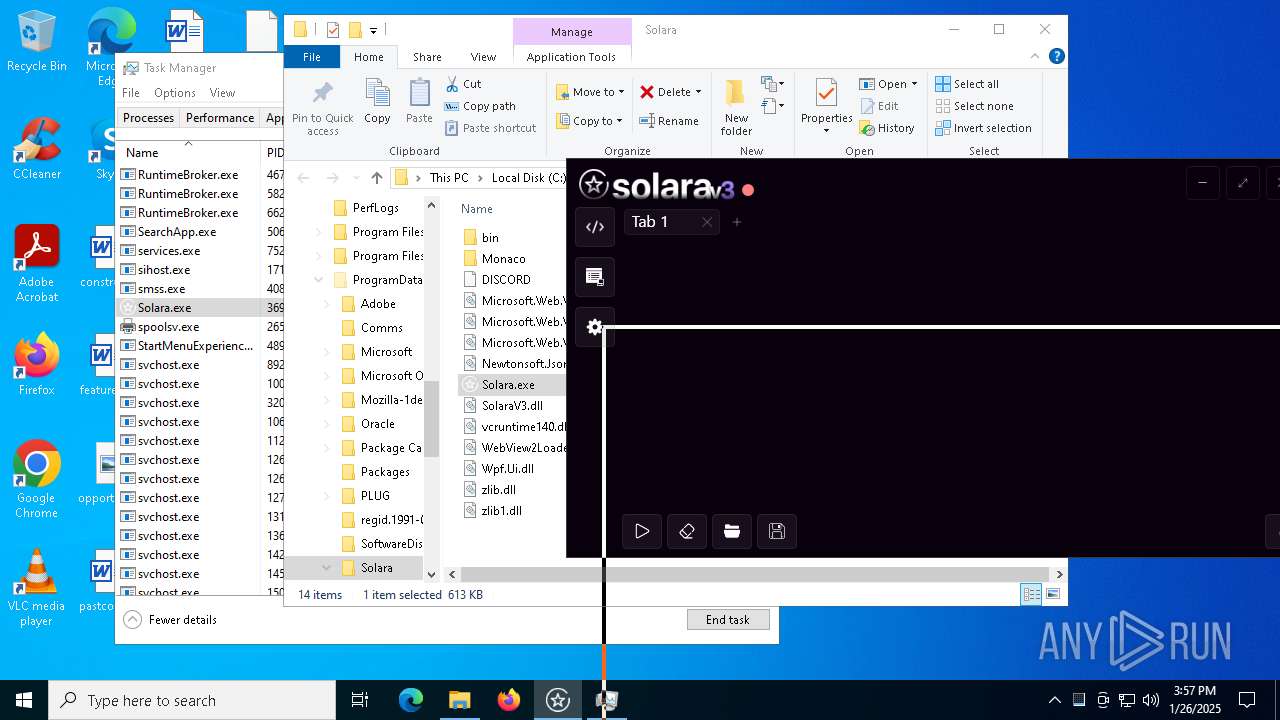
| File name: | BootstrapperNew(1).exe |
| Full analysis: | https://app.any.run/tasks/5d6ec585-36eb-400f-9330-c48c1a4aee4b |
| Verdict: | Malicious activity |
| Analysis date: | January 26, 2025, 15:55:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | 4D207914AB7B161D4A8E6BF45CD27DE4 |
| SHA1: | ACCD340B49754A770FD8DEBC10A379FE587336F6 |
| SHA256: | 3C4DCF944E748C91DF983422349E3A10F8271D3EF77CEEE73D071B3D5E764F1B |
| SSDEEP: | 98304:FYzoojJRba+nPSqNCrRasNk0LW4kr+zIIvt4Fi1VG86jieQEnYr2OCQekIflB2bQ:y+J |
MALICIOUS
Adds path to the Windows Defender exclusion list
- BootstrapperNew(1).exe (PID: 6276)
SUSPICIOUS
Reads security settings of Internet Explorer
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeUpdate.exe (PID: 6076)
- Solara.exe (PID: 3696)
Script adds exclusion path to Windows Defender
- BootstrapperNew(1).exe (PID: 6276)
Starts POWERSHELL.EXE for commands execution
- BootstrapperNew(1).exe (PID: 6276)
Executable content was dropped or overwritten
- BootstrapperNew(1).exe (PID: 6276)
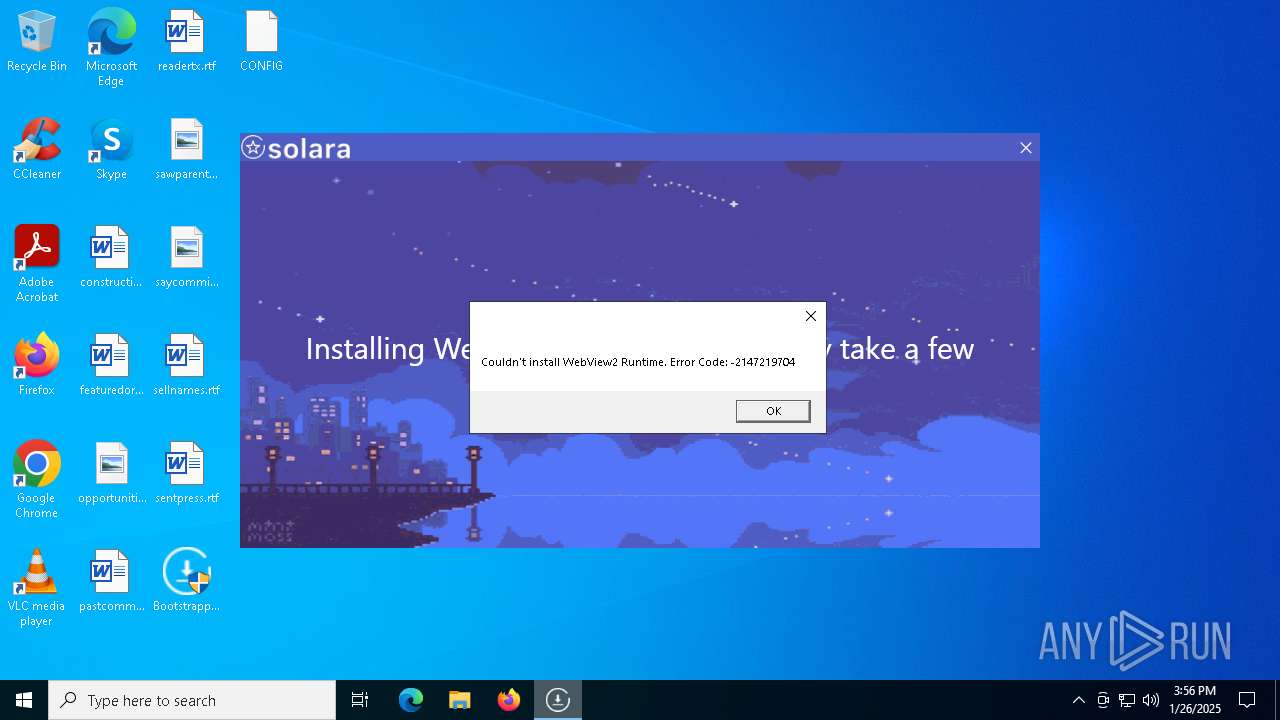
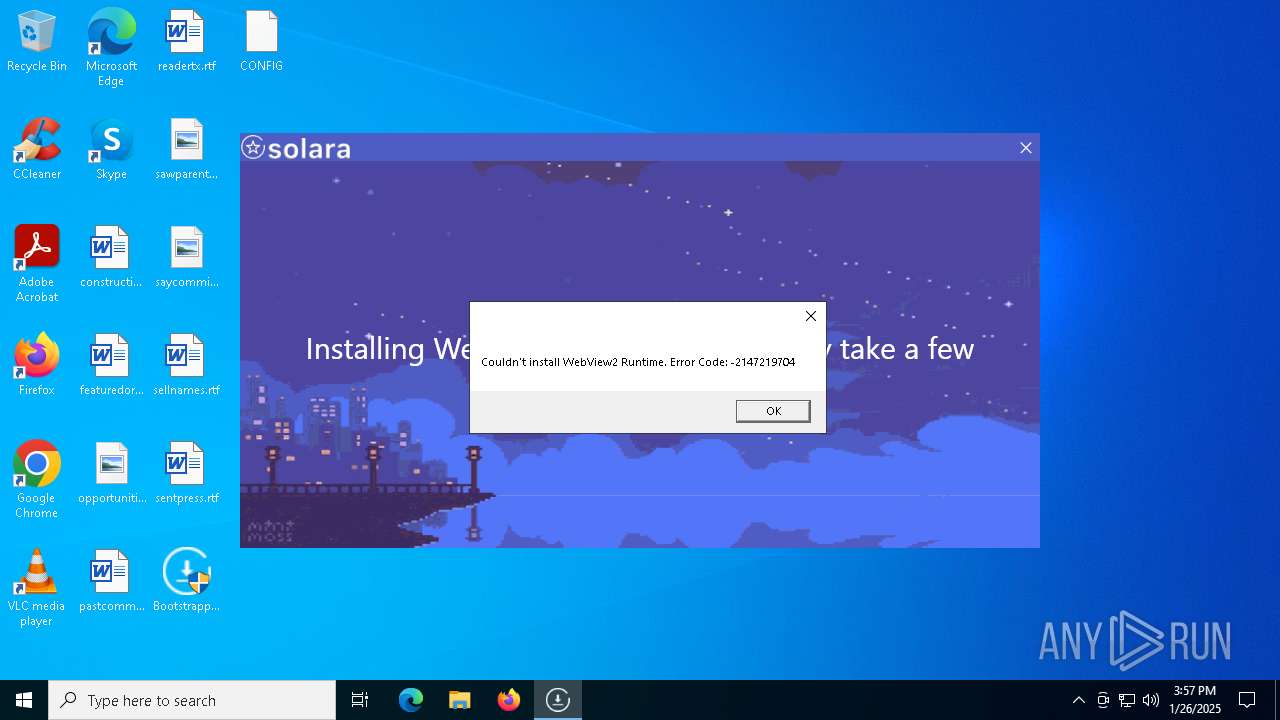
- MicrosoftEdgeWebview2Setup.exe (PID: 7032)
Process drops legitimate windows executable
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeWebview2Setup.exe (PID: 7032)
- MicrosoftEdgeUpdate.exe (PID: 6076)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 7032)
- MicrosoftEdgeUpdate.exe (PID: 6076)
Disables SEHOP
- MicrosoftEdgeUpdate.exe (PID: 6076)
The process drops C-runtime libraries
- BootstrapperNew(1).exe (PID: 6276)
Reads the date of Windows installation
- BootstrapperNew(1).exe (PID: 6276)
Reads the BIOS version
- Solara.exe (PID: 3696)
Query Microsoft Defender preferences
- BootstrapperNew(1).exe (PID: 6276)
INFO
Reads the computer name
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeUpdate.exe (PID: 6076)
- Solara.exe (PID: 3696)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeUpdate.exe (PID: 6076)
- wermgr.exe (PID: 6912)
- Solara.exe (PID: 3696)
Reads the machine GUID from the registry
- BootstrapperNew(1).exe (PID: 6276)
- SearchApp.exe (PID: 5064)
- Solara.exe (PID: 3696)
Checks supported languages
- BootstrapperNew(1).exe (PID: 6276)
- SearchApp.exe (PID: 5064)
- MicrosoftEdgeWebview2Setup.exe (PID: 7032)
- MicrosoftEdgeUpdate.exe (PID: 6076)
- Solara.exe (PID: 3696)
Creates files in the program directory
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeWebview2Setup.exe (PID: 7032)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 4384)
- powershell.exe (PID: 6568)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6568)
Checks proxy server information
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeUpdate.exe (PID: 6076)
- wermgr.exe (PID: 6912)
- Solara.exe (PID: 3696)
Disables trace logs
- BootstrapperNew(1).exe (PID: 6276)
- Solara.exe (PID: 3696)
Create files in a temporary directory
- BootstrapperNew(1).exe (PID: 6276)
The sample compiled with english language support
- BootstrapperNew(1).exe (PID: 6276)
- MicrosoftEdgeWebview2Setup.exe (PID: 7032)
- MicrosoftEdgeUpdate.exe (PID: 6076)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 6076)
- Solara.exe (PID: 3696)
- BootstrapperNew(1).exe (PID: 6276)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 6076)
- BootstrapperNew(1).exe (PID: 6276)
- SearchApp.exe (PID: 5064)
Creates files or folders in the user directory
- wermgr.exe (PID: 6912)
Manual execution by a user
- Taskmgr.exe (PID: 6968)
- Taskmgr.exe (PID: 3420)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6968)
Process checks whether UAC notifications are on
- Solara.exe (PID: 3696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2080:06:10 14:23:56+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 2994688 |
| InitializedDataSize: | 9216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Bootstrapper |
| FileVersion: | 1.0.0.0 |
| InternalName: | Bootstrapper.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | Bootstrapper.exe |
| ProductName: | Bootstrapper |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
145
Monitored processes
15
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1220 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3696 | "C:\ProgramData\Solara\Solara.exe" | C:\ProgramData\Solara\Solara.exe | BootstrapperNew(1).exe | ||||||||||||
User: admin Company: CMD Softworks Integrity Level: HIGH Description: Solara V3 Version: 3.0.0.0 Modules
