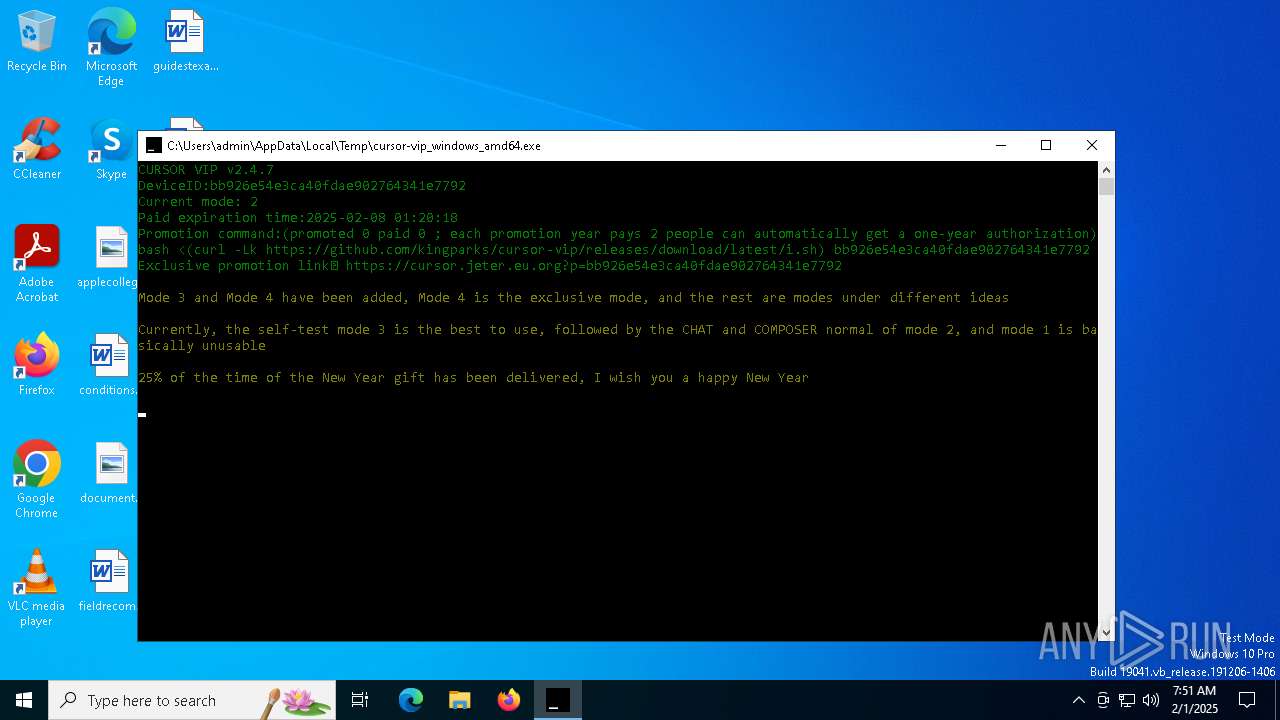
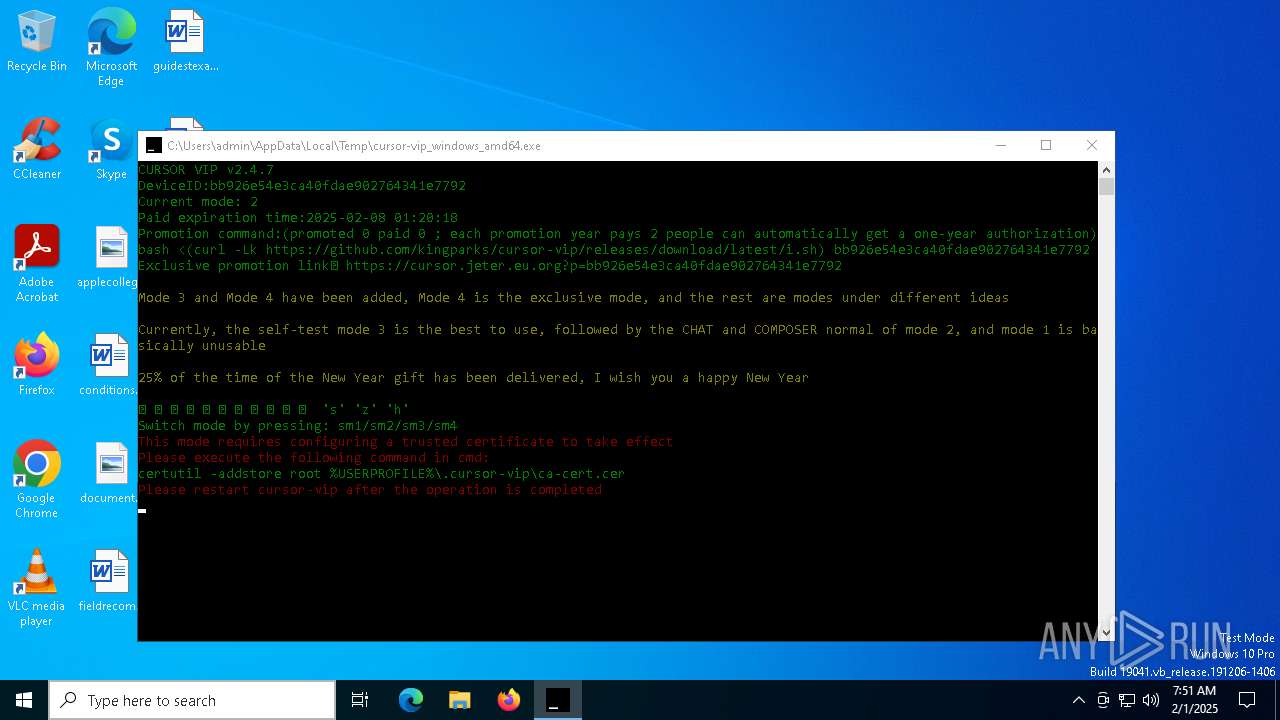
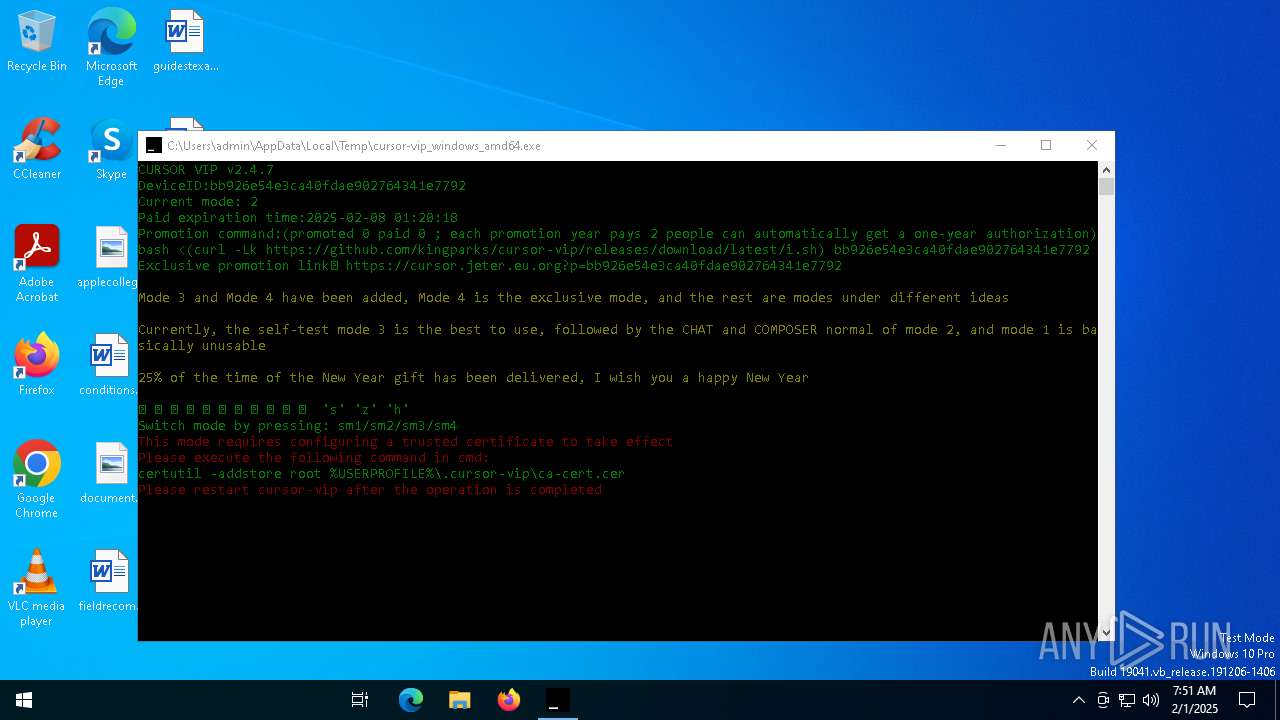
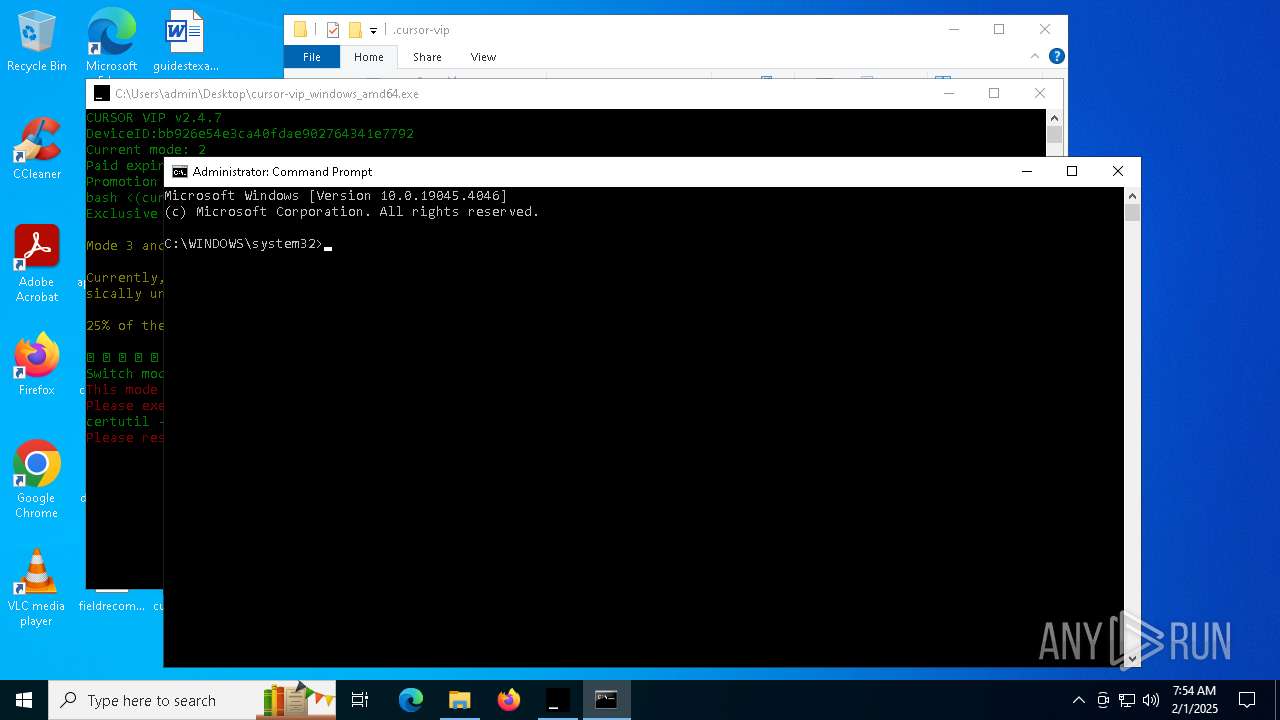
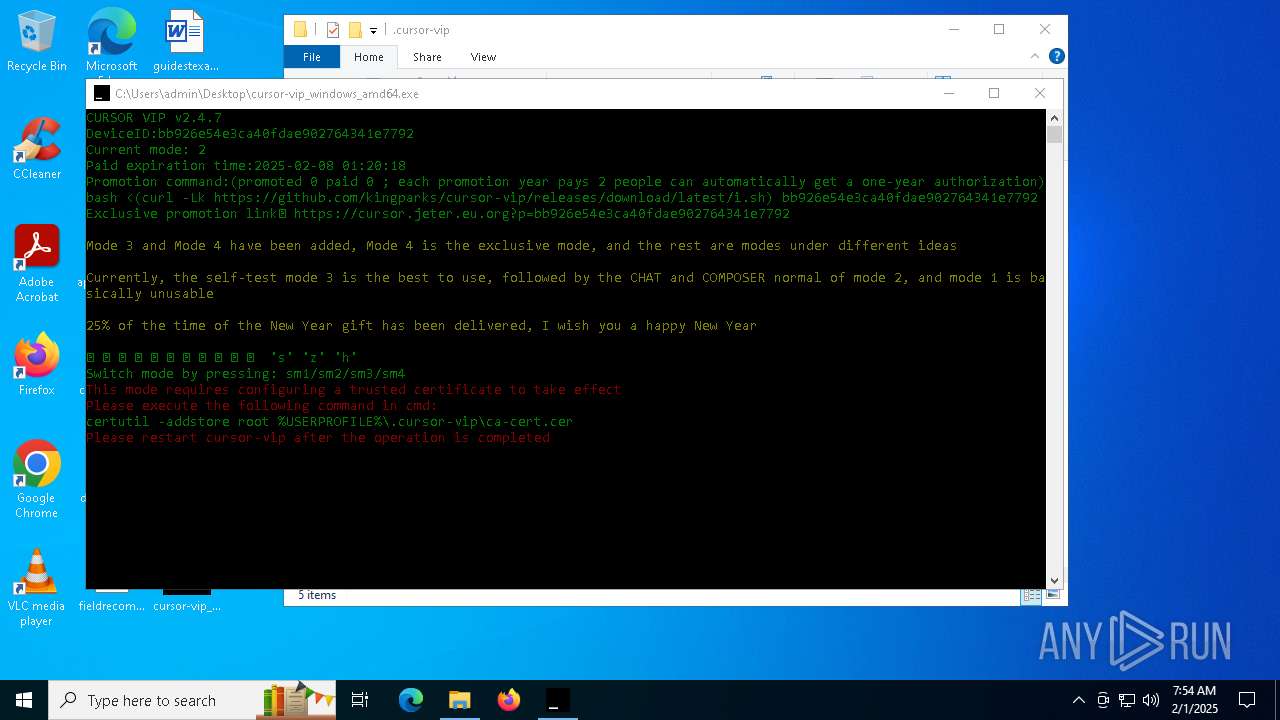
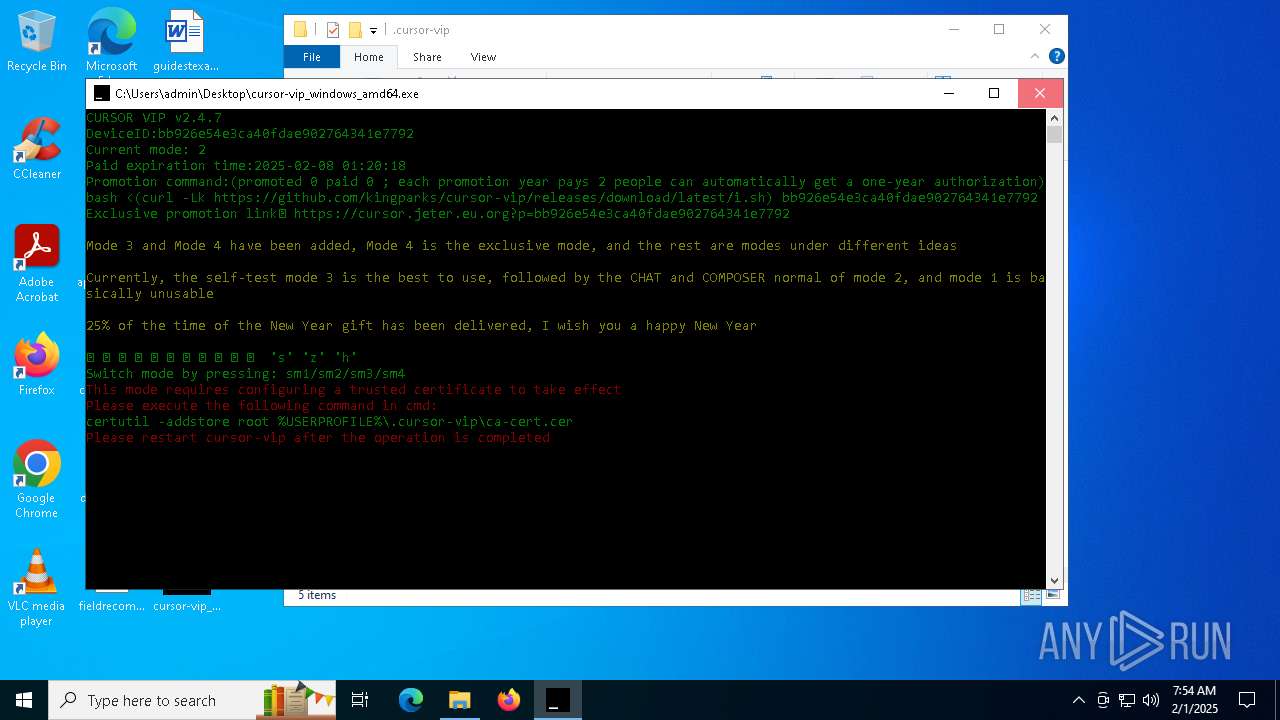
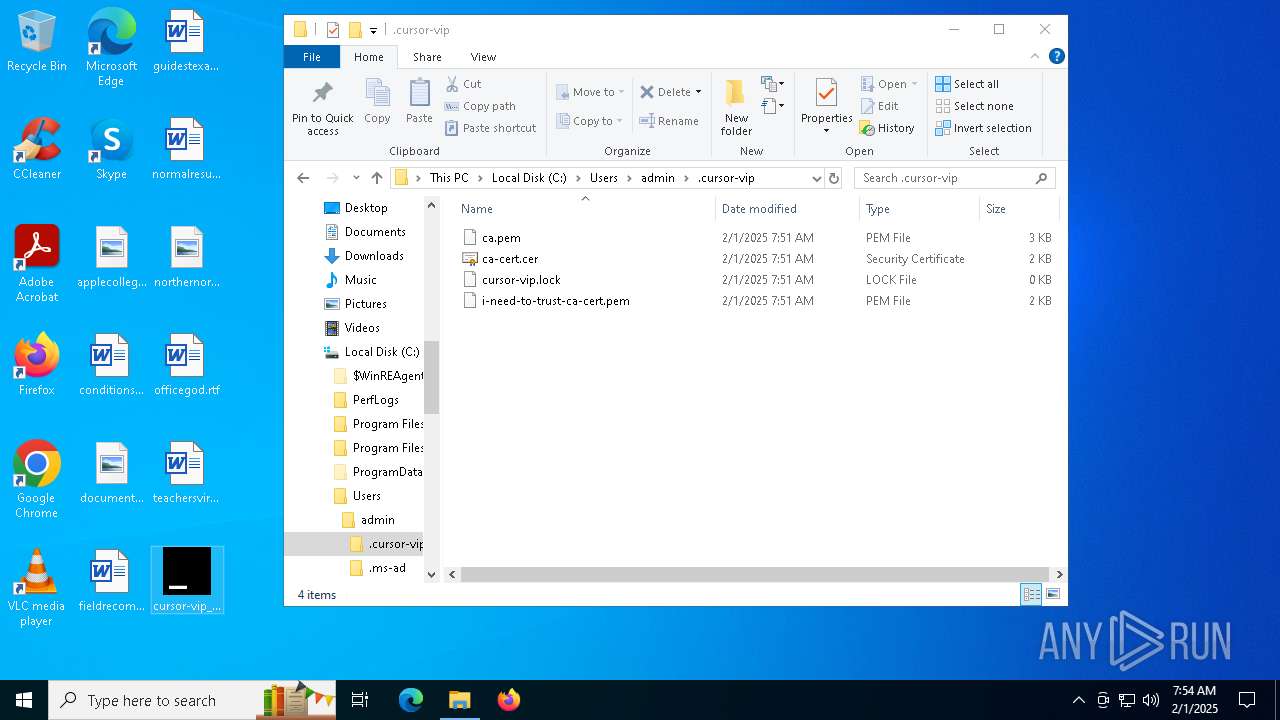
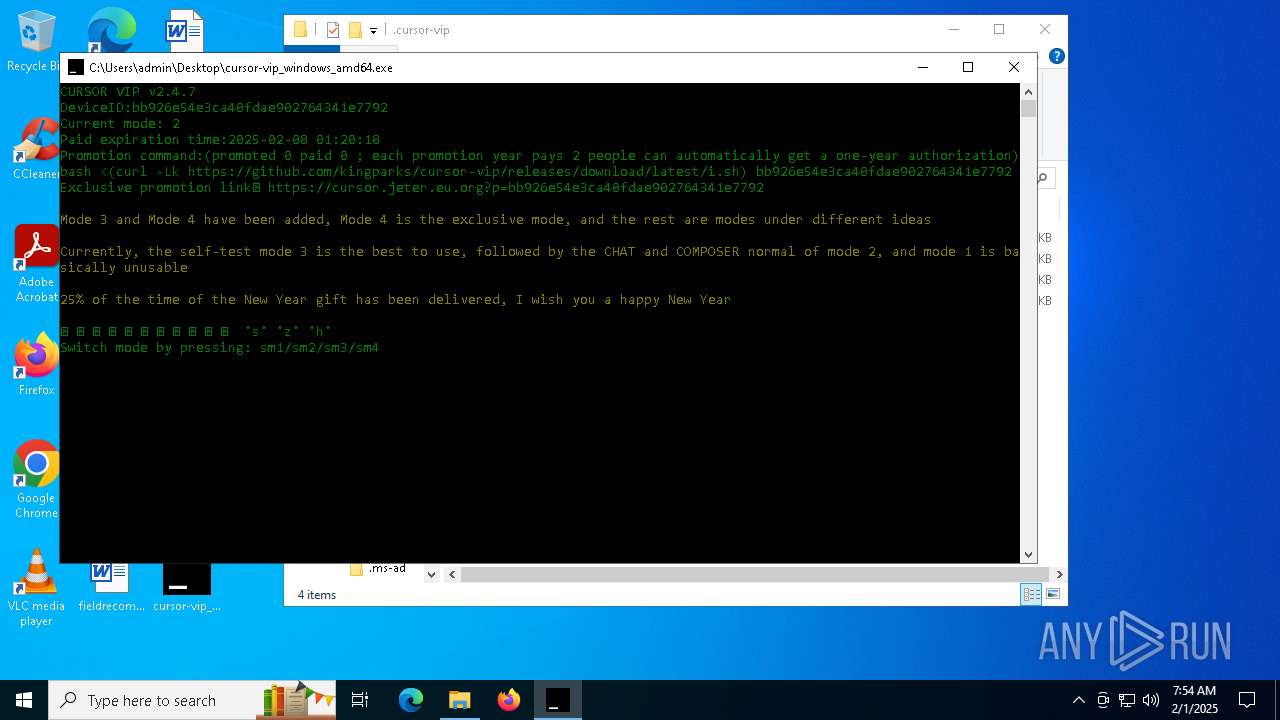
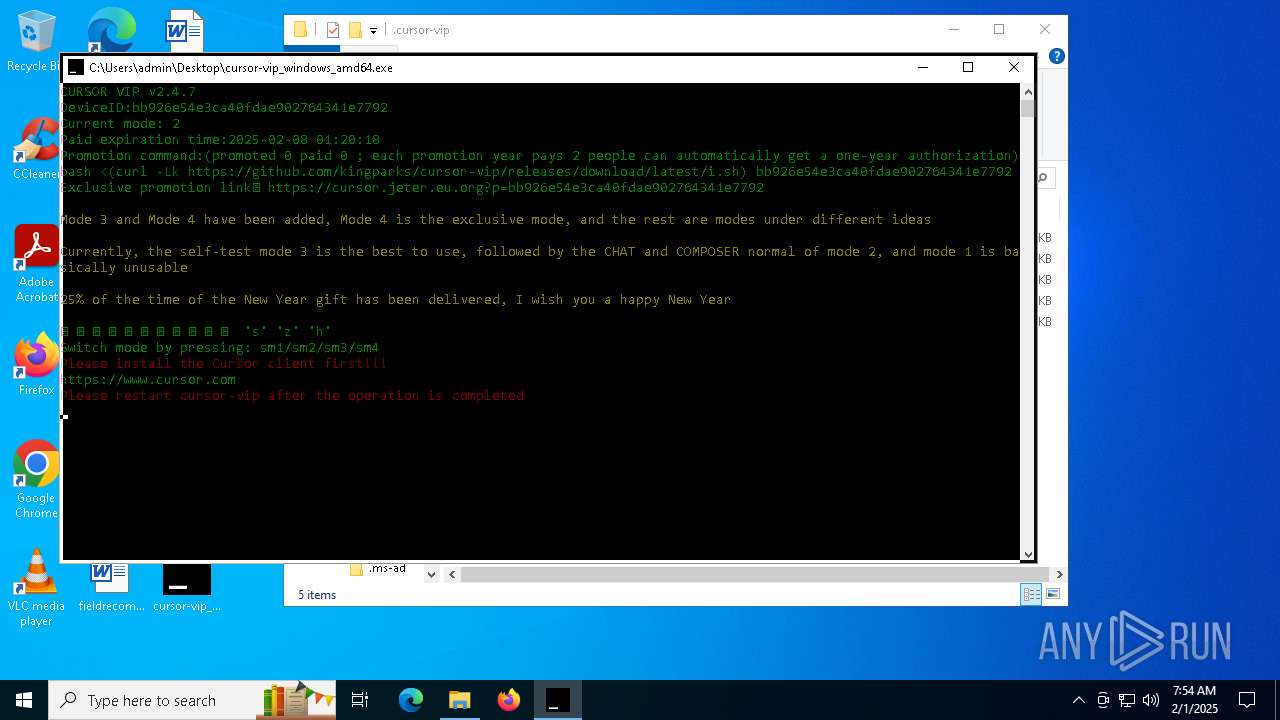
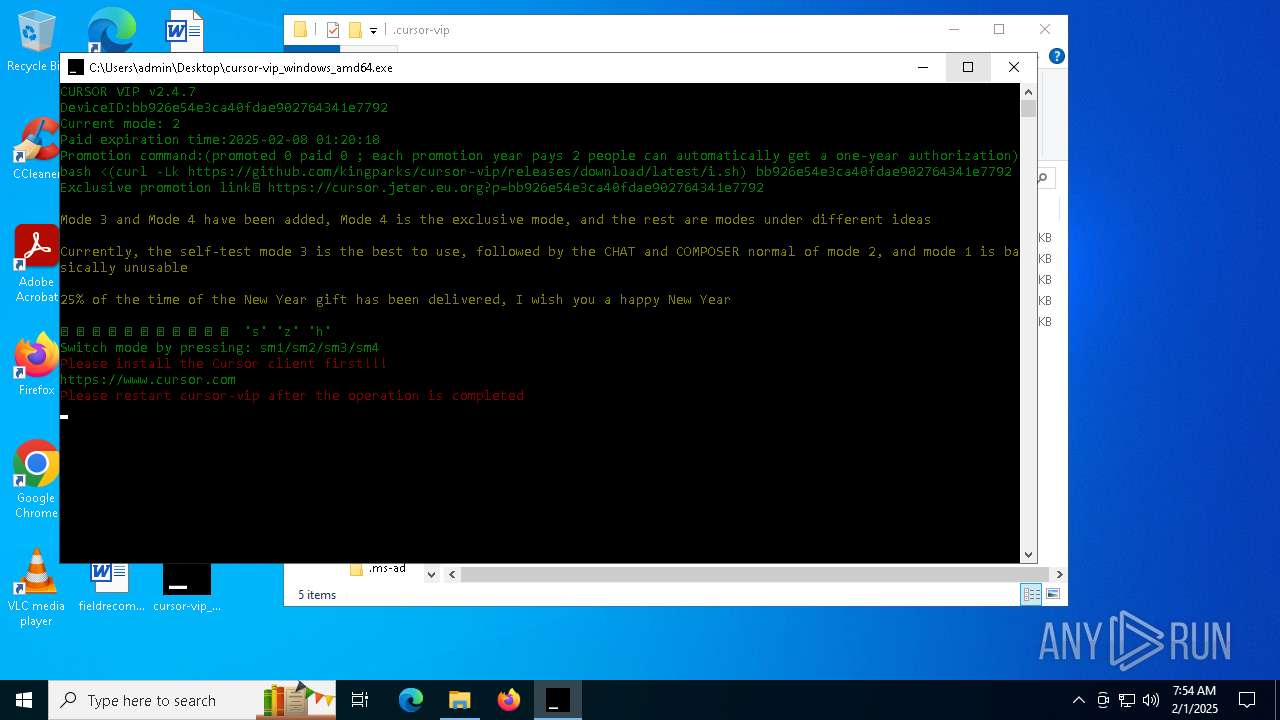
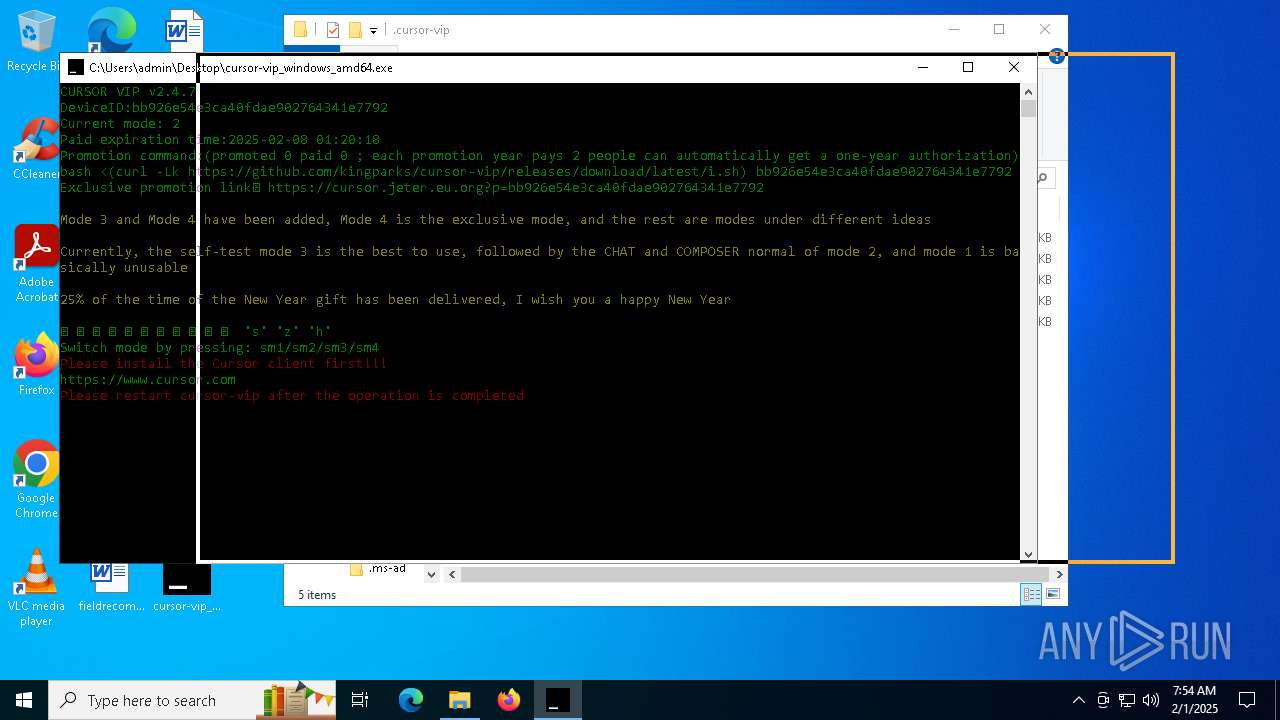
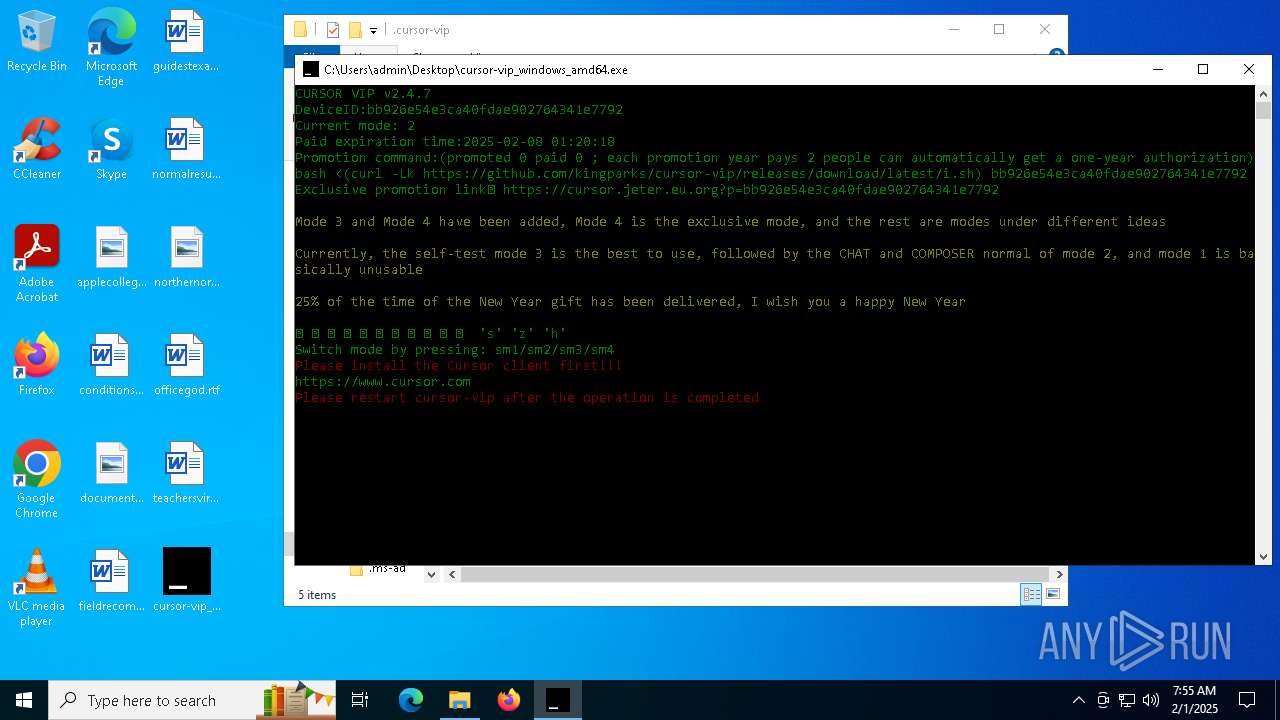
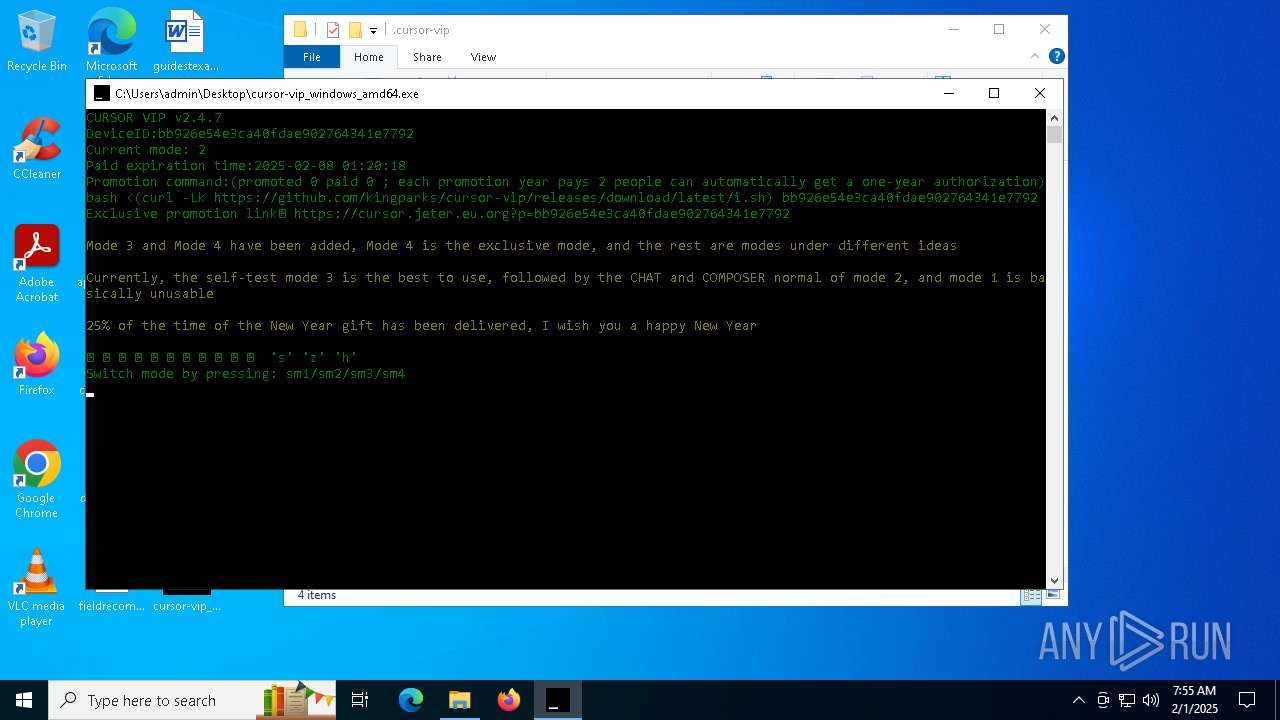
| File name: | cursor-vip_windows_amd64.exe |
| Full analysis: | https://app.any.run/tasks/460e97d7-e843-4cc2-826b-ea12aeb25e1d |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2025, 07:51:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 9 sections |
| MD5: | BA0EF9C8A17A2D74E69D0FDC16F5997D |
| SHA1: | FF1CD2914DCD257381A7D792748C2F5CAA8B47B8 |
| SHA256: | 3BA2CE5EADB71ED9F39F0AC92402137FFF7C6C471E69649CFAFEB81138C30FAD |
| SSDEEP: | 98304:iIGI4qThGHFKDCP6XO91aOhMOCsXQU0DP6n7KytOHD9wfuBC7KOKhq5+ywtlhRZo:Ni |
MALICIOUS
No malicious indicators.SUSPICIOUS
Uses TASKKILL.EXE to kill process
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 2124)
There is functionality for taking screenshot (YARA)
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
Starts POWERSHELL.EXE for commands execution
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cursor-vip_windows_amd64.exe (PID: 1220)
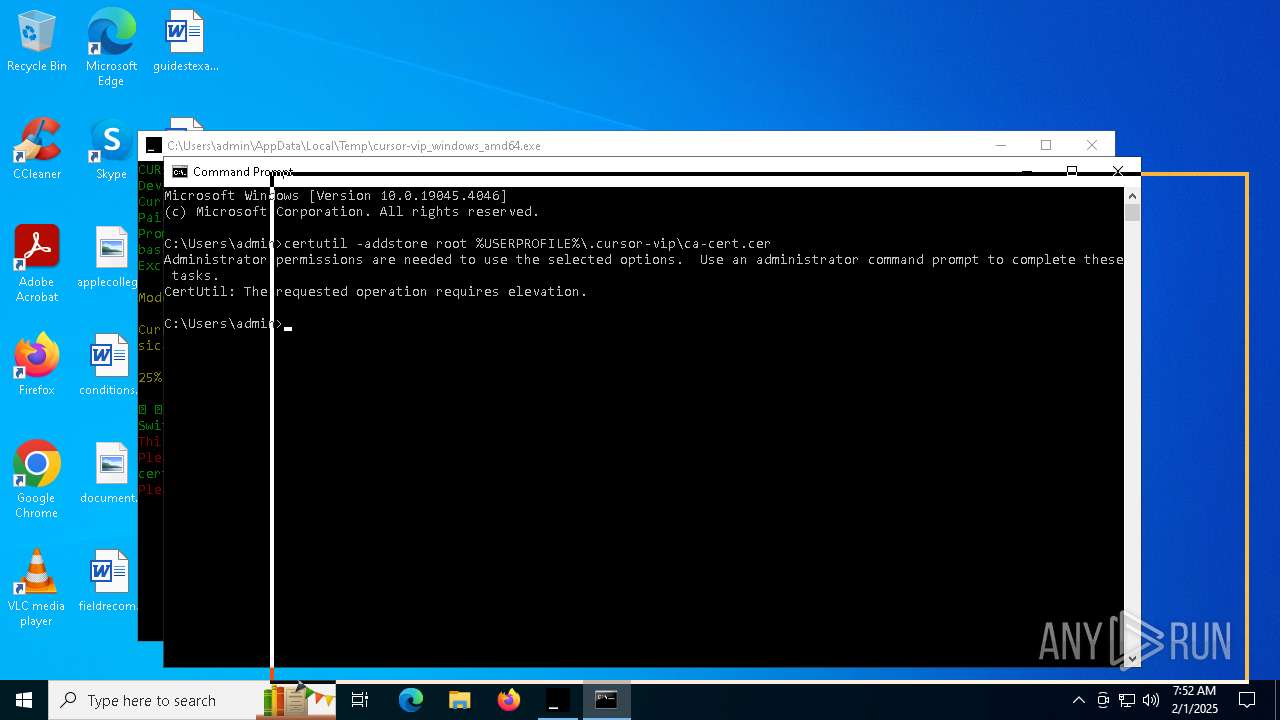
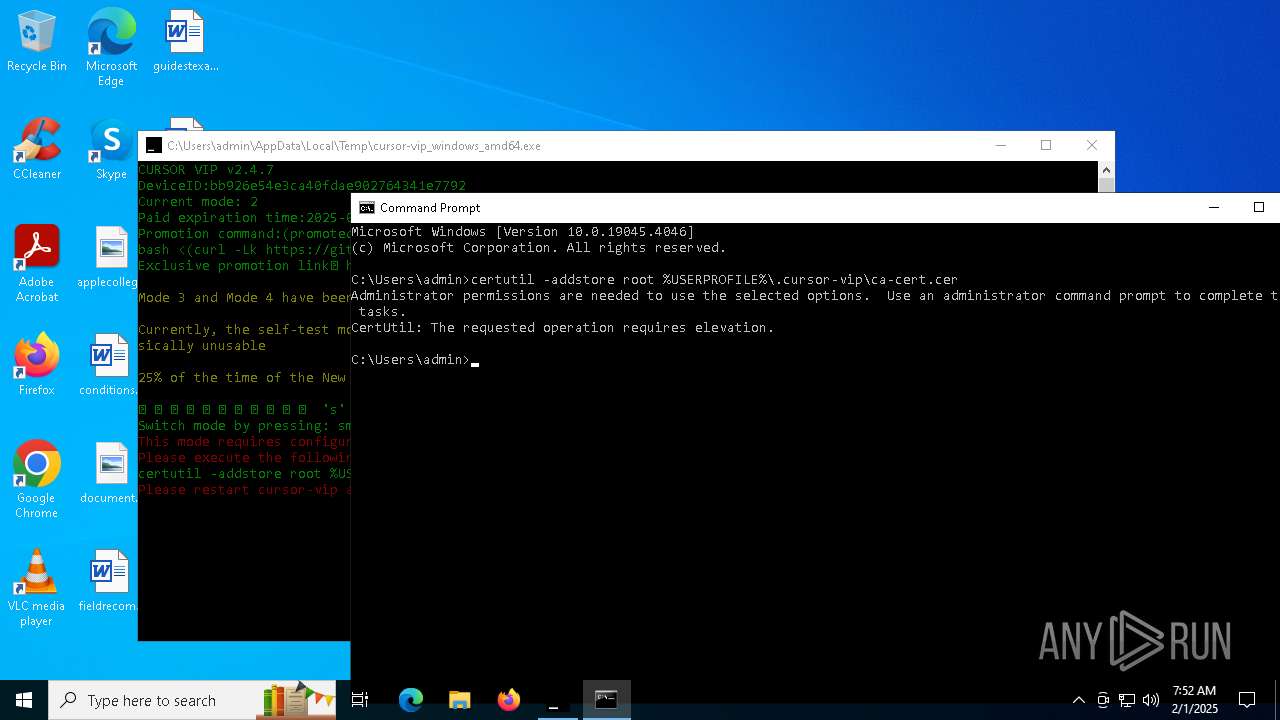
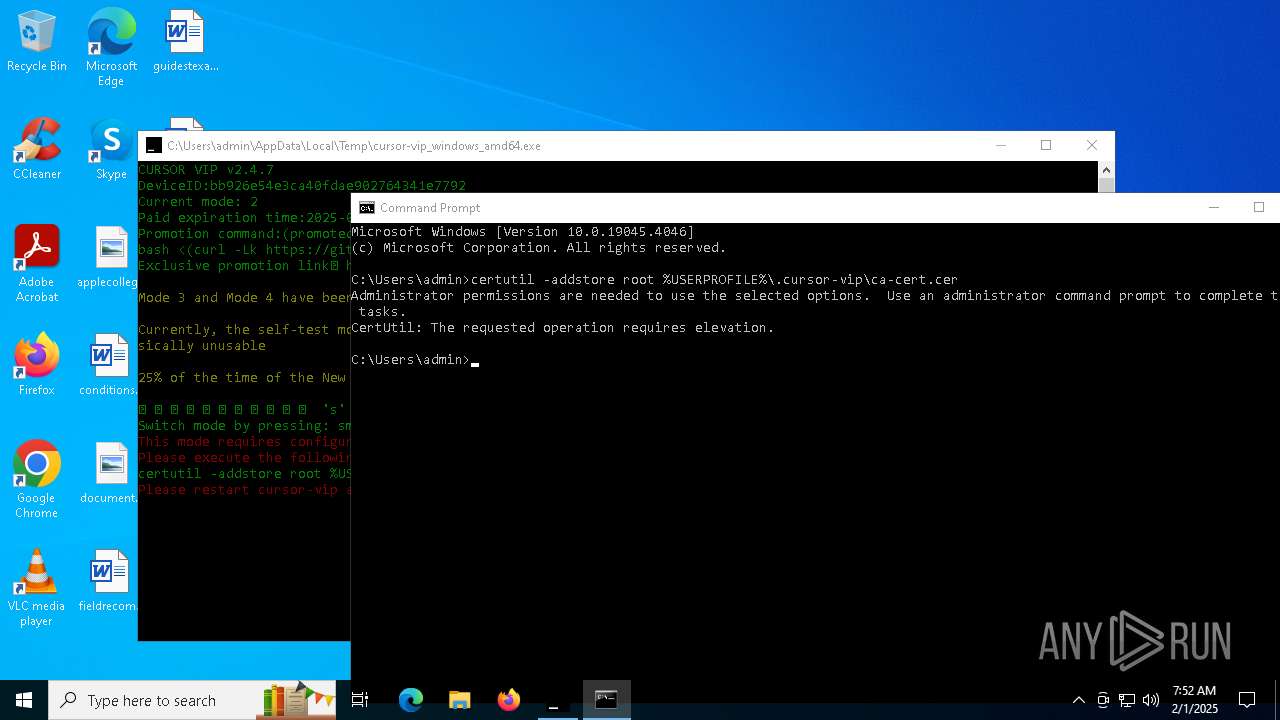
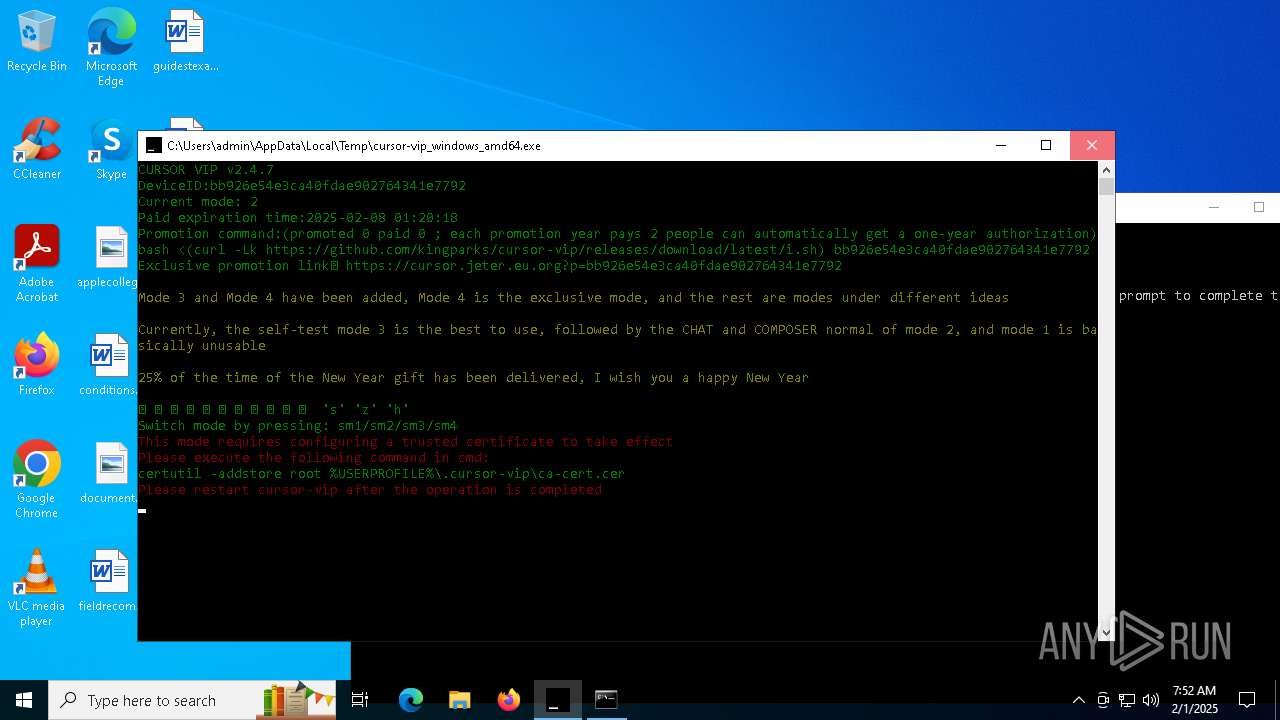
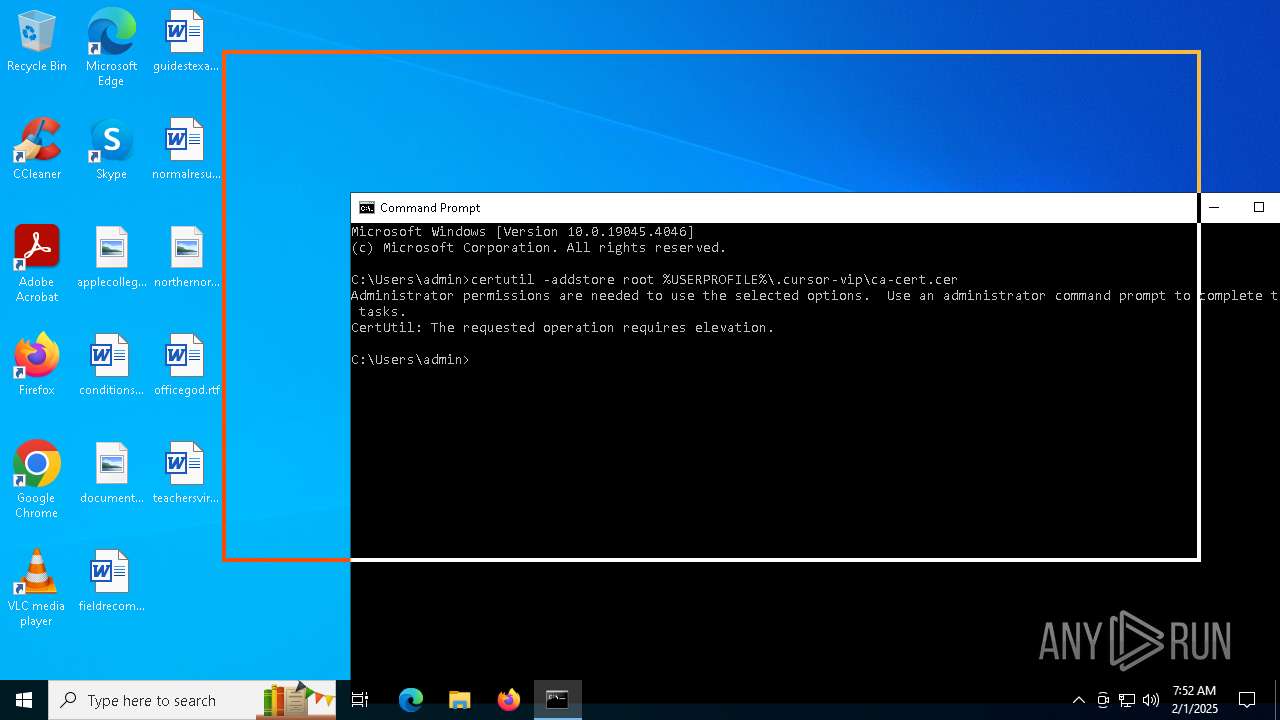
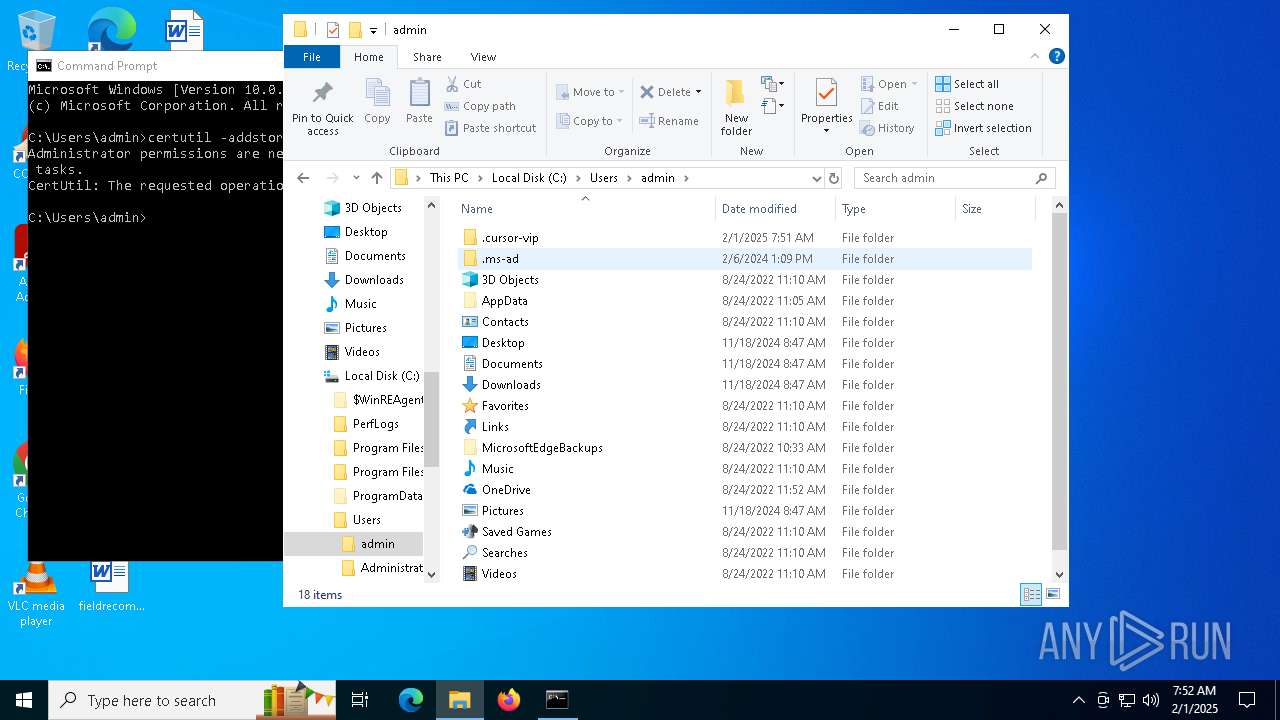
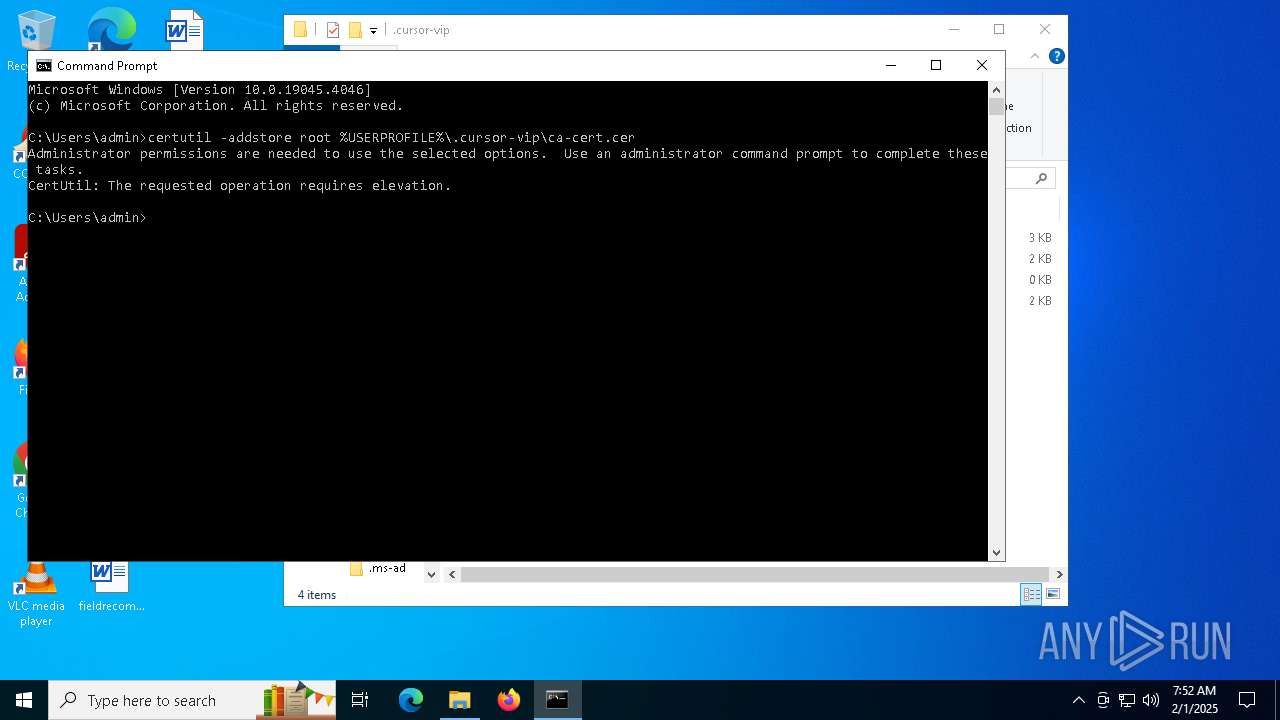
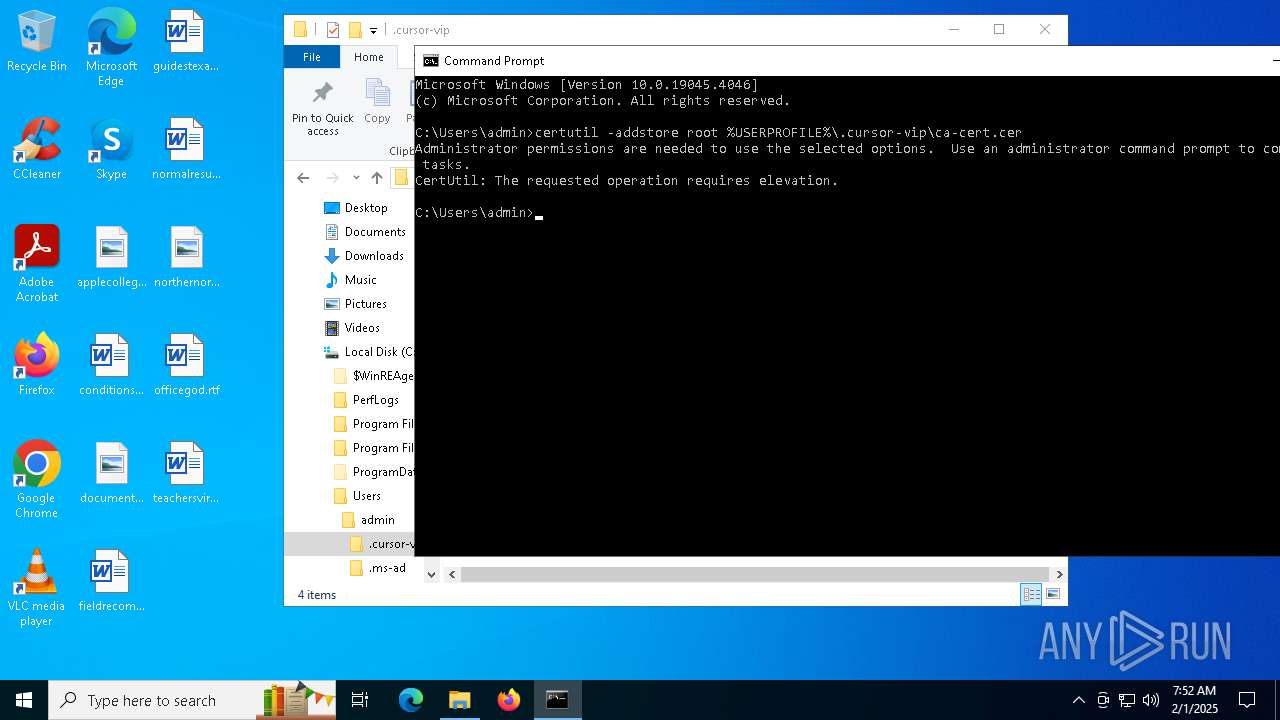
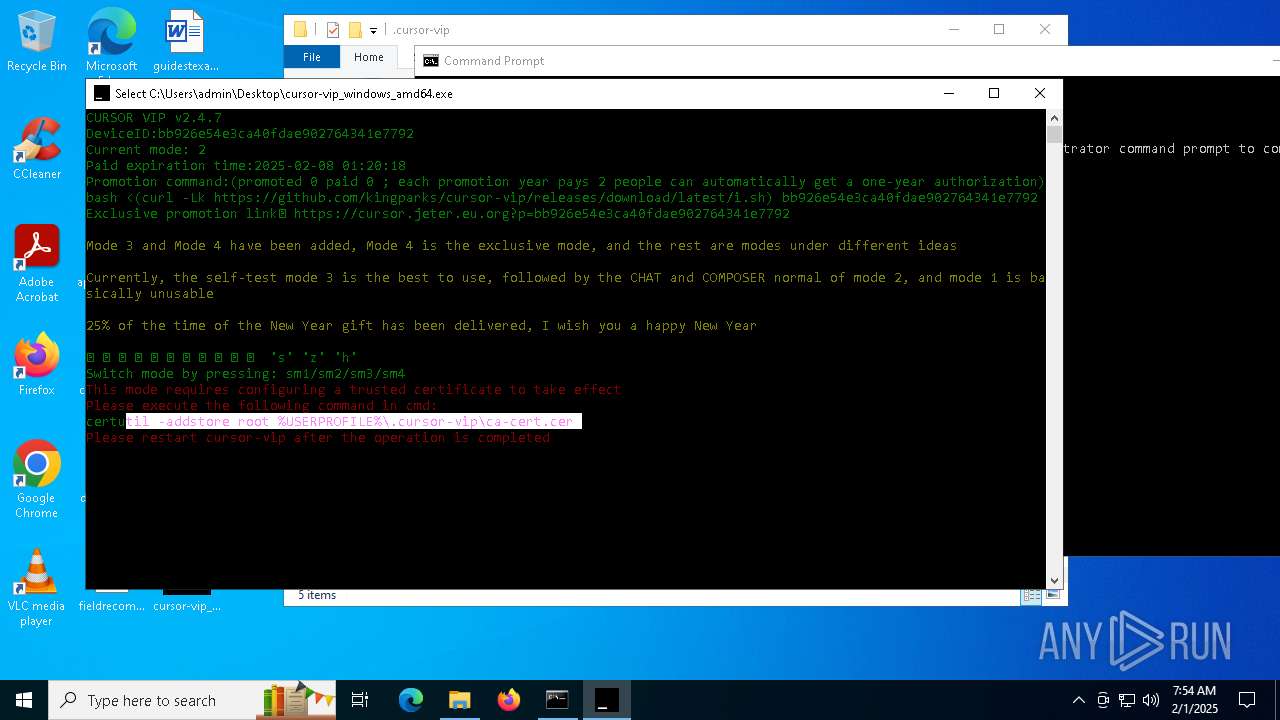
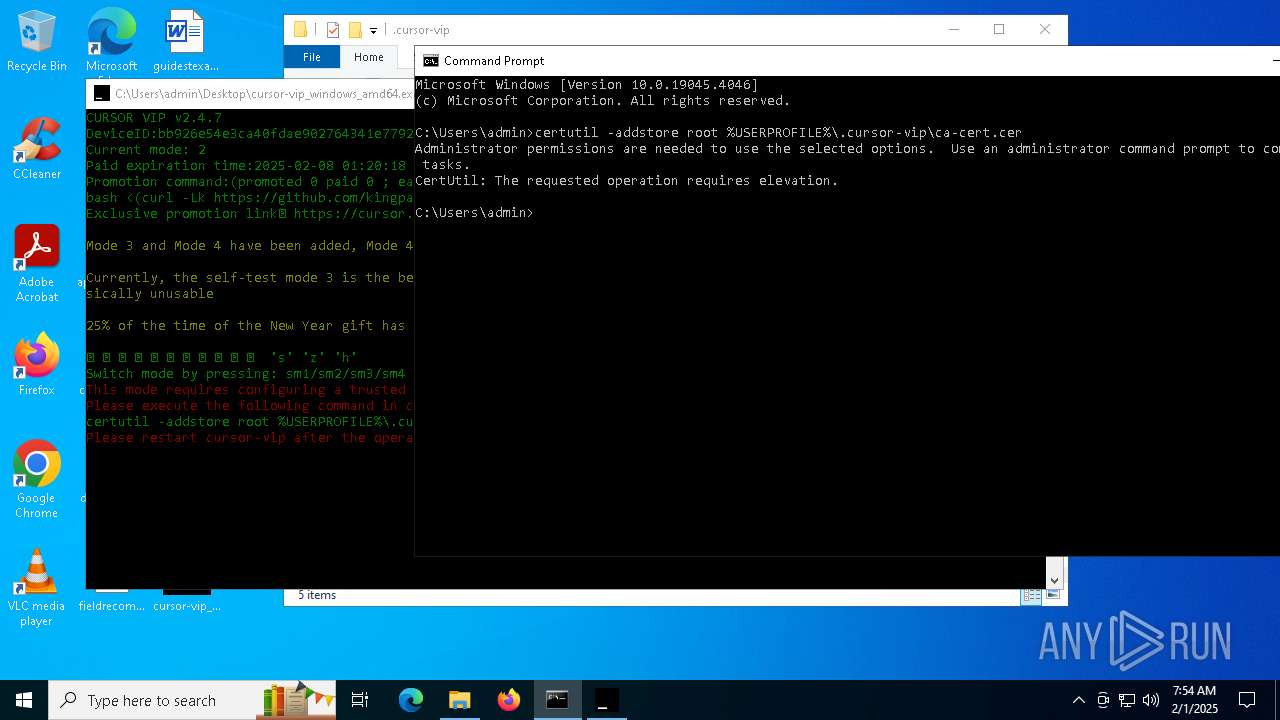
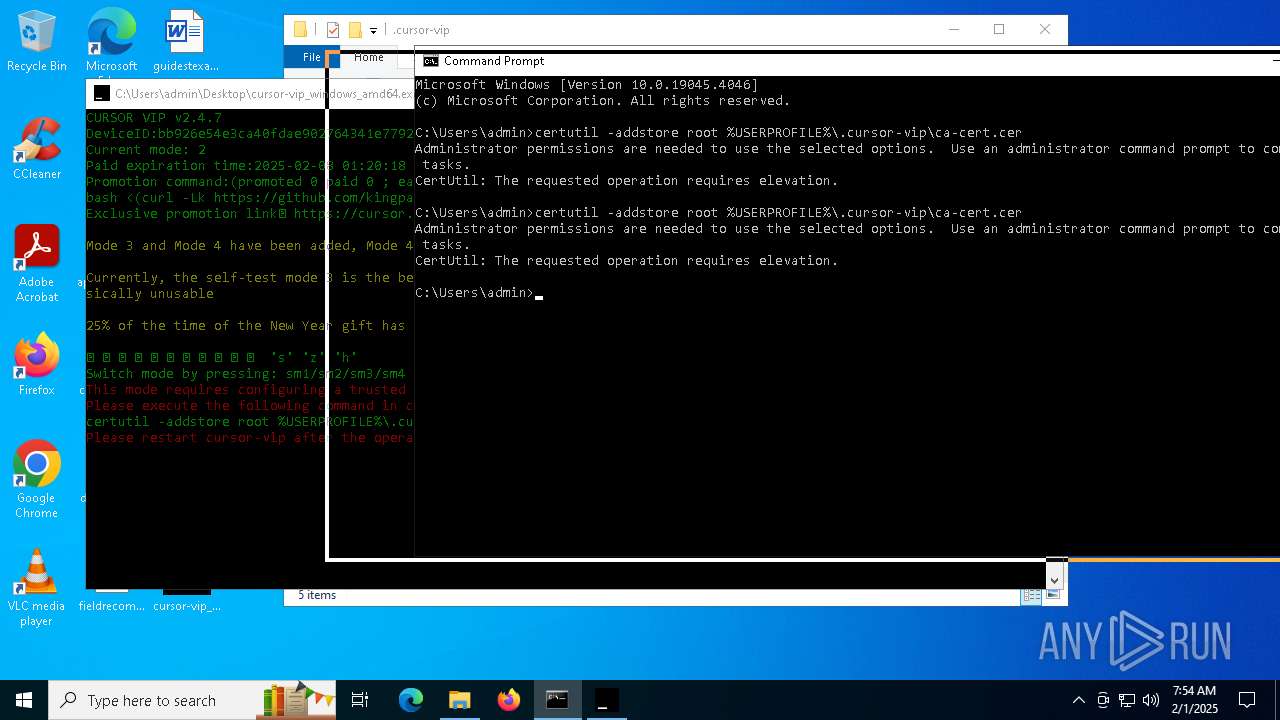
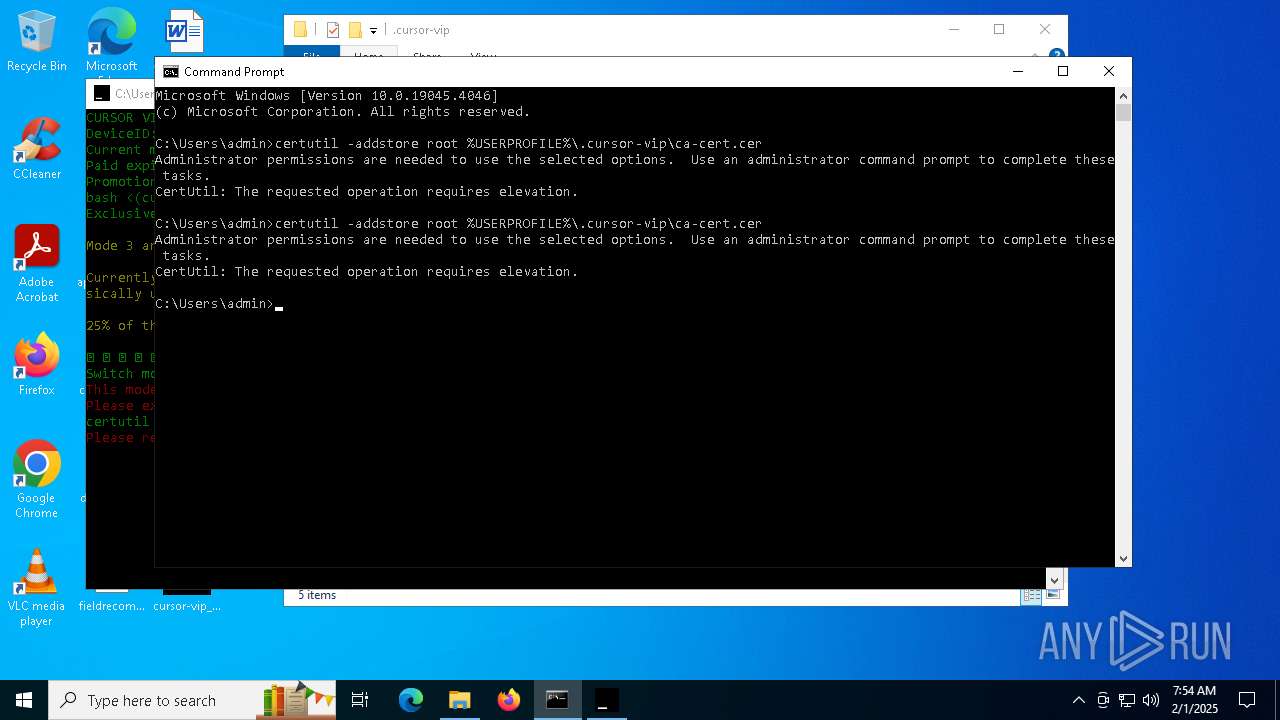
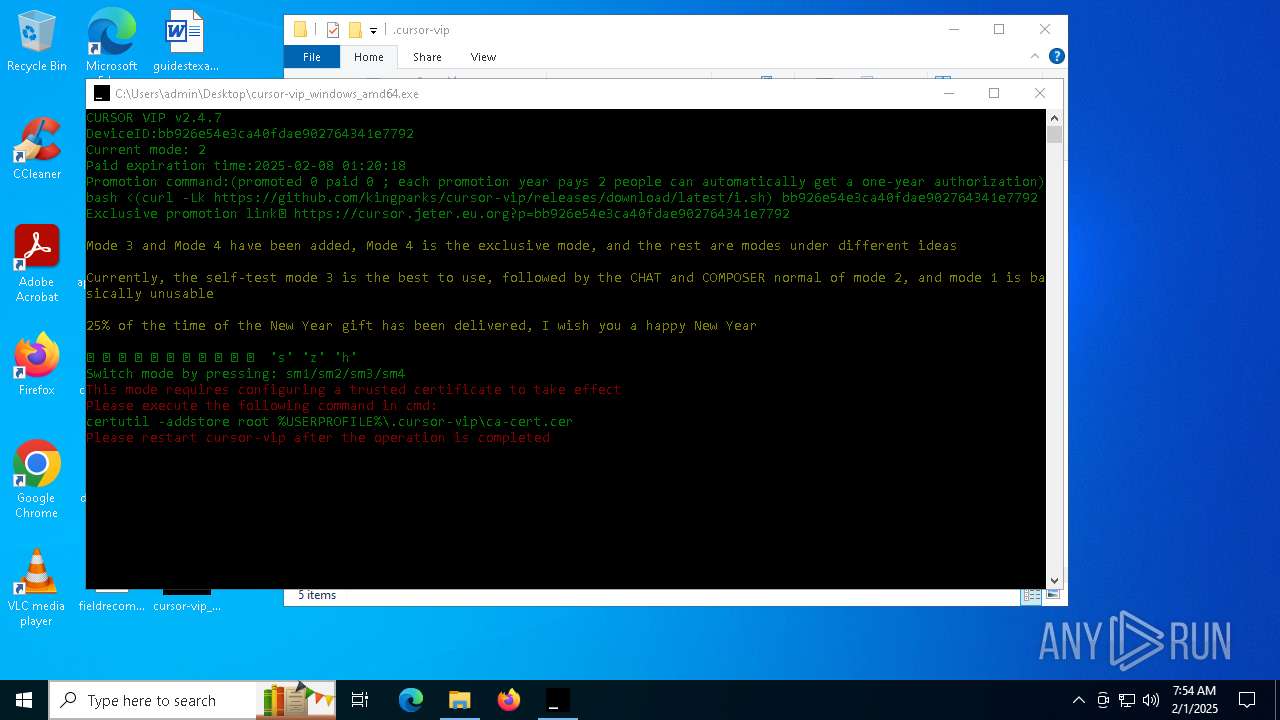
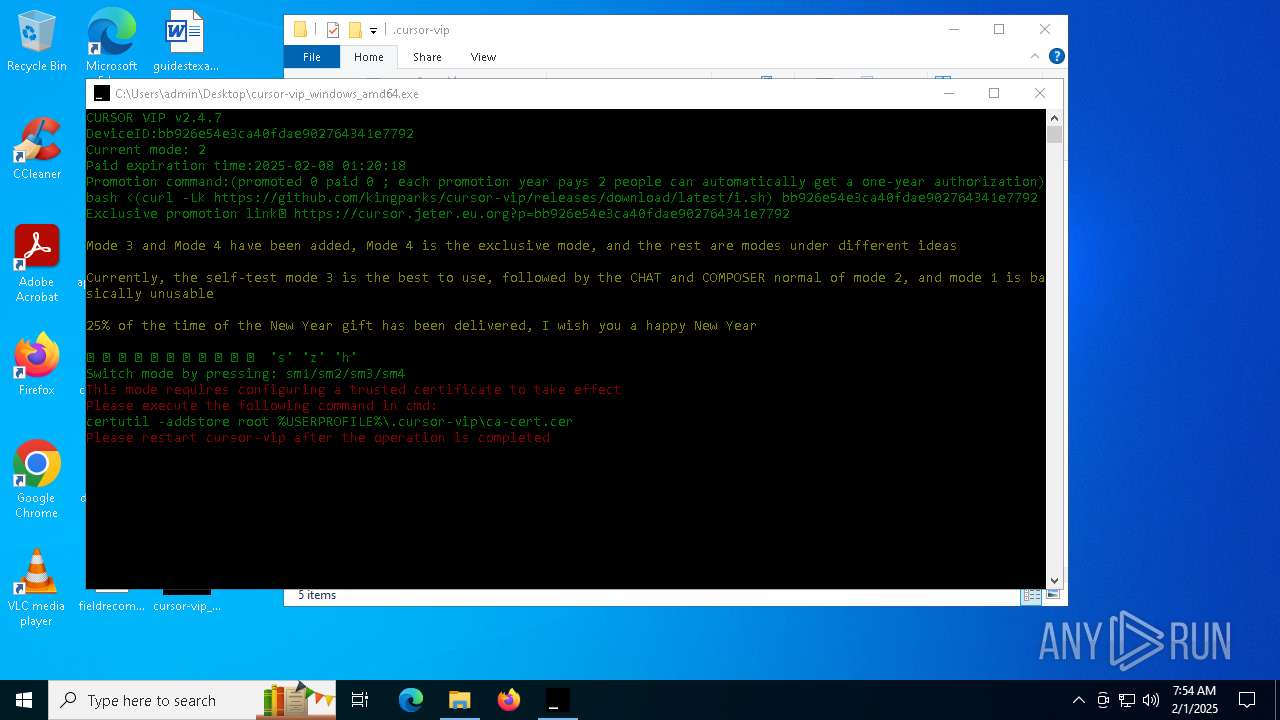
Adds/modifies Windows certificates
- certutil.exe (PID: 6424)
INFO
Reads the computer name
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cursor-vip_windows_amd64.exe (PID: 1220)
Application based on Golang
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
Checks supported languages
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cursor-vip_windows_amd64.exe (PID: 1220)
Reads the machine GUID from the registry
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cursor-vip_windows_amd64.exe (PID: 1220)
Drops encrypted JS script (Microsoft Script Encoder)
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cursor-vip_windows_amd64.exe (PID: 1220)
Manual execution by a user
- cmd.exe (PID: 2464)
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cmd.exe (PID: 6220)
- cursor-vip_windows_amd64.exe (PID: 1220)
Detects GO elliptic curve encryption (YARA)
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
Reads the software policy settings
- cursor-vip_windows_amd64.exe (PID: 5628)
- cursor-vip_windows_amd64.exe (PID: 7024)
- cursor-vip_windows_amd64.exe (PID: 2124)
- cursor-vip_windows_amd64.exe (PID: 1220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 5879296 |
| InitializedDataSize: | 552960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6e1c0 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
155
Monitored processes
23
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1220 | "C:\Users\admin\Desktop\cursor-vip_windows_amd64.exe" | C:\Users\admin\Desktop\cursor-vip_windows_amd64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\Desktop\cursor-vip_windows_amd64.exe" | C:\Users\admin\Desktop\cursor-vip_windows_amd64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2464 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3416 | powershell "Get-Culture | select -exp Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | powershell "Get-Culture | select -exp Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3564 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cursor-vip_windows_amd64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | certutil -addstore root C:\Users\admin\.cursor-vip\ca-cert.cer | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 2147943140 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
34 595
Read events
34 590
Write events
4
Delete events
1
Modification events
| (PID) Process: | (6424) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (6424) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (6424) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (6424) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 6FA0031078F0673146822A9B9D3D875D70B387F4 |
Value: | |||
| (PID) Process: | (6424) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\6FA0031078F0673146822A9B9D3D875D70B387F4 |
| Operation: | write | Name: | Blob |
Value: 0300000001000000140000006FA0031078F0673146822A9B9D3D875D70B387F420000000010000007E0300003082037A30820262A00302010202060FCF84F08603300D06092A864886F70D01010B0500302A31133011060355040A130A637572736F722D766970311330110603550403130A637572736F722D7669703020170D3235303133303037353134305A180F32313235303130383037353134305A302A31133011060355040A130A637572736F722D766970311330110603550403130A637572736F722D76697030820122300D06092A864886F70D01010105000382010F003082010A0282010100A23B86A972DFE1A514A97ACCEBABA9166167EB07B950DE2933E45560BFD1E62066D2302BFB6187EF6802F24D7797C36E4EF399A4E770CD971F4A5FB1E7947C2F22FC93AE146C348A78AB91C721011CD23A19288CA1B18E3482DF9EF173FB7202012E02F01B167EBA881F95522CB5480FD8BAE7FD17FAF1E29B6600E7BD1DB643ED17B07AB651700174106DB2D148D5CCC551632B0DD89AC48BF3C683C32C27680086C8F2FF387A2DD36E92B7193ADB6B4D7190A1AC825FE68CC7CFDBD32003A2C294AC3F50C823D4636C9B7257867FF80D03FFEF0677C8B0ACB8B973600E1B263258819EF68D685D3E72EF0AC7199BEFC49C495CD2EE9D388017F9C79EDA166F0203010001A381A33081A0300E0603551D0F0101FF040403020106305E0603551D250457305506082B0601050507030106082B0601050507030206082B0601050507030406082B0601050507030806082B06010505070303060A2B060104018237020116060A2B0601040182370A030306096086480186F8420401300F0603551D130101FF040530030101FF301D0603551D0E04160414BF3B94175672384CDED024BE66FE71D19D9F7EF5300D06092A864886F70D01010B0500038201010081E786BE6EE9756C1C4929150E02C5773A7D5A7D2345C6C052D3A50260BF0CD491F9127D6860A368F36987610AF84B0F6EE09DDFE1A6F493FA5991600AA7FC230077A16A0DDA92308F6341460B4F75DBB0C9BC81A2D0F0FE89D5E2E0CB9C72F5C733DBD3F6AE9E891DECE226F10BD02F5DE2046A950083CF1FC6321735513ED335C6162F71DFA4403A366ED0DB14A4DC762BE7B4D2F4CA4E3B02F3065760ED6B59465DE1472EE219D76703E9D586B8EAE436E335C7B26B89A7E4BF015A0053E776492019F88202A27D2062601E3F31A2627990A680C7E689ABD025192714556B2FC5FD9DEA2B13060097566ADED8A509E23C004A438FFF996EA54CEA16149B83 | |||
Executable files
0
Suspicious files
1
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6160 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:615FA33AF2248F6046D6C105DF16E6B2 | SHA256:225C2906436791A32583FCF67EBE29A8C10E7BC761EB637E0A2DEA9E56169312 | |||
| 3524 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_a23z13rq.vcj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
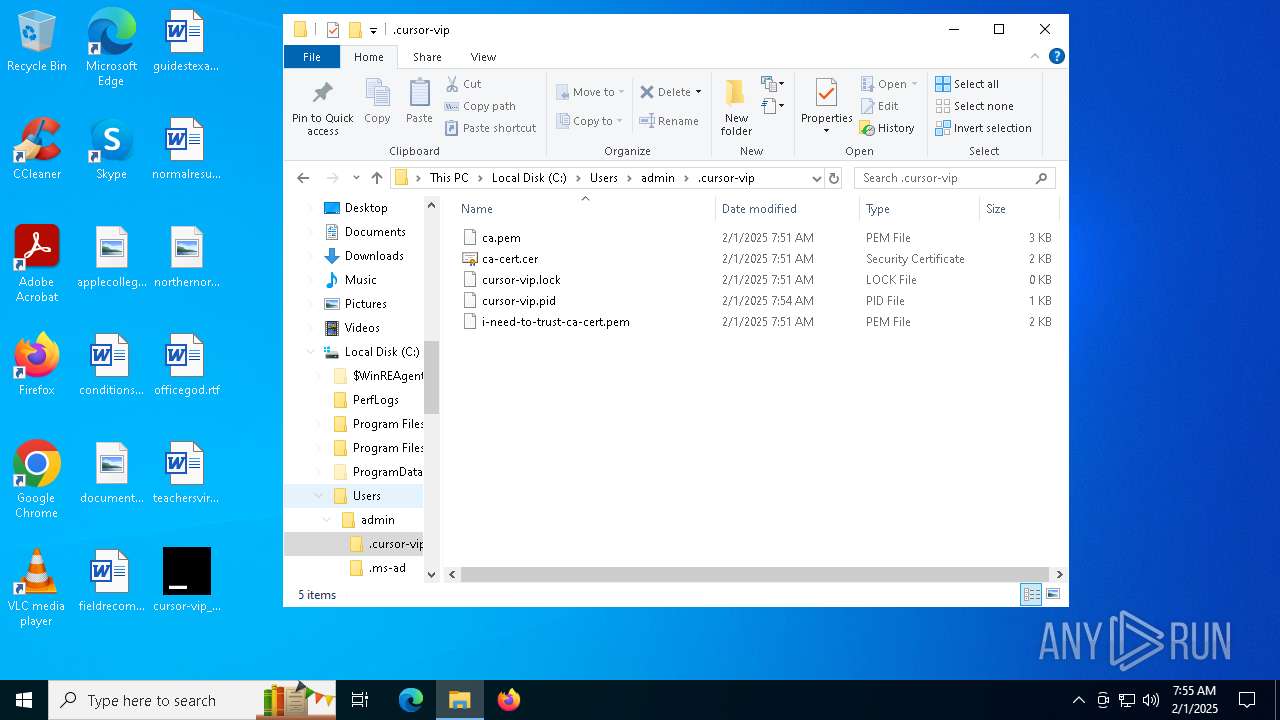
| 5628 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\ca.pem | text | |
MD5:A5E39B1C3F68C3C9EEBC51A0BF6F32A7 | SHA256:26E3908DF33D9584989C43CFF55D57E1F88C2B49060F89CC652CD10C3B60CD71 | |||
| 5628 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\cursor-vip.pid | text | |
MD5:2548A4AC7AD6EDDD035BCED24EC6D964 | SHA256:24DDFBBB780C9417EDDD6483367176CBECF8E97B8E135383EEA7AB936F90130D | |||
| 5628 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\i-need-to-trust-ca-cert.pem | text | |
MD5:A3296AFDF0B583449FB46B72B97E3B18 | SHA256:EEB875A2217F702F19A619ADD3B23AC39C1DFAE2CDEB585700DAEA0422F318F1 | |||
| 1220 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\cursor-vip.pid | text | |
MD5:B24D516BB65A5A58079F0F3526C87C57 | SHA256:F79B8977720743F5E7C8B5B2E3813A8A4CC9AACD97EB20FCF41A7169E66EC1B9 | |||
| 2124 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\cursor-vip.pid | text | |
MD5:EF41D488755367316F04FC0E0E9DC9FC | SHA256:70E8D52A9B4616E728112408CECA7ABD9507E93F30E958ECB09F6EA607D99D06 | |||
| 7024 | cursor-vip_windows_amd64.exe | C:\Users\admin\.cursor-vip\cursor-vip.pid | text | |
MD5:006C64491CB8ACF2092CE0E0341797FE | SHA256:79EF20635E7DF738C608556EE967254FC7CC01C8444FBD6F6BD9E083799592F4 | |||
| 3416 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zxkbmyb4.gcc.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6160 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h5pizh0a.wxi.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
67
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5004 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5004 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7072 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7072 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6520 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5004 | svchost.exe | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5004 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5004 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
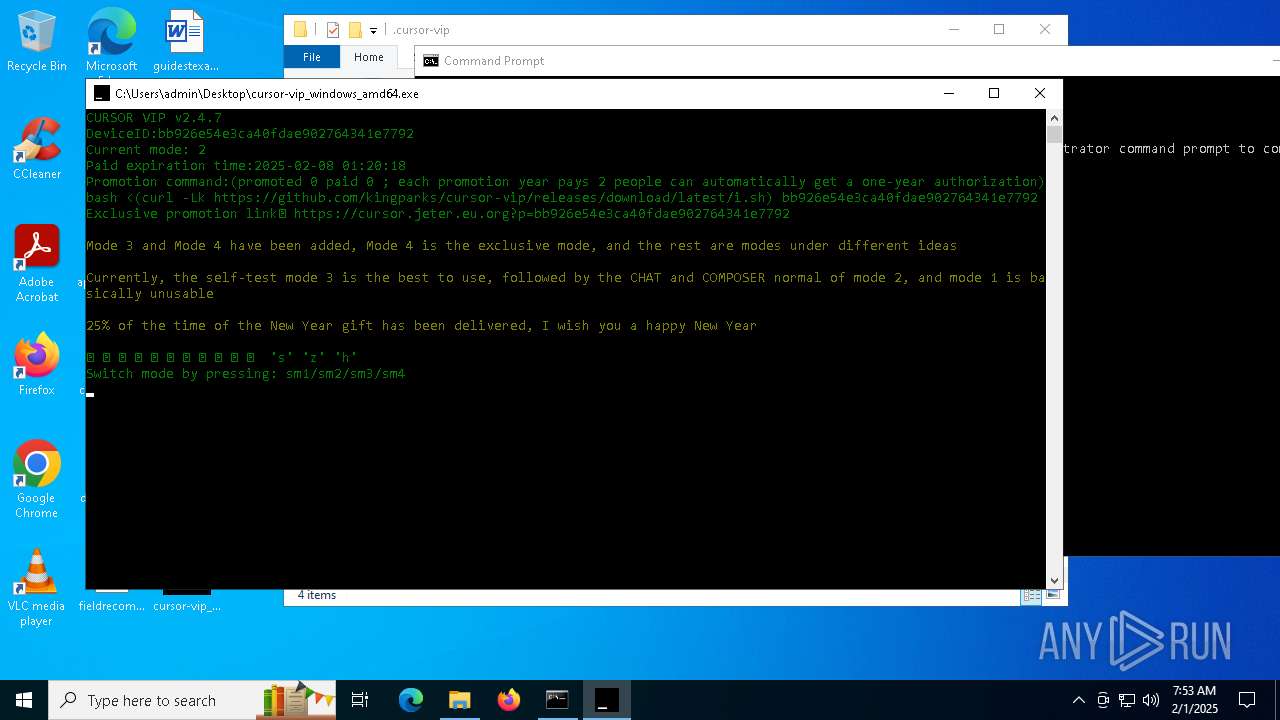
5628 | cursor-vip_windows_amd64.exe | 172.67.147.141:443 | cursor.jeter.eu.org | CLOUDFLARENET | US | unknown |
5064 | SearchApp.exe | 2.21.65.154:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
cursor.jeter.eu.org |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |