| File name: | 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn |
| Full analysis: | https://app.any.run/tasks/faace79a-db6d-463c-b83f-996e9f6d95ed |
| Verdict: | Malicious activity |
| Analysis date: | April 04, 2025, 18:49:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | BFB729BA575953DFB5F0BE1D8EF5AA9B |
| SHA1: | 774746C92CB42B9DBFAD8BAECCDDD7A00915CB4F |
| SHA256: | 3C8AFA615487CC7B635E1CA40FC1CA78250A48688775112BA5088FAC0F653BD4 |
| SSDEEP: | 393216:UF4u5BmxT6HpAKp2+W71sMnlW2NB2sWZm:We6JAK49BTnw2Ng7Zm |
MALICIOUS
JEEFO has been detected
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
- icsys.icn.exe (PID: 7808)
- svchost.exe (PID: 7904)
- explorer.exe (PID: 7844)
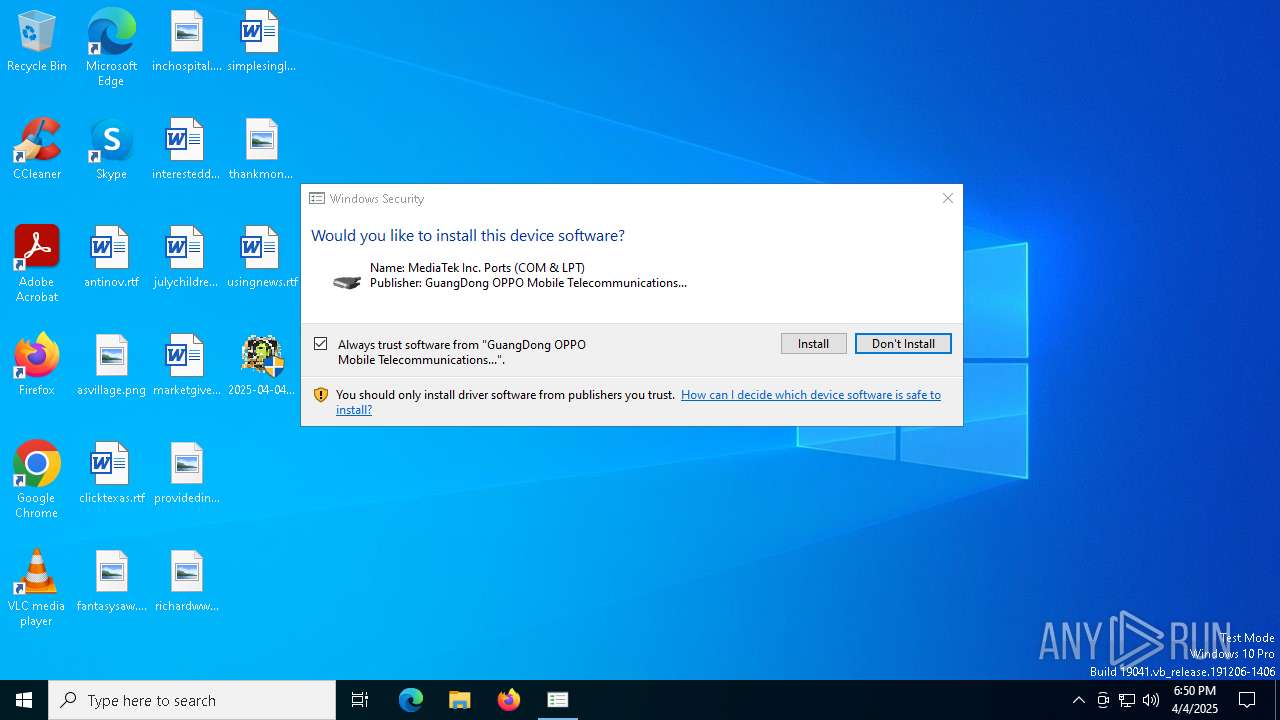
Executing a file with an untrusted certificate
- dpinst64.exe (PID: 4988)
- dpinst64.exe (PID: 1912)
- dpinst64.exe (PID: 7652)
- dpinst64.exe (PID: 7960)
Changes the autorun value in the registry
- explorer.exe (PID: 7844)
- svchost.exe (PID: 7904)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- icsys.icn.exe (PID: 7808)
- explorer.exe (PID: 7844)
- spoolsv.exe (PID: 7884)
- irsetup.exe (PID: 7852)
- dpinst64.exe (PID: 4988)
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 7468)
- drvinst.exe (PID: 7504)
- dpinst64.exe (PID: 1912)
- dpinst64.exe (PID: 7652)
- drvinst.exe (PID: 7676)
- dpinst64.exe (PID: 7960)
- drvinst.exe (PID: 7824)
Starts application with an unusual extension
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
Starts itself from another location
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
- icsys.icn.exe (PID: 7808)
- explorer.exe (PID: 7844)
- spoolsv.exe (PID: 7884)
- svchost.exe (PID: 7904)
Reads security settings of Internet Explorer
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- irsetup.exe (PID: 7852)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 7808)
- spoolsv.exe (PID: 7884)
Process drops legitimate windows executable
- irsetup.exe (PID: 7852)
- dpinst64.exe (PID: 4988)
- drvinst.exe (PID: 1660)
Drops a system driver (possible attempt to evade defenses)
- irsetup.exe (PID: 7852)
- dpinst64.exe (PID: 4988)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 7468)
- dpinst64.exe (PID: 1912)
- drvinst.exe (PID: 7504)
- dpinst64.exe (PID: 7652)
- drvinst.exe (PID: 7676)
- dpinst64.exe (PID: 7960)
- drvinst.exe (PID: 7824)
Executes as Windows Service
- VSSVC.exe (PID: 8112)
Starts a Microsoft application from unusual location
- dpinst64.exe (PID: 4988)
- dpinst64.exe (PID: 1912)
- dpinst64.exe (PID: 7652)
- dpinst64.exe (PID: 7960)
Creates files in the driver directory
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 7468)
- drvinst.exe (PID: 664)
- drvinst.exe (PID: 7504)
- drvinst.exe (PID: 1272)
- drvinst.exe (PID: 7676)
- drvinst.exe (PID: 7824)
Adds/modifies Windows certificates
- irsetup.exe (PID: 7852)
Searches for installed software
- dllhost.exe (PID: 8068)
Starts CMD.EXE for commands execution
- irsetup.exe (PID: 7852)
Creates or modifies Windows services
- svchost.exe (PID: 7904)
INFO
The sample compiled with english language support
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- irsetup.exe (PID: 7852)
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 4380)
- dpinst64.exe (PID: 4988)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 7468)
- dpinst64.exe (PID: 1912)
- drvinst.exe (PID: 7504)
- dpinst64.exe (PID: 7652)
- drvinst.exe (PID: 7676)
- dpinst64.exe (PID: 7960)
- drvinst.exe (PID: 7824)
Create files in a temporary directory
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- icsys.icn.exe (PID: 7808)
- spoolsv.exe (PID: 7884)
- explorer.exe (PID: 7844)
- svchost.exe (PID: 7904)
- irsetup.exe (PID: 7852)
- spoolsv.exe (PID: 7956)
- dpinst64.exe (PID: 4988)
- dpinst64.exe (PID: 1912)
- dpinst64.exe (PID: 7652)
- dpinst64.exe (PID: 7960)
Checks supported languages
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7704)
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- icsys.icn.exe (PID: 7808)
- explorer.exe (PID: 7844)
- spoolsv.exe (PID: 7884)
- irsetup.exe (PID: 7852)
- svchost.exe (PID: 7904)
- spoolsv.exe (PID: 7956)
- dpinst64.exe (PID: 4988)
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 7468)
- drvinst.exe (PID: 664)
- drvinst.exe (PID: 7504)
- drvinst.exe (PID: 1272)
- dpinst64.exe (PID: 1912)
- dpinst64.exe (PID: 7652)
- drvinst.exe (PID: 7676)
- dpinst64.exe (PID: 7960)
- drvinst.exe (PID: 7824)
Reads the computer name
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- irsetup.exe (PID: 7852)
- svchost.exe (PID: 7904)
- dpinst64.exe (PID: 4988)
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 664)
- drvinst.exe (PID: 7468)
- drvinst.exe (PID: 1272)
- dpinst64.exe (PID: 1912)
- drvinst.exe (PID: 7504)
- dpinst64.exe (PID: 7652)
- dpinst64.exe (PID: 7960)
- drvinst.exe (PID: 7676)
- drvinst.exe (PID: 7824)
Process checks computer location settings
- 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe (PID: 7748)
- irsetup.exe (PID: 7852)
The sample compiled with arabic language support
- irsetup.exe (PID: 7852)
The process uses Lua
- irsetup.exe (PID: 7852)
UPX packer has been detected
- irsetup.exe (PID: 7852)
Manages system restore points
- SrTasks.exe (PID: 5512)
Reads the software policy settings
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 664)
- drvinst.exe (PID: 7468)
- drvinst.exe (PID: 7504)
- drvinst.exe (PID: 1272)
- rundll32.exe (PID: 7664)
- slui.exe (PID: 5400)
- drvinst.exe (PID: 7676)
- drvinst.exe (PID: 7824)
Reads the machine GUID from the registry
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 4380)
- drvinst.exe (PID: 6372)
- drvinst.exe (PID: 7388)
- drvinst.exe (PID: 664)
- drvinst.exe (PID: 7468)
- drvinst.exe (PID: 1272)
- drvinst.exe (PID: 7504)
- drvinst.exe (PID: 7676)
- drvinst.exe (PID: 7824)
Adds/modifies Windows certificates
- drvinst.exe (PID: 7504)
- drvinst.exe (PID: 7676)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 7664)
Checks proxy server information
- slui.exe (PID: 5400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
159
Monitored processes
32
Malicious processes
22
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{8e1fdb47-c9a1-a845-8c76-b96e53296958}\tetherxp.inf" "9" "4382e9c87" "00000000000001F0" "WinSta0\Default" "0000000000000188" "208" "c:\users\admin\appdata\local\temp\_ir_sf_temp_0\ver1" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{d606cf57-2345-0443-9298-f1dcc9507e1d}\wpdmtp.inf" "9" "45ebf2ab3" "0000000000000210" "WinSta0\Default" "000000000000020C" "208" "c:\users\admin\appdata\local\temp\_ir_sf_temp_0\ver1" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{fc575942-dd08-7e4d-b7a5-65ab85a334d4}\android_winusb.inf" "9" "41cf5beef" "00000000000001CC" "WinSta0\Default" "00000000000001C0" "208" "c:\users\admin\appdata\local\temp\_ir_sf_temp_0\ver1" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst64.exe" /PATH "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\VER2\WIN10" /SW /SA /SE /LM | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst64.exe | irsetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 Modules
| |||||||||||||||
| 4380 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{45e40bd0-aa9b-ef40-9e1d-c4e8271dc616}\mtkmbim7_x64.inf" "9" "4a2e1981f" "0000000000000188" "WinSta0\Default" "00000000000001F0" "208" "c:\users\admin\appdata\local\temp\_ir_sf_temp_0\ver1" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst64.exe" /PATH "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\VER1" /SW /F /SA /SE /LM | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\dpinst64.exe | irsetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 1792 Version: 2.1 Modules
| |||||||||||||||
| 5400 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5512 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | CMD.exe /D /A /C RMDIR C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0 /S /Q | C:\Windows\SysWOW64\cmd.exe | — | irsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
41 941
Read events
41 712
Write events
201
Delete events
28
Modification events
| (PID) Process: | (7704) 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7808) icsys.icn.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7844) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7844) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7844) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7844) explorer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
| (PID) Process: | (7904) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Explorer |
Value: c:\windows\resources\themes\explorer.exe RO | |||
| (PID) Process: | (7904) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Svchost |
Value: c:\windows\resources\svchost.exe RO | |||
| (PID) Process: | (7904) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Explorer |
Value: | |||
| (PID) Process: | (7904) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | Svchost |
Value: | |||
Executable files
84
Suspicious files
107
Text files
9
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7748 | 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | executable | |
MD5:6910D08F901A704D8B6076DAAF6D5CEF | SHA256:D8525864299C3E66BC492ACA0D8707FE6A710A2A85B7ABE0EEA8771B7DFA8AE7 | |||
| 7852 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\Wow64.lmd | executable | |
MD5:DA1D0CD400E0B6AD6415FD4D90F69666 | SHA256:7A79B049BDC3B6E4D101691888360F4F993098F3E3A8BEEFFF4AC367430B1575 | |||
| 7808 | icsys.icn.exe | C:\Windows\Resources\Themes\explorer.exe | executable | |
MD5:EB0A6DFC59B465FAF66150C6AA817618 | SHA256:A828F79021EB66D2B866834BD45AABACBB13172B4300E17A5066051566D6F654 | |||
| 7704 | 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe | C:\Windows\Resources\Themes\icsys.icn.exe | executable | |
MD5:E91BEC894C392976AD3952E441BD4D03 | SHA256:6297A7544783064E67801A68F3CC92B97BB04EC1BD71A725C166BB1F3494A4F3 | |||
| 7748 | 2025-04-04_bfb729ba575953dfb5f0be1d8ef5aa9b_amadey_hijackloader_rhadamanthys_smoke-loader_swisyn.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:C333AF59FA9F0B12D1CD9F6BBA111E3A | SHA256:FAD540071986C59EC40102C9CA9518A0DDCE80CF39EB2FD476BB1A7A03D6EB34 | |||
| 7884 | spoolsv.exe | C:\Windows\Resources\svchost.exe | executable | |
MD5:D9FC32D0CA53159EB0C8773C37F2CD93 | SHA256:DFB84D526B779E804C48D043BA4F79D143B4FD47FE7B28E5981042A21BA6AA41 | |||
| 7852 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.dat | binary | |
MD5:C86C1CBC97E06D2D249A9DE0831560D1 | SHA256:EB076E2CF104303FC48C0860F499F955A3480FD9F0F27BBD5241D027B1DB63C3 | |||
| 7884 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DF337B31EB6B6A0058.TMP | binary | |
MD5:A18F0FDDA964C85AFE52533D027807F9 | SHA256:60BA9EEDE552C27FEC509A7DDFF2C09012E0AF034BE61182F26C92239228951B | |||
| 7852 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\Chimera.ico | image | |
MD5:0160C98A5BCE74331271DC08719C6D68 | SHA256:9216A46311C9375B1BFAF86B89B1B93998DD0404EE6B15A62C7A62983AF63D88 | |||
| 7956 | spoolsv.exe | C:\Users\admin\AppData\Local\Temp\~DFF1E19201FFBCE959.TMP | binary | |
MD5:E3B237F603EDC5D3790CA1CECBAB0DCB | SHA256:C631F078F4EC7ECFDF0B582E8665040C33884230099402738C709C694D3EECD7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7380 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5400 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |