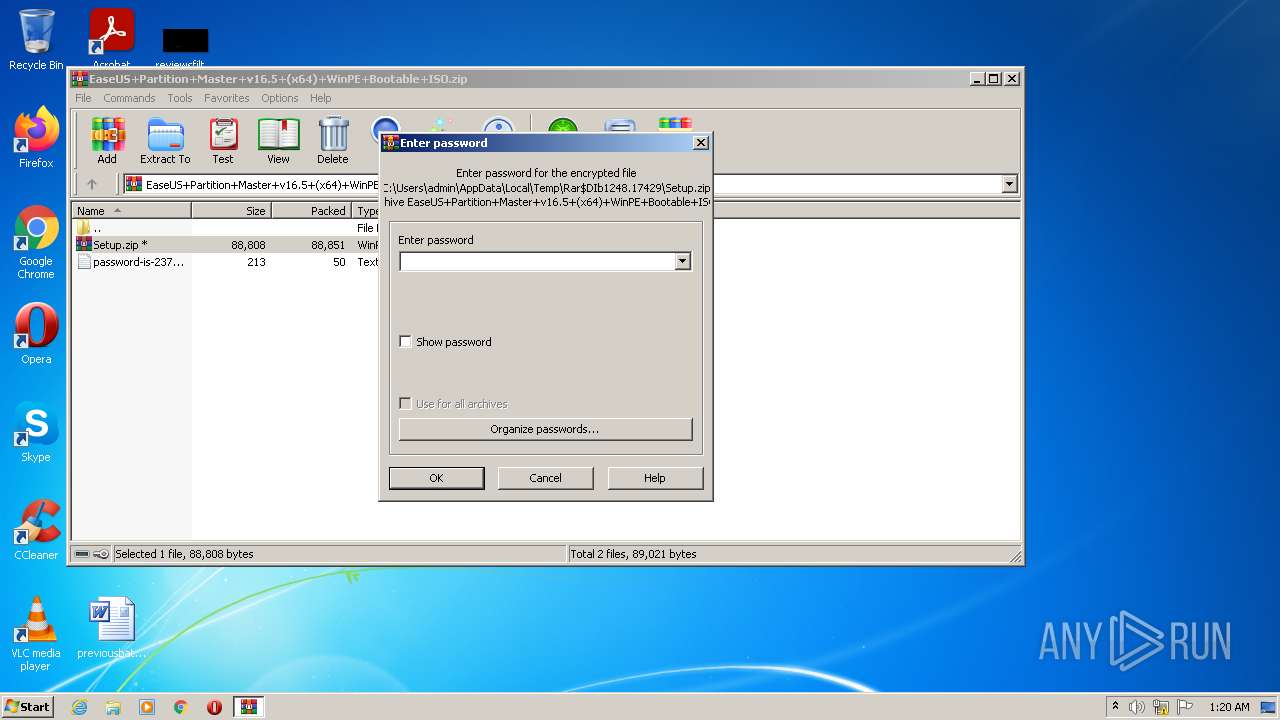
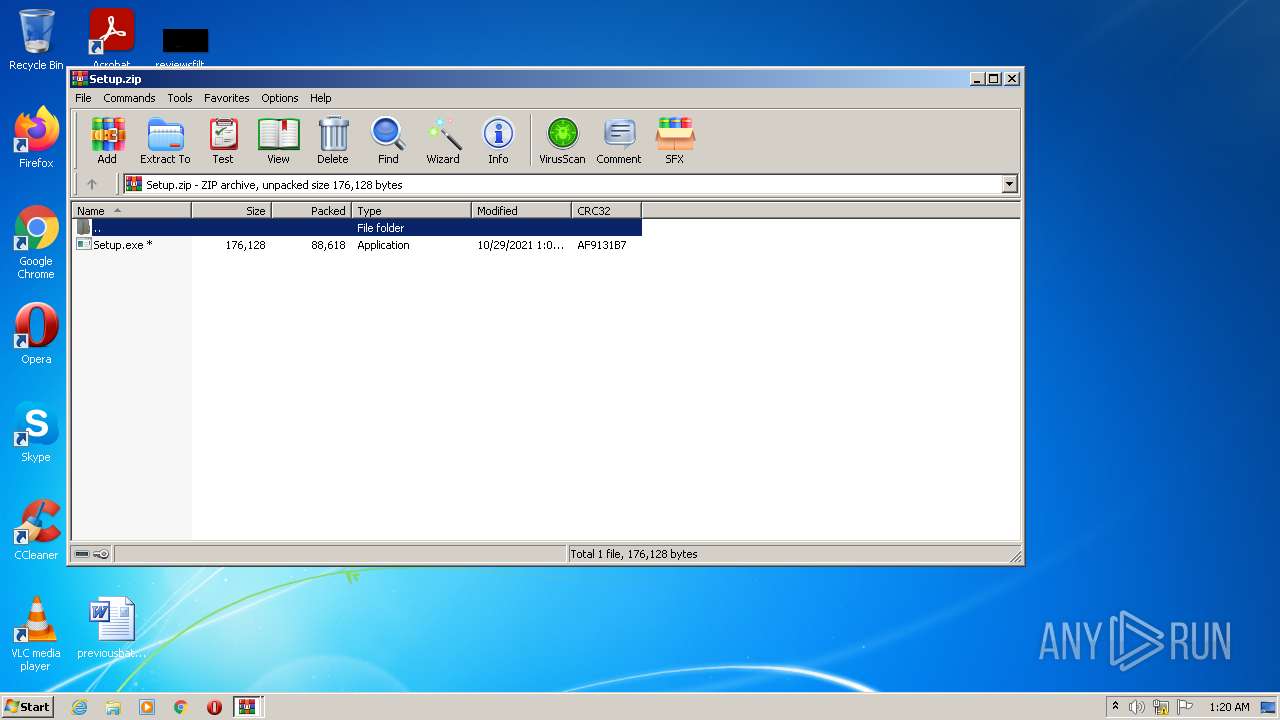
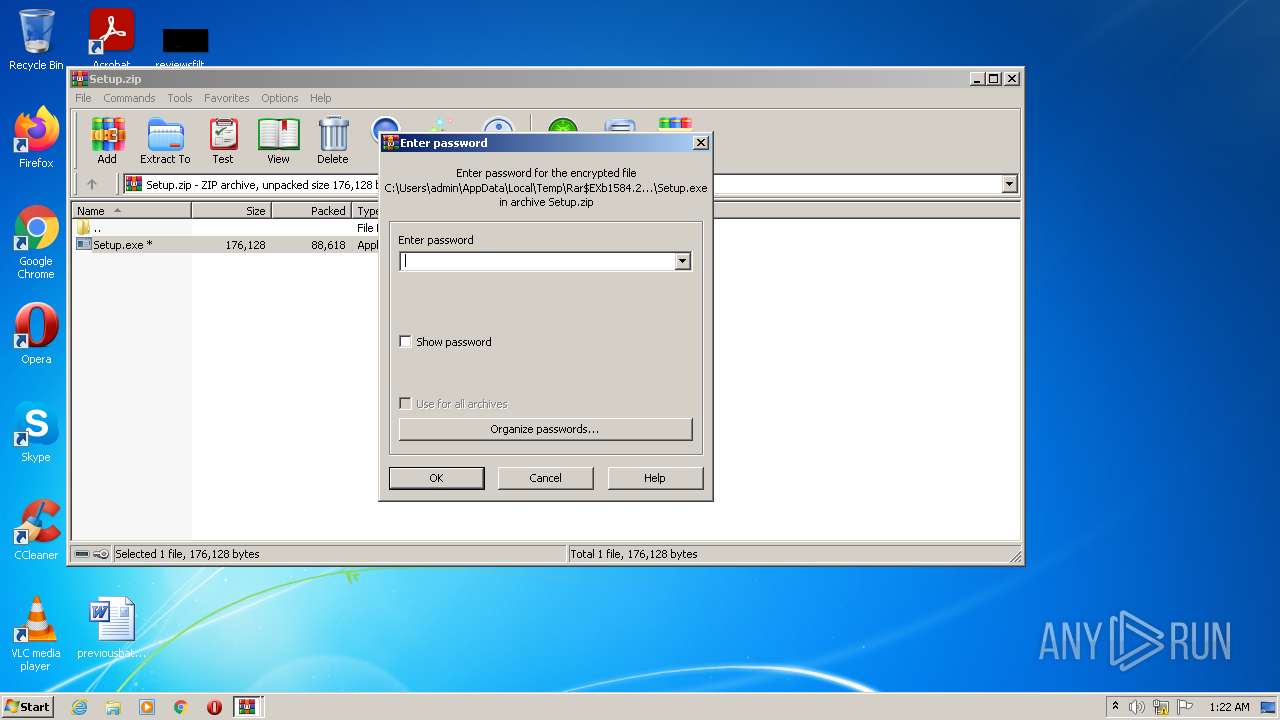
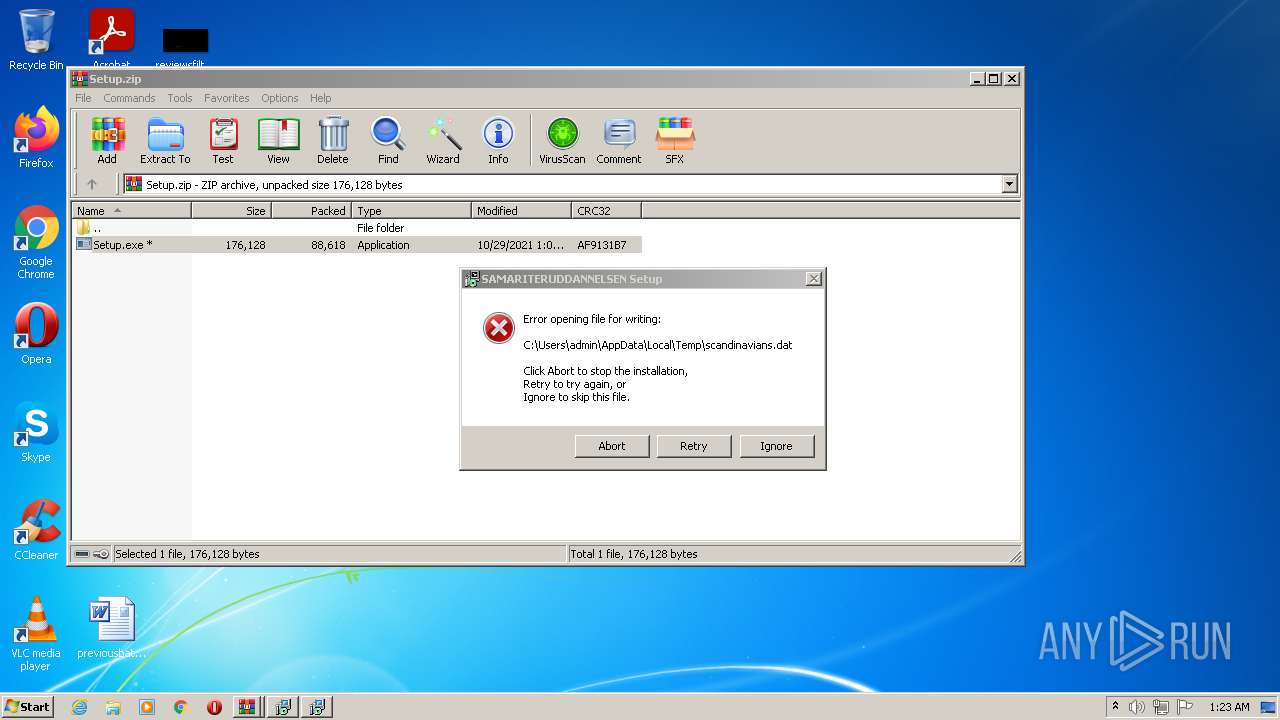
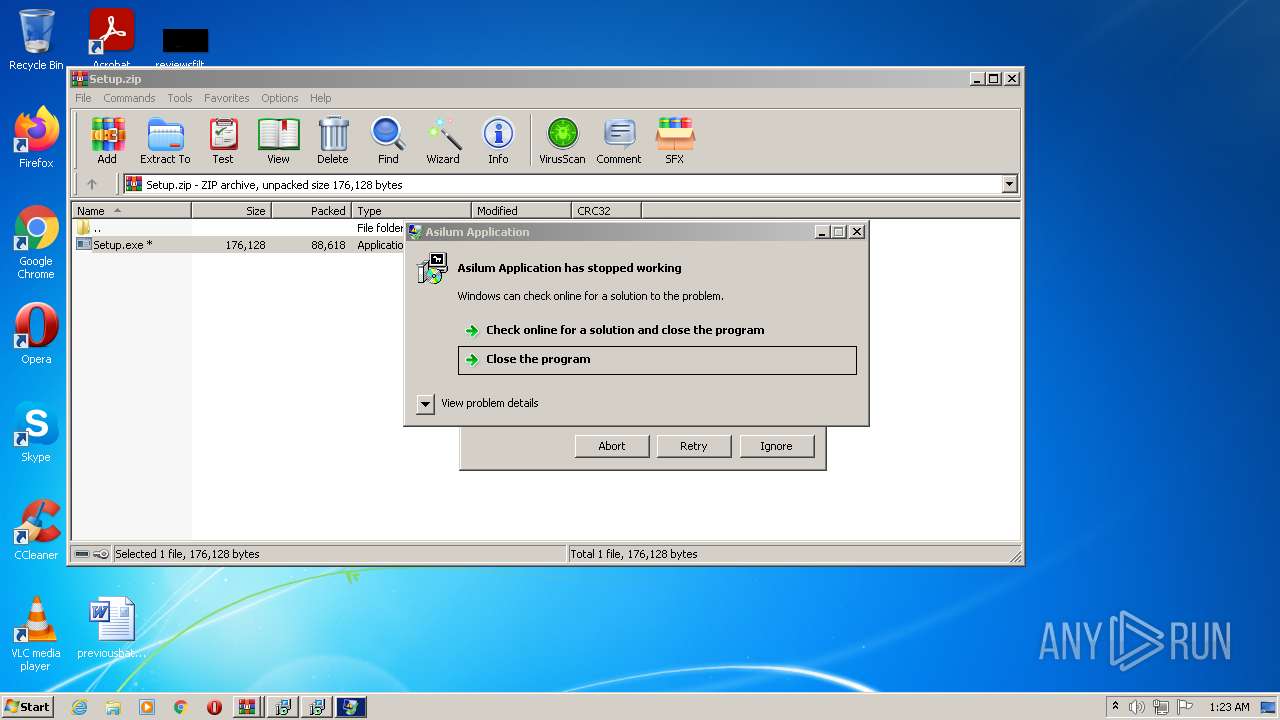
| File name: | EaseUS+Partition+Master+v16.5+(x64)+WinPE+Bootable+ISO.zip |
| Full analysis: | https://app.any.run/tasks/e605982a-3a2c-4803-b13b-3c6f3a00cbad |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | December 27, 2021, 01:20:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 074ECB04CE55D125FE5496D8703B1519 |
| SHA1: | 7F46AD3FD5477237C4EB1E89519EEA89153BCE21 |
| SHA256: | 3BB76F4859FAEA9EF4FE2ADD7E0999385B82E1B7B160981320DC94832556C036 |
| SSDEEP: | 1536:zdR38+ckL/DfxuX190ntOuhpWOvhSvdcXoWKzcuqc63nKjHamuJgdQm:3nDxuX1ylhhsd1nXqFnu6Lm |
MALICIOUS
Application was dropped or rewritten from another process
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3088)
- ElEMd1CxhRNZeDpKLkETdrkZ.exe (PID: 2336)
- Setup.exe (PID: 2928)
- Setup.exe (PID: 3552)
- Ef0crPgRczAgGzghRIBCZSM_.exe (PID: 3764)
- Q9E_G81uqw6phhYdkdj4r451.exe (PID: 4032)
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
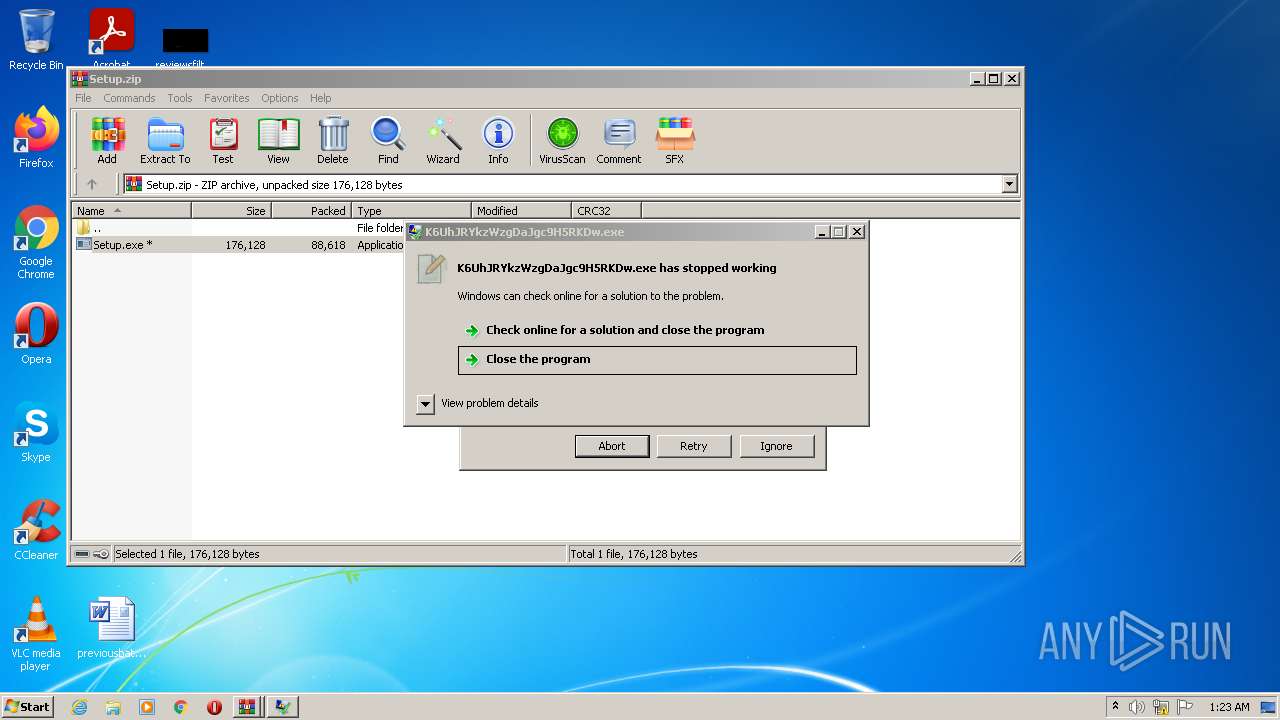
- K6UhJRYkzWzgDaJgc9H5RKDw.exe (PID: 2716)
- pJchOMzCqCmb4ysvN1ZygsuH.exe (PID: 2748)
- PJ3k324Fy5Lk7oA7Na5U9g7O.exe (PID: 2588)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- 3252117132521171.exe (PID: 2124)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- Wyshygyloqi.exe (PID: 3820)
- Wyshygyloqi.exe (PID: 4060)
- ezAwMuC9EjnY4UJW5vfffcle.exe (PID: 2940)
- Xaelifaelive.exe (PID: 388)
- Nuholaenysu.exe (PID: 1240)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
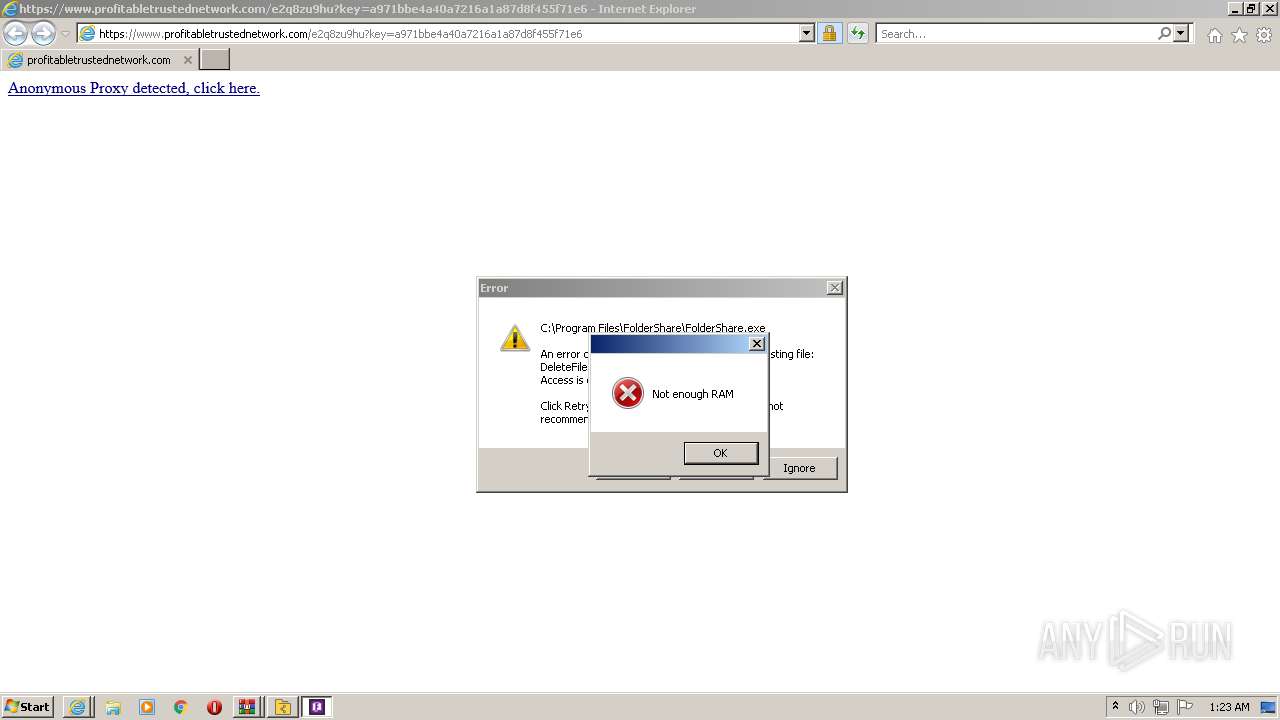
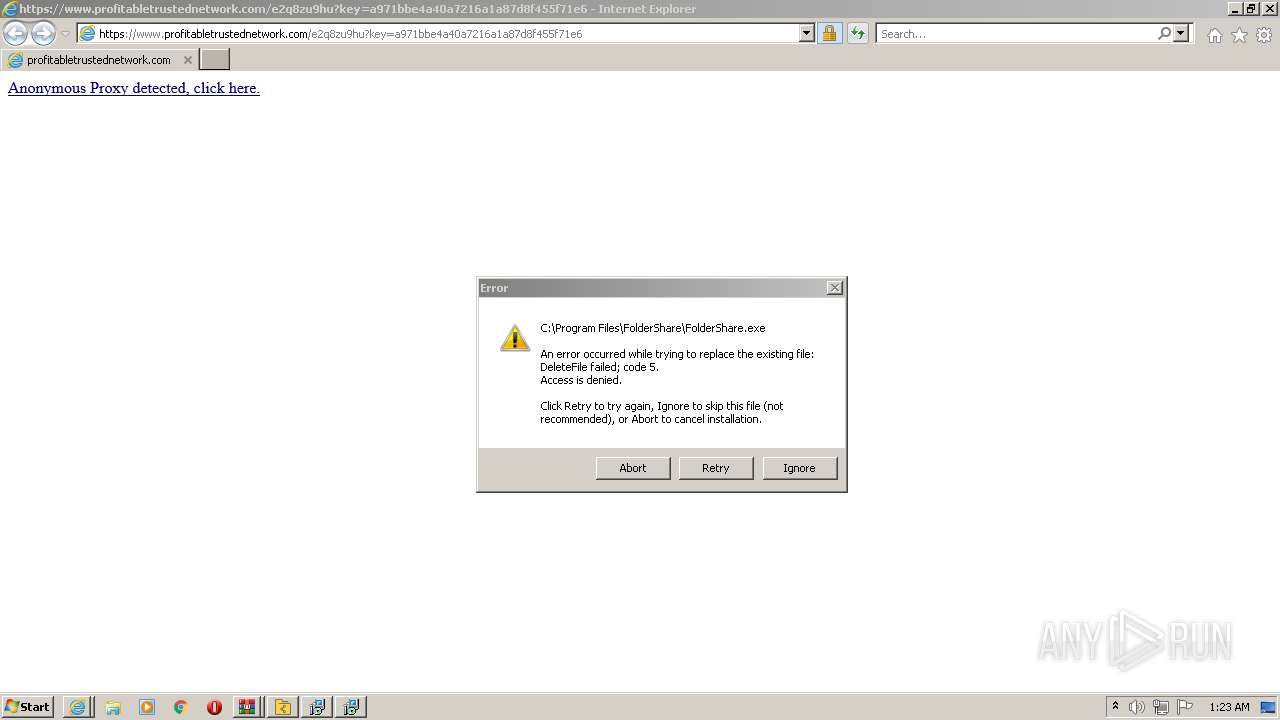
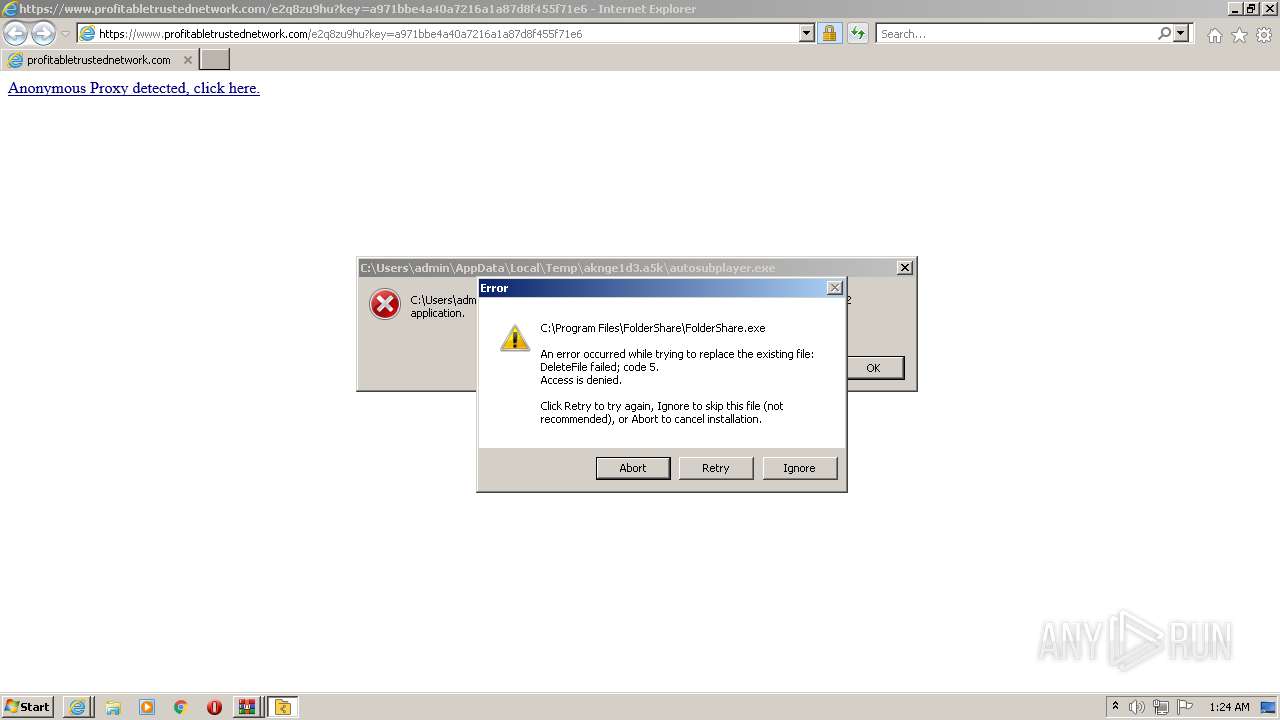
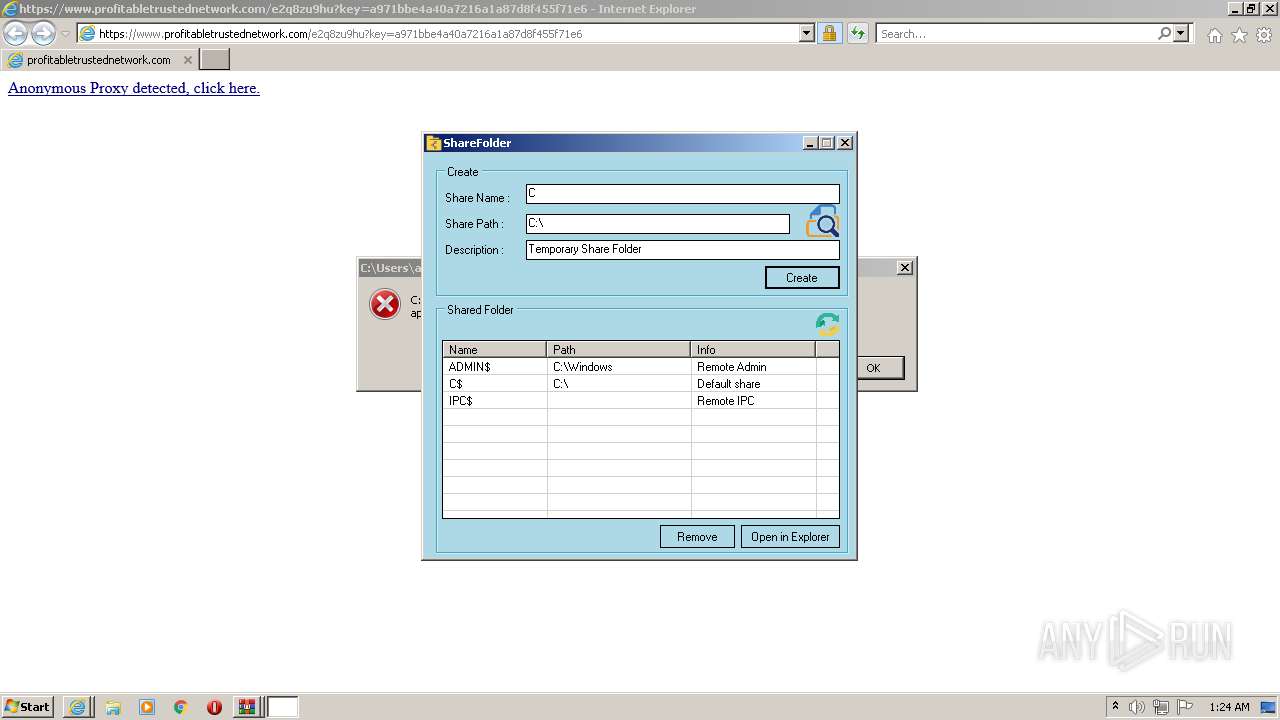
- foldershare.exe (PID: 456)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- foldershare.exe (PID: 492)
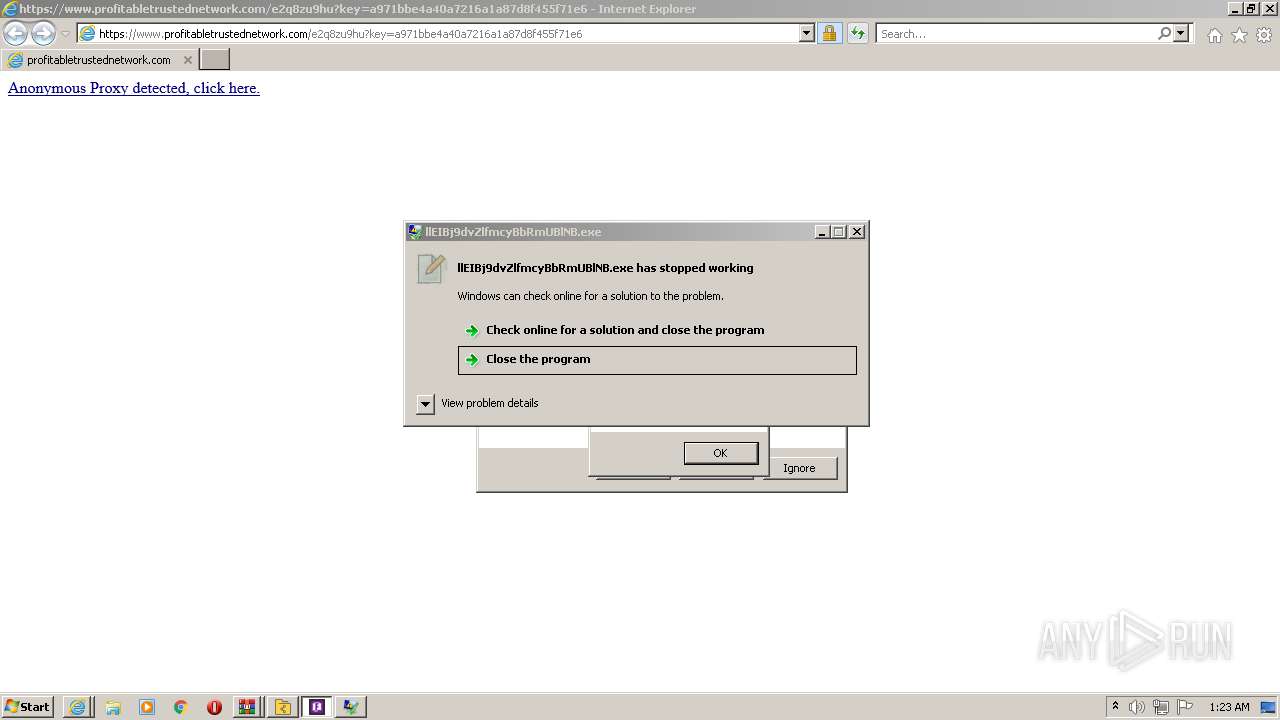
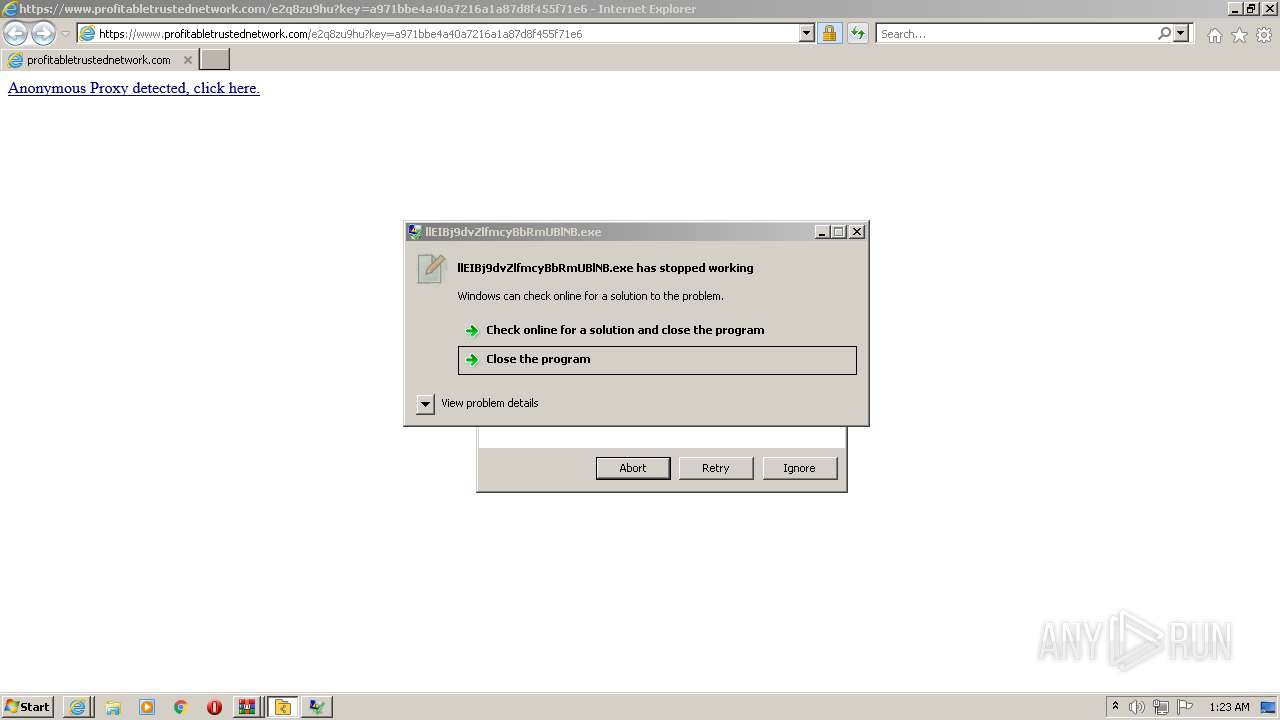
- llEIBj9dvZlfmcyBbRmUBlNB.exe (PID: 5224)
- vghSoREneeOWphSb7T71LI_s.exe (PID: 6868)
- lKZcDnrfU7pj0sN9fWuChskc.exe (PID: 6988)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 4852)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 756)
- installer.exe (PID: 4376)
- installer.exe (PID: 6508)
- random.exe (PID: 9316)
- Wycozhaecome.exe (PID: 7168)
- Boshohygaecae.exe (PID: 7404)
- random.exe (PID: 6884)
- 2270810.exe (PID: 2944)
- yangxiuying.exe (PID: 9168)
- yangxiuying.exe (PID: 7176)
- Setup.exe (PID: 3840)
- Install.exe (PID: 5028)
- askinstall42.exe (PID: 3012)
- installer.exe (PID: 8660)
- f.exe (PID: 4180)
- random.exe (PID: 2472)
- random.exe (PID: 5760)
- installer.exe (PID: 8684)
Actions looks like stealing of personal data
- svchost.exe (PID: 876)
- WinRAR.exe (PID: 1584)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- LzmwAqmV.exe (PID: 2196)
- 42d8f7b8-1c86-498b-b5aa-0d0b16bb44bc.exe (PID: 4976)
- cmd.exe (PID: 6660)
- Outlab01.exe (PID: 10172)
- Setup.exe (PID: 3840)
- Proxyupd.exe (PID: 10076)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- AppLaunch.exe (PID: 4620)
Disables Windows Defender
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
Changes settings of System certificates
- Setup.exe (PID: 3024)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Nuholaenysu.exe (PID: 1240)
- chrome.exe (PID: 3412)
Connects to CnC server
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- AppLaunch.exe (PID: 4620)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- md9_1sjm.exe (PID: 5684)
- 41e98be2-adf5-48f7-b0e0-0d049838b03d.exe (PID: 4468)
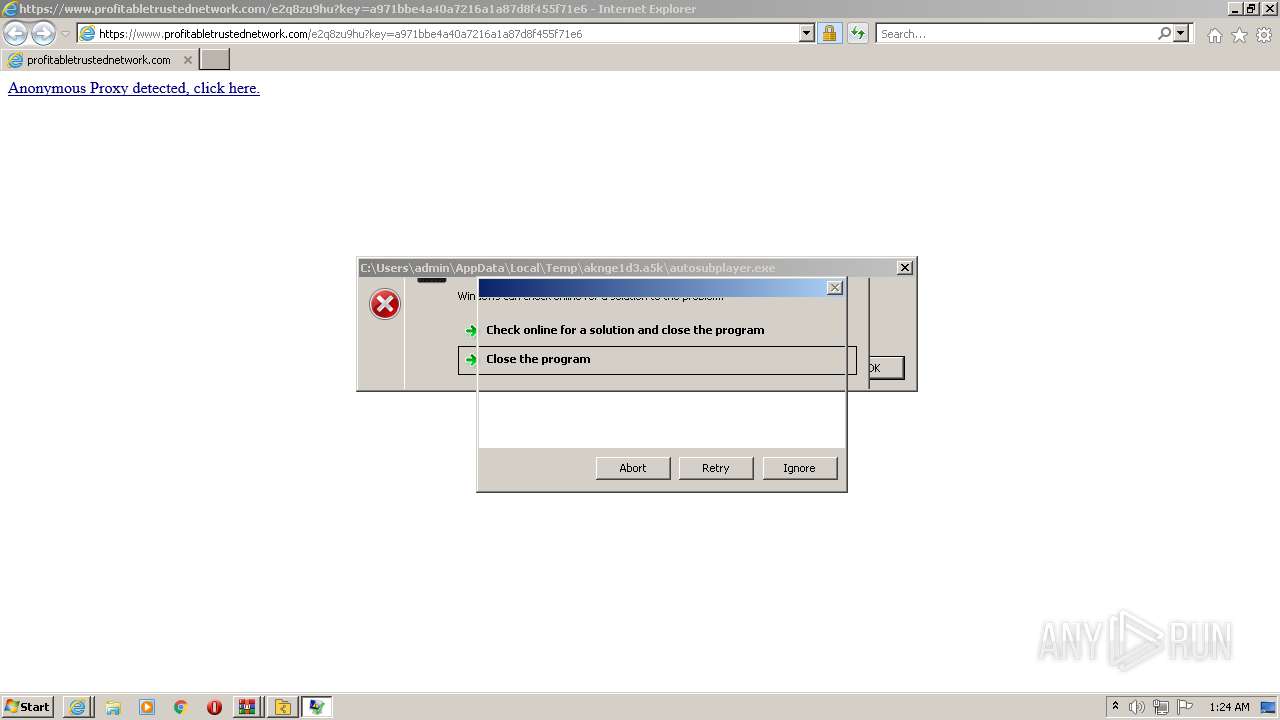
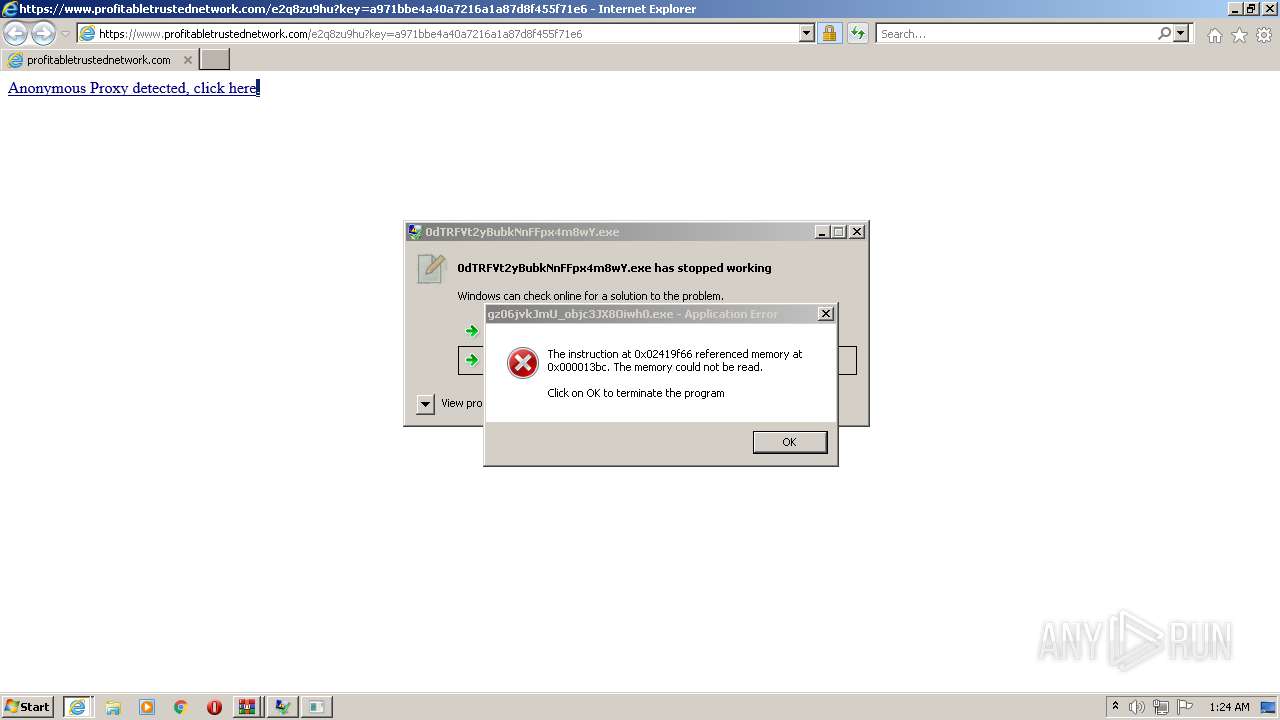
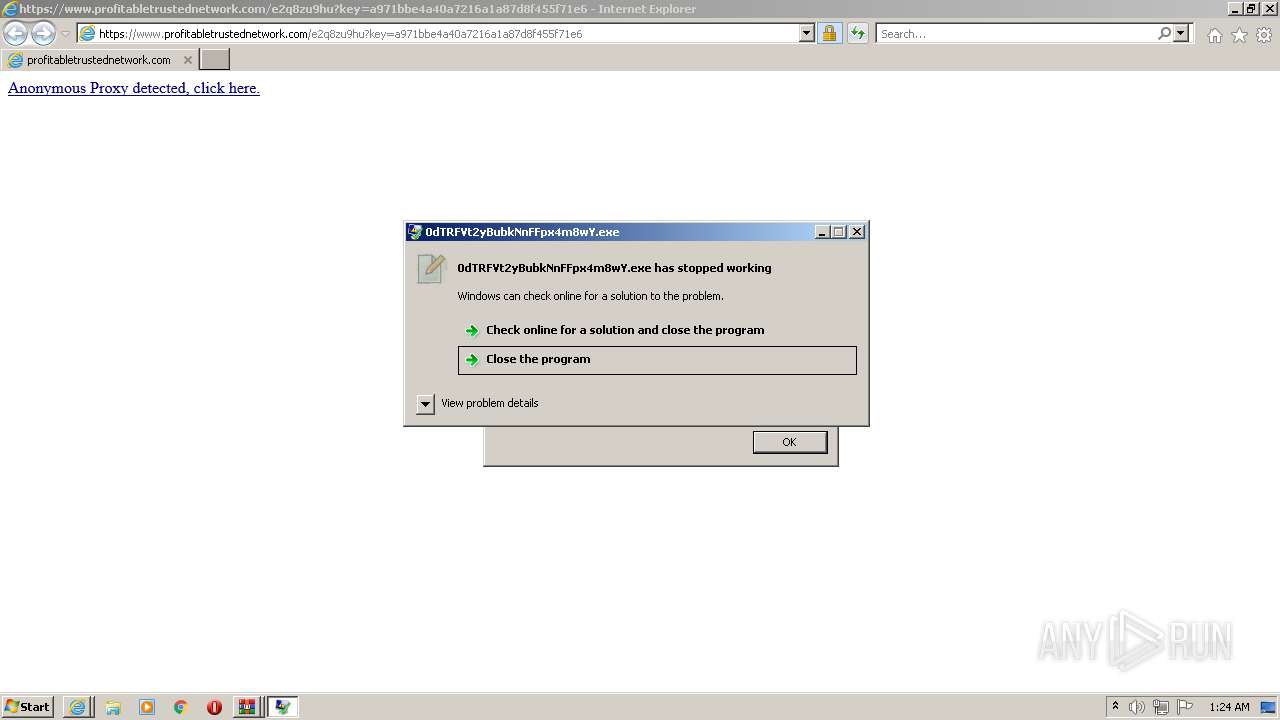
Drops executable file immediately after starts
- ElEMd1CxhRNZeDpKLkETdrkZ.exe (PID: 2336)
- Q9E_G81uqw6phhYdkdj4r451.exe (PID: 4032)
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- PJ3k324Fy5Lk7oA7Na5U9g7O.exe (PID: 2588)
- pJchOMzCqCmb4ysvN1ZygsuH.exe (PID: 2748)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
Loads dropped or rewritten executable
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- Q9E_G81uqw6phhYdkdj4r451.exe (PID: 4032)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- WerFault.exe (PID: 3604)
- Outlab01.exe (PID: 10172)
REDLINE was detected
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- AppLaunch.exe (PID: 4620)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- 41e98be2-adf5-48f7-b0e0-0d049838b03d.exe (PID: 4468)
Uses Task Scheduler to run other applications
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- Install.exe (PID: 5028)
Uses Task Scheduler to autorun other applications
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 584)
- schtasks.exe (PID: 1952)
- MsiExec.exe (PID: 7132)
- schtasks.exe (PID: 6704)
- schtasks.exe (PID: 5280)
- schtasks.exe (PID: 9948)
- svchost.exe (PID: 876)
VIDAR was detected
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Outlab01.exe (PID: 10172)
Stealing of credential data
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
Changes the autorun value in the registry
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
Steals credentials from Web Browsers
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- Outlab01.exe (PID: 10172)
- AppLaunch.exe (PID: 4620)
Runs injected code in another process
- rundll32.exe (PID: 5596)
- rundll32.exe (PID: 4380)
- rundll32.exe (PID: 7044)
Application was injected by another process
- svchost.exe (PID: 876)
Registers / Runs the DLL via REGSVR32.EXE
- acaWMbzUfCXTkWlKZUPnciF_.exe (PID: 5944)
Loads the Task Scheduler DLL interface
- schtasks.exe (PID: 2500)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 1248)
- WinRAR.exe (PID: 1584)
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- Ef0crPgRczAgGzghRIBCZSM_.exe (PID: 3764)
- Q9E_G81uqw6phhYdkdj4r451.exe (PID: 4032)
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- ElEMd1CxhRNZeDpKLkETdrkZ.exe (PID: 2336)
- K6UhJRYkzWzgDaJgc9H5RKDw.exe (PID: 2716)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- EcDpXKnyihU3lPRDXQU4CQRG.exe (PID: 3416)
- cmd.exe (PID: 588)
- PJ3k324Fy5Lk7oA7Na5U9g7O.exe (PID: 2588)
- pJchOMzCqCmb4ysvN1ZygsuH.exe (PID: 2748)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- dJW70TPBhg88Utq3oX9qOr5q.exe (PID: 2504)
- Bouderbela.exe (PID: 3416)
- Bouderbela.exe (PID: 1008)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- 3252117132521171.exe (PID: 2124)
- Wyshygyloqi.exe (PID: 4060)
- Nuholaenysu.exe (PID: 1240)
- Xaelifaelive.exe (PID: 388)
- Wyshygyloqi.exe (PID: 3820)
- foldershare.exe (PID: 456)
- foldershare.exe (PID: 492)
- foldershare.tmp (PID: 3664)
- foldershare.tmp (PID: 3252)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- FolderShare.exe (PID: 2664)
- ezAwMuC9EjnY4UJW5vfffcle.exe (PID: 2940)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- dg10x768J4Xvl7eYitBXGvVA.exe (PID: 2592)
- 49kyiytYIRHKNCaDq_Mjafgg.exe (PID: 4252)
- cmd.exe (PID: 2628)
- cmd.exe (PID: 4208)
- Install.exe (PID: 5180)
- Install.exe (PID: 5028)
- cmd.exe (PID: 5420)
- powershell.exe (PID: 5796)
- WMIC.exe (PID: 4076)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- pdCklnBKzox0uAWhJ7HCXrmD.exe (PID: 2264)
- powershell.exe (PID: 4660)
- WMIC.exe (PID: 6012)
- powershell.exe (PID: 4548)
- WMIC.exe (PID: 5024)
- powershell.exe (PID: 5036)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 4852)
- WMIC.exe (PID: 4056)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 756)
- llEIBj9dvZlfmcyBbRmUBlNB.exe (PID: 5224)
- tYb8JVCRCQVwz0yiMHiE1Oak.exe (PID: 5716)
- cmd.exe (PID: 5852)
- vghSoREneeOWphSb7T71LI_s.exe (PID: 6868)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- lKZcDnrfU7pj0sN9fWuChskc.exe (PID: 6988)
- vghSoREneeOWphSb7T71LI_s.tmp (PID: 7112)
- lKZcDnrfU7pj0sN9fWuChskc.tmp (PID: 6600)
- cmd.exe (PID: 5540)
- installer.exe (PID: 4376)
- sToriB34ieJP5moZGEiTjEB3.exe (PID: 9136)
- powershell.EXE (PID: 2320)
- skhUn7Sqcc_uurDy1JBayMmk.exe (PID: 7572)
- Bouderbela.exe (PID: 7948)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 7820)
- Bouderbela.exe (PID: 7832)
- acaWMbzUfCXTkWlKZUPnciF_.exe (PID: 5944)
- AppLaunch.exe (PID: 4620)
- cmd.exe (PID: 6256)
- 2270810.exe (PID: 2944)
- installer.exe (PID: 6508)
- cmd.exe (PID: 8556)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- cmd.exe (PID: 9004)
- random.exe (PID: 9316)
- random.exe (PID: 6884)
- LzmwAqmV.exe (PID: 2196)
- Wycozhaecome.exe (PID: 7168)
- Boshohygaecae.exe (PID: 7404)
- RobCleanerInstll33132.exe (PID: 9532)
- jli.exe (PID: 9728)
- Proxyupd.exe (PID: 10076)
- Outlab01.exe (PID: 10172)
- jli.exe (PID: 7620)
- inst.exe (PID: 7876)
- setup.exe (PID: 6616)
- askinstall25.exe (PID: 5304)
- chrome update.exe (PID: 2748)
- MyNotes Installation.exe (PID: 5852)
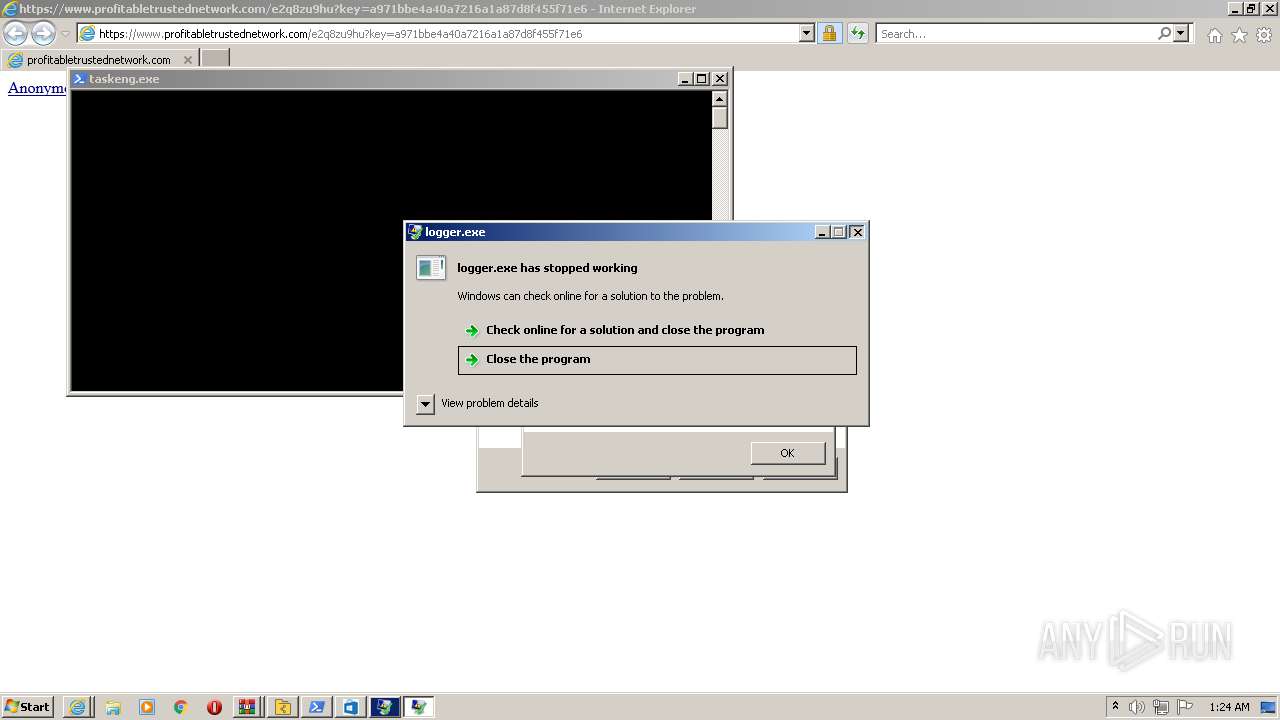
- logger.exe (PID: 8628)
- chrome1.exe (PID: 8020)
- chrome.exe (PID: 3412)
- cmd.exe (PID: 9200)
- chrome2.exe (PID: 4236)
- 42d8f7b8-1c86-498b-b5aa-0d0b16bb44bc.exe (PID: 4976)
- 5f0b7a81-e18b-43ab-89bd-6ddb21393f7f.exe (PID: 4420)
- cmd.exe (PID: 6660)
- Setup.exe (PID: 3840)
- yangxiuying.exe (PID: 9168)
- askinstall35.exe (PID: 9252)
- setup.exe (PID: 9308)
- md9_1sjm.exe (PID: 5684)
- yangxiuying.exe (PID: 7176)
- Cube_WW6.exe (PID: 8076)
- cmd.exe (PID: 4356)
- cmd.exe (PID: 6276)
- installer.exe (PID: 8660)
- askinstall42.exe (PID: 3012)
- f.exe (PID: 4180)
- cmd.exe (PID: 5312)
- cmd.exe (PID: 9504)
- 41e98be2-adf5-48f7-b0e0-0d049838b03d.exe (PID: 4468)
- cmd.exe (PID: 5672)
- random.exe (PID: 2472)
- cmd.exe (PID: 9464)
- cmd.exe (PID: 6972)
- installer.exe (PID: 8684)
- random.exe (PID: 5760)
Reads the computer name
- WinRAR.exe (PID: 1584)
- WinRAR.exe (PID: 1248)
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- Q9E_G81uqw6phhYdkdj4r451.exe (PID: 4032)
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- EcDpXKnyihU3lPRDXQU4CQRG.exe (PID: 3416)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- dJW70TPBhg88Utq3oX9qOr5q.exe (PID: 2504)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- 3252117132521171.exe (PID: 2124)
- Wyshygyloqi.exe (PID: 3820)
- Wyshygyloqi.exe (PID: 4060)
- Xaelifaelive.exe (PID: 388)
- Nuholaenysu.exe (PID: 1240)
- foldershare.tmp (PID: 3664)
- foldershare.tmp (PID: 3252)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- FolderShare.exe (PID: 2664)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- Install.exe (PID: 5028)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- powershell.exe (PID: 5796)
- WMIC.exe (PID: 4076)
- pdCklnBKzox0uAWhJ7HCXrmD.exe (PID: 2264)
- powershell.exe (PID: 4660)
- WMIC.exe (PID: 6012)
- powershell.exe (PID: 4548)
- WMIC.exe (PID: 5024)
- powershell.exe (PID: 5036)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 4852)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 756)
- WMIC.exe (PID: 4056)
- tYb8JVCRCQVwz0yiMHiE1Oak.exe (PID: 5716)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- vghSoREneeOWphSb7T71LI_s.tmp (PID: 7112)
- lKZcDnrfU7pj0sN9fWuChskc.tmp (PID: 6600)
- installer.exe (PID: 4376)
- dg10x768J4Xvl7eYitBXGvVA.exe (PID: 2592)
- sToriB34ieJP5moZGEiTjEB3.exe (PID: 9136)
- powershell.EXE (PID: 2320)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 7820)
- Bouderbela.exe (PID: 7832)
- acaWMbzUfCXTkWlKZUPnciF_.exe (PID: 5944)
- Bouderbela.exe (PID: 7948)
- AppLaunch.exe (PID: 4620)
- 2270810.exe (PID: 2944)
- installer.exe (PID: 6508)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- random.exe (PID: 9316)
- random.exe (PID: 6884)
- Wycozhaecome.exe (PID: 7168)
- LzmwAqmV.exe (PID: 2196)
- Boshohygaecae.exe (PID: 7404)
- jli.exe (PID: 7620)
- jli.exe (PID: 9728)
- askinstall25.exe (PID: 5304)
- RobCleanerInstll33132.exe (PID: 9532)
- Proxyupd.exe (PID: 10076)
- chrome update.exe (PID: 2748)
- setup.exe (PID: 6616)
- logger.exe (PID: 8628)
- MyNotes Installation.exe (PID: 5852)
- chrome1.exe (PID: 8020)
- chrome.exe (PID: 3412)
- chrome2.exe (PID: 4236)
- 42d8f7b8-1c86-498b-b5aa-0d0b16bb44bc.exe (PID: 4976)
- 5f0b7a81-e18b-43ab-89bd-6ddb21393f7f.exe (PID: 4420)
- Outlab01.exe (PID: 10172)
- Setup.exe (PID: 3840)
- askinstall35.exe (PID: 9252)
- yangxiuying.exe (PID: 9168)
- yangxiuying.exe (PID: 7176)
- setup.exe (PID: 9308)
- md9_1sjm.exe (PID: 5684)
- Cube_WW6.exe (PID: 8076)
- installer.exe (PID: 8660)
- askinstall42.exe (PID: 3012)
- 41e98be2-adf5-48f7-b0e0-0d049838b03d.exe (PID: 4468)
- random.exe (PID: 2472)
- f.exe (PID: 4180)
- random.exe (PID: 5760)
- installer.exe (PID: 8684)
Checks for external IP
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
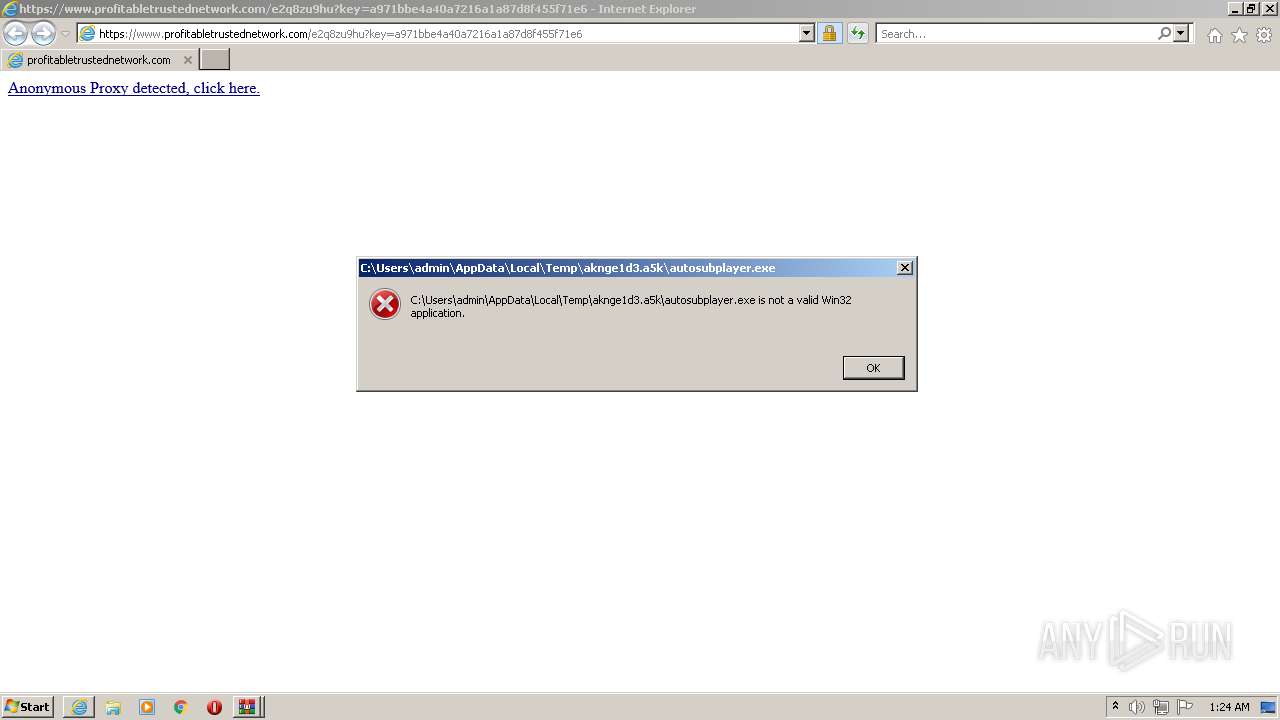
Executable content was dropped or overwritten
- Setup.exe (PID: 3024)
- WinRAR.exe (PID: 1584)
- ElEMd1CxhRNZeDpKLkETdrkZ.exe (PID: 2336)
- Setup.exe (PID: 3552)
- Q9E_G81uqw6phhYdkdj4r451.exe (PID: 4032)
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- pJchOMzCqCmb4ysvN1ZygsuH.exe (PID: 2748)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- PJ3k324Fy5Lk7oA7Na5U9g7O.exe (PID: 2588)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- dJW70TPBhg88Utq3oX9qOr5q.exe (PID: 2504)
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- Nuholaenysu.exe (PID: 1240)
- Xaelifaelive.exe (PID: 388)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- Install.exe (PID: 5028)
- RobCleanerInstll33132.exe (PID: 9532)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- foldershare.tmp (PID: 3252)
Application launched itself
- WinRAR.exe (PID: 1248)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 4852)
- msiexec.exe (PID: 4416)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 7820)
- random.exe (PID: 9316)
- jli.exe (PID: 9728)
- yangxiuying.exe (PID: 9168)
- random.exe (PID: 2472)
Adds / modifies Windows certificates
- Setup.exe (PID: 3024)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Nuholaenysu.exe (PID: 1240)
- chrome.exe (PID: 3412)
Drops a file that was compiled in debug mode
- Setup.exe (PID: 3552)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Bouderbela.exe (PID: 3416)
- Bouderbela.exe (PID: 1008)
- Nuholaenysu.exe (PID: 1240)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- Xaelifaelive.exe (PID: 388)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
Drops a file with a compile date too recent
- Setup.exe (PID: 3552)
- 4c51caQPI4UqwnOZ3lxgNRTI.exe (PID: 3640)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- dJW70TPBhg88Utq3oX9qOr5q.exe (PID: 2504)
- Nuholaenysu.exe (PID: 1240)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- RobCleanerInstll33132.exe (PID: 9532)
- Xaelifaelive.exe (PID: 388)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
Starts CMD.EXE for commands execution
- EcDpXKnyihU3lPRDXQU4CQRG.exe (PID: 3416)
- Nuholaenysu.exe (PID: 1240)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Install.exe (PID: 5028)
- forfiles.exe (PID: 4220)
- forfiles.exe (PID: 3124)
- forfiles.exe (PID: 3828)
- forfiles.exe (PID: 2492)
- forfiles.exe (PID: 6564)
- forfiles.exe (PID: 6704)
- Xaelifaelive.exe (PID: 388)
- tYb8JVCRCQVwz0yiMHiE1Oak.exe (PID: 5716)
- setup.exe (PID: 6616)
- Boshohygaecae.exe (PID: 7404)
- setup.exe (PID: 9308)
- Outlab01.exe (PID: 10172)
- Wycozhaecome.exe (PID: 7168)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 588)
- cmd.exe (PID: 4208)
- cmd.exe (PID: 5852)
- MsiExec.exe (PID: 8344)
- cmd.exe (PID: 9200)
- cmd.exe (PID: 4356)
- cmd.exe (PID: 5672)
Drops a file with too old compile date
- Setup.exe (PID: 3552)
- PJ3k324Fy5Lk7oA7Na5U9g7O.exe (PID: 2588)
- pJchOMzCqCmb4ysvN1ZygsuH.exe (PID: 2748)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- Nuholaenysu.exe (PID: 1240)
- foldershare.tmp (PID: 3252)
Creates a directory in Program Files
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- foldershare.tmp (PID: 3664)
- msiexec.exe (PID: 4416)
- Setup.exe (PID: 3840)
Creates files in the program directory
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- WerFault.exe (PID: 3604)
- msiexec.exe (PID: 4416)
- Setup.exe (PID: 3840)
- Outlab01.exe (PID: 10172)
- svchost.exe (PID: 876)
Reads the Windows organization settings
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- foldershare.tmp (PID: 3664)
- foldershare.tmp (PID: 3252)
- vghSoREneeOWphSb7T71LI_s.tmp (PID: 7112)
- lKZcDnrfU7pj0sN9fWuChskc.tmp (PID: 6600)
- installer.exe (PID: 4376)
- msiexec.exe (PID: 4416)
Reads Windows owner or organization settings
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- foldershare.tmp (PID: 3664)
- foldershare.tmp (PID: 3252)
- vghSoREneeOWphSb7T71LI_s.tmp (PID: 7112)
- lKZcDnrfU7pj0sN9fWuChskc.tmp (PID: 6600)
- installer.exe (PID: 4376)
- msiexec.exe (PID: 4416)
Reads Environment values
- dJW70TPBhg88Utq3oX9qOr5q.exe (PID: 2504)
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- Wyshygyloqi.exe (PID: 3820)
- Wyshygyloqi.exe (PID: 4060)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Nuholaenysu.exe (PID: 1240)
- Xaelifaelive.exe (PID: 388)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- pdCklnBKzox0uAWhJ7HCXrmD.exe (PID: 2264)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- installer.exe (PID: 4376)
- MsiExec.exe (PID: 4308)
- MsiExec.exe (PID: 8344)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- Bouderbela.exe (PID: 7832)
- Bouderbela.exe (PID: 7948)
- Boshohygaecae.exe (PID: 7404)
- Wycozhaecome.exe (PID: 7168)
- RobCleanerInstll33132.exe (PID: 9532)
- AppLaunch.exe (PID: 4620)
- chrome update.exe (PID: 2748)
- logger.exe (PID: 8628)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- chrome.exe (PID: 3412)
- chrome1.exe (PID: 8020)
- chrome2.exe (PID: 4236)
- Proxyupd.exe (PID: 10076)
- 42d8f7b8-1c86-498b-b5aa-0d0b16bb44bc.exe (PID: 4976)
- Outlab01.exe (PID: 10172)
Creates files in the Windows directory
- svchost.exe (PID: 876)
- schtasks.exe (PID: 2500)
Reads the cookies of Google Chrome
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- AppLaunch.exe (PID: 4620)
Reads the cookies of Mozilla Firefox
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- AppLaunch.exe (PID: 4620)
Creates files in the user directory
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- installer.exe (PID: 4376)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- powershell.EXE (PID: 2320)
- f.exe (PID: 4180)
Searches for installed software
- RBf87uuH6_mnjcM1ZmuHmocI.exe (PID: 684)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- gKGi3YMnTHQFfECvW0hRvley.exe (PID: 1976)
- 3XP2DSF86macEpvlIsIJBG2h.exe (PID: 3432)
- foldershare.tmp (PID: 3252)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- hhcNvPPSmcWzO3K8ZKWDT0H9.exe (PID: 6104)
- WXNM6CCc299CENNTXOdZfFH6.exe (PID: 8016)
- Outlab01.exe (PID: 10172)
- 42d8f7b8-1c86-498b-b5aa-0d0b16bb44bc.exe (PID: 4976)
- cRRjQiD_Bxu1hwbS2DAyqG25.exe (PID: 5040)
- AppLaunch.exe (PID: 4620)
Starts itself from another location
- 0e1c3664-d80e-4fbf-8a10-5a1146d7cc00.exe (PID: 2908)
- 49kyiytYIRHKNCaDq_Mjafgg.exe (PID: 4252)
Reads CPU info
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Outlab01.exe (PID: 10172)
Starts Internet Explorer
- Wyshygyloqi.exe (PID: 4060)
- Wyshygyloqi.exe (PID: 3820)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 1684)
Starts CMD.EXE for self-deleting
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- Outlab01.exe (PID: 10172)
Executes PowerShell scripts
- cmd.exe (PID: 5624)
- cmd.exe (PID: 4848)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 5296)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 6908)
- cmd.exe (PID: 7200)
Executed as Windows Service
- msiexec.exe (PID: 4416)
Starts Microsoft Installer
- installer.exe (PID: 4376)
Executed via Task Scheduler
- powershell.EXE (PID: 2320)
PowerShell script executed
- powershell.EXE (PID: 2320)
Executed via WMI
- rundll32.exe (PID: 5596)
- rundll32.exe (PID: 4380)
- rundll32.exe (PID: 7044)
Reads the date of Windows installation
- powershell.EXE (PID: 2320)
Creates a software uninstall entry
- msiexec.exe (PID: 4416)
- Setup.exe (PID: 3840)
Reads default file associations for system extensions
- 2270810.exe (PID: 2944)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 520)
Removes files from Windows directory
- svchost.exe (PID: 876)
Executes application which crashes
- chrome2.exe (PID: 4236)
- chrome1.exe (PID: 8020)
INFO
Reads settings of System Certificates
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- 2Ld68_MTjyZ03jXmPN0v7Yu3.exe (PID: 3828)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- dJW70TPBhg88Utq3oX9qOr5q.exe (PID: 2504)
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- Wyshygyloqi.exe (PID: 3820)
- Wyshygyloqi.exe (PID: 4060)
- 405104d7-1ff3-44c2-bb34-f1e1b709b759.exe (PID: 3720)
- Nuholaenysu.exe (PID: 1240)
- Xaelifaelive.exe (PID: 388)
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 1684)
- df244149-12bb-493b-9189-a9beda885c87.exe (PID: 2716)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 572)
- 167e9098-496c-45c3-8e84-34db442fa9bc.exe (PID: 2512)
- pdCklnBKzox0uAWhJ7HCXrmD.exe (PID: 2264)
- K6WtD8S_9UIOZjaWwYPfQLgT.exe (PID: 756)
- installer.exe (PID: 4376)
- msiexec.exe (PID: 4416)
- MsiExec.exe (PID: 8344)
- Bouderbela.exe (PID: 7832)
- Bouderbela.exe (PID: 7948)
- random.exe (PID: 6884)
- Boshohygaecae.exe (PID: 7404)
- Wycozhaecome.exe (PID: 7168)
- jli.exe (PID: 7620)
- chrome update.exe (PID: 2748)
- askinstall25.exe (PID: 5304)
- RobCleanerInstll33132.exe (PID: 9532)
- Outlab01.exe (PID: 10172)
- chrome.exe (PID: 3412)
- chrome2.exe (PID: 4236)
- chrome1.exe (PID: 8020)
- MyNotes Installation.exe (PID: 5852)
- logger.exe (PID: 8628)
- yangxiuying.exe (PID: 7176)
- Cube_WW6.exe (PID: 8076)
- askinstall42.exe (PID: 3012)
- random.exe (PID: 5760)
- f.exe (PID: 4180)
- 42d8f7b8-1c86-498b-b5aa-0d0b16bb44bc.exe (PID: 4976)
Checks Windows Trust Settings
- Setup.exe (PID: 3024)
- Setup.exe (PID: 3552)
- 2dAtfMfiuAk66GgckxVitW9M.exe (PID: 2700)
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 1684)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 572)
- powershell.exe (PID: 5796)
- powershell.exe (PID: 4660)
- powershell.exe (PID: 4548)
- powershell.exe (PID: 5036)
- installer.exe (PID: 4376)
- msiexec.exe (PID: 4416)
- MsiExec.exe (PID: 8344)
- askinstall25.exe (PID: 5304)
- Outlab01.exe (PID: 10172)
- MyNotes Installation.exe (PID: 5852)
- powershell.EXE (PID: 2320)
- Cube_WW6.exe (PID: 8076)
- askinstall42.exe (PID: 3012)
- f.exe (PID: 4180)
Reads the computer name
- taskkill.exe (PID: 2248)
- schtasks.exe (PID: 584)
- schtasks.exe (PID: 1952)
- WerFault.exe (PID: 3604)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 1684)
- taskkill.exe (PID: 4720)
- taskkill.exe (PID: 4444)
- msiexec.exe (PID: 4416)
- MsiExec.exe (PID: 4308)
- msiexec.exe (PID: 6532)
- MsiExec.exe (PID: 8344)
- taskkill.exe (PID: 8716)
- schtasks.exe (PID: 6704)
- MsiExec.exe (PID: 7132)
- schtasks.exe (PID: 5280)
- rundll32.exe (PID: 5596)
- control.exe (PID: 520)
- taskkill.exe (PID: 6976)
- schtasks.exe (PID: 9948)
- rundll32.exe (PID: 4380)
- schtasks.exe (PID: 2500)
- taskkill.exe (PID: 8208)
- rundll32.exe (PID: 7044)
- taskkill.exe (PID: 6036)
- gpupdate.exe (PID: 3172)
Checks supported languages
- taskkill.exe (PID: 2248)
- schtasks.exe (PID: 584)
- schtasks.exe (PID: 1952)
- svchost.exe (PID: 876)
- WerFault.exe (PID: 3604)
- iexplore.exe (PID: 572)
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 1684)
- iexplore.exe (PID: 3984)
- taskkill.exe (PID: 4720)
- timeout.exe (PID: 5168)
- forfiles.exe (PID: 4220)
- cmd.exe (PID: 5624)
- forfiles.exe (PID: 3124)
- cmd.exe (PID: 4848)
- forfiles.exe (PID: 3828)
- cmd.exe (PID: 4572)
- forfiles.exe (PID: 2492)
- cmd.exe (PID: 5296)
- taskkill.exe (PID: 4444)
- forfiles.exe (PID: 6564)
- forfiles.exe (PID: 6704)
- cmd.exe (PID: 6908)
- reg.exe (PID: 7008)
- cmd.exe (PID: 7200)
- reg.exe (PID: 7292)
- msiexec.exe (PID: 4416)
- MsiExec.exe (PID: 4308)
- MsiExec.exe (PID: 8344)
- taskkill.exe (PID: 8716)
- msiexec.exe (PID: 6532)
- MsiExec.exe (PID: 7132)
- schtasks.exe (PID: 6704)
- schtasks.exe (PID: 5280)
- rundll32.exe (PID: 5596)
- regsvr32.exe (PID: 9028)
- control.exe (PID: 520)
- rundll32.exe (PID: 5928)
- taskkill.exe (PID: 6976)
- schtasks.exe (PID: 9948)
- rundll32.exe (PID: 4380)
- ntvdm.exe (PID: 5988)
- schtasks.exe (PID: 2500)
- ntvdm.exe (PID: 7116)
- taskkill.exe (PID: 8208)
- rundll32.exe (PID: 7044)
- taskkill.exe (PID: 6036)
- gpupdate.exe (PID: 3172)
- timeout.exe (PID: 7468)
Application was dropped or rewritten from another process
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- vghSoREneeOWphSb7T71LI_s.tmp (PID: 7112)
- lKZcDnrfU7pj0sN9fWuChskc.tmp (PID: 6600)
- Bouderbela.exe (PID: 7832)
- Bouderbela.exe (PID: 7948)
Loads dropped or rewritten executable
- PJ3k324Fy5Lk7oA7Na5U9g7O.tmp (PID: 2352)
- pJchOMzCqCmb4ysvN1ZygsuH.tmp (PID: 1032)
- foldershare.tmp (PID: 3252)
- foldershare.tmp (PID: 3664)
- vghSoREneeOWphSb7T71LI_s.tmp (PID: 7112)
- lKZcDnrfU7pj0sN9fWuChskc.tmp (PID: 6600)
Creates files in the program directory
- Bouderbela.exe (PID: 1008)
- Bouderbela.exe (PID: 3416)
- foldershare.tmp (PID: 3664)
- foldershare.tmp (PID: 3252)
Changes internet zones settings
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 572)
Application launched itself
- iexplore.exe (PID: 2300)
- iexplore.exe (PID: 572)
Creates a software uninstall entry
- foldershare.tmp (PID: 3664)
Creates files in the user directory
- iexplore.exe (PID: 3984)
Reads internet explorer settings
- iexplore.exe (PID: 3984)
- iexplore.exe (PID: 1684)
Dropped object may contain Bitcoin addresses
- 4akRWxwrYAC8lcXso9jEasou.exe (PID: 3016)
Check for Java to be installed
- MsiExec.exe (PID: 4308)
- MsiExec.exe (PID: 8344)
Reads Microsoft Office registry keys
- MsiExec.exe (PID: 4308)
- MsiExec.exe (PID: 8344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Setup/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:09:11 22:15:01 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
280
Monitored processes
180
Malicious processes
57
Suspicious processes
19
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Users\admin\AppData\Local\Temp\13-2405d-0b8-7bda3-8007e10b75c5a\Xaelifaelive.exe" | C:\Users\admin\AppData\Local\Temp\13-2405d-0b8-7bda3-8007e10b75c5a\Xaelifaelive.exe | Bouderbela.exe | ||||||||||||
User: admin Company: degla87760_art_ Integrity Level: HIGH Description: degla87760_art_ Exit code: 0 Version: 2.2.1.2 Modules
| |||||||||||||||
| 456 | "C:\Program Files\Windows Portable Devices\BHIKKHODGN\foldershare.exe" /VERYSILENT | C:\Program Files\Windows Portable Devices\BHIKKHODGN\foldershare.exe | — | Bouderbela.exe | |||||||||||
User: admin Company: FolderShare Integrity Level: HIGH Description: FolderShare Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 492 | "C:\Program Files\Microsoft\WYVFZKZWEZ\foldershare.exe" /VERYSILENT | C:\Program Files\Microsoft\WYVFZKZWEZ\foldershare.exe | — | Bouderbela.exe | |||||||||||
User: admin Company: FolderShare Integrity Level: HIGH Description: FolderShare Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 520 | "C:\Windows\System32\control.exe" "C:\Users\admin\AppData\Local\Temp\EdRGQQA5.cPl", | C:\Windows\System32\control.exe | — | 2270810.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.profitabletrustednetwork.com/e2q8zu9hu?key=a971bbe4a40a7216a1a87d8f455f71e6 | C:\Program Files\Internet Explorer\iexplore.exe | Wyshygyloqi.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 584 | schtasks /create /f /RU "admin" /tr "C:\Program Files\PowerControl\PowerControl_Svc.exe" /tn "PowerControl HR" /sc HOURLY /rl HIGHEST | C:\Windows\system32\schtasks.exe | — | 2Ld68_MTjyZ03jXmPN0v7Yu3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 588 | "C:\Windows\System32\cmd.exe" /c taskkill /im "EcDpXKnyihU3lPRDXQU4CQRG.exe" /f & erase "C:\Users\admin\Pictures\Adobe Films\EcDpXKnyihU3lPRDXQU4CQRG.exe" & exit | C:\Windows\System32\cmd.exe | — | EcDpXKnyihU3lPRDXQU4CQRG.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 684 | "C:\Users\admin\Pictures\Adobe Films\RBf87uuH6_mnjcM1ZmuHmocI.exe" | C:\Users\admin\Pictures\Adobe Films\RBf87uuH6_mnjcM1ZmuHmocI.exe | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 756 | "C:\Users\admin\Pictures\Adobe Films\K6WtD8S_9UIOZjaWwYPfQLgT.exe" -u | C:\Users\admin\Pictures\Adobe Films\K6WtD8S_9UIOZjaWwYPfQLgT.exe | K6WtD8S_9UIOZjaWwYPfQLgT.exe | ||||||||||||
User: admin Company: initool Integrity Level: HIGH Description: initool Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 876 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\system32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
224 416
Read events
221 878
Write events
2 481
Delete events
57
Modification events
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EaseUS+Partition+Master+v16.5+(x64)+WinPE+Bootable+ISO.zip | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1248) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
92
Suspicious files
81
Text files
78
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3024 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\PL_Client[1].bmp | binary | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\Documents\T9aZunTSaNJLBVfIkgF5mtQo.dll | binary | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_811809BE12AFE5624F00A379DF595152 | der | |
MD5:— | SHA256:— | |||
| 1248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1248.17429\Setup.zip | compressed | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\NiceProcessX32[1].bmp | executable | |
MD5:— | SHA256:— | |||
| 876 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 3024 | Setup.exe | C:\Users\admin\Pictures\Adobe Films\ElEMd1CxhRNZeDpKLkETdrkZ.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
236
TCP/UDP connections
512
DNS requests
156
Threats
628
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3024 | Setup.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
3552 | Setup.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | — | — | malicious |
3552 | Setup.exe | GET | — | 45.133.1.107:80 | http://45.133.1.107/server.txt | unknown | — | — | malicious |
3024 | Setup.exe | HEAD | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | — | — | malicious |
3552 | Setup.exe | HEAD | 404 | 212.193.30.29:80 | http://212.193.30.29/WW/file1.exe | RU | — | — | malicious |
3552 | Setup.exe | HEAD | 200 | 212.193.30.29:80 | http://212.193.30.29/download/Service.bmp | RU | — | — | malicious |
3024 | Setup.exe | GET | 200 | 2.56.59.42:80 | http://2.56.59.42/base/api/statistics.php | unknown | binary | 94 b | malicious |
3024 | Setup.exe | GET | 200 | 45.144.225.57:80 | http://45.144.225.57/download/NiceProcessX32.bmp | unknown | executable | 259 Kb | malicious |
3024 | Setup.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3024 | Setup.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEANU1M2ZQDK8u8QlB3wxsb0%3D | US | der | 280 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3024 | Setup.exe | 45.133.1.107:80 | — | — | — | malicious |
3024 | Setup.exe | 162.159.130.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
3024 | Setup.exe | 45.144.225.57:80 | — | — | — | malicious |
3024 | Setup.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3024 | Setup.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3024 | Setup.exe | 52.219.170.22:80 | ellissa.s3.eu-central-1.amazonaws.com | — | US | unknown |
3024 | Setup.exe | 212.193.30.29:80 | — | — | RU | malicious |
3552 | Setup.exe | 45.133.1.107:80 | — | — | — | malicious |
3552 | Setup.exe | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
3552 | Setup.exe | 2.56.59.42:80 | — | — | — | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ipinfo.io |
| shared |
ellissa.s3.eu-central-1.amazonaws.com |
| malicious |
stylesheet.faseaegasdfase.com |
| malicious |
jjjjjjjjjjjj.s3.eu-central-1.amazonaws.com |
| unknown |
tg8.cllgxx.com |
| malicious |
baanrabiengfah.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3024 | Setup.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3024 | Setup.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
3024 | Setup.exe | A Network Trojan was detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
3024 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY Possible External IP Lookup SSL Cert Observed (ipinfo.io) |
3024 | Setup.exe | A Network Trojan was detected | ET TROJAN Win32/Unk.HRESQ! MultiDownloader Checkin |
3024 | Setup.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3024 | Setup.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
3024 | Setup.exe | A Network Trojan was detected | AV POLICY EXE or DLL in HTTP Image Content Inbound - Likely Malicious |
3024 | Setup.exe | A Network Trojan was detected | ET TROJAN Win32/Unk.HRESQ! MultiDownloader Checkin |
3024 | Setup.exe | A Network Trojan was detected | ET TROJAN Win32/Unk.HRESQ! MultiDownloader Checkin |
328 ETPRO signatures available at the full report