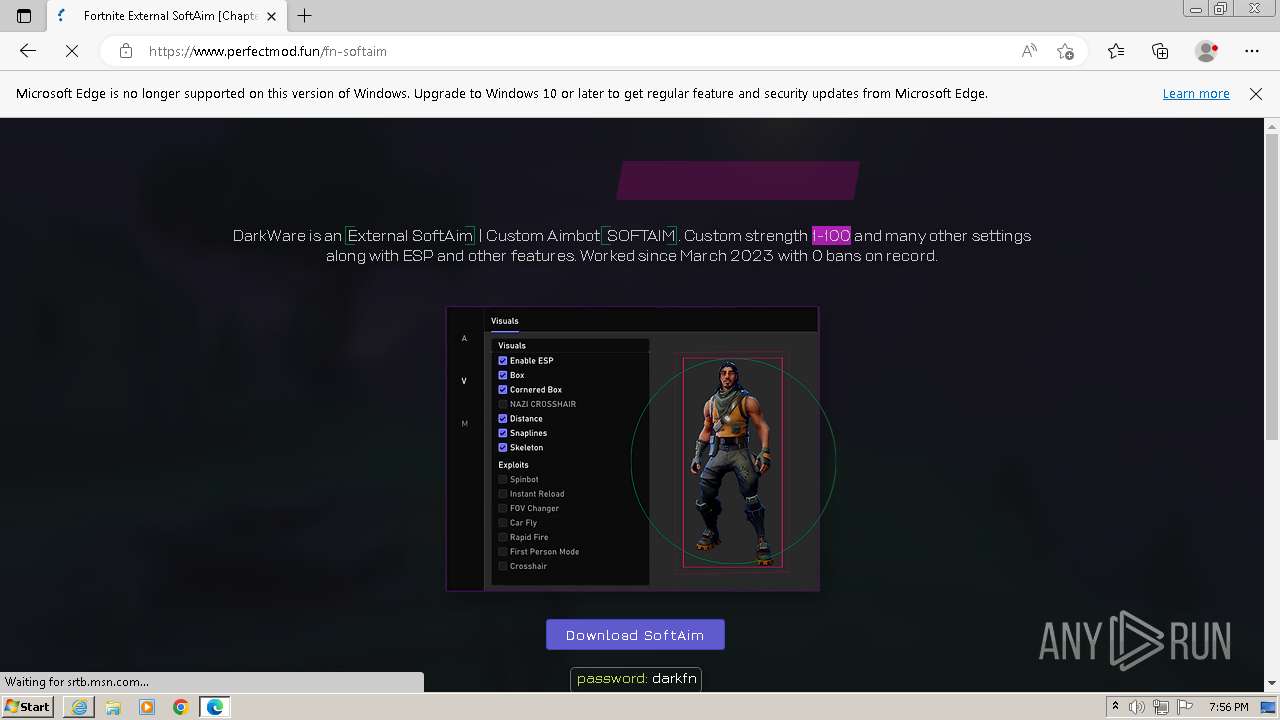
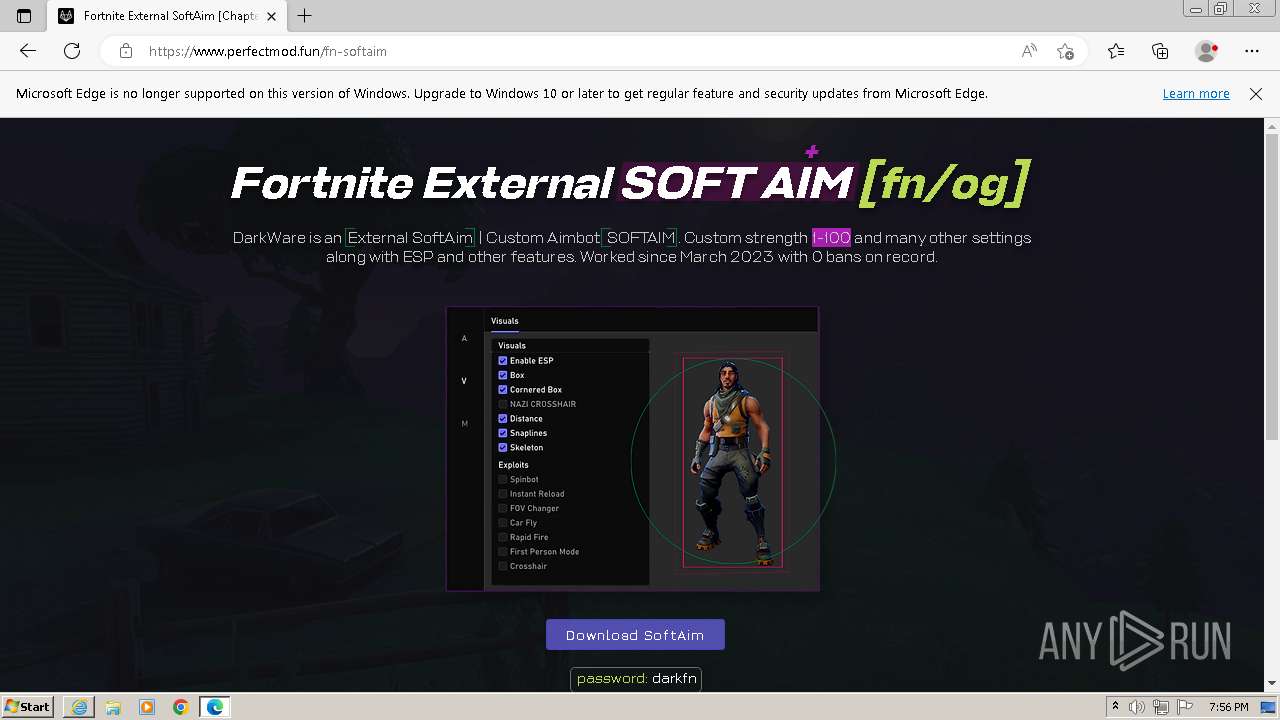
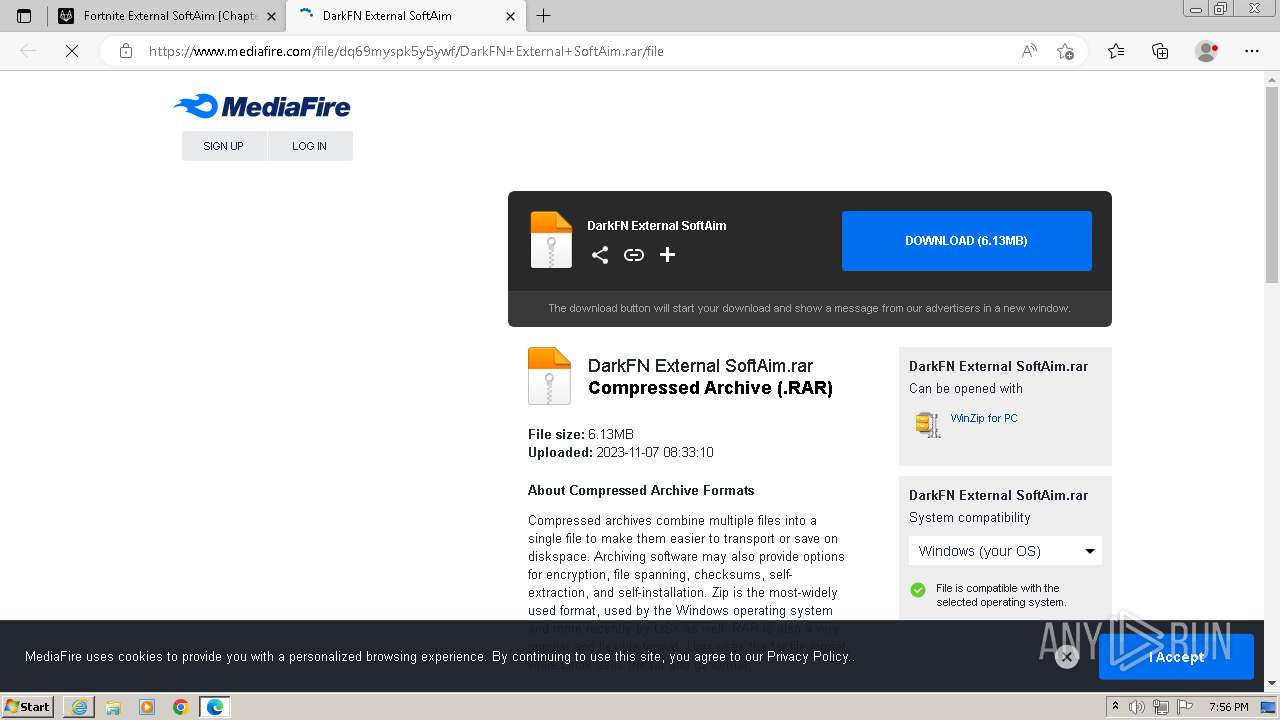
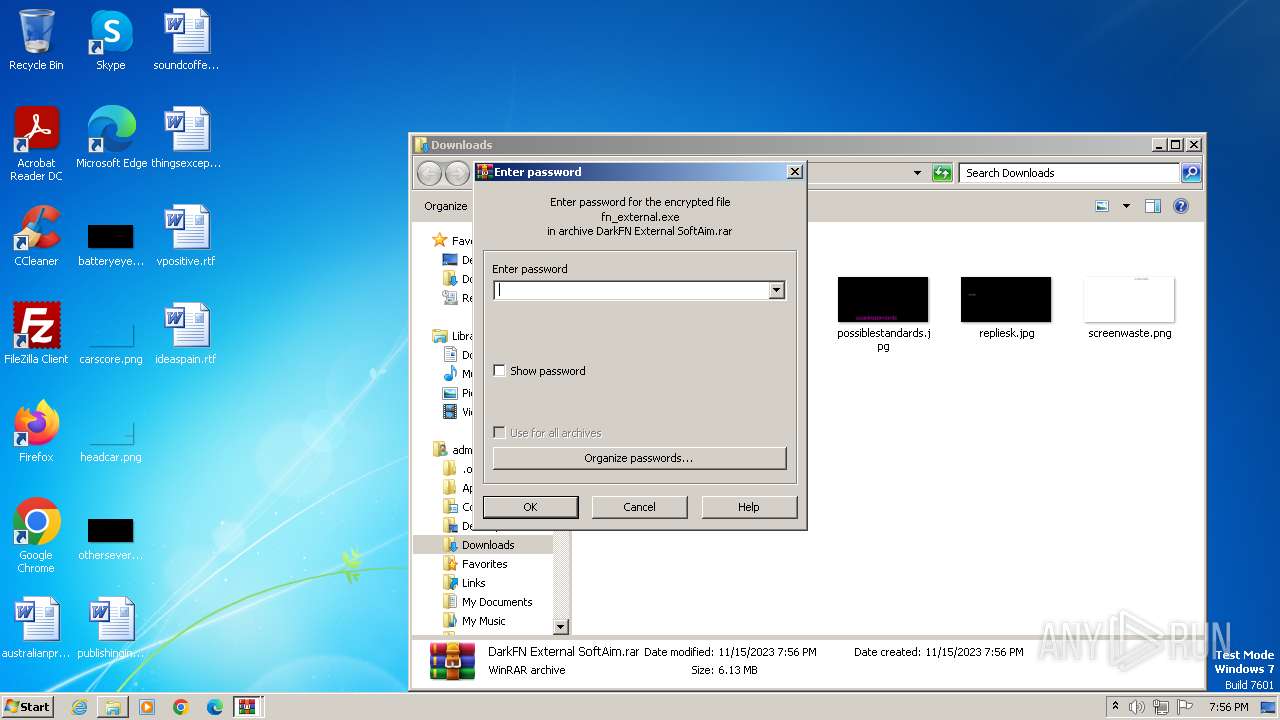
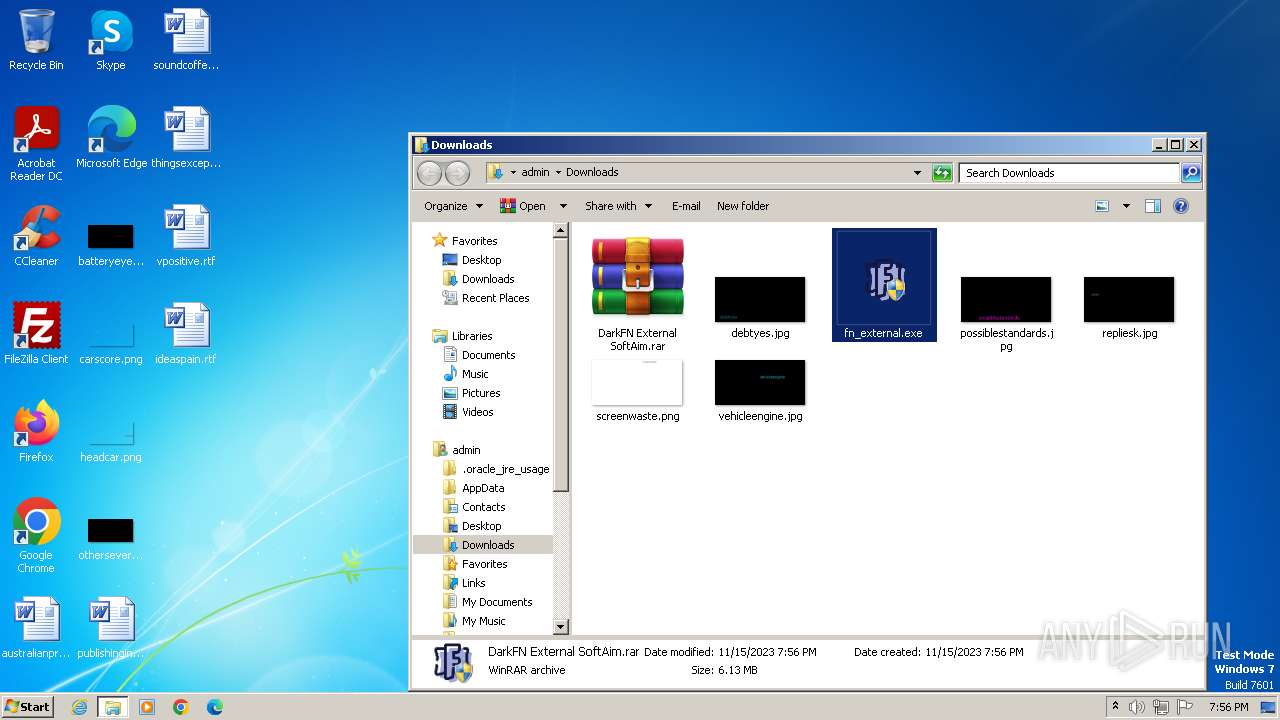
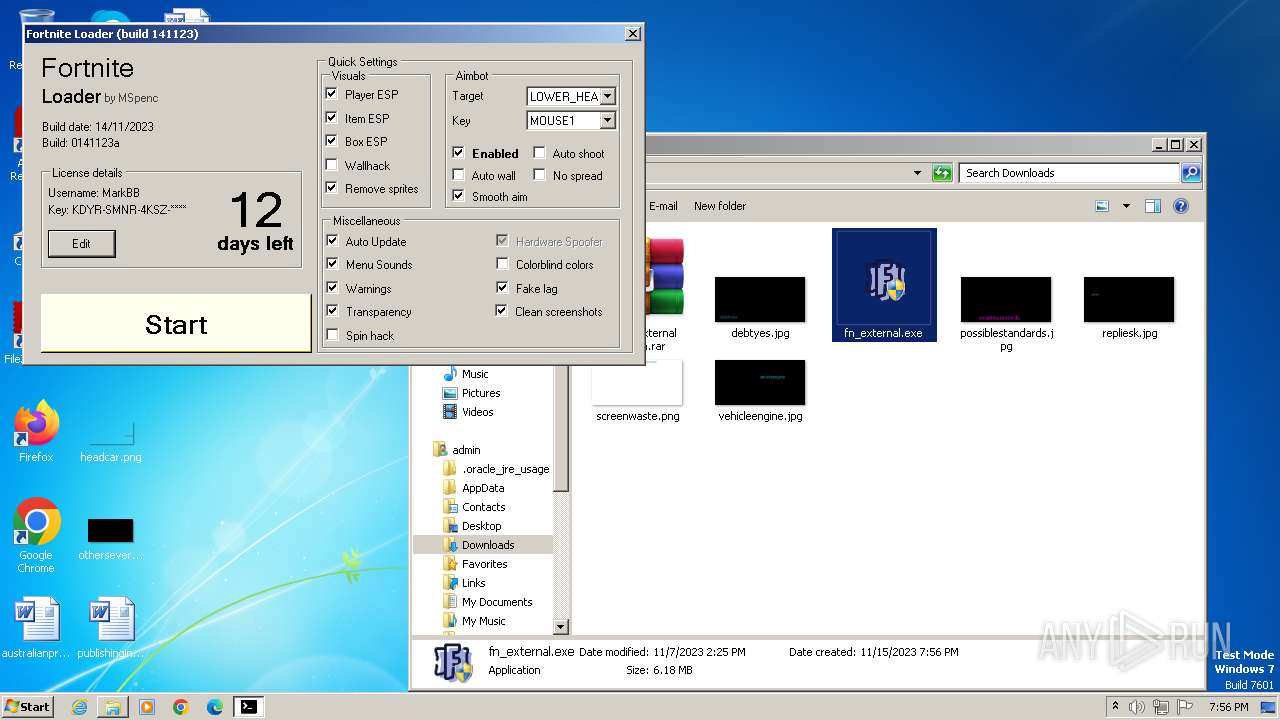
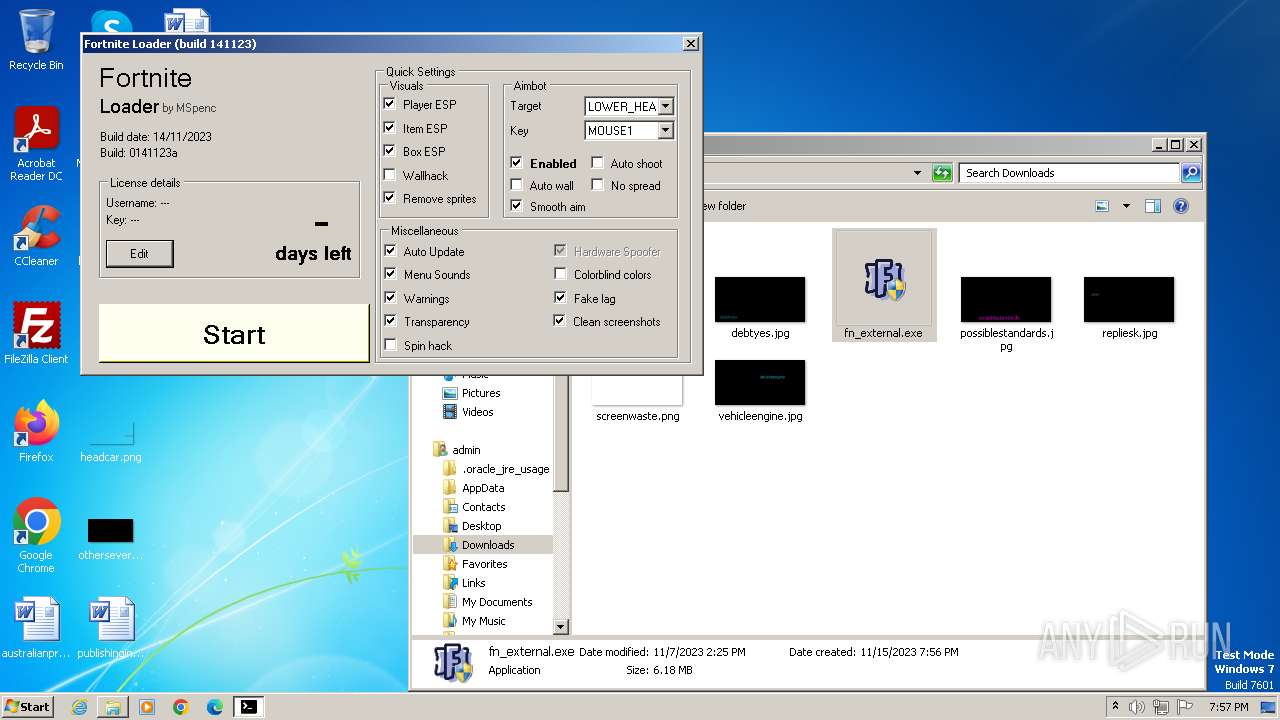
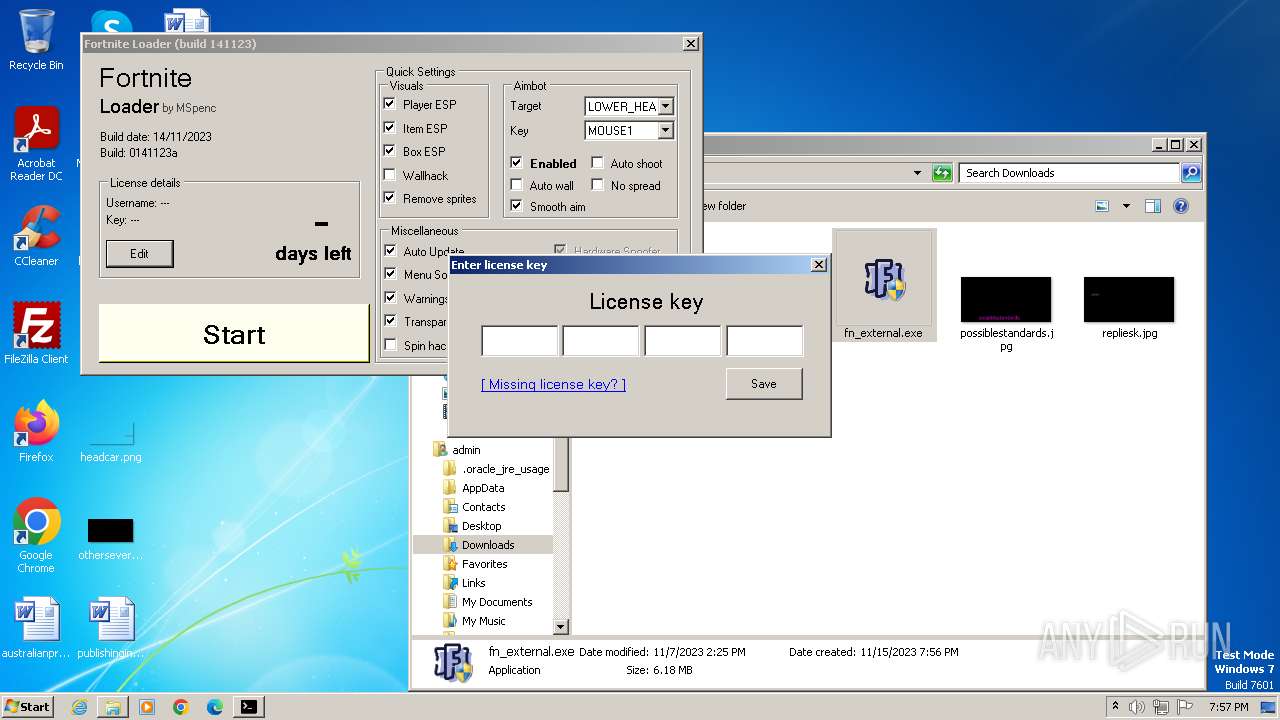
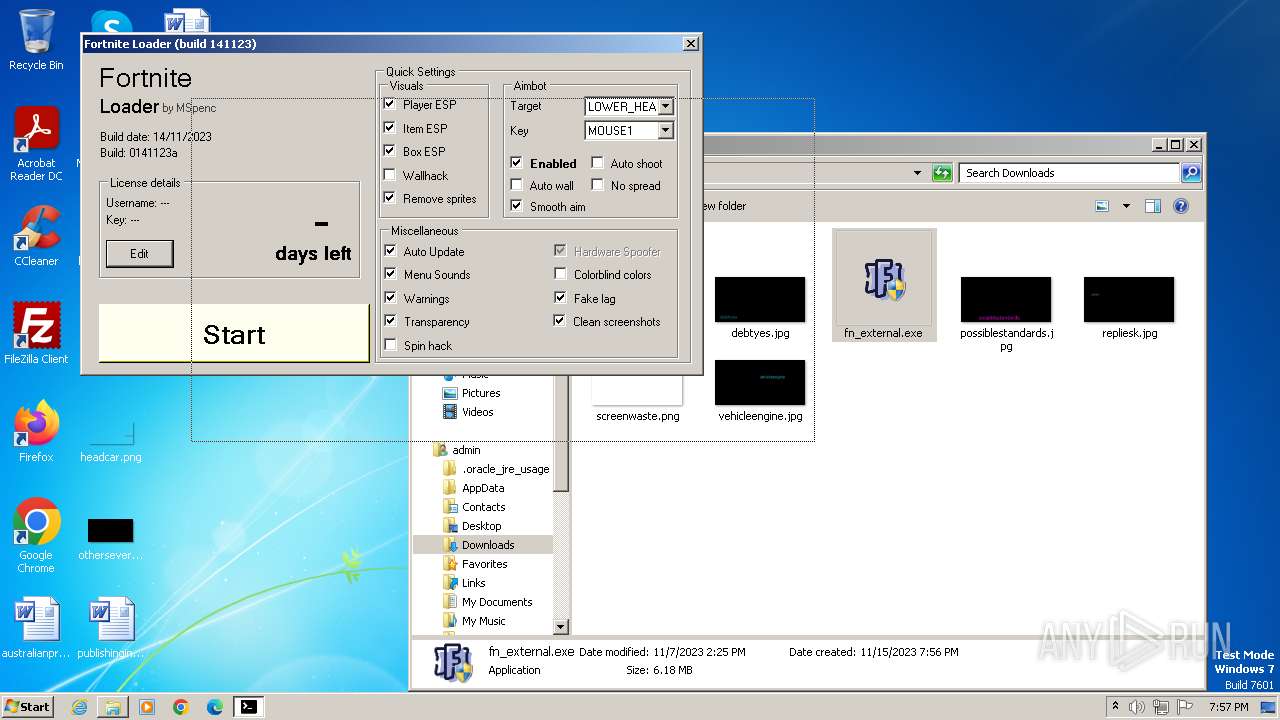
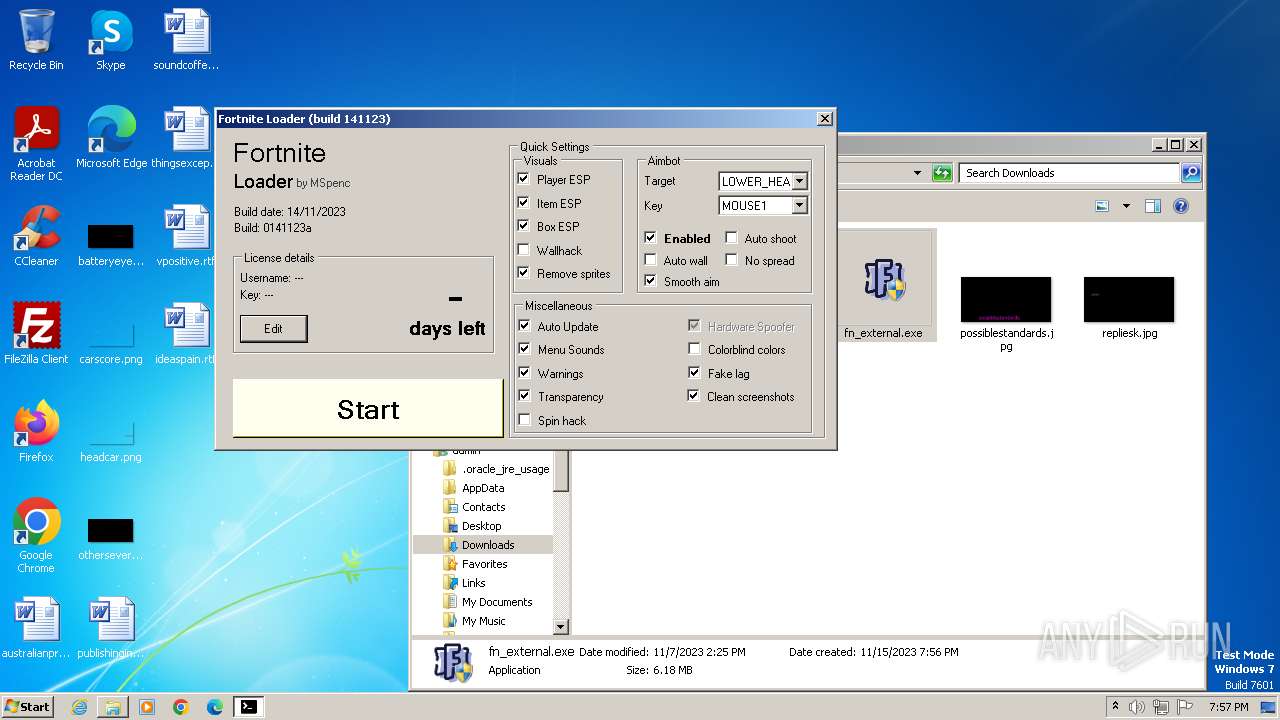
| URL: | https://perfectmod.fun/fn-softaim |
| Full analysis: | https://app.any.run/tasks/5e9d4635-2bb8-4463-b981-829a34174883 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2023, 19:56:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 7916C967D67896FF1AA6017B04D20E458893A0A7 |
| SHA256: | 3BF47C154E9A676ABC6708C7B233B73C34909378C71468C89233DCBDD35EBA1F |
| SSDEEP: | 3:N8Ex3BlD83S:2El7Y3S |
MALICIOUS
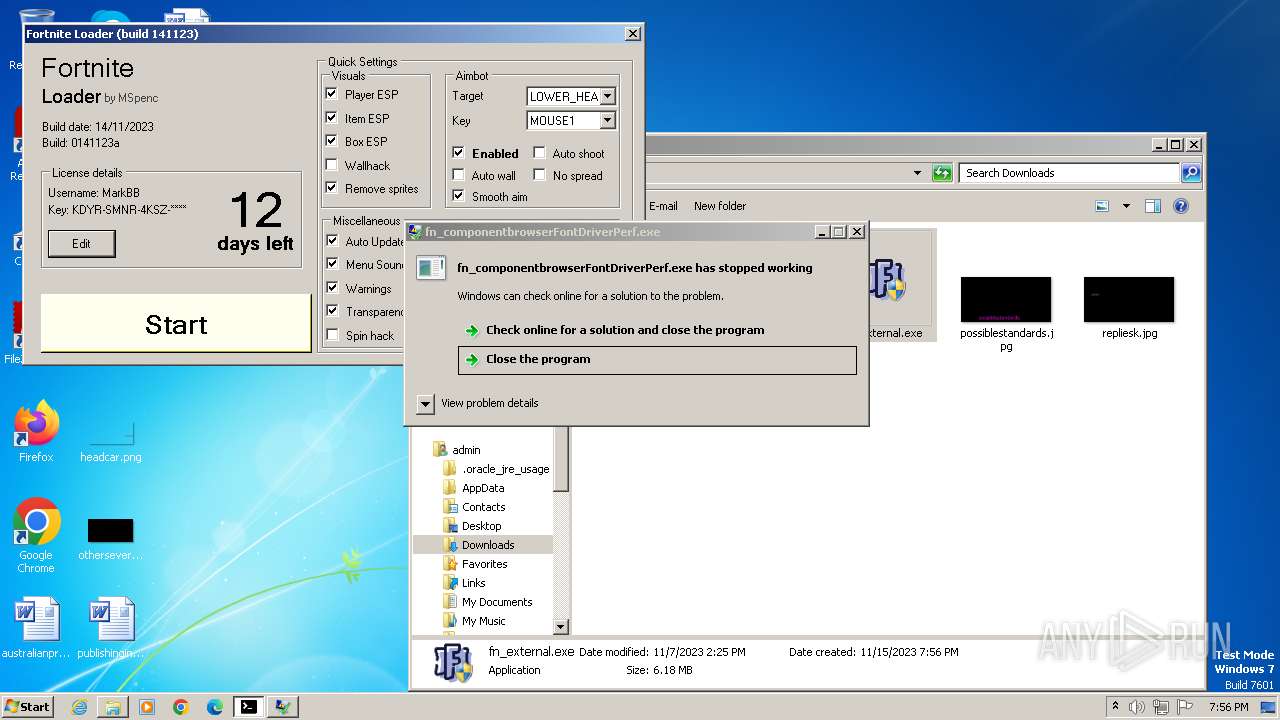
Drops the executable file immediately after the start
- fn_external.exe (PID: 1004)
- fn_componentbrowserFontDriverPerf.exe (PID: 2476)
SUSPICIOUS
Reads the Internet Settings
- fn_external.exe (PID: 1004)
Base64-obfuscated command line is found
- fn_external.exe (PID: 1004)
Starts POWERSHELL.EXE for commands execution
- fn_external.exe (PID: 1004)
BASE64 encoded PowerShell command has been detected
- fn_external.exe (PID: 1004)
Powershell version downgrade attack
- powershell.exe (PID: 2496)
Reads Internet Explorer settings
- fortnite_inj.exe (PID: 3388)
INFO
Application launched itself
- iexplore.exe (PID: 3448)
- msedge.exe (PID: 4012)
Checks supported languages
- wmpnscfg.exe (PID: 3924)
- fn_external.exe (PID: 1004)
- fn_componentbrowserFontDriverPerf.exe (PID: 2476)
- fortnite_inj.exe (PID: 3388)
Reads the computer name
- wmpnscfg.exe (PID: 3924)
- fn_external.exe (PID: 1004)
- fn_componentbrowserFontDriverPerf.exe (PID: 2476)
- fortnite_inj.exe (PID: 3388)
Manual execution by a user
- msedge.exe (PID: 4012)
- wmpnscfg.exe (PID: 3924)
- fn_external.exe (PID: 4068)
- WinRAR.exe (PID: 3988)
- fn_external.exe (PID: 1004)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3924)
- fn_componentbrowserFontDriverPerf.exe (PID: 2476)
The process uses the downloaded file
- msedge.exe (PID: 3348)
- WinRAR.exe (PID: 3988)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3988)
Creates files or folders in the user directory
- fn_external.exe (PID: 1004)
Reads Environment values
- fn_componentbrowserFontDriverPerf.exe (PID: 2476)
Reads product name
- fn_componentbrowserFontDriverPerf.exe (PID: 2476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
28
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1460 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1452 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2304 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1004 | "C:\Users\admin\Downloads\fn_external.exe" | C:\Users\admin\Downloads\fn_external.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 0,0,0,0 Modules
| |||||||||||||||
| 1068 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=5592 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2284 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1260 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=5328 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=5600 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=3500 --field-trial-handle=1204,i,17281043639160033951,1857005269926224355,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
21 870
Read events
21 664
Write events
197
Delete events
9
Modification events
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000059010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3448) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
31
Suspicious files
426
Text files
65
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:EC191A75922618816855B66FBD49117A | SHA256:E67338B655395FE42D6833940F24C2046DA4F479DB2C85D93CF0A84C805DFB1C | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94C18AA77707A64853AFFBE6D6382F75 | binary | |
MD5:217691D7CA900939993694EB50DEABA8 | SHA256:4A08BD739A2DF487922A0A94F478578B53F2424F9E1AE1CE1CA52BE03B245EF5 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\fn-softaim[1].htm | html | |
MD5:6BAB08CD6300599BA7372033DEFED689 | SHA256:5A8D2D2DC6B55FB8C67E1C95FC8C9324A11DD4521875EC7F3D39F3B82136EA75 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94C18AA77707A64853AFFBE6D6382F75 | binary | |
MD5:4F20DBAAD21BF2679D5B4F686D9E4CEF | SHA256:414CD6B65BC7F81E443D3943144429ACDA0939B833AD733C8A25D4C188821647 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\focus-within-polyfill[1].js | text | |
MD5:C187011C9A45C15A6FCBF5D62A5D755F | SHA256:452A163BE231D77006015E7D6F2A5B8AB5987D915C1F1E6907DDFBBA3AEC6EEC | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\minified[1].js | text | |
MD5:18EB21E8D1074FD7A594D3748BA0CB33 | SHA256:C64775436F34A6D26E276BBBC97BECDA2D4C73F15D70D5B13587D72123DFC5FD | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\thunderbolt-commons.2a091505.bundle.min[1].js | text | |
MD5:3B09FEE1D1B5F6CAD36B7190FC29FE6F | SHA256:034E401945B7A7ED759D7826FAEADDC1A4D8EAEC1C09F68EF0A7E3FF957C6F63 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\siteTags.bundle.min[1].js | text | |
MD5:7145D37309F2D1AD0F961C6C0A0DB191 | SHA256:CA3396F3825BB4251AC34B999DDC5F589EF860B95E3667D57EE26E3061503CA8 | |||
| 3484 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\wix-perf-measure.umd.min[1].js | text | |
MD5:5E646FA090A760653CFA56C727BB5A13 | SHA256:D0E6054D7B47B8DE059E88C419A16A3E745E038B05B75AF9D57C2E8593BD1D78 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
156
DNS requests
172
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3448 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3484 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d6bb2ad0af14907d | unknown | compressed | 4.66 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 67.27.159.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a1f744e7e9e1d6c2 | unknown | compressed | 4.66 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEFXmhGEJhUmGJG5%2BWz0P3mI%3D | unknown | der | 471 b | unknown |
3484 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEBcTU0k%2F6HFyQ0P%2Be%2BBGUOY%3D | unknown | binary | 471 b | unknown |
3484 | iexplore.exe | GET | 200 | 151.101.2.133:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEH6HwqMlsnS7%2BryQ1sUoZV4%3D | unknown | binary | 1.40 Kb | unknown |
3484 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://crl.starfieldtech.com/sfroot-g2.crl | unknown | binary | 584 b | unknown |
3484 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEHgnk5%2FZKEYAQUsEAs4i3T4%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3484 | iexplore.exe | 185.230.63.186:443 | perfectmod.fun | Wix.com Ltd. | US | unknown |
3484 | iexplore.exe | 67.27.159.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | malicious |
3484 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
3484 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3484 | iexplore.exe | 34.149.87.45:443 | www.perfectmod.fun | GOOGLE | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3484 | iexplore.exe | 34.96.106.200:443 | static.parastorage.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
perfectmod.fun |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
www.perfectmod.fun |
| unknown |
static.parastorage.com |
| shared |
polyfill.io |
| whitelisted |
static.wixstatic.com |
| whitelisted |
crl.starfieldtech.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3760 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
3760 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
3760 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
3760 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
3760 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
3760 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |