| File name: | duplicate-file-finder-setup.exe |
| Full analysis: | https://app.any.run/tasks/23c9e987-8829-40b3-90df-2dd535516a06 |
| Verdict: | Malicious activity |
| Analysis date: | January 10, 2024, 18:30:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7B441544E8C39FB92303AAD4F8E80052 |
| SHA1: | 04885CEF38119272E0FE46E0222A1E25E738B463 |
| SHA256: | 3C5D5EE4B228E8F09A376B75BC4F9049BDD6C796FF45077EB52D7DAC6AE74D21 |
| SSDEEP: | 98304:eM9p/LNfM+hA/MOR8ngM3c6GGWJk5T3lt6EJk642KYMHmwq7dFcQT4f6ssD+suNj:5G8D9tMsCe7V9lguxxzI/XKQ |
MALICIOUS
Steals credentials from Web Browsers
- duplicate-file-finder-setup.tmp (PID: 2016)
Registers / Runs the DLL via REGSVR32.EXE
- duplicate-file-finder-setup.tmp (PID: 2016)
Actions looks like stealing of personal data
- duplicate-file-finder-setup.tmp (PID: 2016)
SUSPICIOUS
Reads the Internet Settings
- duplicate-file-finder-setup.tmp (PID: 2016)
- GASender.exe (PID: 1220)
Reads the Windows owner or organization settings
- duplicate-file-finder-setup.tmp (PID: 2016)
Loads DLL from Mozilla Firefox
- dllhost.exe (PID: 696)
Reads browser cookies
- duplicate-file-finder-setup.tmp (PID: 2016)
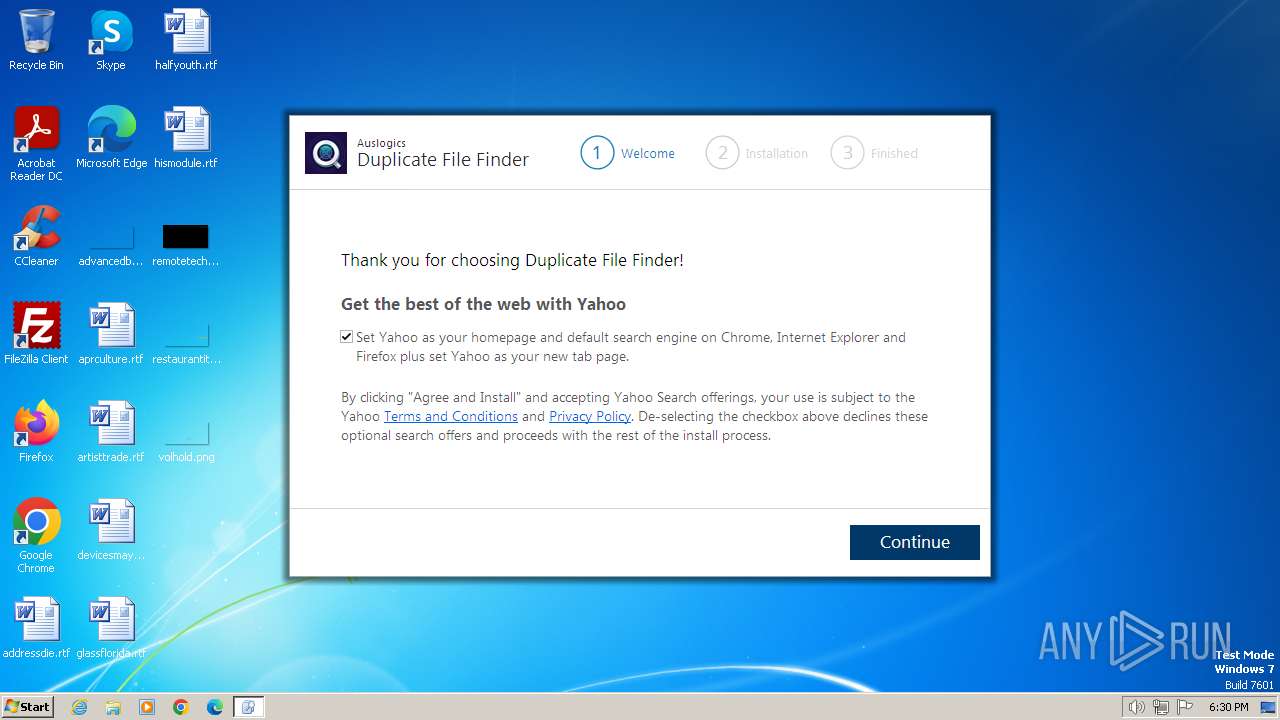
Changes the title of the Internet Explorer window
- duplicate-file-finder-setup.tmp (PID: 2016)
Changes the Home page of Internet Explorer
- duplicate-file-finder-setup.tmp (PID: 2016)
Starts CMD.EXE for commands execution
- duplicate-file-finder-setup.tmp (PID: 2016)
INFO
Checks supported languages
- duplicate-file-finder-setup.exe (PID: 120)
- duplicate-file-finder-setup.tmp (PID: 128)
- reader.exe (PID: 268)
- duplicate-file-finder-setup.exe (PID: 2024)
- duplicate-file-finder-setup.tmp (PID: 2016)
- DuplicateFileFinder.exe (PID: 2340)
- DuplicateFileFinder.exe (PID: 1572)
- GASender.exe (PID: 1220)
Create files in a temporary directory
- duplicate-file-finder-setup.exe (PID: 120)
- duplicate-file-finder-setup.exe (PID: 2024)
- duplicate-file-finder-setup.tmp (PID: 2016)
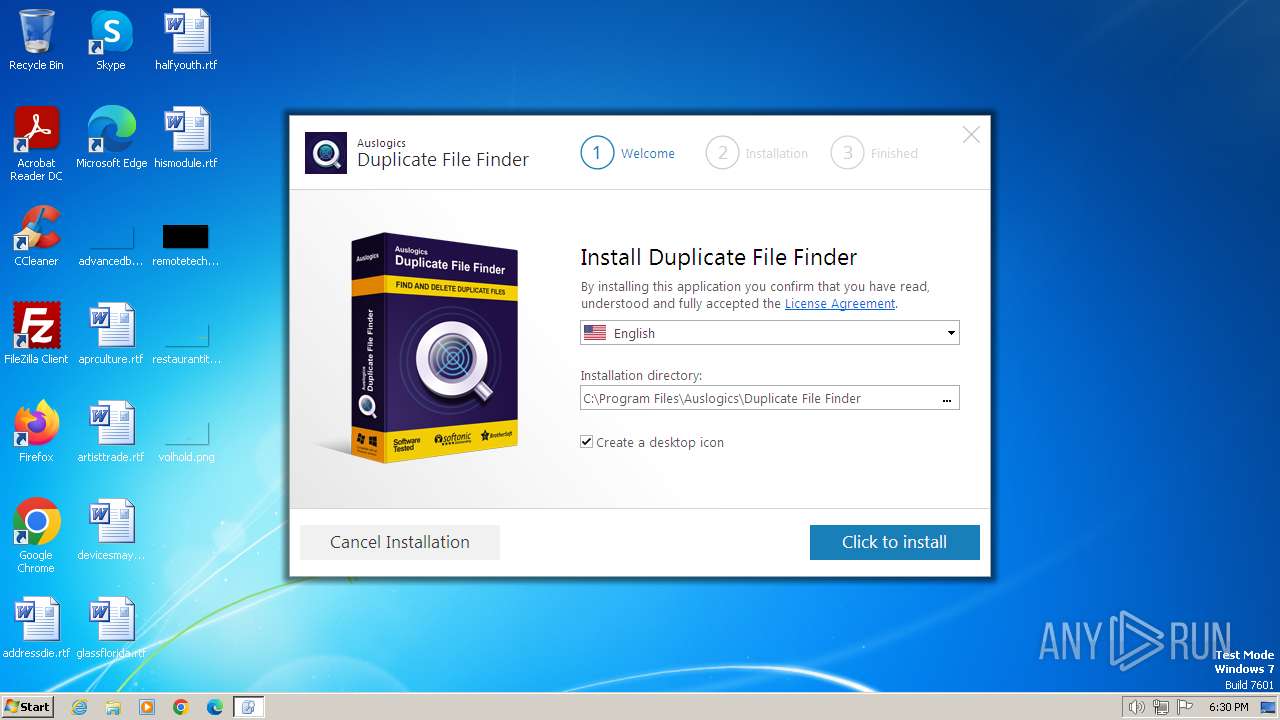
Drops the executable file immediately after the start
- duplicate-file-finder-setup.exe (PID: 120)
- duplicate-file-finder-setup.exe (PID: 2024)
- duplicate-file-finder-setup.tmp (PID: 2016)
Reads the computer name
- duplicate-file-finder-setup.tmp (PID: 2016)
- duplicate-file-finder-setup.tmp (PID: 128)
- DuplicateFileFinder.exe (PID: 1572)
- DuplicateFileFinder.exe (PID: 2340)
- GASender.exe (PID: 1220)
Process drops legitimate windows executable
- duplicate-file-finder-setup.tmp (PID: 2016)
Process drops SQLite DLL files
- duplicate-file-finder-setup.tmp (PID: 2016)
