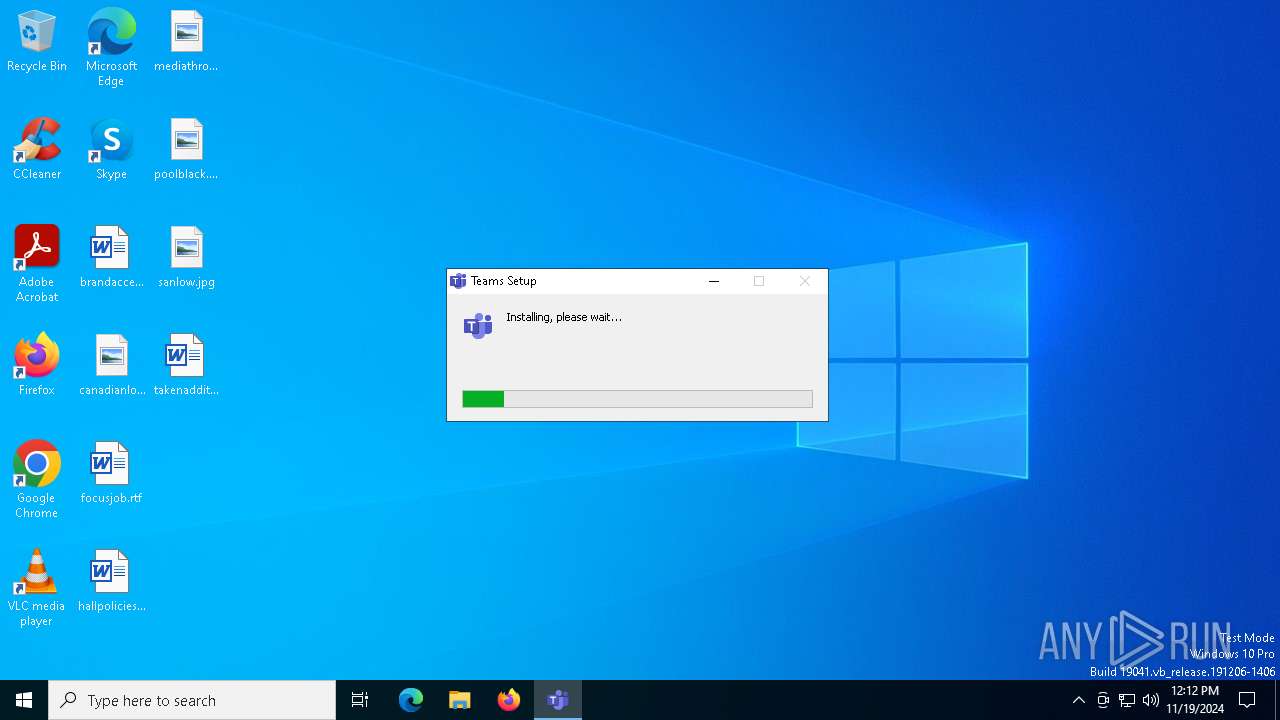
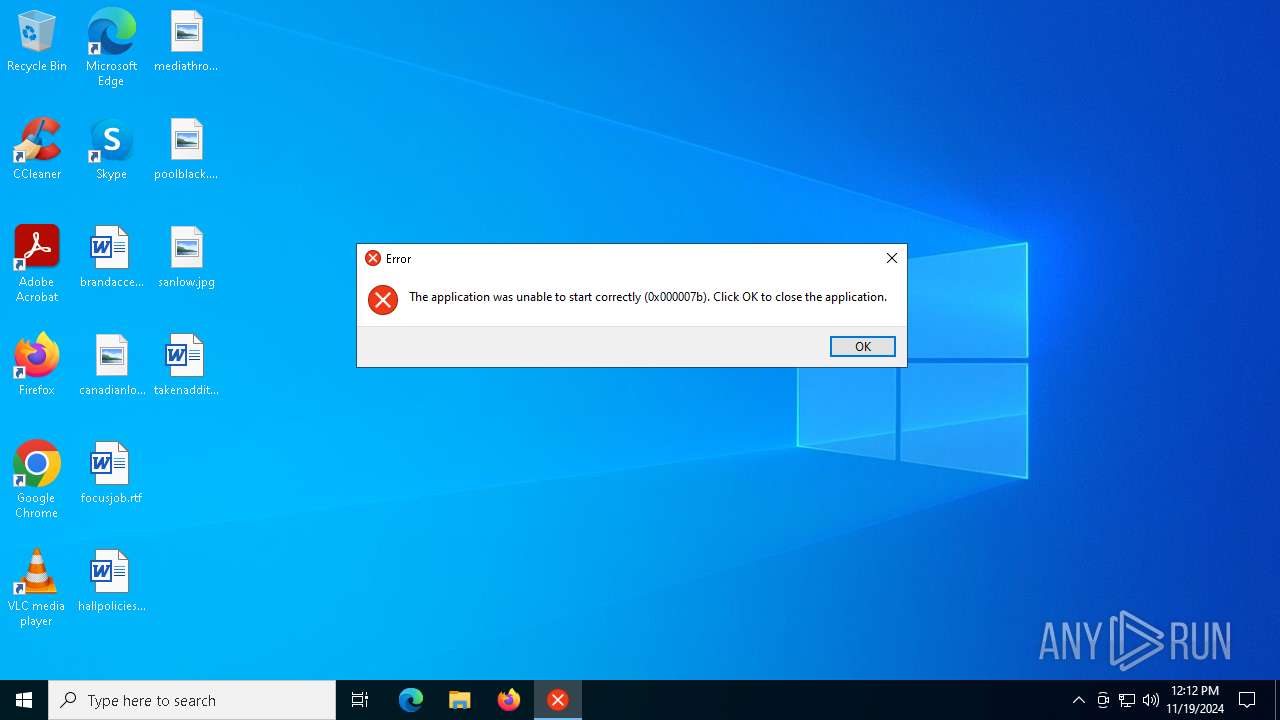
| File name: | Chromium Setup x64.exe |
| Full analysis: | https://app.any.run/tasks/b90717e9-eecb-4d1e-bcd0-34836d989332 |
| Verdict: | Malicious activity |
| Analysis date: | November 19, 2024, 12:11:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | B408E3DA98F0E457D627510165374DDD |
| SHA1: | 49DE055D881896670CE8B1BA1633D5F8B4F8E193 |
| SHA256: | 3C3F458400C557D279C4D4993F67ADC8BA3DA4BAD8FC844ADFEF8C7DE475A1F7 |
| SSDEEP: | 786432:cf9I04sVpGuNS6r0aMdCRzM9jhXtoe8qCs2VVsh48:cf9IvqGuS807dljhXqe2VVsh48 |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- Chromium Setup x64.exe (PID: 3208)
Malware-specific behavior (creating "System.dll" in Temp)
- Chromium Setup x64.exe (PID: 3208)
Process drops legitimate windows executable
- Chromium Setup x64.exe (PID: 3208)
Drops 7-zip archiver for unpacking
- Chromium Setup x64.exe (PID: 3208)
Starts CMD.EXE for commands execution
- Chromium Setup x64.exe (PID: 3208)
- Teams.exe (PID: 2356)
Application launched itself
- Teams.exe (PID: 2356)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4224)
Executable content was dropped or overwritten
- Chromium Setup x64.exe (PID: 3208)
Get information on the list of running processes
- Chromium Setup x64.exe (PID: 3208)
- cmd.exe (PID: 1296)
INFO
Checks supported languages
- Chromium Setup x64.exe (PID: 3208)
Create files in a temporary directory
- Chromium Setup x64.exe (PID: 3208)
Reads the computer name
- Chromium Setup x64.exe (PID: 3208)
Manual execution by a user
- Teams.exe (PID: 2356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:12:15 22:26:14+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 473088 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.1.0 |
| ProductVersionNumber: | 5.1.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | - |
| FileVersion: | 5.1.1 |
| LegalCopyright: | Copyright © 2024 Teams |
| ProductName: | Teams |
| ProductVersion: | 5.1.1 |
Total processes
127
Monitored processes
11
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1296 | "C:\WINDOWS\system32\cmd.exe" /c tasklist /FI "USERNAME eq %USERNAME%" /FI "IMAGENAME eq Teams.exe" /FO csv | "C:\WINDOWS\system32\find.exe" "Teams.exe" | C:\Windows\SysWOW64\cmd.exe | — | Chromium Setup x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2292 | tasklist /FI "USERNAME eq admin" /FI "IMAGENAME eq Teams.exe" /FO csv | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe" | C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe | — | explorer.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: Teams Version: 5.1.1 Modules
| |||||||||||||||
| 3172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3208 | "C:\Users\admin\AppData\Local\Temp\Chromium Setup x64.exe" | C:\Users\admin\AppData\Local\Temp\Chromium Setup x64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 5.1.1 Modules
| |||||||||||||||
| 4224 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell "$s=(New-Object -COM WScript.Shell).CreateShortcut('C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\MyElectronApp.lnk');$s.TargetPath='C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe';$s.Save()"" | C:\Windows\System32\cmd.exe | — | Teams.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4340 | "C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\Teams" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1732,i,13304316585699375969,10617647254705402608,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=1724 /prefetch:2 | C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe | — | Teams.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: Teams Version: 5.1.1 Modules
| |||||||||||||||
| 5752 | "C:\WINDOWS\system32\find.exe" "Teams.exe" | C:\Windows\SysWOW64\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6148 | "C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\Teams" --field-trial-handle=2080,i,13304316585699375969,10617647254705402608,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2076 /prefetch:3 | C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe | — | Teams.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: Teams Version: 5.1.1 Modules
| |||||||||||||||
Total events
6 216
Read events
6 205
Write events
11
Delete events
0
Modification events
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\Teams | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | ShortcutName |
Value: Teams | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | DisplayName |
Value: Teams 5.1.1 | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\Teams\Uninstall Teams.exe" /currentuser | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\Teams\Uninstall Teams.exe" /currentuser /S | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | DisplayVersion |
Value: 5.1.1 | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Local\Programs\Teams\Teams.exe,0 | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (3208) Chromium Setup x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\8013f783-e1a2-5f53-80da-b1ad483bd59f |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
24
Suspicious files
129
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\nsExec.dll | executable | |
MD5:EC0504E6B8A11D5AAD43B296BEEB84B2 | SHA256:5D9CEB1CE5F35AEA5F9E5A0C0EDEEEC04DFEFE0C77890C80C70E98209B58B962 | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\locales\cs.pak | pgc | |
MD5:92E3FD1EB47767A0CB5F6E734DE4EEC1 | SHA256:D269E16FBD9B2AFE95B148ECE22B2AC803768FB53EE42E1FAD0181F9DEC84544 | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\chrome_200_percent.pak | pgc | |
MD5:DC48A33BD20BFC7CACFC925A84B015B6 | SHA256:2C1B3E4B8A0CF837AE0A390FCA54F45D7D22418E040F1DFEA979622383ACCED6 | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\locales\bg.pak | pgc | |
MD5:7C37C8C9B4215089B6C16D22838D256B | SHA256:2EBD582DFAA3139CD6A03E9892A94A3D9BB6936E0B04085B8F2D27E1DEC0BC8A | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\LICENSE.electron.txt | text | |
MD5:4D42118D35941E0F664DDDBD83F633C5 | SHA256:5154E165BD6C2CC0CFBCD8916498C7ABAB0497923BAFCD5CB07673FE8480087D | |||
| 3208 | Chromium Setup x64.exe | C:\Users\admin\AppData\Local\Temp\nsrD88A.tmp\7z-out\locales\ca.pak | pgc | |
MD5:E1AC7F4C28177F68FAC3BE2375A9368C | SHA256:EFA1BA906F8ABCE91EBB9D6442B64E0D5AE7DAB78DDA8A49A6FED1A342C71B9B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
33
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4932 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3812 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4932 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 92.123.104.11:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.31.69:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |