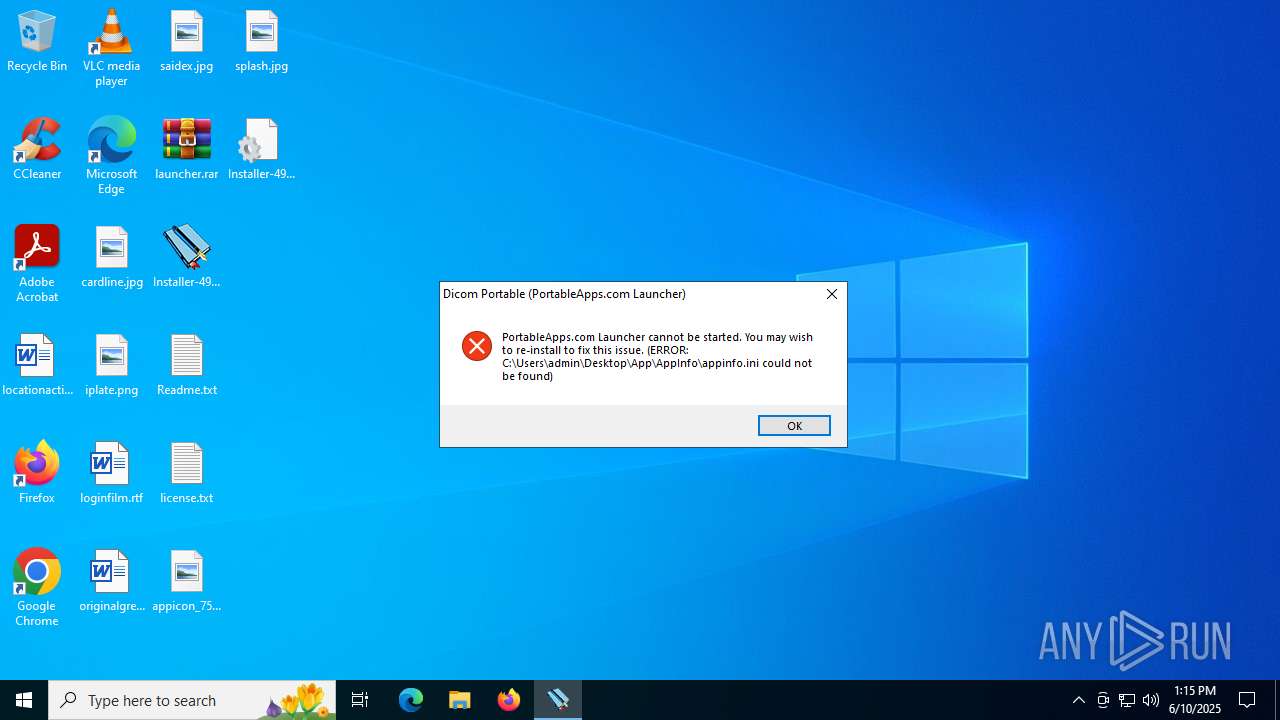
| 2212 | "C:\Users\admin\Desktop\Installer-49.220.6132.exe" | C:\Users\admin\Desktop\Installer-49.220.6132.exe | — | explorer.exe | |||||||||||
User: admin Company: PortableApps.com Integrity Level: MEDIUM Description: Dicom Portable (PortableApps.com Launcher) Exit code: 2 Version: 2.2.2.1 Modules
| |||||||||||||||
| 4576 | "C:\Users\admin\Desktop\Installer-49.220.6132.exe" | C:\Users\admin\Desktop\Installer-49.220.6132.exe | explorer.exe | ||||||||||||
User: admin Company: PortableApps.com Integrity Level: MEDIUM Description: Dicom Portable (PortableApps.com Launcher) Exit code: 0 Version: 2.2.2.1 Modules
| |||||||||||||||
| 4760 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 311
Read events
13 281
Write events
30
Delete events
0
Modification events
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\launcher.rar | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1604) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1132) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.jpg\OpenWithProgids |
| Operation: | write | Name: | jpegfile |
Value: | |||
| (PID) Process: | (1132) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MrtCache\C:%5CProgram Files%5CWindowsApps%5CMicrosoft.ScreenSketch_10.1907.2471.0_x64__8wekyb3d8bbwe%5Cmicrosoft.system.package.metadata%5CS-1-5-21-1693682860-607145093-2874071422-1001-MergedResources-0.pri\1d8b7afeb5c569c\55e3c056 |
| Operation: | write | Name: | @{microsoft.screensketch_10.1907.2471.0_x64__8wekyb3d8bbwe?ms-resource://microsoft.screensketch/files/assets/screensketchsquare44x44logo.png} |
Value: C:\Program Files\WindowsApps\Microsoft.ScreenSketch_10.1907.2471.0_x64__8wekyb3d8bbwe\Assets\ScreenSketchSquare44x44Logo.targetsize-16_contrast-black.png | |||
Executable files
4
Suspicious files
4
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppData\Installer.49.220.6132.exe | — | |
MD5:— | SHA256:— | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppData\license.txt | text | |
MD5:4E9137B92ABD5E5BA212CF667D833B2C | SHA256:B5CD774C1D086CEBB073999A7A93D17CB81525540D5F6096C044A949D0BD91B1 | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppInfo\appicon_75.png | image | |
MD5:C692296206B9F1A8A8B3380BE1F818AC | SHA256:EA78CA5FAE638CEBF7663BE92E212C4DDD8CE713D186B81DDD6E5704A47A5384 | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\license.txt | text | |
MD5:4E9137B92ABD5E5BA212CF667D833B2C | SHA256:B5CD774C1D086CEBB073999A7A93D17CB81525540D5F6096C044A949D0BD91B1 | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppInfo\appinfo.ini | ini | |
MD5:4B7044C10372EC673BAD23E1DCB41AA5 | SHA256:8ABC2D5C4C9075E69B6BCA67015BB069E427D4B70A86D8F7D23BD3A1CE5394B7 | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppInfo\appicon.ico | image | |
MD5:9B6CF5C6F65A252CAF85DCFA6BA0E7BC | SHA256:F4E2CD6D28E98E0624FEB064B92CCDC438DCA91BDF6358FDE48FAED94ED90CA3 | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppInfo\appicon_32.png | image | |
MD5:AB3A4B1972C4CAEA8668E32A0836BE1B | SHA256:8F0EAC6AE9F575B12F0B0EE13CD842198A01CFCB793C4DE35637EA8019F4CBB9 | |||
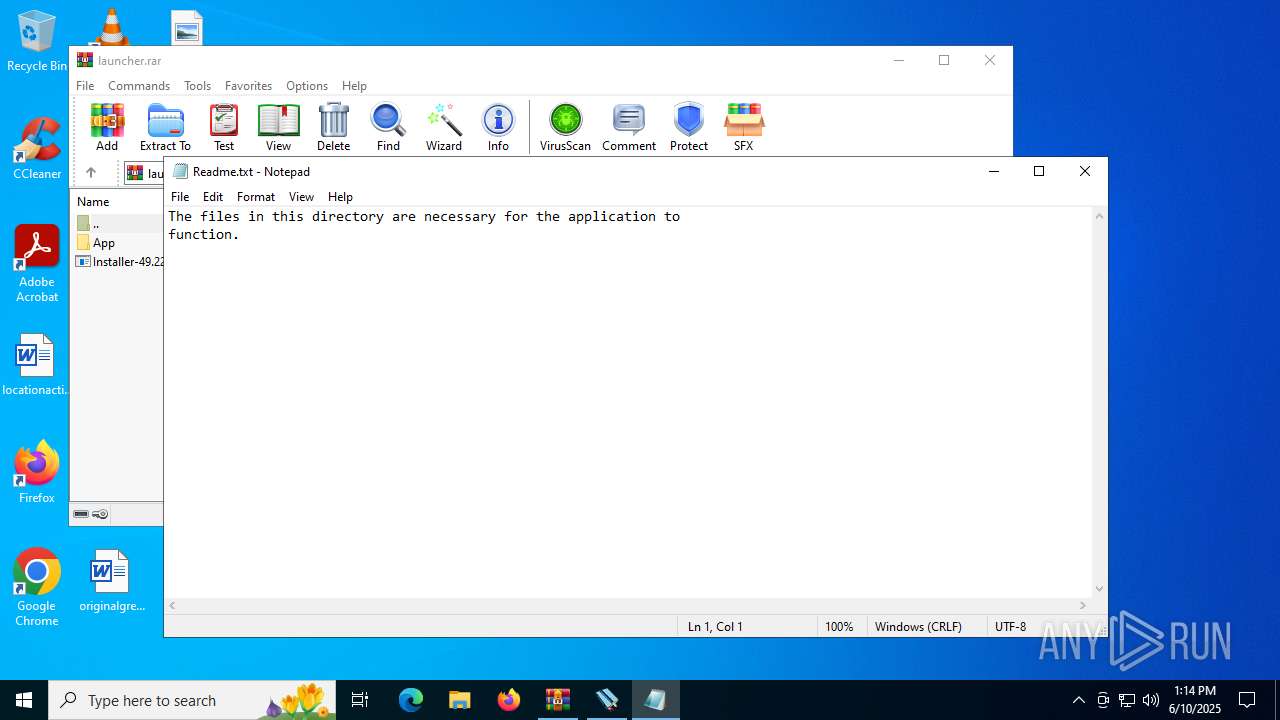
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\Readme.txt | text | |
MD5:AEC5DC9A01419DF4765CED7418AC9A44 | SHA256:42241D10C9C6AA8E38F9A4097EF722FB362DEA7B0BB1253DAE76B5F3BC5526E5 | |||
| 2212 | Installer-49.220.6132.exe | C:\Users\admin\AppData\Local\Temp\nsd7E58.tmp | binary | |
MD5:2577E11A54854D2E7548C4AD9C12829B | SHA256:FB8A50962358B500A7E9B44BAED2E98BE685CDC453DC8901FA8DA971E3CA644D | |||
| 2028 | WinRAR.exe | C:\Users\admin\Desktop\App\AppInfo\appicon_128.png | image | |
MD5:8E29B69E420D4683529549857D3BFAEB | SHA256:7595F8FCDA88FAAC9E780DAEC64537141DD1CD7DEBDE6E61FF23D4D847588D8A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
59
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4808 | RUXIMICS.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.1:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
1324 | SIHClient.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
1324 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.131:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4808 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4808 | RUXIMICS.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |