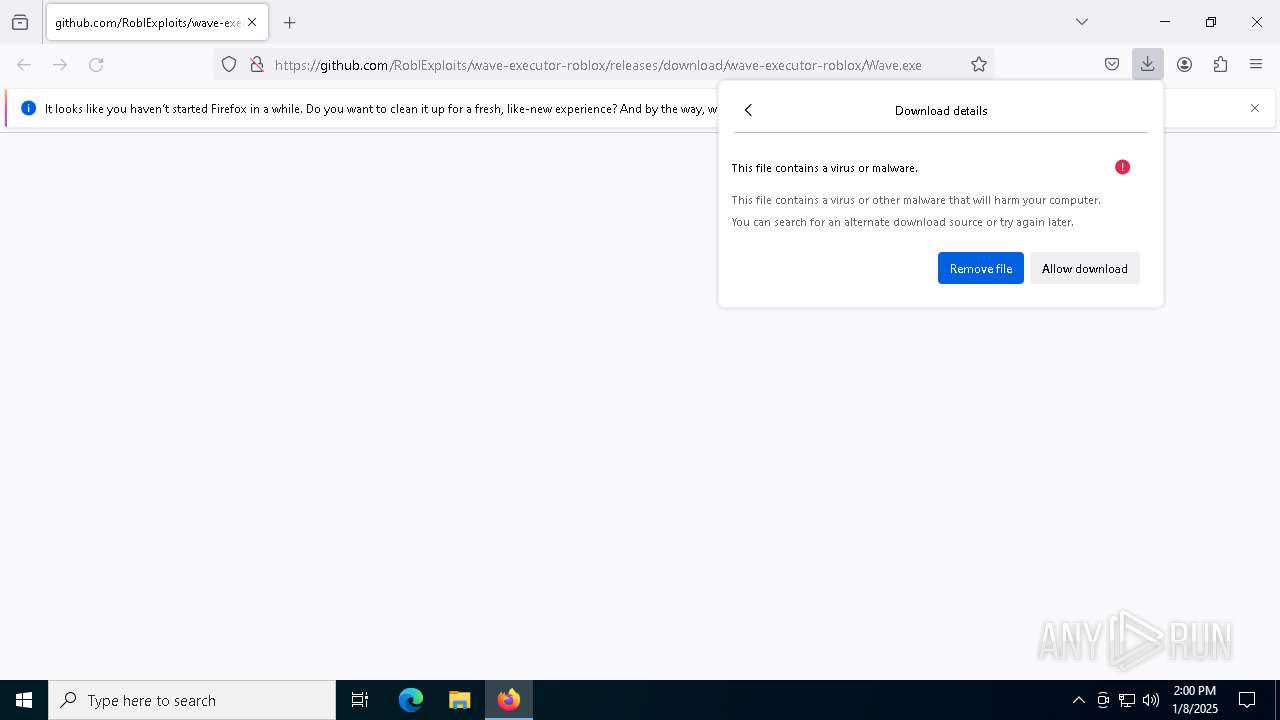
| URL: | https://github.com/RoblExploits/wave-executor-roblox/releases/download/wave-executor-roblox/Wave.exe |
| Full analysis: | https://app.any.run/tasks/e0dd6a35-3a76-4ade-9755-b4e579d6ebf7 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | January 08, 2025, 13:59:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | EA6708F83AE061EF5549949EB5943650 |
| SHA1: | 85F099904A6FB2F87B83BC3A10B6DAD4AA303DEA |
| SHA256: | 3BB77219F8A6CAF8111D7B5968DDB256610FE78CAD7A6C946CDE8C7FB973B8E3 |
| SSDEEP: | 3:N8tEdqOdrSEMIxZKH7AOrkCjxZKH3lAn:2usOdrSrIZKHEOrvZKH3lAn |
MALICIOUS
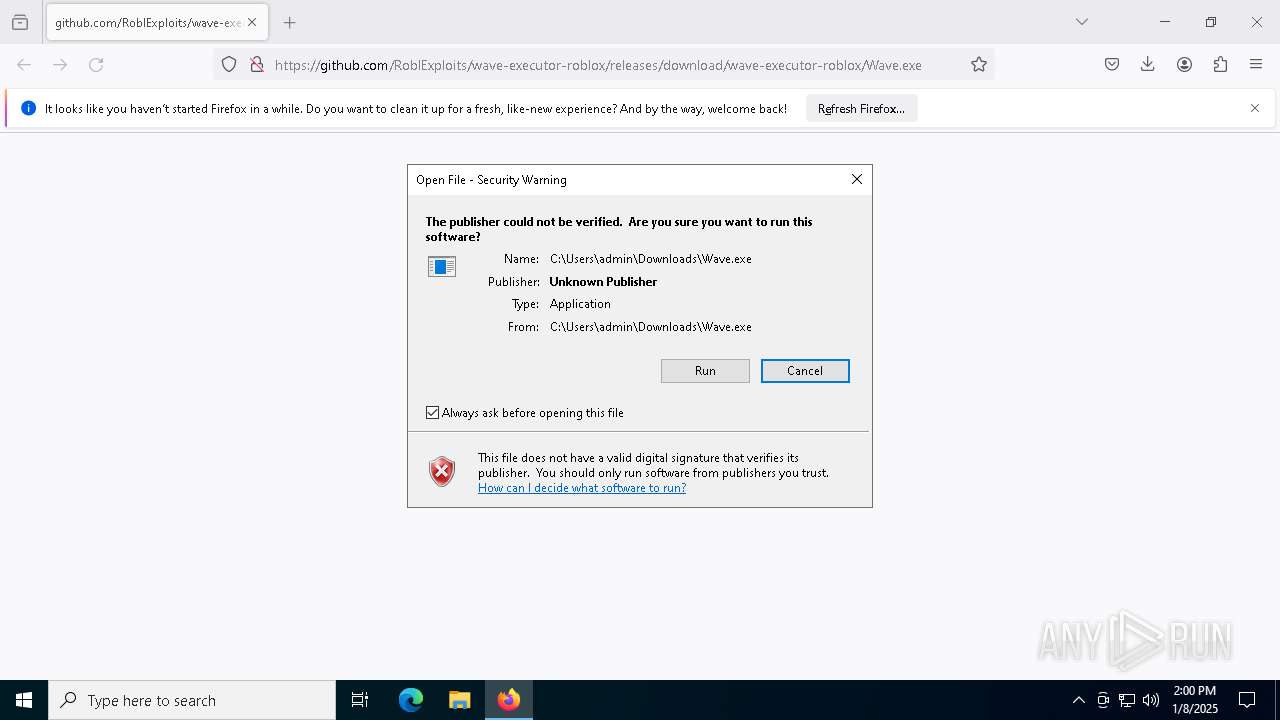
Executing a file with an untrusted certificate
- Wave.exe (PID: 7220)
- Wave.exe (PID: 5472)
Actions looks like stealing of personal data
- Wave.exe (PID: 5472)
LUNA has been detected
- Wave.exe (PID: 5472)
Steals credentials from Web Browsers
- Wave.exe (PID: 5472)
DISCORDGRABBER has been detected (YARA)
- Wave.exe (PID: 5472)
Starts CMD.EXE for self-deleting
- Wave.exe (PID: 5472)
SUSPICIOUS
Process drops python dynamic module
- Wave.exe (PID: 7220)
The process drops C-runtime libraries
- Wave.exe (PID: 7220)
Executable content was dropped or overwritten
- Wave.exe (PID: 7220)
Process drops legitimate windows executable
- firefox.exe (PID: 6472)
- Wave.exe (PID: 7220)
Application launched itself
- Wave.exe (PID: 7220)
Loads Python modules
- Wave.exe (PID: 5472)
Uses NETSH.EXE to obtain data on the network
- Wave.exe (PID: 5472)
There is functionality for taking screenshot (YARA)
- Wave.exe (PID: 5472)
Possible usage of Discord/Telegram API has been detected (YARA)
- Wave.exe (PID: 5472)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7868)
Uses WMIC.EXE to obtain CPU information
- Wave.exe (PID: 5472)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 7824)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7172)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 1580)
Checks for external IP
- svchost.exe (PID: 2192)
- Wave.exe (PID: 5472)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4864)
- cmd.exe (PID: 4968)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7212)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 5712)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7036)
Potential Corporate Privacy Violation
- Wave.exe (PID: 5472)
Hides command output
- cmd.exe (PID: 3564)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3564)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 8188)
Starts CMD.EXE for commands execution
- Wave.exe (PID: 5472)
INFO
Application launched itself
- firefox.exe (PID: 6400)
- firefox.exe (PID: 6472)
Reads the computer name
- Wave.exe (PID: 7220)
- Wave.exe (PID: 5472)
Executable content was dropped or overwritten
- firefox.exe (PID: 6472)
The sample compiled with english language support
- firefox.exe (PID: 6472)
- Wave.exe (PID: 7220)
Checks supported languages
- Wave.exe (PID: 7220)
- Wave.exe (PID: 5472)
Create files in a temporary directory
- Wave.exe (PID: 7220)
- Wave.exe (PID: 5472)
The process uses the downloaded file
- firefox.exe (PID: 6472)
PyInstaller has been detected (YARA)
- Wave.exe (PID: 7220)
- Wave.exe (PID: 5472)
Checks proxy server information
- Wave.exe (PID: 5472)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7172)
- WMIC.exe (PID: 7212)
Attempting to use instant messaging service
- Wave.exe (PID: 5472)
- svchost.exe (PID: 2192)
UPX packer has been detected
- Wave.exe (PID: 5472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(5472) Wave.exe
Discord-Webhook-Tokens (1)1298638543257735180/Y51MXyrPJjVGDTNVfwX6gTq8MlDnIHPZSiF08MZUHo4SP2BwWGW5n2X81lfnbQ5DnkGi
Discord-Info-Links
1298638543257735180/Y51MXyrPJjVGDTNVfwX6gTq8MlDnIHPZSiF08MZUHo4SP2BwWGW5n2X81lfnbQ5DnkGi
Get Webhook Infohttps://discord.com/api/webhooks/1298638543257735180/Y51MXyrPJjVGDTNVfwX6gTq8MlDnIHPZSiF08MZUHo4SP2BwWGW5n2X81lfnbQ5DnkGi
Total processes
165
Monitored processes
39
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | wmic cpu get Name | C:\Windows\System32\wbem\WMIC.exe | — | Wave.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | wmic os get Caption | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | wmic computersystem get totalphysicalmemory | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4124 -childID 2 -isForBrowser -prefsHandle 4116 -prefMapHandle 4112 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1236 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e13fd6cd-e23b-4f28-a32d-48fc8d643027} 6472 "\\.\pipe\gecko-crash-server-pipe.6472" 1b338ed7310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 15 Version: 123.0 Modules
| |||||||||||||||
| 3564 | C:\WINDOWS\system32\cmd.exe /c "ping localhost -n 3 > NUL && del /A H /F "C:\Users\admin\Downloads\Wave.exe"" | C:\Windows\System32\cmd.exe | — | Wave.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4536 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 162
Read events
17 160
Write events
2
Delete events
0
Modification events
| (PID) Process: | (6472) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6472) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
103
Suspicious files
746
Text files
88
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6472 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 6472 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6472 | firefox.exe | C:\Users\admin\Downloads\Wave.kQD7xawV.exe.part | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
83
DNS requests
121
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.209.210.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6472 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5988 | svchost.exe | GET | 200 | 23.209.210.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6472 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6472 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
6472 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
6472 | firefox.exe | POST | 200 | 95.101.54.195:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6472 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
6472 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6472 | firefox.exe | POST | 200 | 95.101.54.114:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 23.209.210.103:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5988 | svchost.exe | 23.209.210.103:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.198:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
6472 | firefox.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
6472 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | whitelisted |
6472 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
github.com |
| shared |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
5472 | Wave.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2192 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
5472 | Wave.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
5472 | Wave.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1 ETPRO signatures available at the full report