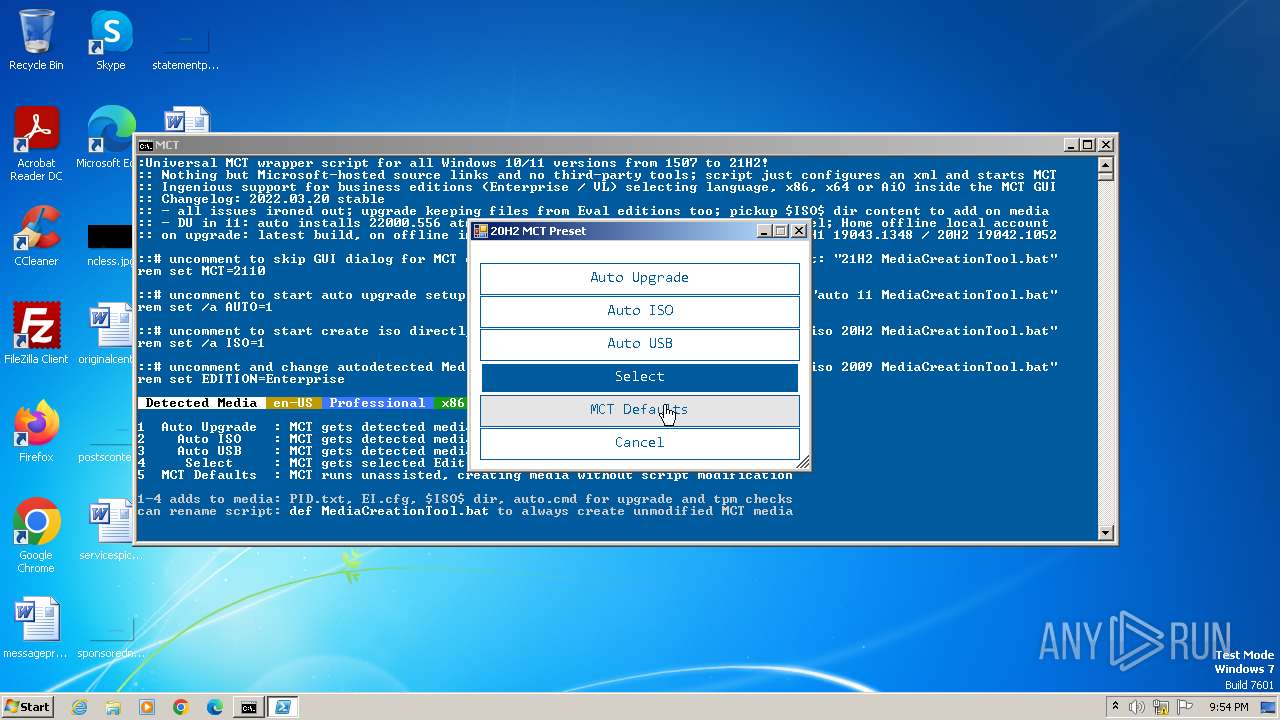
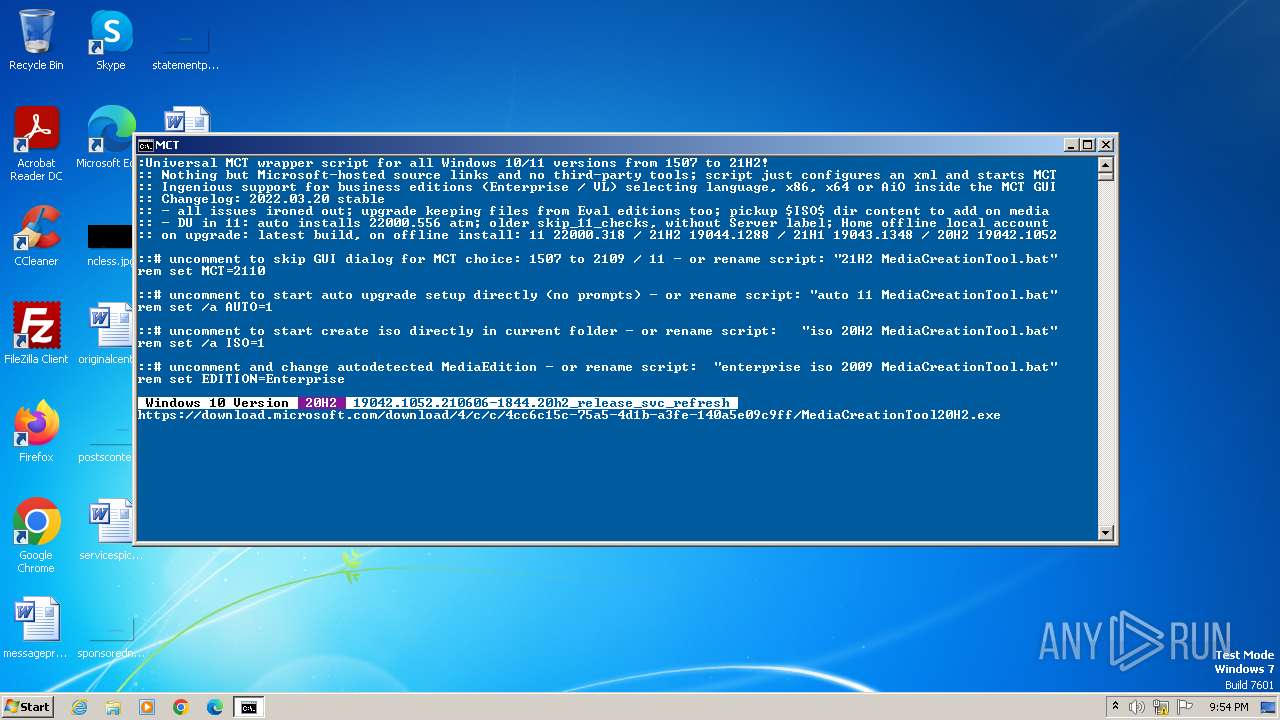
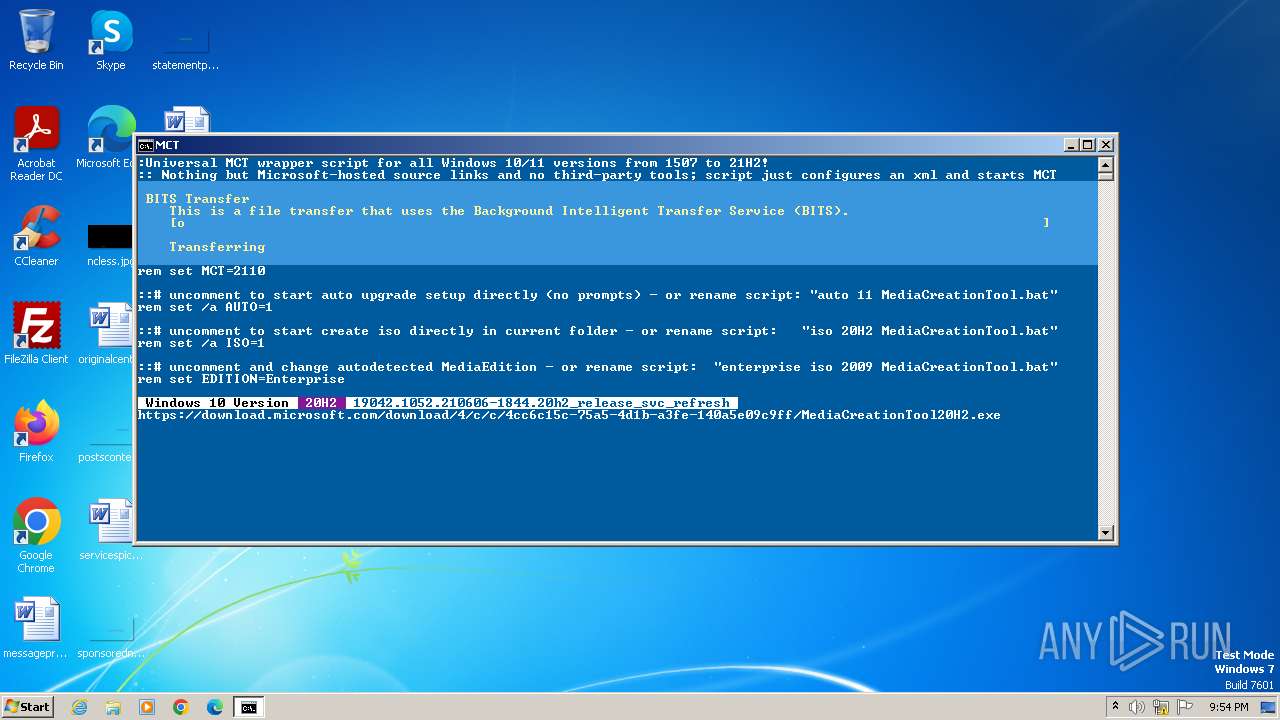
| File name: | MediaCreationTool.bat |
| Full analysis: | https://app.any.run/tasks/c205ef01-322e-4084-a43d-9099fbd25050 |
| Verdict: | Malicious activity |
| Analysis date: | November 28, 2023, 21:53:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 980EE7D2766111B564DDCB231EF61E08 |
| SHA1: | 37F36266F5E6B2F794BE2494775B6DB6F14B6882 |
| SHA256: | 3C9C3ACAC3986A79DC55C5491FDA009C7F7A907BFD2727BFC3FA7D37BFFB8611 |
| SSDEEP: | 3072:LuME2D/VQ2w33dFepssMCyJnMuumU6VxjuBxpro2A+N/Lhu:LuME2D/VQV33dFmmnMuumNuDprTw |
MALICIOUS
Drops the executable file immediately after the start
- MediaCreationTool20H2.exe (PID: 3704)
The DLL Hijacking
- SetupHost.Exe (PID: 1808)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 564)
- cmd.exe (PID: 3984)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 564)
- cmd.exe (PID: 3984)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 564)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 304)
- cmd.exe (PID: 3080)
Application launched itself
- cmd.exe (PID: 564)
- cmd.exe (PID: 3984)
- cmd.exe (PID: 1360)
- cmd.exe (PID: 3168)
- cmd.exe (PID: 2520)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 564)
- cmd.exe (PID: 3984)
- cmd.exe (PID: 1360)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 3168)
Executing commands from a ".bat" file
- cmd.exe (PID: 564)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2968)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3984)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 2968)
- cmd.exe (PID: 3984)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 2968)
- cmd.exe (PID: 3984)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2968)
- cmd.exe (PID: 3984)
Reads the Internet Settings
- cmd.exe (PID: 3984)
- SetupHost.Exe (PID: 1808)
Process drops legitimate windows executable
- MediaCreationTool20H2.exe (PID: 3704)
The process creates files with name similar to system file names
- MediaCreationTool20H2.exe (PID: 3704)
INFO
Checks supported languages
- chcp.com (PID: 844)
- Robocopy.exe (PID: 3776)
- chcp.com (PID: 2336)
- Robocopy.exe (PID: 1936)
- MediaCreationTool20H2.exe (PID: 3704)
- SetupHost.Exe (PID: 1808)
- wmpnscfg.exe (PID: 3340)
Reads the computer name
- Robocopy.exe (PID: 3776)
- Robocopy.exe (PID: 1936)
- wmpnscfg.exe (PID: 3340)
- SetupHost.Exe (PID: 1808)
Manual execution by a user
- wmpnscfg.exe (PID: 3340)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3340)
- SetupHost.Exe (PID: 1808)
Create files in a temporary directory
- makecab.exe (PID: 3792)
Reads Environment values
- SetupHost.Exe (PID: 1808)
Process checks computer location settings
- SetupHost.Exe (PID: 1808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
124
Monitored processes
82
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | reg add HKCU\Console /v ForceV2 /d 0x01 /t reg_dword /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "C:\ESD\MCT\MediaCreationTool20H2.exe" /Selfhost | C:\ESD\MCT\MediaCreationTool20H2.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows 10 Setup Exit code: 3221226540 Version: 10.0.19041.572 (vb_release_svc_prod1.201007-1724) Modules
| |||||||||||||||
| 304 | C:\Windows\system32\cmd.exe /c reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "EditionID" /se "|" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\MediaCreationTool.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 580 | reg add "HKCU\Console\MCT" /v WindowSize /d 2097272 /t reg_dword /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 844 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1004 | powershell -nop -c ";$f0=[io.file]::ReadAllText($env:0); $0=($f0-split '#\:CHOICES2\:' ,3)[1]; $1=$env:1-replace'([`@$])','`$1'; iex($0+$1)" | C:\Windows\System32\windowspowershell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion" /v "ProductName" /se "|" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1128 | reg add "HKCU\Console\MCT" /v ColorTable15 /d 0xffffff /t reg_dword /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1212 | reg add "HKCU\Console\MCT" /v ColorTable07 /d 0xcccccc /t reg_dword /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 357
Read events
6 126
Write events
228
Delete events
3
Modification events
| (PID) Process: | (1004) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3172) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3340) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{C76F1B5B-1A04-45A8-B90F-3A960CABBD31}\{C8EDF55D-D3E8-41C4-9696-64A0A3575F3F} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3340) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{C76F1B5B-1A04-45A8-B90F-3A960CABBD31} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3340) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{803A1095-4B6E-4658-8F60-AC59ED44E574} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2900) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2456) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3984) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3984) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
19
Suspicious files
20
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | cmd.exe | C:\Users\admin\AppData\Roaming\c | binary | |
MD5:28D397E87306B8631F3ED80D858D35F0 | SHA256:A9253DC8529DD214E5F22397888E78D3390DAA47593E26F68C18F97FD7A3876B | |||
| 1004 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1bdcef.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 1004 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 3776 | Robocopy.exe | C:\ESD\MediaCreationTool.bat | text | |
MD5:980EE7D2766111B564DDCB231EF61E08 | SHA256:3C9C3ACAC3986A79DC55C5491FDA009C7F7A907BFD2727BFC3FA7D37BFFB8611 | |||
| 2900 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1c7e9d.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 3984 | cmd.exe | C:\ESD\latest_MCT.url | text | |
MD5:ACCAC7A89787C165104D357395B0786C | SHA256:870B4D39E2A91AFB2061A679F4588ACE4F42617B10A6F6D7ECE20649FAF3CCED | |||
| 3172 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1c4c43.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 1004 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\UWAGNCEJVCG6W6D9UAR4.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2900 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\L4ROLBHNPUVZ8MIBZWXI.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2900 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
15
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
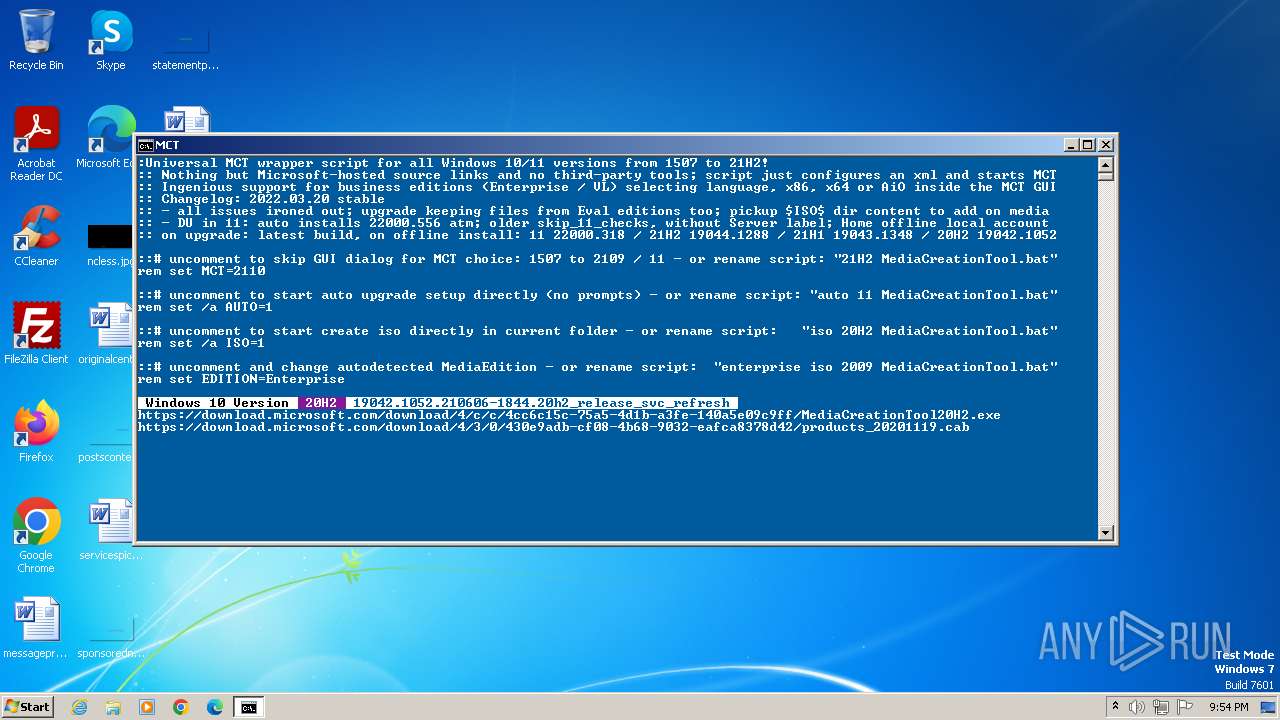
868 | svchost.exe | HEAD | 302 | 23.35.228.223:80 | http://download.microsoft.com/download/4/c/c/4cc6c15c-75a5-4d1b-a3fe-140a5e09c9ff/MediaCreationTool20H2.exe | unknown | — | — | unknown |
868 | svchost.exe | GET | 302 | 23.35.228.223:80 | http://download.microsoft.com/download/4/c/c/4cc6c15c-75a5-4d1b-a3fe-140a5e09c9ff/MediaCreationTool20H2.exe | unknown | — | — | unknown |
868 | svchost.exe | HEAD | 302 | 23.35.228.223:80 | http://download.microsoft.com/download/4/3/0/430e9adb-cf08-4b68-9032-eafca8378d42/products_20201119.cab | unknown | — | — | unknown |
868 | svchost.exe | GET | 302 | 23.35.228.223:80 | http://download.microsoft.com/download/4/3/0/430e9adb-cf08-4b68-9032-eafca8378d42/products_20201119.cab | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 23.35.228.223:80 | download.microsoft.com | AKAMAI-AS | DE | unknown |
868 | svchost.exe | 23.35.228.223:443 | download.microsoft.com | AKAMAI-AS | DE | unknown |
1808 | SetupHost.Exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
1 ETPRO signatures available at the full report