Process checks computer location settings
- duplicate-file-finder-setup.tmp (PID: 2016)
Reads the machine GUID from the registry
- duplicate-file-finder-setup.tmp (PID: 2016)
- DuplicateFileFinder.exe (PID: 1572)
- GASender.exe (PID: 1220)
Creates files or folders in the user directory
- duplicate-file-finder-setup.tmp (PID: 2016)
Creates files in the program directory
- duplicate-file-finder-setup.tmp (PID: 2016)
Checks proxy server information
- GASender.exe (PID: 1220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:07:16 15:24:20+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 65024 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x113bc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.2.0.0 |
| ProductVersionNumber: | 6.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Auslogics Labs Pty Ltd |
| FileDescription: | Auslogics Duplicate File Finder Installation File |
| FileVersion: | 6.2.0.0 |
| LegalCopyright: | Copyright © 2008-2017 Auslogics Labs Pty Ltd |
| ProductName: | Auslogics Duplicate File Finder |
| ProductVersion: | 6.2.0.0 |
Total processes
54
Monitored processes
14
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\AppData\Local\Temp\duplicate-file-finder-setup.exe" | C:\Users\admin\AppData\Local\Temp\duplicate-file-finder-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Auslogics Labs Pty Ltd Integrity Level: MEDIUM Description: Auslogics Duplicate File Finder Installation File Exit code: 0 Version: 6.2.0.0 Modules
| |||||||||||||||
| 128 | "C:\Users\admin\AppData\Local\Temp\is-USUPD.tmp\duplicate-file-finder-setup.tmp" /SL5="$301AA,7919988,139776,C:\Users\admin\AppData\Local\Temp\duplicate-file-finder-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-USUPD.tmp\duplicate-file-finder-setup.tmp | — | duplicate-file-finder-setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\reader.exe" "C:\Users\admin\AppData\Local\Temp\duplicate-file-finder-setup.exe" "(x32)HKEY_LOCAL_MACHINE\Software\Auslogics\Duplicate File Finder\6.x\Settings" | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\reader.exe | — | duplicate-file-finder-setup.tmp | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 696 | C:\Windows\system32\DllHost.exe /Processid:{93469602-4134-4012-A6BC-67DE7D0C96E3} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1220 | "C:\Users\admin\AppData\Local\Temp\_Del_duplicate-file-finder-setup\GASender.exe" C:\Users\admin\AppData\Local\Temp\_Del_duplicate-file-finder-setup\GA.json | C:\Users\admin\AppData\Local\Temp\_Del_duplicate-file-finder-setup\GASender.exe | cmd.exe | ||||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: GoogleAnalyticsSender Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
| 1496 | "C:\Windows\system32\regsvr32.exe" /s "C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\BrowserCareHelper.Agent.x32.dll" | C:\Windows\System32\regsvr32.exe | — | duplicate-file-finder-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1540 | "C:\Windows\system32\regsvr32.exe" /s /u "C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\BrowserCareHelper.Agent.x32.dll" | C:\Windows\System32\regsvr32.exe | — | duplicate-file-finder-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | "C:\Program Files\Auslogics\Duplicate File Finder\DuplicateFileFinder.exe" | C:\Program Files\Auslogics\Duplicate File Finder\DuplicateFileFinder.exe | — | duplicate-file-finder-setup.tmp | |||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: Duplicate File Finder Exit code: 0 Version: 6.2.0.0 Modules
| |||||||||||||||
| 1736 | "C:\Windows\system32\regsvr32.exe" /s "C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\BrowserCareHelper.Agent.x32.dll" | C:\Windows\System32\regsvr32.exe | — | duplicate-file-finder-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1812 | /C "start "title" "C:\Users\admin\AppData\Local\Temp\_Del_duplicate-file-finder-setup\GASender.exe" C:\Users\admin\AppData\Local\Temp\_Del_duplicate-file-finder-setup\GA.json" | C:\Windows\System32\cmd.exe | — | duplicate-file-finder-setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 762
Read events
2 677
Write events
37
Delete events
48
Modification events
| (PID) Process: | (2016) duplicate-file-finder-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2016) duplicate-file-finder-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2016) duplicate-file-finder-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2016) duplicate-file-finder-setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1820) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{F2C6F7D1-ED32-49E5-9919-2DEB70C0A642}\1.0\0\win32 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1820) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{F2C6F7D1-ED32-49E5-9919-2DEB70C0A642}\1.0\0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1820) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{F2C6F7D1-ED32-49E5-9919-2DEB70C0A642}\1.0\HELPDIR |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1820) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{F2C6F7D1-ED32-49E5-9919-2DEB70C0A642}\1.0\FLAGS |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1820) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{F2C6F7D1-ED32-49E5-9919-2DEB70C0A642}\1.0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1820) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{F2C6F7D1-ED32-49E5-9919-2DEB70C0A642} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
76
Suspicious files
33
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 120 | duplicate-file-finder-setup.exe | C:\Users\admin\AppData\Local\Temp\is-USUPD.tmp\duplicate-file-finder-setup.tmp | executable | |
MD5:B185DD40B76641E050F02C01F94859B6 | SHA256:36E8B6C714EECEBDAF99FCD44FB6505546687B5F9069CBDDC7A853D14AE3B47C | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\SetupCustom.dll | executable | |
MD5:2EAD10DF0EC46F5872D60B585802EAE4 | SHA256:CBD24513994675EF848DFC6851C410D0552BDFFDCD9BA119118A473F7C1E71B6 | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\AxComponentsRTL.bpl | executable | |
MD5:787433D71D05BB75237B75D536D1D14D | SHA256:E0E8F3823003B08D1F2D34667CBEF1D7790F23BE11605DD71FF0893ADB53DA17 | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\AxBrowsers.dll | executable | |
MD5:7938D0049CE63444C1C58730DD447235 | SHA256:00C31E62C23DC4122CC6F71011A30DC1AC297CFD593A036380C000F140F01F1E | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\CommonForms.Site.dll | executable | |
MD5:E2A94A832970037D83BD7BDFA776C8B6 | SHA256:AF5A747EE81B6F77A5ACAC2A3AE977A7DB8DDA629AE1EC34A95061B1F4C78D4D | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\DuplicateFileFinder.exe | executable | |
MD5:A657699B2965A7644E7BD1B2BAF224D6 | SHA256:F9BB68A3B97B5FC99FCADB48960805EB30ED51DE5E1AEB586C076E068EF8A727 | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\sqlite3.dll | executable | |
MD5:9103797E3C159B30E716FCABB33BBB52 | SHA256:153277BE579DE0EBA8D1C2FF016BF4A1CBCABD96A98F564EE1130EAA3D0A4119 | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\Localizer.dll | executable | |
MD5:C32C2ABEDA3F0C5134A9DA6C52ECF202 | SHA256:CDDCC7113C05F0009C8836654B367FFA2F2B41CCDD20EE7553ED085E08C09C06 | |||
| 2016 | duplicate-file-finder-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-BV000.tmp\reader.exe | executable | |
MD5:56EFB0F436BC2A9CF61DC723B03558DA | SHA256:E201CABB4803A83C2F5852A26EE07952258AAAC6A9030D98DACB3114C52D2119 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
1220 | GASender.exe | POST | 200 | 142.250.185.206:80 | http://www.google-analytics.com/collect | unknown | image | 35 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1220 | GASender.exe | 142.250.185.206:80 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |