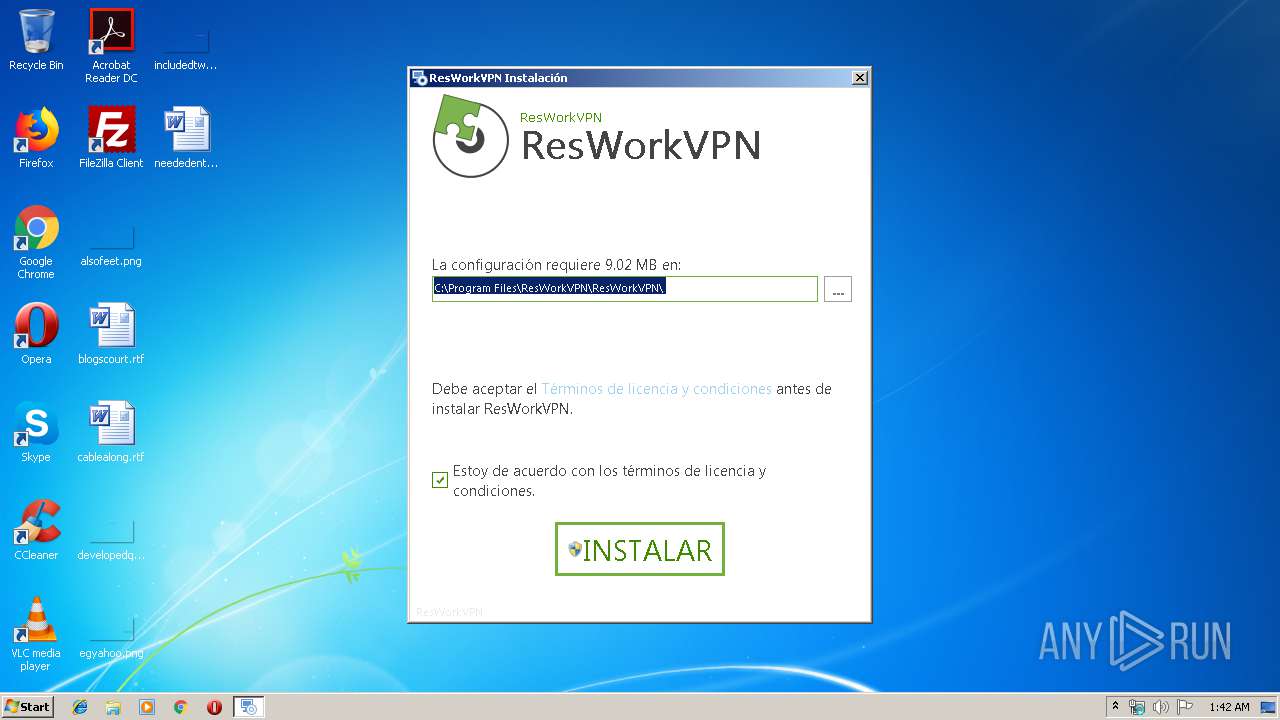
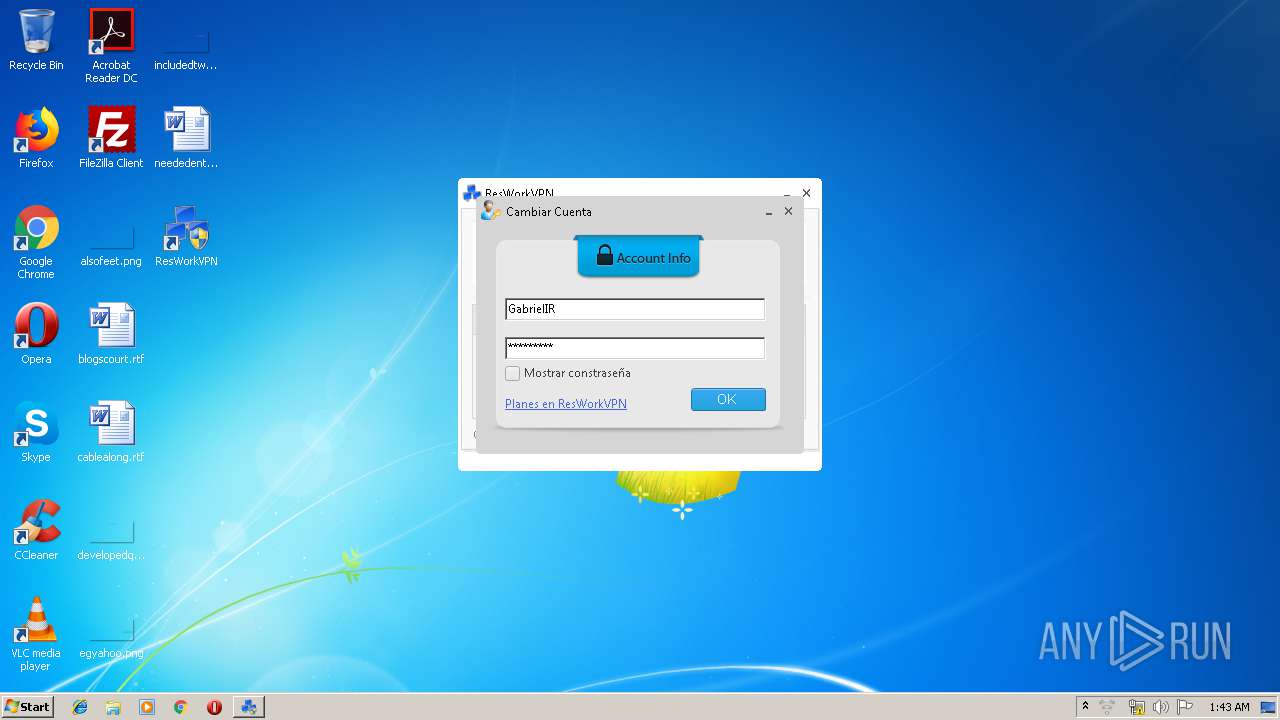
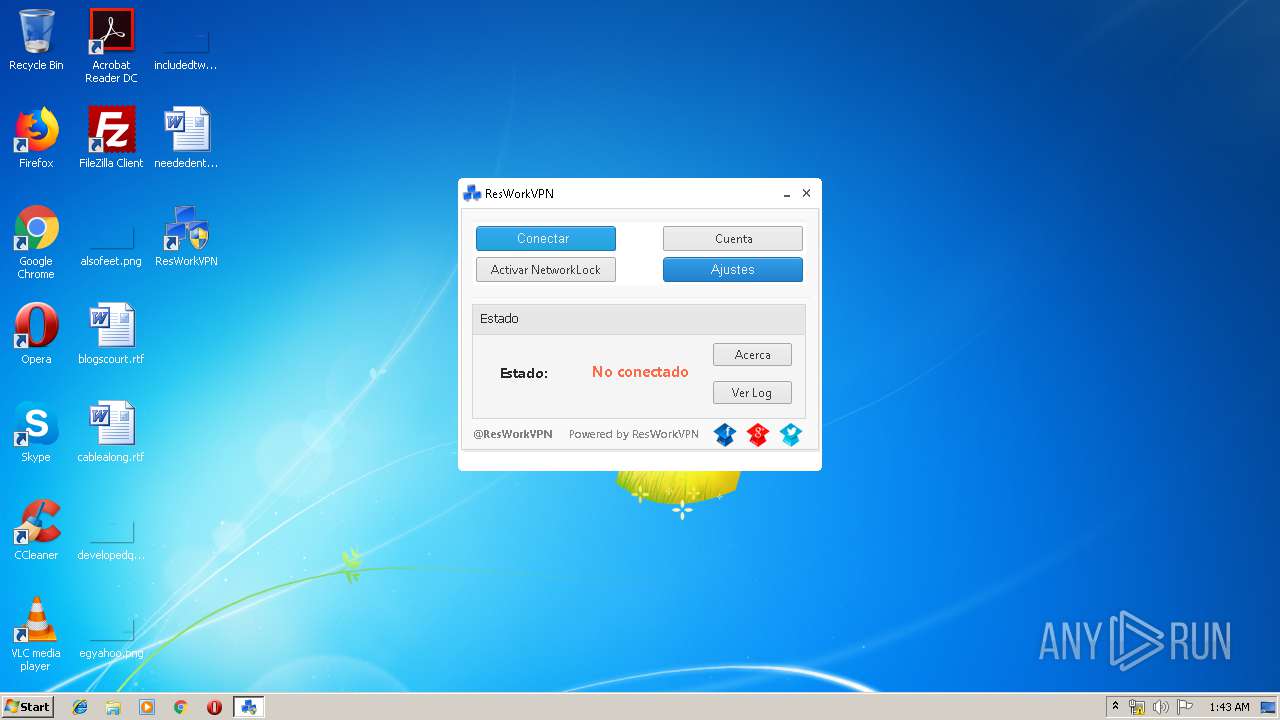
| File name: | ResWorkVPN_1.2.1.exe |
| Full analysis: | https://app.any.run/tasks/3c79a3cd-8984-45c3-9d00-432908a0dd7b |
| Verdict: | Malicious activity |
| Analysis date: | November 17, 2019, 01:41:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 93CEAEFE32CCAA3623CC0C093759DE39 |
| SHA1: | 61D353BB1C0E2BD87A96B72292CD540685DA4B1E |
| SHA256: | 3BCA98C07EF27C5A9939897527FC3A2D313B071258E2208ED986AFF19B132781 |
| SSDEEP: | 49152:6mikkfM0X+eChdolxRve1+CUq2ktBBLdsW5bCHwE53BS9Uh+jLAXvyurfB1Lf4iz:6mbEM8+5kwPs0eu9UYjLuvD+0OG7t |
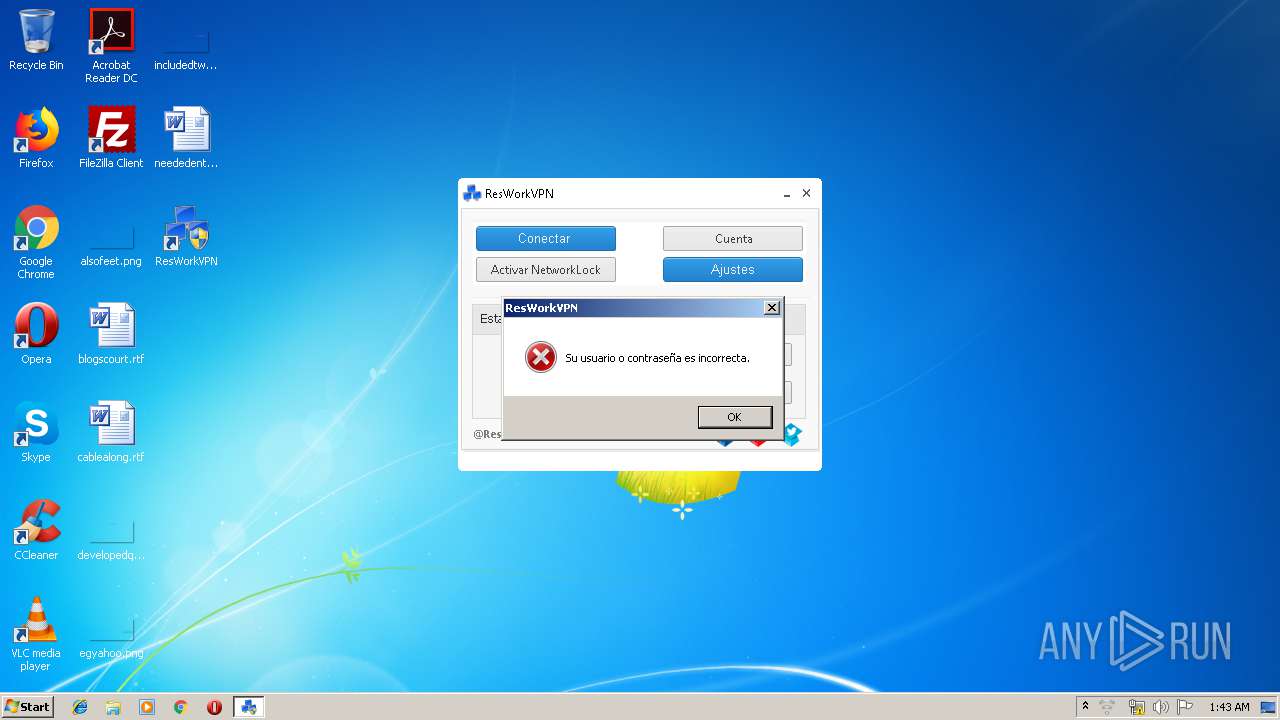
MALICIOUS
Writes to a start menu file
- msiexec.exe (PID: 3452)
Application was dropped or rewritten from another process
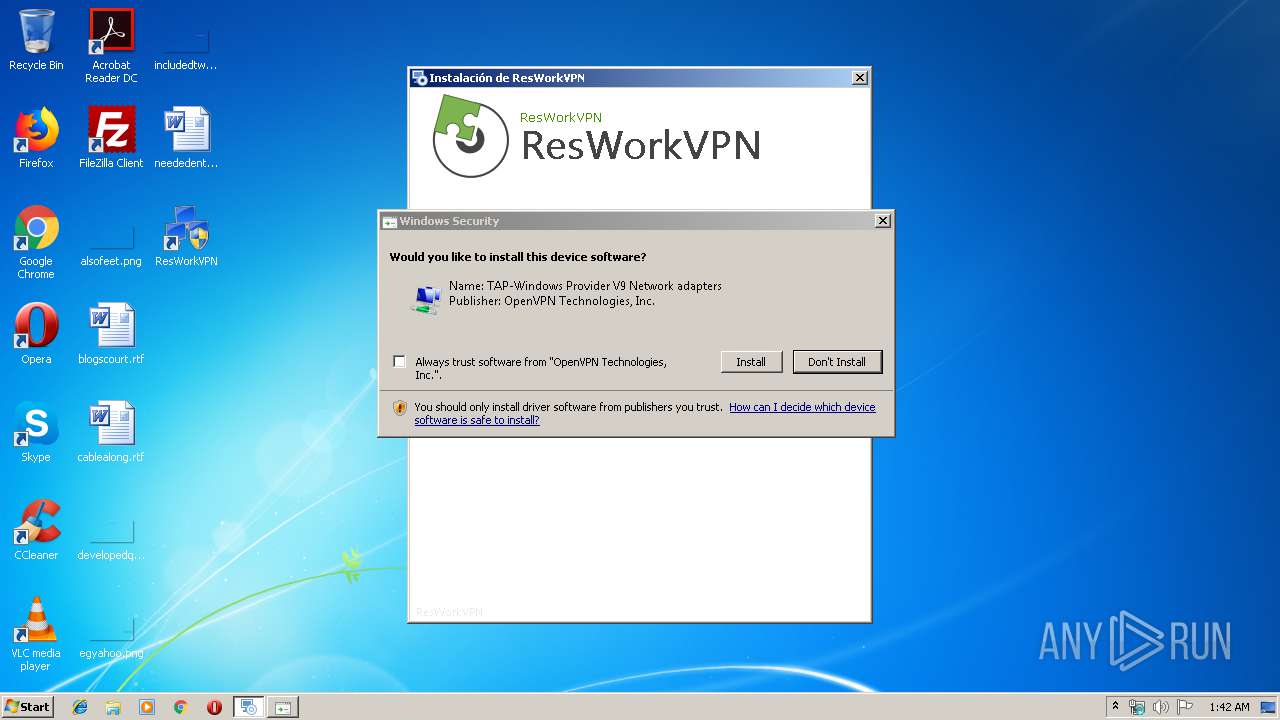
- tapinstall.exe (PID: 2336)
- tapinstall.exe (PID: 2520)
- ResWorkVPN.exe (PID: 2200)
- ResWorkVPN.exe (PID: 1940)
- openvpn.exe (PID: 3324)
Loads the Task Scheduler DLL interface
- ResWorkVPN_1.2.1.exe (PID: 2760)
Changes settings of System certificates
- ResWorkVPN.exe (PID: 1940)
Loads dropped or rewritten executable
- openvpn.exe (PID: 3324)
- ResWorkVPN_1.2.1.exe (PID: 2760)
SUSPICIOUS
Creates files in the user directory
- ResWorkVPN_1.2.1.exe (PID: 2760)
- MsiExec.exe (PID: 2988)
Starts CMD.EXE for commands execution
- MSICBED.tmp (PID: 3012)
- ResWorkVPN.exe (PID: 1940)
Executed via COM
- DrvInst.exe (PID: 2336)
- DrvInst.exe (PID: 1880)
Executable content was dropped or overwritten
- tapinstall.exe (PID: 2520)
- ResWorkVPN_1.2.1.exe (PID: 2760)
- DrvInst.exe (PID: 2336)
- DrvInst.exe (PID: 1880)
- ResWorkVPN_1.2.1.exe (PID: 3468)
- msiexec.exe (PID: 3452)
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 2988)
- DrvInst.exe (PID: 2336)
Creates files in the driver directory
- DrvInst.exe (PID: 2336)
- DrvInst.exe (PID: 1880)
Creates files in the Windows directory
- DrvInst.exe (PID: 2336)
- DrvInst.exe (PID: 1880)
Removes files from Windows directory
- DrvInst.exe (PID: 2336)
- DrvInst.exe (PID: 1880)
Executed as Windows Service
- vssvc.exe (PID: 3748)
Creates files in the program directory
- ResWorkVPN_1.2.1.exe (PID: 3468)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2056)
Adds / modifies Windows certificates
- ResWorkVPN.exe (PID: 1940)
Application launched itself
- ResWorkVPN_1.2.1.exe (PID: 2760)
INFO
Creates a software uninstall entry
- msiexec.exe (PID: 3452)
Creates files in the program directory
- msiexec.exe (PID: 3452)
Application was dropped or rewritten from another process
- MSICBED.tmp (PID: 3012)
Starts application with an unusual extension
- msiexec.exe (PID: 3452)
Application launched itself
- msiexec.exe (PID: 3452)
Searches for installed software
- DrvInst.exe (PID: 2336)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3748)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3008)
- MsiExec.exe (PID: 2988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:11:29 13:34:32+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.11 |
| CodeSize: | 1152000 |
| InitializedDataSize: | 527872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd0d69 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.1.0 |
| ProductVersionNumber: | 1.2.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | Spanish (Modern) |
| CharacterSet: | Unicode |
| CompanyName: | ResWorkVPN |
| FileDescription: | Esta base de datos del instalador contiene la lógica y los datos necesarios para instalar ResWorkVPN. |
| FileVersion: | 1.2.1 |
| InternalName: | ResWorkVPNInstaladorInstalador |
| LegalCopyright: | Copyright (C) 2019 ResWorkVPN |
| OriginalFileName: | ResWorkVPNInstalador.exeInstalador |
| ProductName: | ResWorkVPNInstalador |
| ProductVersion: | 1.2.1 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 29-Nov-2017 12:34:32 |
| Detected languages: |
|
| Debug artifacts: |
|
| CompanyName: | ResWorkVPN |
| FileDescription: | Esta base de datos del instalador contiene la lógica y los datos necesarios para instalar ResWorkVPN. |
| FileVersion: | 1.2.1 |
| InternalName: | ResWorkVPNInstaladorInstalador |
| LegalCopyright: | Copyright (C) 2019 ResWorkVPN |
| OriginalFileName: | ResWorkVPNInstalador.exeInstalador |
| ProductName: | ResWorkVPNInstalador |
| ProductVersion: | 1.2.1 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 29-Nov-2017 12:34:32 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00119314 | 0x00119400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64226 |
.rdata | 0x0011B000 | 0x000543E8 | 0x00054400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.58461 |
.data | 0x00170000 | 0x00007154 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.19572 |
.rsrc | 0x00178000 | 0x000159D4 | 0x00015A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.34124 |
.reloc | 0x0018E000 | 0x00014AC0 | 0x00014C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.58253 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.221 | 1915 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_MANIFEST |
2 | 3.1591 | 9640 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_ICON |
3 | 3.46873 | 4264 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_ICON |
4 | 3.54157 | 2440 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_ICON |
5 | 4.01317 | 1128 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_ICON |
9 | 3.31635 | 1318 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_STRING |
10 | 3.31258 | 2148 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_STRING |
11 | 3.27233 | 734 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_STRING |
12 | 3.19114 | 1476 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_STRING |
13 | 3.32064 | 896 | Latin 1 / Western European | Spanish - Spain (International sort) | RT_STRING |
Imports
KERNEL32.dll |
msi.dll (delay-loaded) |
Total processes
65
Monitored processes
19
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1880 | DrvInst.exe "2" "211" "ROOT\NET\0000" "C:\Windows\INF\oem4.inf" "oemvista.inf:tap0901:tap0901.ndi:9.0.0.21:tap0901" "6d14a44ff" "0000052C" "000005E8" "000005EC" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1940 | "C:\Program Files\ResWorkVPN\ResWorkVPN\ResWorkVPN.exe" | C:\Program Files\ResWorkVPN\ResWorkVPN\ResWorkVPN.exe | MsiExec.exe | ||||||||||||
User: admin Company: ResWorkVPN Integrity Level: HIGH Description: ResWorkVPN Exit code: 0 Version: 1.2.1 Modules
| |||||||||||||||
| 2056 | cmd /ctaskkill /f /im openvpn.exe | C:\Windows\system32\cmd.exe | — | ResWorkVPN.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2200 | "C:\Program Files\ResWorkVPN\ResWorkVPN\ResWorkVPN.exe" | C:\Program Files\ResWorkVPN\ResWorkVPN\ResWorkVPN.exe | — | MsiExec.exe | |||||||||||
User: admin Company: ResWorkVPN Integrity Level: MEDIUM Description: ResWorkVPN Exit code: 3221226540 Version: 1.2.1 Modules
| |||||||||||||||
| 2328 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{6a8a7dc7-e7b9-7907-99d5-ee7b1d6ac91a} Global\{2b0b152d-1708-1014-aefd-4e5e759c0d27} C:\Windows\System32\DriverStore\Temp\{79388293-b3f9-43e8-5bca-8e24e285fb75}\oemvista.inf C:\Windows\System32\DriverStore\Temp\{79388293-b3f9-43e8-5bca-8e24e285fb75}\tap0901.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2336 | tapinstall.exe remove tap0901 | C:\Program Files\ResWorkVPN\ResWorkVPN\drivers\x86\tapinstall.exe | — | cmd.exe | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
| 2336 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{536d4912-52e8-1012-a207-c86b4931a812}\oemvista.inf" "0" "6d14a44ff" "0000052C" "WinSta0\Default" "0000039C" "208" "c:\program files\resworkvpn\resworkvpn\drivers\x86" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | tapinstall.exe install OemVista.inf tap0901 | C:\Program Files\ResWorkVPN\ResWorkVPN\drivers\x86\tapinstall.exe | cmd.exe | ||||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
| 2752 | "C:\Windows\System32\cmd.exe" /C "C:\Program Files\ResWorkVPN\ResWorkVPN\drivers\install.bat" | C:\Windows\System32\cmd.exe | — | MSICBED.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2760 | "C:\Users\admin\AppData\Local\Temp\ResWorkVPN_1.2.1.exe" | C:\Users\admin\AppData\Local\Temp\ResWorkVPN_1.2.1.exe | explorer.exe | ||||||||||||
User: admin Company: ResWorkVPN Integrity Level: MEDIUM Description: Esta base de datos del instalador contiene la lógica y los datos necesarios para instalar ResWorkVPN. Exit code: 0 Version: 1.2.1 Modules
| |||||||||||||||
Total events
2 061
Read events
1 328
Write events
671
Delete events
62
Modification events
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2988) MsiExec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\MsiExec_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
38
Suspicious files
22
Text files
251
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | ResWorkVPN_1.2.1.exe | C:\Users\admin\AppData\Roaming\ResWorkVPN\ResWorkVPN 1.2.1\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 2760 | ResWorkVPN_1.2.1.exe | C:\Users\admin\AppData\Local\Temp\MSIB012.tmp | — | |
MD5:— | SHA256:— | |||
| 2760 | ResWorkVPN_1.2.1.exe | C:\Users\admin\AppData\Local\Temp\MSIB032.tmp | — | |
MD5:— | SHA256:— | |||
| 2988 | MsiExec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@google[1].txt | — | |
MD5:— | SHA256:— | |||
| 2988 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\tinB04F.tmp.part | — | |
MD5:— | SHA256:— | |||
| 2988 | MsiExec.exe | C:\Users\admin\AppData\Local\Temp\tinB04F.tmp | — | |
MD5:— | SHA256:— | |||
| 2760 | ResWorkVPN_1.2.1.exe | C:\Users\admin\AppData\Roaming\ResWorkVPN\ResWorkVPN 1.2.1\install\1AE960F\ResWorkVPNAppInstaller.x64.msi | executable | |
MD5:— | SHA256:— | |||
| 2760 | ResWorkVPN_1.2.1.exe | C:\Users\admin\AppData\Roaming\ResWorkVPN\ResWorkVPN 1.2.1\install\1AE960F\ResWorkVPNAppInstaller.msi | executable | |
MD5:— | SHA256:— | |||
| 2988 | MsiExec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@google[2].txt | text | |
MD5:— | SHA256:— | |||
| 2760 | ResWorkVPN_1.2.1.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_2760\frame_top_mid.bmp | image | |
MD5:F623CB070F63ADADF31212D6564805B9 | SHA256:E4AB79B964317D20D8E15D8723CADCA3691878520CFE498EB62674FD8E4A3DC2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2988 | MsiExec.exe | GET | 200 | 216.58.207.68:80 | http://www.google.com/ | US | html | 11.3 Kb | malicious |
2988 | MsiExec.exe | GET | 200 | 216.58.207.68:80 | http://www.google.com/ | US | html | 11.3 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1940 | ResWorkVPN.exe | 104.24.108.149:443 | resworkvpn.com | Cloudflare Inc | US | shared |
3324 | openvpn.exe | 24.7.51.129:1194 | computerroomnas.myqnapcloud.com | Comcast Cable Communications, LLC | US | unknown |
2988 | MsiExec.exe | 216.58.207.68:80 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
resworkvpn.com |
| suspicious |
computerroomnas.myqnapcloud.com |
| unknown |
Threats
2 ETPRO signatures available at the full report