| |||||||||||||||
| 4384 | "powershell" -Command "Get-MpPreference | Select-Object -ExpandProperty ExclusionPath" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | BootstrapperNew(1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5392 | "C:\Users\admin\Desktop\BootstrapperNew(1).exe" | C:\Users\admin\Desktop\BootstrapperNew(1).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Bootstrapper Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6076 | "C:\Program Files (x86)\Microsoft\Temp\EU4E0F.tmp\MicrosoftEdgeUpdate.exe" /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Program Files (x86)\Microsoft\Temp\EU4E0F.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Update Exit code: 2147747592 Version: 1.3.195.43 Modules
| |||||||||||||||
| 6276 | "C:\Users\admin\Desktop\BootstrapperNew(1).exe" | C:\Users\admin\Desktop\BootstrapperNew(1).exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
22 011
Read events
21 915
Write events
90
Delete events
6
Modification events
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 50111 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 000052A49AC50A70DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | \REGISTRY\A\{ee080948-b2ea-145a-6870-f9164b908eb9}\LocalState\DynamicSearchBox |
| Operation: | write | Name: | TelemetryID |
Value: 000069599FC50A70DB01 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\Internet Explorer\DOMStorage\bing.com |
| Operation: | write | Name: | Total |
Value: 50667 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsAADCloudSearchEnabled |
Value: 0 | |||
Executable files
211
Suspicious files
23
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:5A2319A8A6ABF90BD79D1AD5F5384F96 | SHA256:442C7C0EADCC492BD2483121EFE86004CF6BEF367DB81EECC8DA5AD3602DF328 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\95d9a2a97a42f02325559b453ba7f8fe839baa18.tbres | binary | |
MD5:A5BAF5E460C1F5D914B8B00310974526 | SHA256:79FCAF8B5B4477ACBCA2F39FFC12D9D337AD4EACC2EB6AD7D8FAF1ABE4BDD918 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\Q84V0JUH\fpconfig.min[1].json | binary | |
MD5:3855374125A0A7A2B30A0548A2E079BF | SHA256:5EFADD6CDF7C28B32AF2A7C4A0AAA3604CEBEB6922C5C8EB989851FA4BBD6D0D | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:7461DB9E0CE36DB5BE811DDB633A0D3D | SHA256:D8A288A3E28E2E05D7E4F11411D9071CD0B15971CB196E59803D8401186E0ED8 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:6C12C74F976F99542E86212A9B2A4713 | SHA256:488779F0E05A70F50DA15B666FD500BB88B2FDEC821F1959A99FDE805BC9302C | |||
| 6276 | BootstrapperNew(1).exe | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | executable | |
MD5:B49D269A231BCF719D6DE10F6DCF0692 | SHA256:BDE514014B95C447301D9060A221EFB439C3C1F5DB53415F080D4419DB75B27E | |||
| 4384 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:F4E43DDA49C1D38F0D56D1C4E6486DE3 | SHA256:EA76F868D0BEC08716AFA4D8FABD8A91146C49C427105DC2A97661C9E4098FA0 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\M8N5R19A\trans[1].gif | image | |
MD5:325472601571F31E1BF00674C368D335 | SHA256:B1442E85B03BDCAF66DC58C7ABB98745DD2687D86350BE9A298A1D9382AC849B | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\INetCache\NLQCMX2T\trans[1].gif | image | |
MD5:325472601571F31E1BF00674C368D335 | SHA256:B1442E85B03BDCAF66DC58C7ABB98745DD2687D86350BE9A298A1D9382AC849B | |||
| 4384 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fqftsd2k.3x0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
55
DNS requests
36
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.180:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3952 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3612 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3952 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6912 | wermgr.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 23.48.23.180:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5880 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1076 | svchost.exe | 2.23.242.9:443 | go.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
1176 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO DNS Query to Cloudflare Page Developer Domain (pages .dev) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |
6276 | BootstrapperNew(1).exe | Misc activity | ET INFO Observed Cloudflare Page Developer Domain (pages .dev in TLS SNI) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |