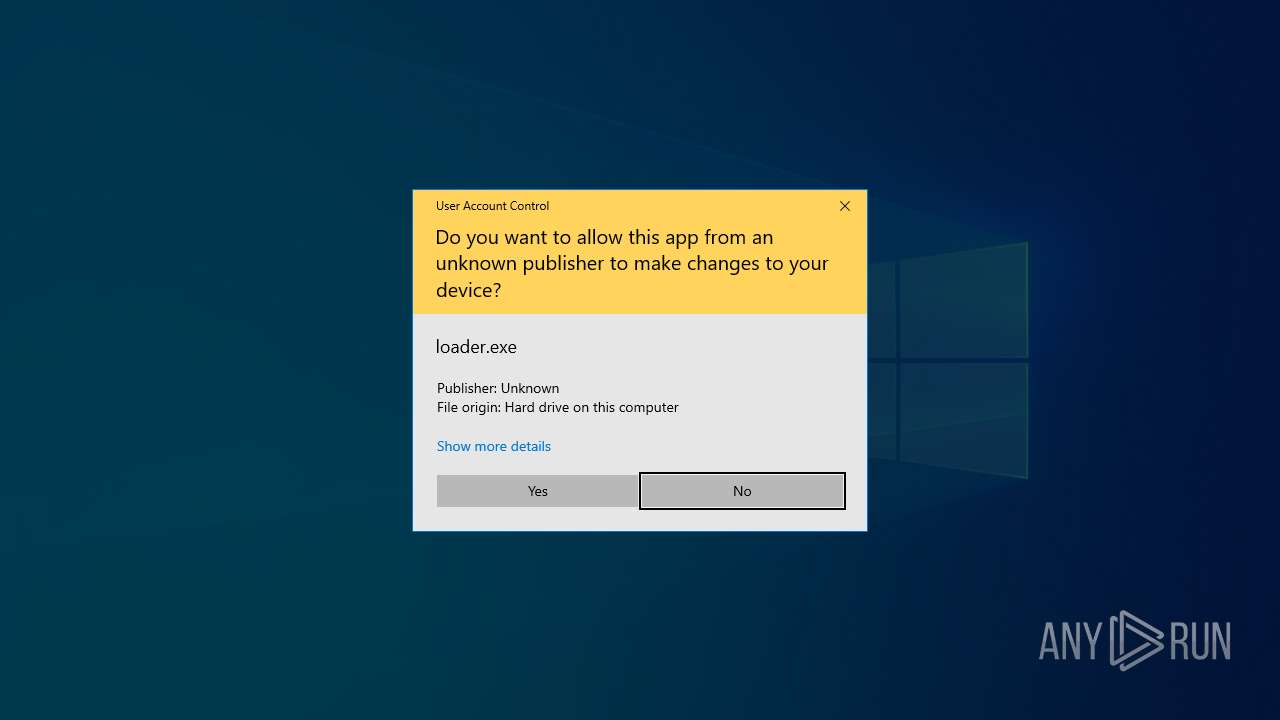
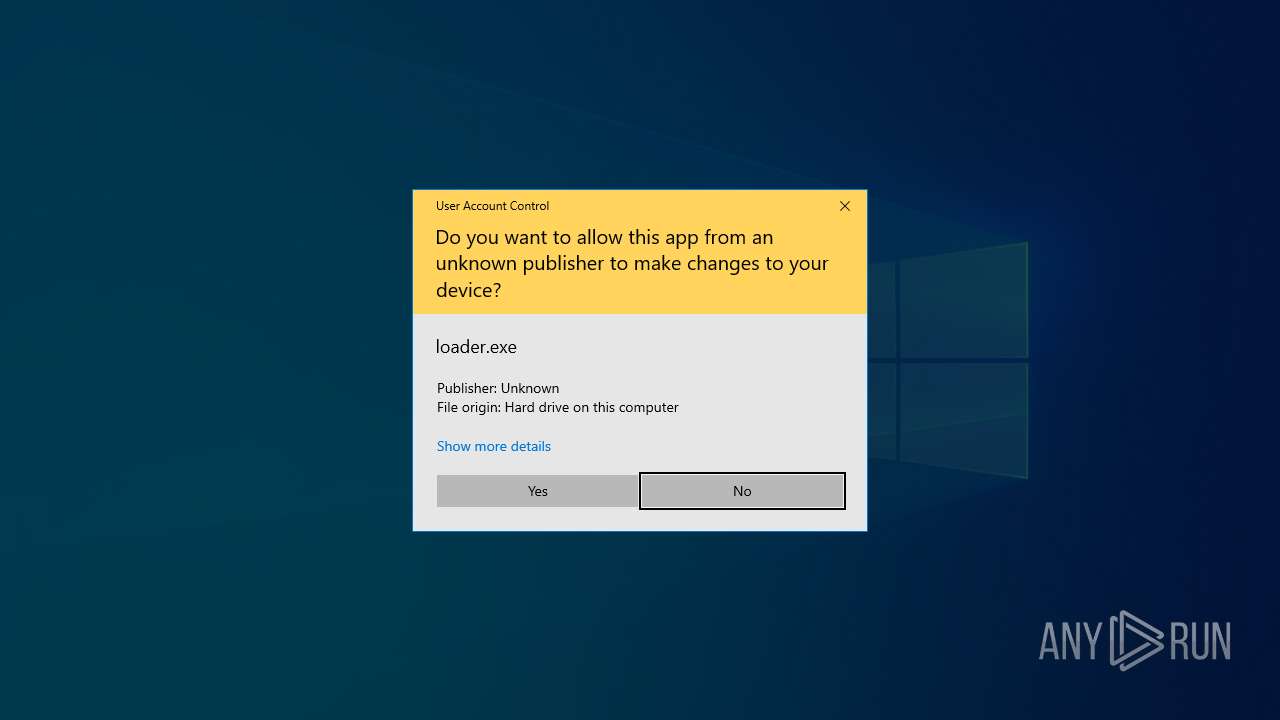
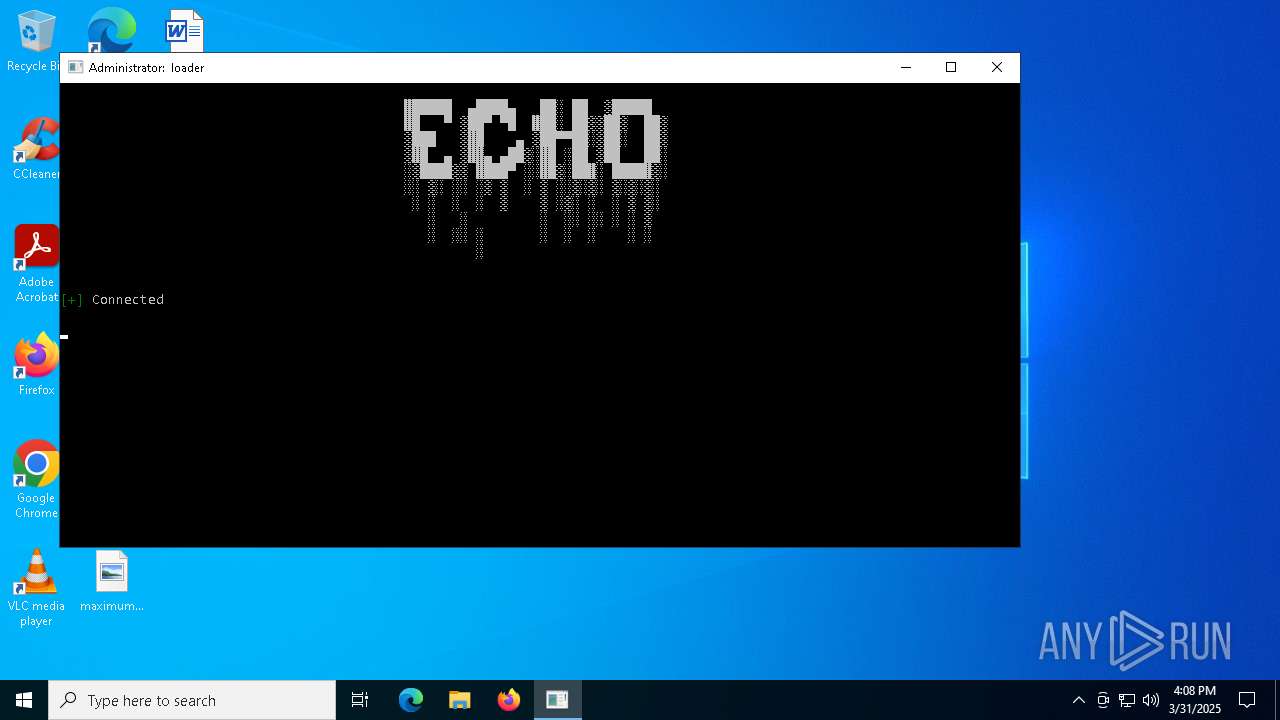
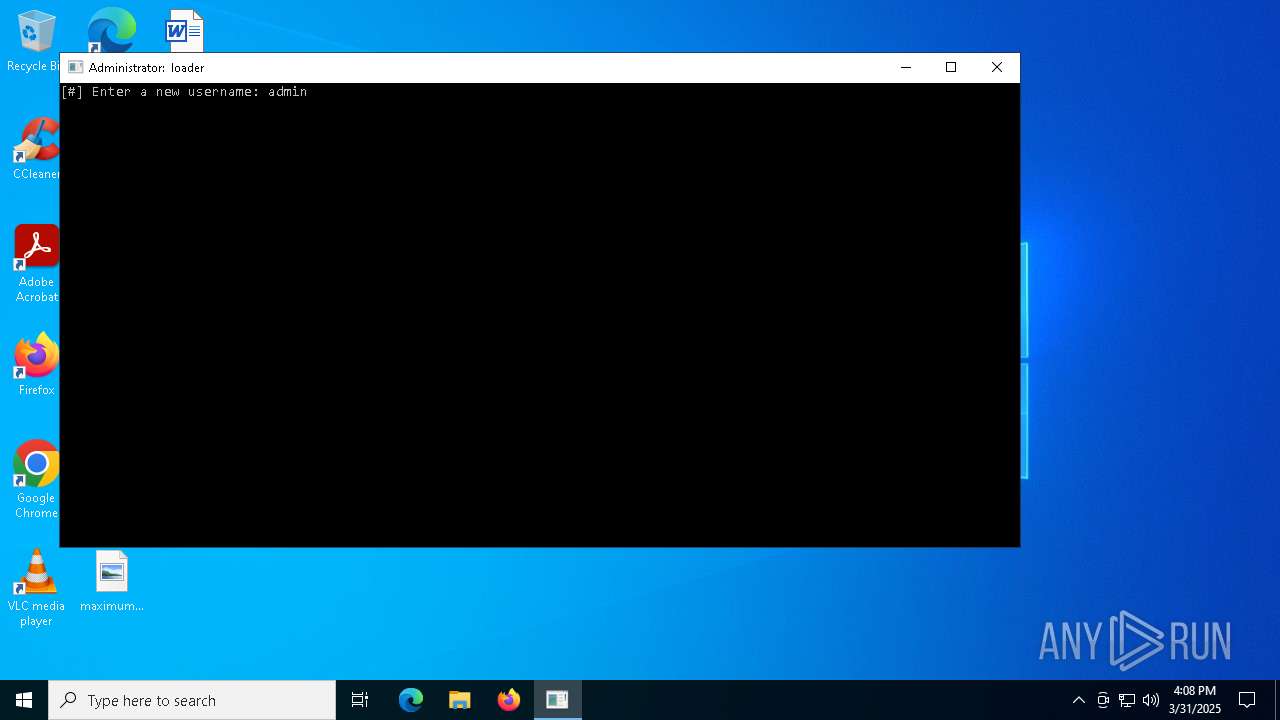
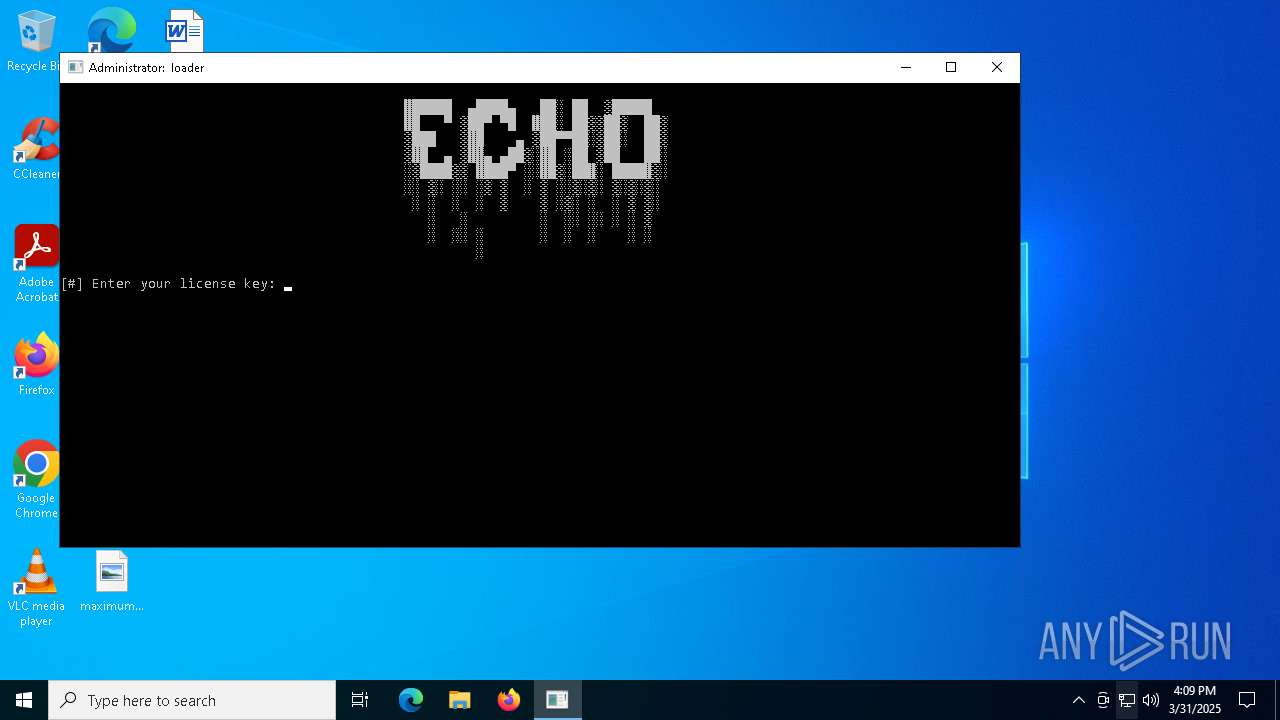
| download: | /loader.exe |
| Full analysis: | https://app.any.run/tasks/ad9f1734-c075-4159-b47e-f3daae3a0873 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2025, 16:07:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | 8FA4FBC14D91FFDFFB284DEC11D0E639 |
| SHA1: | 3B10B00AC89883DC2219EFFC2E44923D6B3B5233 |
| SHA256: | 3CBB9C06B3E217D273E30650650FF955983A7A9C3D6A3FAE7FB9FEA5EC839AEB |
| SSDEEP: | 1536:fULaGp0b+IgEs2f0BVoz0xwlRN5Cc2+sWMbBrPGk5YkJom/1enyplwp:gIgEs2fQVSCc0rtxJoeQwC |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executing commands from a ".bat" file
- loader.exe (PID: 7584)
- cmd.exe (PID: 8092)
- cmd.exe (PID: 7608)
- loader.exe (PID: 8064)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 8092)
- cmd.exe (PID: 8108)
- cmd.exe (PID: 7200)
- loader.exe (PID: 8064)
- loader.exe (PID: 7584)
- cmd.exe (PID: 7608)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 7232)
- cmd.exe (PID: 960)
Starts application with an unusual extension
- cmd.exe (PID: 8108)
- cmd.exe (PID: 5352)
Application launched itself
- cmd.exe (PID: 7200)
- cmd.exe (PID: 8108)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 7232)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 960)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7200)
- cmd.exe (PID: 8108)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 5352)
- cmd.exe (PID: 7232)
- cmd.exe (PID: 960)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8108)
- cmd.exe (PID: 5352)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 8108)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 8108)
Executable content was dropped or overwritten
- cmd.exe (PID: 8108)
- curl.exe (PID: 6044)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7716)
- cmd.exe (PID: 7932)
Get information on the list of running processes
- cmd.exe (PID: 8108)
Connects to unusual port
- curl.exe (PID: 8152)
- curl.exe (PID: 7832)
- curl.exe (PID: 1676)
- curl.exe (PID: 5408)
- curl.exe (PID: 7360)
- curl.exe (PID: 4980)
- curl.exe (PID: 5744)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 8108)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 2236)
INFO
Creates a new folder
- cmd.exe (PID: 7900)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7504)
- cmd.exe (PID: 7564)
Starts MODE.COM to configure console settings
- mode.com (PID: 7804)
- mode.com (PID: 8140)
Checks supported languages
- mode.com (PID: 7804)
- loader.exe (PID: 7584)
- chcp.com (PID: 8132)
- curl.exe (PID: 8152)
- curl.exe (PID: 6044)
- curl.exe (PID: 7260)
- loader.exe (PID: 8064)
- mode.com (PID: 8140)
- chcp.com (PID: 7872)
- curl.exe (PID: 7832)
- curl.exe (PID: 6032)
- curl.exe (PID: 1676)
- curl.exe (PID: 7360)
- curl.exe (PID: 5744)
- curl.exe (PID: 5408)
- curl.exe (PID: 4980)
Create files in a temporary directory
- loader.exe (PID: 7584)
- curl.exe (PID: 6044)
- curl.exe (PID: 7260)
- loader.exe (PID: 8064)
- curl.exe (PID: 6032)
Changes the display of characters in the console
- cmd.exe (PID: 8108)
- cmd.exe (PID: 5352)
Reads the computer name
- curl.exe (PID: 6044)
- curl.exe (PID: 7260)
- curl.exe (PID: 6032)
Execution of CURL command
- cmd.exe (PID: 8108)
- cmd.exe (PID: 5352)
Creates files or folders in the user directory
- cmd.exe (PID: 8108)
- cmd.exe (PID: 5352)
Manual execution by a user
- loader.exe (PID: 7928)
- loader.exe (PID: 8064)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6752)
- WMIC.exe (PID: 8116)
Checks proxy server information
- slui.exe (PID: 5392)
Reads the software policy settings
- slui.exe (PID: 5392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:04:22 18:25:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 57344 |
| InitializedDataSize: | 11550720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7f86 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
227
Monitored processes
91
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | timeout /t 2 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | C:\WINDOWS\system32\cmd.exe /c type logs\login.txt | findstr "user_id" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | taskkill /F /IM loader.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | timeout /t 3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | C:\WINDOWS\system32\cmd.exe /c wmic baseboard get serialnumber /value | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\Desktop\loader.exe" | C:\Users\admin\Desktop\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1672 | timeout /t 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | curl -s -X POST http://54.38.157.20:5000/create_account -H "Content-Type: application/json" -d "{\"username\":\"admin\", \"password\":\"admin\", \"hwid\":\"\"}" -o logs\account.txt | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 1760 | findstr /C:"\"status\": \"success\"" logs\account.txt | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 772
Read events
3 772
Write events
0
Delete events
0
Modification events
Executable files
2
Suspicious files
3
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8008 | cmd.exe | C:\Users\admin\AppData\Local\Temp\i6.f | text | |
MD5:FBB567216D6FA2A929F4FE2389740816 | SHA256:D10A6587021A36C1AF3B558DE7D5BDE0C047D0C494454C1ED08B6A19BBCF842A | |||
| 7584 | loader.exe | C:\Users\admin\AppData\Local\Temp\wtmpd\tmp78824.bat | text | |
MD5:0DBB6BF004BA3B0B304963F097DD2F2F | SHA256:415232BC67C8426FFDBC34615FABE286CF1A07BE95DC024B6580589D7F4AED77 | |||
| 6044 | curl.exe | C:\Users\admin\AppData\Local\Temp\loader_new.exe | executable | |
MD5:8FA4FBC14D91FFDFFB284DEC11D0E639 | SHA256:3CBB9C06B3E217D273E30650650FF955983A7A9C3D6A3FAE7FB9FEA5EC839AEB | |||
| 7584 | loader.exe | C:\Users\admin\AppData\Local\Temp\i6.bat | text | |
MD5:1AF1AB0E1E623C11529763D3016C0818 | SHA256:57F6713E8C793D5D81FBBF2E16DB7098B1D5A3A608915E62468F2435DAFBFD85 | |||
| 7584 | loader.exe | C:\Users\admin\AppData\Local\Temp\wtmpd\tmp18804.exe | text | |
MD5:3C52638971EAD82B5929D605C1314EE0 | SHA256:5614459EC05FDF6110FA8CE54C34E859671EEFFBA2B7BB4B1AD6C2C6706855AB | |||
| 7260 | curl.exe | C:\Users\admin\AppData\Local\Temp\latest_version.txt | text | |
MD5:73CCD957744DD2396F454D124D02080B | SHA256:24F502B1E3ABFA8EA2DB55A62DD09FD7BE591D415B91F82AF0CE90CD7A443063 | |||
| 7988 | cmd.exe | C:\Users\admin\AppData\Local\Temp\i6.t | text | |
MD5:21438EF4B9AD4FC266B6129A2F60DE29 | SHA256:13BF7B3039C63BF5A50491FA3CFD8EB4E699D1BA1436315AEF9CBE5711530354 | |||
| 8064 | loader.exe | C:\Users\admin\AppData\Local\Temp\wtmpd\tmp72094.bat | text | |
MD5:FF0DE3DC977BCA9B711EAAC070A9A3B4 | SHA256:7676A50B47348FF89451D8E7EEEC093632FB96D81B354619CFF779ECD4E0AD48 | |||
| 5352 | cmd.exe | C:\Users\admin\AppData\Roaming\Loader\license.txt | text | |
MD5:210CF7AA5E2682C9C9D4511F88FE2789 | SHA256:3BE481CA29E74A01367CEACA0B5C7F5EE53E9A407D26D4368EDD539541F7B13C | |||
| 1676 | curl.exe | C:\Users\admin\Desktop\logs\account.txt | binary | |
MD5:0C1E7E331FF98F81D1DA7874942C8141 | SHA256:77FB2073462B0ABA5EE8C449EC16680D0379096666084F43166CE53D590A67B5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
33
DNS requests
23
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5780 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8152 | curl.exe | GET | 200 | 54.38.157.20:5000 | http://54.38.157.20:5000/status | unknown | — | — | unknown |
5780 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 23.209.213.129:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 2.19.120.133:80 | http://e6.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBTUejiAQejpjQc4fOz2ttjyD6VkMQQUDcXM%2FZvuFAWhTDCCpT5eisNYCdICEgU5ncLLotvVuAz3YjJe2GmmKg%3D%3D | unknown | — | — | whitelisted |
7836 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7832 | curl.exe | GET | 200 | 54.38.157.20:5000 | http://54.38.157.20:5000/status | unknown | — | — | unknown |
7836 | SIHClient.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4244 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3216 | svchost.exe | 20.7.1.246:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5780 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
8152 | curl.exe | 54.38.157.20:5000 | cdn.echostore.cc | OVH SAS | DE | unknown |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7260 | curl.exe | 54.38.157.20:443 | cdn.echostore.cc | OVH SAS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8152 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7832 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
1676 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
5408 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
4980 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
7360 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |
5744 | curl.exe | Potentially Bad Traffic | ET HUNTING curl User-Agent to Dotted Quad |