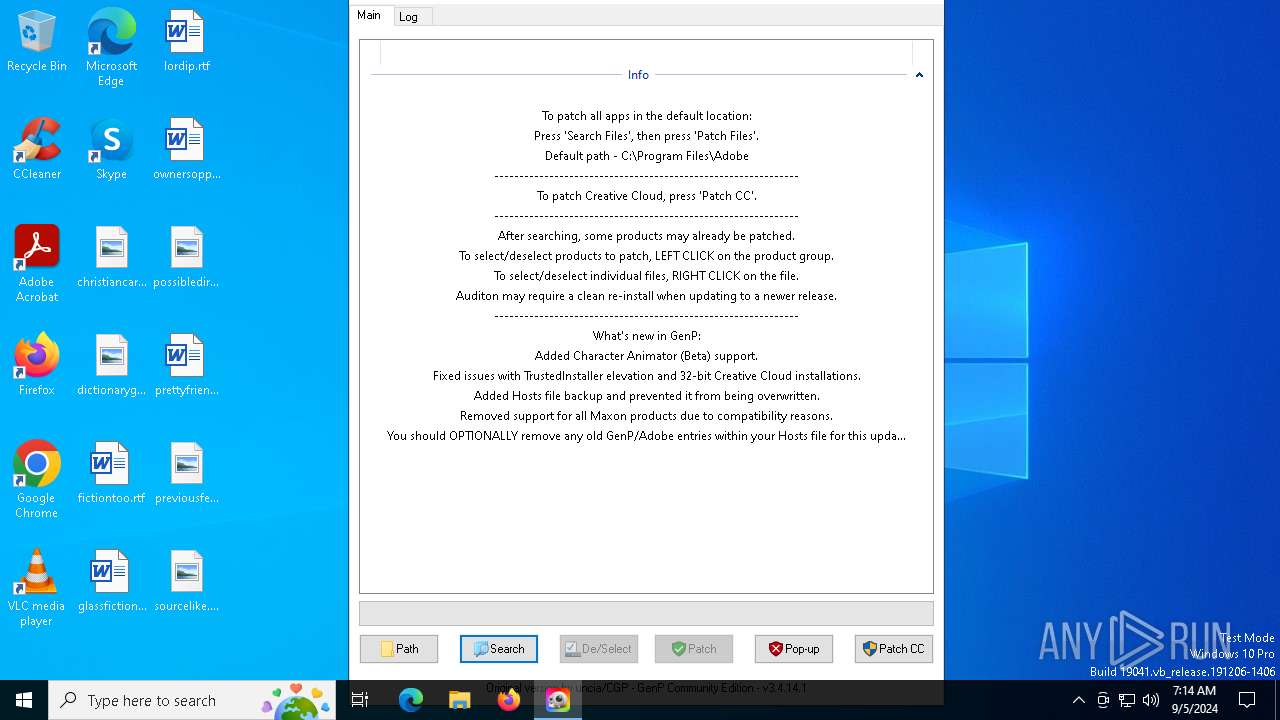
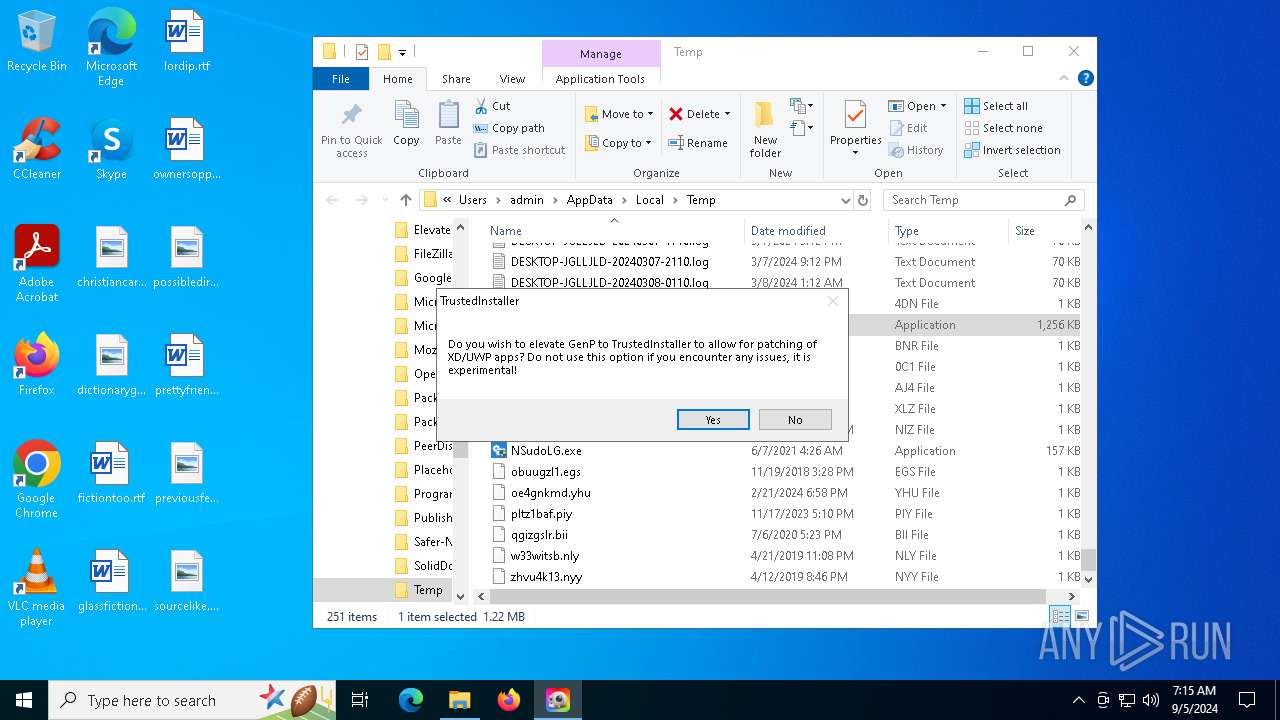
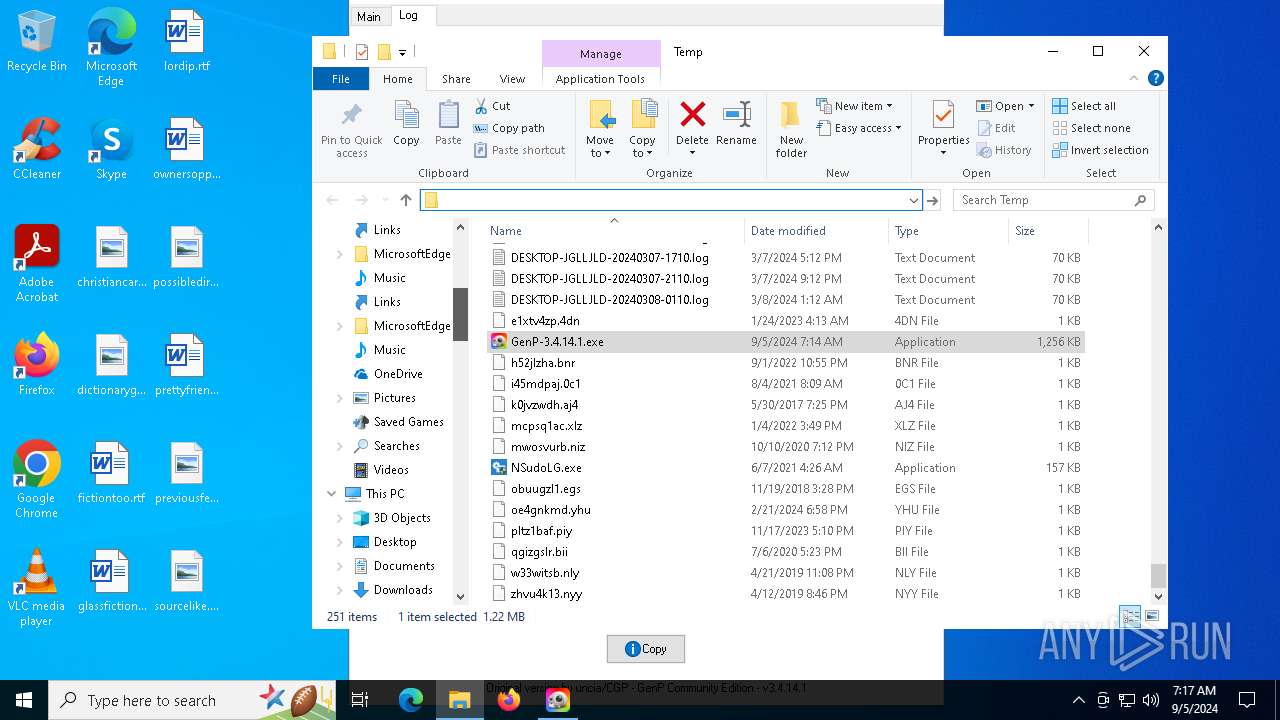
| File name: | GenP-3.4.14.1.exe |
| Full analysis: | https://app.any.run/tasks/c743df9c-43ac-4108-bd82-8eea6b4af22d |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 07:13:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 5AA73CE6297B35AAC0067529A47B44C5 |
| SHA1: | 48238C0C52990AB1F64CA8FAA7FC310FD729AF49 |
| SHA256: | 3BDDB83344219A07A43E53F68A0F6920FDD51B7412540D0DAAEAC353B6AB11A2 |
| SSDEEP: | 49152:JE/XUraxm5O9QMal0QRO8tWDqSnXmYwj9hCcGaH6BBpOz46P1VW:J9rem5Oide69VW |
MALICIOUS
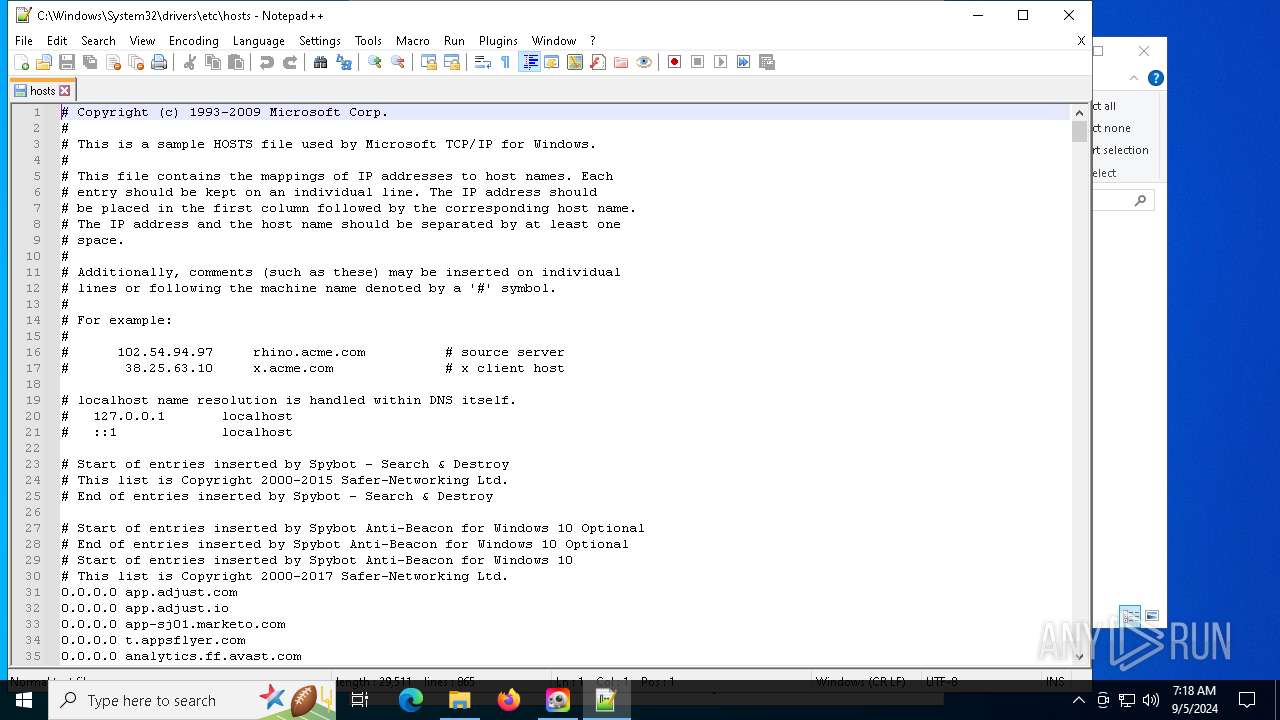
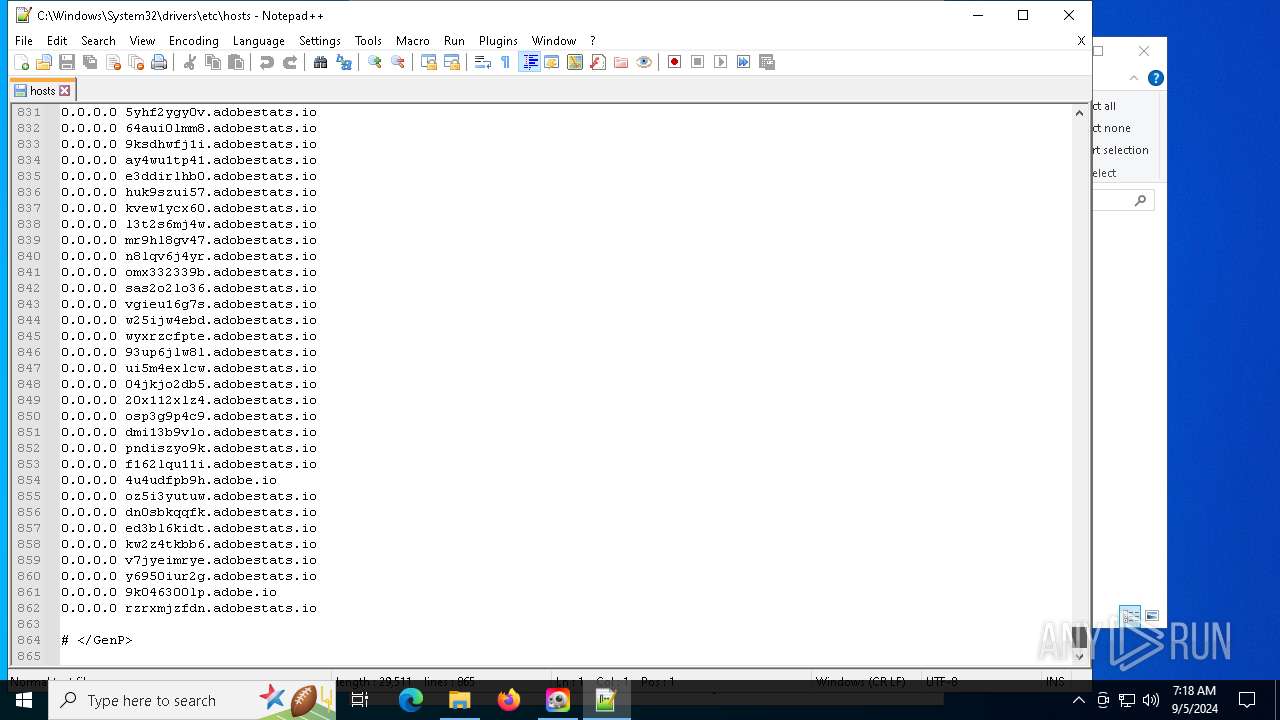
Modifies hosts file to block updates
- powershell.exe (PID: 7060)
SUSPICIOUS
Executable content was dropped or overwritten
- GenP-3.4.14.1.exe (PID: 304)
- GenP-3.4.14.1.exe (PID: 936)
- GenP-3.4.14.1.exe (PID: 7164)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 4060)
- GenP-3.4.14.1.exe (PID: 3176)
- GenP-3.4.14.1.exe (PID: 4092)
Application launched itself
- GenP-3.4.14.1.exe (PID: 4092)
- GenP-3.4.14.1.exe (PID: 3176)
Reads the date of Windows installation
- GenP-3.4.14.1.exe (PID: 4092)
- GenP-3.4.14.1.exe (PID: 3176)
Starts POWERSHELL.EXE for commands execution
- GenP-3.4.14.1.exe (PID: 7164)
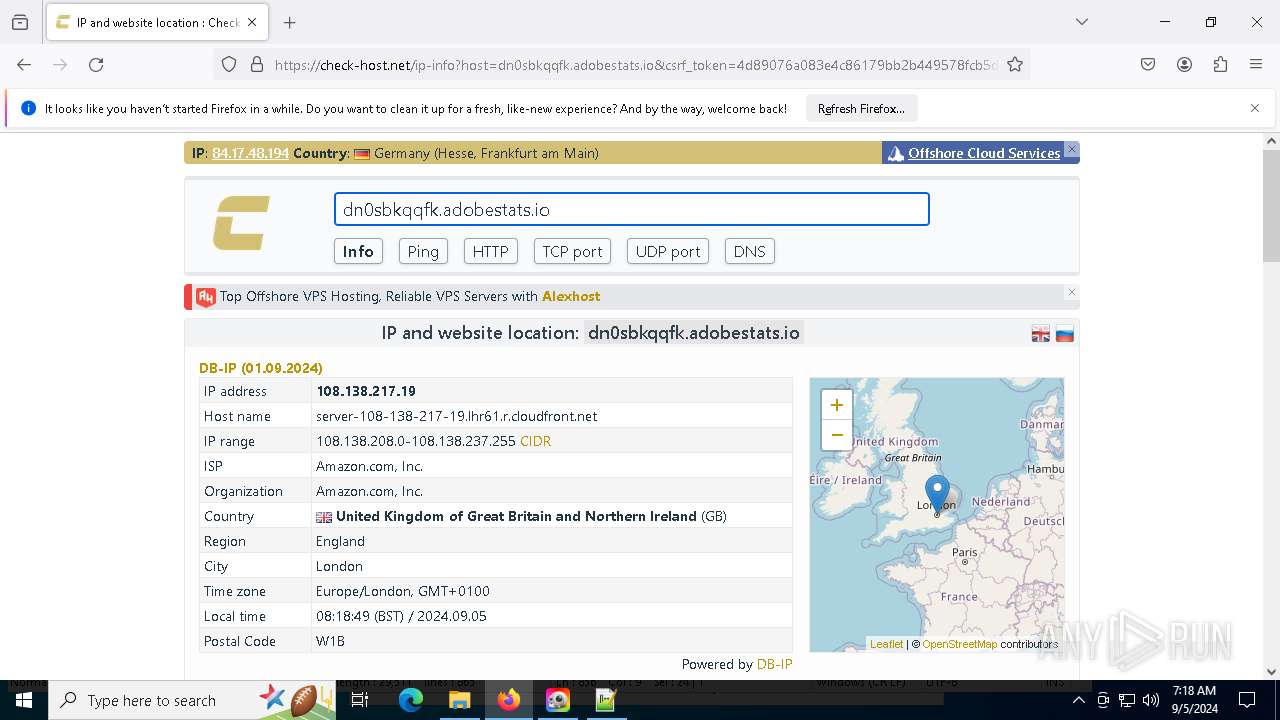
Found IP address in command line
- powershell.exe (PID: 6620)
Probably obfuscated PowerShell command line is found
- GenP-3.4.14.1.exe (PID: 7164)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- GenP-3.4.14.1.exe (PID: 7164)
Uses NETSH.EXE to add a firewall rule or allowed programs
- GenP-3.4.14.1.exe (PID: 7164)
The process checks if current user has admin rights
- GenP-3.4.14.1.exe (PID: 7164)
Request a resource from the Internet using PowerShell's cmdlet
- GenP-3.4.14.1.exe (PID: 7164)
Creates files in the driver directory
- powershell.exe (PID: 7060)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 7060)
INFO
The process uses the downloaded file
- GenP-3.4.14.1.exe (PID: 3176)
- GenP-3.4.14.1.exe (PID: 4092)
- powershell.exe (PID: 320)
Reads mouse settings
- GenP-3.4.14.1.exe (PID: 3176)
- GenP-3.4.14.1.exe (PID: 936)
- GenP-3.4.14.1.exe (PID: 304)
- GenP-3.4.14.1.exe (PID: 4092)
- GenP-3.4.14.1.exe (PID: 4528)
- GenP-3.4.14.1.exe (PID: 7164)
Create files in a temporary directory
- GenP-3.4.14.1.exe (PID: 936)
- GenP-3.4.14.1.exe (PID: 4528)
Checks supported languages
- GenP-3.4.14.1.exe (PID: 936)
- GenP-3.4.14.1.exe (PID: 304)
- ShellExperienceHost.exe (PID: 4060)
- GenP-3.4.14.1.exe (PID: 4092)
- NSudoLG.exe (PID: 6512)
- GenP-3.4.14.1.exe (PID: 4528)
- NSudoLG.exe (PID: 3568)
- GenP-3.4.14.1.exe (PID: 7164)
- GenP-3.4.14.1.exe (PID: 3176)
Reads the computer name
- GenP-3.4.14.1.exe (PID: 936)
- ShellExperienceHost.exe (PID: 4060)
- GenP-3.4.14.1.exe (PID: 304)
- GenP-3.4.14.1.exe (PID: 4092)
- GenP-3.4.14.1.exe (PID: 4528)
- GenP-3.4.14.1.exe (PID: 7164)
- NSudoLG.exe (PID: 3568)
- GenP-3.4.14.1.exe (PID: 3176)
- NSudoLG.exe (PID: 6512)
Sends debugging messages
- ShellExperienceHost.exe (PID: 4060)
- notepad++.exe (PID: 6160)
Manual execution by a user
- GenP-3.4.14.1.exe (PID: 4092)
- notepad++.exe (PID: 6160)
- firefox.exe (PID: 2728)
Process checks computer location settings
- GenP-3.4.14.1.exe (PID: 3176)
- GenP-3.4.14.1.exe (PID: 4092)
Reads the software policy settings
- slui.exe (PID: 7096)
- slui.exe (PID: 3208)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7060)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7060)
Checks proxy server information
- slui.exe (PID: 3208)
Application launched itself
- firefox.exe (PID: 5304)
- firefox.exe (PID: 2728)
Disables trace logs
- powershell.exe (PID: 7060)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:02 21:32:52+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.16 |
| CodeSize: | 734208 |
| InitializedDataSize: | 550400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2549c |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.4.14.1 |
| ProductVersionNumber: | 3.4.14.1 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 3.4.14.1 |
| Comments: | GenP v3.4.14.1 |
| FileDescription: | GenP v3.4.14.1 |
| ProductName: | GenP v3.4.14.1 |
| ProductVersion: | 3.4.14.1 |
| CompanyName: | GenP |
| LegalCopyright: | GenP |
| LegalTradeMarks: | GenP |
Total processes
168
Monitored processes
35
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Users\admin\AppData\Local\Temp\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\GenP-3.4.14.1.exe | NSudoLG.exe | ||||||||||||
User: SYSTEM Company: GenP Integrity Level: SYSTEM Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 304 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1900 -parentBuildID 20240213221259 -prefsHandle 1832 -prefMapHandle 1824 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {69dbb764-5976-4a83-958c-ab449a513004} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 1244f7e4910 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 320 | "C:\Windows\System32\WindowsPowerShell\v1.0\PowerShell.exe" -Command "$currentDate=Get-Date;$ipAddresses=@();try{$SOA=(Resolve-DnsName -Name adobe.io -Type SOA -ErrorAction Stop).PrimaryServer}catch{$SOA=$null};if($SOA){Do{if((New-TimeSpan -Start $currentDate -End (Get-Date)).TotalSeconds -gt 5){if($ipAddresses.Count -eq 0){$ipAddresses+='False'};break};try{$ipAddress=(Resolve-DnsName -Name adobe.io -Server $SOA -ErrorAction Stop).IPAddress}catch{$ipAddress=$null};if($ipAddress){$ipAddresses+=$ipAddress};$ipAddresses=$ipAddresses|Select -Unique|Sort-Object}While($ipAddresses.Count -lt 8)}else{$ipAddresses+='False'};Do{if((New-TimeSpan -Start $currentDate -End (Get-Date)).TotalSeconds -gt 5 -or $ipAddresses[0] -eq 'False'){break};try{$ipAddress=(Resolve-DnsName -Name 3u6k9as4bj.adobestats.io -ErrorAction Stop).IPAddress}catch{$ipAddress=$null};if($ipAddress){$ipAddresses+=$ipAddress};$ipAddresses=$ipAddresses|Select -Unique|Sort-Object}While($ipAddresses.Count -lt 12 -and $ipAddresses[0] -ne 'False');$ipAddresses=$ipAddresses -ne 'False'|Select -Unique|Sort-Object;$ipAddressList=if($ipAddresses.Count -eq 0){'False'}else{$ipAddresses -join ','};$ipAddressList" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | GenP-3.4.14.1.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | "C:\Users\admin\AppData\Local\Temp\GenP-3.4.14.1.exe" ! | C:\Users\admin\AppData\Local\Temp\GenP-3.4.14.1.exe | GenP-3.4.14.1.exe | ||||||||||||
User: admin Company: GenP Integrity Level: HIGH Description: GenP v3.4.14.1 Exit code: 6512 Version: 3.4.14.1 Modules
| |||||||||||||||
| 964 | netsh advfirewall firewall add rule name="Adobe Unlicensed Pop-up" dir=out action=block remoteip="107.22.247.231,18.207.85.246,18.245.31.121,18.245.31.2,18.245.31.74,18.245.31.79,23.22.254.206,34.193.227.236,52.202.204.11,52.5.13.197,54.144.73.197,54.227.187.23" | C:\Windows\System32\netsh.exe | — | GenP-3.4.14.1.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1948 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2476 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5160 -childID 6 -isForBrowser -prefsHandle 6512 -prefMapHandle 6528 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1488 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {a91b1c7d-f076-42a1-b7b4-93e8b45c3a94} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 1245af67bd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2648 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2248 -parentBuildID 20240213221259 -prefsHandle 2240 -prefMapHandle 2228 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {386efeb9-0f1b-4996-99c7-6958ce754b6b} 5304 "\\.\pipe\gecko-crash-server-pipe.5304" 12442c82710 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
30 136
Read events
30 089
Write events
39
Delete events
8
Modification events
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00470065006E0050002D0033002E0034002E00310034002E0031002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070000000 | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: FFFFFFFF | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {F02C1A0D-BE21-4350-88B0-7367FC96EF3C} {000214E6-0000-0000-C000-000000000046} 0xFFFF |
Value: 01000000000000006392794563FFDA01 | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {D9144DCD-E998-4ECA-AB6A-DCD83CCBA16D} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 010000000000000088F67B4563FFDA01 | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {4E77131D-3629-431C-9818-C5679DC83E81} {0C6C4200-C589-11D0-999A-00C04FD655E1} 0xFFFF |
Value: 0100000000000000755B7E4563FFDA01 | |||
| (PID) Process: | (304) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | 0 |
Value: 470065006E0050002D0033002E0034002E00310034002E0031002E006500780065000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080020000E0010000000000000000000000000000000000000100000000000000 | |||
Executable files
4
Suspicious files
153
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 936 | GenP-3.4.14.1.exe | C:\Users\admin\AppData\Local\Temp\config.ini | text | |
MD5:ADD427035968BC6F8BCDF0C5D7580495 | SHA256:66232A4D8677CD50612EAEBC664B2F2F3556B497D5BF8657967C259EF4723B68 | |||
| 936 | GenP-3.4.14.1.exe | C:\Users\admin\AppData\Local\Temp\autB4C1.tmp | binary | |
MD5:C8974BCA42D238986F542ECE4EBA859A | SHA256:1AE68F2E79AA2072FFD717E58B162CABF31785D341A398FBF3D9C67BB07332F1 | |||
| 304 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_32.db | binary | |
MD5:6FAFDC1C523D68F9B8D5810BD1F0E165 | SHA256:AFD4676F4313BAD89902EA1FF5ED9789C21D1A1BFE2B5F09F3D123858DB5D2C1 | |||
| 936 | GenP-3.4.14.1.exe | C:\Users\admin\AppData\Local\Temp\NSudoLG.exe | executable | |
MD5:7AACFD85B8DFF0AA6867BEDE82CFD147 | SHA256:871E4F28FE39BCAD8D295AE46E148BE458778C0195ED660B7DB18EB595D00BD8 | |||
| 304 | GenP-3.4.14.1.exe | C:\Windows\Temp\NSudoLG.exe | executable | |
MD5:7AACFD85B8DFF0AA6867BEDE82CFD147 | SHA256:871E4F28FE39BCAD8D295AE46E148BE458778C0195ED660B7DB18EB595D00BD8 | |||
| 936 | GenP-3.4.14.1.exe | C:\Users\admin\AppData\Local\Temp\autB4D2.tmp | binary | |
MD5:6F040B192B47D1D0860045AA30C102A0 | SHA256:A85D89E380CBF4929EE5B6E7D91BE71AF1C3A727A91CF30AFFB414B98E912180 | |||
| 304 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_idx.db | binary | |
MD5:546946FC802A2BFC395813150D9C7494 | SHA256:4354D2D9F2E51890C5AB4D842E0572F61728D40FE865D8FB3B28059FF90F0BC5 | |||
| 304 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_16.db | binary | |
MD5:14F4F76B352D3C1D2E3430B71B053926 | SHA256:980982E3051A6BF460C09AB9108D758375F25ED9AEA8D0212277A03383C5B2D2 | |||
| 304 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_256.db | binary | |
MD5:8FAA8531B8CF001D6A83FFDB69850F05 | SHA256:828EA3D7F8BA2CE21B260A59CC054BBD0942FCF93C46E3FDC7FDA0D3FF95DCE4 | |||
| 304 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_1280.db | binary | |
MD5:2DD3F3C33E7100EC0D4DBBCA9774B044 | SHA256:5A00CC998E0D0285B729964AFD20618CBAECFA7791FECDB843B535491A83AE21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
111
DNS requests
121
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6208 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5304 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5304 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6208 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4132 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1776 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1776 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5304 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
5304 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|