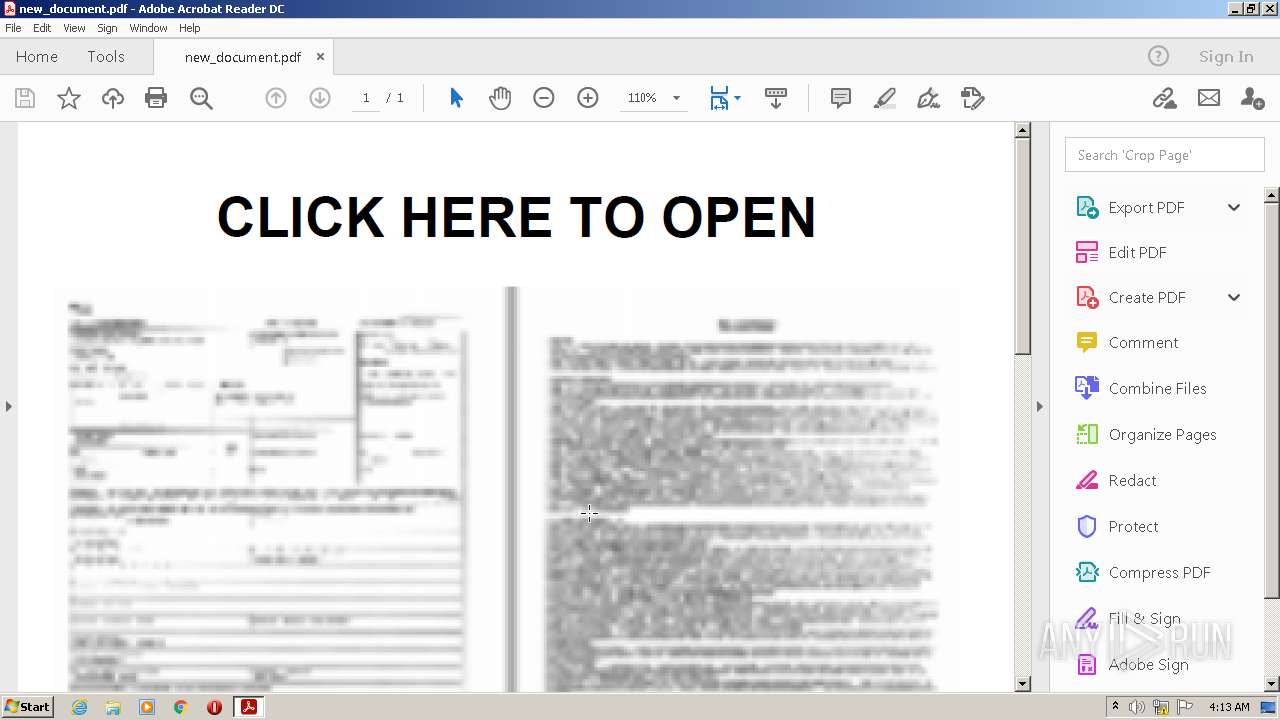
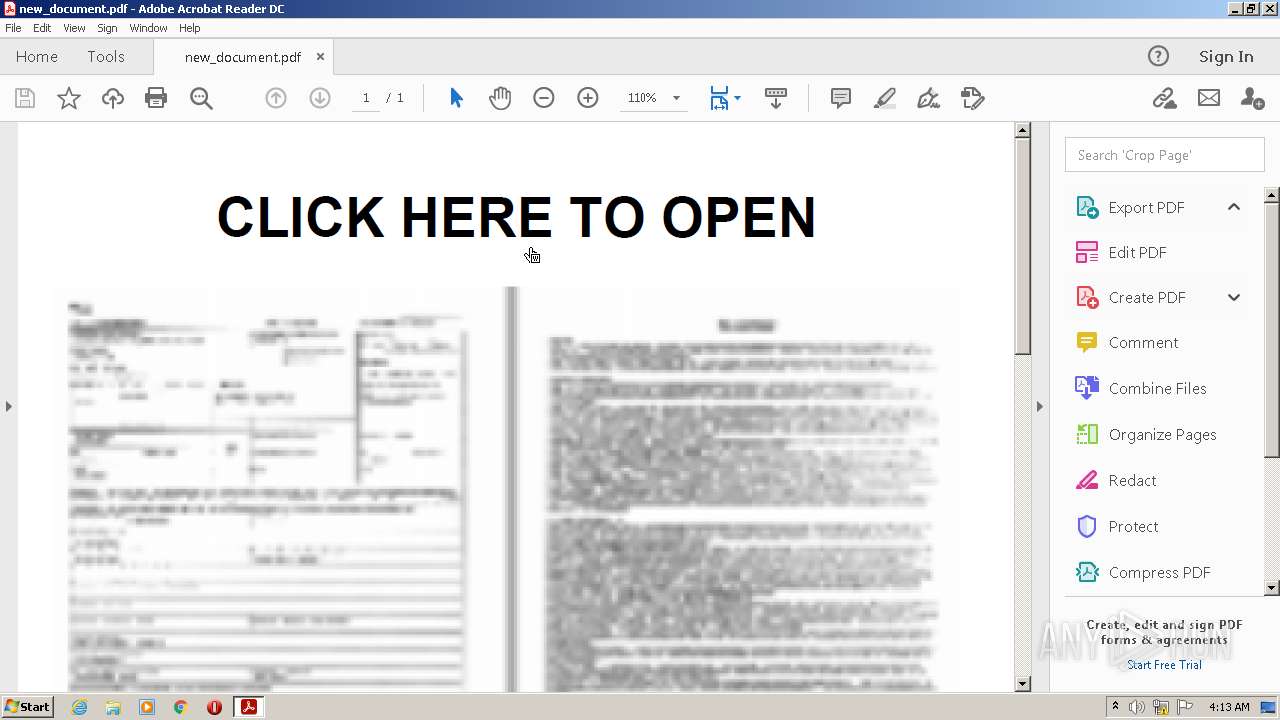
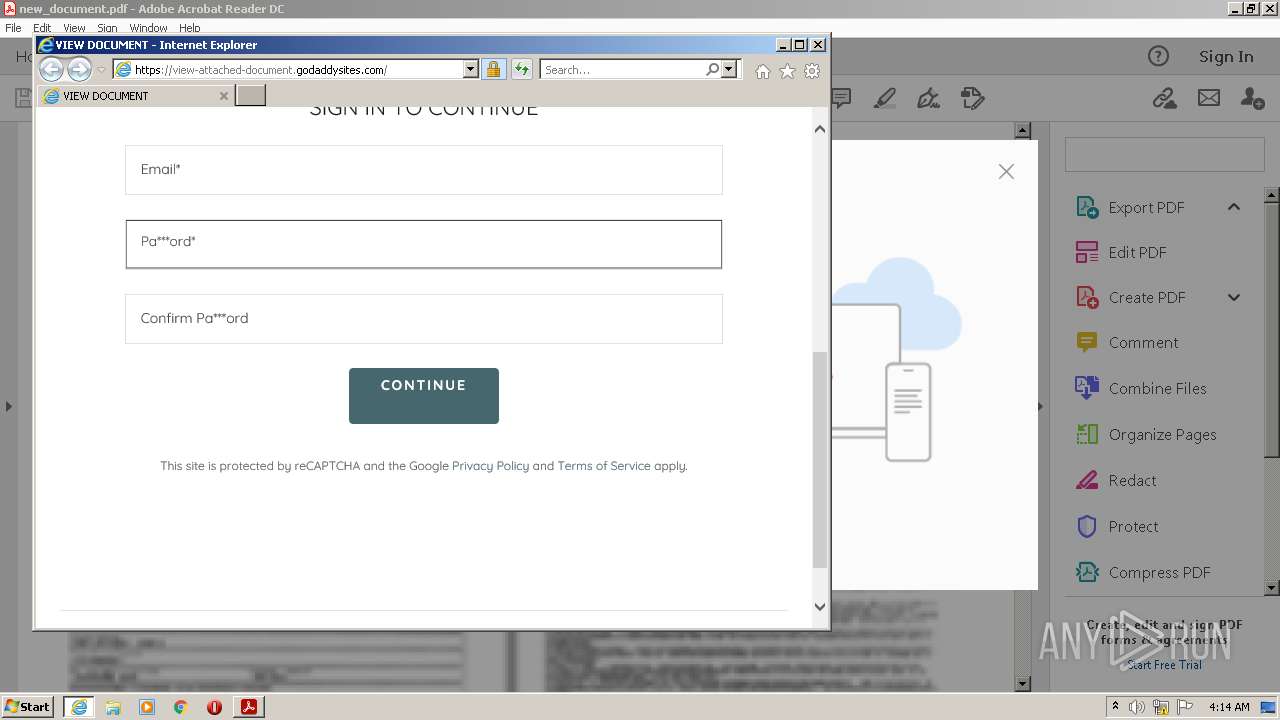
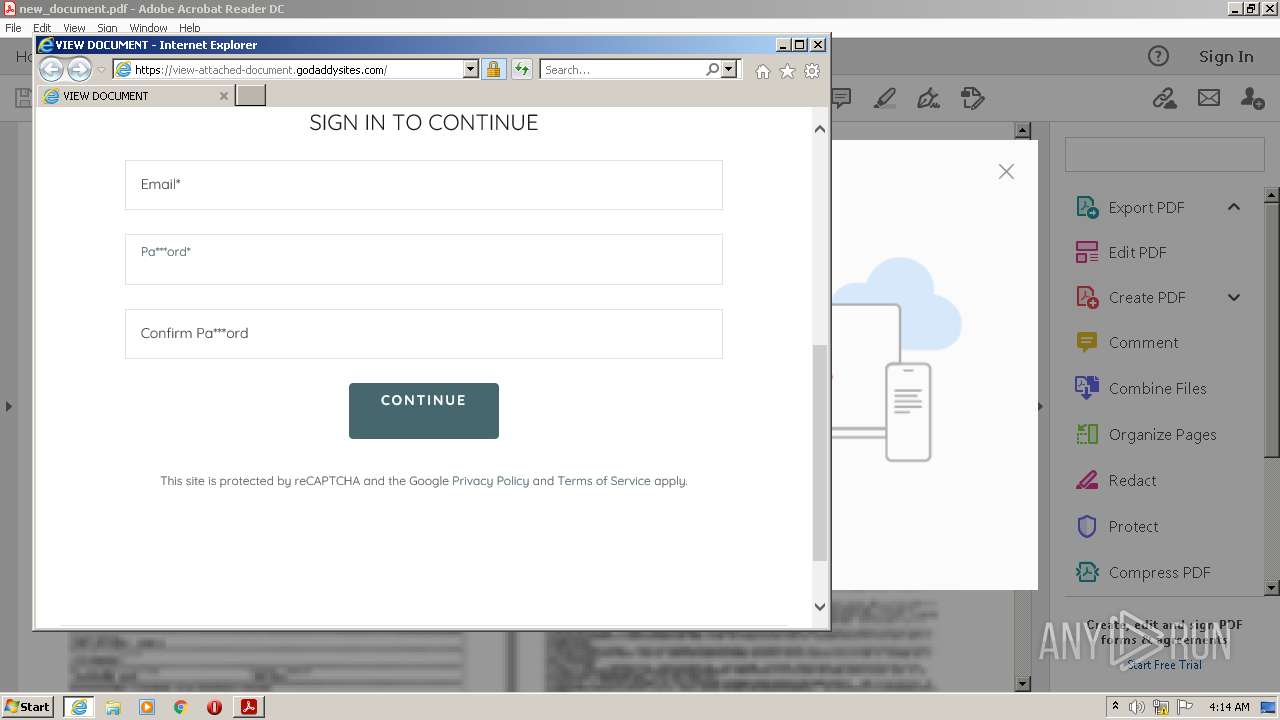
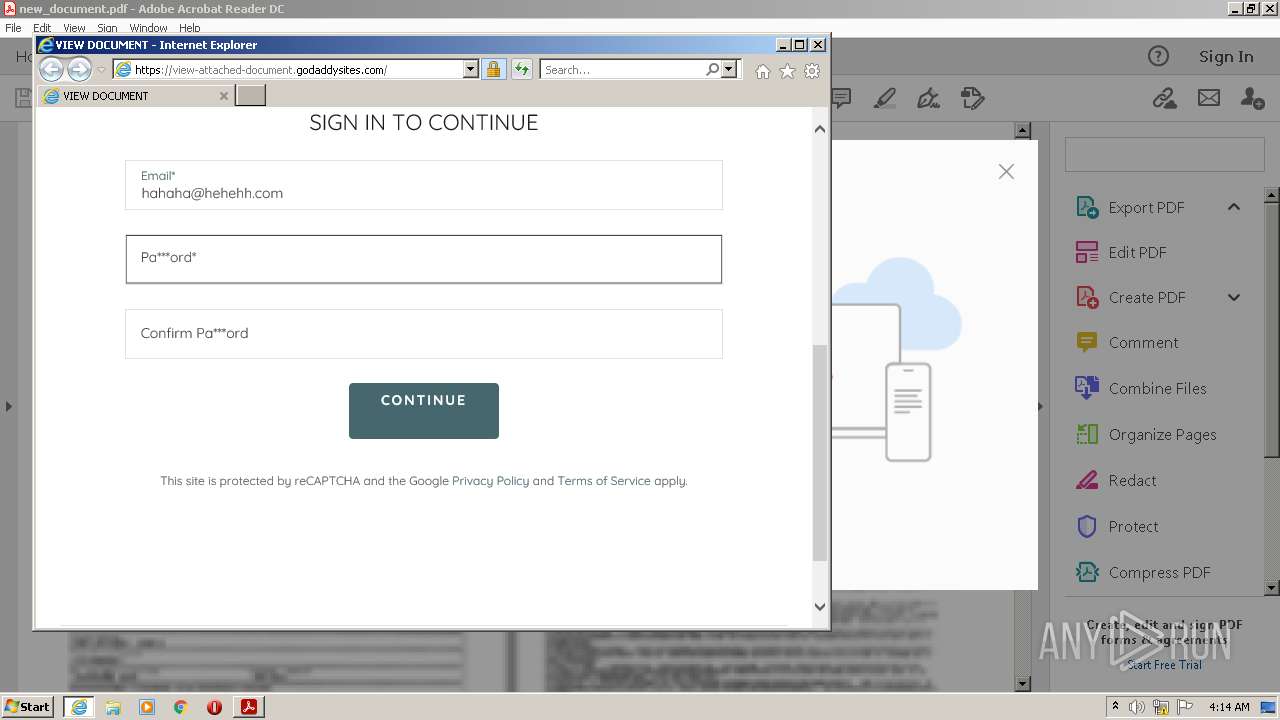
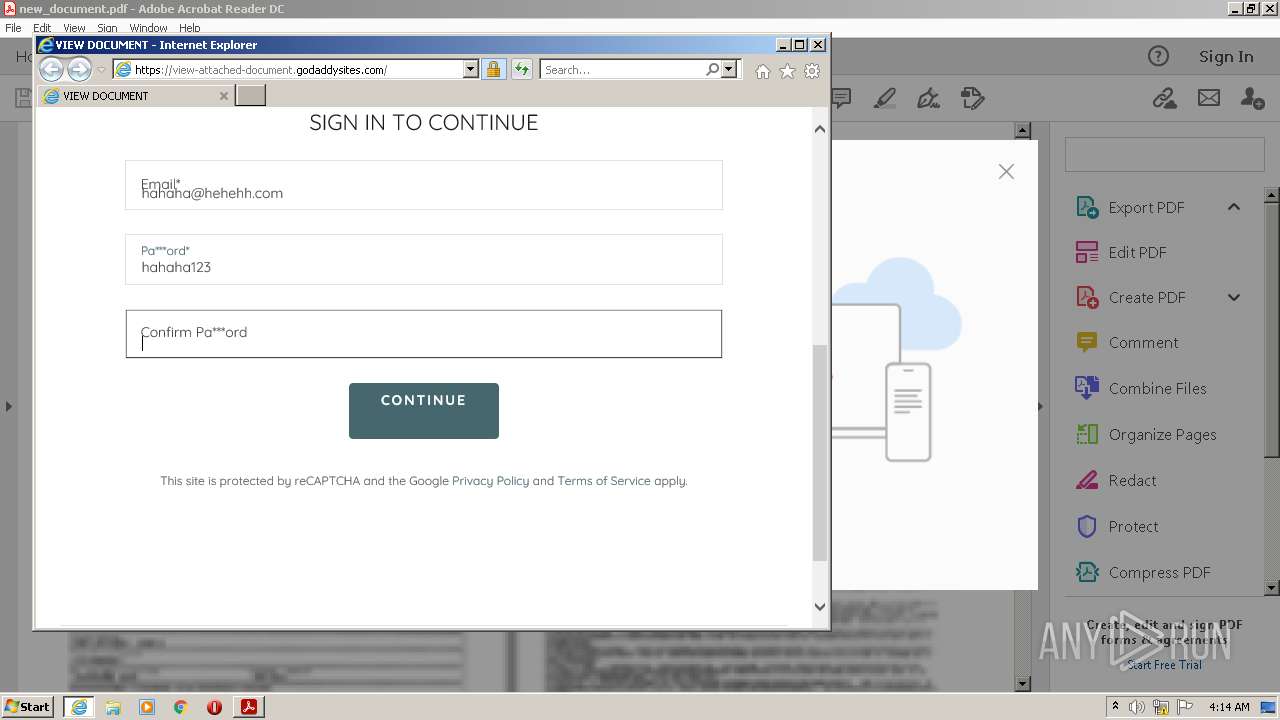
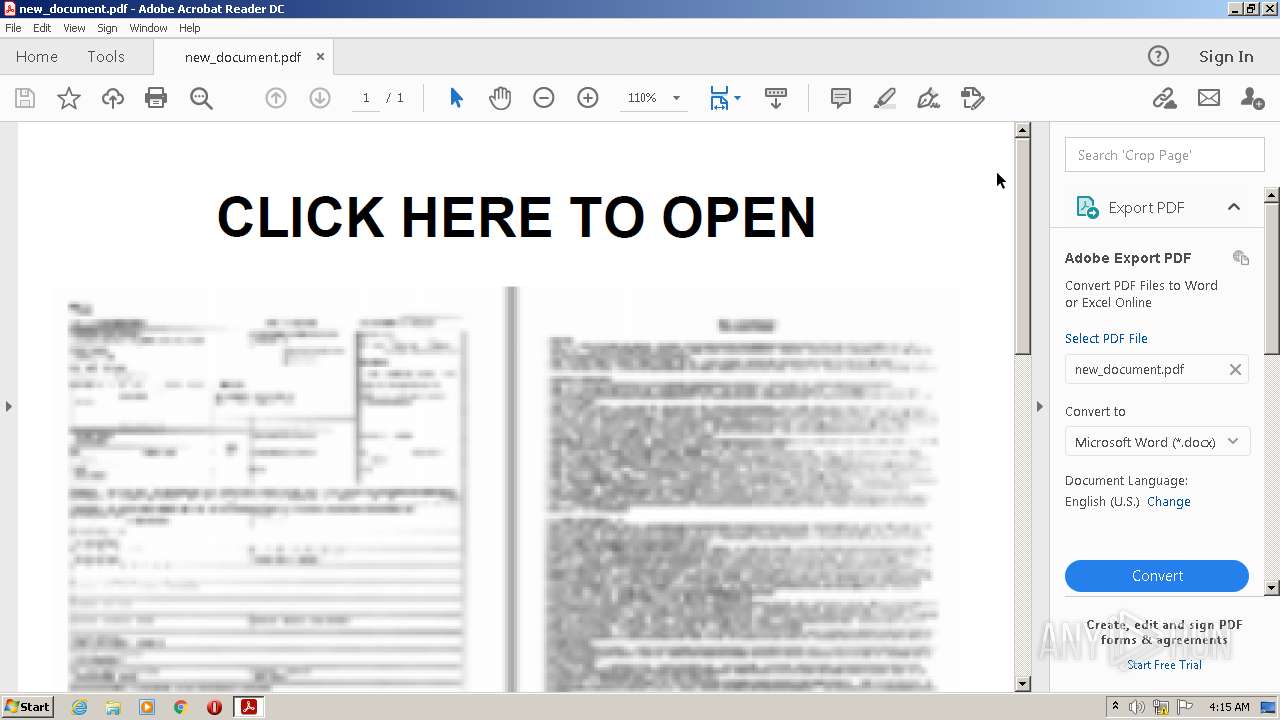
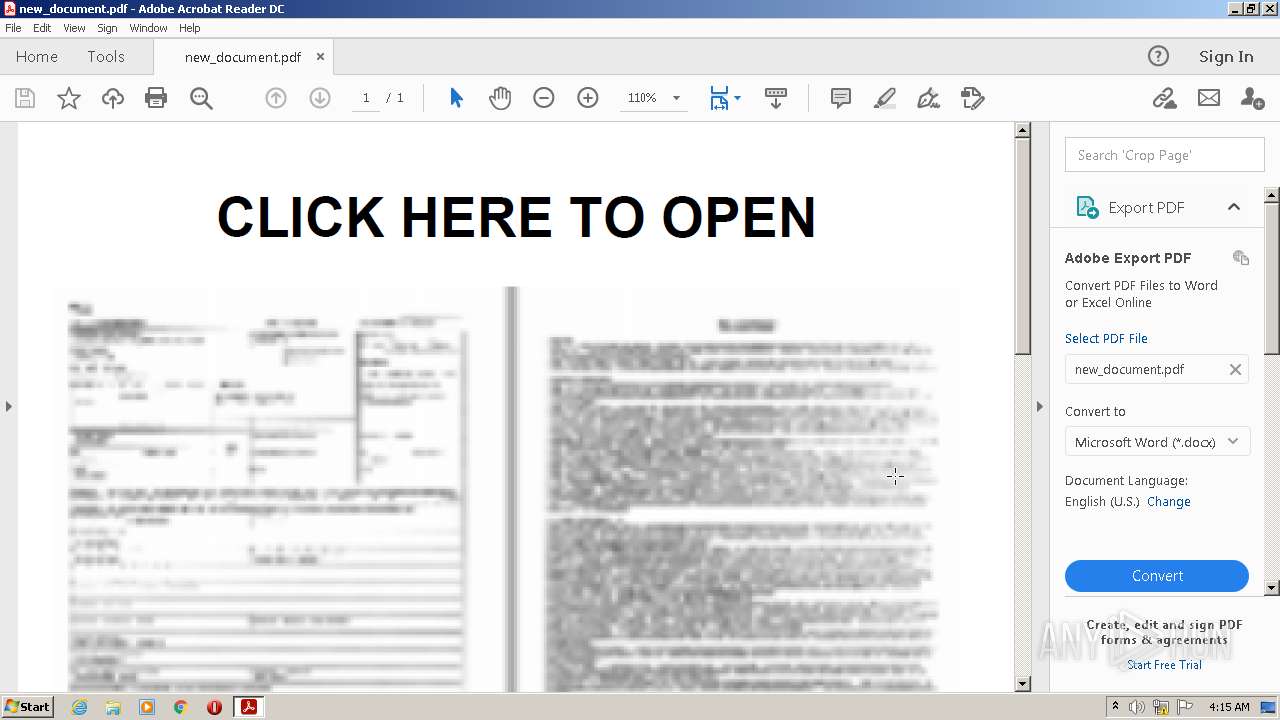
| File name: | new_document.pdf |
| Full analysis: | https://app.any.run/tasks/0f0fb3a6-10db-4d06-9f4b-2d0f482e9714 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 03:13:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.5 |
| MD5: | 367C72F09DCD299D3EC2907FF4E87221 |
| SHA1: | 15C371B048969B15E8F8C4B188CA8BD410F66976 |
| SHA256: | 3C13E20F21E341259BA79D0F1328581615A178BAEDCE68543195AE03A9F63CBD |
| SSDEEP: | 768:toR9cuZO2an7sj+Wws3ox50pNcxekMJMhLSR2YixZc+G2d/czE:EcQBQ5ZtNSXincLA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 2228)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2608)
Checks supported languages
- AdobeARM.exe (PID: 768)
- Reader_sl.exe (PID: 2596)
Reads the computer name
- AdobeARM.exe (PID: 768)
Creates files in the program directory
- AdobeARM.exe (PID: 768)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 768)
INFO
Checks supported languages
- AcroRd32.exe (PID: 2228)
- RdrCEF.exe (PID: 3544)
- AcroRd32.exe (PID: 3220)
- RdrCEF.exe (PID: 2252)
- RdrCEF.exe (PID: 1008)
- RdrCEF.exe (PID: 2120)
- RdrCEF.exe (PID: 2072)
- iexplore.exe (PID: 708)
- iexplore.exe (PID: 2608)
- RdrCEF.exe (PID: 2868)
- RdrCEF.exe (PID: 672)
- RdrCEF.exe (PID: 444)
Reads the computer name
- AcroRd32.exe (PID: 2228)
- AcroRd32.exe (PID: 3220)
- RdrCEF.exe (PID: 3544)
- iexplore.exe (PID: 708)
- iexplore.exe (PID: 2608)
Searches for installed software
- AcroRd32.exe (PID: 2228)
- AcroRd32.exe (PID: 3220)
Application launched itself
- AcroRd32.exe (PID: 2228)
- RdrCEF.exe (PID: 3544)
- iexplore.exe (PID: 708)
Reads CPU info
- AcroRd32.exe (PID: 3220)
Reads the hosts file
- RdrCEF.exe (PID: 3544)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 2228)
- iexplore.exe (PID: 2608)
- AdobeARM.exe (PID: 768)
- iexplore.exe (PID: 708)
Reads settings of System Certificates
- AcroRd32.exe (PID: 2228)
- iexplore.exe (PID: 2608)
- AdobeARM.exe (PID: 768)
- iexplore.exe (PID: 708)
- RdrCEF.exe (PID: 3544)
Changes internet zones settings
- iexplore.exe (PID: 708)
Reads internet explorer settings
- iexplore.exe (PID: 2608)
Adds / modifies Windows certificates
- iexplore.exe (PID: 708)
Changes settings of System certificates
- iexplore.exe (PID: 708)
Reads the date of Windows installation
- iexplore.exe (PID: 708)
Creates files in the user directory
- iexplore.exe (PID: 2608)
- iexplore.exe (PID: 708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| Subject: | - |
|---|---|
| Author: | - |
| Title: | - |
| ModifyDate: | 2022:05:21 01:46:23+02:00 |
| CreateDate: | 2022:04:04 13:51:53+02:00 |
| Producer: | 2.4.8 (4.3.4) |
| Creator: | - |
| HasXFA: | No |
| PDFVersion: | 1.5 |
| PageCount: | 1 |
| Linearized: | No |
Total processes
52
Monitored processes
14
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1196,8916203965425568993,2025499683463249789,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8991017782955772452 --renderer-client-id=7 --mojo-platform-channel-handle=1736 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 672 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1196,8916203965425568993,2025499683463249789,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=635243326584287305 --renderer-client-id=6 --mojo-platform-channel-handle=1692 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
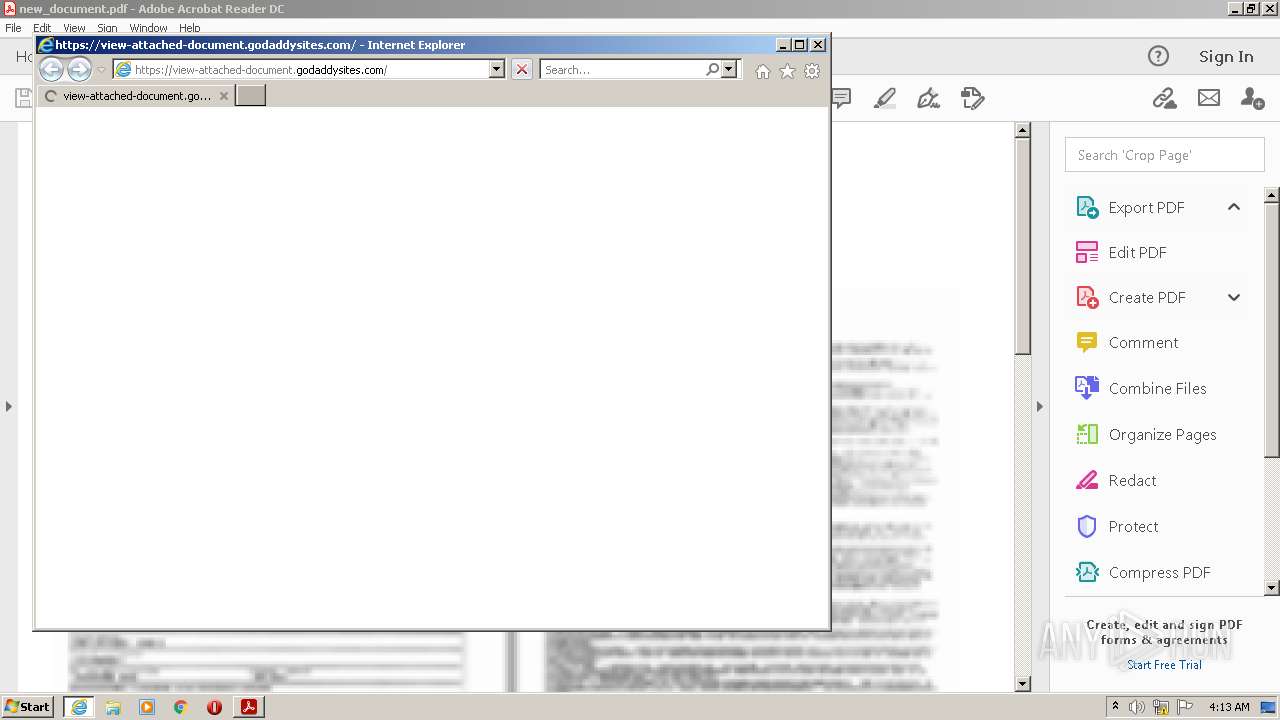
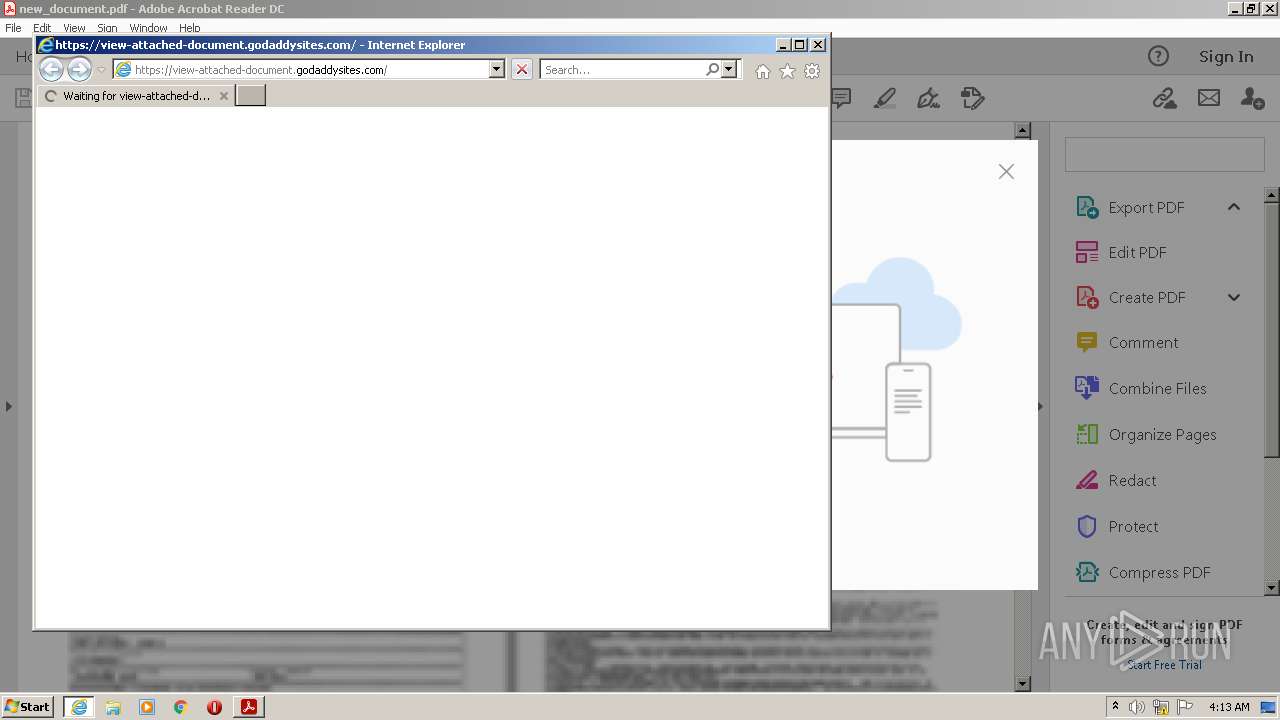
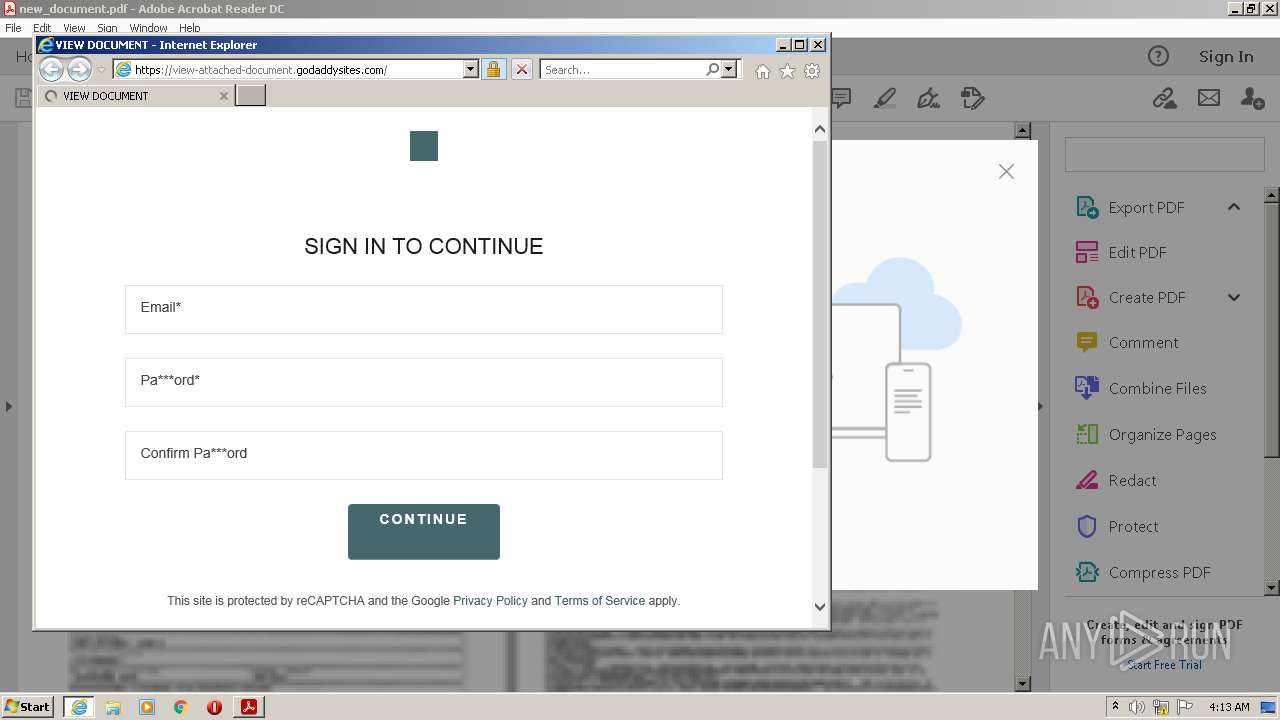
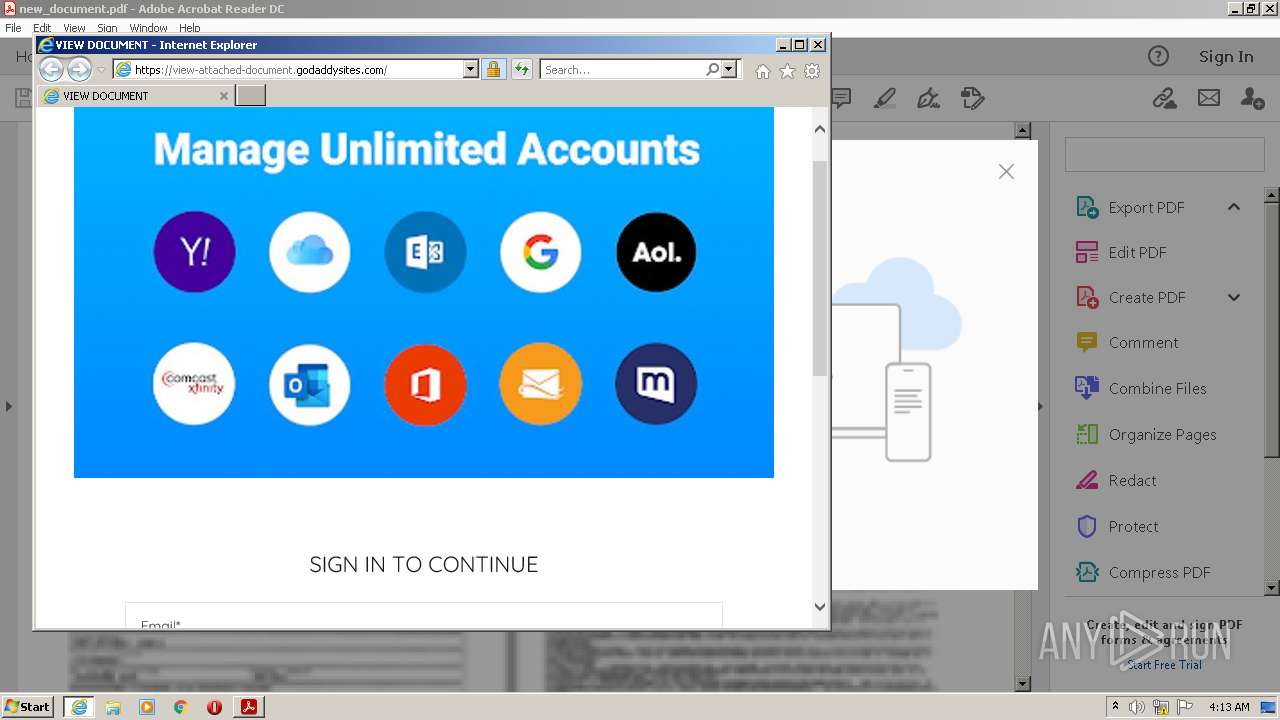
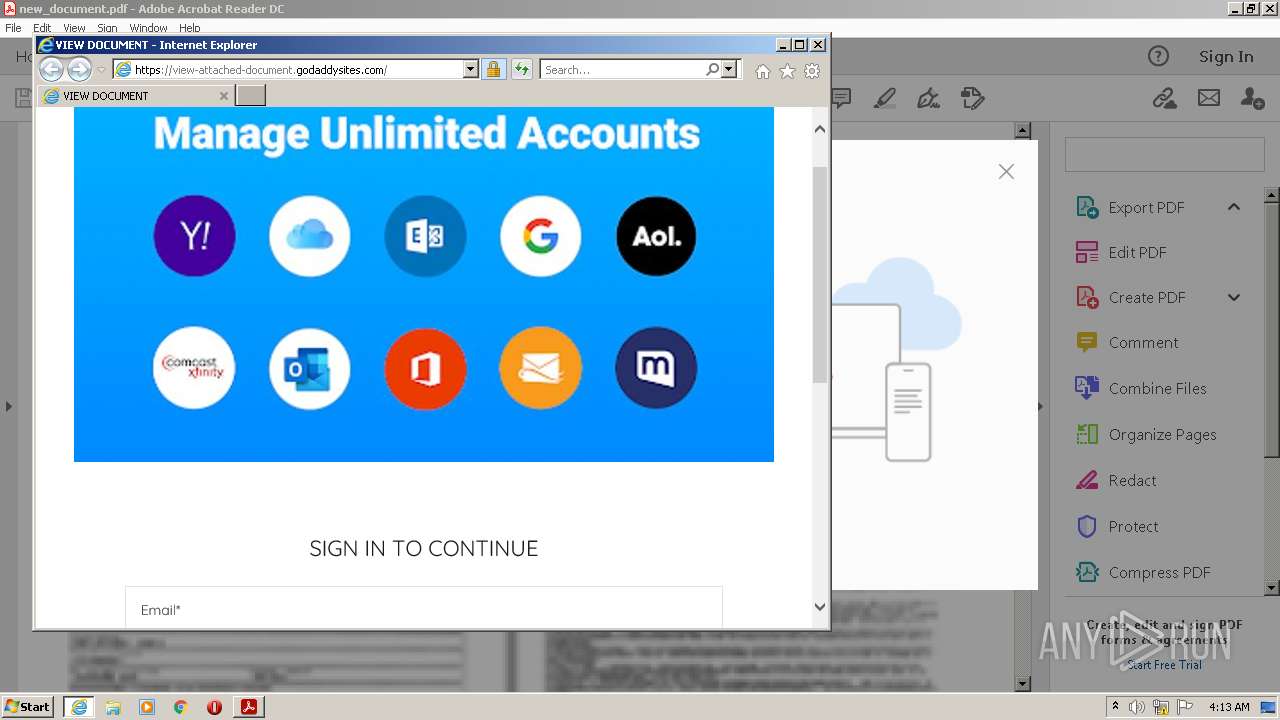
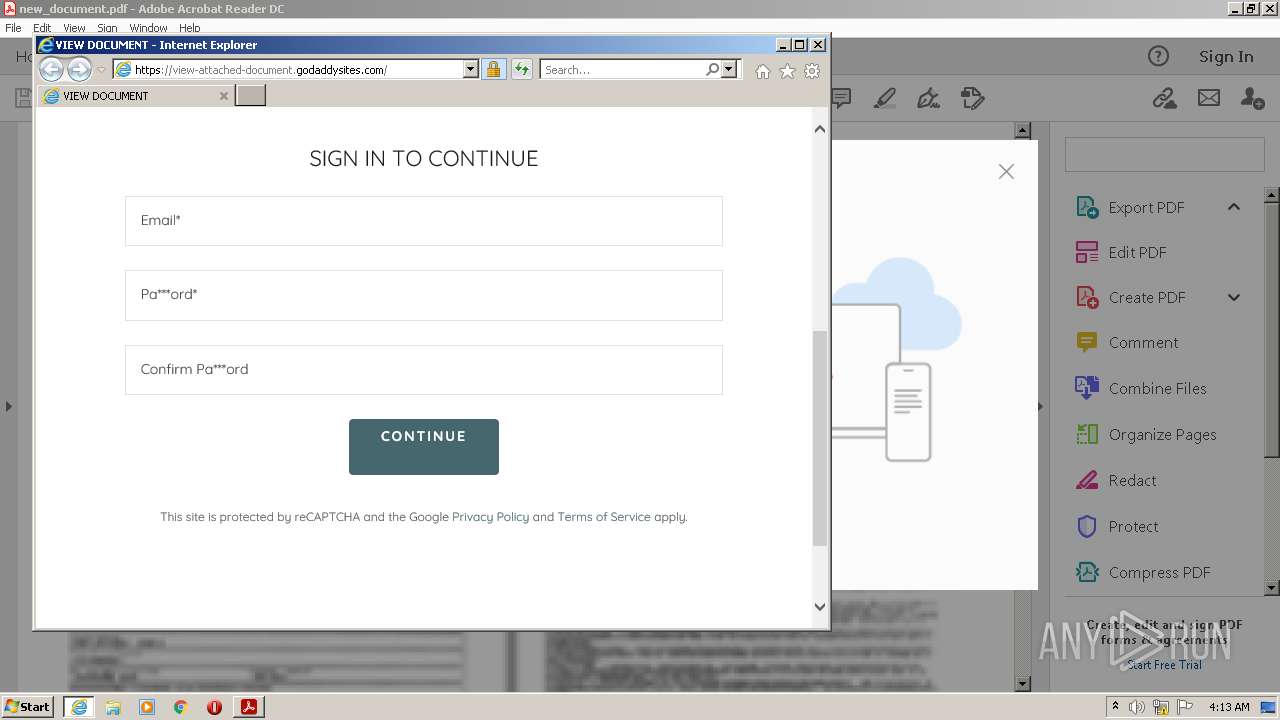
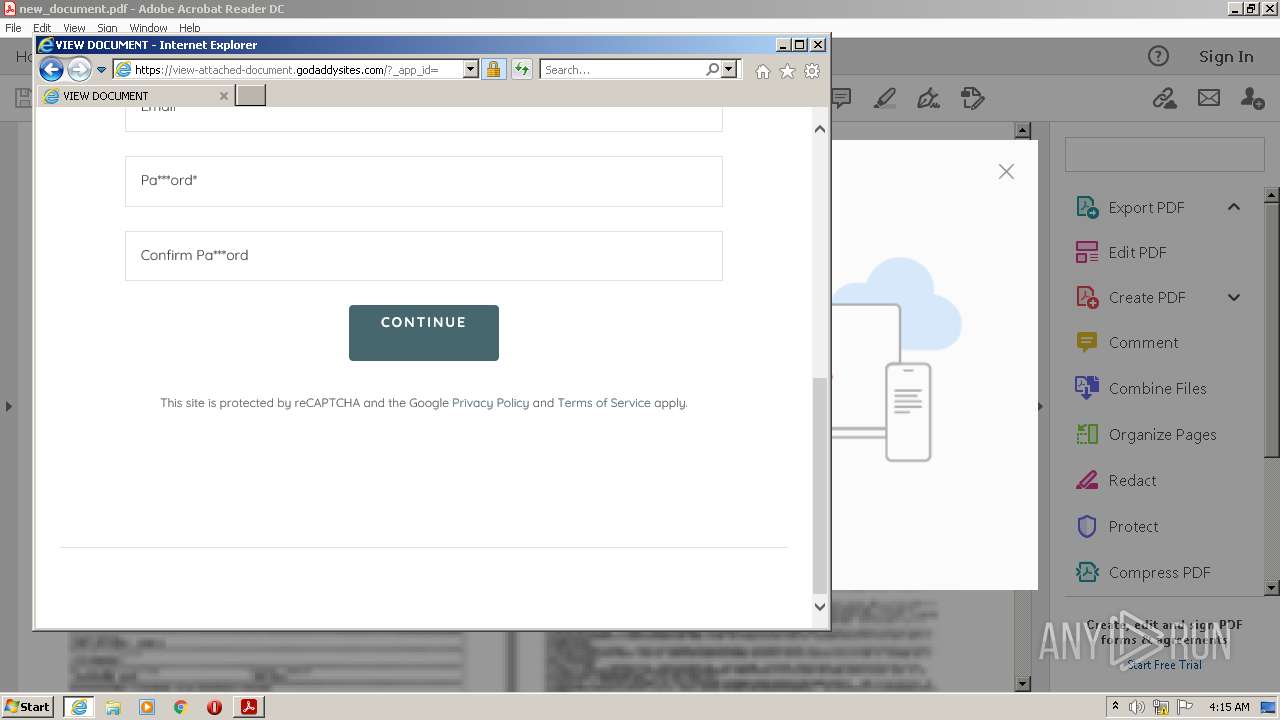
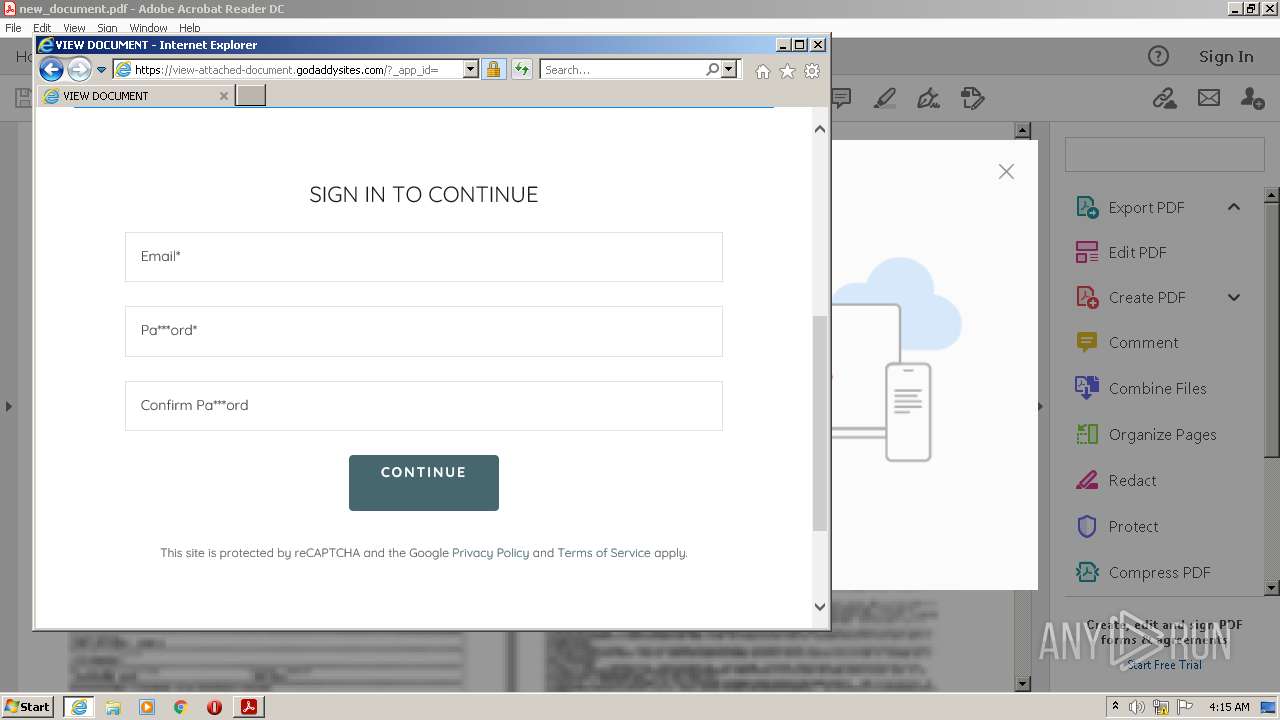
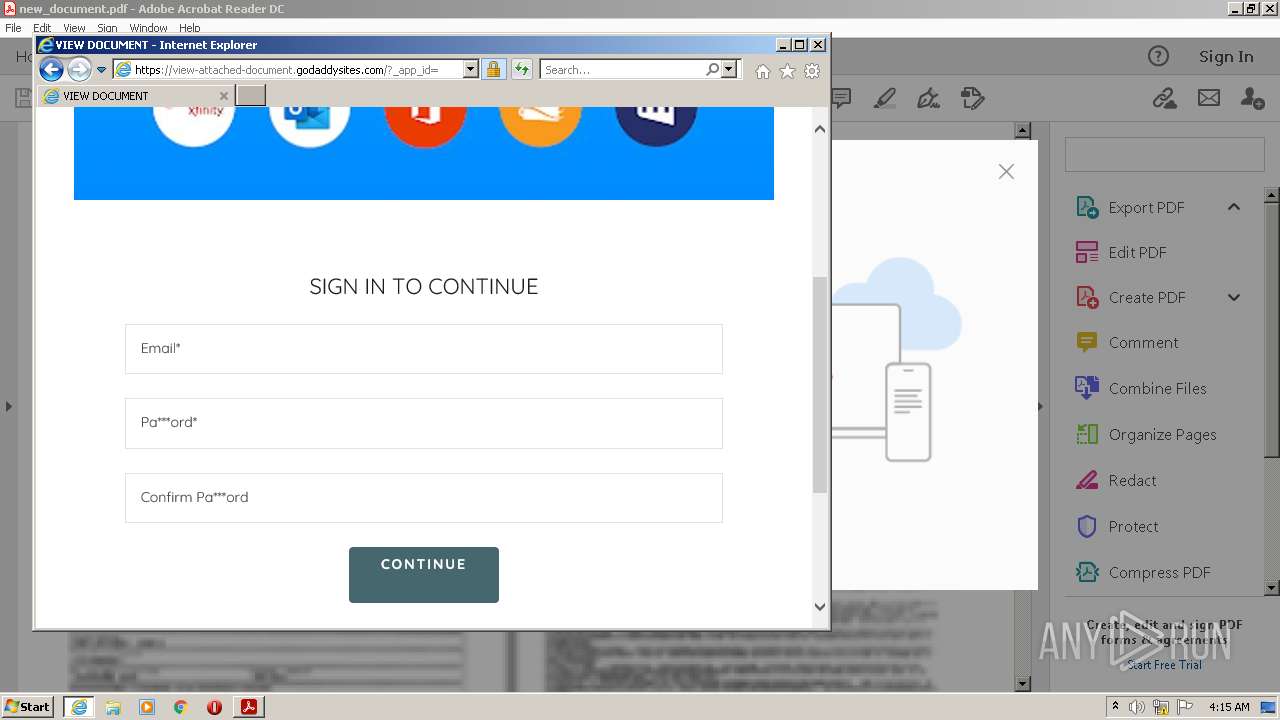
| 708 | "C:\Program Files\Internet Explorer\iexplore.exe" https://view-attached-document.godaddysites.com/ | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 768 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:20.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.39.9311 Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1196,8916203965425568993,2025499683463249789,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=2034522833613138654 --mojo-platform-channel-handle=1404 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1196,8916203965425568993,2025499683463249789,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=13644201860186229183 --mojo-platform-channel-handle=1280 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1196,8916203965425568993,2025499683463249789,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=11944932742457648620 --mojo-platform-channel-handle=1244 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2228 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\new_document.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | Explorer.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2252 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1196,8916203965425568993,2025499683463249789,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8425048213156503807 --renderer-client-id=2 --mojo-platform-channel-handle=1204 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 20.12.20041.394260 Modules
| |||||||||||||||
Total events
33 350
Read events
33 070
Write events
270
Delete events
10
Modification events
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 2 | |||
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | write | Name: | bShowUpdateFTE |
Value: 1 | |||
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcome |
| Operation: | write | Name: | bIsAcrobatUpdated |
Value: 1 | |||
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcomeFirstMileReader |
| Operation: | write | Name: | iCardCountShown |
Value: 2 | |||
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | delete value | Name: | iLastCardShown |
Value: 0 | |||
| (PID) Process: | (2228) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3220) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Adobe Acrobat\DC\DiskCabs |
| Operation: | write | Name: | bForms_AdhocWorkflowBackup |
Value: 0 | |||
| (PID) Process: | (2228) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2228) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
1
Suspicious files
167
Text files
31
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c84d92a9dbce3e0_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\560e9c8bff5008d8_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 3544 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\febb41df4ea2b63a_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
41
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2608 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2608 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.starfieldtech.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCAzkUhA%3D%3D | US | der | 1.70 Kb | whitelisted |
2608 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.starfieldtech.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQUwPiEZQ6%2FsVZNPaFToNfxx8ZwqAQUfAwyH6fZMH%2FEfWijYqihzqsHWycCAQc%3D | US | der | 1.74 Kb | whitelisted |
708 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
708 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2608 | iexplore.exe | GET | 200 | 192.124.249.23:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCG%2FPPudZSUXe | US | der | 1.74 Kb | whitelisted |
2228 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2608 | iexplore.exe | GET | 200 | 67.26.75.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e9992c0bd12fd371 | US | compressed | 4.70 Kb | whitelisted |
2608 | iexplore.exe | GET | 200 | 67.26.75.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a07a67d96e0b41e2 | US | compressed | 4.70 Kb | whitelisted |
708 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
708 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3544 | RdrCEF.exe | 2.20.156.175:443 | geo2.adobe.com | Akamai International B.V. | — | whitelisted |
2608 | iexplore.exe | 67.26.75.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
2228 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3544 | RdrCEF.exe | 3.233.129.217:443 | p13n.adobe.io | — | US | unknown |
708 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
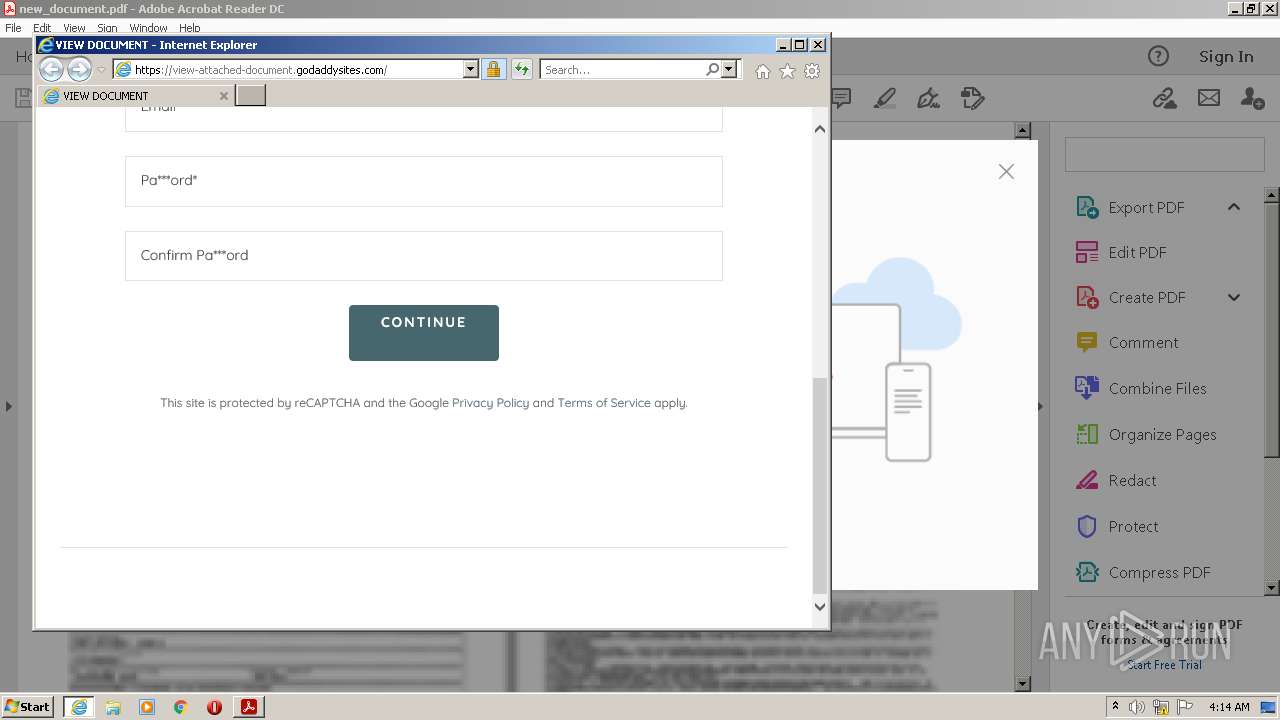
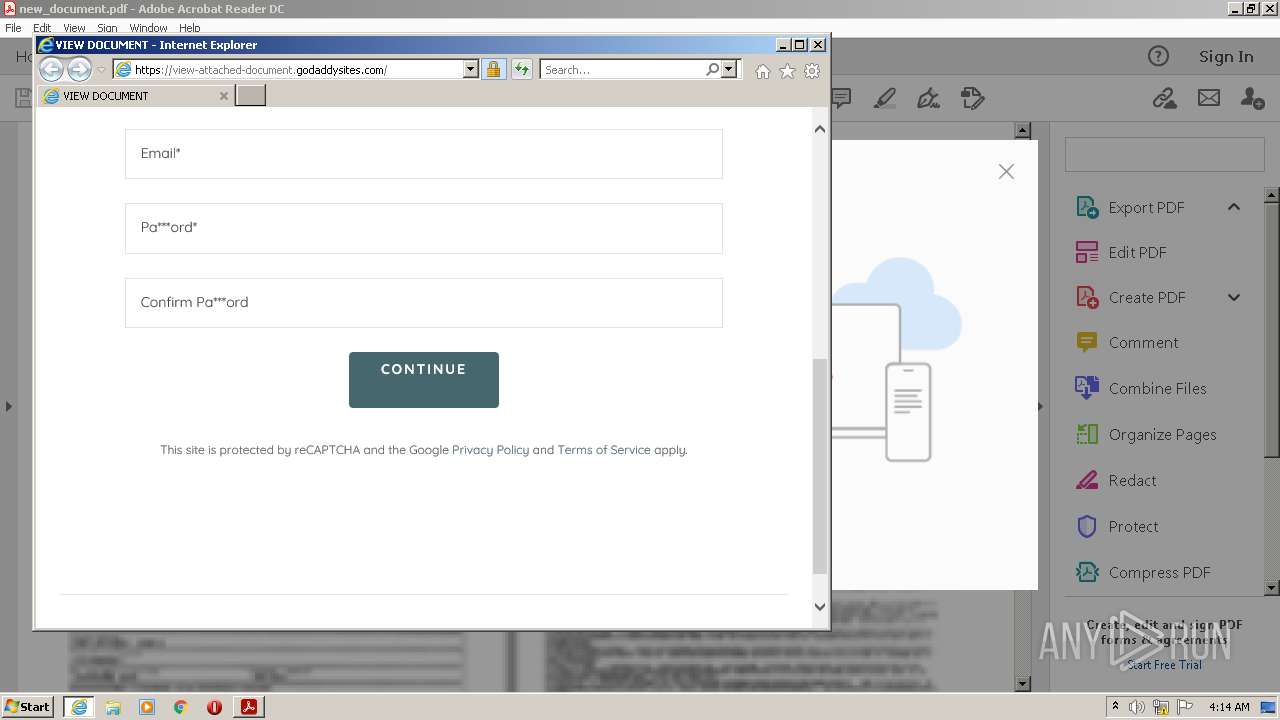
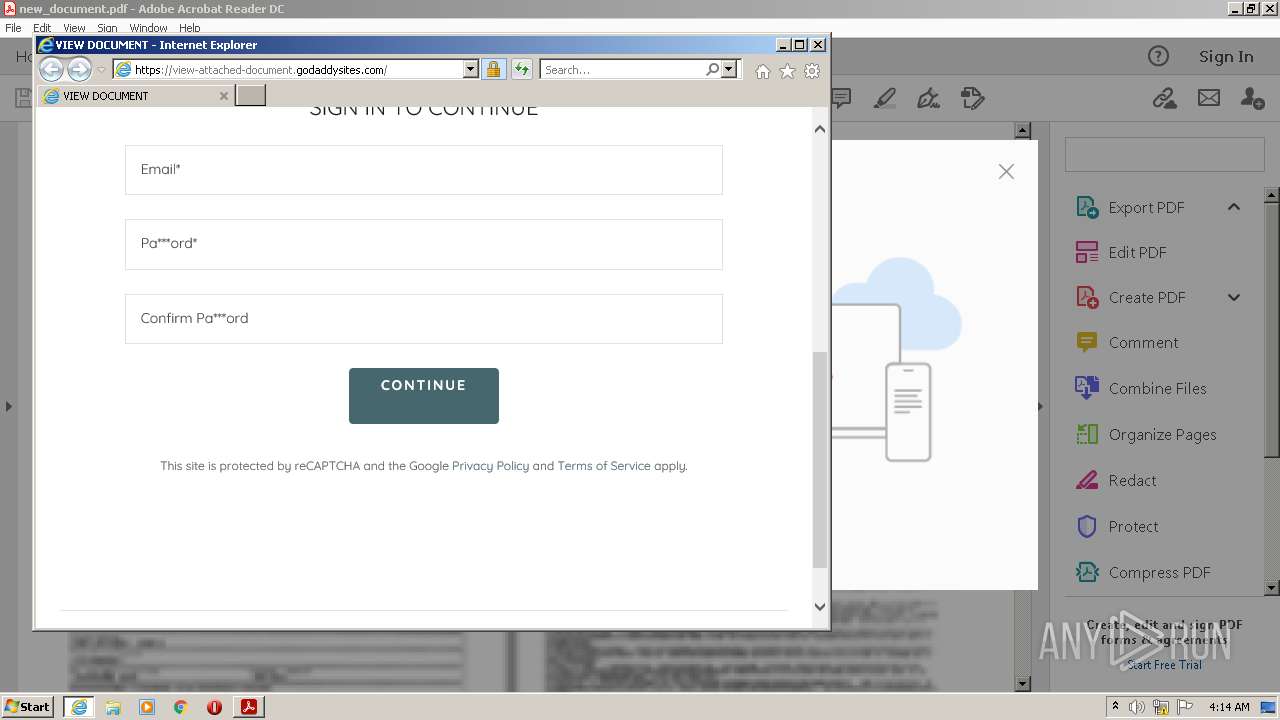
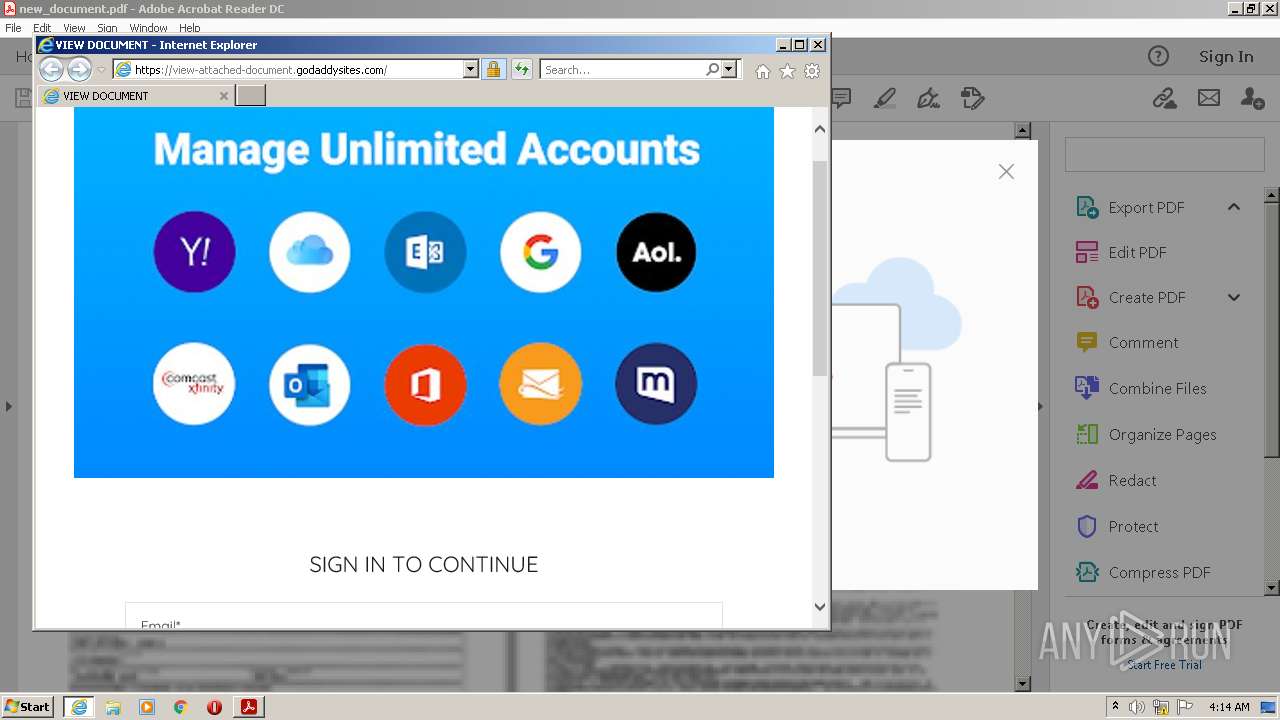
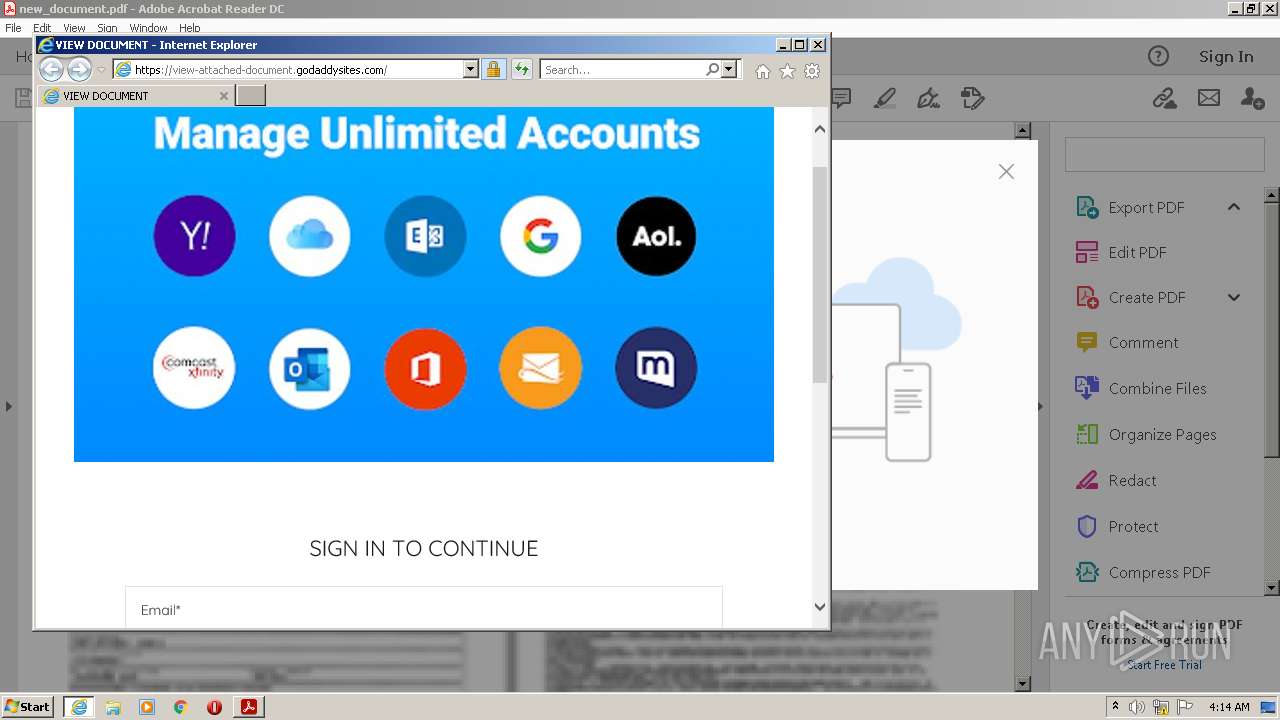
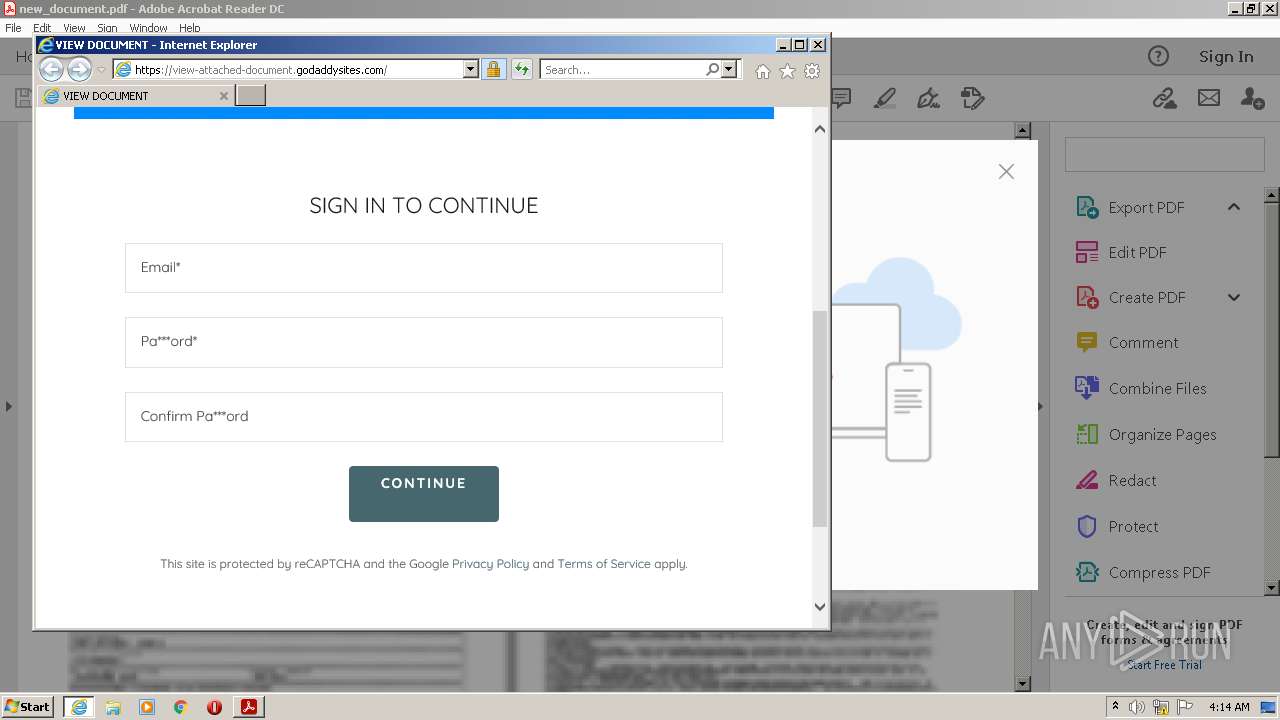
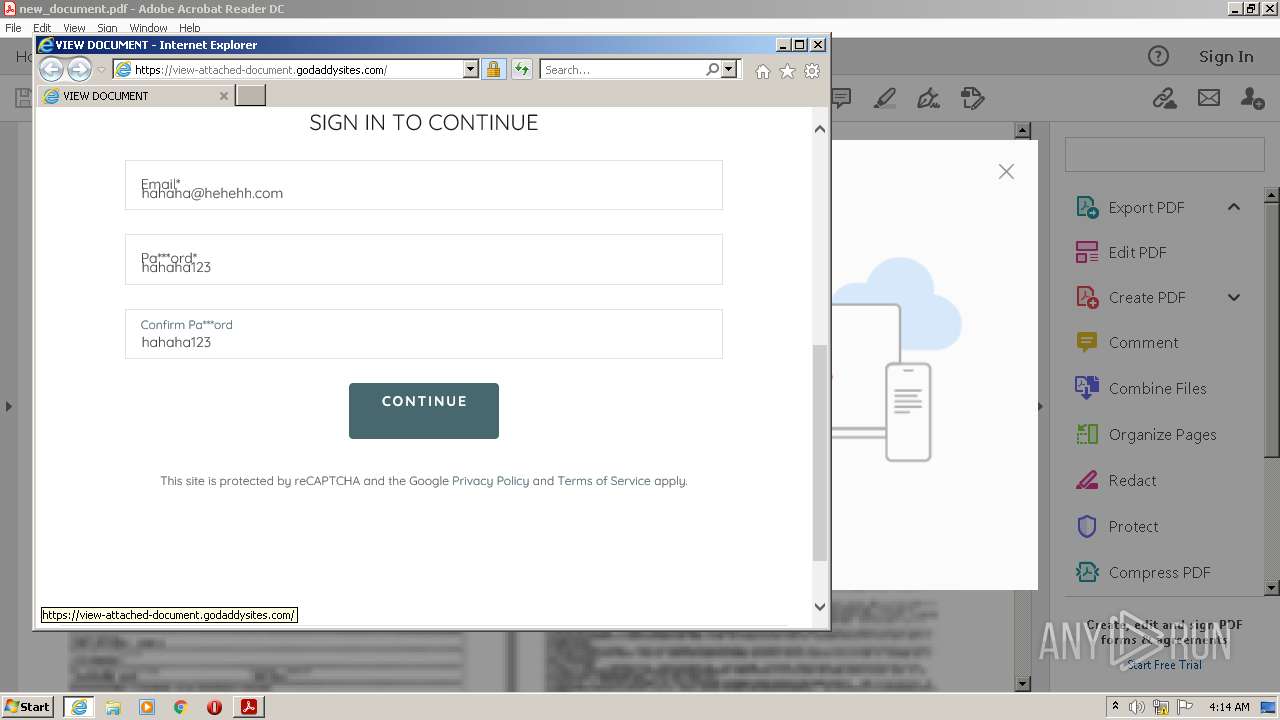
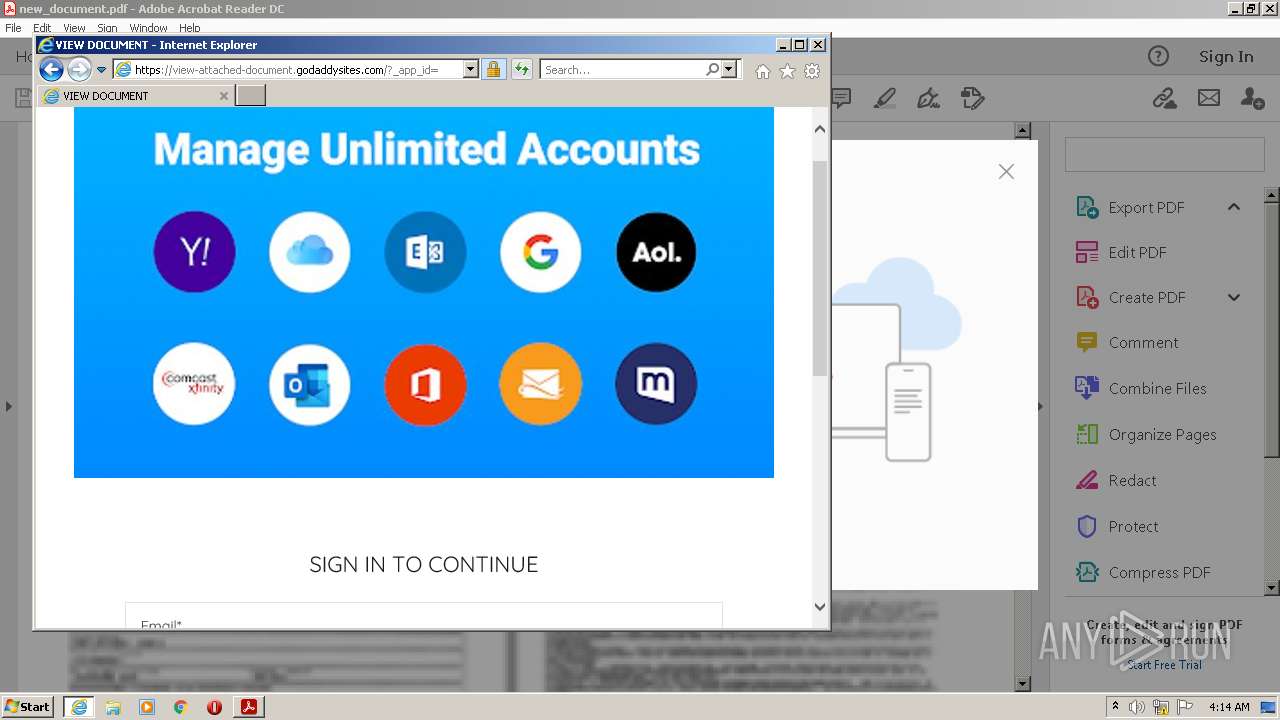
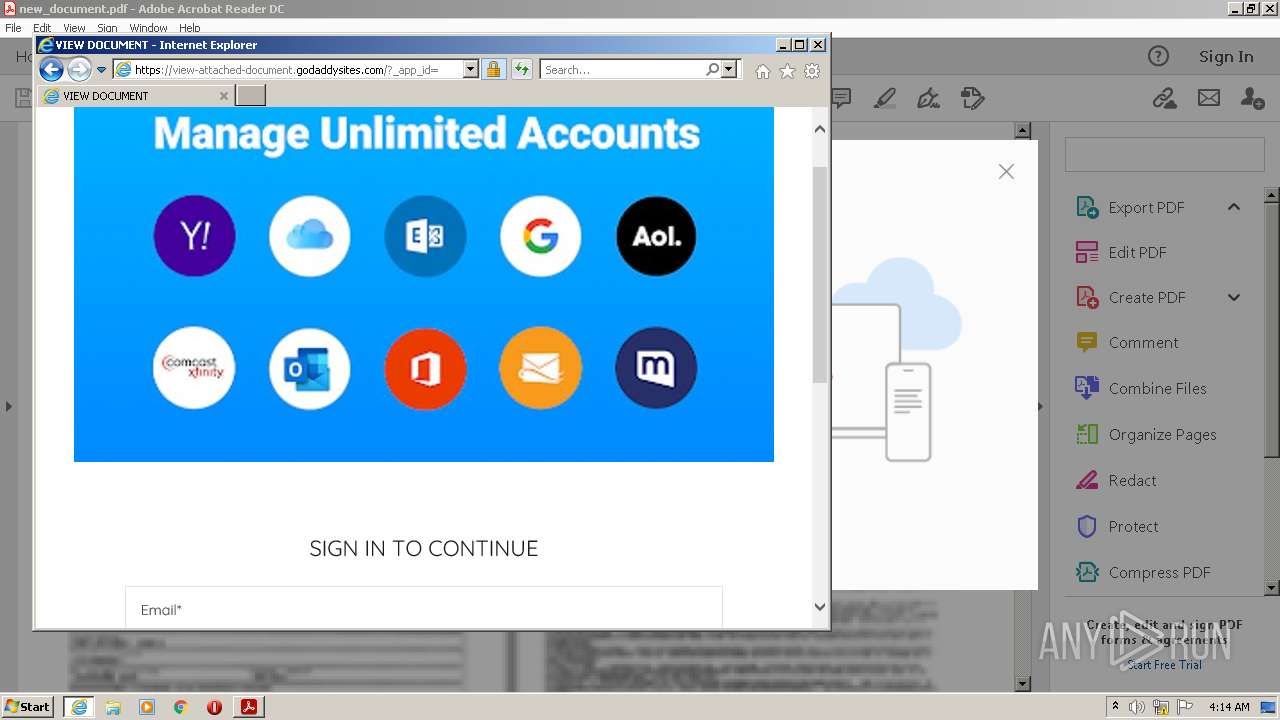
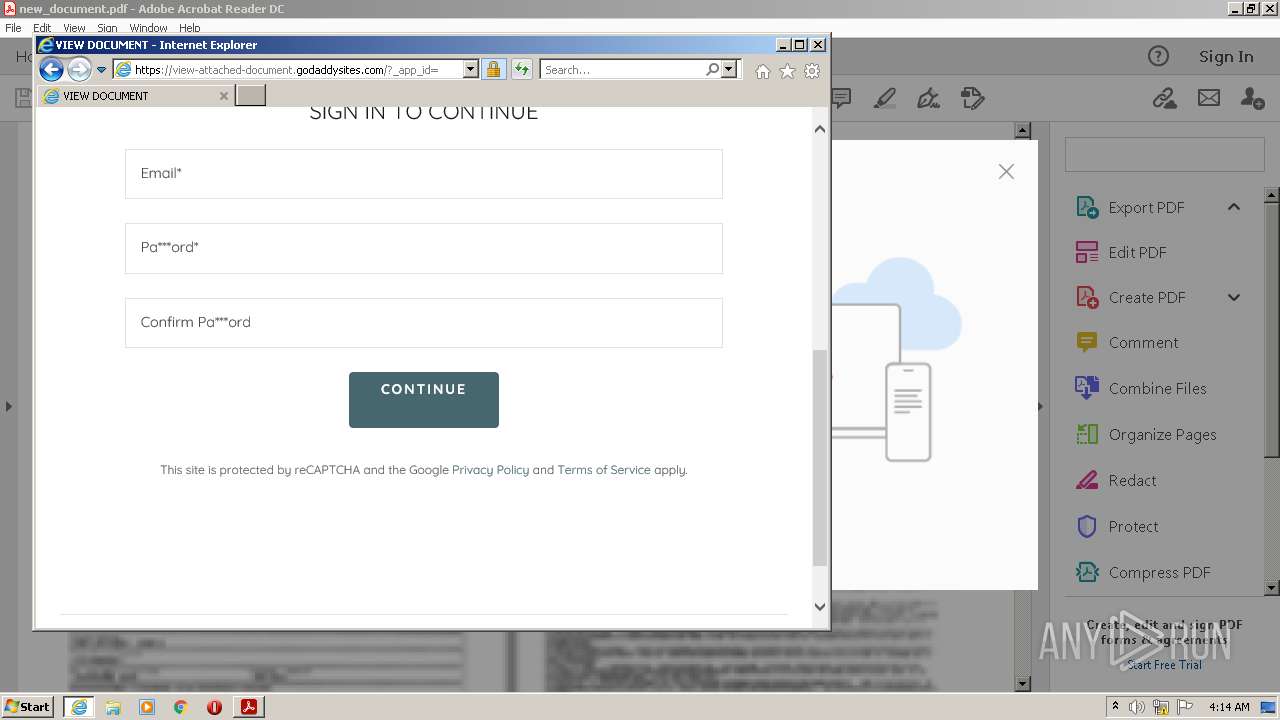
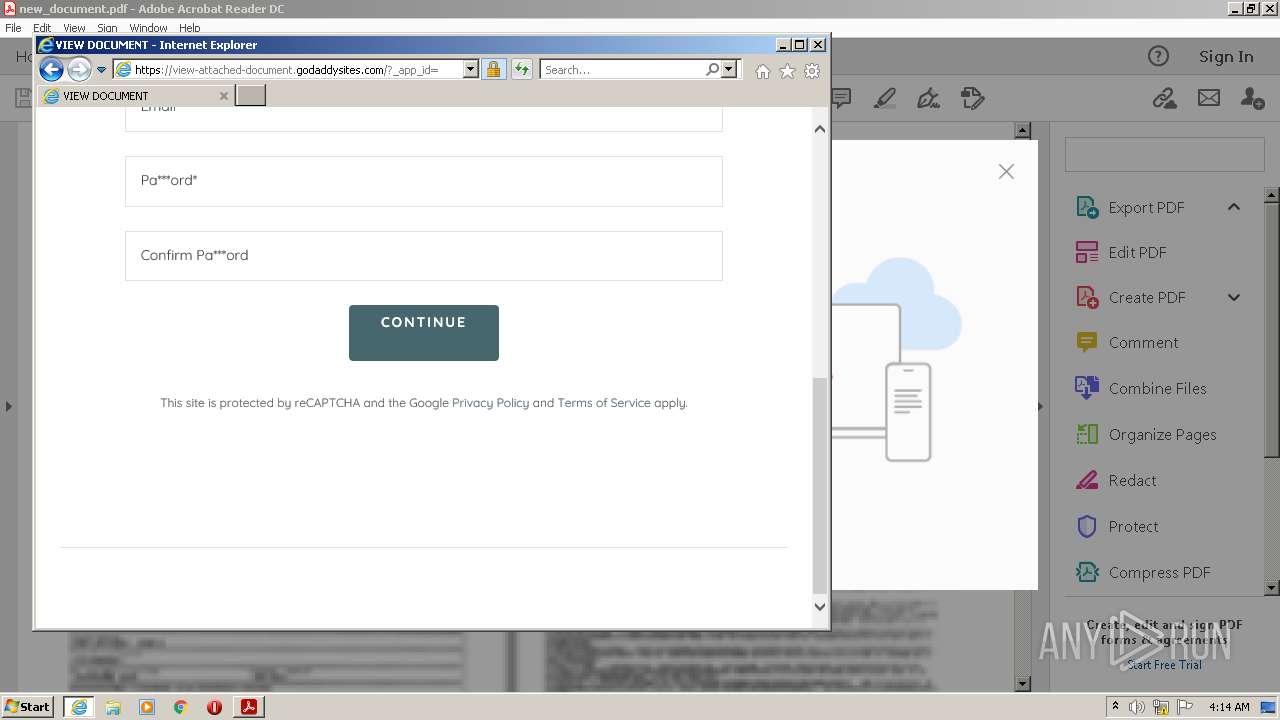
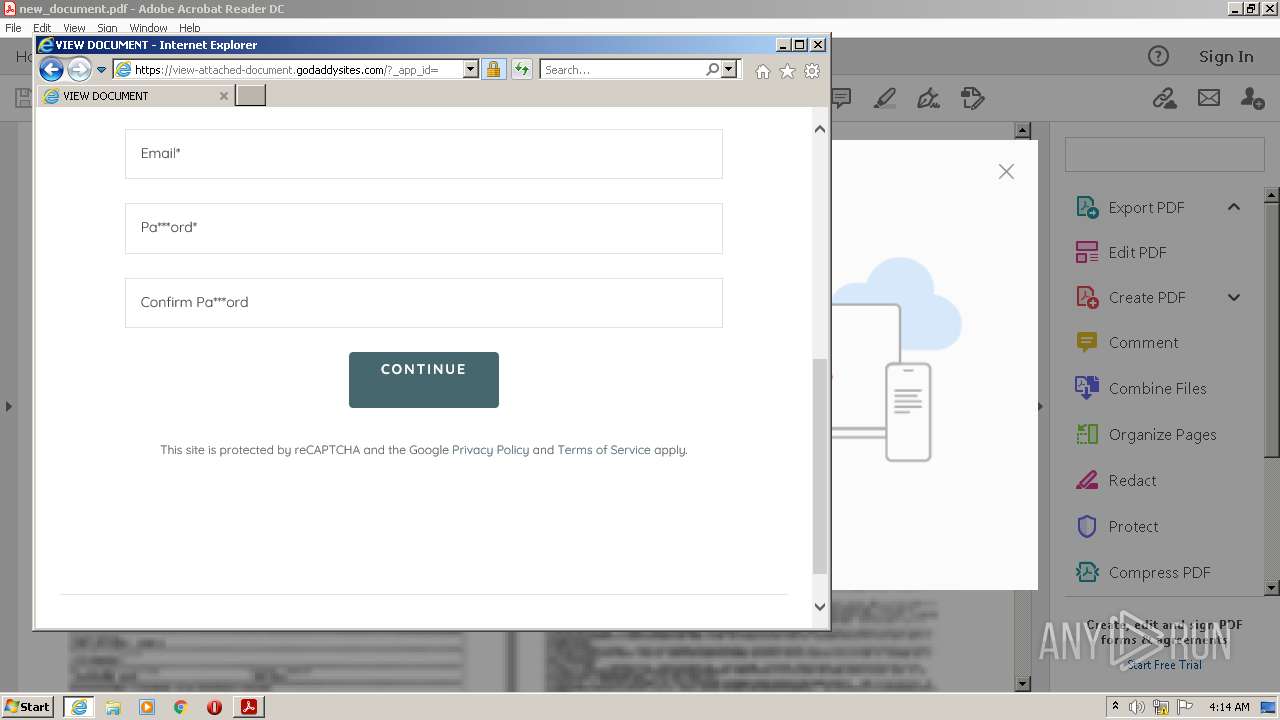
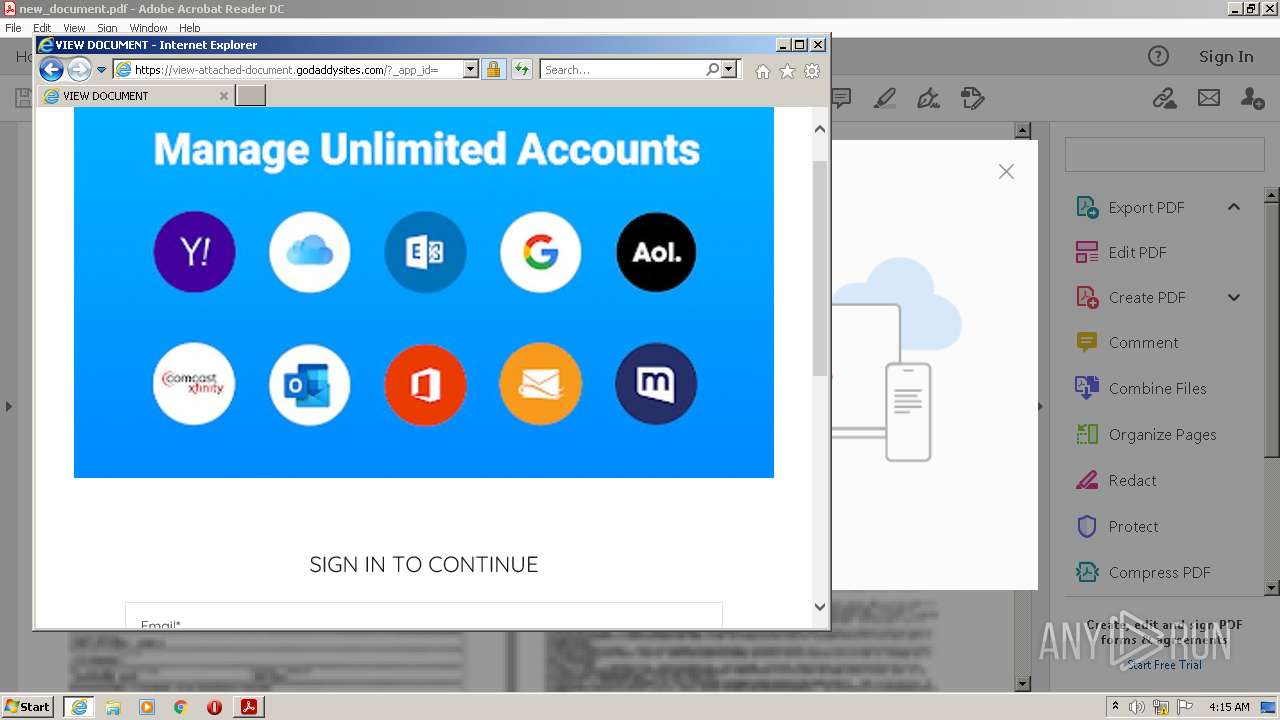
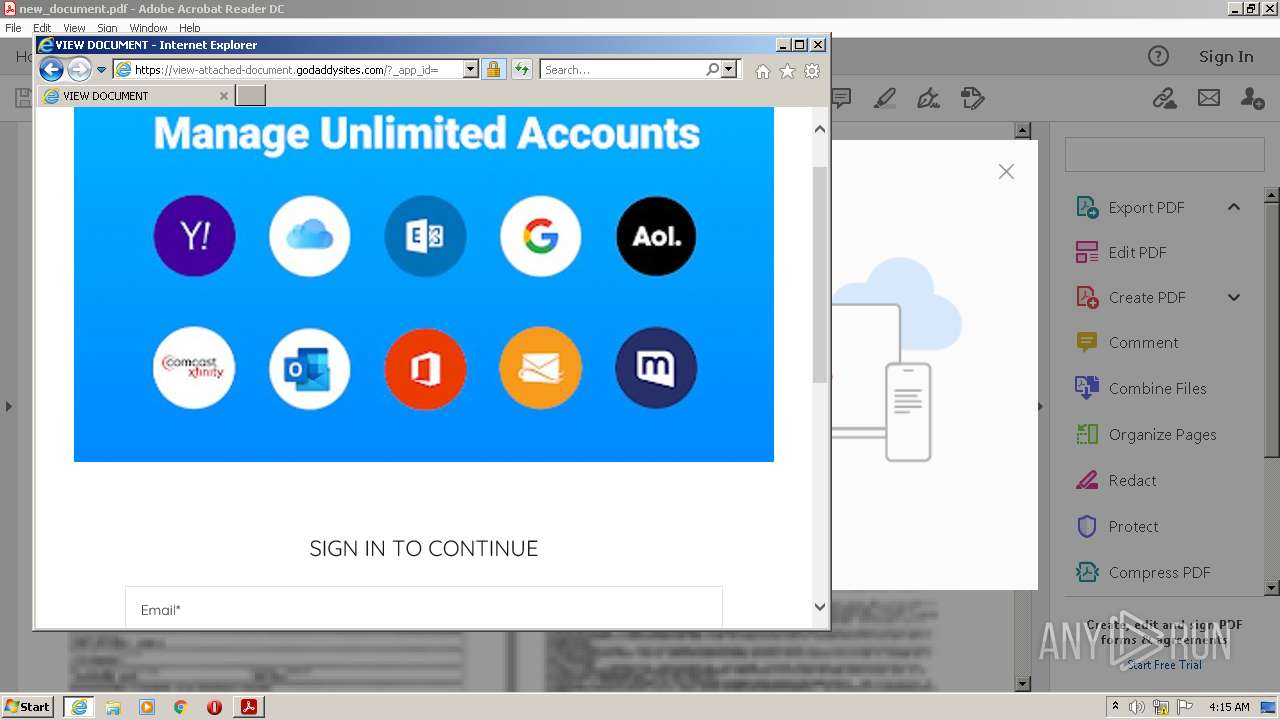
2608 | iexplore.exe | 72.167.191.83:443 | view-attached-document.godaddysites.com | GoDaddy.com, LLC | US | suspicious |
880 | svchost.exe | 104.79.88.64:443 | armmf.adobe.com | Time Warner Cable Internet LLC | US | suspicious |
880 | svchost.exe | 92.123.225.26:443 | ardownload3.adobe.com | Akamai International B.V. | — | suspicious |
2228 | AcroRd32.exe | 92.123.225.59:443 | acroipm2.adobe.com | Akamai International B.V. | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
view-attached-document.godaddysites.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
www.bing.com |
| whitelisted |
img1.wsimg.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.starfieldtech.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
880 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |